Abstract
Internet of Underwater Things (IoUTs) is completely embraced by acoustic sensor nodes that are commonly battery consumption. The sensor’s battery life is restricted and it is problematic while it needs to recharge. Moreover, these kinds of underwater sensor nodes may form the cluster to store the huge amount of energy. The cluster head formation is the main problem that the cluster head needs to use added energy for aggregation and data collection to broadcast the data packets to the destination. The autonomous underwater vehicles (AUVs) have to be used to connect the sensor nodes with the internet or particular devices, the path discovery within the AUV is the primary issue for producing the efficient routing in IoUTs. In this paper, the proposed routing strategy is used to provide energy proficiency while performing the cluster-based routing. AUV is responsible for selecting the cluster head and maintaining cluster-based scheduling. The AUV path is constructed to increase the residual energy for the sensor nodes in the network. It coordinates the AUV’s effective way of arranging calculations into the steering convention. This incorporated specialized strategy depends on two stages: A-ANTD (AUV-Assisted Network Transmit Devising) and TARD (Transmit Assisted Route Devising). A-ANTD uses the collaboration of performance of multiple ventures to decrease energy utilization for the system and stays away from the problem area and sector issue with a vital GN (Gateway Nodules) plans. The experimental results show that the proposed methodology has improved performance compared with the other methods.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Wireless underwater mobile sensor networking (Patil et al. 2019) is that the enhancing technology for these applications that accommodates a variable variety of sensors and vehicles that area unit deployed to achieve cooperative observation (Pompili et al. 2006). To attain this aim for sensors that are deployed randomly with the ocean-atmosphere to utilize the submerged systems administration might be a fairly obscure space however submerged interchanges are tested with high constriction anyway zone unit disappeared with dispersing (Hirai et al. 2012). Besides, the transmission of optical flags needs high exactness in educates the slim optical gadget shafts. Accordingly, interfaces in submerged systems zone unit upheld acoustic remote interchanges (Ali 2014). The typical technique for sea section perception is to forward the submerge sensors that store data all through the perception mission (Ayaz et al. 2012). Non-wired method of information transmission via the Ocean is one amongst the sanctioning technological aspects in the futuristic levels of Ocean- observatories and Detector Networks (Harold Robinson et al. 2019a). Various uses of Underwater Wireless Sensor Networks vary from Refining Industries to cultivation, and embody instrument observance, Pollutant & Pollution Control Management, Weather Data Processing, and prediction of natural calamities Earthquakes & Tsunamis, Deploy and Hunt missions, and examining the deep-aquatic environments etc. (Ruoyu et al. 2013).
Underwater Mobile sensor networks with acoustic transmissions are having unique challenges like the utilization of huge transmission power, huge propagation delay and mobility of the nodes (Chen et al. 2010). The delay-aware opportunistic communication scheduling algorithm is commonly constructed for underwater mobile sensor networks (Yoon et al. 2012). It utilized the local data to improve concurrent communication with minimized collisions (Chen and Lin 2013). The improved procedure that allows the outstanding packets in the sender side that facilitating multiple communication sessions has been used for increases the entire throughput (Carlson et al. 2007). Every node knows the adjacent node’s propagation delay data and their transmission schedule to improve the packet transmissions along with the proposed methodology (Harold Robinson et al. 2019b). This method mainly focuses on achieving enhanced channel utilization by reusing the temporal and spatial data (Salva-Garau and Stojanovic 2003). The performance evaluation shows that the proposed algorithm generates the fairness in medium access whenever the node mobility is alive (Harold Robinson et al. 2019c). Hence, the proposed method also accumulates the transmission energy by reducing the collisions with increased throughput (Mainwaring et al. 2002).
The proposed algorithm has organized to implement for IoUTs (Rani et al. 2017) to provide energy-efficient routing (Ayaz et al. 2011). In this methodology, AUV gathers the data from the clusters in the networks for creating the cluster head formation (Harold Robinson and Golden Julie 2019). For data collection, the cluster is formed for real-time data communication to analyze the status of the residual energy (Huang et al. 2014); AUV selects the cluster head from the group of nodes (Akyildiz et al. 2005). The shortest routing path is used for collecting data through the AUV with the utilization of energy (Kredo II and Mohapatra 2007). Hence, the reduction of energy consumption has been achieved through the proposed algorithm for producing the optimized path with energy efficiency through AUV transmission (Wang et al. 2016). The sensor nodes are placed in the underwater environment through the mobility-based beacon architecture for identifying the localization and the position of the nodes in the network (Guo et al. 2019). Whenever the coverage related problems occurred in the network, the weak k-barrier coverage framework is utilized (Shen et al. 2019). The protocol stack is used to provide the energy efficient data transmission in the network (Goyal et al. 2019). The cluster head related routing illustrates the reduced amount of average communication cost in the network (Bhattacharjya et al. 2019).
The Major challenges prevailing in the transmission media and routing are done with the radio and optical signals under the terrestrial wireless sensor networks. The transmission parameters use the high frequency radio signals to initiate the transmission (Alsalih et al. 2008). While communicating through the low frequencies and for long transmission, the power utilised and energy usage is higher (Vimal et al. 2020a). This is the preliminary challenge that has a high impact of looking for routing algorithms and protocols, and also the protocols which are applied to IoT cannot be applied directly to the IoUT (Pasupathi et al. 2020). So in order to analyse the findings the proposed method is paved with the hybrid model and clustering algorithm to analyse the IoUT transmission and routing process (Vimal et al. 2016). The Hybrid model is proposed in a way to support the table-driven and On-Demand Routing with multicast tree formation using the IoUT (Vimal et al. 2020b). The challenges that mostly prefer in the IoUT is the Delay that has about 1500 ms. The reliability is another challenge and it should be low and unstable. In terms of energy, it is hard to replace or recharge (Annamalai et al. 2019). The bandwidth is assumed to be between 10 and 100 kbps (Qiu et al. 2020). The proposed hybrid model will analyse all these facts in terms of bandwidth utilisation, cluster formation, Multilevel routing to monitor the performance evaluation with minimal energy utilization.
The main contribution of the paper is
-
The proposed hybrid algorithm is utilized to minimize the energy utilization for the sensor nodes which are battery oriented.
-
The fixed time period is maintained to perform the cluster based transmission technique to forward the data to the cluster head within the specified time slot.
-
The performance evaluation is conducted to produce the result of minimized energy utilization for the cluster head and the other sensor nodes.
The paper is organised as follows, Section 1 highlights the Introduction section, Section 2 presents the Related works, Section 3 explains the proposed methodology with the experimental study and implementation, Section 4 proposes the performance valuation and finally, Section 5 concludes the paper with future works.
Related works
In Cascading Multi-hop Reservation and Transmission (CMRT) (Lee and Cho 2014), most of the adjacent nodes start their handshaking process between the source and destination. Due to this relaying, cascade and makes the data to be delivered down to the destination. Apart from the above, CMRT also improves the channel utilization in a very efficient manner through the process of adopting a packet generation in which multiple data packets are aggregated jointly by handshaking. It subsequently minimizes the time required for exchanging the control packet and thus it enhances the throughput. In CMRT, intermediate node processes its moves within several dissimilar states such as WaitResp, Idle, DelayData, WaitData, DataRx and DataSilence. WaitRespis mainly enhances the state of making the node to wait for the proper response from the receiver to the control packet. DelayData mainly helps the hidden nodes in avoiding the possible collisions by making the sender delay the data transmission. WaitData is the state in which it makes the receiver to wait for time to get the reliable data from the sender. In DataRx state the receiver receives the data packets from the sender.
In order to avoid collisions between the neighbour nodes, silence node helps in making the channel reservation to remain silent when there is a cause for neighbour node to overheard the swapping the control packets (Pinjari et al. 2018). The remaining state which was not included in the above comes under the idle state. The Segmented Data Reliable Transport (SDRT) (Xie et al. 2010) has been developed to attain the dependable data relocate in underwater sensor circumstances. It mainly adopts high efficient random forward error correction codes, erasure codes, in order to move the determined packets hop by hop or block by block (Dey et al. 2018). It gradually reduces the total amount of communicated packets thereby improving the energy and also shortening the services. Basically, it is a hybrid approach of both Forward Error Correcting (FEC) (Xie and Cui 2007) and Automatic Repeat Request (ARQ) (Tomasi et al. 2015). The packets are mainly communicated to the destination from the source that apart from the data packets, an intermediate node will be encoding each data block using the process of random forward error correction codes and also it pumps the encoded data packets into the channels (Chen et al. 2001). As soon as the receiver gets the encoded packet, immediately decoding process will be done to extract the original data blocks (Rosalie et al. 2018). The Multi-hop related energy proficient MAC protocol (Zenia et al. 2016) is mainly preferred for overcoming the packet collisions happened and also the proposed protocol efficiently produces the multi-hop networking by splitting the 1-hop disputation resolution methodology (Roy and Sarma 2018). In this approach, the first phase illustrates the elimination of local nodes from the contention by the way in the final phase the undesirable possessions of hidden nodes are diminished (Yu and Fei 2016). Hence, this methodology of providing 2-hop contention resolution technique mainly improves the quality of service.
The data communication entails that packet is efficiently received by the determined receiver (Chen et al. 2018). After that, data communication has been visualized by the three parts of the logical time frame. In limited link reservation, the period slots play a major role in determining the contention round. For efficient usage of the process, short-duration tones are highly preferred for resolving the contention that happened among the nodes (Li et al. 2019). In order to consume the energy loss, two types of receivers such as data receiver and low power wake up tone receiver are used (Dey et al. 2020). The extra features will enhance the process by ensuring the nodes in the hidden links by rescheduling the receiving data packets towards the destination (Harold Robinson et al. 2019d). Geographic routing protocols are very familiar with limited required signalling and scalability (Jiang et al. 2016). A global positioning system is highly used for global systems for correctly plotting the position of several sensor nodes in which some among them are not working properly in an underwater environment (Jain et al. 2019). Apart from these routing protocols, certain sensors, UAVs (Liu et al. 2019), UUVs (Xu et al. 2019), etc., are used to recognize the exact position irrespective of other approaches. In vector-based forwarding routing (Chengzhi et al. 2020), a little portion of the nodes in routing is involved such that it does not need any state data on the sensors (Harold Robinson et al. 2019e). In a distributed geographical routing, the nodes work in either greedy mode or recovery mode for efficient delay insensitive applications (Cai et al. 2013a). The recovery mode is activated in the case of a node failure to forward a message to the next feasible neighbour node (Cai et al. 2013b). The threshold-based Energy efficient modeling has been framed to provide enhanced energy consumption (Feng et al. 2019). The security has been increased and providing the quality of service with the data aggregation technique (Goyal et al. 2020). The transmission has been established using the overlay network model in the network (Pavitra and Janani 2019). The grid related routing technique has been implemented to ensure the reduced amount of hop count for providing the active transmission (Al-Salti et al. 2019). The target tracking technique has been established with noise-based multiplicative function (Luo et al. 2019) and the Energy efficiency is improved using the computational technique (Luo and Han 2019). Gonzalez-Crespo R et.al., proposed that the Ant colony optimization and K-Means Clustering algorithms has been used to search the shortest route analysis from source to destination. This ACO algorithm is applied to measure the Quality of Source (QoS) constraints in IoUT environment (Kumar et al. 2020). The IoT network atmosphere increases the response time with the time aware scheduling model for IoUT (Núñez-Valdez et al. 2020). Table 1 outlines the most important UW sensor types deployment in terms of localization approach and their limitations.
The common drawbacks for the energy efficient cluster based routing mechanism are the increased energy consumption, maximum end-to-end delay and several issues for cluster head selection procedure. Sometimes, the connection within the Internet and the devices through the autonomous underwater vehicles are weak. So, the deployment of the sensor nodes is an important factor for constructing the Internet of Underwater Things in real-time (Vedachalam et al. 2019). The minimized end-to-end delay while transmitting the AUV travelled distance with the highest amount of cluster head is the challenging task for routing in the Internet of Underwater Things (Shinde and Olesen 2018; Schaller and Mueller 2009).
Proposed methodology
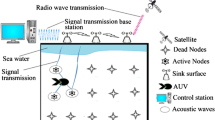
The proposed architecture for constructing the Internet of Underwater Things is encompassed of a sink based surface floating on the sea that broadcasts the monitoring station through the link which contains the AUV of underwater wireless communication channel. Figure 1 demonstrates the Architecture of proposed hybrid optimization routine maintenance. The proposed Hybrid is done for making the transmission without end to end delay, good transmission coverage and with low bandwidth without no network issues. The proposed Hybrid Optimization routing maintenance has been constructed with two phases. Phase I contains A-ANTD (AUV-Assisted Network Transmit Devising) and Phase II contains TARD (Transmit Assisted Route Devising). Phase I computes the AUV timestamp for selecting the cluster head, Phase II calculates the Reply time to produce the signal to ratio. The 2 Phases have constructed the Hybrid optimization routing maintenance. Table 2 illustrates the symbols used in this proposed methodology for producing the computation and the abbreviation denotes the methodologies are used in the related methods. It is also used to define the variables to be used in the computation.
Network formation
The AUV provides the path to communicate the deep-sea sensors through the sink surface with the ability of energy and data processing. The sensor nodes are deployed in the random model to the surface station with the location data for every sensor nodes. The location data using region-based is segregated into different kind of sectors for utilizing the proposed methodology (Paul and Rho 2016).
Figure 2 demonstrates the architecture for Internet of Underwater Things that the Base station is responsible for providing the routing functionality. The base station is connected with the surface station which is interconnected with the cluster head and the sensor nodes. The cluster is formed and the cluster head is selected based on the communication range of the specific sensor nodes.
Phase I: A-ANTD (AUV-assisted network transmit devising)
A-ANTD goes for structure vitality effective information dispatch course among AUV and sensor nodules. In An ANTD, AUV is accountable for communicating HPs and gathers information from sensor nodules while transitory an area (Vimal et al. 2018). At the point when sensor nodules get HP, it ensures whether the HP ought to be sent or not. On the off chance that the HP might be sent, the sensor nodules refresh the transmittable table into the delivering cushion. At the point when the delivering period is prepared, the sensor nodules could invigorate and advance these HP. In the meantime, several sensor nodules that get HP from AUV, forward ARP to AUV to request GN capability, and they may gather information after AUV disappears in the event that they are picked as GN. In light of the transmittable table, a dynamic multi-jump information dispatch course can be worked among AUV and sensor nodules (Rho 2015). A Hello Packet is broadcasted to initiate and frame a Network Structure or Scheme. This event triggers when the length of the AUV touches X meters. The obtained HP’s are dispatched by the sensor nodules to construct data dispatch routes to the AUV. The HP withholds totally four fields namely: AUV Time Stamp, Nodule ID, The Layer ID and Hello Packet Sign. HP’s broadcasted time variables are contained in the AUV’s Timestamp. The sensor which has dispatched the HP has its own physical address which id the Nodule ID (Vimal et al. 2017). To perform extrication of packet type is established using the Hello Packet Sign. Here, in this data dispatch route, the Layer ID is a labeling of the obtained nodule. Initially, when the AUV broadcasts the HP, the value of the Layer ID is one, whose value gets incremented by one each time by the sensor nodule when it determines to push forward the HP until it reached the threshold n. n value should not be too large in order to prevent the pre-mature energy deprivation of first-hop nodules which may contain way too many no. of child nodules. A settable threshold n and the communication range of the nodule are utilized to set the value of X (Paul et al. 2015).
This system consists of multiple AUV’s which roam around in non-static paths to gather data & information and send it to the Ground control or the Base Station. This event triggers when the length of the AUV touches X meters. The route is constructed in such a way that it can collect data at a very high rate. Initially when the AUV broadcasts the HP, the value of the Layer ID is one, whose value gets incremented by one each time by the sensor nodule when it determines to push forward the HP until it reached the threshold n. n value should not be too large in order to prevent the pre-mature energy deprivation of first-hop nodules which may contain way too many no. of child nodules. They receive hello packets and are capable of forwarding them to other nodules (Ayyanar et al. 2019). It also senses the nearest AUV and GN’s.
Routing scheme is established during packet switch which can hold network constructs & schemas to keep the route devising intact and make sure the nodes are connected. Based on the received data, ON decides whether to choose GN or the AUV. GN at times can enact as an ON when AUV dispatches a Hello Packet & it directly broadcasts data that is stored to the AUV. A DRP is dispatched by the nodule to search & spot out the AUV’s even before the information gets initialized and sent. AUVs and GNs that get the DRP, forward DRPRs to the dispatch nodule. At the point when the dispatch nodule gets the DRPRs, it picks the principal feed-backing AUV as next jump or picks the primary feed-backing GN as adjacent bounce when there is no input from AUV. AUV picks some specialist nodules among the initial-bounce nodules as GNs. They in-turn gather information once the AUV changes position. Sensor nodules, those of which attain a Hello Packet along with a Layer ID of one, dispatches an ATP to AUV to request GN capability. It comprises of 5 fields: ATP Signature, Nodular ID, Nodule Placement & Distance, No. of Neighbors, and Unconsumed Energy. Every sensor nodule keeps in count the total number of neighbors it has. ATP signature is utilized in such a way that it separates and the packet standard within the system. The physical location of the nodules is called as the Nodule ID. The distance of separation between the primary jump nodule and the AUV is called as the Nodule Distance. Number of Neighbors is the quantity count of all sensor nodules’ neighbors both in transmittable table and in Neighbor Nodules Catalogues. The remaining levels of energy of the Sensor nodule are called as the Lingering or Residual Energy. AUV’s picked the GNs relying upon the ATP & ascertains for every first-bounce nodule, a weight GN. Table 3 demonstrates the transmit Information Sustained by the Sensor Nodule.
The centroid point is generated for the cluster in each sector that the cluster nodes are connected with the sensor nodes in the transmission range through the AUV. The centroid point is computed in Eq. (1).
The entire region is traversed by sector; the AUV is capable of delivering the status report to the cluster head in IoUTs. For providing the active transmission in underwater, the establishment of channel is essential task for underwater environment. The frequency is computed using Eq. (2)
The noise variation is computed using frequency and it is computed in Eq. (3)
The timer for delay is computed using Eq. (4)

Phase II: TARD (transmit assisted route devising)
At the point when the relocation extent of AUV achieves V meters, AUV communicates HPs and shifts gradually amid a Random period. Amid this period, AUV communicates HPs at in excess of three unique locations, and after that AUV may find the main bounce nodules effectively. Along these lines, the geology area of first-bounce nodules could be assessed. AUV picks a gathering of GNs from the initial bounce nodules amid and saves the area of the GNs. The AUV strategy is an active way relying upon some several key focuses and transmit data that may ensure that AUV gathers information within an information serious way. What’s more, AUV can change the estimation of V to maintain a strategic distance from transmitting hot division issue in each circle. It fundamentally demonstrates the impact of transmitting data on AUV’s way of arranging. In every cycle, AUV must cross several key focuses to guarantee that the way can cover mission territory. The key focuses control the AUV’s way all in all. The game plan of key focuses has an imperative effect on system inclusion. The course of the AUV will be one-sided by the area subtleties of the GN’s from the past information accumulation arrangement that was recorded by the AUV. Then again, when there is totally nil information gathering amid the past accumulation cycles, first-jump nodules and key qualities that were at first set by the base station or the ground control is utilized to delineate the course of the AUV.
On dispatch HPs, sensor nodules manufacture an information dispatch course to AUV contingent upon the arrival of the Hello Packets and transcripts some upcoming-bounce nodules in a transmit table. At the point, while the sensor nodule gets an HP, it will ensure the data of HP and decide if the forwarding nodule ought to be included into transmit table that gives the transmit table that keeps up the data of the following jump. After the sensor nodule records the sending nodule, it progresses the HP. The sensor nodule invigorates its transmitting table and conveys the HP to its neighbors if the forwarding nodule can be recorded. The HP’s dispatch system will maintain until the restored Layer ID generates the edge n. something different, the sensor nodule basically incorporate the forwarding nodule into a Neighbor Nodule List lacking dispatch the HP.
A sensor nodule stores different next-jump nodules in transmit table. At the point when the recorded nodule is accessible, the sensor nodule, which isn’t the AUV’s main transmit or bounce-off, it juts sends its information throughput for the freshest updated upcoming-jump in the transmit table straightforwardly. Just the primary bounce nodules are required to send a DRP before the information is sent. The dispatch component may possibly initiate a decrease in the vitality utilization that stays away from the Demand/Feedback system. The configuration of Data Packets is basic. It comprises of totally five various data values for control aspects: Data Packet Signature, ID of the afterward-Hop, Origin Nodule ID, Packet Sequence No. and the Geo Co-ordinates, as appeared in Fig. 3. ID of the afterward-hop contains the next bounce’s physical co-ordinates.
Packet Esq-No is an interesting succession no. doled out by the origin nodule to the bundle. Alongside the Origin Nodule ID and Packet Sequence No. both values are utilized to separate parcels in recipient. The co-ordinates are the topography directions of the forwarding nodule. In the event that there is just a single passage in transmit table, the dispatch nodule sends information parcel to this recorded nodule legitimately. In the event that there are more than one passage in its transmit table and it’s anything but a GN, the dispatch nodule will pick next jump with the most up to date AUV Time Stamp. In the event that there is no section in its transmit table and this circumstance has to keep going for many information gathering cycles and has to spot a outlined neighbor and then send the information to it.
For providing the acoustic communication through the AUV, the channel attenuation has been maintained within the distance to identify the noises with different kind of regions and it is computed using Eq. (5)
The signal-to ratio with the distance and the frequency signal is computed in Eq. (6)
During the transmission, the data packet is received to the destination without error; the SNR has the threshold value for communication. The probability of bit error is computed using Eq. (7).
The probability of delivering the data packet within the distance is calculated in Eq. (8)
In the main information gathering cycle, GN is absent and the impact of the GN’s is not considered by the AUV. A component vector is setup by the AUV towards every first-jump nodules and of the following key point. In-case of different information gathering cycle, there are gatherings of those GN’s, the one’s whose topography data’s were recorded by AUV’s whilst the previous information gathering cycles were under process. AUV computes a loaded position for every gathering cycle of GNs, and revises past key focuses with a unit loaded focus. The No. is the neighbour’s amount of every GN and n-aggregate is the whole of No. is the aggregate sum of all the GNs. Also, subsequent to the irregular time, a unit vector is assigned by the AUV towards every first-jump nodule and the upcoming key points, and afterwards ascertains the push frontwards course pursue. The AUV also gathers information along another way which demonstrates the impact of GNs.

Performance evaluation
The performance analysis has been simulated using the MATLAB software. The high configuration system is used to implement the process with the proposed system has been constructed with the energy utilization system for communication and also the reception. The acoustic signals in the IoUTs have some restrictions like the restricted bandwidth and the high amount of energy consumption. The proposed method has been constructed to eliminate the limitations of the existing techniques. The performance metrics for proving the efficiency of the proposed technique are Average communication cost, Energy consumption, AUV travelled distance, number of cluster heads and End-to-end delay. Table 4 demonstrates the simulation parameters which are used to implement the proposed methodology for comparison.
The proposed Hybrid optimization routing management has been compared with the relevant works of LSHL (Han et al. 2014), DLCA (Tsai et al. 2017), and CMDG (Ghoreyshi et al. 2018). The LSHL algorithm is used to work with three sensor nodes such as surface buoys, anchor nodes, and ordinary nodes. The algorithm proposes a localization approach to identify the transmission process in unknown node and anchor node.The Euclidean distance is measured between the nodes and high concentration has been given on the unknown node to estimate the node-node delivery and the energy utilisation. The Diffusion Logarithm Correntropy algorithm (DLCA) is considered by assuming each node in the network. The algorithm works on with relatively error free network by taking the steeper steps in the non stationary environments using the AUV travelling distance. Cluster Based Mobile Data Gathering Scheme(CMDG) has been used to analyse the tradeoff between the data gathering using the latency and the energy saving. CMDG is one of the AUV transmission pattern to deal the underwater sensor. CMDG is compared with the proposed approach in terms to analyse the localization approach for the energy saving, Data gathering and the packet delivery ratio. The DLCA, LSHL and CMDG are compared for analysing the AUV travelling distance and the maximum energy utilisation in IoUT environment. Localization coverage is the ratio of the localizable ordinary nodes with the ordinary nodes. The error is obtained and measured with the proposed approach and with DLCA, LSHL and CMDG to analyse the estimated postion and average position. The algorithms are compared to identify the maximum energy consumed with the network using the localizable ordinary nodes. The Table 5 proposes the pros and cons of the proposed model with other models.
The performance metrics are used for implementing the proposed methodology is Average communication cost, AUV travelled distance, number of cluster heads, Average End-to-end delay and the Energy utilization. The Average communication cost for the node is computed from the forward packet reception and the backward packet reception and the average value is calculated from the total amount of communication cost in the network. The average communication cost is computed in Eq. (9).
Figure 3 demonstrates the node mobility effect for the performance of the localization. The proposed methodology formats the data packet corrections for identifying the locations and minimizes the average communication cost compared with the related techniques.
Figure 4 demonstrates the AUV travelled distance for gathering data in IoUTs. It is also suggested that the distance is increased whenever the total amount of nodes are in increased order. So, the proposed technique is coordinated well to the relevant techniques.
The cluster head can be covered within the communication range, whenever the total amount of nodes are increased, the cluster heads are also increased with respect to the AUV travelled distance so that the speed of transmission is guaranteed. The experimental result shows that the proposed technique has the increased amount of cluster heads compared with the relevant methods in Fig. 5.
The average end-to-end delay is directly related with the AUV travelled distance using the cluster heads for providing optimized routing in Internet of Underwater Things. The minimum amount of end-to-end delay has ensured that the optimized routing within the sensor nodes. The End-to-End delay has measured from the total amount of sensor nodes in the network that the difference between the arrival time for the data packets and the delivered packet time. The average value for each transmission is taken as the Average end-to-end delay. It is computed in Eq. (10).
Figure 6 illustrates that the proposed technique has the lowest end-to-end delay compared with the related techniques. The end-to-end delay calculation is very simple. The calculation is based on average delay time of packet created from sensor node to successful delivery of packets to sink. These packets were delivered with low end-to end delay. Because of AUV travel through shortest path with data collection from CHs, these data packets were held with shortest time also.
The Energy consumption is computed as the total amount of Energy consumed for every transmission as the amount of transmitted bits and the Energy consumed for every receiving data packets. The Energy consumption for the forwarding data packets in the network is computed using Eq. (11).
The forwarder nodes are capable of gathering information and transmitting it through the sink to be shared within the sensor nodes. The selection of nodes procedure is completed according to the residual energy of the sensor nodes. If the total amount of residual energy is minimum than the average energy and it is computed in Eq. (12)
Figure 7 demonstrates the energy utilized per node in every techniques. It is proved that the energy utilization of the proposed technique is measureably minimum that of communications is minimized with lower values. It is also noticed that the energy consumption is very less because of the cluster heads. The highest amount of clusters will minimize the distance within the sensors and cluster heads. Hence, the proposed method is saving the energy consumption.
Figure 8 demonstrates a comparison with the end-to-end delay of the proposed method and the related methods. The proposed technique has the minimum value than other techniques according to the smallest forwarding distance within the nodes in the complex conditions. The load balancing is another factor that other methods have highest amount of delay. Another reason is that the forwarding packets having the minimum hops and the complex channel conditions to increase the packet loss, hence the packets have to be retransmitted for more delay. So, the packets delivered into the sink with a minimum delay in the proposed technique maintain the communication impairments of the underwater channel. The end-to-end delay calculation is based on average delay time of packet created from sensor node to successful delivery of packets to sink. These packets were delivered with low end-to end delay. Because of AUV travel through shortest path with data collection from CHs, these data packets were held with shortest time also. In the hybrid optimization routing management, a vicinity of sensing element nodules cut the Demand/Feedback structure and uphold data directly, which may scale back consumption of energy of the network. Since the AUV has a fluctuating route and the GN’s allocation takes place in random manner, the energy utilization of the network may be equitable. This sequentially biases the forward route of the AUV. An increased performance result has been projected by the simulation outcomes for the delay and energy utilization.
Conclusion
In this paper, the hybrid optimization routing management for Internet of Underwater Things is proposed and successfully implemented. The energy consumption is the basic parameter for this proposed technique. The efficient routing has been established using the autonomous underwater vehicles through the connectivity of the sensor nodes to the devices with the Internet. The cluster head is elected for provided the efficient routing. The proposed technique has been implemented with 2 phases of AUV-Assisted Network Transmit Devising and Transmit Assisted Route Devising. The Gateway Nodules are utilized to gather the information related to the autonomous underwater vehicles. AUV timestamp has the ability to transmit the information by the sensor nodule using the centroid point and the transmission range. The limitations and the challenges of the proposed technique are the longest multipath delay, complex environment, lowest bandwidth; sever noise, and the restricted battery life of the underwater sensor nodes. The acoustic waves restrict the frequency range while performing the underwater transmission with the temperature in the water. The simulation results proved that the proposed technique has the improved performance. The limitations and the challenges of the proposed technique are the longest multipath delay, complex environment, lowest bandwidth, sever noise, and the restricted battery life of the underwater sensor nodes. The acoustic waves restricts the frequency range while performing the underwater transmission with the temperature in the water. Increasing the lifespan of the network and handling new spots, sector drawbacks is set to be the strategy in the future.
References
Akkaya K, Newell A (2009) Self-deployment of sensors for maximized coverage in underwater acoustic sensor networks”, Computer Communications, Volume 32, Issues 7–10, 28, Pages 1233–1244
Akyildiz F, Pompili D, Melodia T (2005) Underwater acoustic sensor networks: research challenges. Ad Hoc Net 3(3):257–279
Ali T (2014) Low tang Jung, rahima Faye, “end-to-end delay and energy efficient transmit protocol for underwater wireless sensor networks”, in. Wireless Pers Commun 79:339–361
Alsalih W, Hassanein H and Akl S (2008) "delay constrained placement of mobile data collectors in underwater acoustic sensor networks," 2008 33rd IEEE Conference on Local Computer Networks (LCN), Montreal, Que, 2008, pp. 91–97, doi: https://doi.org/10.1109/LCN.2008.4664156
Al-Salti F, Alzeidi N, Day K, Touzene A (2019) An efficient and reliable grid-based routing protocol for UWSNs by exploiting minimum hop count. Computer Networks 16224:–106869
Annamalai S, Udendhran R, Vimal S (2019) Cloud-Based Predictive Maintenance and Machine Monitoring for Intelligent Manufacturing for Automobile Industry. Novel Practices and Trends in Grid and Cloud Computing:74–81. https://doi.org/10.4018/978-1-5225-9023-1.ch006
Ayaz M, Baig I, Abdullah A, Faye I (2011) A survey on routing techniques in underwater wireless sensor networks. J Netw Comput Appl 34(6):1908–1927
Ayaz M, Abdullah A, Faye I, Batira Y (2012) An efficient dynamic addressing based transmit protocol for underwater wireless sensor networks. Comput Commun 35(4):475–486
Ayyanar A, Maruthavanan A, Harold Robinson Y, Golden Julie E, Kumar R, Son LH (2019), “Design a prototype for automated patient diagnosis in wireless sensor networks”, Medical & Biological Engineering & Computing
Bhattacharjya K, Alam S, De D (2019) CUWSN: energy efficient routing protocol selection for cluster based underwater wireless sensor network. Microsyst Technol. https://doi.org/10.1007/s00542-019-04583-0
Cai S, Gao Z, Yang D, Zhao J, Zhao Y (2013a) IPool-ADELIN: an extended ADELIN based on IPool node for reliable transport of underwater acoustic sensor networks. Ad Hoc Netw 11(4):1435–1442
Cai S, Gao Z, Yang DS, Yao N (2013b) A network coding based protocol for reliable data transfer in underwater acoustic sensor. Ad Hoc Netw 11(5):1603–1609
Carlson EA, Beaujean P and An E (2007) “An Improved Location-Aware Transmit Protocol for Mobile Underwater Acoustic Networks”.OCEANS
Chen Y-S, Lin Y-W (2013) Mobicast transmit protocol for underwater sensor networks. IEEE Sensors J 13(2):737–749
Chen, K. Jamieson, H. Balakrishnan, and R. Morris (2001) Span: an energy efficient coordination algorithm for topology maintenance in ad hoc wireless networks. In Proceedings of the ACM International Conference on Mobile Computing and Networking, Rome, Italy
Chen B, Hickey PC, and Pompili D (2010) “Trajectory-aware Communication Solution for Underwater Gliders using WHOI Micro-Modems”. IEEE Secon 2010
Chen YK, Ji F, Guan Q, Wang Y (2018) Adaptive RTO for handshaking-based MAC protocols in underwater acoustic networks. Future Generation Computer Systems 86:1185–1192
Chengzhi Q, Gai W, Zhong M, Zhang J (2020) A novel reinforcement learning based grey wolf optimizer algorithm for unmanned aerial vehicles (UAVs) path planning. Applied Soft Computing 89:106099
Dey N, Hassanien AE, Bhatt C, Ashour A, Satapathy SC (eds) (2018) Internet of things and big data analytics toward next-generation intelligence. Springer, Berlin, pp 3–549
Dey N, Mahalle PN, Shafi PM, Kimabahune VV, Hassanien AE (eds) (2020) Internet of things. A Roadmap Ahead. Springer International Publishing, Smart Computing and Technology, pp 3–403
Feng P, Qin D, Ji P, Zhao M, Guo R, Berhane TM (2019) Improved energy-balanced algorithm for underwater wireless sensor network based on depth threshold and energy level partition. J Wireless Com Network 2019:228. https://doi.org/10.1186/s13638-019-1533-y
Ghoreyshi SM, Shahrabi A, and Boutaleb T (2018) on “A Cluster-Based Mobile Data-Gathering Scheme for Underwater Sensor Networks”, International symposium on networks, Computers and Communications (ISNCC), IEEE
Goyal N, Dave M, Verma AK (2019) Protocol stack of underwater wireless sensor network: classical approaches and new trends. Wireless Pers Commun 104:995–1022. https://doi.org/10.1007/s11277-018-6064-z
Goyal N, Dave M, Verma AK (2020) SAPDA: secure authentication with protected data aggregation scheme for improving QoS in scalable and survivable UWSNs. Wireless Pers Commun 113:1–15. https://doi.org/10.1007/s11277-020-07175-8
Guo Y, Han Q, Kang X (2019) Underwater sensor networks localization based on mobility-constrained beacon. Wirel Netw 26:2585–2594. https://doi.org/10.1007/s11276-019-02023-5
G. Han, A. Qian, C. Zhang, Y. Wang, and J. J. P. C. Rodrigues (2014) “Localization algorithms in large-scale underwater acoustic sensor networks: a quantitative comparison,” International Journal of Distributed Sensor Networks, vol. 2014, Article ID 379382, pp. 1–11
Harold Robinson Y & Golden Julie E (2019) SMR: A Synchronized Multipath Rebroadcasting Mechanism for Improving the Quality of Conversational Video Service, vol. 104, no. 3, pp. 1149–1173, Wireless personal communications, Springer
Harold Robinson Y, Balaji S & Golden Julie E (2019a) PSOBLAP: Particle Swarm Optimization-Based Bandwidth and Link Availability Prediction Algorithm for Multipath Routing in Mobile Ad Hoc Networks, vol. 106, no. 4, pp. 2261–2289, Wireless personal communications, Springer
Harold Robinson Y, Balaji S & Golden Julie E (2019b) Design of a Buffer Enabled Ad hoc On-demand Multipath Distance Vector Routing Protocol for Improving Throughput in Mobile Ad hoc Networks, vol. 106, no. 4, pp. 2053-2078, wireless personal communications, Springer
Harold Robinson Y, Santhana Krishnan R, Golden Julie E, Kumar R, Son LH, Thong PH (2019c) Neighbor Knowledge-based Rebroadcast Algorithm for minimizing the Routing overhead in Mobile Ad-hoc Networks, Ad Hoc Networks, Elsevier
Harold Robinson Y, Golden Julie E, Kumar R & Son LH (2019d) Probability-based cluster head selection and fuzzy multipath routing for prolonging lifetime of wireless sensor networks, pp. 1-15, peer-to-peer networking and applications, Springer, DOI https://doi.org/10.1007/s12083-019-00758-8
Harold Robinson Y, Golden Julie E, Saravanan K, Kumar R, Son LH (2019e), “DRP: dynamic routing protocol in wireless sensor networks”, Wireless Personal Communications
Hirai S, Tanigawa Y and Tode H (2012) “Integration Method between Localization and Transmit in Underwater Sensor Networks”, Computational Science and Engineering (CSE).IEEE 15th International Conference on, page 689–693. IEEE Computer Society
Huang Y, Zhou S, Shi Z, and Lai L (2014) “Experimental study of secret key generation in underwater acoustic channels,” in Proc. of the Asilomar Conference on Signals, Systems and Computers
Ibrahim S, Cui JH, Ammar R (2008) Efficient surface gateway deployment for underwater sensor networks Proceedings of the 13th IEEE Symposium on Computers and Communications (ISCC '08)July 2008117711822-s2.0–55849151358 10.1109/ISCC.2008.4625609
Jain G, Yadav G, Prakash D, Shukla A, Tiwari R (2019) MVO-based path planning scheme with coordination of UAVs in 3-D environment. Journal of Computational Science 37:101016
Jiang J, Han G, Guo H, Shu L, Joel J, Rodrigues PC (2016) Geographic multipath routing based on geospatial division in duty-cycled underwater wireless sensor networks, Journal of Network and Computer Applications, vol. 59, pp. 4–13
Kredo II KB and Mohapatra P (2007) “A hybrid medium access control protocol for underwater wireless networks,” Proc. ACM Int’l. Wksp. Underwater Net., Montreal, Canada
Kumar S, Kumar-Solanki V, Choudhary SK, Selamat A, Gonzalez-Crespo R (2020) Comparative study on ant Colony optimization (ACO) and K-means clustering approaches for jobs scheduling and energy optimization model in internet of things (IoT). International Journal of Interactive Multimedia and Artificial Intelligence 6(1):107–116. https://doi.org/10.9781/ijimai.2020.01.003
Lee JW, Cho HS (2014) Cascading multi-hop reservation and transmission in underwater acoustic sensor networks. Sensors 14(10):18390–18409. https://doi.org/10.3390/s141018390
Li S, Wenyu Q, Liu C, Qiu T, Zhao Z (2019) Survey on high reliability wireless communication for underwater sensor networks. Journal of Network and Computer Applications 148:102446
Liu X, He D, Ding H (2019) Throughput maximization for UAV-enabled full-duplex relay system in 5G communications. Physical Communication 32:104–111
Luo J, Han Y (2019) A node depth adjustment method with computation-efficiency based on performance bound for range-only target tracking in UWSNs. Signal Processing 158:79–90
Luo J, Han Y, He X (2019) Optimal bit allocation for maneuvering target tracking in UWSNs with additive and multiplicative noise. Signal Processing 164:125–135
Mainwaring A, Polastre J, Szewczyk R, and Culler D (2002) Wireless sensor networks for habitat monitoring. In Proceedings of the ACM Workshop on Sensor Networks and Applications, Atlanta, Georgia, USA
Nazrul Alam SM, Haas ZJ. (2006) Coverage and connectivity in three-dimensional networksProceedings of the 12th Annual International Conference on Mobile Computing and Networking (MOBICOM '06)September 20063463572-s2.0–33751061514
Núñez-Valdez E, Solanki VK, Balakrishna S, Thirumaran M (2020) Incremental hierarchical clustering driven automatic annotations for unifying IoT streaming data. International Journal Of Interactive Multimedia And Artificial Intelligence 6(2):56–70. https://doi.org/10.9781/ijimai.2020.03.001
Pasupathi S, Vimal S, Harold-Robinson Y, Khari M, Verdú E, Crespo RG (2020) Energy efficiency maximization algorithm for underwater Mobile sensor networks. Earth Sci Inform. https://doi.org/10.1007/s12145-020-00478-1
Patil K, Jafri M, Fiems D, Marin A (2019) Stochastic modelling of depth based routing in underwater sensor networks, Ad Hoc Networks, vol. 89, pp. 132–141
Paul A, Rho S (2016) Probabilistic model for M2M in IoT networking and communication. Telecommun Syst 62(1):59–66
Anand Paul, Awais Ahmad, M. Mazhar Rathore, and S. Rho (2015) "Power Aware Mobility Management of M2M for IoT Communications," Mobile Information Systems, Article ID 521093, pp. 1–14
Pavitra ARR, Janani ESV (2019) Overlay networking to ensure seamless communication in underwater wireless sensor networks. Comput Commun 147:122–126
Hameed Pinjari, Anand Paul, Won-Hwa Hong, HyunCheol Seo, and S. Rho (2018) "Fog Computing Based IoT for Health Monitoring System," Mobile Networks and Applications ,Volume 2018, Article ID 1386470, pp 1–7
Pompili D, Melodia T, and Akyildiz IF (2006) “Routing Algorithms for Delay-Insensitive and Delay-Sensitive Applications in Underwater Sensor Networks,” Proc. ACM MobiCom, Los Angeles, CA
Pompili D, Melodia T, Akyildiz IF (2009) Three-dimensional and two-dimensional deployment analysis for underwater acoustic sensor networks. Ad Hoc Networks 7(4):778–790
Qiu T, Zhao Z, Zhang T, Chen C, Chen CLP (2020) Underwater internet of things in Smart Ocean: system architecture and open issues. in IEEE Transactions on Industrial Informatics 16(7):4297–4307. https://doi.org/10.1109/TII.2019.2946618
Rani S, Ahmed SH, Malhotra J, Talwar R (2017) Energy efficient chain based routing protocol for underwater wireless sensor networks. Journal of Network and Computer Applications 92:42–50
Rho S (2015) "An IoT Patent Trend Analysis for Technological Convergence on Hyper Connected Society," Journal of Korea Institute of Information and Communication Engineering, Vol. 19, No. 11
Rosalie M, Danoy G, Chaumette S, Bouvry P (2018) Chaos-enhanced mobility models for multilevel swarms of UAVs. Swarm and Evolutionary Computation 41:36–48
Roy A, Sarma N (2018) Effects of various factors on performance of MAC protocols for underwater wireless sensor networks. Materials Today: Proceedings 5(1):2263–2274
Ruoyu S, Venkatesan R, Li C (2013) “A new nodule coordination schemefor data gathering in underwater acoustic sensor networks using autonomous underwater vehicle”. Wireless Communications and Networking Conference (WCNC), 2013 IEEE
Salva-Garau F and Stojanovic M (2003) Multi-cluster protocol for ad hoc mobile underwater acoustic networks. In Proceedings of the IEEE OCEANS’03 Conference, San Diego, CA
Schaller A, Mueller K (2009) Motorola's experiences in designing the internet of things. International Journal of Ambient Computing and Intelligence 1(1):75–85
Shen W, Zhang C, Shi J (2019) Weak k-Barrier Coverage Problem in Underwater Wireless Sensor Networks. Mobile Netw Appl 24:1526–1541. https://doi.org/10.1007/s11036-019-01273-z
Shinde GR, Olesen H (2018) Beacon-based cluster framework for internet of people, things, and services (IoPTS). International Journal of Ambient Computing and Intelligence 9(4):15–33
Teixeira PV, Dimarogonas DV, Johansson KH and Sousa J (2010) "event-based motion coordination of multiple underwater vehicles under disturbances," OCEANS'10 IEEE SYDNEY, Sydney, NSW, 2010, pp. 1–6, doi: https://doi.org/10.1109/OCEANSSYD.2010.5603980
Tomasi B, Casari P, Badia L, Zorzi M (2015) Cross-layer analysis via Markov models of incremental redundancy hybrid ARQ over underwater acoustic channels, Ad Hoc Networks, vol. 34, 2015, pp. 62–74
Tsai P, Tsai R, Wang S (2017) Hybrid Localization Approach for Underwater Sensor Networks, Journal of Sensors, Article ID 5768651, pp. 1–13, https://doi.org/10.1155/2017/5768651
Vedachalam N, Ramesh R, Jyothi VBN, Prakash VD, Ramadass GA (2019) Autonomous underwater vehicles - challenging developments and technological maturity towards strategic swarm robotics systems. Marine Georesources & Geotechnology 37(5):525–538. https://doi.org/10.1080/1064119X.2018.1453567
Vimal S, et al (2016) “Secure data packet transmission in MANET using enhanced identity-based cryptography”. International Journal of New Technologies in Science and Engineering Vol. 3, No.12, pp.35–42
Vimal S, Kalaivani L, Kaliappan (2017) Collaborative approach on mitigating spectrum sensing data hijack attack and dynamic spectrum allocation based on CASG modeling in wireless cognitive radio networks. M. Cluster Computing. https://doi.org/10.1007/s10586-017-1092-0
Vimal S, Kalaivani L, Kaliappan M, Suresh A, Gao X-Z, Varatharajan R (2018) Development of secured data transmission using machine learning based discrete time partial observed markov model and energy optimization in Cognitive radio networks. Neural Comput & Applic. https://doi.org/10.1007/s00521-018-3788-3
Vimal S, Khari M, Crespo RG, Kalaivani L, Dey N, Kaliappan M (2020a) Energy enhancement using Multiobjective Ant colony optimization with Double Q learning algorithm for IoT based cognitive radio networks. Computer Communications 154:481–490
Vimal S, Khari M, Dey N, Crespo RG, Robinson YH (2020b) Enhanced resource allocation in mobile edge computing using reinforcement learning based MOACO algorithm for IIOT. Computer Communications, Volume 151(1):355–364
Wang Z, Guo H, Longjie J, Xiaoning F (2016) on “AUV-Aided Communication Method for Underwater Mobile Sensor Network” - 16 - 2016 IEEE
Xia N et al (2014) Rigidity driven underwater sensor self-organized deployment: rigidity driven underwater sensor self-organized deployment. Chinese Journal of Computers 36:494–505
Xie P, Cui J (2007) An FEC-based Reliable Data Transport Protocol for Underwater Sensor Networks, Proceedings of 16th International Conference on Computer Communications and Networks, 2007, IEEE Xplore, DOI: https://doi.org/10.1109/ICCCN.2007.4317907
Xie P, Zhou Z, Zheng P, Cui J-H, Shi Z (2010) SDRT: a reliable data transport protocol for underwater sensor networks. Ad Hoc Netw 8(7):708–722
Xu J, Bi P, Du X, Li J (2019) Robust PCANet on target recognition via the UUV optical vision system. Optik 181:588–597
Yoon S, Azad AK, Hoon O, Kim S (2012) AURP: an AUV-aided underwater transmit protocol for underwater acoustic sensor networks. Sensors 12:1827–1845
Yu H, Fei Y (2016) DAP-MAC: a delay-aware probability-based MAC protocol for underwater acoustic sensor networks. Ad Hoc Netw 48:80–92
Zenia NZ, Aseeri M, Ahmed MR, Chowdhury ZI, Kaiser MS (2016) Energy-efficiency and reliability in MAC and routing protocols for underwater wireless sensor network: A survey. Journal of Network and Computer Applications 71:72–85
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Robinson, Y.H., Vimal, S., Julie, E.G. et al. Hybrid optimization routing management for autonomous underwater vehicle in the internet of underwater things. Earth Sci Inform 14, 441–456 (2021). https://doi.org/10.1007/s12145-020-00538-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12145-020-00538-6