Abstract
Modern Underwater Wireless Sensor Networks (UWSN) would provide big administrations with numerous underwater surveying and technical applications, working in the unstable submerged deep-water conditions. A huge obstacle in these networks is the lifetime limit. The submerged correspondence frameworks mostly employ acoustic communication today. Acoustic interchange communication offers longer ranges that are yet limited by three variables: restricted and subordinate data transmission, time-differing multi-way engendering and low speed of sound. In this paper, an AUV (Autonomous Underwater Vehicle)-assisted acoustic correspondence convention, specifically Energy Efficiency Maximization Algorithm (EEMA) has been proposed to minimize the energy consumption. Underwater sensor networks depend on the hub ceaseless operation, the restricted correspondence transmission capacity and the hub lifetime, which entails difficulties in the operation of USWN. The proposed system will enhance the lifetime by lessening the number of bounces amid sensor transmissions, which fundamentally lessens time utilization and lifetime. Dynamic AUV ways and dynamic gateway assignments will enhance lifetime – proficiency balance proportion in the submerged system. To decrease the system energy utilization with an acceptable conveyance proportion is recommended. The Experimental results show that the proposed methodology has improved the level of energy compared with related techniques.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Underwater Submerged remote detecting frameworks are pictured for complete application supported by autonomous underwater vehicles (AUVs) (Dai et al. 2020), as an expansion to cabled frameworks. For instance, cabled sea observatories are being planned on underwater links to convey a solid fibre-optic system of sensors (Lin et al. 2020). These links will bolster correspondence passages plentifully, as cell base stations are associated with the phone, permitting clients to convey from spots wherever links cannot reach (Li et al. 2020). Another model is based on cabled submersibles, named as remotely worked vehicles (ROVs) (Eidsvik and Schjolberg 2018). These are associated with the mother dispatch by a link that may allow fast transmissions over some miles of distance, with high capacity to complete remote communication (Teague et al. 2018).
Presently, vehicle innovation and detecting component innovation allow to energize submerged detecting component systems (Zapadka et al. 2020) (Yoon et al. 2012). Submerged correspondence frameworks nowadays broadly utilize acoustic innovation (Ruoyu et al. 2013). Correspondence methods, as optical and radio-recurrence, are ready for short-run joins (commonly 2–15 m), wherever a steep data frequency (MHz) will undergo misuse (Ali and Jung 2014). All the signals lessen in all respects rapidly, inside certain meters (radio) or several meters (optical), requiring either high-voltage or enormous reception apparatuses (Yu et al. 2020). Acoustic correspondences give longer ranges, anyway square measure is influenced by 3 factors: confined and removed subordinate data measure, time-differing multi-way spread and low speed of sound (Peng and Kong 2020). Together, these elements lead to a station of low quality and high inertness, so it makes correspondence of earthbound portable and satellite radio stations much difficult (Yadav and Kumar 2019).
Among the essential Underwater Acoustic Frameworks was the submarine correspondence framework created inside the USA amid the end of the Second World War. It utilized simple balance inside the 8–11 rate groups. Since then, investigation has pushed advanced modulation– discovery procedures into the bleeding edge of ongoing acoustic interchanges (Luo and Han 2019). At present, numerous styles are represented for acoustic modem square measure, presenting capable of operating with certain kilobits every second (kbps) over separations up to certain kilometres. In spite of these advanced outcomes, square measure is still inside the space of test investigation (Luo et al. 2019).
In addition, acoustic modems square measure commonly confines to half-duplex task. These limitations infer that acoustic-cognizant convention styles will offer higher efficiencies than direct use of conventions produced for earthly systems (Al-Salti et al. 2019). Furthermore, for secured detecting component systems, vitality power is as fundamental as in earthbound systems, because battery re-charging underneath the sea surface is troublesome and expensive (Ahmed et al. 2017). This is one of the most significant features that distinguish underwater sensing element networks from their global complement, and basically changes several network style paradigms that square measure or else engaged as right (Wang et al. 2016). Whereas these days there are not habitually operational underwater sensing element networks, their development is close. The basic frameworks typify armadas of collaborating self-sufficient vehicles and long-run deployable base ascended detecting component systems (Abbas et al. 2015). Dynamic investigation that powers this improvement is the primary subject of our paper.
The main objectives of the presented work are:
-
i.
Underwater Remotely Operated vehicle is used to remain stationary at the natural disasters for data collecting functionality.
-
ii.
The routing path has been successfully constructed using the sink node and the energy utilization from the cluster head is forwarded through the cluster members.
-
iii.
The objective function is used to reduce the entire data collection cost in every round for maintaining the routing path in Underwater surroundings.
-
iv.
The performance of the proposed method is analyzed for effective routing in underwater mobile sensor networks in terms of throughput, delay, delivery ratio and the network lifetime.
Related works
In this part, we confer the feasibleness of our hypothesis by observing varied recent research in Underwater Wireless Sensor Networks (UWSNs) (Pavitra and Janani 2019). The submerged remote interchanges will cause changes in a few logical, natural, business, security, and military applications. Remote flag transmission is furthermore significant to oversee instruments in sea and to change the harmonization of swarms of self-ruling submerged robots, assuming the job of portable nodules in future sea perception arranges through their adaptability and re-configurability (Goyal et al. 2017). To make submerged developments practical, correspondence conventions among submerged gadgets, supported by acoustic remote innovations allowing region unit separations of more than 100 m, ought to be empowered with the high lessening and dispersing that influence radio and optical waves, severally (Ali et al. 2012). The attributes of submerged acoustic channels like confined and separate ward data measure, high proliferation postponements, and time shifted multipath, make necessary new, conservative and dependable correspondence conventions to organize various gadgets, either static or portable, most likely over numerous jumps (1’Goyal et al. 2020).
In the modern days, the demand for the discrimination of underwater components in the underwater medium is slightly higher (Feng et al. 2019). Moreover, the propensity to prohibit terrestrial network protocols has attenuated and inclusion of water is the biggest challenge for producing the result with the usage of optical waves and radio waves (Bhattacharjya et al. 2019). The formation of underwater networks has the most of redundant messages; therefore we need to minimize these redundant messages. The tendency has been to propose integration techniques between localization and transmission that were mentioned one by one thus far, by merely enlarging management packets changed for localization (Khan and Dwivedi 2018). The output is to economically setup the network. At last, we have a tendency to show the effectiveness of the projected techniques by theoretical account (Goyal et al. 2019).
Expanding the correspondence execution in an Underwater Wireless detecting component Network is troublesome due to the unpredictable attributes of the submerged setting (Hirai et al. 2012). Radio signs cannot appropriately spread submerged, subsequently there is a need for acoustic innovation which will bolster higher learning rates and dependable submerged remote interchanges (Ghoreyshi et al. 2018). Nodule quality, 3-D territories and level correspondence joins region unit imply some imperative difficulties to the examination specialist in arranging new transmit conventions for UWSNs (Shen et al. 2019). In this paper, we have anticipated a one of a kind transmit convention known as Layer to layer Angle-Based Flooding (L2-ABF) (Goyal et al. 2016) to manage the problems of nonstop nodule developments, start to finish postponements and vitality utilization. In L2-ABF, every nodule will ascertain its flooding edge to advance information bundles toward the sinks while not exploiting any express design or area data. The generated results demonstrate that L2-ABF has a few advantages regarding current flooding related procedures and may likewise essentially oversee quickly transmit changes wherever nodule development’s region unit visit (Ali et al. 2014).
Pre-established secret keys in the area unit are typically used to code and decode information in communication systems, as well as underwater acoustic (UWA) systems (Kalkan and Levi 2014). Additionally, once the elevated area unit is compromised, the transmission is not protected. Therefore, it is important to propose models of distributed secret keys within the field (Guo et al. 2019). The methodology is to get secret keys dynamically according to the related channel capacity that depends on the unpredictability within the atmosphere and does not need the confidentiality of data changed throughout the method. However, the generated key is compromised with the channel frequency responses (Fu et al. 2017).
The energy efficient grid related geographical routing protocol for UWSN (Salti et al. 2017) is implemented for increasing the residual energy. The dynamic layered dual based cluster heads are used for an efficient routing methodology (Jiang et al. 2016). The energy level is increased with cubical related path planning called EECPPA (Aslam et al. 2017). E-CARP has been implemented for data transmission in internet of underwater things (Zhou et al. 2016).
The disadvantages of the related methods are: slow knowledge gathering at the sink and low efficiency in forwarding the data packets. Besides, while transmitting the data packets, the collisions can occur so that the Energy is wasted. The network congestion is maximized while transmitting the data packets through the sink node that cannot find the amendment within the topology; also the energy consumption is not managed. The network life is weak with unpredictable topology and the bandwidth is limited (Nighot et al. 2018); it will cause the loss of information and with limited security. The nodule quality of the network can entail frequent link breakages, which could cause frequent path failures and route discoveries. The failure of data packet transmission will increase the energy consumption in nodules. The fact that the residual energy is minimum means that it has no awareness regarding energy levels of nodules. The chance for partial and total scarcity in energy increases the possibility that the nodule failure occurs. The response time should be as low as possible for better network performance (Kumar et al. 2020).
The limitations of the related methods are the challenges behind the energy and the quality based data transmission in UWSNs. Most of the methods have been constructed using the shortest path based on data transmission; it is useful in simple underwater environments for efficient data transmission. The common issues in UWSNs are the latency and high amount of redundancy (Vimal et al. 2020a).
Proposed method
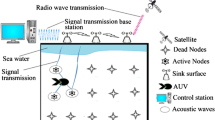
Ocean Ground detecting component nodules territory units are considered to modify applications for oceanographic data variety, contamination perception, seaward investigation, fiasco obstacle, route guiding, and planning of police examination. Various remote-controlled outfitted with inundated sensors, additionally will acknowledge the common underneath sea assets of logical data in agreeable perception missions. To construct these applications appropriately, it is required to modify inundated correspondences within inundated components. Submerged detecting component nodules and vehicles ought to get self-setup capabilities, i.e., they should probably arrange their task by trading plan, area and development information, and to transmit checked data inland station. Figure 1 demonstrates the wireless Underwater mobile sensor network with detailed construction.
Below, a recognizable proof of remote-controlled Underwater Remotely Operated Vehicle (ROV) is presented. The proof is devised once investigation is done on numerous writing surveys and pondered cases. In this paper, the disadvantages found are targeted in subtleties like framework, underneath roused condition, cause recuperation or station continuing, coupling issues and correspondence procedure. ROV is one among the remote-controlled Underwater Vehicle (UWV) bound with point link and remotely worked by a vehicle operator. Arrangement of ROV might be somewhat complicated to infer from the obscure non-direct hydrokinetics impacts, parameters vulnerabilities and, in this manner, there is an absence of an express model of the ROV elements and parameters. Run of the mill controller cannot progressively get up to speed with un-demonstrated vehicle liquid mechanics powers or obscure aggravations. The propelled condition is plot all in all having less administration contributions than level of opportunity, in this manner anyway the ROV needs to keep up a definite reason or profundity following mission once one or a great deal of thrusters breakdown conjointly a trouble to be featured. Cause recuperation is one among the biggest issues in the ROV system (Vimal et al. 2020d). This approach is utilized to keep up an edge in regard to another moving ROV in light of the fact that the ROV attempts to remain stationary at the required profundity with blessing the natural unsettling influences like breeze, waves, current and astounding ecological aggravations. Coupling issue between the tie and link with ROV body are one disadvantage in accommodating the ROV itself since it pairs the vehicle load (Vimal et al. 2020b).
The data collecting route is fluctuating in every round of the data collection series. This is required to enable the AUV to commission different nodules as GN in the existing sectors. This can greatly improve Hot-Spot and Sector complexities. AUV gathers data re-tracing the route under active run by the GN’s of the previous series, in order to gain potentially more likelihood to retract the energy of the GN’s.
The sensor nodes deliver a connection request to the base station through the cluster head, and then the head generates a route path to the sink node. The cluster head discovers the shortest way with reduced amount of hop count. The cluster members can hold the details of the routing path and these details are gathered by the cluster head simultaneously. Hence the energy utilization from the cluster head will differ to the cluster members. The energy utilization for the cluster head is computed using Eq. (1).
Where d is the data gathering level, n is the received amount of data and μa is the aggregation function. The data gathering may be different according to the position of the sensor nodes in the network. The adjacent nodes are used to measure the distance within the sensor nodes. The required energy for the cluster head is comparatively very high to the cluster members. Whenever the aggregation level gets increased, the energy utilization will also increase. The main characteristics of the Objective function (δobj) is to minimize the whole data collection cost in every round i for maintaining events in the underwater surroundings. The objective function is computed using Eq. (2)
Where Pkdr denotes the packet delivery ratio, Trp is the throughput, Rtm is the Retransmission, Dey demonstrates the delay, Con is the congestion and Pker denotes the packet error rate.
The proposed methodology is constructed to get the solution for the routing problem in Underwater Mobile sensor networks according to the monitoring system, a numerical optimization methodology has been utilized to perform the Gaussian mutation operations. The dead sensor node has zero residual energy Ey0. The fitness value is computed for every sensor node in Underwater Mobile sensor networks. The top most fitness sensor nodes are organized to form the mating poll using a ranking system. The vector format for computing the fitness value within the deterministic time interval \( \left({\delta}_t^i\right) \) for the active round ri is demonstrated using Eq. (3).
The discovery of binary tournament for every node is demonstrated using the fitness value. The best individual value is selected to produce the pool from randomly selected individual nodes. The binary tournament is computed using Eq. (4)
Where BTy is the binary tournament for parameter y. ρw∈[0,1] is the random weight value for every parameter y in every stage i. The crossover probability (Probco) is computed using Eq. (5)
Where α is the normal distribution for Gaussian function that ∈[0,1], ρmin is the lower bound and ρmax is the upper bound. The new fitness function is computed in Eq. (6)
The whole optimization demonstrates the predefined condition is satisfied discovering the suitable clusters based on active routing to provide the solution according to the current situation. The network initialization procedure achieves accurate discovery of neighbours in unusual underwater surroundings. This kind of procedure produces a group of messages like initialization, discovery of neighbours, acknowledgement and replay in underwater mobile sensor networks. The base station forwards the initialization message to the sink node to process the network initialization procedure. After the received message, the sink node regulates the communication and transmits the frequent messages within the particular area in the network (Vimal et al. 2020c).
The message contains the packet communication time, the data about the current location and the sink identification. After successfully transmitted the message, the sink node checks the surface information and neighbouring data table is formulated to every node in the network. Whenever the sink node receives the messages about the sea surface, the neighbouring node discovery message is communicated to the nodes in the underwater mobile sensor networks (Annamalai et al. 2019a).
The energy consuming model is constructed after monitoring the characteristics of underwater sensor network formation, the energy efficiency model of this underwater mobile sensor networks is entirely different from the energy model of Wireless sensor networks. The energy computation is performed using Eq. (7)
Where δ0 is the threshold value for power constraint, dis is the communication distance, co be the energy efficient coefficient, Energy(dis,co) is the computation of energy utilization to forward the data to the destination, the value of a is computed using Eq. (8)
The frequency is the main parameter to construct the value of a and it is demonstrated in Eq. (9)
Where f is the signal frequency in Hz and a(f) is the received frequency in dBm. The Expected energy (Energyex) for consumption is computed using Energy consumed (Energycon) in Eq. (10)
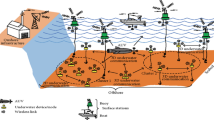
The proposed methodology in underwater mobile sensor network is deployed in a communication range. The distance within the nodes is computed in every specified time period (Annamalai et al. 2019a). The multi-hop communication produces the unbalanced energy utilization. The cluster heads which are nearer to the sink nodes forward the communication within the other cluster heads. The sensor nodes forward the data to the sink nodes without using any other nodes. The architecture is demonstrated in Fig. 2 to maintain the balance of energy utilization within the sensor nodes in every cluster, the cluster head is selected using the residual energy of the sensor nodes (Annamalai et al. 2019b).
Whenever the sensor node receives the communication message from the adjacent nodes, Communication cost (Commcost) for every node is computed using Eq. (11).
Where Energyres is the residual energy, Energyinit is the initial energy, t is the time duration for communication and τ is the constant value. The energy balance of the entire network is computed using the forwarding behaviour of the sensor node. The competition radius Radiuscom is computed using the weighted value (wt) and radius in Eq. (12).
The optimization for the multi-objective methodology is used to compute the cost value for every sensor node, which is computed with the degree value of the particular node using Eq. (13)
Algorithm – Energy Efficient Maximization Algorithm (EEMA).
The underwater mobile sensor network is dynamically structured and the nodes are moving randomly according to the water component. Hence, the structure of cluster can be changed at any cost of time period. The recovery technique is used whenever the node failed to delivered the data to this cluster head (Borhani 2020). For this issue, the sensor node inspects the packets and cluster heads. Every cluster head computes the average energy level of the cluster, if the computed energy is minimum than the actual energy then the data about the routing is modified. For the entire network, at every round of data communication, the sink nodes produce the good delivery ratio (Vimal.s, et al. 2016). Whenever the delivery ratio is minimum, the sink nodes can transmit the restructure details to the senor nodes and the underwater sensor nodes will be responsible for building the new clusters. This process is illustrated in Fig. 3.
Table 1 contains the abbreviations and symbols used in the proposed methodology.
Performance evaluation
The Performance Evaluation for the proposed methodology (EEMA) is evaluated and the results are compared with the related methods of EECPPA (Aslam et al. 2017), EMGGR (Salti et al. 2017). The simulations are successfully implemented in MATLAB, the amount of sensor nodes are maintained in the entire simulation process. Table 2 shows the simulation parameters used in this paper.
In this proposed methodology, the methods are evaluated according to network lifetime, energy utilization, delay, delivery ratio, and stability. The stability period refers to the time period until a first node dies in the entire network. To evaluate the stability performance, the method is compared with related techniques. The related methods are performed using a huge amount of repeated data packets, which are normally generated. The minimized network lifetime for the initial node is the drawback for the relevant methods compared to the proposed methodology. Data forwarding fully depends on the source node for implementing the clustering technique to minimize the amount of data forwarding. Figure 4 demonstrates the number of dead nodes with time in seconds.
The network lifetime is estimated as the time taken until all nodes die in the entire network. Figure 5 illustrates the network lifetime of all the techniques. The simulation results prove that the lifetime of the proposed methodology is higher than the other relevant methods. The related methods have bigger amount of repeated data and rebroadcasting, so the lifetime is shorter compared to the proposed methodology. The proposed method improves energy utilization and reduces the amount of repeated data so the network lifetime for the proposed method is higher compared to the related methods, as shown in Fig. 5.
Throughput is calculated as the total amount of data packets successfully transmitted to the sink nodes. The existing methods have received a higher amount of data packets compared to the proposed methodology because of the repeated data. Figure 6 shows the throughput of the proposed technique, which is compared with the related methods.
The delivery ratio is calculated as the rate of total amount of data packets received in the sink nodes according to the total amount of packets delivered from the source nodes. The comparison is performed using simulations and implemented to execute the delivery ratio for all the methods. Figure 7 shows the results for delivery ratio for the proposed method which is compared with the relevant methods. For reducing the repeated information, the proposed methodology minimizes the forwarding nodes. Energy utilization is the primary parameter for analyzing the performance of the network that reveals the network lifetime status.
Minimized energy utilization produces the improved network lifetime. Figure 8 demonstrates the simulation results regarding the energy utilization. The proposed method has effectively utilized the energy consumption compared with the related methodologies. The proposed technique selects the forwarder node according to the residual energy. It also evades the total amount of forwarding nodes. Additionally, the proposed technique has used the priority assignment method, the repeated communications of the same data picketers are minimized considerably. As shown in Fig. 8, the proposed methodology has improved residual energy compared with the related methods.
The delay is calculated as the mean time taken for the data packets to be transmitted to the sink nodes. The proposed method is compared with the related methods through the simulation results that are illustrated in Fig. 9. The related methods have the highest amount of delay compared to the proposed technique. A particular holding period is required for forwarding data and the quality of the link is another parameter to perform the data forwarding. According to the simulation results, the proposed methodology has improved network lifetime, provided a high amount of delivery ratio, reduced delay, and provided effective energy utilization compared to the other methods. It can be concluded that the proposed algorithm is an effective routing procedure for Underwater Mobile sensor networks.
Conclusion
This approach is competent in perpetuating the endurance of the chain system and to administer various types of the sector and hot-zone complications. Gathering of data in deep-sea engineering applications is more affordable and possible, where data congregates in a slender intensity range. The transmission method improves the energy efficiency during data transmission. The challenges faced in Underwater Acoustic networks such as nodule’s repeated disturbances, narrow connection bandwidth and nodule energy can be minimized to a profitable extent as well. Future work will carry on the dynamic node based packet delivery in efficient way of UWSNs and also to remove the data redundancy while transmitting the data packets in complex environments.
References
1’Goyal, N., Dave, M. and Verma, A.K. (2020) SAPDA: secure authentication with protected data aggregation scheme for improving QoS in scalable and survivable UWSNs. Wirel Pers Commun (2020). https://doi.org/10.1007/s11277-020-07175-8
Abbas WB, Ahmed N, Usama C, Syed AA (2015) Design and evaluation of a low-cost, DIY-inspired, underwater platform to promote experimental research in UWSN. Ad Hoc Netw 34:239–251
Ahmed M, Mazleena S, Ibrahim Channa M (2017) Routing protocols based on node mobility for underwater wireless sensor network (UWSN): A survey. J Netw Comput Appl 78:242–252
Tariq Ali, Low Tang Jung, rahima Faye (2014) End-to-end delay and energy efficient transmit protocol for underwater wireless sensor networks. Wirel Pers Commun 79: 339–361
Tariq Ali, Tang Jung Low, Tang Jung, Ibrahima Faye (2012) Delay efficient layer by layer angle based flooding protocol (L2-ABF) for underwater wireless sensor networks, ICTA 2012, USA
Ali T, Jung LT, Faye I (2014) End-to-end delay and energy efficient routing protocol for underwater wireless sensor networks. Wirel Pers Commun 79:339–361. https://doi.org/10.1007/s11277-014-1859-z
Al-Salti F, Alzeidi N, Day K, Touzene A (2019) An efficient and reliable grid-based routing protocol for UWSNs by exploiting minimum hop count. Comput Netw 16224:106869
Annamalai S, Udendhran R, Vimal S (2019a) “An Intelligent Grid Network Based on Cloud Computing Infrastructures”, Novel Practices and Trends in Grid and Cloud Computing, pp 59–73. https://doi.org/10.4018/978-1-5225-9023-1.ch005
Annamalai S, Udendhran R, Vimal S (2019b) “Cloud-Based Predictive Maintenance and Machine Monitoring for Intelligent Manufacturing for Automobile Industry”, Novel Practices and Trends in Grid and Cloud Computing, pp 74–81. https://doi.org/10.4018/978-1-5225-9023-1.ch006
M Aslam, F Wang, Z Lv et al. (2017). Energy efficient cubical layered path planning algorithm (EECPPA) for acoustic UWSNs, in 2017 IEEE Pacific rim conference on communications, computers and signal processing (PACRIM), pp. 1–6, Victoria, BC, Canada, august 2017
Bhattacharjya, K., Alam, S. and De, D (2019) CUWSN: energy efficient routing protocol selection for cluster based underwater wireless sensor network. Microsyst Technol https://doi.org/10.1007/s00542-019-04583-0
Borhani M (2020) A multicriteria optimization for flight route networks in large-scale airlines using intelligent spatial information. International Journal of Interactive Multimedia and Artificial Intelligence 6(1):123–131. https://doi.org/10.9781/ijimai.2019.11.001
Dai P, Lu W, Le K, Liu D (2020) Sliding mode impedance control for contact intervention of an I-AUV: simulation and experimental validation. Ocean Eng 196:106855
Eidsvik OAN, Schjolberg I (2018) Finite element cable-model for remotely operated vehicles (ROVs) by application of beam theory. Ocean Eng 163:322–336
Feng P, Qin D, Ji P, Zhao M, Guo R, Berhane TM (2019) Improved energy-balanced algorithm for underwater wireless sensor network based on depth threshold and energy level partition. J Wireless Com Network 2019:228. https://doi.org/10.1186/s13638-019-1533-y
Fu Z, Wu X, Chen J (2017) Using frequency-following responses (FFRs) to evaluate the auditory function of frequency-modulation (FM) discrimination. Appl Inform 4:10. https://doi.org/10.1186/s40535-017-0040-7
Ghoreyshi SM, Shahrabi A, Boutaleb T (2018) A cluster-based mobile data-gathering scheme for underwater sensor networks. 2018 International Symposium on Networks, Computers and Communications (ISNCC). IEEE, Rome, pp 1–6
Goyal N, Dave M, Verma AK (2016) Energy efficient architecture for intra and inter cluster communication for underwater wireless sensor networks. Wirel Pers Commun 89:687–707. https://doi.org/10.1007/s11277-016-3302-0
Goyal N, Dave M, Verma AK (2017) Improved Data Aggregation for Cluster Based Underwater Wireless Sensor Networks. Proc Natl Acad Sci, India, sect A Phys Sci 87:235–245. https://doi.org/10.1007/s40010-017-0344-y
Goyal N, Dave M, Verma AK (2019) Protocol stack of underwater wireless sensor network: classical approaches and new trends. Wirel Pers Commun 104:995–1022. https://doi.org/10.1007/s11277-018-6064-z
Guo Y, Han Q, Kang X (2019) Underwater sensor networks localization based on mobility-constrained beacon. Wirel Netw 26:2585–2594. https://doi.org/10.1007/s11276-019-02023-5
Satoshi Hirai, Yosuke Tanigawa and Hideki Tode (2012). Integration method between localization and transmit in underwater sensor networks. Computational science and engineering (CSE).IEEE 15th international conference on, page 689-693. IEEE Computer Society
Jiang P, Feng Y, Wu F, Yu S, Xu H (2016) Dynamic layered dual-cluster heads routing algorithm based on krill herd optimization in UWSNs. Sensors 16(9):1379
Kalkan K, Levi A (2014) Key distribution scheme for peer-to-peer communication in mobile underwater wireless sensor networks. Peer-to-Peer Netw Appl 7:698–709. https://doi.org/10.1007/s12083-012-0182-2
Khan, G., Dwivedi, R.k. (2018) Autonomous deployment and adjustment of nodes in UWSN to achieve blanket coverage (ADAN-BC). Int j inf tecnol https://doi.org/10.1007/s41870-018-0250-9
Kumar S, Kumar-Solanki V, Choudhary SK, Selamat A, Gonzalez-Crespo R (2020) Comparative study on ant Colony optimization (ACO) and K-means clustering approaches for jobs scheduling and energy optimization model in internet of things (IoT). International Journal of Interactive Multimedia and Artificial Intelligence 6(1):107–116. https://doi.org/10.9781/ijimai.2020.01.003
Li Y, Yu X, Zhao Y, Zhang J (2020) Service differentiation-based spectrum defragmentation in mixed grid optical networks. Opt Fiber Technol 56:102207
Lin Z-t, Lv R-q, Zhao Y, Zheng H-k (2020) High-sensitivity salinity measurement sensor based on no-core fiber. Sensors Actuators A Phys 305:111947
Luo J, Han Y (2019) A node depth adjustment method with computation-efficiency based on performance bound for range-only target tracking in UWSNs. Signal Process 158:79–90
Luo J, Han Y, He X (2019) Optimal bit allocation for maneuvering target tracking in UWSNs with additive and multiplicative noise. Signal Process 164:125–135
Nighot M, Ghatol A, Thakare V (2018) Self-organized hybrid wireless sensor network for finding randomly moving target in unknown environment. International Journal of Interactive Multimedia and Artificial Intelligence 5(1):16–28. https://doi.org/10.9781/ijimai.2017.09.003
Pavitra ARR, Janani ESV (2019) Overlay networking to ensure seamless communication in underwater wireless sensor networks. Comput Commun 147:122–126
Peng X, Kong L (2020) Design and optimization of optical receiving antenna based on compound parabolic concentrator for indoor visible light communication. Opt Commun 464:125447
Ruoyu Su, R. Venkatesan, Cheng Li. (2013). A new nodule coordination scheme for data gathering in underwater acoustic sensor networks using autonomous underwater vehicle. Wireless Communications and Networking Conference (WCNC), 2013 IEEE
Salti FA, Alzeidi N, Arafeh BR (2017) EMGGR: an energy efficient multipath grid-based geographic routing protocol for underwater wireless sensor networks. Wirel Netw 23(4):1301–1314
Shen W, Zhang C, Shi J (2019) Weak k-barrier coverage problem in underwater wireless sensor networks. Mobile Netw Appl 24:1526–1541. https://doi.org/10.1007/s11036-019-01273-z
Teague J, Allen MJ, Scott TB (2018) The potential of low-cost ROV for use in deep-sea mineral, ore prospecting and monitoring. Ocean Eng 147:333–339
Vimal S, Khari M, Dey N, Crespo RG, Robinson YH (2020a) Enhanced resource allocation in mobile edge computing using reinforcement learning based MOACO algorithm for IIOT. Comput Commun 151:355–364
Vimal S, Khari M, Crespo RG, Kalaivani L, Dey N, Kaliappan M (2020b) Energy enhancement using Multiobjective Ant colony optimization with Double Q learning algorithm for IoT based cognitive radio networks. Comput Commun 154:481–490
Vimal S, Suresh A, Subbulakshmi P, Pradeepa S, Kaliappan M (2020c) Edge computing-based intrusion detection system for smart cities development using IoT in urban areas. In: Kanagachidambaresan G, Maheswar R, Manikandan V, Ramakrishnan K (eds) Internet of things in smart Technologies for Sustainable Urban Development. EAI/Springer Innovations in Communication and Computing. Springer, Cham
Vimal S, Kaliappan M, Suresh A (2020d) Development of Cloud Integrated Internet of Things Based Intruder Detection System. J Comput Theor Nanosci 15:3565–3570
Vimal S et al (2016) Secure data packet transmission in MANET using enhanced identity-based cryptography. International Journal of New Technologies in Science and Engineering 3(12):35–42
Wang Zhuo, Guo Hongmei, Jiang Longjie, Feng Xiaoning (2016) AUV-aided communication method for underwater mobile sensor network. OCEANS 2016 – IEEE: 1–7
Yadav S, Kumar V (2019) Hybrid compressive sensing enabled energy efficient transmission of multi-hop clustered UWSNs. AEU Int J Electron Commun 110:152836
Yoon S, Azad AK, Hoon O, Kim S (2012) AURP: an AUV-aided underwater transmit protocol for underwater acoustic sensor networks. Sensors 12(2):1827–1845
Yu C, Wang R, Zhang X, Li Y (2020) Experimental and numerical study on underwater radiated noise of AUV. Ocean Eng 201:107111
Zapadka T, Ostrowska M, Stoltmann D, Krężel A (2020) A satellite system for monitoring the radiation budget at the Baltic Sea surface. Remote Sens Environ 240:111683
Zhou Z, Yao B, Xing R, Shu L, Bu S (2016) E-CARP: an energy efficient routing protocol for UWSNs in the internet of underwater things. IEEE Sensors J 16(11):4072–4082
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
None.
Declaration of interest statement
The authors declare that they do not have any conflict of interest. This research does not involve any human or animal participation. All authors have checked and agreed the submission.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Pasupathi, S., Vimal, S., Harold-Robinson, Y. et al. Energy efficiency maximization algorithm for underwater Mobile sensor networks. Earth Sci Inform 14, 215–225 (2021). https://doi.org/10.1007/s12145-020-00478-1
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12145-020-00478-1