Abstract
In some remote areas under extremely scarce computation and communication resources, unmanned aerial vehicles (UAVs) assisted wireless communications are quite attractive for the more widely communication coverage and powerful computation capacity in contrast to user mobile devices (MDs). In addition to providing relay communication capabilities, the UAV can not only perform user tasks locally, but also offload them to base station or cloudlet for computing, provided that the user tasks require more powerful computation capacities. Considering the fact that the mobility trajectory of UAV could exert a negative impact on mobile offloading, we investigate the mobile offloading problem with a comparative consideration of mobility trajectory, communication, and computation resource allocation, in which the UAV-assisted mobile offloading and trajectory optimization problem (UOTO) is formulated with the objective of maximizing minimum user utility. Unfortunately, the UOTO provided is proven to be non-convex and there is no effective way to solve it. To overcome the difficulties, we develop a near-optimal algorithm by integrating the nonlinear fractional programming (NFP) and successive convex approximation (SCA). The extensive experiments are conducted to illustrate the performance of the proposed scheme.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
With the enduring prosperity of wireless communication techniques, pervasive Wireless Wide Area Networks (WWANs), e.g., the LTE-A networks, the next generation networks (5G) and beyond, have triggered the dramatic shift in people lifestyle and bring plentiful benefits to contemporaries. With WWANs, users can easily access remote Internet resources and enjoy services via Base Stations (BSs) anytime and anywhere, e.g., online shopping on the way to work, watching live broadcast videos during heavy traffic jam, playing interactive games on a high-speed train, to name a few. An irresistible tendency is that the contemporaries are heavily relying on WWANs to fulfill their transmission and computation requirements. Unfortunately, such a lifestyle shift could suffer from severe service degradation under massive transmission and computation scenarios, where huge volumes of mobile traffic are generated and aggregated at the side of network edge, exerting significant pressure on cellular BSs. Even more seriously, users may not be served properly when the BSs are heavily jammed, or even some of them are damaged by natural disasters, e.g., earthquakes or hurricanes.
To address this issue, mobile offloading [2], including traffic offloading and computation offloading, is considered to be of great significance, of which one traditional scheme is that the overloaded networks offload partial tasks to small-cell networks, e.g., WiFi access points and femtocells. For example, Losifidis et al. [3] assumed that the cellular networks can competitively lease residential users as access points for data offloading, while Al-Kanj et al. [4] proposed that the mobile device holders can actively form device-to-device (D2D) networks to offload partial user traffic for the overloaded cellular networks. In addition, Wang et al. [5] proposed a novel architecture that reduced resource consumption and ensured the extensibility of trust evaluation mechanism. The above existing work can be of feasibility and practicality only when the cooperative partners are densely deployed. Unfortunately, such assumptions cannot always hold, especially when partial cellular networks in populated urban areas are severely jammed by overloaded user traffic requirements or damaged by natural disasters. On the other hand, in remote areas out scope of the BS transmission coverage, users’ demands can hardly be fulfilled without the direct connections between users and BS. Considering this fact, leveraging Unmanned Aerial Vehicles (UAVs) to assist traffic or computation offloading in cellular networks is proposed [6,7,8,9], in which the UAVs serve as moving cloudlets or relays to accommodate user demands thanks to the convenient mobility in 3-D spaces [10,11,12,13,14,15]. With this offloading paradigm, the UAV can not only provide a much lager transmission coverage during flight, but also maintain a reliable connection with the cellular networks. As such, the user requirements can be satisfied to a certain extent. The existing work can achieve a better performance when the user demands are homogeneous, i.e., all users require only the same one of services, namely, transmission offloading or computation offloading, rather than both of them.
In this paper, we consider a more complicated and practical scenario, where users are heterogeneous, and each user might have different offloading requirement. Different from the data and computation co-offloading in [16], we use the UAV as a moving cloudlet to provide concurrent serve and relay when the heterogeneous users are not covered by the cellular BS. It is a necessity that the UAV has to fulfill its offloading tasks before a hard deadline during flying to the destination, and new challenges to the UAV-assisted traffic and computation offloading (UOTO) problem are brought in three folds. Firstly, the resource competition in the UOTO problem, including bandwidth and energy, is unavoidable. In comparison to the existing offloading optimization [17, 18], non-linear couple between UAV’s transmit power and bandwidth allocation is incurred, which leads to the UOTO problem difficult to solve optimally. Secondly, different from the assumption of sufficient UAV computation capacity in existing work [19,20,21,22,23], the UAV usually contributes to the computation offloading task with a constrained on-board computation resource during serving as a moving cloudlet. In other words, the user computation tasks could be performed at the locality, the UAV, or the BS server. Therefore, the UAV has to make an instant decision when multiple user tasks come. In addition, the UAV’s trajectory has to be considered since it can affect the resource allocation manner including energy and computation resources. Compared with the existing work [24,25,26], we not only consider the power allocation and trajectory optimization, also consider the heterogeneousness of users need. The above three folds motivate us to optimize the UOTO problem by jointly considering the bandwidth allocation, partial offloading decision and UAV’s trajectory planning. The UOTO problem considered in this paper is more practical since most of users might require traffic offloading and computation offloading concurrently, rather than only one of them. The optimal solution not only relies on the competition in resource competition between traffic offloading and computation offloading but also on the UAV’s trajectory planning. In consideration of the fairness among users, the objective of the UOTO problem is to maximize the minimum user utility. In the formulated problem, there exists non-linear couples among variables and it is an NP-hard problem. To deal with it, we propose a three-stage alternative optimization (TSAO) algorithm to solve it. The main contributions of this paper are summarized as follows.
Considering the heterogeneous demands for mobile offloading, the UAV-assisted mobile offloading and trajectory optimization problem (UOTO) is formulated with the objective of maximizing minimum user utility. And it is a non-convex optimization problem.
We carefully investigate the structure of the UOTO problem, which is decomposed three sub-problems, namely, bandwidth resource allocation, partial offloading decision, and UAV trajectory optimization. The closed form of optimal solution for bandwidth resource allocation is obtained by its dual multipliers.
We develop a three-stage alternative optimization algorithm to solve it iteratively by leveraging the nonlinear fractional programming (NFP) and successive convex approximation (SCA) methods.
The rest of this work is as follows. Section II introduces the system model and presents the formulation of UOTO problem. In Section III, we analyze the property of the problem and propose a three-stage alternative optimization algorithm to solve it. Then, numerical results are given in Section IV. Finally, in Section V, the conclusions are drawn.
2 System model
Considering a mobile offloading scenario with a three-dimensional (3D) Euclidean coordinate, there are N heterogeneous users with fixed locations on the ground. The users might have traffic demand, computation demand, or both of them. In the scenario, although the cellular BS server can provide a more powerful transmission and computing capability, the users cannot connect to the cellular networks directly due to the existing obstacles blocking the transmission between the users and cellular BS, or the users are not in the coverage of the cellular BS. One UAV, equipped with on-board communication circuits and computing processors while constrained energy and computation resources, can provide transmission and computation services for the covered users during floating from one position to another. Assume that there is a LOS transmission condition between the UAV and BS, i.e., the UAV can serve as an aerial platform for the covered users and meanwhile maintain a reliable connection with the BS. The considered system is time slotted with a duration T, which is divided into M identical slots.
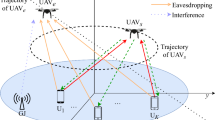
In the system model, three types of users, i.e., users with computation offloading demand, users with traffic offloading demand, and users with both offloading commands are considered. Different from our previous work [1], when the UAV faces some resource-hungry computation tasks, the UAV might transmit partial tasks to the BS server for the sake of saving resources. For the first user type, the UAV functions as a mobile cloudlet to provide computation services for this type of users. For the second user type, the UAV is employed as a relay to download the traffic from BS and then transmit to the kind of users. For the third user type, the UAV will perform traffic and computation offloading for users concurrently. The example of scenario is illustrated in Fig. 1.
A UAV-assisted wireless relay networks for mobile offloading scenario for heterogeneous users, where User 2, User 3 and User 5 require only traffic or computation offloading, while others have both demands. For the users with traffic demand, the UAV will request the relative contents from the BS and then transmit to the users. For the users with computation demand, the UAV and BS server will jointly process the tasks. UAV has a fixed initial and final location [27]
The computation tasks of users are partitioned into two parts, one is completed by the UAV and the other is transmitted to the BS server to perform, which is also called partial computation offloading mode.
The notations used in this paper are summarized in Table 1. Denote the set of UEs as \(\mathcal {N}\) and \(\mathbf {L}_{i}=[x_{i}^{(\text {l})},y_{i}^{(\text {l})},z_{i}^{(\text {l})}]\) as the coordinate of user i (1 ≤ i ≤ N), which can be obtained by the built-in GPS and other sensors [28]. We assume that all the users stand on a flat ground (i.e., \(z_{i}^{(\text {l})}\) is a constant) and the UAV flies at a fixed height H, which is the minimum altitude that is appropriate to the terrain. The wireless communication channels between MDs and UAV are dominated by line-of-sight links. Denote qst and qend as UAV’s the initial location and destination location, respectively. Considering the energy consumption, the UAV’s flight speed has an upper limit, denoted by \(v_{\max \nolimits }\) [28]. According to the slotted system model, M can be sufficiently large, such that the slot duration to be sufficiently small. Therefore, the location of UAV within each slot can be approximately constant [23, 27]. Noted that there are M sets of variables, which means the variables with different slots are irrelevant. Denote q(t) = [x(c)(t),y(c)(t),H] as UAV’s location within slot t, where x(c)(t) and y(c)(t) represent the horizontal and vertical coordinates, respectively. The location of BS is denoted as S = [x(s),y(s),H(s)], where H(s) denotes the altitude of BS.
Assume the bandwidth of downlink and uplink are both B MHz. And time division multiple access (TDMA) scheme is used in downlink and uplink transmission, respectively. Let \(\alpha _{i}^{(\text {d} )}(t)\) and \(\alpha _{i}^{(\text {u})}(t)\) represent the percentage of downlink and uplink communication duration allocated for user i, respectively. Obviously, for the users who have upload demands, the sum of their allocated upload proportion cannot exceed 1. The users who have download demands are similar. The constraints are given as
and
where \(\theta _{i}^{(\text {d} )}\) and \(\theta _{i}^{(\text {u})}\) represent user i’s traffic and computation offloading demands, respectively. And user i has offloading demands if it equals to 1, otherwise not.
The distance between user i and UAV and the distance between BS and UAV within slot t are respectively expressed as
According to [27, 29], the time-varying communication channel between user i and UAV and the time-varying communication channel between BS and UAV follow the free-space path loss model
where δ denotes the communication channel gain at the reference distance equals to 1 m.
According to the standard information theory [30], user i’s transmission rate in uplink within slot t is express as
where \(p_{i}^{(\text {u})}(t)\) represents user i’s transmit power and N0 represents the gaussian noise. Therefore, the traffic volume that user i uploaded is given by
Similarly, user i’s transmission rate in downlink can be expressed as
where \(p_{i}^{(\text {d})}(t)\) represents the transmit power that UAV allocates for user i. Therefore, traffic volume that user i downloaded within slot t is given by
Similarly, the transmit rate of UAV to BS within slot t is given by
Similar to [31, 32], the computing time of UAV and the downloading time of computation result are neglected, which is because UAV’s computing capability is significantly bigger than MDs’ and the returned traffic volume is relatively small. Then, the flight speed of UAV within slot t can be expressed as
Because the flight speed of UAV is upper bounded to its maximum flight speed \(v_{\max \nolimits }\), one has
Similarly, for UAV’s and users’ transmit power, one has
and
where \(p^{(\text {u})}_{i,\max \nolimits }\), \(p^{(\text {uav})}_{\max \nolimits }\) and ps represent the maximum transmit power of user i, UAV and the transmit power that UAV allocates for BS, respectively.
Due to users’ and UAV’s transmit power should be positive or equal to zero, one has
Besides, the sum of the transmission rates allocated by the UAV to all users is less than or equal to the bandwidth allocated by the UAV to the BS, one has
where Bs and p(b) denote the bandwidth that the UAV allocates to the BS and the transmit power of BS, respectively.
Each user has a downlink capacity requirement
where \(R_{i,\min }^{\text {(d)}}(t)\) denotes the minimum downlink capacity requirement of user i.
According to [19, 33], the computation time of user i on the UAV within slot t is given by
where γi and \(f_{i}^{(\text {c})}\) represent the number of CPU cycles per input bit needed for computing and the CPU frequency allocated for user i, respectively. ηi(t) denotes the proportion of computation task that user i computed on the UAV within slot t.
The computation time of user i on the central cloud within slot t is expressed as
The time that UAV offload user i’s partial task to the BS within slot t is given by
According to Eqs. 21-23, the computation delay of user i within slot t is expressed as
Therefore, the delay of user i within slot t is given by
The objective is to maximize user utility [34, 35], which is indicated by the computation size minus the delay, and it is expressed as
where \(\tau _{i}^{\text {(d)}}\) and \(\tau _{i}^{\text {(t)}}\) denote the weights of computation size and delay of user i, respectively. It should be noted that \(0 \le \tau _{i}^{\text {(d)}}, \tau _{i}^{\text {(t)}} \le 1\). Users can set different values of \(\tau _{i}^{\text {(d)}}\) and \(\tau _{i}^{\text {(t)}}\) for their demands. For example, when a user is sensitive to the delay (e.g., online game), the user can set \(\tau _{i}^{\text {(t)}} = 1\) and \(\tau _{i}^{\text {(d)}} = 0\). When user concerns more about the computation size, the value of \(\tau _{i}^{\text {(d)}}\) can be assigned larger. In practice the proper weights can be calculated by the multi-attribute utility approach [36].
We take the Max-Min fairness scheme [37, 38] for users mobile offloading. We introduce a variable \(\xi = \min \limits _{i \in \mathcal {N}}U_{i} \) and add following constraint:
Then, the objective is to maximize ξ. Therefore, we can obtain the UOTO optimization problem as P0.
In problem P0, the objective function represents user utility. Equations 1 and 2 denote the uplink and downlink bandwidth allocation constraints, respectively. And Eqs. 13-14 denote the constraint of UAV’s flight speed and transmit power. Equations 15-20 denote the download rate and transmit power constraints of users. Besides, Eq. 27 denotes the fairness constraint among users.
3 Problem analysis and algorithm design
Due to there exists nonlinear coupling in constraints (20) and (27), the problem P0 is therefore non-convex. At present, there are no effective solutions to obtain the optimal solution. Therefore, instead of resorting to expensive global optimization methods, we propose the TSAO algorithm to decouple the nonlinear coupling variables and solve them iteratively. In detail, we separate the variables into several subsets of non-overlapping variables and then get three sub-problems. For each sub-problem, we replace the non-convex function with suitable convex approximation by leveraging SCA and NFP [39,40,41,42].
Stage I: For the given trajectory and variables ηi(t), \(f_{i}^{\text {(c)}}\), p(s), we have following bandwidth allocation and power optimization problem P1 that related to users and UAV. However, due to the constraint (27) is non-convex, P1 is a non-convex problem.
Let \(\phi _{i}^{(\text {u})}(t) = \alpha _{i}^{(\text {u})}(t)p_{i}^{(\text {u})}(t)\), \(\phi _{i}^{(\text {d})}(t) = \alpha _{i}^{(\text {d})}(t)p_{i}^{(\text {d})}(t)\), \(D_{i}^{\text {(u)}}(t)\) is then transformed into \(D_{i}^{\text {(u1)}}(t)\), which is given by
Besides, constraint (27) can be rewritten as
Thereafter, we can identically transform (30) into following constraints:
Therefore, P0 is reformed as P1.
According to [43, 44], it can be proved that P1 is a convex optimization problem. We can tackle it by adopting the classic algorithm (e.g. Gradient descent) [45,46,47,48], and the optimal solutions of \(\alpha _{i,\text {opt}}^{(\text {u})}(t)\), \(\alpha _{i,\text {opt}}^{(\text {d})}(t)\), \(p_{i,\text {opt}}^{(\text {d})}(t)\), \( p_{i,\text {opt}}^{(\text {u})}(t)\) will be obtained. Moreover, we have the following Theorem 1.
Theorem 1
For a given trajectory, the closed-form of the optimal solution can be directlyobtained by the dual multipliers that associated with constraints in problemP1.
Proof
Let λ(uu),λ(ud), λ(v), λ(pdm), \(\lambda _{i}^{(\text {pum})}\), λ(sum), \(\lambda _{i}^{(\text {u})}, \lambda ^{(\text {ps})},\)\(\lambda _{i}^{(\text {pd})}, \lambda ^{(\text {r})}, \lambda _{i}^{(\text {rm})}, \lambda ^{(\text {e})}, \lambda _{i}^{(\text {f1})}, \lambda _{i}^{(\text {f2})}\) denote the dual multipliers w.r.t. constraints (13)-(20), (31) and (32). Thus, the general Lagrangian function of problem P1 can be expressed as (34) (see next page).
Therefore, the general Lagrangian dual function of problem P1 is given by
Then, the solution of P1 can be obtained by solving its dual problem, which is expressed as
It can be seen that the dual problem of P1 can be divided into N independent convex optimization problems. Thus, by getting the derivation of each sub-problem with respect to variables \(\alpha _{i}^{(\text {u})}(t), \alpha _{i}^{(\text {d})}(t), p_{i}^{(\text {u})}(t), p_{i}^{(\text {d})}(t)\), we can obtain the closed-form of the optimal solution. □
Stage II: After P1 is solved, the optimal values of \(p_{i,\text {opt}}^{(\text {d})}(t)\), \(p_{i,\text {opt}}^{(\text {u})}(t)\), \(\alpha _{i,\text {opt}}^{(\text {u})}(t)\), \(\alpha _{i,\text {opt}}^{(\text {d})}(t)\) under some given variables can be obtained. Then, the problem related to computation can be obtained as P2 for given variables \(\alpha _{i,\text {opt}}^{(\text {u})}(t)\), \(\alpha _{i,\text {opt}}^{(\text {d})}(t)\), \(p_{i,\text {opt}}^{(\text {d})}(t)\), \(p_{i,\text {opt}}^{(\text {u})}(t)\) and q(t). P2 aims at solving the proportion of partial offloading and power optimization related to UAV and BS, which is given as
Due to the fraction in Eq. 32, problem P2 is thus a nonlinear fraction optimization problem, which is hard to solve. We have following lemma by the reformulation of P2.
Lemma 1
problem P 2 can be transformed into an equivalent convex optimization.
Proof
By introducing some additional variables to replace the fraction expressions, we have the following equations:
Then, constraints (31) and (32) are transformed as follows:
Besides, in order to transform P2 into a convex optimization problem, two following constraints should be satisfied [49]:
Therefore, we have following convex problem P3:
□
Therefore, problem P2 is transformed into the convex problem P3, which can be tackled by leveraging the classic optimization algorithm, and the corresponding optimal solutions can be then obtained.
Stage III: When P1 and P3 are solved, the optimal variables expect UAV’s trajectory are obtained. Then, UAV’s trajectory can be obtained by following optimization problem P4.
Because (32) is non-convex, P4 is a non-convex problem. In Eq. 32, variables \(p_{i}^{(\text {u})}\) and q(t) are nonlinear coupled in the form of bilinear expression [50, 51]. We leverage the SCA method to tackle it, which decouples the variables and approximate it to a convex problem. Thereafter, by relaxing the non-convex expressions with Taylor formula, Theorem 2 can be obtained.
Theorem 2
For any given feasible UAV trajectoryq0(t),following inequalities can hold:
where the equalities hold whenq(t) = q0(t).
Proof
Let δ(t) = ||q(t) −l(t)||2, and then \({\log _{2}}(1 + \frac {{p_{i}^{(\text {u})}(t)}}{{{N_{0}}({H^{2}} + ||{\textbf {q}}(t) - {\textbf {l}}(t)|{|^{2}})}})\) is converted into \({\log _{2}}\!(1 \!+ \!\frac {{p_{i}^{(\text {u})}\!(t)}}{{{N_{0}}\!({H^{2}} + \delta (t))}}\!)\). Let \(f(\delta (t)) = {\log _{2}}(1 + \frac {{p_{i}^{(\text {u})}(t)}}{{{N_{0}}({H^{2}} + \delta (t))}})\), in which δ(t) is the variable of function f(δ(t)). Therefore, f(δ(t)) is a convex function. According to Taylor expansion, the following inequality can be obtained.
By substituting δ(t) = ||q(t) −l(t)||2 into (50), inequality (47) is obtained. Similarly, the inequality (48) and (49) are obtained. □
Therefore, the upload traffic size of user i within slot t is transformed into \(D_{i}^{{}^{\prime \prime }(\text {u})}(t)\), which is given by
Substituting (51), (52) and (53) into P5, we have problem P5.
According to [19, 27, 52], it can be proven that problem P5 is convex. Thus, we can tackle it by leveraging classic algorithm (e.g., Gradient descent). Thereafter, substituting the optimal trajectory 6̱oldqopt(t) into problem P1. Then, solve P1, P3 and P5 iteratively until the growth of objective function is less than the threshold ρ1. The details are depicted in Algorithm 1.

The convergence of Algorithm 1 is discussed in [53]. Besides, the complexity of Algorithm 1 is composed of four aspects. The first is the computation of problem P1 by using CVX [54, 55]. The second is the computation of problem P3 by using CVX. Denote A1,B1 as the number of required iterations for the outer loop and inner loop in Algorithm 1, respectively. Thus, according to [56], the complexity of Algorithm 1 is \({\mathcal O}(A_{1}(2M^{3} + B_{1}M^{3}))\).
4 Numerical results
In this section, numerical results are provided to evaluate the performance of proposed scheme. The simulation settings are based on some existing work [27, 57]. There are N = 4 users and their positions are L1 = [0,0], L2 = [10,0], L3 = [0,10] and L4 = [10,10], respectively [43]. The location of BS is set as S = [70,70,0]. Besides, UAV’s initial position and destination position are set as qst = [0,0] and qst = [0,10], respectively. Assume users are static within each slot. Users’ traffic and computation offloading demands are set as a(d) = [1,1,1,0] and a(u) = [1,0,1,1], respectively. Besides, the duration time is set as T = 2s, which is decomposed into M = 50slots. UAV’s maximum flight speed is set as 20m/s. Both uplink and downlink bandwidths are set as 40MHz. \(p_{max}^{\text {(d)}}\) and \(p_{i,max}^{\text {(u)}}\) are set as 4W and 4W, respectively. \(\tau _{i}^{\text {(d)}}\) and \(\tau _{i}^{\text {(t)}}\) are set as 0.5 and 0.5, respectively. The remaining parameters used in the simulations, unless specified otherwise, are summarized in Table 2. The altitude of UAV is set as H = 10m, the channel power gain is set as δ = -50dB and the noise power is set as N0 = -174dBm/Hz. Besides, it is assumed the required CPU cycles per bit of user i is set as γi = 103 and the computing capacity that cloud allocated to user i is set as \(f_{i}^{\text {(c)}}\) = 1GHZ.
Figure 2 shows the dynamics of the minimum user utility during iteration. Similar to [27, 43, 58, 59], the iteration number in Fig. 2 is defined as the number that the three-stage has been looped. That is, we only calculate the number of outer loop in Algorithm 1, and the iterations of solving problem P1,P3 and P5 is not counted. It can be observed that the value of utility will decrease with the iteration. The transmit power of UAV larger, the minimum user utility larger, which is because the transmit rate between UAV and BS increases. More clearly, the transmit power larger, the more data can be processed on UAV and the less delay it takes. And the proposed partial offloading scheme outperforms the scheme that only computing on UAV. The reason is that the proposed partial offloading scheme can take use of BS for computing, which augments the computation capacity of UAV. However, the minimum user utility of proposed partial is less than that of total on UAV during iteration. It’s because that in the alternative process of solving the three-stage problem, the obtained value of some variables are not global optimal. Besides, the proposed algorithm only need several iterations to converge, which indicates it is computationally efficient and has a fast convergence rate.
Figures 3 and 4 show the dynamics of users’ transmit power with different time slots under a given semicircle trajectory. It can be observed that user 1’s transmit power is gradually increasing, which is due to the distance between UAV and user 1 is gradually increasing. Due to the requirements of fairness among users, users will increase transmit power to keep communication rate steady when the distance increases. Besides, it can be observed that the trends of users’ transmit power is opposite to that of the distance between users and UAV. Since user 2 has no computation offloading demand, the transmit power of user 2 equals to zero. Additional, the transmit power of user 4 has an increasing trend after decreasing, which is due to the distance between user 4 and UAV decreases first and increases after slot 25. Thus, it can be inferred that users’ transmit power is related to the distance between UAV and users. In addition, it can be observed that the value of users’ average transmit power are close, and it will lead to the traffic size that users uploaded are close, which denotes the fairness among users.
Similar to Figs. 3 and 4, 5 and 6 show UAV’s transmit power that allocated to each user with different time slots under a given semicirle trajectory. It can be seen that the result is similar to Figs. 3 and 4, which has been described and analyzed above. Moreover, to meet users’ minimum download rate requirement, the minimum transmit power that UAV allocates to users is still relatively high. It implies that the proposed scheme not only guarantees the computation offloading fairness, but also traffic offloading fairness among users.
The proportion of users’ upload duration within each slot is shown in Figs. 7 and 8. It can be seen that the dynamic changes trends in Figs. 7 and 8 are opposite to that in Figs. 3 and 4. That is, the transmit power of users smaller, the proportion of users upload time larger. And it denotes that more traffic of users will be uploaded when the transmit power in low state. In addition, it can be observed that the distance between UAV and users smaller, the upload time of users larger, which guarantees the high computation rate of users.
The proportion of users’ download duration within each slot is shown in Figs. 9 and 10. It can be observed that the dynamic changes trends in Figs. 9 and 10 are opposite to that in Figs. 5 and 6. The transmit power that UAV allocates to users smaller, the proportion of download duration larger, which is due to the minimum download rate requirements of users. That is, in order to satisfy the requirements, the download time of users will increase when in low transmit power range. From another aspect of view, UAV offloads more traffic for users in the low transmit power state, which guarantees UAV can assist more users.
Figure 11 shows the minimum user utility with different user’s and UAV’s maximum transmit power and offloading schemes [27, 43]. It can be observed that with the increasing of users’ maximum transmit power, the minimum user utility is also increasing. The reason is that the transmit power of users higher, the size of data uploaded larger, which is contribute to the user utility. However, the minimum user utility increasing gradually slowly, which is because the transmit rate between UAV and BS is limited. With the upload data increasing, UAV has no enough computation capacity, which leads to the increasing of delay. Therefore, the minimum user utility increases gradually slowly. In addition, it can be observed that minimum user utility under the schemes that only perform computation on UAV and local computation is relatively smaller than the proposed schemes, which indicates the efficiency of proposed algorithm.
Figure 12 show the minimum user utility versus the maximum transmit power of users under several different UAV trajectories. As shown in Fig. 12, the minimum user utility achieved by using proposed scheme is larger than that of semi-circle trajectory mode and trajectory with a constant speed mode. The reason is that users who are far from UAV have low transmit rate, and it leads to the low computation rate and high delay. Besides, the result indicates that the optimization of the trajectory of the UAV can improve the minimum user utility. It also verifies that our proposed scheme outperforms the disjoint optimization scheme. Besides, the relation between the transmit power of users and minimum user utility is consistent with Fig. 11.
Figure 13 show the minimum user utility versus the number of users under different maximum transmit power of UAV. The maximum transmit power of UAV is set as \(p^{(\text {\text {uav}})}_{\max \nolimits }\) = 0.2W, \(p^{(\text {\text {uav}})}_{\max \nolimits }\) = 0.3W or \(p^{(\text {\text {uav}})}_{\max \nolimits }\) = 0.4W. As shown in Fig. 13, the minimum user utility increases with the number of users. The reason is that the number of users larger, the computation rate larger. However, the delay doesn’t increase too much, which is because the UAV offloading some tasks to the BS for computing. It indicates the proposed schemes is adaptive for the large number of users. Besides, it can be observed that the minimum use utility under \(p^{(\text {\text {uav}})}_{\max \nolimits }\) = 0.4W is larger than that of utility under \(p^{(\text {\text {uav}})}_{\max \nolimits }\) = 0.3W and \(p^{(\text {\text {uav}})}_{\max \nolimits }\) = 0.2W. It’s because the maximum transmit power of the UAV larger, the transmit rate between UAV and BS larger, which can reduce the delay and increase the computation rate.
As shown in Fig. 14, the utilities of users are almost equally. With the increasing of user transmit power, the results are similar. It indicates fairness among users.
In conclusion, we evaluate the performance of proposed scheme from several different aspects. First, Fig. 2 shows the proposed algorithm has a fast convergence rate. Then, Figs. 3-6 study the dynamics of users’ and UAV’s transmit power with different time slots, and Fig. 7-10 study the dynamics of download and upload duration allocation. The results show that the resources allocated to each user are almost equally, which demonstrates the fairness among users. Last, the minimum user utility with different parameters and other disjoint optimization schemes are studied in Figs. 11-14. The results show that the proposed scheme can achieve larger user utility under different parameters, which implies the proposed scheme has a better performance than other disjoint optimization schemes.
5 Conclusion
In this paper, we study the UOTO optimization problem. The minimum user utility is maximized under the partial offloading schemes. Since the problem is formulated as a non-convex problem, a three-stage alternative optimization algorithm based on SCA and Nonlinear fractional programming is proposed to jointly optimize the power allocation, bandwidth allocation, offloading decision and UAV trajectory. Simulation results show that the proposed schemes outperform other disjoint optimization schemes. Besides, it is shown that the convergence speed of proposed algorithm is fast.
For the future work, we are going to study the more general case where multiple UAVs assisted mobile offloading, and the collision avoidance among UAVs should be carefully investigated. Another research direction is to consider UAV flight with a variable altitude, which would be very interesting and challenging.
References
Hu X, Zhuang X, Feng G, Lv H, Wang H, Lin J (2018) Joint optimization of traffic and computation offloading in uav-assisted wireless networks. In: 2018 IEEE 15th international conference on mobile Ad Hoc and sensor systems (MASS). IEEE, pp 475–480
Wang Y, Wang K, Huang H, Miyazaki T, Guo S (2019) Traffic and computation co-offloading with reinforcement learning in fog computing for industrial applications. IEEE Trans Indust Inf 15(2):976–986
Iosifidis G, Gao L, Huang J, Tassiulas L (2015) A double-auction mechanism for mobile data-offloading markets. IEEE/ACM Trans Netw 23(5):1634–1647
Al-Kanj L, Vincent Poor H, Dawy Z (2014) Optimal cellular offloading via device-to-device communication networks with fairness constraints. IEEE Trans Wirel Commun 13(8):4628–4643
Wang T, Zhang G, Liu A, Bhuiyan MZA, Jin Q (2019) A secure iot service architecture with an efficient balance dynamics based on cloud and edge computing. IEEE Internet of Things Journal 6(3):4831–4843
Zeng Y, Zhang R, Teng JL (2016) Wireless communications with unmanned aerial vehicles: opportunities and challenges. IEEE Commun Mag 54(5):36–42
Wang K, Zhou Q, Guo S, Luo J (2018) Cluster frameworks for efficient scheduling and resource allocation in data center networks: A survey. IEEE Commun Surv Tutorials 20(4):3560–3580
Ministry of Internal Affairs Economic Research Office and Japan Communications (MIC). Information and communications in japan. http://www.soumu.go.jp/johotsusintokei/whitepaper/eng/WP2011/2011-index.html
Qiantori A, Sutiono AB, Hariyanto H, Suwa H, Ohta T (2012) An emergency medical communications system by low altitude platform at the early stages of a natural disaster in indonesia. J Med Syst 36(1):41–52
Cheng F, Zhang S, Li Z, Chen Y, Zhao N, Yu R, Leung VCM (2018) Uav trajectory optimization for data offloading at the edge of multiple cells. IEEE Trans Veh Technol 67(7):6732–6736
Li Y, Feng G, Ghasemiahmadi M, Cai L (2019) Power allocation and 3-d placement for floating relay supporting indoor communications. IEEE Trans Mob Comput 18(3):618–631
Zhan P, Yu K, Swindlehurst AL (2011) Wireless relay communications with unmanned aerial vehicles: Performance and optimization. IEEE Trans Aerosp Electron Syst 47(3):2068–2085
Zhang J, Zeng Y, Zhang R (2018) UAV-Enabled Radio Access Network: Multi-Mode Communication and Trajectory Design. ArXiv e-prints
Zhang J, Zeng Y, Zhang R (2017) Spectrum and energy efficiency maximization in uav-enabled mobile relaying. In: IEEE international conference on communications, pp 1–6
Zhao W (2004) A message ferrying approach for data delivery in sparse mobile ad hoc networks. In: Proceedings of ACM Int’l symposium on mobile Ad Hoc networking and computing, pp 187–198
Wang Y, Wang K, Huang H, Miyazaki T, Guo S (2019) Traffic and computation co-offloading with reinforcement learning in fog computing for industrial applications. IEEE Trans Indust Inf 15(2):976–986
Wang T, Zhou J, Liu A, Bhuiyan MZA, Wang G, Jia W (2019) Fog-based computing and storage offloading for data synchronization in iot. IEEE Internet of Things Journal 6(3):4272–4282
Wang T, Zeng J, Lai Y, Cai Y, Tian H, Chen Y, Wang B Data collection from wsns to the cloud based on mobile fog elements. Future Generation Computer Systems, https://doi.org/10.1016/j.future.2017.07.031
Jeong S, Simeone O, Kang J (2017) Mobile cloud computing with a uav-mounted cloudlet: optimal bit allocation for communication and computation. Iet Commun 11(7):969–974
He X, Wang K, Huang H, Miyazaki T, Wang Y, Guo S (2018) Green resource allocation based on deep reinforcement learning in content-centric iot. IEEE Transactions on Emerging Topics in Computing, pp 1–1. https://doi.org/10.1109/TETC.2018.2805718
Zeng Y, Zhang Rx (2017) Energy-efficient uav communication with trajectory optimization. IEEE Trans Wirel Commun 16(6):3747–3760
Hua M, Wang Y, Wu Q, Li C, Huang Y, Yang L (June 2018) Energy Optimization for Cellular-Connected multi-UAV Mobile Edge Computing Systems with Multi-Access Schemes. ArXiv e-prints
Zhang J, Zeng Y, Zhang R (2018) Uav-enabled radio access network: Multi-mode communication and trajectory design
Huang Y, Xu J, Qiu L, Zhang R (2018) Cognitive UAV Communication via Joint Trajectory and Power Control. arXiv:1802.05090
Li P, Guo S, Miyazaki T, Liao X, Jin H, Zomaya AY, Wang K (2017) Traffic-aware geo-distributed big data analytics with predictable job completion time. IEEE Trans Parallel Distrib Syst 28(6):1785–1796
Xu J, Zeng Y, Zhang R (2018) Uav-enabled wireless power transfer: Trajectory design and energy optimization. IEEE Transactions on Wireless Communications 17(8):5092–5106
Jeong S, Simeone O, Kang J (2018) Mobile edge computing via a uav-mounted cloudlet: Optimization of bit allocation and path planning. IEEE Trans Veh Technol 67(3):2049–2063
Motlagh NH, Taleb T, Arouk O (2016) Low-altitude unmanned aerial vehicles-based internet of things services Comprehensive survey and future perspectives. IEEE Internet J 3(6):899–922
Zhang H, Zheng WX (2018) Denial-of-service power dispatch against linear quadratic control via a fading channel. IEEE Trans Autom Control 63(9):3032–3039
Cover TM, Thomas JA (2006) Elements of information theory (wiley series in telecommunications and signal processing). Wiley-Interscience, New York
Wang F, Xu J, Wang X, Cui S (2017) Joint offloading and computing optimization in wireless powered mobile-edge computing systems. IEEE Trans Wirel Commun 17(3):1784– 1797
Zhang H, Meng W, Qi J, Wang X, Zheng WX (2019) Distributed load sharing under false data injection attack in an inverter-based microgrid. IEEE Trans Indust Electron 66(2):1543–1551
Yang G, He S, Shi Z (2017) Leveraging crowdsourcing for efficient malicious users detection in large-scale social networks. IEEE Internet J 4(2):330–339
Xu C, Jiao L, Li W, Fu X (2015) Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE/ACM Trans Netw 24(5):2795–2808
Thengvall BG, Bard JF, Yu G (2003) A bundle algorithm approach for the aircraft schedule recovery problem during hub closures. Transp Sci 37(4):392–407
Wallenius J, Dyer JS, Fishburn PC, Steuer RE, Zionts S, Deb K (2008) Multiple criteria decision making, multiattribute utility theory: Recent accomplishments and what lies ahead. Manage Sci 54(7):1336–1349
Sun R, Hong M, Luo ZQ (2014) Joint downlink base station association and power control for max-min fairness: Computation and complexity. IEEE J Sel Areas Commun 33(6):1040–1054
Li Y, Sheng M, Tan CW, Zhang Y, Sun Y, Wang X, Shi Y, Li J (2015) Energy-efficient subcarrier assignment and power allocation in ofdma systems with max-min fairness guarantees. IEEE Trans Commun 63 (9):3183–3195
Fang B, Qian Z, Zhong W, Shao W (2015) An-aided secrecy precoding for swipt in cognitive mimo broadcast channels. IEEE Commun Lett 19(9):1632–1635
Mokhtari A, Koppel A, Scutari G, Ribeiro A (2017) Large-scale nonconvex stochastic optimization by doubly stochastic successive convex approximation. In: IEEE international conference on acoustics, speech and signal processing, pp 4701–4705
Tian X, Zhang W, Yang Y, Wu X, Peng Y, Wang X (2018) Toward a quality-aware online pricing mechanism for crowdsensed wireless fingerprints. IEEE Trans Veh Technol 67(7):5953–5964
Yang C, Shi Z, Han K, Zhang JJ, Gu Y, Qin Z (2018) Optimization of particle cbmember filters for hardware implementation. IEEE Trans Veh Technol 67(9):9027–9031
Zhou F, Wu Y, Qingyang Hu R, Qian Y (June 2018) Computation Rate Maximization in UAV-enabled Wireless Powered Mobile-Edge Computing Systems. ArXiv e-prints
Yang G, He S, Shi Z, Chen J (2017) Promoting cooperation by the social incentive mechanism in mobile crowdsensing. IEEE Commun Mag 55(3):86–92
Faybusovich BV (2006) Convex optimization. IEEE Trans Autom Control 51(11):1859–1859
Bai Y, Zhang L (2017) A full-newton step interior-point algorithm for symmetric cone convex quadratic optimization. J Indust Manag Optim 7(4):891–906
Tian X, Li W, Yang Y, Zhang Z, Wang X (2018) Optimization of fingerprints reporting strategy for WLAN, indoor localization. IEEE Trans Mob Comput 17(2):390–403
Wang Y, Lopez JA, Sznaier M (2018) Convex optimization approaches to information structured decentralized control. IEEE Trans Autom Control 63(10):3393–3403
Shen K, Yu W (2018) Fractional programming for communication systems-part I: power control and beamforming. CoRR, arXiv:1802.10192
Sherali HD, Alameddine A (1992) A new reformulation-linearization technique for bilinear programming problems. J Glob Optim 2(4):379–410
Zhu Y, Zhong Z, Basin MV, Zhou D (2018) A descriptor system approach to stability and stabilization of discrete-time switched pwa systems. IEEE Trans Autom Control 63(10):3456–3463
Zhu Y, Zhong Z, Zheng WX, Zhou D (2018) Hmm-based h-infinity filtering for discrete-time markov jump LPV systems over unreliable communication channels. IEEE Trans Syst Man Cybern Syst 48(12):2035–2046
Scutari G, Facchinei F, Lampariello L, Song P (2014) Parallel and distributed methods for nonconvex Optimization-Part I: Theory. ArXiv e-prints
Grant M, Stephen B (2014) CVX: Matlab software for disciplined convex programming, version 2.1. http://cvxr.com/cvx
Chen J, Hu K, Wang Q, Sun Y, Shi Z, He S (2017) Narrowband internet of things Implementations and applications. IEEE Internet J 4(6):2309–2314
Bubeck S (May 2014) Convex Optimization: Algorithms and Complexity. ArXiv e-prints
Cao X, Xu J, Zhang R (2018) Mobile edge computing for cellular-connected uav: Computation offloading and trajectory optimization. In: 2018 IEEE 19th international workshop on signal processing advances in wireless communications (SPAWC), https://doi.org/10.1109/SPAWC.2018.8445936
Zhou F, Wu Y, Sun H, Chu Z (2018) Uav-enabled mobile edge computing: Offloading optimization and trajectory design. In: 2018 IEEE international conference on communications, ICC 2018, Kansas City, MO
Hua M, Huang Y, Yi W, Wu Q, Dai H, Yang L (2018) Energy optimization for cellular-connected multi-uav mobile edge computing systems with multi-access schemes. J Comm Inform Netw 3(4):33–44
Acknowledgments
This work is supported by the Natural Science Foundation of China (No. 61872104), the Natural Science Foundation of Heilongjiang Province in China (No. F201 6009), the Fundamental Research Fund for the Central Universities in China (No. HEUCF180602) and the National Science and Technology Major Project (No. 2016 ZX03001023-005).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: Special Issue on Networked Cyber-Physical Systems
Guest Editors: Heng Zhang, Mohammed Chadli, Zhiguo Shi, Yanzheng Zhu, and Zhaojian Li
A preliminary version of this work has been published in the 2018 IEEE 15th International Conference on Mobile Ad Hoc and Sensor Systems(MASS) [1].
Rights and permissions
About this article
Cite this article
Feng, G., Wang, C., Li, B. et al. UAV-assisted wireless relay networks for mobile offloading and trajectory optimization. Peer-to-Peer Netw. Appl. 12, 1820–1834 (2019). https://doi.org/10.1007/s12083-019-00793-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00793-5