Abstract
The interesting features of chaos theory are utilized now a day’s in information security. The simplest chaotic dynamical system is the double pendulum. Here in this article, two double pendulums are used to enhance the chaotic behavior of a dynamical system. This system is sensitive to initial conditions and bears complex and chaotic trajectory. Moreover, being multi dimensional system it endures grander solution space for the generation of large number of S-boxes. Furthermore, a permutation comprising on only two cycles of symmetric group of order 256 is applied to generate integer values for the construction of desired substitution box. The algebraic analysis of suggested S-box emphasis on its application, thereafter, an image is encrypted with the help of this S-box, whose statistical analysis validates its efficacy.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The exploration of chaotic systems started some 200 years ago. A system whose current state cannot be determined by initial conditions is known as chaotic system. The current state of the system is the consequence of the past initial conditions, medium of communication, the noise and external circumstances beyond the control of the observer. Hence randomness, ergodicity and sensitivity to initial conditions are ultimate topographies of chaotic system. These features attract cryptographers to use such system for secure communications of media using cryptographic algorithms. The purpose of cryptography in secure transmission is to convert valuable and meaningfull messages into the bogus ones. Such targets are achieved specifically in symmetric key cryptography and assymetric key cryptography, the two main divisions of cryptography. This paper make use of symmetric key cryptography. These are further divided by gauging mode of applications like block ciphers and stream ciphers.
Block cryptosytem works by selecting blocks of input data for further application of cryptographic procedures. The two main objectives of block cryotograms are to induce confusion and diffusion in the plain-text message. This was the idea introduced by Shannon [1]. Diffusion is attained by distorting the statistical configuration i.e. the original bits are scattered in cipher text. While confusion is achieved by modification of original bits. These two are attained in many block cryptosystems by means of round repetition of an algorithm. The four steps of recent block cryptograms include permutation, substitution, addition of key and mixing [2,3,4,5].
The usage of chaotic systems in cryptography specifically in block cryptosystems like the case here in this article is due to the fact of their pecuiler behaviour. These systems exhibt random behaviour, unpredictability and sensitivity towards initial inputs and parameters [6, 7]. An assaulter can not predict the chaotic system and the results obtained from this without having the knowledge of initial conditions. Chaotic dynamical systems are useful in the the design of cryptostem for acquiring confusion and dissusuion in the ciphered text. Henceforth, chaos is getting place in recent cryptosystem [8,9,10,11,12].
Secure communication using wireless channels is mandatory since cryptanalysts are always in line to extract the vital information. Thus, use of cryptography is only way to tackle such situations. The main aim of cryptographic algorithms is to create ambiguity in the enciphered information which is achieved using substitution boxes. These are only nonlinear components of block ciphers generating pandemonium in cryptosystems. Many articles are available in literature to construct such non-linear components utilizing different algebraic and chaotic maps, some of them are listed here. [13,14,15,16,17,18], but the chaotic dynamical systems are utilized very often in the field of cryptography.
The motivation behind the utilization of chaotic dynamical systems like double pendulum in the design of cryptosystems is due to the fact of the unpredictability and complex behaviour of the system. These systems are governed by the differential equtions. A physical system is modelled initially by finding derivatives of the function. These systems are key sensitive i.e. for a different set of initial conditions and parameters, a totally dissimilar chaotic trajectory is obtained. Moreover, with the involvement of numerous equations and conditions, chaotic dynamical systems are having enriched key space as compared to one dimensional systems like [7, 10, 15, 16, 19].
2 Double Pendulum
The simplest chaotic dynamical system is double pendulum. Whenever initial angels are slightly changed, the bifurcation pattern of this system changes exponentially. Being sensitive to initial conditions, the chaotic dynamical system is found prolific in generating confusion and diffusion in the cryptosystem. In this article, two double pendulums having same inclinations initially are used to generate integer values to design the non-linear components of block cipher. The mathematical formulation of a double pendulum shown in Fig. 1 is explained as follow
where \(x_{1}\) and \(x_{2}\) are horizontal components and \(y_{1}\) and \(y_{2}\) are vertical components of masses \(m_{1}\) and \(m_{2 }\) respectively. Now the potential energy \(P\) for case of double pendulum is given as
And kinetic energy \(K\) is obtained by finding derivatives of Eqs. (1)–(4), we get
The Langrangian (L) of a system is defined as the difference of kinetic energy and potential energy, which, for the case of a double pendulum is
Then,
Since Langrangian of a system satisfies the Euler-Langrange differential equation
Substituting Eqs. (9) and (10) in above equation we get
Extracting \(\ddot{\varphi }_{1}\) from the above equ, we get:
Similarly, we can derive an equation using Euler–Langrange equation for \(\varphi_{2}\), which is as follow
Solving above two equations simultaneously to derive the following differential equations
Now replacing \(\varphi_{1} , \varphi_{2} , \ddot{\varphi }_{1} {\rm and} \, \ddot{\varphi }_{1}\) by \(\zeta_{1} , \zeta_{2} ,\zeta_{3} ,and \zeta_{4}\) respectively. Differentiation of these yields the following four first order differential equations after substituting \(\ddot{\varphi }_{1}\) and \(\ddot{\varphi }_{2}\):
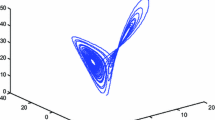
Solving the above four first order differential equations for two double pendulums in MATLAB for 50 s. The graph given in Fig. 2 depicts the chaotic nature of this dynamical system. The trajectories of two double pendulums are represented by colors in figure i.e. blue and red.
The initial inclinations of two double pendulums along with initial conditions of differential equations are responsible to determine the chaotic trajectory of dynamical system. A slight change in their values generate a different bifurcation pattern as demonstarted in Fig. 3. In other words, the solution space is sensitive to initial keys. This concept is very useful in cryptography for the generation of S-boxes. The robustness of the scheme based on such systems increases exponentially. For the case of two double pendulums, slight variation in initial parameters generated the following different bifurcation pattern. It implies that with theses values one can generate a totally different substitution box. Hence the suggested method is key sensitive.
The dominance of chaotic dynamical systems over low dimensional discrete chaotic systems is due to the fact that they have larger and complex solution space. Their larger key space and key sensitivity are also contributing in their supremacy. Moreover, chaotic range of continuous chaotic systems is bigger than discrete systems. Additionally, with the invention of modern computing devices, the chance of resistance attacks like brute force etc. are minimum for chaotic dynamical systems as compared to 1D and 2D systems.
3 Review of S-Boxes Connected to the Suggested Scheme
This section includes the contextual background regarding the suggested scheme. System of differential equations like Chaotic Lorenz system and Rabionvich–Fabrikant system is used by [13, 20, 21] to generate S-box. Khan et al. used multi chaotic systems for the construction of block cipher in [22]. The chaotic maps with improved chaotic range are utilized in [7] to synthesize nonlinear component of block cipher. The chaotic behavior of tent and sine maps are used to encipher the image by Zhou et al. in [5] and Attaullah et al. in [23]. Chaotic Gingerbreadman and symmetric group of order 8 was used for the design of an S-box in [24]. Authors used ABC optimization [25] and three dimensional baker maps for the production of S-boxes [17]. In [26] authors used the concept of coset diagram with bijecteive map and in [27] primitive irreducible polynomials over the field Z2 for the construction of S-boxes. There is enough relevant material available in literature for the construction of S-boxes based on chaotic maps [19, 28,29,30,31] but chaotic dynamical systems are less utilized in cybersecurity.
4 Construction of Substitution Box
The confidentiality in any cryptosystem is increased utilizing substitution boxes. We suggest a new scheme for the design of S-box based on chaotic dynamical system. The simplest chaotic dynamical system is double pendulum. Two double pendulums making an extreme chaotic trajectory are used to construct S-box in this scheme. The result analysis of nonlinearity, strict avalanche criterion (SAC), bit independence criterion (BIC) and linear and differential approximation probability validates the proficiency of the suggested S-box. Substitution box construction involves the following steps.
Initially, from the solution space of two double pendulums a chaotic sequence \(U\left( {1 \times 256} \right)\) of integers is generated using MATLAB.
Find the sequence \(V\left( {1 \times 256} \right)\) as follow.
$$V\left( i \right) = U\left( {256} \right) - U\left( i \right) 1 \le i \le 256$$Arranging \(V\left( i \right)\) in ascending order to obtain \(W\left( i \right)\).
After that each element of \(W\left( i \right)\) is replaced by its order in \(U\left( i \right)\) to obtain \(Z\left( i \right)\).
A new sequence \(Z^{\prime}\left( i \right)\) is obtained by the following relation
$$Z^{\prime}\left( i \right) = Z\left( 1 \right) - Z\left( i \right) 1 \le i \le 256$$Permuting the position of \(Z^{\prime}\left( i \right)\) with random permutation generated by MATLAB to obtain the \(16 \times 16\) matrix \(M_{16}\) given in Table 1.
Table 1 \(16 \times 16\) matrix In the last step, a permutation \(\mu\) from symmetric group \(S_{256}\), containing only two cycles, is utilized for permuting the entries of \(M_{16}\). This process leads us to obtain the desired substitution box given in Table 2.
$$\begin{aligned} & \mu = (0\; 125\; 171\; 106\; 242\; 81 \;164\; 217\; 138\; 244\; 187\; 201\; 13\; 224\; 253\; 226\; 41\; 50\; 216\; 129\; 20 \\ & 194 \;205 \;60\; 99\; 37\; 67\; 150 \;240 \;114\; 246\; 118\; 198\; 113\; 97\; 57\; 69\; 119\; 191\; 117\; 18\; 51\;1 \;64\; 94 \\ & 241\; 115\; 210\; 12\; 59\; 124\; 111\;131\; 74\; 228\; 248\; 123\; 31\; 104\; 245\; 25\; 102\; 86\; 10\; 32\; 197\; 44\; 128 \\ & 48\;239\;151\; 7\; 130\; 89\; 196\;168\; 229\; 8 \;172\; 93\; 61\; 126\; 52\; 178\; 160\; 193\; 180\; 73\; 146\; 225\; 66\; 170 \\ & 212\; 163\; 71\; 213\; 127\; 14 \;211 \;254\; 42\; 70\; 38\; 159\; 219\; 87\; 153\; 101\; 207\; 9\; 157\; 62\; 108\; 195\; 83 \\ & 47\; 223\; 218 \;182 \;252\; 133\; 92\; 88\; 165\; 96\; 147\; 58\; 17\; 177\; 214\; 39\; 233\; 121\; 43\; 166 \;189 \;215 \\ & 179\; 137\; 134\; 152\; 135\; 149\; 162\; 200\; 103) \;(2 \;155 \;255\; 91\; 227\; 26\; 95\; 145\; 183\; 65\; 192\; 105 \\ & 110\; 49\; 85\; 72\; 243\; 45\; 63\; 174\; 167\; 132\; 29\; 176\; 84\; 22\; 231\; 53\; 75\; 156\; 190\; 33\; 21\; 79\; 112\; 158 \\ & 140\; 36\; 15 \;186 \;181\; 208\; 238\; 30\; 78\; 5\; 175\; 230\; 169\; 6\; 54 \;209\; 202\; 40\; 204\; 188\; 247\; 251\; 142 \\ & 55 \;221\; 232\; 107\; 235\; 35\; 143\; 56\; 34\; 19\; 220\; 4 \;236\; 122\; 109\; 3\; 11\; 234\; 68\; 139\; 46\; 24\; 120\; 250 \\ & 27\; 206 \;185\; 154\; 249\; 80\; 100\; 77\; 28\; 16 \;90 \;237\; 136\; 161\; 76 \;199\; 148\; 184\; 173\; 23\; 82\; 116\; 144 \\ & 222\; 203\; 98\, 141) \\ \end{aligned}$$Table 2 Designed substitution box
4.1 Nonlinearity
It is the most imperative property of a cryptosystem. Principally, the nonlinearity of an outstanding cryptographic system is higher. It measures the confrontation of a system against linear cryptanalysis as given in Table 3. For a set of affine Boolean functions \(f_{j}\), the following equation describes the nonlinearity of a Boolean function \(v\):
4.2 Bit Independence Criterion
The statistical property of output bit independent criterion (BIC) for an S-box given by Webster and Tavares [32] is delineated as, for a certain collection of avalanche vectors, altogether the avalanche variables should be pairwise autonomous. This principle highlights the efficacy of confusion function. BIC values for the suggested S-box are tabultaed in Table 4.
4.3 Strict Avalanche Criterion
The Strict avalanche effect (SAC) introduced by Webster and Tavares in 1985, basically elaborates the generality of avalanche effect and completeness given in Table 5. It states that the chances of variation in output bits must by 0.5 for alteration of sole input bit. Mathematically, for
4.4 Linear Approximation Probability
The linear approximation probability (LAP) is used to measure the maximum amount of discrepancy of an event. For a set \(S\) containing total members \(2^{p}\) of possible input bits. If \(\tau_{i} \;and\; \tau_{o}\) are denoting input and output values respectively, then (LAP) values for the proposed S-box given in Table 6, is explained by the following equation:
4.5 Differential Approximation Probability
The differential homogeneity is an ultimate trait of a substitution box. The degree of a differential equality is also known as differential approximation probability. The corresponding values of DP are depicted in Table 7. Mathemaitcally, it is defined as follow:
5 Majority Logic Criterion
Majority logic criterion (MLC) is used to gauge the texture of an encrypted image after enciphering of an input image by an S-box. It includes the analyses like homogeneity, contrast, correlation, entropy and energy [33]. These analyses are used to establish the statistical strength of nonlinear component of block ciphers by measuring the amount of alterations occurred in an image after encryption. Some very brief details of these analysis are given hereafter.
5.1 Information Entropy Analysis
The rate of disorder in the cipher image gives the information entropy. The entropy for an image having total pixels \(N\) and the probability \(p\left( {u_{j} } \right)\) for the pixel \(u_{j}\) will be calculated by:
For a grayscale image, if \(p\left( {u_{j} } \right)\) of occurance for any pixel \(u_{j}\) is equal then the hypothetical value of entropy is 8. Hence, the information entropy for the suggested scheme should approximately be 8, to validate its efficacy. Table 7 compares the entropy outcomes for the suggested scheme with [4, 7, 34].
5.2 Correlation Analysis
The adjoining pixels (horizontally, vertically and diagonally) of the host image are highly correlated. A secure and robust encryption procedure make these adjacent pixels unrelated, i.e. the correlation of adjacent pixels approaches to zero of an enciphered image. The correlation for the neighbouring pixels \(r\) and \(s\) for a grayscale image is given by:
The outcomes generated by above relation are shown in Table 8. The correlation values of the processed image is almost zero as required.
5.3 Contrast, Homogeneity and Energy Analyses
An appropriate amount of brightness is present in the host image, which vanishes in the enciphered image. This loss is measured by the contrast analysis. The secure encryption yields the higher values of contrast for the encrypted image. Furthermore, the texture of an encrypted image is measured utilizing homogeneity and energy analysis (Figs. 4, 5).
6 Conclusion
To increase the vagueness of a cryptosystem, use of chaotic maps in the construction of a substitution box is a recent trend. In this paper, the simplest chaotic dynamical system i.e. double pendulum is used for the first time to generate integer values along with the application of symmetric group in construction of non-linear components of block cipher. The amalgamation of these two yields confusion and diffusion in the suggested cryptosystem. For a practical application, an image is encrypted afterwards with the designed S-box. The standard algebraic and statistical analyses available in literature validate the efficacy of the proposed system for the safe communication of data. Hence, designed chaotic S-box generated by means of chaotic dynamical system and symmetric group has the ability to become hurdle in the path of cryptanalysts.
References
Shannon, C. E. (1949). Communication theory of secrecy systems. Bell Systems Technical Journal,28, 656–715.
Kocarev, L. (2001). Chaos-based cryptography: A brief overview. IEEE Circuits and Systems Magazine,1, 6–21.
Dachselt, F., & Schwarz, W. (2001). Chaos and cryptography. IEEE Transactions on Circuits and Systems I: Fundamental Theory and Applications,48(12), 1498–1509.
Khan, M., Shah, T., & Batool, S. I. (2016). Construction of S-box based on chaotic Boolean functions and its application in image encryption. Neural Computing and Applications,27(3), 677–685.
Zhou, Y., Bao, L., & Chen, C. L. P. (2014). A new 1D chaotic system for image encryption. Signal Processing,97, 172–182.
Jakimoski, G., & Kocarev, L. (2001). Chaos and cryptography: Block encryption ciphers. IEEE Transactions on Circuits and Systems I: Fundamental Theory and Applications,48(2), 163–169.
Ullah, A., Jamal, S. S., & Shah, T. (2017). A novel construction of substitution box using a combination of chaotic maps with improved chaotic range. Nonlinear Dynamics. https://doi.org/10.1007/s11071-017-3409-1.
Li, X., Wang, L., Yan, Y., & Liu, P. (2016). An improvement color image encryption algorithm based on DNA operations and real and complex chaotic systems. Optik-International Journal for Light and Electron Optics,127(5), 2558–2565.
Hussain, I., Shah, T., & Gondal, M. A. (2012). A novel approach for designing substitution-boxes based on nonlinear chaotic algorithm. Nonlinear Dynamics,70(3), 1791–1794.
Khan, M., & Shah, T. (2014). A novel image encryption technique based on Henon chaotic map and S8 symmetric group. Neural Computing and Applications,25(7), 1717–1722.
Zhang, Y., & Xiao, D. (2014). Self-adaptive permutation and combined global diffusion or chaotic color image encryption. International Journal of Electronics and Communications,68(4), 361–368.
Zhang, W., Yu, H., Zhao, Y., & Zhu, Z. (2016). Image encryption based on three-dimensional bit matrix permutation. Signal Processing,118, 36–50.
Özkaynak, F., & Özer, A. B. (2010). A method for designing strong S-boxes based on chaotic Lorenz system. Physics Letters A,374(36), 3733–3738.
Brown, R., & Chua, L. O. (1996). Clarifying chaos: examples and counter examples. International Journal of Bifurcation and Chaos,6(2), 219–242.
Fridrich, J. (1998). Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos,8(6), 1259–1284.
Tang, G., Liao, X., & Chen, Y. (2005). A novel method for designing S-boxes based on chaotic maps. Chaos, Solitons & Fractals,23(2), 413–419.
Chen, G., Chen, Y., & Liao, X. (2007). An extended method for obtaining S-boxes based on 3-dimensional chaotic baker maps. Chaos, Solitons & Fractals,31(3), 571–579.
Arroyo, D., Diaz, J., & Rodriguez, F. B. (2013). Cryptanalysis of a one round chaos-based substitution permutation network. Signal Processing,93(5), 1358–1364.
Ullah, A., Javeed, A., & Shah, T. (2019). A scheme based on algebraic and chaotic structures for the construction of substitution box. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-019-07957-8.
Khan, M., Shah, T., Mahmood, H., Gondal, M. A., & Hussain, I. (2012). A novel technique for the construction of strong S-boxes based on chaotic Lorenz systems. Nonlinear Dynamics,70(3), 2303–2311.
Javeed, A., Shah, T., & Ullah, A. Design of an S-box using Rabinovich–Fabrikant system of differential equations perceiving third order nonlinearity. Multimedia Tools and Applications, https://doi.org/10.1007/s11042-019-08393-4.
Khan, M., Shah, T., Mahmood, H., & Gondal, M. A. (2013). An efficient method for the construction of block cipher with multi chaotic systems. Nonlinear Dynamics,71(3), 489–492.
Ullah, A., Jamal, S. S., & Shah, T. (2018). A novel scheme for image encryption using substitution box and chaotic system. Nonlinear Dynamics,91(1), 359–370.
Khan, M., & Asghar, Z. (2018). A novel construction of substitution box for image encryption applications with Gingerbreadman chaotic map and S8 permutation. Neural Comput & Applications,29(4), 993–999.
Ahmad, M., Doja, M. N., & Beg, M. M. S. (2018). ABC optimization based construction of strong substitution-boxes. Wireless Personal Communications,101(3), 1715–1729.
Razaq, A., Yousaf, A., Shuaib, U., Siddiqui, N., Ullah, A., & Waheed, A. (2017). A novel construction of substitution box involving coset diagram and a bijective map. Security and Communication Networks,2017, 5101934.
Shah, T., & Shah, D. (2019). Construction of highly nonlinear S-boxes for degree 8 primitive irreducible polynomials over Z2. Multimdeia Tools and Applications,78(2), 1219–1234.
Khan, M., & Munir, N. (2019). A novel Image encryption technique based on generalized advanced encryption standard based on field of any characteristic. Wireless and Personal Communication,109(2), 849–867.
Wang, X. Y., Feng, L., & Zhao, H. (2019). Fast image encryption algorithm based on parallel computing system. Information Sciences,486, 340–358.
Khan, M., Hussain, I., Jamal, S. S., & Amin, M. (2019). A privacy scheme for digital images based on quantum particles. Intrnational Journal of Theoretical Physics. https://doi.org/10.1007/s10773-019-04301-6.
Wang, X. Y., & Gao, S. (2020). Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. Information Sciences,507, 16–36.
Webster, A. F., & Tavares, S. (1986). On the design of S-boxes. In: Advances in cryptology: Proceedings of CRYPTO’85. Lecture Notes in Computer Science, pp. 523–534.
Hussain, I., Shah, T., Gondal, M. A., & Mahmood, H. (2012). Generalized majority logic criterion to analyze the statistical strength of S-boxes. Zeitschrift für Naturforschung A,67, 282–288.
Belazi, A., Khan, M., El-Latif, A. A., & Belghith, S. (2016). Efficient cryptosystem approaches: S-boxes and permutation–substitution-based encryption. Nonlinear Dynamics,87, 337–361.
Daemen, J., & Rijmen, V. (2002). The design of Rijndael-AES: The advanced encryption standard. Berlin: Springer.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Javeed, A., Shah, T. & Ullah, A. Construction of Non-linear Component of Block Cipher by Means of Chaotic Dynamical System and Symmetric Group. Wireless Pers Commun 112, 467–480 (2020). https://doi.org/10.1007/s11277-020-07052-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-020-07052-4