Abstract
VANETs are wireless sensor networks that suffer from the drawback of highly mobile nodes. The main objective of any type of network is to achieve efficient transmission goals. The vehicles act as the transmitting nodes. Cognitive radio technology helps in sensing the spectrum in order to ensure the efficient usage of the reserved channels by all the nodes. Our proposed system incorporates a routing protocol with the cognitive radio technology for efficient channel assignment. The routing protocol applies a tree based structure for efficient routing within and between networks. The tree routing protocol is further altered by the inclusion of an efficient optimized scheme. The proposed technique involves a Genetic Whale Optimization Algorithm which helps in choosing a root channel for transmission. When the selected root channel becomes active, the other channels are disabled. The proposed tree routing protocol is called the modified cognitive tree routing protocol (MCTRP).Apart from routing this protocol also caters to the need of effective channel utilization by allocating the spectrum fairly. This scheme results in ranking the channels based on their transmission efficiency and also aims to reduce the inherent delay usually associated with VANETs. The protocol also handles link breakages efficiently. The proposed scenario is simulated in NS2 and is evaluated based on the major network metrics. Our protocol shows a sharp decline in the associated delay and guarantees effective channel utilization. The proposed MCTRP method is effective over other protocols, such as, CTRP and OLSR. The analytical results show that MCTRP promises minimum overheads with effective channel utilization than the existing protocols.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Wireless communication has massively grown in today’s internet world in which wireless networks are used in a wide range of applications [1]. In fact wireless networks have come under the research area which concerns the efficient usage of the spectrum (licensed or unlicensed) Cognitive radio is a technique that tries to access the idle portions of a spectrum during a transmission overload. This helps in mitigating the traffic and reduces the heavy load in the network [2].The alterations of these parameters depends on the active monitoring factors such as the radio frequency spectrum, user activities, and network transitions. Cognitive Radio method was proposed by Joseph Mitola III and Gerald Q. Maguire [3]. It is the multichannel wireless network in which it uses sensor nodes dynamically to the available communication channel and uses the underutilized spectrum resources along time and frequency and gives an efficient dynamic spectrum access [4]. In CRN, the cognitive or the temporary users (known as Secondary Users-SU) are permitted to use the spectrum with the licensed users (Primary Users- PU), for achieving a good quality of service without interfering with the primary users [5]. When a SU wants to transmit data to a PU (who is currently not using the spectrum) and is allocated the frequency of the PU (to which the SU wishes to transmit), then the SU will scan for a separate frequency to transmit to that PU [6].The cognitive radios collaborate together to transmit their spectrum based decisions to a common node. Based on the information collected, the base station arrives at a decision regarding the usage of the spectrum. This scheme is known as cooperative spectrum sensing. This method is more powerful than other schemes because it overcomes the hidden terminal problem, which results when the PU is overshadowed by obstacles and the SU cannot detect it, thus causing a high interference with the PUs [7].The security aspect of this scheme concerns the successful fusion of data in the cognitive radio network [8]. The concatenated links between the nodes sometimes results in the deterioration of the network performance throughout [9].
Scheduling and allocation of the spectrum is difficult to handle because of the involvement of large number of users in a cognitive radio network. It will result in a high drop rate and degradation of the network performance [10]. These CRNs are capable of sensing environment in order to identify and locate the spectrum holes or white space, and adjusting their transmitting and receiving parameters for their transmission [11]. TCP/IP protocol stack is utilized by cognitive radio networks for the purpose of communication in the physical layer as well as the medium access control (MAC) layer [12]. The CR networks can manipulate their operating parameters to use the spectrum vacancies effectively. Opportunistic spectrum access (OSA) can overcome the various challenges related to spectrum scarcity and thus efficiently use the spectrum [13]. In CRSN, a multimedia and delay-sensitive application makes it easier to combine the low cost hardware and the sensor nodes as in wireless sensor networks [14]. This technology is highly useful in resolving the issue of underutilizing the spectrum and enables dynamic spectrum access (DSA) in wireless networks [15]. The CRSN may have several types of topologies because of their application dependent nature. Next generation sensor networks will definitely require Dynamic spectrum management which is an essential functionality of CRSN in order to employ adaptive allocation policies for the efficient use of the spectrum [16].
2 Related Works
Houaidia et al. [17], have discussed the problems associated with QoS in a heterogeneous single-radio single-channel multi rate wireless mesh network. The routing metric proposed helps in supplying information on the network parameters using the PHY and MAC characteristics. The metric also helps in reducing interferences between network transmissions as well as balancing the traffic on the links. The conflict graph model along with the maximum cliques helps in calculating the available bandwidth along a path including the nature of flow within each network. The proposed metric is compared with the existing metrics and the study is simulated to get a better understanding of the metric’s performance. The results of the proposed protocol (LARM) support network scalability with a high throughput and a limited delay. AL-Turjman [18] put forth a technique to handle data delivery in larger networks. This also helped in managing unforeseen disasters in the network. According to their proposed scheme, numerous wireless sensors are widely spread over the traffic infrastructure of a city (e.g. shopping arcades, parking lots etc.)This distribution framework is applicable in the Internet of Things (IoT). Relays are used to propagate data to a gateway attached to a larger network. Their paper takes into account the energy expended while the next hop node is being selected to forward the data to in a wireless network. Limitations involving resources such as hop count, energy etc. is considered in this approach. Simulative studies further emulate the effectiveness of the proposed approach. Cognitive radio (CR) is an effective technology which provides an effective solution for spectrum allocation problems. We can exploit the unused licensed bands to meet the increased demand on spectrum bands by applying CR technology. Hashem et al. [19], have developed an enhanced multi-hop multichannel tree routing protocol (EMM-TRP) for cognitive radio network and we contributed to the following: (1) The proposed an EMM-TRP that jointly utilized the tree routing algorithm with a spectrum management module in routing decisions. (2) It also proposed a new metric to find the best route (The main purpose for the design of this metric was safeguarding the PUs traffic from CR node interference and quick data transmission. (3) They have improved the EMM-TRP routing tree algorithm search by adding neighbor’s table technology. (4) Finally, it offered recovery and discovery unit in the case of link failure. Routing is a challenge in a wireless network. Several research papers have studied the problems involved in routing. A few of them have focused on hybrid routing mechanisms for MANETs.Walikar and Biradar [20] have given an overview on the analytical, network and simulation models involved in these hybrid routing mechanisms. This review classifies the hybrid routing mechanisms into four categories named as mesh, tree, zone, and multipath structure based on their relative performances. The paper also compares routing mechanisms based on their effective Routing policies, reliability in delivery efficiency, Packet delay, Packet delivery ratio, Control overheads, and quality of service (QoS). It provides an overview of a Reliable, Energy efficient, Scalable, Fault tolerant, and QoS based hybrid routing mechanisms and discusses varied ideas for future research and development.
Cognitive radio sensor networks (CRSNs) help [in setting up a reliable, robust, and efficient communication infrastructure which considers the existing as well as the future energy management requirements of a smart grid. The existing and future applications of CRSN-based smart grid include varied applications like substation automation, overhead transmission line monitoring, infrastructure metering, environment-aware routing, response to demand, outage management, distribution automation, and asset management. Fadel et al. [21], introduced honey bee mating optimization based outing and cooperative channel assignment algorithms have been proposed. The developed framework shows a significant decrease in packet loss and maintains a high link quality among the sensor nodes in a harsh smart grid spectrum environment. The proposed approach performance has been evaluated in terms of PDR, delay, and energy demonstrating its ability to address the QoS requirements of most of the SG applications presented. Sekhar et al. [22], have stressed on the increasing demand in a layman-friendly, efficient and computational effective vehicles. This has seen a surge in improving the internal designs of the vehicles in terms of deploying sensors, devices that enable communication and hardware that implement the concept of artificial intelligence. In fact communication enabled vehicular nodes are capable of providing service and entertainment. The aim is to enable the vehicles with resources capable of handling the users’ needs. These resources may range from the computing power to online connectivity. These resources can be commercially leased or loaned depending on the available requirements. The road side units (RSUs) are utilized by the vehicular nodes to communicate with the other vehicles. The RSUs are very useful while handling emergency situations since they enable communication between the vehicles. This helps news to propagate faster among the nodes and initiates faster action. The entire setup consists of a RSU, Additional coordinators for the RSUs along the way, vehicular nodes and a secure authority. This approach helps to mitigate the overheads involved in data transmission.
3 Problem Definition
Recent research has taken up communication among vehicular traffic for study. Communication is made possible among the vehicles with aid from sensors. Transmission of data in a VANET has to overcome numerous challenges and shortcomings. For instance,
The network channels have to be effectively assigned.
Resuming transmission even after link breakages.
Node mobility which poses an even greater challenge.
Route node discovery and root channel selection.
Tree Route node identification.
4 Proposed Methodology
Vehicular sensor networks (VSNs) can experience delay in getting emergency alerts due to various factors in the network. These factors include heavy traffic on the road with undue jams along the transmission routes. The existing wireless sensor network is designed using cognitive radio with OLSR protocol.
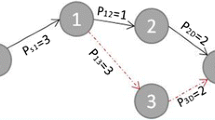
The OLSR protocol is modified by a hybrid GSO-GA algorithm for the selection of nodes. This method achieves better channel utilization capacity compared to other methods. Even though this method attains better channel utilization, it has a few drawbacks. In OLSR, when the number of mobile hosts increases then the overhead also increases. Also, it takes more time to discover the broken link. In order to overcome these drawbacks the proposed technique utilizes an effective routing protocol for cognitive radio based vehicular sensor network. A modified tree routing protocol for cognitive radio network (MCTRP) is used in this paper. The Tree routing protocol for cognitive radio network (CTRP) effectively coordinates between the tree routing module and channel assignment module. The traditional routing protocol is modified by means of an optimization technique. In our proposed method the root channel is optimally selected using GWOA. Based on that an effective root channel is selected for transmission and the other channels are switched to the disabled state. So that MCTRP routing protocol to efficiently manage spectrum allocation that helps reduce the routing delay and rank the channels available from end to end. And also our proposed routing protocol is efficiently deal with frequent link failure. The overall architecture is illustrated in Fig. 1.
Initially VSN is formulated based on the cognitive radio by means of modified tree routing protocol. Here the tree is built by configuring a base station as a tree root node. In our proposed method the root channel is optimally selected using genetic whale optimization algorithm (GWOA). Based on that effective root channel is selected for transmission. Finally, the data packets are transmitted from the source to the destination. The proposed modified tree routing protocol has three main phases such as,
Root node discovery phase.
Selection of root channel.
Root node identification and data transmission.
The step by step procedure of modified tree routing protocol for cognitive radio network (MCTRP) is described in Fig. 1. The below algorithm helps to identify the best node [23], which involve for efficient route discovery process.

4.1 Dynamic Root Node Discovery
In network topology, each node considers itself as the Root Node by setting the Root-ID value equals the Node-ID Value and set the sequence number as zero. In our proposed modified tree routing protocol, each node sends an advertisement packet to every node in the network by increasing the sequence number during every advertisement. After receiving the advertisement message, every node compares the sequence number and stores the sender id and then rebroadcasts the advertisement message to the other nodes. Then the node that has the highest sequence number value is selected as the root node. Otherwise, if the sequence number is equal then, the node compares the Root-ID value to its Root-ID. The nodes select a node that has the highest Node-ID as the root node. So the root election process is ended by selecting one node that has the highest sequence number value or the highest Node-ID as a Root node. After the root node selection procedure is finished, the selected root node becomes the only node which generates the advertisement message. Intermediate nodes in the tree branches rebroadcast advertisement message when received. Once the advertisement message is broadcast with the new Root-ID, the tree begins to grow. The process of the proposed advertisement message is shown in Fig. 2.
Once the nodes receive the advertisement message, they process the following steps,
First, the nodes check the sequence number value.
Second, if the nodes have a value greater than or equal than the one that is stored in their memory, they execute the remaining steps. Otherwise the nodes drop the message.
The proposed root identification process is illustrated in Fig. 3.

4.2 Selection of Root Channel
After waiting for other advertisement messages arriving from other channels, the node selects the best parent node with the best path metric to the root node through all selected root channels. In our proposed method the root channel is optimally selected using a Genetic Whale optimization algorithm (GWOA). The main objective of the proposed technique is to find the optimal channel with help of minimum cost value. The step by procedure of the algorithm is described in further section.
4.3 Genetic Whale Optimization Algorithm
4.3.1 Motivation
Whales are predators that never sleep. This is because of their need to breathe. Only one half of their brain sleeps. Hof and Van Der Gucht [24] state that certain brain cells in the whales resemble the cells found in humans. These cells are termed as spindle cells and these are responsible for the emotional and social behavior of human beings. These spindle cells are twice in number in a whale making them capable of emotions like humans. Though the smartness level of whales is lesser than humans, they can still think, judge, communicate and do other things like humans. In fact, killer whales even have their own dialect. Whales either live alone or in groups. Due to their social interaction most of the whales live in groups. Killer whales have been observed to live in a family for an entire life time. Figure 4a shows the picture of an adult humpback whale. Their favorite prey includes krill and small fish herds. They are known for their unique hunting method [25].They usually hunt the fishes nearer to the surface. These whales create bubbles along the surface in a distinct circular path as depicted in Fig. 4b. Tag sensors were utilized by Goldbogen et al. [26] in order to investigate the behavior of the humpback whales. The bubbles emanating from these whales exhibited either an” upward spiral” or a “double loop”. These behaviors are termed a maneuver. In fact, Goldbogen has derived these maneuvers in detail. There are two important phases in WOA. These two phases are termed as exploitation and exploration. Global search spans networks in search of an optimal solution (exploration) while exploitation refers to the local searches within the network [27].The searching technique of WOA is synonymous to the optimized hunting of the prey. This ultimately results in locating the optimum solution. The WOA algorithm starts out with a population of randomly generated set of solutions (the whales).Each of the generated point has a random positional point as well. The initial iteration a random search agent is selected based on which the other search agents update their positions. The procedure works differently for the second iteration wherein the search agents update their positions based on the best solution obtained. If the value obtained is |\(\vec{A}\)| > 1 then a random search agent is chosen and this results in exploration. When the value of |\(\vec{A}\)| < 1 it refers to the best solution. When all search agents tend to converge it initiates exploitation. WOA algorithm can be termed as a good optimizer meant to service global networks. The hunting pattern can be categorized into three major phases which involves searching for prey, encircling and the final phase of attacking the prey.
4.3.2 Mathematical Notation of Genetic Whale Optimization Algorithm (GWOA)
A genetic whale optimization algorithm (GWOA) is implemented in a problem independent (meta-heuristic) algorithm. The GWOA is formulated based on a bubble net hunting strategy. The algorithm mirrors the hunting behavior of the humpback whales. These whales use spiral shaped bubbles to follow and encircle their prey. We use a hybrid whale optimization crossover for an updated solution. The mathematical stage of GWOA is provided below.
Level 1 Initialization
The algorithm is established by arbitrarily generating an initial population that communicates to the result in the search space. The node value represents the random value, namely, wi (i = 1,2,3…n) where n indicates the number of nodes. The coefficient vectors of whale are initialized as a, \(\vec{A}\), \(\vec{C}\) and R.
Level 2 Fitness Calculation
The fitness is evaluated on the basis of the equation and the solution’s fitness value is calculated to get the best cost value. This is given by
Level 3 Update the position of current node value.
4.3.3 Encircling Prey
The nature of the humpback whales is such that they can locate the prey’s position and attack them by first encircling them. The location of the optimal design is not known within the search space. The best candidate in the solution set involves the prey (target) itself or is very near to the optimum value obtained in the GOA algorithm. When the optimal search agent is identified, the remaining search agents update their positions with reference to the best search agent.
The method for updation is given as follows.
where t—the current iteration, \(\vec{A}\) and \(\vec{C}\)—a Coefficient vector, \(w^{best}\)—a position vector for best solution, w—a current position Vector, | |—represents an absolute value.
The vectors \(\vec{A}\) and \(\vec{C}\) are calculated as follows:
where ‘a’ is linearly updated in the non-increasing order from two to zero. This is done over the course of a series of iterations involving both the exploration and the exploitation phases. ‘r’ is a random vector in (0, 1).
4.3.4 Bubble-Net Attacking Method (Exploitation Phase)
Three approaches can be adapted to model the bubble-net behavior of the humpback whales mathematically. They are
Shrinking encircling mechanism.
Spiral updating position.
Search for prey.
4.3.4.1 Shrinking Encircling Mechanism
This behavior can be achieved by decreasing the value of a in the equation.
The range of fluctuation of \(\vec{A}\) is further decreased by \(\vec{a}\). \(\vec{A}\) Thus is a random value given in the interval of [−a,a]. As stated earlier the value of ‘a’ is linearly updated in the non-increasing order. \(\vec{A}\) is allotted random values in the [−1,1] range. This helps in defining the current new position of the search agent between its original location and the location coordinates of the currently selected best agent.
4.3.4.2 Spiral Updating Position
The helix shaped movement of the humpback whale is depicted in a spiral equation created between the whale and its prey (as given in Eq. 6).
where \(D = \left| {w^{best} (t) - w(t)} \right|\)—The best optimal solution obtained, b—a constant that overrides the spiral shape, k—a random valued number between the [-1,1] range.
The humpback whales encircle the prey along spiral paths while moving in a shrinking circle [28–30]. We assume a fifty percent probability between these two motions of the whale. This helps in studying the simultaneous movement of the whales and also assists in updating the optimal position of the whales. The mathematical representation is illustrated as follows.
where R—a random number in the interval [0, 1].
The humpback whales search for prey randomly in addition to the bubble net method.
4.3.4.3 Search for Prey (Exploration Phase)
A variation of the \(\vec{A}\) can be utilized to explore the nodes. Humpbacks randomly search based on each of their position. Therefore \(\vec{A}\) is used with random values greater than or less than 1. This helps in forcing the search agent to move farther away from the whale used as reference. The position of the search agent is updated in the exploration phase with the help of a randomly chosen search agent. This scheme in addition to \(\left| {\vec{A}} \right| > 1\) lays emphasize on the exploration and helps the GWOA algorithm to carry out a global search. The mathematical model is represented in Eqs. 8 and 9.
where \(w_{rand}\) is a random position vector (a random whale/node) chosen from the current population. At every iteration, the search agents update their positions. This is carried out with respect to either a randomly chosen search agent or the best search agent thus obtained. The updation of the position can be done by genetic operations such as cross over and mutation.
Crossover operation
A crossover is a procedure of replacing one population by corresponding population of the other. Here, the crossover operator takes a pair of the population selected from the WOA operation. It the chooses a crossover point at random for each population, and then exchanges portions of their population based on the crossover point. Two point crossover methods are applied in this paper.
Mutation operation
Here in mutation process, the cross over solution is taken and that solution must be mutated. Here single point mutation is applied for mutation operation. Single point is choose and mutated with other point. ‘a’ is minimized from 2 to 0 in order to improve the exploration and the exploitation phases. When \(\left| {\vec{A}} \right| > 1\) a random search agent can be chosen. When \(\left| {\vec{A}} \right| < 1\) then a best solution can be selected in order to update the position of the search agent. The value of ‘R ‘decides whether the GWOA‘s movement is either spiral or circular in nature.
Step 4 Termination criteria
Repeat process, until a better fitness or maximum number of iterations are met. Based on the above procedure we select the optimal nodes and then these optimal nodes are preceded for Tree construction.
Pseudo - code for Efficient Genetic Whale Optimization Algorithm
k—the current iteration
\(\vec{A}\),\(\vec{C}\)—a Coefficient vector
‘wbest’—position vector of the best solution
‘w’—current position vector
R—random number in [0,1]
Max_IT—max_iterations
wrand—a random search agent

Based on that effective root channel is selected for transmission and the other channels are switched to disabled state. So that MCTRP routing protocol to efficiently manage spectrum allocation that helps reduce the routing delay and rank the channels available from end to end. The flow diagram of root channel selection is shown in Fig. 4.
5 Root Node Identification and Data Transmission
Root node has been identified and each node connects itself toward the root with single root channel which has the optimal path with minimum cost value. When a node receives a packet, the node checks the destination node within its neighbor table (Fig. 5). Each node keeps a neighbor table which contains all first one hop neighbors’ nodes. If the destination node is within its neighbor table the node forwards the message directly. Otherwise the node checks the destination node with the information in its routing table in order to forward the packet down to its children or up to its best parent node towards the root node. If any root channel fails, the proposed method selects the alternate root channel and transmits the packets to the destination. Hence by using MCTRP the vehicles reach the destination without any link failure problems. The performance of the proposed technique is evaluated in Sect. 6.

6 Result and Discussion
This section focuses on the results obtained by utilizing the proposed cognitive radio based vehicular sensor network using optimal tree routing protocol. The root channel is optimally selected by means of GWOA. NS2 is utilized for the implementation of the proposed method. The experimental yield along with the efficiency of the proposed method is clearly described as follows:
Network Simulator (NS-2) is utilized for performing the simulations. The MAC layer protocol utilized is IEEE 802.11. The data is transmitted at the rate of 50kbps in all simulations. The duration taken is 100 s. The total numbers of nodes used were 50, 75, 100, 125 and 150 with an area size of 1000 m × 1000 m. The propagation design used is a Two Ray Ground. Omni directional antenna type is preferred for data reception. In our simulation NS-2 constant bit-rate (CBR) traffic generator is used to set up the connection patterns with different random seeds. Each node has one CBR traffic connection with a unique destination. The transmission range is set to 100 m. The total packet size of data used in our simulation is 512 bytes. The source–destination pairs are spread arbitrarily over the network. The parameters used in the simulation are tabularized in Table 1.
6.1 Effectiveness of Proposed Technique
The effectiveness of the proposed technique is compared with the existing method. Here the analysis is performed by varying the numbers of nodes such as 50, 75, 100, 125 and 150. Our proposed method utilizes optimal tree routing protocol with the help of MCTRPGW. In order to prove the effectiveness of the proposed technique, we consider the existing method as a traditional tree routing protocol (CTRP) and an optimal link state routing protocol (OLSR). Figures 5, 6, 7, 8, 9 and 10 depicts the performance by varying the number of nodes with respect to delay, delivery ratio, drop, overhead, throughput and channel utilization efficiency. The graphical representation is shown below.
For 50 nodes the value of delay obtained using the proposed method is 4.19 s less than that of the existing method. Here the existing CTRP method obtained delay is 7.05 s and existing OLSR method obtained delay is 19.98 s. The delay obtained using the proposed method is 6.84 s less than that of the existing method for 75 nodes. For 100 nodes the delay obtained using the proposed method is 9.06 s but the existing CTRP method is 10.88 s and existing OLSR method is 20.96 s. The existing technique attains the maximum delay value when compared to the recommended technique. The delay value obtained using the proposed method is 6.41 s less than that of the existing CTRP and OLSR method for 125 nodes. For 150 nodes the delay value obtained using the proposed method is 7.103 s and the existing CTRP and OLSR method is 13.93 s and 18.04 s which is maximum value when compared to the proposed technique. The graphical representation of the packet delay values are plotted as follows,
From Fig. 6 it is clear that the delay value is more using the existing CTRP and OLSR method when compared to the proposed MCTRPGW method for varying number of nodes (Table 2).
For 50 nodes the delivery ratio obtained using the proposed method is 48.51% greater than that of the existing CTRP method and 53.78% higher than that of existing OLSR method (Fig. 7). The delivery ratio obtained using the proposed method is 46.01% and 69.57% greater than that of the existing CTRP and OLSR method for 75 nodes. For 100 nodes the delivery ratio obtained using the proposed method is 40.34% greater than that of the existing CTRP method and 45.06% higher than that of existing OLSR method. The delivery ratio obtained using the proposed method for 125 nodes is 48.072% and 62.4% higher than that of the existing CTRP and OLSR method. Similarly for 150 nodes the delivery ratio obtained using the proposed method is higher when compared to the existing method (Table 3).
Hence from the graph it is clear that the delivery ratio is high using the proposed method for varying nodes when compared to the existing method.
For 50 nodes the packet drop value obtained using the proposed method is 52% less than that of the existing CTRP method and 79.43% less than that of existing OLSR method. The packet drop value obtained using the proposed method is 51.7% and 77.83% less than that of the existing method for 75 nodes. For 100 nodes the packet drop value obtained using the proposed method is 37.7% less than that of the existing CTRP method and 51.3% less than that of OLSR method. The packet drop value obtained using the proposed method is 18.89% and 38.43% less than that of the existing CTRP and OLSR method for 125 nodes. Similarly for 150 nodes the value of packet drop using the proposed method is less when compared to the existing method. The graphical representation of the packet drop values are plotted as follows.
From Fig. 8 it is clear that the packet drop is more using the existing CTRP and OLSR method when compared to the proposed MCTRPGW method for varying number of nodes (Table 4).
For 50 nodes the overhead value obtained using the proposed method is 10,922 which is less than that of the traditional method (Fig. 9). The overhead value obtained using the proposed method is 13,029 less than that of the existing method for 75 nodes. For 100 nodes the overhead value obtained using traditional method is 30,995 and 33,445 which is maximum value when compared to the proposed technique. Here the recommended technique is attained the overhead value is 14,954. For 125 nodes, the overhead value obtained using the proposed method is 15,254 and the existing CTRP and OLSR method is attained 27,622 and 33,851. Similarly for 150 nodes the value of overhead using the proposed method is 15,517 less than that of the existing method (Table 5).
Hence from the graph it is clear that the overhead is minimum value using the proposed method for varying nodes when compared to the existing CTRP and OLSR method.
Table 6 shows the throughput comparison of the projected and available technique. Throughput is high for the projected method. For 50 nodes the throughput value obtained using the proposed method is 68,931 Kbps while using the existing CTRP and OLSR method the throughput value is 41,787 Kbps and 13,510 Kbps. 180,961 Kbps of throughput value is obtained using the proposed method for 75 nodes and 70,549 Kbps of throughput value is obtained using the existing CTRP method and 21,655 Kbps of throughput value is obtained using OLSR method. The value of throughput obtained using the proposed method is 208,104 Kbps using the proposed method while the value of throughput obtained using the existing method is 97,687 Kbps and 17,454 Kbps for 100 nodes. The throughput value for 125 nodes using the proposed and existing methods are 429,259 Kbps, 145,730 Kbps and 9462 Kbps. For 150 nodes the throughput value using the proposed method is 589,789 Kbps while using the existing method the throughput value is 221,035 Kbps and 15,951 Kbps respectively. Figure 10 indicates that by varying the number of nodes the throughput value obtained using the proposed MCTRPGW is greater than the throughput value obtained using the existing CTRP and OLSR.
Table 7 shows the channel utilization efficiency of the proposed technique is compared with the existing CTRP and OLSR method.
For 10 channels the channel utilization using the proposed method is 98% while using the existing method the channel utilization is 96% for both CTRP and OLSR. 93%, 88% and 83% of channel utilization is obtained using the proposed and existing CTRP and OLSR method for 20 channels. The value of channel utilization using the proposed and existing method is 87%, 81% and 78% for 30 channels (Table 7). For 40 channels the value of channel utilization is 80% using the proposed method and the value of channel utilization is 78% and 69% using the existing method. 79%, 76% and 67% of channel utilization value is obtained using the proposed and CTRP and OLSR method for 50 channels. The graphical representation of the proposed channel utilization efficiency is shown in below (Fig. 11).
Hence our proposed method has better channel utilization capacity then the existing CTRP and OLSR method. Hence from the above discussion it is clear that our proposed method has low delay, high delivery ratio, low packet drop and maximum throughput, minimum overhead and maximum channel utilization value when compared to the existing CTRP and OLSR method.
7 Conclusion
We have proposed a scheme where VANETs incorporate cognitive radio technology along with the MCTRP protocol. The MCTRP protocol in turn utilizes GWOA algorithm and the complete protocol is simulated using the NS2 platform. The proposed technique is evaluated using the network metrics such as
Delay.
Channel utilization.
Packet delay.
Network overheads.
Packet delivery ratio.
Overall throughput of the network.
These metrics assist us in comparing the MCTRP with GWOA (MCTRPGW) technique with other protocols like OLSR and CTRP. The evaluation is carried out by monitoring the performance of the proposed technique by minimizing and maximizing the number of nodes. This is done in order to study the performance of the protocol when
The traffic is minimum.
The traffic is maximum.
The node variations in the network give us a chance to evaluate the proposed protocol efficiently. When compared to CTRP and OLSR,the proposed MCTRP with GWOA exhibits better utilization of the network channel. In fact the channel is used up to its maximum capacity with almost minimal wastage of resources. The proposed MCTRP with GWOA exhibits
Minimal packet drop.
Maximum channel utilization.
Maximum PDR.
Reduced network overheads.
Minimal delay.
High throughput.
The effectiveness of the proposed technique is compared with traditional CTRP and OLSR routing protocol. Our proposed method has better channel utilization capacity of 86.6% then the existing CTRP and OLSR method. For further research we are planning to incorporate security measures into our technique in order to make it a complete protocol that caters to every need of the wireless sensor networks.
References
Jalil Piran, M., Cho, Y., Yun, J., Ali, A., & Suh, D. Y. (2014). Cognitive radio-based vehicular ad hoc and sensor networks. International Journal of Distributed Sensor Networks,10(8), 1–11.
Nassef, L., & Alhebshi, R. (2016). Secure spectrum sensing in cognitive radio sensor networks: A survey. International Journal of Computational Engineering Research (IJCER),6(3), 1–7.
Patel, J., & Thakkar, M. (2014). A survey on cognitive radio wireless sensor networks. International Journal of Engineering Development and Research, 1(3), 146–148.
Abolarinwa, J. A., Salawu. N., & Achonu. (2013). Cognitive radio-based wireless sensor networks as next generation sensor network: Concept, problems and prospects. Journal of Emerging Trends in Computing and Information Sciences,4(8), 146–148.
Qu, Y., Dong, C., Tang, S., Chen, C., Dai, H., Wang, H., et al. (2017). Opportunistic network coding for secondary users in cognitive radio networks. Ad Hoc Networks,56, 186–201.
Rao, K. L., Kalyana Chakravarthy, C., & Chilukuri, S. (2015). Energy efficient routing in cognitive radio networks: Challenges and existing solutions. Journal on Communication Technology: Special Issue,6, 1039–1052.
Mishra, P., & Dewangan, N. (2015). Survey on optimization methods for spectrum sensing in cognitive radio networks. International Journal of New Technology and Research,1(6), 23–28.
Wang, J., Chen, R., Tsai, J. J. P., & Wang, D.-C. (2018). Trust-based mechanism design for cooperative spectrum sensing in cognitive radio networks. Computer Communications,116, 90–100.
Singh, J. S. P., & Rai, M. K. (2017). CROP: Cognitive radio routing protocol for link quality channel diverse cognitive networks. Journal of Network and Computer Applications,104, 48–60.
Rathika, P. D., & Sophia, S. (2017). A distributed scheduling approach for QoS improvement in cognitive radio networks. Computers & Electrical Engineering,57, 186–198.
Ramzan, M. R., Nawaz, N., Ahmed, A., Naeem, M., Iqbal, M., & Anpalagan, A. (2017). Multi-objective optimization for spectrum sharing in cognitive radio networks: A review. Pervasive and Mobile Computing,41, 106–131.
Bouabdellah, M., Kaabouch, N., El Bouanani, F., & Ben-Azza, H. (2018). Network layer attacks and countermeasures in cognitive radio networks: A survey. Journal of Information Security and Applications,38, 40–49.
Ozger, M., & Akan. O.B. (2013). Event-driven spectrum-aware clustering in cognitive radio sensor networks. In Proceedings of INFOCOM (pp. 1483–1491).
Bicen, A. O., Cagri Gungor, V., & Akan, O. B. (2012). Delay-sensitive and multimedia communication in cognitive radio sensor networks. Ad Hoc Networks,10(5), 816–830.
Esmaeelzadeh, V., Hosseini, E. S., Berangi, R., & Akan, O. B. (2016). Modeling of rate-based congestion control schemes in cognitive radio sensor networks. Ad Hoc Networks,36, 177–188.
Kumbhar, S. V., & Durafe, A. (2015). Cognitive radio sensor network future of wireless sensor network. International Journal of Advanced Research in Computer and Communication Engineering,4(2), 492–495.
Houaidia, C., Idoudi, H., Van Den Bossche, A., Saidane, L. A., & Val, T. (2017). Inter-flow and intra-flow interference mitigation routing in wireless mesh networks. Computer Networks,120, 141–156.
Al-Turjman, F. (2017). Cognitive routing protocol for disaster-inspired internet of things. Future Generation Computer Systems,92, 2–21.
Hashem, M., Barakat, S. I., & AttaAlla, M. A. (2017). Enhanced tree routing protocols for multi-hop and multi-channel cognitive radio network (EMM-TRP). Journal of Network and computer applications,10, 1–19.
Walikar, G. A., & Biradar, R. C. (2017). A survey on hybrid routing mechanisms in mobile ad hoc networks. Journal of Network and Computer Applications,77, 48–63.
Fadel, E., Faheem, M., Gungor, V. C., Nassef, L., Akkari, N., Malik, M. G. A., et al. (2017). Spectrum-aware bio-inspired routing in cognitive radio sensor networks for smart grid applications. Computer Communications,101, 106–120.
Sekhar, R., Raja, K., Ravi Chandra, T. S., Pooja, S., & Tapaswi, S. (2016). Light weight security protocol for communications in vehicular networks. Wireless Networks,22(4), 1343–1353.
Sathiamoorthy, J., & Ramakrishnan, B. (2016). Energy and delay efficient dynamic cluster formation using improved ant colony optimization algorithm in EAACK MANETs. Wireless Personal Communications,95, 1531–1552.
Hof, P. R., & Van Der Gucht, E. (2007). Structure of the cerebral cortex of the humpback whale, Megaptera novaeangliae (Cetacea, Mysticeti, Balaenopteridae). The Anatomical Record,290, 1–31.
Watkins, W. A., & Schevill, W. E. (1989). Aerial observation of feeding behavior in four baleen whales: Eubalaena glacialis, Balaenoptera borealis, Megaptera novaean- gliae, and Balaenoptera physalus. Journal of Mammalogy,60, 155–163.
Goldbogen, J. A., Friedlaender, A. S., Calambokidis, J., Mckenna, M. F., Simon, M., & Nowacek, D. P. (2013). Integrative approaches to the study of baleen whale diving behavior, feeding performance, and foraging ecology. BioScience,63, 90–100.
Mirjalili, S., & Lewis, A. (2016). The whale optimization algorithm. Advances in Engineering Software,95, 51–67.
Harikarthik, S. K., Palanisamy, V., & Ramanathan, P. (2017). Optimal test suite selection in regression testing with testcase prioritization using modified ann and whale optimization algorithm. Cluster Computing. https://doi.org/10.1007/s10586-017-1401-7.
Ying, L., Zhou, Y., & Luo, Q. (2017). Lévy flight trajectory-based whale optimization algorithm for global optimization. IEEE Access,5, 6168–6186.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Mohanakrishnan, U., Ramakrishnan, B. MCTRP: An Energy Efficient Tree Routing Protocol for Vehicular Ad Hoc Network Using Genetic Whale Optimization Algorithm. Wireless Pers Commun 110, 185–206 (2020). https://doi.org/10.1007/s11277-019-06720-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06720-4