Abstract
The progression over wireless technologies paves the way for the emergence of wireless body area networks (WBAN) towards several motivating applications. Specifically, in terms of health concern applications, both the performance and reliability is regarded as the essential elements of WBANs. Many of the soft computational methodologies employed the manual modeling of fuzzy logic controllers (FLCs) by evolutionary algorithms in WBAN. This existing model encodes the entire control parameters of “FLCs” membership functions. This leads to the degradation of network performance by maximizing the latency. In order to rectify this issue, here we propose a hybrid firefly grey wolf optimizer (hybrid FGWO) approach for the optimal modeling of “FLC”. The major goal behind our proposed work relays on the optimal selection of control parameters from the “FLCs” with hybrid FGWO. The modeling of “FLCs” is carried out with CLFB (cross-layer fuzzy logic dependent back-off controller) mechanism to control the frequent access of channels. The efficiency of the “FLCs” model is enhanced by utilizing the coding technique known as unrestricted coding scheme. The performance of our hybrid FGWO approach is contrasted with three conventional “EAs”. Two major modeling goals are established whereas, the initial goal aims for the modeling of “FLCs” on particular configuration of network and the second goal aims on the modeling of “FLCs” over multiple network configurations. The “FLCs” modeled by means of our proposed hybrid FGWO approach exhibits its performance in terms of throughput, latency and packet delivery ratio with some of the challenging algorithms.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
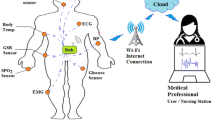
A wireless body area network (WBAN) specifically includes of the highly efficient as well as the sensor nodes with minimized power that can function closer to the human body in a wireless manner [1]. The WBANS can be placed on the human body or it can be implanted in order to detect the health status of human being’s by means of distinctive signals. The examples of such bio signals are EEG (Electroencephalography), HR (Heart Rate), BP (Blood Pressure) etc. The basic function of WBAN is to make the patient relieved from the pressure just by eliminating the wires, which makes a great threat to the people. The function of WBAN begins by gathering the essential information from the sensor nodes and transmitting it to the exterior medicinal health framework by means of a particular node referred to as coordinator. The coordinator is termed as a highly significant gadget similar to the ‘smart phone’.
The widely utilized standard over WBAN is IEEE 802.15.4 and this standard is particularly built towards the most significant devices. In order to ignore the collision occurrence in MAC (Medium Access Control) sub-layer it is being specified by the standard IEEE 802.15.4. The collision occurrence normally generates at the time the data packets are transmitted simultaneously by means of sensor nodes with the aid of channel assessment. The performances of IEEE 802.15.4 were determined by the previous authors and they stated that this standard faces the limitations of network reliability. Consequently, the reliability is estimated through \(P_{dr}\) (Packet delivery ratio) and the performance is estimated by means of throughput [2,3,4].
In order to deal with the above described drawbacks, more literal works [4,5,6,7] are being advanced prior for the enhancement of performance as well as reliability that corresponds to the standard IEEE 802.15.4. Moreover to the investigation, “FLCs” have been admitted to make use of the information about cross layer for the accurate channel scheduling approach. Consequently, “FLCs” efficient modeling turns to be important in the achievement of highly significant performance and reliability that corresponds to WBANs. Presently, the enhanced versions of WBANS performance completely depend on the man-made applications to model “FLCs” in error prone manner [3, 8, 9]. For this reason, we studied the benefits behind the automatic techniques to generate the organized modeling of “FLCs” against WBANs.
In addition to the above delineated drawbacks, our proposed hybrid FGWO have the benefits of translucent equilibrium, yet they possess the ability to function with distinctive sorts of fuzzy rules in the automatic modeling of “FLCs” [10]. Thus to generate effective “FLCs” model by hybrid FGWO, we make use of three technical issues. For the generation of efficient “FLCs” model, we, in turn, carried out the experimentation with the “URCS” coding technique utilizing multiple constraint degrees. Our experimental analysis ensures that the coding technique with minimized constraints can enhance the WBANs performance. The next subsequent issue aims for the modeling of fitness function in order to regulate the procedures of evolutionary computation in more convenient manner. The major concern behind our work is to enhance \(P_{dr}\) (Packet delivery ratio) it means reliability, latency and the throughput performance. Throughout this work, it is well known that the throughput can be attained just by the enhancement of \(P_{dr}\). But by the enhancement of \(P_{dr}\) spontaneously it maximizes the latency in the transmission of packets. The main perspective is to follow the \(P_{dr}\) as the major concern and the latency as one of the restriction.
Related to our research, if it experiences latency in the transmission of packets based on the “FLCs” candidates, yet it is better as similar to the standard IEEE 802.15.4, then we focused on the enhancement of \(P_{dr}\) by the fitness function. Alternatively, if it experiences corrosion over the latency contrasted to the IEEE 802.15.4, here the penalization is carried out for the fitness function, thus to maintain better equilibrium among latency and \(P_{dr}\). The third concern is to focus on distinctive modeling goals of “FLC” over WBAN. In this work, two basic modeling goals are defined. The initial goal is the optimal modeling of “FLCs” in order to maintain the performance and reliability in terms of particular network setting against WBAN. The next subsequent goal is the optimal modeling of “FLCs” in terms of various network configurations.
The short contributions behind this work are organized as follows:
-
Here we present a hybrid FGWO approach for the optimal modeling of “FLC” with optimal control parameters selection.
-
Fitness function influences are keenly investigated for the strong maintenance of equilibrium among performance and reliability of networks.
-
The experimental validation is carried out with distinctive two goals, which aims for the optimal modeling of “FLC with specific and multiple configurations of network.
-
The efficiency of the proposed hybrid FGWO approach utilizing “URCS” coding technique is evaluated with three conventional “Evolutionary Algorithms” namely (firefly, GWO and PSO). From the analysis it is inferred that our proposed hybrid FGWO algorithm shows better performance than the other three conventional “EAs”.
-
The performance analysis is also carried out with several challenging algorithms such as IEEE 802.15.4, D2MAC, ACS, and NB-Step stated in [7] and from the experimental outcome it is possible to identify that our proposed hybrid FGWO approach exhibits better performance in terms throughput, collision, latency and \(P_{dr}\) (packet delivery ratio).
The residual part of this paper is structured as follows: Sect. 2 provides the review of the literal works. The zone 3 provides the background study of the algorithms. The advantageous behind “FLCs” modeling are portrayed in zone 4. Section 5 describes the proposed hybrid FGWO dependent “FLCs” modeling against WBANs. Results behind this work are analyzed in zone 6. This paper gets completed up with zone 7.
2 Review of Related Works
Various standards were proposed for the WBANs functions, the examples for such standards are IEEE 802.15.6 and standard IEEE 802.15.4. Several investigations have been carried out by the researches in order to improve the functionalities of IEEE 802.15.6 just by yielding the WBANs energy which is portrayed in [10,11,12,13]. Additionally, Ibarra et al. [14, 15] established the control technique by means of three modules in order to attain the efficient Qos services by making use of the optimized energy. The similar researches in [16] also introduced HEHMAC (Human Energy Harvesting MAC). The functionality of this methodology is to prioritize the sensor nodes depending upon their functions. Particularly, the sensor nodes which makes use of the polling applications is regarded as the highly prioritized data and it can access the data in contention-free manner.
Furthermore, the node that functions with normal prioritized data utilizes the contention dependent mechanisms. Consequently, the WBANs in turn access of the standard IEEE 802.15.4 than the standard IEEE 802.15.6 according to [1, 17]. Moreover, the standard IEEE 802.15.4 demands for the commonly known application referred to as CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) in order to prioritize the parallel access of channel [18].
Establishment of arbitral (random) BackoffDelay prior to the access of channel by means of carrier sense approach obtains the ability to attain the CA (Collision Avoidance) application. Specifically, the assessment of channel is in a busy state and then BackoffDelay is maximized with an exponential velocity. Thus the present transmission eliminates of the channel criteria over the standard IEEE 802.15.4 which utilizes the “CSMA/CA” applications. Depending upon these present channel criteria it unknowingly initiates the entire BackoffDelay procedures as an alternative of balancing the BackoffDelay. Since the assessment of channel remains to a busy state, and then the rate of collision is maximized in an exceeding manner. The spontaneous increase in the rate of collision results in the reduction of throughput.
In order to resolve this problem, various adjustments were established thus for the updation of the tremendous amount of BackoffDelay through a more convenient approach [19]. For instance, the application namely ECR (Enhanced Collision Resolution) have been depicted clearly in [19]. This technique converts of the “CSMA/CA” application to be effectively utilized over the busy state of the channel, hence the networks performance is decreased in the condition if the criteria of channel disrupt continuously. Thus to balance this fluctuated latency or delay, a technique referred to as ACS (Additional Carrier Sensing) is proposed by Wong et al. [20]. They, in turn, utilize of the additional assessment of channel prior to the maximization of BackoffDelay in order to gather huge information based on the condition of the channel. Therefore BackoffDelay is not being able to be administered depending upon the particular requirements of application over every sensor nodes. In order to cope with these drawbacks, the new path is provided by the cross-layer throughput the entire investigation [20].
The cross-layering frameworks [2, 6, 7] that relate to the soft computing methodology makes use of the specific fuzzy logic applications. Previous studies translucently explain about the mechanism of fuzzy logic in the management of cross layer control over assessment of channel due to its simplicity and flexibility [2, 3, 6, 7, 9]. This application is appropriate in the management of non-linear frameworks considering of various inputs that belong to the typical nature as well as to associate these inputs and outputs it defines few specific rules. We, in turn, proposed the CLFB (cross-layer fuzzy logic based back-off controller) [4] to control the assessment of channel. The “CLFB” makes use of the data rate applications as well as the busy rate of the channel for the generation of BackoffDelay. Regardless to the automatic modeling of “FLC” our simulative investigations demonstrate the performance of the “CLFB” with few challenging algorithms.
Clearly, an intense modeling of “FLCs” is necessary to provide flexible communication among WBANs [2,3,4, 6, 7]. Anyway, the literature study reveals the basic modeling issues behind WBANs which is not being entirely reported. Commonly, the authors completely relates the “FLCs” automatic modeling that demands for a tremendous amount of man-made mechanisms, but it couldn’t deliver any of the assurance for performance [2, 4, 6, 7]. In order to cope with these drawbacks, the WBANs entire modeling of “FLCs” has been investigated. Moreover to the comparison among these methods, our proposed hybrid FGWO based “EAs” have the benefits of translucent equilibrium, yet they possess the ability to function with distinctive sorts of fuzzy rules in the automatic modeling of “FLCs”. This depends on distinctive sorts of \(MF_{ns}\) as well as to the rule base frameworks [11].
In addition to this “EAs” the “Gradient-Free Optimizer” method [21] can be extensively applied to the issues of multimodal as well as to the noisy environment. The advantage behind this is due to the effective functions of WBANs it possess the ability to operate well in the multimodal and noisy environment [22]. Depending on the review of literature study, we are in need to investigate the effective modeling of “FLCS” that depends to the “EAs” towards the perspective of WBANs. Various “EAs” includes the algorithms namely GA (genetic algorithm [8, 23], DE (differential evolutionary) [11, 12], firefly algorithm [24] and PSO (particle swarm optimization) [10, 25]. These “EAs” turns to be an effective application for the modeling of “FLCs”. Table 1 provides the summarization of few recent investigation works. For instance, Bingul et al. [10] modeled the Gaussian \(MF_{ns}\) by means of PSO. Pishkenari et al. [12] utilized the GA and DE in terms of effective modeling of trapezoidal \(MF_{ns}\). Hachicha et al. [11] make use of the DE alone for the modeling of triangular \(MF_{ns}\).Two well known “EAs” namely GA as well as PSO is proposed by Martinez et al. [26] for the efficient modeling of \(MF_{ns}\). They, in turn, evaluate the benchmark issues and reported that the “EA” can outperform the GA. It should be noted that several authors focused only on the single objective to enhance the modeling of “FLCs” [10,11,12]. Moreover, Marinaki et al. [27] introduced various optimal tasks of PSO for the FLCs modeling to compute the issues of vibration management.
Looking into this strategy the similar authors established a novel multi-modeling technique referred to as DE [28]. The comparison is carried out with these similar approaches to evaluate its performance. In this work, we are in demand to increase the performance of EA dependent modeling. Towards this existing work, this research work focused on the modeling of single “FLC”. In because of this, it moves on to distinctive approaches. The proposed work aims for the significant \(P_{dr}\) (Packet delivery ratio) and minimized latency in the deliverance of packets as a major concern, the disruption in this constraint is ought to be fined (penalized) over the fitness function. Thus to resolve the difficulty in the modeling procedures, Nasseer et al. [25] introduced the triangular \(MF_{ns}\) in the reduction of search space by two optimal control parameters namely the width and center. More probably, Chang et al. [29] utilized the triangular \(MF_{ns}\) of the symmetric form for the search space reduction. Liu et al. [13] verified the basic issues as well as reported the investigation of linguistic modifiers group corresponding to the stable fuzzy rules in the “FLCs” effective modeling. By the condition, both the control parameters as well as the linguistic modifiers related to \(MF_{ns}\) are regarded and the complete pattern for the modeling of “FLCs” is introduced in [23]. Casillas et al. [23] conducted the experiments on linguistic modifiers and reported that it doesn’t violate the framework of “FLCs” thus it has the ability to regularize the interpretation.
Throughout the investigations, we take into account the odds of utilizing the linguistic modifiers during the modeling of “FLCs” over WBANs. Thus for the reduction of difficulties in the modeling procedures we just focused on the optimal determination of control parameters over \(MF_{ns}\) using hybrid FGWO. Thus the literal works [10,11,12, 23] aimed at the determination of other coding techniques. As a result, this suffers from the limitation over efficiency and reliability by the comparison of distinctive coding techniques. To recover this we move towards the investigation of “URCS” coding technique amended with multiple degrees of constraints. From the experimental outcome, it is inferred that the coding techniques with limited constraints exhibit good performance over WBANs. The acronyms utilized throughout this work are delineated in Table 2.
3 Background Informations of GWO and Firefly
3.1 Grey Wolf Optimization (GWO)
The GWO is termed as a geographically motivated optimization algorithm. The GWO algorithm [30], in turn, exhibits the hunting (chasing) characteristic that depends on the family of the grey wolf. Basically, the preference of grey wolves tends to be situated over the pack. The size of pack related to the grey wolves ranges to the limit of 5–12. They, in turn, dominate the social hierarchy in 4 degrees. Based on the levels of hierarchy, the finest (best) candidate of the grey wolf is known as \(\alpha\)-alpha it is termed as the top most leader of the pack of wolves. The next finest candidate referred to as \(\beta\)-beta is known as the second leader among the pack. If the topmost leader \(\alpha\) is absent, then the second leader \(\beta\) dominant the pack. The least ranked wolves are defined by means of \(\omega\)-omega. The function of \(\omega\) wolves is to permit other wolves to eat first and this stays at last. The wolves that are not being recognized as \(\beta\)-beta or \(\omega\)-omega wolf are declared as \(\delta\)-delta. The function of \(\delta\) wolves is to suggest \(\alpha\), \(\beta\) wolves but in turn, it possesses the leadership against \(\omega\) wolves situated over the pack [30]. The order of hierarchical leadership is presented below in Fig. 1.
The numerical pattern of GWO algorithm includes the stages tracing, prey encircles and prey attack [30]. The initial stage of chasing is prey encircling. The numerical evaluation for prey encircling is expressed below:
whereas the present iteration is denoted by \(\vec{G}\), and the coefficient vectors are termed as \(\vec{F}\) and \(\vec{H}\) the prey’s position vector is represented by \(\vec{Y}_{p}\), yet the grey wolf’s position vector is \(\vec{Y}\). The vectors \(\vec{F}\) and \(\vec{H}\) is expressed below
Hence \(\vec{k}\) is termed as variable, on the way of iteration it is decremented linearly from (2 to 0). The random vectors are expressed as \(\vec{R}_{1}\) and \(\vec{R}_{2}\). Depending on the random vectors \(\vec{R}_{1}\) and \(\vec{R}_{2}\) the position updation can be carried out randomly (arbitrarily) over the search domain [30, 31]. The hunting operation is normally done by means of the leader \(\alpha\), preceded by \(\beta\) and \(\delta\). The grey wolves chasing (hunting) characteristics can be stated numerically as:
whereas the initial three finest (best) solutions are being taken into account and the residual solutions are eliminated, hereby the average measure of 3 finest (best) solutions is provided by \(\vec{Y}\).The hunting process gets terminated only after prey attack, and prey should pause its movement. By the condition if \(\left| F \right| < 1\) the attacking process of prey is done by grey wolf, yet if \(\left| F \right| > 1\) after this they take a diversion from the prey and moves towards the finest (best) prey which is fitter one. Hereby, \(\vec{k}\) is denoted as linear variable and random vectors \(\vec{R}_{1}\) and \(\vec{R}_{2}\) are being chosen arbitrarily (randomly).
3.2 Firefly Algorithm
The establishment of firefly algorithm was carried out by Yang [32] thus it completely depends on the potential flashing behaviors of fireflies. The flashing behavior of fireflies can be defined by 3 conditions, they are as follows:
-
The entire fireflies are focused as unisex; therefore a single firefly gets attracted by another firefly without considering the gender.
-
Attractiveness is generally related to the brightness, in because of the characteristics of the fireflies that diminished brighter follows the highly brighter fireflies. Attractiveness is highly related to brightness, thus the following fireflies reduce their brightness in terms of increased distance. By chance, if any of the Fireflies doesn’t possess the brightness, then the Firefly begins to relocate in a random manner.
-
The firefly’s intensity or brightness is being gradually damaged or being identified by means of objective functions background that is ought to be evaluated (optimized).
More conveniently, the intensity of light is termed as \(L(z)\) that may change accordingly with the distance \(z\) in exponent form and is expressed as
The actual intensity of light is \(L_{0}\) and the coefficient of light absorption is \(\alpha\). The attractiveness of fireflies is largely related to the intensity of light obtained from the nearby fireflies, the firefly’s attractiveness can be defined as,
whereas \(\gamma_{0}\) is referred to as attractiveness over \(z = 0\). The significant point to be noted is that towards the function \(\alpha z^{2}\) the exponent is possible to be replaced with the exponent \(\alpha z^{k}\) if \(k > 0\).The measure of distance against two fireflies noted as \(g\) and \(h\), the “Cartesian Distance” is being determined to utilize Eq. (10)
whereas \(Y_{g,e}\) is referred to as the \(e{\text{th}}\) element related to the spatial coordinate of \(g{\text{th}}\) Firefly. The relocation of Firefly \(g\) towards the far brighter (more attractive) Firefly \(h\) is evaluated based on the Eq. (11):
The attraction of fireflies is defined in the second term and the randomization is defined in the third term, whereas the parameter of randomization is shown by the notation \(\beta_{1}\), the ‘random number generator’ is noted by the notation \(r_{and}\) which is being uniformly distributed over the limit [0–1].
4 System Model
4.1 Functions of FLC (“fuzzy logic controller”) on WBAN’s
The WBAN includes of various distinctive quick, well-enhanced sensor nodes with minimized consumption of power. Example for such type of minimized power consumed sensor nodes are ‘heart rate’, ‘glucose degree’, and ‘blood pressure’ sensors and these sensors, in turn, are administered to various positions of the human body. The WBAN includes of one of the particular node referred to as the coordinator [1], is well delineated into Fig. 2. This dominant coordinator node holds of the similar functions of a highly enhanced device known as PDA (personal digital assistant). The main function of the coordinator node is to receive the sensors information and to redirect this received information towards an exterior medicinal health framework.
Various studies demonstrate about the wireless channels eminence that the channels closer to the human body show low quality as well as it experiences link loss in an extreme manner [22]. The WBANs with low-quality channels may suffer from the transmission drops as well as it faces the reduced performance and reliability, which are regarded as chief elements in the applications of healthcare domain [4]. In order to tackle the uncertainty of the channels, the FLC is commonly employed over WBANs by considering a number of factors such as the requirements of application and condition of the channel. The next subpart 4.2 provides the IEEE 802.15.4 MAC layers overview. Under the Sect. 4.3 it explains about the introduction of CLFB (cross-layer fuzzy logic dependent back-off controller) [4] over the access of control channel. The observations recognized from this segment promote us to develop a hybrid FGWO based FLC model is planned to be projected under the Sect. 5.
4.2 Description of IEEE 802.15.4
This segment provides the complete illustration of IEEE 802.15.4 slots of MAC [33]. The CSMA/CA which is being slotted turns to be the main concern in the WBANs mode of communication as well as it functions on the “Back-off Period” (BP) unit time. Based on this mode of communication, each of the nodes is in demand to evaluate the channel prior to the occurrence of every transmission; it means to pay attention before the initiation of communication [22, 34,35,36]. In case, the transmission doesn’t begins at the time of channels idle state, the transmission is ought to be delayed in terms of the arbitral (random) interval known as “Back-off Delay”. Figure 3 delineates the flow description of both the CSMA/CA slots as well as the CLFB (for more reference took a glance over Sect. 4.3). The CLFB is allotted for the identification of “Back-off delay”, at the condition “FUZZYENABLE = True”, yet at the condition, “FUZZYENABLE = False” the CSMA/CA which is being slotted over IEEE 802.15.4 are administered.
The MAC (medium access control) is described with 3 specific variables over the slotted “CSMA/CA”:
-
Back-off exponent \(B_{{e_{x} }}\): \(B_{{e_{x} }}\) captures the amount of Back-off periods \((B_{ps} )\) in which a node should wait prior to each of channel estimation. The initial stage of “CSMA/CA” begins by initializing \(B_{{e_{x} }}\) to \(Mac_{\hbox{min} } B_{{e_{x} }} ( = 3)\). During the transmission process over the node, if a packet is in the ready state, then the “CSMA/CA” approach pushes of the node to eliminate the collision by permitting the node towards the Back-off meant for the arbitrary (random) delay. The arbitral (random) delay are being preferred in a uniform manner arbitrarily (randomly) at a limit of \([0,2^{{B_{{e_{x} }} }} - 1]\) is expressed underneath:
$$Backofftime = r_{and} (0,2^{{B_{{e_{x} }} }} - 1) \times B_{p}$$(12)Subsequent to the condition after the completion of Backofftime, yet the channel remains in the busy state then \(B_{{e_{x} }}\) should be added with one, till it attains \(Mac_{\hbox{max} } B_{{e_{x} }}\)(the measure in default is setup to 5 towards the valid limit of [2, 3…8]). After this, the measure that relates to \(B_{{e_{x} }}\) is capped next to \(Mac_{\hbox{max} } B_{{e_{x} }}\).
-
Contention window \(Cw\): \(Cw\) represents the count of Backoffperiods demanded by the channel for the clarity prior to the initiation of each and every process of transmission. The term \(Cw\) should be initiated by means of \(Cw_{0} ( = 2).\) Then this initialized measure is ought to be retuned to \(Cw_{0}\), at the criteria if the channel is recognized at the busy state. In case, if it is recognized as clear, then \(Cw\) should be decreased with one. This process is continued till \(Cw\) attains the level zero, only after this process the transmission of data begins.
-
Count of Back-offs \(CB\): \(CB\) estimates the amount of Backoff trials practiced in terms of the present transmission trials. The term Count of Backoffs should be initiated to zero \(CB = 0\), in terms of any occurrence of novel transmission. By chance if any of the channels is reviewed in the busy state then \(CB\) should be added with one. At this criteria the algorithm discourage the permission of \(CB\) to go beyond the limit of \(Mac_{\hbox{max} } B_{{e_{x} }}\)(= 4). If the algorithm courage’s \(CB\) to go beyond the limit \(CB = Mac_{\hbox{max} } B_{{e_{x} }}\) then the failure in transmission is identified, else the procedure Backoff trials are continued.
4.3 Mechanisms of CLFB (Cross Layer Back-Off) Utilizing Fuzzy Logic
At the time of BackoffDelay adjustment the IEEE 802.15.4 has no ability to take into account the particular requirements of application; example for this is channel access frequencies. Hence, IEEE 802.15.4 increments \(B_{{e_{x} }}\) potentially if the accessed channel is in busy state. The procedures are well delineated in Fig. 3. Figure 3 illustrates that each node rebuilds the entire process of Backoff by means of every novel transmission, apart from the particular requirements of application and present condition of the channel. As a result, nodes faces complexity in the adjustment of BackoffDelay rapidly, this leads to the momentous increase in the rate of the collision over WBANs [9, 37]. Consequently, the utility, as well as the reliability of channels, are influenced negatively. Thus to overcome this problem, we just established “CLFB” [4] in order to accomplish the BackoffDelay by balancing \(B_{{e_{x} }}\), which in turn relates to distinctive conditions of channel and requirements of the application. The FLC (fuzzy logic controller) is utilized by CLFB in order to tune \(B_{{e_{x} }}\) that relates to the present conditions of the network and to the application requirements. Thus to differentiate the term \(B_{{e_{x} }}\) identified by means of “FLC” mechanism administered in CLFB and also \(B_{{e_{x} }}\) over IEEE 802.15.4, the previous one is referred to as \(FuzzyB_{{e_{x} }}\) throughout this work. Accordingly, prior to the channel assessment in CLFB the arbitrary (random) BackoffDelay pursued along every node is expressed as follows:
Taking a glimpse over Fig. 4 the “FLC” mechanism administered to “CLFB” takes off two input variables known as \(CB_{Rt}\) (count of backoffs rate) and \(D_{Rt}\) (data rate), which is well illustrated in under beneath section.
4.3.1 Input and Output Variables of FLC
The initial input variable assigned to “FLC” over “CLFB” is termed as \(CB_{Rt}\). The term \(CB_{Rt}\) should be evaluated by means of the \(CB\) average measure relocating with a certain period (time).
whereas \(\gamma ,\;0 \le \gamma \le 1,\) is referred to as the factor of discount and \(CB_{fine}\) denotes the fine (penalty) allotted for the failure of each transmission. It is to be noted that the measure of \(\gamma\) must is assigned with a larger measure similar to 0.86 in order to obtain better performance [4]. By the condition, \(CB_{fine}\) is ought to be rigorously larger than \(Mac_{\hbox{max} } \,Backoffs\) based on our trials the penalty of \(CB\) is administered as \(CB_{fine} = 6\). Moreover, \(CB\) behaves as a straight forward indicator for the condition of channel over years, but if the condition of the channel is depreciated, then \(CB_{Rt}\) begins to grow spontaneously. Likewise, it gets decreased by further improvement in the channel conditions. Subsequently related to our prior research, four fuzzy degrees are fuzzified for \(CB_{Rt}\) they are Very low, moderate, high and very high [4].
Data rate \(D_{Rt}\) is noted as “FLC” 2nd inputted variable, which is shown in Fig. 4. As described in [4], in order to identify the appropriate BackoffDelay it is necessary to consider each sensor nodes \(D_{Rt}\). For the occasion, a node that possesses larger \(D_{Rt}\) leads to frequent access of channel, yet it must be assigned with corresponding larger delay thus to withstand the major collisions. The \(D_{Rt}\) within WBAN has the ability to change considerably over distinctive kinds of nodes. Thus to deal with distinctive settings of network, the normalization of \(D_{Rt}\) against “CLFB” is administered in the scope of about [1, 2, 3…. 100] [4]. The partitioning is carried out for normalized \(D_{Rt}\) into 4 distinctive degrees of fuzzy namely, very low, moderate, high and very high. The term \(FuzzyB_{{e_{x} }}\) is considered as the output for “FLC”. Thus to increase the accuracy level, the term \(FuzzyB_{{e_{x} }}\) is being partitioned up into 4 distinctive fuzzy degrees, denoted as \(E_{1} ,E_{2} ,E_{3}\) and \(E_{4}\).
Towards “FLC” the ‘Centre of Gravity’ is utilized for the de-fuzzification of \(FuzzyB_{{e_{x} }}\) to generate the crisp measure in Eq. (13). On behalf of efficiency and simplicity for the entire input and output variables of “FLC”, we make use of the membership function in triangular shape [6, 7]. Figure 5 delineates the example for such type of membership function. Throughout this entire work, the membership functions control parameters denoted as p, q and r are designed automatically by means of our proposed hybrid FGWO algorithm. By the proper implementation of this membership functions, it turns easy to control “FLCs” BackoffDelay (for more convenience see Sect. 4.3) as well as it attains better steadiness over performance and reliability of WBANs (go through the Sect. 5).
4.3.2 Rules of Fuzzy Logic
Here in this work, it includes 16 distinctive conditions (antecedents). The 16 distinctive antecedents are meant by 4 degrees of fuzzy \(CB_{Rt} \times\) 4 degrees of fuzzy \(D_{Rt}\). Subsequently, about 16 distinctive rules are being comprised in function of “FLC” administered over “CLFB”. Each rule of fuzzy pursue the general structure, which is delineated below:
The “CLFB” fuzzy rules summarizations are described in Table 3. The table shows that if \(CB_{Rt}\) is termed as Very Low then it demonstrates that busy state is not being experienced by the channel, to avoid the longer delays our “FLC” sets \(FuzzyB_{{e_{x} }}\) to \(E_{1}\), for instance, the rules of fuzzy \(RL^{(1)} ,RL^{(2)} ,and\;RL^{(3)}\) illustrated in Table 3. Moreover, the node that contributes large \(D_{Rt}\) aims to take into account the larger delays thus to shield it against from the blockage of Very Low \(D_{Rt}\) nodes, an example for this is \(RL^{(4)}\). In terms of the highly congested channel, it means that \(CB_{Rt}\) is at Moderate degree, at this stage our “FLC” generates reasonably higher \(FuzzyB_{{e_{x} }}\), an example for this is \(RL^{(5)} ,RL^{(6)} ,and\;RL^{(7)}\). Anyway, the nodes that experience very high \(D_{Rt}\) tends to achieve the longer delays, an example for this is \(RL^{(8)}\). This is due to the fact, nodes that experience larger \(D_{Rt}\) generate tremendous amount of packets as well as it achieves the channel in more frequent form. The occurrence of collisions in the packet can be diminished by accepting the longer delays. In addition to the criteria, that the channel turns to be highly congested (High) in order to diminish the collision occurrence the BackoffDelay established the rules of fuzzy, it means \(RL^{(9)} ,RL^{(10)} ,and\;RL^{(11)}\) turns to \(E_{3}\). However the node that experiences very high \(D_{Rt}\) tends to achieve the longer delays, it means \(E_{4}\). At last, if the utility of channel is very high then “FLC” in turn generates a longer delay \(E_{4}\), with respect to the input \(D_{Rt}\). One of the exceptional nodes that still attains the shorter delay, it means \(E_{3}\) by the node that experiences very low \(D_{Rt}\). Consequently, to describe the rules of fuzzy, we just go through two very low \(D_{Rt}\) sensor nodes over the network; the idle state of the channel is identified for the more frequent period. Related to \(RL^{(1)}\), \(FuzzyB_{{e_{x} }}\) tends to be shorter and each sensor node shows only minimized delay. Based on rules, \(RL^{(12)}\) and \(RL^{(16)}\) the \(FuzzyB_{{e_{x} }}\) remains Very High thus to eliminate the unimportant occurrence of collisions in terms of entire WBANs reliability.
5 Optimal Modeling of FLCs in WBANs by Proposed Hybrid FGWO
In this segment, we propose a hybrid Firefly and Grey Wolf Optimization (FGWO) algorithm to model the “FLCs” optimally in CLFB in order to acquire the enviable equilibrium between performance and reliability of WBANs. The extensive report maintained in the past research [11, 18,19,20,21], most of the Evolutionary Algorithm [EAs] were administered for the automatic modeling of “FLCs” by distinctive aspects. As delineated in Fig. 5, the main goal of this work is to optimize the control parameters of “FLCs” entire Membership Functions \(MF_{ns}\).
Specifically, based on the perspective of WBANs, we recognized some of the methodological issues related to the “FLC” modeling. The issues are being categorized into three forms namely, (a) encoding method (b) fitness derivation and (c) estimation technique. These issues are well described correspondingly to the upcoming sections. For the progression of our work, we preferred hybrid FGWO for the optimal modeling procedures of “FLC” due of their worthiness stated in [7, 10, 11, 25, 27, 29]. The preference for hybrid Firefly based Grey wolf Optimization (hybrid FGWO) is carried out owing to their familiarity, yet they do not override the odds of utilizing other ‘Evolutionary Algorithms’.
5.1 Encoding Method
Several “EAs” works mainly over the population of candidate solutions. Each and every specific ‘candidate solution’ presents an individual model of “FLC” and it works by following a particular coding technique. Thus the coding technique encodes each and every \(MF_{ns}\) (Membership Functions) entire control parameters by means of numbers in the form of real or by floating point vectors. Moving towards this vector, the control parameters separate groups are formed with dimensions of 3 successive numbers. For instance, take a glance over Fig. 6 in which the parameters initial group that in turn controlling initial \(MF_{n}\) is tinted in pink color. In because of the triangular \(MF_{ns}\) utilization, it follows the criteria that in any specific group \((p,q,r)\) the initial control parameter should be lesser than the parameter located in the intermediate position \((p < q)\). Similarly the intermediate control parameter should be lesser than the parameter located at the third position \((q < r)\). For the sake of clarity, the above-mentioned encoding method can be referred to as URCS (Unrestricted Coding Scheme). As delineated in Fig. 6 if “URCS” is being utilized the \(MF_{ns}\) domain has the ability to cover other \(MF_{ns}\) domain. It can be explained by means of Fig. 6, the membership function \(F_{1}\) domain tinted in pink color encompasses the other membership functions \(F_{2}\) and \(F_{3}\) domains entirely. The “URCS” coding technique is utilized by our proposed hybrid FGWO approach due its simplicity and is well suited for control parametric selection.
5.2 Fitness Derivation
The evaluation of fitness measure is to be carried out, thus for the maintenance of equilibrium among performance and reliability over WBANs. The term \(P_{dr}\) (Packet delivery ratio) is utilized for the estimation of reliability according to [5], which is derived entirely throughout the work. The term \(P_{dr}\) is defined as the proportion between the successful deliverance of packets towards coordinator to the amount of packets transmitted by entire sensor nodes which in turn related to the WBAN, the condition is provided underneath transparently:
Moreover, in the sense, if \(P_{dr}\) is in very high rate, then the critical data copes with reduced collision at the time of WBANs data transmission. In order to accomplish this collision reduction goal, the term \(P_{dr}\) is denoted as \(\nabla P_{dr}\).
whereas \(P_{{dr_{CLFB} }}\) and \(P_{{dr_{STD} }}\) denotes the “Packet delivery ratios” acquired by means of the utilization of both CLFB as well as IEEE 802.15.4 standard, correspondingly. In case, \(\nabla P_{dr} > 0\) then CLFB’s reliability is regarded as the better one than the reliability attained by IEEE 802.15.4. Beyond reliability, this turns to be largely enviable in the enhancement of WBAN’s performance. The assessment of performance is carried out by means two sorts of metrics, they are delay and throughput. Furthermore, the throughput enhancement is comprehended by the improvement of \(P_{dr}\). Hence, throughout this work, throughput is considered in an implicit manner. Accordingly, the major aim of this work depends on reduction of ‘packet latency’. The packet delay is denoted as \(\nabla_{latency}\) and it is expressed as,
The measure of \(\nabla_{latency}\) is maintained at 0. Moreover with Eq. (18), \(\nabla_{latency}\) shows the behavior in the constraint manner. If the delay experienced is in minimized form, the major goal of our implementation procedure mainly depends on the \(P_{dr}\) maximization. Based on the above-explained terms, \(\nabla P_{dr}\) represented in Eq. (17) is considered as the main term for the optimization as well as \(\nabla_{latency}\) represented in Eq. (18) functions as the constraint form in order to balance the delay attained through “FLC” over CLFB with challenge to IEEE 802.15.4. Accordingly, the fitness measure is computed as,
whereas \(\eta\) is considered as coefficient. For illustration, if \(P_{{dr_{CLFB} }} = 0.55\) and \(P_{{dr_{STD} }} = 0.80\), hereby by computation \(\nabla P_{dr} = 0.55 - 0.80 = - 0.25\). At this condition, if \(\nabla_{latency} = 0\) the measure of the fitness in Eq. (19) turns to be \(- 0.25\). From this it can be noted that the latency reduction attained by means of “FLC” is regarded as the better one similar to the standard IEEE 802.15.4 and \(P_{dr}\) is possible to be enhanced by not including any of the fine (penalty). This work mainly focused on the determination of appropriate coefficient thus to acquire the enviable trade-off among delay (latency) and \(P_{dr}\).
5.3 Estimation Technique
In this work, the estimation of fitness related to each of the candidate solutions are being coordinated by means of two distinctive design goals. The initial design goal \(G_{1}\) is applied for the modeling of “FLCs” that operates efficiently towards the particular network configuration. Example for this is the application that relates to healthcare examination, that means a old person after a long interval sent back to home subsequently from the recovery of cardiac surgery, followed by the per-fixed settings of WBAN with the inclusion of ‘ECG’ (Electrocardiogram) with 3 leads, namely the Blood Pressure (BP), Heart Rate (HR) sensors are in demand [38]. Consequently, we aimed for the enhancement of performance and reliability towards this specific configuration. The second goal \(G_{2}\) aims to operate frequently throughout various configurations (settings) of network. The goal \(G_{2}\) aims for the enrichment of “FLCs” general applications. Thus for the differentiation of modeling goals, each results related to the utilization of “CLFB” depending to the goals \(G_{1}\) and \(G_{2}\) are referred to as \(CLFBG_{1}\) and \(CLFBG_{2}\), correspondingly. Related to these design goals, two distinctive estimation techniques are considered. The initial technique estimates the candidate solution depending on the WBAN’s pre-defined individual measure. The next subsequent estimation technique makes use of various prefixed settings of WBAN just for the mutual computation of similar candidate solution. Comparatively on the second technique, the measured \(\nabla P_{dr}\) and \(\nabla_{latency}\) against various settings of network is used for the determination of candidate solutions fitness measure based on the Eqs. (17), (18) and (19). Each and every settings of network is ought to be verified for about 5 non-dependent executions in terms of both estimation techniques. For sake of clarity, please take a quick look on Sect. 4.
5.4 Optimal Control Parameters Selection by Hybrid-FGWO
The main goal behind our proposed approach relays on the optimal selection of control parameters related to entire \(MF_{ns}\) of the “FLC” model. Here in this work we just passed over hybrid FGWO (hybrid firefly grey wolf optimization) algorithm, in because of GWO constraint, which means the optimal position is being controlled by two selected constant variables. In order to overcome this drawback, we propose hybrid FGWO instead of conventional GWO. Based on the hybrid method, the GWO executes the optimal position of prey and at the same moment, optimal controlling parameters \(\vec{R}_{1}\) and \(\vec{R}_{2}\) are being selected by firefly operator. The basic inspiration behind proposed hybrid FGWO algorithm is to merge the benefits of firefly with the conventional GWO in order to withstand the GWO’s static issues. Hereby, the conventional GWO includes of the arbitral (random) control parameters selection namely the parameters \(\vec{R}_{1}\) and \(\vec{R}_{2}\), the local minimal issue emerges out due to these static control parameters. At this point, firefly is utilized to pick out the optimal control parameters in favor of GWO. The steps behind the control parameters selection by proposed hybrid FGWO algorithm is described below:
-
At the chasing (hunting) operation, prey encircling is carried out by grey wolves and the grey wolfs, in turn, confirms about the movement of prey (i.e. none of the prey is in moving condition). The prey encirclement operation can be performed by utilizing the Eqs. (1) and (2), here the firefly picks out the control parameters \(\vec{R}_{1}\) and \(\vec{R}_{2}\). When moving towards the conventional ‘firefly algorithm’ it is observed that the optimization methods are enacted by means of the attractiveness and intensity variations.
-
In proposed hybrid FGWO algorithm (Table 4) the entire \(MF_{ns}\) optimal control parameters selection is done by the subsequent strides: (i) Depending upon the fitness measure sorting and ranking of entire fireflies is carried out (ii) Finest (better) fitness value is being selected in terms of present generation or iteration and this selected fitness measure is ought to be replaced, only if it is inferred that the currently estimated fitness measure is better than the fitness measure acquired over previous generation (iteration), else maintain the previously generated fitness measure alone. The measure of intensity that corresponds to the Firefly acquired at the final cycle (trials) is considered as the optimal solution. The resultant output generated by means of firefly includes the optimal control measures. (iii) The intensity value of the firefly obtained at the end of the trials is the optimum best solution for the optimization problem. Here the output of Firefly algorithm consists of optimum control parameters. Figure 7 illustrates a flow chart of proposed hybrid FGWO approach.
6 Results and Discussion
This section describes about the WBANs simulation settings under Sect. 6.1, the parameters setting of proposed hybrid FGWO are described under Sect. 6.2. Finally, the results obtained by simulation are delineated in Sects. 6.4 and 6.5. The outcomes obtained from modeling of “FLCs” to attain the goal \(G_{1}\)(it means particular network management (settings) in FLCs) are described under Sect. 6.4. The simulation outcomes obtained by means of “FLCs” modeling over goal \(G_{2}\)(it means various network management (settings) in FLCs) is analyzed under Sect. 6.5. Initially under Sect. 6.4, to identify fitness functions appropriate coefficients in Eq. (19), we conducted experiments on 11 distinctive coefficients. After this evaluation, we move towards the specific investigations on “FLCs” efficiency by our proposed hybrid FGWO approach utilizing “URCS” coding technique with three conventional “evolutionary algorithms” (firefly, GWO and PSO), these conventional algorithms are used for comparison with our proposed hybrid approach due to its simplicity and efficiency in terms of effective modeling of “FLCs”. Based on the investigation, we inferred that our proposed hybrid FGWO approach outperforms other three conventional “EAs” in terms of significant \(P_{dr}\) and minimized latency. At last, from the wide-ranging simulation experiments, we finalized that our proposed hybrid FGWO in modeling of “FLC” also obtains the ability to override more of the challenging algorithms such as, IEEE 802.15.4, D2MAC, ACS, and NB-Step stated in [7]. Initially, under Sect. 6.5, we just illustrated various scenarios for modeling of “FLCs” automatically based on the goal \(G_{2}\).
6.1 WBANs Experimental Environment
For the simulation of WBAN, we, in turn, make use of the networking simulator “NS2” [39]. Subsequently, classical setup over the research [5] \(D_{Rt}\) is maximized about a rate of 250 kb/s along with 2.5 GHZ frequency. Based on our simulation, the deployment of entire sensor nodes is carried out in a random manner within the search space of \(3 \times 3m^{2}\) amended along with the individual coordinator of WBAN utilizing ‘star topology’. Correspondingly, the simulation time of network related to our experiment is about 500 s (simulation time should not be in higher form to vary our main identification). Here, we just utilized the model of ‘log-normal shadow’ the same as the channel design form. When contrasted to the modernized distributions of both “Rayleigh and Ricean” fading of about small scale are generated to WBANs conveniently by means of “log-normal shadowing” [35].
6.2 Parameter Settings of Hybrid FGWO
The main scope of our research is to demonstrate that our proposed hybrid FGWO algorithm works effectively on the “FLC” modeling approach. As a result, two familiar Conventional “EAs” namely “Firefly and Grey Wolf Optimizer” aided with standardized functions are used for the effective implementation of “FLC” modeling. For both the conventional Firefly and GWO approach, the size of the population is administered to 50, whereas, the maximum number of iterations or generations is employed to 100. Based on this setup, it is inferred that the hybrid FGWO is near to the convergence subsequent to 100 iterations, the same as shown in Fig. 8. Table 5 delineates the parameter settings of proposed hybrid FGWO.
In order to obtain the consistent outcomes, our proposed hybrid FGWO based on the same administrations is continually repeated for about 30 epochs considering distinctive initial seeds. Thus to gather reliable information about the distinctive differences in reliability and performance the “ANOVA” (Analysis of Variance) test is performed. Also, to determine the flexible distinction over reliability and performance two different analyses are executed namely the “t test” and “Tukey’s post hoc” experiment. From the analysis, it is inferred that our proposed FGWO exceeds the performance of the conventional Firefly and GWO algorithms.
6.3 Validation Metrics
The WBANs performance and reliability are compared quantitatively by means of four validation metrics, they are as follows:
-
Packet delivery ratio (\(P_{dr}\)) Proportion between the successful deliverance of packets towards coordinator to the amount of packets transmitted by entire sensor nodes as presented in Eq. (16).
-
The rate of collision The average collision occurrence of data packets towards the WBANs interaction (communication) channel.
-
Latency It is measured by means of the data packets arrival time to the coordinator. The latency in the arrival of data packets begins as soon as the frames of data come closer to the “MAC sub-layer”.
-
The throughput of MAC The successful deliverance of data frames to the “MAC sub-layer” transmitted by means of a communication channel.
Thus in terms of flexible judgment with few challenging algorithms, each of the challenging algorithms is ought to be executed for about 30 runs individually at the simulative environment. The results acquired for the performance and reliability are again utilized to distinguish the “FLCs” modeling intended by means of our proposed hybrid FGWO.
6.4 Modeling of FLCs with Goal \(G_{1}\)
The simulative environment of WBAN with a goal \(G_{1}\) is established in this sub-segment. After this, the flexibility of multiple coding techniques aided with hybrid FGWO for the modeling of “FLC” is examined. Subsequently, the wide-ranging coefficient influence namely \(\eta\) is investigated over the fitness measure in Eq. (19). At last, the “CLFBs” performance and reliability attained by means of “FLCs” modeling against this work are contrasted with few challenging algorithms.
6.4.1 Simulation Setup of Network with Goal \(G_{1}\)
The initial design goal \(G_{1}\) is applied for the modeling of “FLCs” that operates efficiently towards the particular network management. For instance, we just include the application that relates to healthcare examination, that means a old person after a long interval sent back to home subsequently from the recovery followed by certain procedures, such as per-fixed settings of WBAN by the inclusion of ‘ECG’ (“Electrocardiogram”) with 3 leads, namely the blood pressure (BP), heart rate (HR) sensors, EEG (“Electroencephalogram”), motion sensors, Rate of respiratory and a coordinator of ‘Smart-Phone’. The sensor nodes certain interactive (communication) features are discussed in the underneath Table 6.
6.4.2 Comparing Hybrid FGWO with the Conventional “Evolutionary Algorithms”
Utilizing the scenarios of WBAN we just portrayed the outcomes of hybrid FGWO obtained by means of “URCS” coding technique as well as with distinctive coefficients (i.e.\(\eta\)) are delineated in Table 7. Based on the outcomes, it is inferred that our proposed hybrid FGWO algorithm utilizing “URCS” coding technique shows better performance than the “EAs” namely Firefly, GWO and PSO in terms of both the \(P_{dr}\) and packet latency strategies. These two strategies are evidenced by well known test referred to as “One-Way ANOVA” and “Turkey’s post hoc”. For instance, if the measure of the coefficient \(\eta = 2\) as shown in Table 7, it is observed that the coding technique “URCS” utilized by our proposed hybrid FGWO maintains the highly reliable \(P_{dr}\) and appropriately diminished latency when contrasted it with the conventional “Evolutionary Algorithms”. Let us consider another instance \(\eta = 2.5\), the “URCS” coding technique with our proposed hybrid FGWO exhibits highly reliable \(P_{dr}\)(p measures < 0.0001) as well as diminished latency when contrasted to the other three “EAs” (Firefly, GWO and PSO)
The “FLCs” modeling examples of hybrid FGWO utilizing “URCS” coding technique are depicted in Fig. 9 correspondingly. The depiction in Fig. 9 shows that the domain related to individual \(MF_{n}\) of “URCS” has the ability to encompass entirely by means of other \(MF_{ns}\) domains. For instance, the \(MF_{ns}\) domain in terms of \(E_{2}\) contradicted in Fig. 9c is entirely encompassed with \(E_{3}\) domain related to the \(MF_{n}\). As a result, the “URCS” \(MF_{ns}\) in hybrid FGWO approach is possible to be classified in terms of both performance and reliability. Encompassing the Fuzzy partition [62] is another interpretation characteristic for “FLCs”. As tinted in Fig. 9b the \(MF_{ns}\) molded by means of “URCS” may ignore some of the essential data points. Expect the issues in interpretability; the outcomes demonstrated in Table 7 shows that the hybrid FGWO approach utilizing “URCS” performance turns to be good when contrasted to the performance of the conventional “EAs” (Firefly, GWO and PSO). Moreover, traditionally the performance is provided with higher priority also the interpretation necessity is also investigated. Practically, the hybrid FGWO approach with “URCS” can maintain the reliable pathway among the performance and reliability; this is well delineated in our simulative result. Besides, the implemented rules possess some of the recent WBANs information. The rules administered in Table 3 \(RL^{(1)} ,RL^{(2)} ,andRL^{(3)}\) expresses that prior to the transmission of packets the sensor node is not in a constraint to wait as much as the channel returns to an idle state (i.e. not in a busy state.
Thus for the better providence of performance and reliability equilibrium over the network, it is in demand for the identification of fitness functions Eq. (19) appropriate coefficients. As a result, the \(\nabla_{latency}\) different coefficients namely, \(\eta\) are being analyzed. From the description provided in Table 7, we obtain some of the identifications that the coefficient \(\eta\) with higher measure (i.e. \(\eta > 2.5)\) promotes higher concentration on our proposed hybrid FGWO for the reduction of packet latency to highly minimized level (this is not considered as an essential term). By the fact, \(P_{dr}\) appears to be more influenced if the measure of \(\eta\) turns to be small (example for this is \(\eta < 2.0)\). Moreover, we in turn, presented analysis by means of detached “One-Way ANOVA” against entire coefficients in terms of each and every illustrated coding technique. From the result it is verified that over the criteria \(\eta < 2.0\), \(CLFB_{{G_{1} }}\) shows gradual variation in latency. Notably, as delineated in Table 7, if the measure of coefficient \(\eta\) varies by means of 2.0–1.5, the latency gets increased with 0.038 scs. Conversely, if in turn, \(\eta > 2.0\) the latency variation is constantly lesser than 0.015 scs. As a result, two coefficients are chosen it means \(\eta = 2.0\) as well as \(\eta = 2.5\) all the way throughout the investigation. Thus, these two coefficients for convenience are demonstrated in bolded form over the Table 7, this, in turn, afforded a probable equilibrium over \(P_{dr}\) and latency.
6.4.3 Comparison Among Hybrid FGWO Dependent FLC Modeling (Goal \(G_{1}\)) and the Challenging Algorithms
Thus to determine the efficiency of “FLCs” automatic modeling, we distinguished it with some of the well known challenging algorithms namely, IEEE 802.15.4, D2MAC, ACS, and NB-Step. Table 8 demonstrated that the \(CLFB_{{G_{1} }}\) overrides some of the challenging algorithms IEEE 802.15.4, D2MAC, ACS, and NB-Step by means of \(P_{dr}\) and latency. The analysis technique namely “One-Way ANOVAs” provides considerable variations among them p measures < 0.0001. Thus the subsequent “Tukey’s post hoc” test also ensures our statement. Particularly, \(P_{dr}\) attained for \(CLFB_{{G_{1} }}\) is appreciably larger than the challenging algorithms IEEE 802.15.4, D2MAC, ACS, and NB-Step, not including any of the influence on latency. As illustrated in Sect. 6.4.2, another modeling goal is to enhance the throughput and this can be achieved with the improvement of \(P_{dr}\). Moreover, Table 8 also suggested the throughput of WBAN utilizing each of the challenging algorithms. The statistical test also ensures that the \(CLFB_{{G_{1} }}\) greatly attains larger throughput over the challenging algorithms. Hence, the rate of collision can be significantly diminished in \(CLFB_{{G_{1} }}\) by carrying out entire challenging algorithms comparison.
6.4.4 Summary
Related to this sub-segment, we in turn, achieved the efficient modeling of “FLCs” depending to the hybrid FGWO with goal \(G_{1}\). We further determined the efficiency of “FLCs” model with the “URCS” coding technique. From the analysis, we finalized that “URCS” coding technique utilized by our proposed FGWO approach in the modeling of “FLCs” outperforms other “Evolutionary Algorithms” performance (Firefly, GWO and PSO). Moreover, for the satisfaction of WBANs requirements of performance and reliability, it is necessary to employ the measure \(\eta = 2.5\) for the fitness evaluation. At last, we proved the \(CLFB_{{G_{1} }}\) efficiency in a statistical manner thus by distinguishing it with various challenging algorithms. From the statistical result, it is analyzed that the \(CLFB_{{G_{1} }}\) utilizing the sensor nodes maintains significant performance as well as reliability in contradiction with the challenging algorithms namely, ‘IEEE 802.15.4, D2MAC, ACS, and NB-Step. Anyway, once the modeling of \(CLFB_{{G_{1} }}\) is done, then it is possible to employ within each of the sensor nodes and it can be utilized towards distinctive applications of WBAN.
6.5 Modeling of FLCs Automatically with Goal \(G_{2}\)
Moving to this sub-segment it first explains about the simulative environment of WBAN in goal \(G_{2}\).Consequently, the proposed hybrid FGWO algorithms efficiency has been studied statistically with distinctive scenarios. At last, the \(CLFB_{{G_{2} }}\) performance and reliability is contrasted with distinctive challenging algorithms.
6.5.1 Simulative Environment of Network with Goal \(G_{2}\)
Modeling of “FLC” with a goal \(G_{2}\) couldn’t generate the proficient equilibrium by means of performance and reliability towards the extensive setting settings of WBAN. As a result delineated under Sect. 4.3, we in turn aimed for the modeling of “FLCs” depending on the goal \(G_{2}\), it means improving the reliability and performance towards various (multiple) settings of WBAN. Due to this fact, we constructed distinctive training as well as testing states. Specifically, training in a sense is put forward by means of five distinctive settings of the network, which is illustrated in Table 10. All over again each and every sensor nodes interaction features are recognized under Table 10. Moreover, Table 11 comprises entire testing states administered to this work. Subsequently, the “FLCs” models enhancement is tested by means of 8 distinctive sensors. The efficiency of each and every sensor is determined clearly on distinctive studies [5, 38]. Thus, for the determination of WBAN under high congestion (traffic load), about two sensors of ECG are employed over the testing condition 9 provided in Table 11.
6.5.2 Modeling of FLC Based on Hybrid FGWO
In the view of the fact, the Sect. 6.4 ensures that our proposed hybrid FGWO is highly significant in the effective modeling of “FLCs”. Consequently, the hybrid FGWO training and testing outcomes acquired in terms of “URCS” coding technique are illustrated in the Tables 9 and 10. Based on the results obtained, it is inferred that distinguishing the efficiency of proposed algorithm with distinctive scenarios in statistical form turns to be a tedious approach. Conversely, the training conditions with seven as well as eight, hybrid FGWO utilizing the coding technique “URCS” provides better performance, it means it delivers the enhanced \(P_{dr}\) amended with reduced latency. It is more essential to point out that the “FLCs” modeling computational time tends to be completely sensible; hence the “FLCs” design is possible to be utilized frequently on various applications of WBAN, as well as the networks efficiency is enhanced in a significant manner.
6.5.3 Comparison Among Hybrid FGWO Dependent FLC Modeling (Goal \(G_{2}\)) and the Challenging Algorithms
The \(CLFB_{{G_{2} }}\) on differentiating it against the challenging algorithms comprising of \(CLFB_{{G_{1} }}\) over testing the outcomes (refer to the Tables 11, 12, 13 and 14), we observed that \(CLFB_{{G_{2} }}\) has the ability to override the performance of IEEE 802.15.4 in terms of \(P_{dr}\) and latency. It can be explained in another form that the throughput and highly significant \(P_{dr}\) can be attained only by means of the algorithm \(CLFB_{{G_{2} }}\) than the altered algorithm IEEE 802.15.4. This is not only efficient in terms of IEEE 802.15.4 but also it overrides the other challenging algorithms in the way it promotes a highest significant level of reliability. The \(P_{dr}\) achieved is about 100% in the case if the network includes of the coordinator together with two nodes alone. The level of \(P_{dr}\) begins to reduce, if the congestion (traffic load) gets increased by the tremendous addition of sensor nodes. Table 11 illustrates that \(CLFB_{{G_{1} }}\), NB-Step and D2MAC attains larger \(P_{dr}\) than \(CLFB_{{G_{2} }}\) based on few conditions (example for this is conditions 3, 4 and 5). By prompting the larger back-offs, higher \(P_{dr}\) can be attained. Alternatively, from the outcome it is observed that \(CLFB_{{G_{2} }}\) turns to be highly flexible than the ACS and IEEE 802.15.4 not including any of the higher back-offs over the sensor nodes.
More probably, by maximizing the amount of nodes, the level of \(P_{dr}\) gets diminished over entire algorithms. The reduction in the level of \(P_{dr}\) is due to the maximized occurrence of collision in the network, which is delineated in Table 12. Furthermore, \(CLFB_{{G_{2} }}\) on contrasting with \(CLFB_{{G_{1} }}\), NB-Step and D2MAC,\(CLFB_{{G_{2} }}\) shows lesser rate of collision. They in turn admit more pressure on the sensor nodes just for maximizing the BackoffDelay in order to eliminate the occurrence of collisions. Hereby, without forfeiting any of the interaction (communication) latency, the \(CLFB_{{G_{2} }}\) exhibits better performance than ACS and IEEE 802.15.4 towards the rate of collision occurrence. Prior to the explanation, the throughput of the “MAC-sub layer” illustrated in Table 13 is enhanced just by maximizing the \(P_{dr}\) related to the WBANs. Hence \(CLFB_{{F_{1} }}\), NB-Step and D2MAC attains larger \(P_{dr}\) than \(CLFB_{{G_{2} }}\) based on few conditions related to throughput (example for this is conditions 3, 4 and 5). Alternatively, from the outcome, it is observed that \(CLFB_{{G_{2} }}\) turns to be highly flexible than ACS and IEEE 802.15.4 if the network includes in excess of two sensor nodes. Consequently, the outcomes of \(CLFB_{{G_{1} }}\), NB-Step and D2MAC may attain the larger throughput and \(P_{dr}\) against \(CLFB_{{G_{2} }}\), yet it permits the tremendous amount of packet latency, due to this function it turns to be less flexible in the applications of WBAN (i.e. for delay responsive). For instance, over the condition 7,\(CLFB_{{G_{1} }} ,\) NB-Step and D2MAC establishes larger latency than IEEE 802.15.4. Contrasting to the challenging algorithms in Table 14, \(CLFB_{{G_{2} }}\) obtains the ability to maintain its packet latency nearer to the IEEE 802.15.4 levels. Specifically, the analysis techniques namely, “ANOVA” and “Tukey’s post hoc” demonstrates that the latency attained by means of \(CLFB_{{G_{2} }}\) is complex to distinguish from ACS and IEEE 802.15.4. For the moment,\(CLFB_{{G_{2} }}\) has the ability to handle the consequently diminished latency than D2MAC, \(CLFB_{{G_{1} }}\) and NB-Step.
6.5.4 Summary
Related to this sub-segment, we, in turn, achieved the efficient modeling of “FLCs” depending on the goal \(G_{2}\) and based on our proposed hybrid FGWO. The basic strength of \(CLFB_{{G_{2} }}\) is revealed in our simulation outcomes, it means its efficiency. From the outcome, it is inferred that \(CLFB_{{G_{2} }}\) is regarded as the significant approach that can override the performance of IEEE 802.15.4 taking into account both the performance and reliability. In addition to its efficiency and its flexibility, \(CLFB_{{G_{2} }}\) also promotes basic applications. The basic applications here it means is the practical usage, the patients, in turn, can remove or fix the sensor nodes to his/her body, but the network stays to be stable and effectual.
7 Conclusion
In this paper, we proposed the hybrid FGWO algorithm for optimal modeling of “FLCs” over WBANs. The proposed work relays on the optimal selection of control parameters from the “FLCs” with hybrid FGWO. The modeling of FLC is done by utilizing the CLFB (“Cross-Layer Fuzzy logic dependent Back-off controller”) mechanism to control the frequent access of channels. By the optimal selection of control parameters the reliability and the performance can be achieved by minimizing the latency in the network. Thus “FLCs” are modeled optimally by means of our hybrid FGWO approach. The experimental analysis is carried out with three conventional “Evolutionary Algorithms” namely, Firefly, GWO and PSO, in order to derive the effectiveness of our proposed approach utilizing “URCS” coding technique. These three “EAs” are considered because of its simplicity and efficiency stated in [10, 27, 30]. From the evaluation we identified that our proposed hybrid FGWO utilizing “URCS’ coding technique promotes better \(P_{dr}\) (Packet delivery ratio) with minimized latency than the other conventional “EAs”. Moving towards the effectiveness of “FLCs”, two major modeling goals are established. The initial goal \(G_{1}\) aims for effective modeling of “FLCs”, it means \(CLFB_{{G_{1} }}\) attempts to promote better performance and reliability towards the particular configuration of WBAN. Meanwhile, the next subsequent goal \(G_{2}\) intends for the optimal modeling of “FLCs”, it means \(CLFB_{{F_{2} }}\) to function on multiple configurations of WBAN. In addition to this, we just proved that \(CLFB_{{G_{1} }}\) acquires the ability to attain significant performance and reliability than other challenging algorithms D2MAC, IEEE 802.15.4, ACS and NB-Step. Through experimentation, we ensured that the \(CLFB_{{G_{2} }}\) exhibits higher performance than IEEE 802.15.4in regards of packet latency as well as \(P_{dr}\) towards the extensive scope of interactive (communication) conditions. It is important to be noted that over the entire modeling procedures, we, in turn, established neither the probable variations nor the specific applications against IEEE 802.15.4. We have selected the fuzzy rules throughout this work for the modeling of “FLCs” because of its simplicity and easy computational techniques. After modeling of “FLCs” in CLFB by means of our proposed hybrid FGWO algorithm, it can be penetrated towards the sensor nodes if and only if they are in well-matched form against IEEE 802.15.4 not including any of the key variations. Our future scope is to attain the better interpretability by means of multi objective algorithm. In order to withstand our modeling issues, the advantages of EMO (Evolutionary Multi-Objective) algorithms can be applied. However, our work focused mainly on the CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) employed over IEEE 802.15.4. The WBANs reliability and performance, can be attained in highly effective manner just by interlinking the TDMA (Time Division Multiple Access) to the CSMA/CA approach. Therefore, to interlink both these approaches, we require the “FLCs” hierarchical modeling. In favor of this function, we aim to generate the novel modeling technique referred to as “co-operative co-evolution” technique in order to enhance the WBANs functionalities in practice.
References
Cavallari, R., Martelli, F., Rosini, R., Buratti, C., & Verdone, R. (2013). A survey on wireless body area networks: Technologies and design challenges. IEEE Communications Surveys Tutorials, 16(3), 1635–1657.
Otal, B., Alonso, L., & Verikoukis, C. (2010). Design and analysis of an energy-saving distributed MAC mechanism for wireless body sensor networks. EURASIP Journal on Wireless Communications and Networking, 27(4), 571407.
Alonso, J. M., Castiello, C., & Mencar, C. (2015). Interpretability of fuzzy systems, Current Research Trends and Prospects (pp. 219–237). Berlin: Springer.
Nekooei, S. M., Chen, G., & Rayudu, R. K. (2015) A fuzzy logic based cross-layer mechanism for medium access control in WBAN. In IEEE 26th annual international symposium on personal, indoor, and mobile radio communications (PIMRC) (pp. 1094–1099).
Otal, B., Alonso, L., & Verikoukis, C. (2009). Highly reliable energy-saving MAC for wireless body sensor networks in healthcare systems. IEEE Journal on Selected Areas in Communications, 27(4), 553565.
Mouzehkesh, N., Zia, T., Shafigh, S., & Zheng, L. (2013) D2MAC: Dynamic delayed medium access control (MAC) protocol with fuzzy technique for wireless body area networks. In IEEE international conference on body sensor networks (BSN) (pp. 1–6).
Chen, M., Zhu, X., & Zhu, H. (2013). Service adaptively medium access control algorithm based on fuzzy logical for energy harvesting wireless sensor networks. Journal of Networks, 9(9), 2336–2341.
Kim, J., Moon, Y., & Zeigler, B. (1995). Designing fuzzy net controllers using genetic algorithms. IEEE Control Systems, 15(3), 66–75.
Bradai, N., Fourati, L. C., & Kamoun, L. (2014). Investigation and performance analysis of fMACg protocols for fWBANg networks. Journal of Network and Computer Applications, 46, 362–373.
Bingul, Z., & Karahan, O. (2011). A fuzzy logic controller tuned with PSO for 2 DOF robot trajectory contro. Expert Systems with Applications, 38(1), 1017–1031.
Hachicha, N., Jarboui, B., & Siarry, P. (2011). A fuzzy logic control using a differential evolution algorithm aimed at modeling the financial market dynamics. Information Sciences, 181(1), 79–91.
Pishkenari, H. N., Mahboobi, S., & Alasty, A. (2011). Optimum synthesis of fuzzy logic controller for trajectory tracking by differential evolution. Scientia Iranica, 18(2), 261–267.
Liu, B. D., Chen, C. Y., & Tsao, J. Y. (2001). Design of adaptive fuzzy logic controller based on linguistic-hedge concepts and genetic algorithms. IEEE Transactions on Systems, Man, and Cybernetics, Part B: Cybernetics, 31(1), 32–53.
Ibarra, E., Antonopoulos, A., Kartsakli, E., Rodrigues, J. J. P. C., & Verikoukis, C. (2016). Qos-aware energy management in body sensor nodes powered by human energy harvesting. IEEE Sensors Journal, 16(2), 542–549.
Ibarra, E., Antonopoulos, A., Kartsakli, E., Rodrigues, J. J. P. C., & Verikoukis, C. (2014) Joint power-qos control scheme for energy harvesting body sensor nodes. In 2014 IEEE international conference on communications (ICC) (pp. 3511–3516).
Ibarra, E., Antonopoulos, A., Kartsakli, E., & Verikoukis, C. (2015). Heh-bmac: Hybrid polling mac protocol for WBANs operated by human energy harvesting. Telecommunication Systems, 58(2), 111–124.
Mouzehkesh, N., Zia, T., Shafigh, S., & Zheng, L. (2015). Dynamic backoff scheduling of low data rate applications in wireless body area networks. Wireless Networks, 21(8), 2571–2592.
IEEE Standard for local and metropolitan area networks-part 15.4. (2011). Low-rate wireless personal area networks (LR-WPANs), IEEE Std 802.15.4- 2011 (Revision of IEEE Std 802.15.4-2006) (pp. 1–314).
Ha, J. Y., Kim, T. H., Park, H. S., Choi, S., & Kwon, W. H. (2007). An enhanced CSMA-CA algorithm for IEEE 802.15.4 LR-WPANs. IEEE Communications Letters, 11(5), 461–463.
Wong, C. M., & Lee, B. H. (2012). An improvement of slotted CSMA/CA algorithm in IEEE 802.15.4 medium access layer. Wireless Personal Communications, 63(4), 807–822.
Espinosa, J., Vandewalle, J., & Wertz, V. (2005). Constructing fuzzy models from input-output data. In F. Logic (Ed.), Identification and predictive control, Advances in Industrial Control (pp. 21–58). London: Springer.
Mahmood, D., Khan, Z. A., Qasim, U., Umair Naru, M., Mukhtar, S., Akram, M. I., et al. (2014). Analyzing and evaluating contention access period of slotted CSMA/CA for IEEE802. 15.4. Procedia Computer Science, 34, 204–211.
Cassillas, J., Cordon, O., del Jesus, M., & Herrera, F. (2005). Genetic tuning of fuzzy rule deep structures preserving interpretability and its interaction with fuzzy rule set reduction. IEEE Transactions on Fuzzy Systems, 13(1), 13–29.
Sundararaj, V. (2016). An efficient threshold prediction scheme for wavelet based ECG signal noise reduction using variable step size firefly algorithm. International Journal of Intelligent Engineering and Systems, 9(3), 117–126.
Bachache, N., & Wen, J. (2013). Design fuzzy logic controller by particle swarm optimization for wind turbine. In Y. Tan, Y. Shi, & H. Mo (Eds.), Advances in swarm intelligence (Vol. 7928, pp. 152–159)., Lecture Notes in Computer Science Berlin: Springer.
Martinez-Soto, R, Castillo, O., Aguilar, L., & Melin, P. (2010). Fuzzy logic controllers optimization using genetic algorithms and particle swarm optimization. In Advances in soft computing, Lecture Notes in Computer Science, (Vol. 6438, pp. 475–486). Berlin: Springer.
Marinaki, M., Marinakis, Y., & Stavroulakis, G. (2011). Fuzzy control optimized by a multi-objective particle swarm optimization algorithm for vibration suppression of smart structures. Structural and Multidisciplinary Optimization, 43(1), 29–42.
Marinaki, M., Marinakis, Y., & Stavroulakis, G. E. (2015). Fuzzy control optimized by a multi-objective differential evolution algorithm for vibration suppression of smart structures. Computers and Structures, 147, 126–137.
Ching-Chang, W., Hou-Yi, W., & Shih-An, L. (2009). PSO-based motion fuzzy controller design for mobile robots. International Journal of Fuzzy Systems, 10(1), 284–292.
Mirjalili, S., Mirjalili, S. M., & Lewis, A. (2014). Grey wolf optimizer. Advances in Engineering Software, 69, 46–61.
Sahoo, A., & Chandra, S. (2017). Multi-objective grey wolf optimizer for improved cervix lesion classification. Applied Soft Computing, 52, 64–80.
Yang, X. S., & Deb, S. (2010). Eagle strategy using Levy walk and firefly algorithms for stochastic optimization. In J. R. Gonzalez et al. (Eds.), Nature inspired cooperative strategies for optimization (NISCO 2010), studies in computational intelligence (Vol. 284, pp. 101–111). Berlin: Springer.
Baykasoğlu, A., & Ozsoydan, F. B. (2014). An improved firefly algorithm for solving dynamic multidimensional knapsack problems. Expert Systems with Applications, 41, 3712–3725.
Rezaee, A. A., & Pasandideh, F. (2017). A fuzzy congestion control protocol based on active queue management in wireless sensor networks with medical applications. Wireless Personal Communications, pp. 1–28.
Collotta, M., Gentile, L., Pau, G., & Scata, G. (2014). Flexible IEEE 802.15. 4 deadline-aware scheduling for DPCSs using priority-based CSMA-CA. Computers in Industry, 65(8), 1181–1192.
Yasari, A. K. I, Latiff, L. A., Dziyaudin, D. A., Lilo, M. A., Aljeroudi, Y., & Atee, H. A. (2017) Flexible online multi-objective optimization framework for ISA100. 11a standard in beacon-enabled CSMA/CA mode. Computers & Electrical Engineering.
Zhou, J., Guo, A., Juan, X., & Steven, S. (2014). An optimal fuzzy control medium access in wireless body area networks. Neurocomputing, 142, 107–114.
Health informatics–PoC medical device communication–part 00101. (2008). Guide {guidelines for the use of RF wireless technology, IEEE Std 11073- 00101-2008 (2008) (pp. 1–99).
The Network Simulator version 2 (NS2). Home Page. http://www.isi.edu/nsnam/NS2/.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Banu, S.S., Baskaran, K. Hybrid FGWO Based FLCs Modeling for Performance Enhancement in Wireless Body Area Networks. Wireless Pers Commun 100, 1163–1199 (2018). https://doi.org/10.1007/s11277-018-5626-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5626-4