Abstract
This paper focuses on the event based investigations over different data dissemination routing protocols for highly dense wireless sensor networks. Initially for the wireless sensor network domain, we analyzed data dissemination flooding and gossiping routing protocols. We etude and exemplify our proposed model for data dissemination based evaluation with Delphi random generator distribution strategy. We calculated performance metrics as sense count, transmit count, receive count and receive redundant count. At the end, simulations analysis has been carried out to prove the validity of our designed scenario.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Recent advancement towards the minimization of microelectronics and mechanistic structures (MSME) led to battery based sensor nodes with intellection, infusion and processing capabilities [1, 2]. Wireless sensor networks innovated a new domain of application areas such as military navigation, artificial structural and weather monitoring system and target tracking system [3, 4]. Wireless sensor network constitutes a large number of tiny nodes deployed in ad-hoc fashion in order to accomplish a distributed sensing task by automatically configuring topology for communication and coordination with each other [5].
Other application areas of wireless sensor networks include remote monitoring [6, 7], feature capturing [8], joint line monitoring, inventory tracking, wild fire and health monitoring. Energy efficiency acts as an extremely important criterion in the performance determination of entire wireless sensor networks system. Wireless sensor nodes are battery operated which always remains typically a scarce and expensive resource. Hence, focus on energy efficient communication techniques remains indispensable for the enhancement of network life time in the wireless sensor network. In broadcasting communication technique, one node sends the packets to all the other nodes in the network. Many applications such as location identification, routes establishment and related queries use broadcasting or its variation. Broadcasting can be useful for finding the multiple path discoveries between nodes and route maintenance. One of the variations of broadcasting where each node retransmit packets when received for the first time. Resultant of flooding generates redundant transmission which leads to broadcast storm problem [9]. Minimizing the broadcasting overhead remains always on the top priority for the protocol designer for wireless sensor networks. In the literature, a number of proposals were given by different research groups. Centralized broadcasting approaches were presented in references [10–12]. To reduce redundant messages using neighborhood information in wireless ad-hoc networks, solution were proposed in references [13–18]. Efficient data dissemination remains the highest priority for the assessment of routing protocol in the wireless sensor network system. An optimal route surely enhances the performance of the overall system, but it may not be shortest. Packets delivered in duplicate to the destination result in more resources utilization and consume higher energy. Specifically in the case of bulky and disruptive environment, the track keeping on entire message becomes extremely difficult. Network size influences the performance of the entire operating environment when evaluating a specific routing protocol. The motto remains there to carefully investigate routing protocols and present an optimal resultant that can comply with the expected requirement without compromising any constraints. Therefore, a typical analysis should be required to access the scope of different data dissemination routing protocols for the wireless sensor networks.
Section 2 deals with surveys two data dissemination routing protocols for wireless sensor networks. Section 3 describes the meticulous design of our evolved scenario. Simulation consequences and some open problems are presented and discussed in Sect. 4. Finally, Sect. 5 concludes this paper followed by the references.
2 Data Dissemination Protocols with Related Prior Work
This section provides the background and related work on flooding and gossiping protocols with assumptions required for the designed framework for the later sections.
2.1 Data Dissemination Flooding Protocol
In this protocol, each node receives a packet broadcast up to maximum hop count threshold value provided it does not act as the packet destination. This methodology does not prescribe complex constraints like topology maintenance and route discovery in the network. Every node receives a packet and retransmits the same packet after caching the source identity and sequence number of the message to all of its neighbors and may results in propagation of various unnecessary routing messages. Three major loop holes with flooding protocol namely—implosion, overlap and resource blindness were identified by Heinzelman et al. [19]. A straightforward broadcast of packets become costly in terms of time and energy with the CSMA an implementation mechanism. Ni et al. [20] reported the seriousness of this broadcast storm problem consequences in redundancy, contention and collisions. Proposals for reducing the broadcast problem were reported by researchers in Ref. [20, 21]. Lot of energy gets wasted in contention and collision as proposals remain CSMA based. TDMA based MAC protocol INFUSE for data dissemination was proposed in Ref. [22]. It reduced energy and time taken for flooding but also considers implicit acknowledgment for lossy channels which result in extra energy consumption. Recently time synchronization through flooding has been bestowed due attention. Elson et al. [23] eliminated transmitter side non determinism. A hierarchical level structure was proposed in Ref. [24] where the root node initiates the control phase and the control messages relays from higher level to lower level nodes resulting in synchronization error reduction. Both the schemes reported in Ref. [23, 24] for large message exchange inherits synchronization error which results in data loss. Flooding time synchronization as a solution uses inherent broadcast property to synchronize several receivers as showed in Ref. [25]. Zeng et al. [26] invented a synchronization scheme based on TDMA to reduce energy consumption and proposes guidelines for size determination of synchronization frame. There can be wastage of time if the size of the frame remains too large or too small and also makes the calculation and reception computation complex. Shanti and Sahoo [27] investigated TDMA based protocol TREEFP where after topology information gathering, slots have been assigned without message passing and proved higher reliability as compared to Ref. [26]. As per the TREEFP requirement, each node should be aware about its position relative to the sink either by some localization algorithm or with nodes programming during the deployment time.
2.2 Data Dissemination Gossiping Protocol
A modified version of the flooding protocol refers to gossiping protocol, where the nodes send the packets to randomly selected neighbor but do not broadcast packets. As a resultant it avoids the problem of implosion, but on the other side a message takes more time to propagate throughout the network. Gossiping considerably lowers the flooding protocol overhead but does not guarantee about the message delivery to all nodes across the network. To eventually propagate the message gossiping protocol relies on the randomly selected neighbor. Recent researches suggested the significance of gossip protocols towards the engineering a new generation of monitoring systems incorporating criteria such as high scalability and fault tolerant [28]. Till date, however, no monitoring systems based on gossiping have been developed. Wuhib et al. [29] presented research work on gossip-based aggregation for real-time monitoring [30] and evaluated gossip-based monitoring against traditional tree-based monitoring. Gossip protocols also known as epidemic protocols, are actually based on round specific distributed algorithms. Each node selects a subset of other nodes to interact with in a round, whereby the selection function remains probabilistic. Nodes interact via “small” messages as reported in [28, 31, 32]. Initially Gossip protocols were proposed for the purpose of disseminating updates in large database systems [31]. More recently the scope of these protocols have enhanced for various other tasks such as robust overlays construction [33], network slicing [34], network size estimation [35] and network wide aggregates monitoring [30, 32]. In terms of Gossip bimodal behavior [36–40], Let p be the gossip probability and for sufficiently large graphs with fractions θ S(p) and θ R(p) arranged in such a manner the gossip quickly dies out in 1 − θ S(p) of the executions Almost in all of the fraction θ S(p) of the executions, a fraction θ R(p) of the nodes get the message if the gossip does not die out otherwise in many cases, θ R(p) remains close to 1.In case of pure gossip, a source sends the route request with probability 1 and when a node first receives a route request with probability p, it broadcasts the request with probability 1 − p to its neighbors provided it discards request; if the same request again received by the node. Initial condition shows the problem of very few neighbors. For the first k hops, we gossip with probability 1 and for k + 1 hops, the gossip probability is p. GOSSIP1 (1, 1) shows equivalent behavior to the flooding. GOSSIP1(p,1) represent equivalent behavior to pure GOSSIP1(p). if θ S0 (p) denotes well-defined probability and θ F0 (p) = Message reception probability and forwardness then following relation holds for gossip protocol θ S0 (p) = θ F0 (p) = def θ 0(p) provided θ S0 (p) < 1. We used gossip algorithm as an extension of the standard nearest-neighbor gossip reported by Boyd et al. [41] using mobility model in natural manner. In a graph G, each time agents move independently to new locations with random selection. For each time t = 1, 2… the following events occurred. Let i and j denotes agents, l i (t) denotes new location, μ i denotes mobility distribution, \( {\mathcal{N}}li\left( t \right) \) denotes a set, then following relation holds:
True average with probability greater than 1 − ϵ represented by following relation
where \( \left\| \cdot \right\| \) denotes the Euclidean norm. Denantes et al. [42] analyzed that bounds on the spectral gap yield an asymptotic deterministic rate of vanishing error. Authors in [43] analyzed bounds in a way that can be used to correlate both the rate of convergence in probability and averaging error which decays in exponential and asymptotic manner.
3 Proposed Evaluation Model
In this section, we present the investigation framework for data dissemination based on parameters namely—sense count, transmit count and receive redundant count in the highly dense wireless sensor networks. For this, we have developed a whole scenario focusing on three main targets. First, we are concerned with finding the number of node operations of our proposed framework. In other words, we want to find out the summation of operations in the entire model. Since our model has a strong basis on node operation counting, we considered that it would be also quite interesting to take care about the number of events in terms of specific protocols for the proposed model. Smaller number of node operation is always given due consideration as it consumes fewer resources. Finally, as a possible measure of the adaptability of our model, we made the inclusive evaluation of two data dissemination protocols in our proposed framework scenario. Table 1 displays the parameters in our proposal.
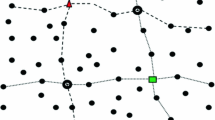
The simulations had the following structure. We launched our model with 10 numbers of events (i.e. each event request for a service 10 times with respect to number of nodes) over 500–2500 wireless sensor networks randomly generated with Delphi random generator distributions. The sensor field constitutes width and height 2000 m with an individual range of node and sensor 200 m. In the simulation model, value of sectoral sweeper coefficient and lobe count value remain 2 with beam angle 90 with counter clockwise direction of operation in the proposal. Figure 1 shows the set up of our simulation.
4 Results and Discussions
To evaluate the performance of our approach, we used an event driven wireless sensor network simulator SNetSim [44, 45] over Windows platform. It allows the researchers to simulate and represent random network distributions and provides statistics of different data dissemination policies including the provision for high density node environment. The proposed model was verified on two data dissemination protocols and we reported a comparative analysis over classical flooding and gossiping protocols. In the simulation, we collected data for three metrics namely sense count, transmit count and receive redundant count. Sense count metric exhibits the capability of a wireless sensor node to measure number of signals required for sensing operation whereas transmit count metric shows the number of signals required during transmission for a specified number of nodes present in the scenario. Receive redundant count metric reflects the number of fraudulent signals occurred during the overall communication.
Figure 2 indicates the comparative analysis of flooding and gossiping protocols based on events. Initially, we calculated sense count (SC), transmit count (TC) and receive redundant count (RRC) for 500 nodes. In case of flooding protocols, sense count operation shows incremental behavior as compare to gossiping protocol which consumes less sense count operations. As far as transmit count operation concerns, flooding protocol exhibits zigzag behavior but the gossiping protocol shows continuous growth with respect to the increment of the number of events. For receive redundant count operation, gossip protocol outperforms than flooding protocols. This shows the good agreement with the results reported in Ref. [46]. A typical comparative investigation over broadcast protocol for sensor network and ad-hoc broadcast protocol for 100 nodes networks was reported by Arjan et al. [46]. We enhanced the contribution to a certain extent by incorporating highly dense wireless sensor networks where the node value ranges from 500 to 2500.
Figure 3 reflects approximately similar behavior provided the comparison lies for 1000 nodes resulting in more number of operations in the scenario with respect to the number of events. Node scalability affects all the three metrics operations.
Sense count operation in flooding protocol changes its value to more than three times, when compared with gossiping protocol. In case of transmit count, number of operations from the first event to the last event varies from 999 to 1709 in flooding protocol whereas the value enhanced ten times in case of gossiping i.e. from 2000 to 20,000. The SC flooding has high value of node operation in case of receive redundant count for flooding still i.e. 89,406–153,316 whereas for gossiping it lies in between 1256 and 19,002 operations. Moving ahead towards further comparative evaluation, an analysis of flooding and gossiping protocol for 1500 and 2000 nodes is illustrated in the Figs. 4 and 5. The operations for sense count metrics remains less than flooding in gossiping protocol at the first event and exceed than flooding protocol for the last events for both the cases of 1500 and 2000 nodes. In flooding protocol number of operation for transmit count decreases with increase in the number of events with respect to scalability. More number of nodes, lesser will mean the difference corresponds to operations value. On the other hand, gossiping shows precipitous increase in its value of operations corresponds to the events value increment. With the increase in number of nodes, the value to receive redundant count metric increases in case of flooding protocol and decreases for gossiping protocol.
Finally, we evaluated our proposed model for highly dense wireless sensor network with 2500 nodes as showed in Fig. 6. Each node requests for a service correspond to each event and sequence continues for all the nodes residing in the network. Sense count metric requires more number of operations in flooding protocol than gossiping protocol. Transmit count operations vary in a steadfast manner in gossiping protocol than flooding protocol. There remains very superior number of receive redundant count operations in flooding protocol than gossiping protocol. This reflects that gossiping protocol is more robust than flooding protocol even in the highly dense wireless sensor networks.
Arjan et al. [46] reported only the performance evaluation of broadcast protocol for wireless sensor network and ad-hoc broadcast protocol with 100 numbers of nodes. We have extended the concept towards more scalability and robustness. Harshavardhan et al. [46] explored classical flooding, modified flooding and location aided flooding up to 1000 nodes. We extended this concept of Ref. [47] for flooding and gossiping protocol. Verma et al. [48] presented scalability analysis of AODV routing protocol in wireless sensor networks. Here we further enhanced the concept towards more rigorous analysis of highly dense wireless sensor networks. Our analysis shows that gossiping protocols consumes less number of resources and more efficient as compared to flooding protocol with respect to the number of events. The summarized evaluation of node operation for flooding and gossiping protocols confirming our arguments stated as below in Table 2.
5 Conclusion and Future Work
Wireless sensor networks have proved to be a novel and innovative research field of work in the last few years. We have evaluated a highly dense WSN framework which implements two data dissemination routing protocols with respect to performance metrics: sense count, transmit count and receive redundant count. We estimated flooding and gossiping protocol specifically for node operations with reference to the number of events. The goodness of the routing protocols changes along with the number of nodes and event present in the scenario. Here, first time works focused toward the comparative analysis of highly dense WSN routing protocols. We reported preliminary simulation demonstration our proposed scenario. Our research on wireless sensor network assessment continues along specified directions. The current state of art in these models, a number of aspects like sense count, transmit count, and receive redundant count have been identified and analyzed. We investigated towards the implementation and assessment of these models in our proposed scenario. The resultants show that gossiping protocol performance overweighs flooding protocols in highly dense wireless sensor networks in all the cases node count operation from an efficiency viewpoint. Future work can be focused on three major aspects viz enhancement, restructuring and extending the experiments carried out to demonstrate accuracy of our proposed model. Finally, we expect this work seems to a benchmark for designer for enhanced evaluation.
References
Estrin, D., Govindan, R., Heidemann, J., & Kumar, S. (1999). Next century challenges: Mobile networking for smart dust. In Proceedings of ACM conference mobile computing and networking, pp. 271–278.
Pottie, G. J., & Kaiser, W. (2000). Wireless sensor networks. Communications of ACM, 43, 51–58.
Haas, Z. J., & Small, T. (2006). A new networking model for biological applications of ad hoc sensor networks. IEEE/ACM Transactions on Networking, 14(1), 27–40.
Brooks, R. R., Ramanathan, P., & Sayeed, A. A. (2003). Distributed target classification and tracking in sensor networks. Proceedings of the IEEE, 91, 1163–1171.
Estrin, D., & Cerpa, A. (2004). ASCENT: Adaptive self-configurable sensor networks topologies. IEEE Transactions on Mobile Computing, 3(3), 272–285.
Clouqueur, T., Saluja, K. K., & Ramanathan, P. (2004). Fault tolerance in collaborative sensor networks for target detection. IEEE Transactions on Computers, 53, 320–333.
Phipatanasuphorn, V., & Ramanathan, P. (2004). Vulnerability of sensor networks to unauthorized traversal and monitoring. IEEE Transactions on Computers, 53(3), 364–369.
Krishnamachari, B., & Iyengar, S. S. (2004). Distributed bayesian algorithms for fault-tolerant event region detection in wireless sensor networks. IEEE Transactions on Computers, 53, 241–250.
Ni, S. Y., et al. (1999). The broadcast storm problem in a mobile ad hoc network. In Proceedings of ACM MOBICOM, pp. 151–162.
Alon, N., Bar-Noy, A., Linial, N., & Peleg, D. (1991). A lower bound for radio broadcast. Journal of Computing Systems Science, 43, 290–298.
Gaber, I., & Mansour, Y. (1995). Broadcast in radio networks. In Proceedings of sixth annual ACM-SIAM symposium on discrete algorithms, pp. 577–585.
Guha, S., & Khuller, S. (1996). Approximation algorithms for connected dominating sets. In Proceedings of fourth annual European symposium on algorithms (ESA), pp. 179–193.
Lim, H., & Kim, C. (2000). Multicast tree construction and flooding in wireless ad hoc networks. In Proceedings of ACM international workshop on modeling, analysis and simulation of wireless and mobile systems (MSWIM), pp. 61–68.
Wu, J., & Dai, F. (2003). Broadcasting in ad hoc networks based on self-pruning. In Proceeding of IEEE INFOCOM.
Peng, W., & Lu, X. (2000) On the reduction of broadcast redundancy in mobile ad hoc networks. In Proceeding of MOBIHOC.
Peng, W., & Lu, X. (2002). AHBP: An efficient broadcast protocol for mobile ad hoc networks. Journal of Science and Technology-Beijing, China.
Qayyum, A., Viennot, L., & Laouiti, A. (2000). Multipoint relaying: An efficient technique for flooding in mobile wireless networks. Technical Report 3898, INRIA-Rapport de Recherche, 2000.
Sucec, J., & Marsic, I. (2000). An efficient distributed network-wide broadcast algorithm for mobile ad hoc networks. Rutgers: CAIP Technical Report 248, Rutgers Univ.
Rabiner Heinzelman, W., Kulik, J., & Balakrishnan, H. (1999). Adaptive protocols for information dissemination in wireless sensor networks. In Proceedings of the fifth annual ACM/IEEE international conference on mobile computing and networking (MobiCom ‘99), Seattle, Washington, August 15–20, pp. 174–185.
Ni, S.-Y., Tseng, Y.-C., Chen, Y.-S., & Sheu, J.-P. (1999). The broadcast storm problem in a mobile ad hoc network. In Proceedings of the 5th annual ACM/IEEE international conference on mobile computing and networking, ser. MobiCom’99, 1999, pp. 151–162.
Levis, P., Patel, N., Culler, D., & Shenker, S. (2004). Trickle: A selfregulating algorithm for code propagation and maintenance in wireless sensor networks. In Proceedings of the first USENIX/ACM symposium on networked systems design and implementation (NSDI), pp. 15–28.
Kulkarni, S. S., & Arumugam, M. (2006). Infuse: A TDMA based data dissemination protocol for sensor networks. IJDSN, pp. 55–78.
Elson, J., Girod, L., & Estrin, D. (2002). Fine-grained network time synchronization using reference broadcasts. In OSDI’02: Proceedings of the 5th symposium on operating systems design and implementation, pp. 147–163.
Ganeriwal, S., Kumar, R., & Srivastava, M. B. (2003). Timing-sync protocol for sensor networks. In SenSys’03: Proceedings of the 1st international conference on Embedded networked sensor systems, pp. 138–149.
Maŕoti, M., Kusy, B., Simon, G., & Léedeczi, A. (2004). The flooding time synchronization protocol. In SenSys’04: Proceedings of the 2nd international conference on embedded networked sensor systems, pp. 39–49.
Zeng, Y., Hu, B., & Feng, H. (2007). Time division flooding synchronization protocol for sensor networks. In MOBIQUITOUS’07: Proceedings of the 2007 fourth annual international conference on mobile and ubiquitous systems: Networking & services, pp. 1–8.
Chilukuri Shanti & Anirudha Sahoo (2011). TREEFP: A TDMA-based reliable and energy efficient flooding protocol for WSNS. IEEE international symposium on a world of wireless, mobile and multimedia networks (WoWMoM), pp. 1–7.
Birman, K. (2007). The promise, and limitations, of gossip protocols. SIGOPS Operations System Review, 41(5), 8–13.
Wuhib, Fetahi, Dam, Mads, & Stadler, Rolf. (2010). A gossiping protocol for detecting global threshold crossings. IEEE Transactions on Network and Service Management, 7(1), 42–56.
Wuhib, F., Dam, M., Stadler, R., & Clemm, A. (2009). Robust monitoring of network-wide aggregates through gossiping. IEEE Transactions on Network Service Management, 6, June 2009.
Demers, A., Greene, D., Hauser, C., Irish, W., Larson, J., Shenker, S., et al. (1987). Epidemic algorithms for replicated database maintenance. In Proceedings of PODC’87: Sixth annual ACM symposium on principles distributed computer, New York, NY, USA, pp. 1–12.
Kempe, D., Dobra, A., & Gehrke, J. (2003). Gossip-based computation of aggregate information. In Proceedings of FOCS’03: 44th annual IEEE symposium on foundations computer science, p. 482.
Tang, C., & Ward, C. (2005). Gocast: Gossip-enhanced overlay multicast for fast and dependable group communication. In Proceedings of DSN’05: 2005 International conference on dependable systems Network, Washington, DC, USA, pp. 140–149.
Fernandez, A., Gramoli, V., Jimenez, E., Kermarrec, A.-M., & Raynal, M. (2007). Distributed slicing in dynamic systems. In Proceedings of ICDCS’07: 27th International Conf. Distributed Comput. Syst., Los Alamitos, CA, USA,p. 66, 2007.
Kostoulas, D., Psaltoulis, D., Gupta, I., Birman, K., & Demers, A. (2005). Decentralized schemes for size estimation in large and dynamic groups. In Proceedings of NCA’05: Fourth IEEE international symposium on networks computing applications, pp. 41–48.
Haas, Z., Halpern, J. Y., & Li, L. (2002). Gossip-based ad hoc routing. In Proceedings of INFOCOM 2002.
Christopher L. Barrett, Stephan J. Eidenbenz, Lukas Kroc, Madhav Marathe, James P. Smith. Parametric Probabilistic Sensor Network Routing. WSNA’03, San Diego, California, USA, September 19, 2003.
Eugster, P. Th., Guerraoui, R., Handurukande, S. B., Kermarrec, A. M., & Kouznetsov, P. (2001). Lightweight probabilistic broadcast. In Proceedings of the 2001 international conference on dependable systems and networks (DSN’01), pp. 443–452, IEEE Computer Society, Washington, DC, USA.
Rodrigues, L., Handurukande, S., Pereira, J., Guerraoui, R., & Kermarrec, A.-M. (2003). Adaptive gossip-based broadcast. DSN’03, 2003.
Werner Vogels, Robbert van Renesse, & Ken Birman. (2003). The power of epidemics: Robust communication for large-scale distributed systems. ACN SIGCOMM, 33(1).
Boyd, S., Ghosh, A., Prabhakar, B., & Shah, D. (2006). Randomized gossip algorithms. IEEE Transaction on Information Theory, 52(6), 2508–2530.
Denantes, P, Bénézit, F., Thiran, P., & Vetterli, M. (2008) Which distributed averaging algorithm should I choose for my sensor network? In Proceedings of 27th conference on computer and communications, pp. 986–994.
Sarwate, A. D., & Dimakis, Ag. (2012). Impact of mobility on gossip algorithms. IEEE Transactions on Information Theory, 58(3), 1731–1742.
http://www.naval-academy.ab-archive.net/software/snetsim.html
Durresi, A., Paruchuri, V. K., Iyengar, S. S., & Kannan, R. (2005). Optimized broadcast protocol for sensor networks. IEEE Transaction on Computers, 54, 1013–1024.
Sabbineni, H., & Chakrabarty, K. (2005). Location-aided flooding: an energy-efficient data dissemination protocol for wireless-sensor networks. IEEE Transactions on Computers, 54(1), 36–46.
Verma, V. K., Singh, S., & Pathak, N. P. (2014). Analysis of scalability for AODV routing protocol in wireless sensor networks. Optik-International Journal for Light and Electron Optics, 125(2), 748–750.
Acknowledgments
We would like to thank Naval Science and Engineering Institute, Istanbul, Turkey [44] for SNetSim simulator for wireless sensor network which greatly supports us for our research work. Additionally, we would like to thank Department of Electronics and Communication Engineering, SLIET, Longowal, India for providing us Wireless SignalPro software.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Verma, V.K., Singh, S. & Pathak, N.P. Analytical Event Based Investigations Over Delphi Random Generator Distributions for Data Dissemination Routing Protocols in Highly Dense Wireless Sensor Network. Wireless Pers Commun 87, 1209–1222 (2016). https://doi.org/10.1007/s11277-015-3049-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-3049-z