Abstract
Chaos is the impromptu behavior exhibited by some nonlinear dynamical systems and has been applied extensively in secure communication over the last decade. In this paper, the chaotic behavior of Van der Pol oscillator is studied and proposed a method to generate Substitution Box (S-box) from it. The generated S-box have some good statistical properties such as PSNR, MSE, correlation, energy, Homogeneity, entropy and contrast. The performance of proposed S-box is compared with other S-boxes like AES, gray, APA, Lui J and S8 to show the strength of anticipated technique.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In the modern world, today’s society is tightly surrounded by the sphere of information era, which is classified by scholar assets and utilizable inside data being considered exceptionally precious. Furthermore, information is electronically processed and conveyed through public networks. The safety of this information during transfer, saving and in routine practice is very important. To ensure the safety of this information, the field of secure communication plays an important role and overcome this issue. Secure communication can be broadly classified in to three subjects, namely, cryptography, steganography and watermarking. The purpose of cryptography and steganography is same, i.e. to conceal the information message but the methodologies employed in these techniques are different. The methodology of watermarking and steganography is same but the purposes of these techniques are different. Watermarking deals with copyright protection of digital data while steganography concerns about the hiding of digital data. One of the most sophisticated cryptographic algorithms used today for encrypting digital data is Advanced Encryption Standards (AES) [3]. AES is a well known block cipher. The block cipher is a type of symmetric-key encryption algorithm that transforms a fixed-length plaintext data into cipher text data of the same dimension. This transformation takes place under the action of a user provided secret key. The decryption is performed by applying the reverse transformation to the cipher text block using the same secret key. AES consists of four steps, which are: byte sub, shift row, mixed column and add round key, the first step is an important one, also known as substitution step performed by the help of S-box. The byte sub step plays a pivotal role in the encryption process because it creates confusion that is reflected in the encrypted data and is the only nonlinear component in AES. S-box is a bijective mapping relation which holds one to one and onto relations; in which a message symbol is replaced with only one unique symbol/element of S-box. S-box can be thought of as a bijective function, \(f(x)\), that is [1],
Equation (1) represents an \(n \times m\) S-box which takes \(n\) bits as the input and gives \(m\) bits as the output, such that
if
then
A major performing criterion of the S-box in encryption techniques is its non-linearity. A foremost research development in the past few years for the construction of S-boxes has been done mainly to increase the non-linearity of these S-boxes [2]. There are many methods proposed in literature for the construction of S-boxes, some of them are AES [3], gray [4], APA [5], Lui J [6] and S8 [7]. In this paper, we proposed a technique of generating S-box from a chaotic map and then compare the performance analysis of anticipated S-box with some of the existing proposed S-boxes.
2 Van der Pol and Proposed Algorithm
In dynamics, the Van der Pol oscillator is a non-conservative oscillator with non-linear damping. It evolves in time according to the second order differential equation, defined as [8]:
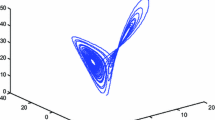
In which, \(\mathop {x}\limits ^{.}\) represents the derivative of \(x\) with respect to time. As it is a nonlinear system with the nonlinearity \(x^{2}\), so there is no analytical solution to it. The iterative solution of (4) is a chaotic solution obtained after initializing it with some initial conditions. The solution of Van der Pole along with the phase trajectory are plotted in Fig. 1. The solution of Van der Pole will be used for designing the S-box as mentioned in the following algorithm.
The flow chart of the proposed algorithm is shown in Fig. 2. The methods involve in the proposed technique are:
-
M.1: The iterative solution of chaotic map is obtain via applying numerical technique.
-
M.2: Apply the ceiling function on the chaotic values to map the real values to the smallest integers, defined as:
$$\begin{aligned} \left\lceil y \right\rceil = min\{n \in {\mathbb {Z}} \mid n \ge y\} \end{aligned}$$(5)where \(y\) is the real value obtain from chaotic map, \(n\) is the nearest integer to \(y\) and \({\mathbb {Z}}\) is the set of integers.
-
M.3: Scale the solution of chaotic map between \(0\) to \(255\) by applying modulo operation denoted by \(\%\), i.e. take \(n\) modulo \(255\), which is remainder on division of \(n\) by \(255\) resulted in \(x\), defined as:
$$\begin{aligned}&\displaystyle x = n \% 255\nonumber \\&\displaystyle n = 255 \times m + x \Rightarrow x = n - 255 \times m \end{aligned}$$(6)In terms of ceiling function,
$$\begin{aligned} x = n - 255 \times \left\lceil \frac{n}{255} \right\rceil \end{aligned}$$(7)where
$$\begin{aligned} m \in {\mathbb {Z}}, \left\lceil m \right\rceil = \left\lceil \frac{y}{255} \right\rceil \end{aligned}$$ -
M.4: Pick the first \(256\) distinct integers to make strong chaotic S-box as shown in Table 1
3 Stimulated Results and Statistical Analysis
The proposed S-box is applied on the Lena plain image to substitute with it. The plain and substituted images are shown in Fig. 3. To demonstrate the strength of proposed technique, few security statistical analysis have been done defined below:
3.1 Correlation
The most fundamental method used in determining the similarity between two images is the correlation analysis. The correlation of an image is given as:
where \(i, j\) corresponds to image pixels positions, \(p(i, j)\) is pixel value at ith row and jth column of digital image, \(\mu \) is the variance and \(\sigma \) is the standard deviation.
3.2 Entropy
Entropy is a magnitude of the uncertainty of a random variable to come in a random process and can be use to show the randomness of the digital image as well. Entropy is defined as:
where \(p(x_{i})\) is the probability of random variable \(x\) at \(\textit{ith}\) index.
3.3 Contrast
The contrast analysis of the image enables the viewer to vividly identify the objects in texture of an image. The contrast of an image is given as:
3.4 Homogeneity
The homogeneity analysis processes the closeness of the distribution in the gray level cooccurrence matrix (GLCM) to GLCM diagonal. The GLCM shows the measurements of combinations of pixel brightness values or gray levels in tabular form. The frequency of the patterns of gray levels can be inferred from the GLCM table. The homogeneity can be determined as:
3.5 Energy
The energy of the image gives the sum of squared values of gray pixels of a digital image defined as:
3.6 Mean Squared Error
Mean Squared Error (MSE) is used to measure the difference between two digital images. It can be defined as:
where \(X_{i}\) corresponds to original image pixel at \(\textit{ith}\) position, \(X_{i}^{*}\) corresponds to resulted image pixel at \(\textit{ith}\) position.
3.7 Peak Signal to Noise Ratio
Pick Signal to Noise Ratio (PSNR) has the same function as MSE, but it takes the signal strength and divided it by noise strength or the difference between the images (MSE), thus gives the better comparative statistical analysis. It is given as:
where \(MAX\) represents the maximum pixel value in the image.
These analysis are done on the proposed technique, as well as on some of the existing S-boxes like AES [3], gray [4], APA [5], Lui J [6] and S8 [7] to show the strength of proposed technique. The results of these analysis, as well as in comparison are listed in Table 2. We can see that the results of proposed technique are much better than the existing techniques.
4 Conclusion
S-box is the most important component in the encryption algorithm, combine in the substitution-permutation network to play a pivotal role. In this paper, a method for designing strong chaotic S-box is presented based on Van der Pole oscillator. The generated S-box shows good results as compared to some existing S-boxes, as evident from the statistical analysis done in this paper.
References
Anees, A. (2014). Design of security systems based upon nonlinear dynamics. MS Thesis, MIlitary College of Signals, NUST.
Anees, A., Siddiqui, A. M., & Ahmed, F. (2014). Chaotic substitution for highly autocorrelated data in encryption algorithm. Communications in Nonlinear Science and Numerical Simulations, 19(9), 3106–3118.
Daemen, J., & Rijmen, V. (2002). The design of Rijndael: AES–the advanced encryption standard. Springer, Berlin.
Tran, M. T., Bui, D. K., & Doung, A. D. (1998). Gray S-box for advanced encryption standard. In International Conference on Computational Intelligence and Security, pp. 253–256.
Cui, L., & Cao, Y. (2007). A new S-box structure named Affine- Power-Affine. International Journal of Innovative Computing, Information and Control, 3(3), 45–53.
Lui, J., Wai, B., Cheng, X., & Wang, X. (2005). An AES S-box to increase complexity and cryptgraphic analysis. International Conference on Advanced Information Networking and Applications, 1, 724–728.
Hussain, I., Shah, T., & Mehmood, H. (2010). A new algorithm to construct secure keys for AES. International Journal of Contemporary Mathematical Sciences, 5(26), 1263–1270.
Cartwright, M. L. (1960). Balthazar van der Pol. Journal of the London Mathematical Society, 35, 367–376.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Anees, A., Ahmed, Z. A Technique for Designing Substitution Box Based on Van der Pol Oscillator. Wireless Pers Commun 82, 1497–1503 (2015). https://doi.org/10.1007/s11277-015-2295-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2295-4