Abstract
A new problem of spectrum scarcity has emerged due to the incredible technological advances in wireless communication. The spectrum scarcity issue is a bottleneck for the next generation of wireless communications. Therefore, efficient spectrum utilization has attracted considerable attention. This paper proposes a novel method of utilizing the white spaces in the licensed spectrum while ensuring the incumbent licensees’ rights. The protocol predicts the incumbents’ arrival using a historical prediction method and protects the incumbent users from the interference of opportunistic spectrum users. Distributed sensing is used to determine the network wide spectrum opportunity. The channel access delay in the proposed protocol is evaluated by simulation and mathematical analysis. The protocol has the advantages of a decentralized system, flexibility and low computing complexity. The simulations show that the protocol outperforms the existing opportunistic spectrum-sharing, media-access-control protocols in terms of the goodput and delay.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The current static allocation of a spectrum is not efficient in spectrum utilization. On one hand, the spectrum license is quite expensive. Therefore, many new technologies have been designed for license-free bands. Consequently, these license-free bands are already heavily congested, and are a bottleneck for the development of future generation wireless communication. On the other hand, in many cases, licensed users only occupy the spectrum for certain durations, and the desired transmission only covers certain geographical areas. Several unutilized or underutilized licensed areas of the license spectrum can be found at different combinations of frequency, time, and space. For example, the measurements taken in urban Auckland, New Zealand showed that the spectrum use in the frequency range between 806 and 2,750 MHz is approximately 6.2 % on average in both indoor and outdoor environments [1]. Similar (spectrum underutilized) results have been observed in different places [2–4]. Studies by the FCCs Spectrum Policy Task Force also reported vast temporal and geographic variations in the use of the allocated spectrum with utilization ranging from 15 to 85 % [4].
These observations have led to a new paradigm of opportunistic spectrum access known as dynamic spectrum access (DSA). Cognitive radio (CR) technology is being considered to enable CR networks (sometimes also called DSA networks), where unlicensed opportunistic spectrum users, also called secondary users (SUs), can actively search for any unused spectrum (white holes) in the licensed bands and communicate using these white holes. This vision is supported by regulatory bodies, such as the FCC [5].
Several MAC protocols for CR networks are proposed in the literature [6, 7], however most of them have not address the issues of behavior of PUs on the channel, utilization of channel negotiation (CN) window, protection of incumbents, high level cooperative sensing, traditional hidden node problem, exposed node problem and multichannel hidden node problem. The proposed protocol accommodates all these issues.
This paper proposes a novel decentralized media access control (MAC) protocol to protect incumbent license users, also called the primary users (PUs), in CR networks. The proposed protocol is a synchronization-based multi-transceiver and multi-channel MAC protocol. In this protocol, time is divided into beacon intervals (BIs), which are then subdivided into CN and data communication windows. In the CN window, SUs negotiate for the channels by sending a list of idle channels available for communication in a common control channel (CCC). This channel selection is based on the history of the incumbents’ behavior in the channel. After CN, the SUs begin sending data in the data channel. Once the incumbent reclaims the data channel currently used by the SUs, the SUs stop sending packets and send an emergency control message in the CCC and handoff spectrum.
This paper addresses efficient spectrum utilization, protection of licensed users with little or no tolerable damage and well-known channel allocation problems. The following presents the main contributions of this paper.
-
(a)
Channel selection algorithm: A novel channel selection algorithm is proposed based on historical prediction model (HPM) (i.e. prediction based on incumbents’ behavior on the channel for a period of time). The protocols with and without a prediction model are simulated and compared.
-
(b)
Utilization of CN window: In most of existing protocols, the CR nodes do not send data packets in the CN window. The proposed protocol does not wait until the end of the CN window and sends data packets just after successful CN. The average additional maximum achievement in each BI using this strategy is the product of the channel access probability, half of the CN window and total number of data channels available.
-
(c)
Analysis of the channel access delay: The channel access delay in CN period is analyzed and the correctness of the analysis is verified by the simulation.
-
(d)
Incumbent protection: Several strategies are carried out to protect the rights of the incumbents. Cooperative sensing, i.e. nodes share the sensing information and maintain knowledge of the channels’ status in the entire networks, is used. In addition, sensing twice in a single BI helps protect the incumbents with little or no damage but the small cost of delay.
In addition, the proposed protocol takes care of the traditional hidden node problem, exposed node problem and multiple channels hidden node problem. The incumbents reclaim resolution and spectrum handoff method is also proposed to reconnect the communication links after the incumbents reclaimed the channel. This method prevents the SUs from waiting a long time after the incumbent is detected in the currently used channel.
The remainder of this paper is organized as follows. Section 2 reviews some of the most recent papers. Section 3 discusses the system model. Section 4 describes the proposed decentralized predictive spectrum-sharing MAC protocol for ad hoc CR networks, and analyzes the channel access delay in CN time. Section 5 discusses the simulation results and performance evaluations. Section 6 provides the conclusions and future work.
2 Related Work
Designing an efficient MAC protocol for CR networks is one of the most challenging issues. This is more challenging than for other types of wireless networks because it would be very sophisticated and more intelligent to not only increase the performance of SUs, but also protect the incumbents’ rights. Many researchers suggested several ways of improving the spectral efficiency in CR networks to mitigate the spectrum scarcity crisis by balancing the underutilized license bands and over-utilized license-free bands. Some related studies are discussed briefly.
The IEEE 802.22 working group aims to construct a Wireless Regional Area Networks (WRAN) and recently standardized a MAC layer based on CR for reusing the spectrum allocated to the TV broadcast service [8]. In this standard, each WRAN can deliver up to 22 Mbps per channel without interfering with the reception of existing TV broadcast stations. IEEE 802.22 specifies that the network should operate point-to-multipoint. The architecture of the 802.22 MAC layer is centralized and relies on a base station.
Wu et al. [9] proposed a multi-channel MAC protocol for multi-hop mobile ad hoc networks based on an on-demand channel assignment concept called dynamic channel allocation (DCA). Similar to DCA, Nan et al. [10] proposed a MAC protocol for CR networks called the distributed coordinated spectrum sharing MAC protocol (DCSS). In DCSS, the request to send (RTS) and clear to send (CTS) are exchanged before the communications. RTS/CTS include the available data channel list. The time slot mechanism in DCSS is used to detect the incumbents. This is a multiple antenna-based protocol. On the other hand, DCA negotiates for a data channel per data packet and also relies fully on a dedicated common CCC. The DCA-based protocols may incur control-channel starvation when too much control information is sent over the CCC. All nodes need to contend for access to the control channel and data channels remain underutilized [11]. The maximum number of channels that can be fully utilized using DCA-based protocols is approximately Ld/3Lc, where Ld is the data packet size and Lc is the control packet size [9].
A multichannel MAC protocol (MMAC-CR) is proposed for CR networks [11]. This is also a single transceiver-based protocol that is similar to MMAC [12]. As in the power saving mechanisms in the IEEE 802.11 distributed coordination function (DCF) [13], in the MMAC-CR protocol, time is divided into an ad hoc traffic indication message (ATIM) window and data window. The control packets for CN and channel reservation are transferred in the ATIM windows, whereas the data packets are transferred in the data windows. Similar to MMAC-CR, an energy efficient CR MAC protocol for QoS provisioning (ECRQ-MAC) is proposed [14]. These protocols are less prone to the CCC bottleneck problem because only one handshake on the CCC is needed per connection during the BI. Little control information is required compared to DCA-based protocols, where one handshake per sent packet is needed. On the other hand, these protocols wait until the end of ATIM window to send and receive data packets. Therefore, the channel bandwidth of all data channels in the ATIM window is wasted, which leads to more delay and lower throughput. They may also suffer from multiple channel switching overheads and multichannel hidden node problems.
Several authors have introduced other new approaches. For example, a distributed MAC protocol to operate spectrum-agile radios in a multi-hop ad hoc network is proposed in [15]. It requires dual-receive, single-transmit radio that can simultaneously receive two independent bit streams on any two of the available channels, but can only transmit over one channel. Most of all these protocols select data channel randomly without observing the incumbents’ behavior on the channel.
A CCC based hardware constrained MAC (HC-MAC) protocol is proposed in [16]. HC-MAC is a decentralized random access protocol, which conducts efficient spectrum sensing and spectrum access decision by considering the hardware constraint e.g. a single radio, partial spectrum sensing, and spectrum aggregation limits. HC-MAC has three operation phases namely contention, sensing, and transmission. The main drawback of this protocol is that neighboring nodes may not receiver packets if they are engaged in transferring data packets, because CR node starts sensing after winning contention on the CCC.
An opportunistic cognitive MAC (OC-MAC) protocol is proposed in [17]. OC-MAC protocols allow SUs to identify and use the available frequency spectrum without interfering to the PUs. It needs two transceivers, one is for a dedicated control channel and the other is for selected data channel. All licensed channels are time-slotted and primary and secondary networks are synchronized. In control channel, the slots are further divided into reporting phase and negotiation phase. The reporting phase has n mini-slots, where n is the number of channels. At the beginning of each time slot, the cognitive user senses one of the channels. If a channel is idle, node sends a beacon over the CCC during the corresponding mini-slot of the reporting phase. P-persistent carrier sense multiple access is used in the negotiation phase for negotiation. Although, OC-MAC exploited two sensing policies to enhance spectrum opportunities detection, it cannot guarantee fairness to the SUs.
Dynamic open spectrum sharing (DOSS) MAC [18] protocol uses multiple antennas for a data band, a control channel, and a busy tone band. DOSS MAC protocol supports efficient multicast, needs no synchronization, and provides an option that eliminates the hidden and exposed terminal problems. However, the spectrum is not efficiently utilized because DOSS MAC protocol use separate and out-of-band spectrum for issuing the busy tones and for the CCC. It has hardware cost overhead and energy consumption overhead as it uses three antennas.
3 System Model
This section presents the system model for the HPM based a decentralized MAC (here after referred as P-MAC) protocol for an ad hoc CR networks. Assume there are \(\left\{ Ch|Ch_{i}, i=1,2, \ldots N\right\} \) non-overlapping incumbent license channels (LCs) conditionally and opportunistically accessible by the SUs. The channel refers to the physical channel, which is a spectrum band with a certain amount of bandwidth. For convenience, all channels are assumed to have an identical channel bandwidth. Logical channels, such as different coding schemes in code division multiple access (CDMA), are not considered. The packets transmitted on different channels do not interfere with each other because none of the channels overlap. An additional assumption is that there is a dedicated CCC available with all the required qualities for reliable communication for all times. The CCC is used mainly for control packet exchange and is common among all the SUs in the networks. This channel is free of incumbents’ interference.
3.1 Beacon Interval and Synchronization
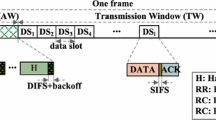
The entire time is slotted into BIs. One BI is equal to the maximum tolerable time of the incumbent license user. Each BI is divided into a CN window and data window (DW) as shown in Fig. 1. The CN windows contain beaconing, rapid sensing and CN message exchange time. Each node is synchronized by periodic beacon transmission to learn the network-wide spectral opportunities. The secondary transmission should be paused or stopped, whereas the SUs are sensing the channels because it is difficult to discriminate the primary transmission and secondary transmission if both transmissions are in progress while sensing the channels. Time synchronization is performed to pause or stop the secondary transmission and determine the network-wide spectral opportunities. P-MAC uses the timer synchronization function (TSF), as in the IEEE 802.11 MAC protocol [13] for synchronization.
3.2 Cognitive Radio Devices
Cognitive radio (CR) devices are assumed to be intelligent software-defined radio (SDR) devices with the cognition capacity that can observe, orient, plan, learn, decide and act as mentioned in [19, 20]. These devices can form CR networks, utilizing the white spaces without interfering with the incumbents. Each CR device is equipped with two half-duplex transceivers, called the control transceiver and data transceiver. The control transceiver is permanently hooked into the CCC, and is used to control the message exchange (e.g. sending traffic indication message, receiving acknowledge, sending channel reservation message etc.). This transceiver wakes up immediately before fast sensing ends at the middle of data window and enters into the doze state after the CN window. This transceiver remains in the doze state for approximately 40 % of the time. The approach to turn off the transceivers can increase the energy conservation but does not decrease the SU performance, nor does it increase the probability of a collision with the incumbents. In the remaining 60 % of time, the control transceiver remains active for synchronization, CN, better protection of incumbents and reconnection of the broken communications links. The data transceiver is for the data channel and is capable of switching multiple types of frequencies (and environments) dynamically; its function is to send data and receive ACK. The data transceiver is also responsible for fine sensing and fast sensing. The data transceiver remains in the doze state whenever there is no data to send and receive.
3.3 Incumbent Detection or Sensing
At the system level, P-MAC follows two types of sensing: fast sensing and fine sensing, as in 802.22 [8]. Fast sensing (e.g. energy detection) takes a very small time, \(<1\) ms/channel, and gives three results: (a) channel is busy, (b) channel is idle and (c) uncertain. These sensing results are used to determine if subsequent fine sensing stage is needed. Power consumption is assumed to be the same as that of the idle state because it is a kind of limited sensing. As fast sensing takes a very small time, the accuracy is low. Fine sensing is performed to decrease the incidence of false alarm and increase the QoS. This is a tradeoff to improve the sensing accuracy but at the cost of time. Fine sensing gives two results: (a) channel is busy or (b) channel is idle. Power consumption for fine sensing is assumed to be equal to that of the receiving state.
3.4 Distributed Spectrum Sensing and Channel Status Table
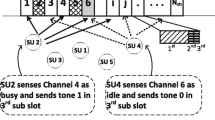
With the exception of the detection method, the sensing efficiency of the network-wide spectral opportunities depends on when and how many SUs sense the channels. P-MAC employs distributed spectrum sensing (DSS) to prevent incumbent-SU collision. This allows each user to detect signals in the channels and maintains the channel usage list (CUL) in the channel status table (CST). Sensing inefficiency can occur if the nodes sense the channel randomly all the time. Many SUs in the system may sense the same channel, while many channels might not be sensed. This inefficiency can be an obstacle to gathering network-wide spectral opportunities. This issue has been described well in [21–23]. P-MAC follows some basic rules for channel sensing to gather the network-wide spectral opportunities and avoid sensing inefficiency. At the very beginning, the nodes wait for a synchronization signal. When a node receives information about the next BI, it selects a channel randomly for fast sensing (FS). From the next BI, as a node receives information of the other channels from distributed sensing, it selects a channel with the least nodes performing FS. This DSS strategy in the system-level design improves the accuracy of the channel state and helps to select the best common channel from the available channel list between the communication pair.
After sensing, each SU updates the current channel status by its own sensing result and overhearing the neighbors’ CNs on the CCC in their proximity. As shown in Table 1, the CST contains network-wide sensing results of the channels. The record field in the table contains the record of a period from \(BI_1\) to \(BI_n\). The CUL (\(Ch_{i}\)) fields contain information as to whether channel 1 was busy at the start of \(BI_1\), and the signal to noise ratio (SNR) fields contain the SNR of channel i at the sensing time. The SUs employ the CUL for channel state prediction using the HPM (discussed below) and to select channels for possible data transfer. The SUs maintain channel ranking according to the channel selection factor (CSF) (1). The CUL of channel i has three values, CUL(\(Ch_i\)) \(=\) [0, 1, 2], where,
-
CUL(\(Ch_{i}\)) \(=\) 0, if the incumbent is not detected (or channel is idle),
-
CUL(\(Ch_{i}\)) \(=\) 1, if the incumbent is detected (or channel is busy),
-
CUL(\(Ch_{i}\)) \(=\) 2, uncertain.
4 Protocol Description
The operation of P-MAC is divided into two stages: control operation and data operation. The control operation is performed in the CN window and the data operation is performed after CN.
4.1 Control Operation
At the beginning of the CN window, as shown in Fig. 1, each node has a minimum backoff of \(t_{m}\), where \(t_{m} = t_{f} + t_{b}\). \(t_{f}\) is the time for fast sensing, \(t_{b}\) is the random backoff time and \(0 < t_{b} \le CW\). Contention window (CW) is initially set to be minimum CW (W). After time \(t_{m}\), the node with buffered packets in the transmit queue sends CN packets with the preferred channel list (PCL) to the destination. Each node maintains its own PCL level for sending it with the CN packet or replying to the receiver’s common PCL (RCPCL) with the CN acknowledgement (CN-ACK). The PCL contains a list of channels that do not have 1 and 2 of CUL (i.e. only CUL \(=\) 0) in the CST, and lists the channels from the most preferred to least preferred channel according to the PCL level. The PCL level is the ranking index of the channel, which depends on the probability of the incumbents’ arrival in the channel calculated by a node. This index value can differ for the same channel, according to the time and geographical location of the SU. More sophisticated parameters (e.g. channel fading, transmission rate, etc.) can accumulate in the algorithm to make it more realistic. The effect of adding parameters that are more sophisticated will be examined in future work for making the proposed protocol simple. The PCL is derived from the CSF, as expressed in Eq. (1), and is a function of channel utilization (\(U_{t}\)) and SNR. In Eq. (1), \(U_{t}\left( Ch_{i}\right) \) is the utilization of channel i by the incumbent, \({\textit{SNR}}_{min}\) is the threshold for the minimum SNR required, and SNR(\(Ch_{i}\)) is the SNR of channel i.
P-MAC uses linear HPM to predict the incumbent’s arrival to make a robust decision to select a communication channel. The channel utilization parameters are received from the physical layer. \(U_{t}\) depends on the incumbent’s arrival. The more the incumbents’ utilize the channels, the higher the \(U_{t}\). The incumbent’s \(U_{t}\) of channel i can be derived as follows
where, \(U_{t-1}\left( Ch_{i}\right) \) is the channel utilization in the last time slot, \(\gamma \) is the smoothing factor and \(\hat{U}\left( {C{h_i}} \right) \) is the average utilization of the time slot of channel i in the past and can be calculated using Eq. (3).
where, \(\eta \) is the number of records kept so far and is a predefined constant.
After receiving the CN Packet, the receiver analyzes the sender’s PCL. After receiving the CN message from any sender that is destined to the receiver, the receiver selects the channel common to both and with the best PCL level. The receiver sends CN-ACK including RCPCL to the sender, as expressed in Eq. (4).
The sender sends a CN reservation packet (CN-RES) to confirm the channel reservation after receiving the RCPCL. Neighboring nodes update their channel status. A node waits for the DIFS before performing backoff, and waits for the SIFS, before sending ACK. The random backoff time (RBT) is calculated, as expressed in Eq. (5).
where INT is an integer function, CW is an integer between the minimum CW (W) and maximum CW (\({W_m}\)) and random( ) is a pseudo random number between 0 and 1. If the current packet has its first transmission, CW is set to W. CW is doubled after each collision with this packet, until it reaches \(W_{m}\). The detail channel access delay analysis is given in the channel access delay section.
The CN/CN-ACK packet contains network allocation vector (NAV) information to avoid the hidden terminal problem, which is similar to the RTS/CTS packets. The control transceiver enters the doze state after the CN window and wakes up immediately before fast sensing ends at the middle of the data window. Because the CN window is approximately one fourth of the data window, this cycle allows the control transceiver to remain in the doze state for approximately 40 % of the operation time.
4.2 Data Operation
Unlike existing CN based CR MAC (CR-MAC) protocols [11, 14] that are close to the proposed approach, the nodes do not wait to send data until the start of the data window. As shown in Fig. 1, the sender immediately starts the data transmission procedure to the data channel after negotiating for the channel and sending the CN-RES packet in the CCC. The average additional maximum achievement in each BI with this strategy is \({\Pr _s} \times {1 \over 2}{\textit{CNW}} \times {C_N}\). Where, \({\Pr _s}\) is the success probability of a CR node for channel access, CNW is the size of the CN window and \({C_N}\) is the number of available data channels. The optimal CN window is approximately one fourth of the data window (\({I_{data}}\)). Therefore, the maximum achievement in each BI with the proposed protocol is \({1 \over 8}\left( {{{{\Pr }_s}} \times {I_{data}} \times {C_N}} \right) \).
Communication pairs exchange RTS/CTS before sending an actual data packet to avoid the traditional hidden terminal problem. The sender sends the data packet to the receiver, after successful RTS/CTS exchange, the receiver sends the ACK packet back to the sender after receiving the data as an acknowledgement of the data packet, similar to the 802.11 DCF’s operation. If there is no data in the transmission queue and no packets to receive, it begins fine sensing (FiS) after the CN window. The node enters the doze state after fine sensing. The strategy to turn off data transceiver saves considerable energy when the transmission queue is empty and there is no data to receive, even though the main objective is not power saving.
4.3 Incumbents’ Reclaiming Resolution and Spectrum Handoff
To protect the incumbents’ right on the channel, the SUs need to vacate the channels immediately when the incumbent licensed users wish to use them. When the incumbents reclaim the band, the affected communication links of the SUs will be lost. On the other hand, if the SUs can sense idle sub-bands, they can reconstruct the communication links to them. This is termed spectrum handoff [24]. The nodes sense the channels at the beginning of each BI in the proposed approach because the incumbents’ protection is the first priority. The channel is selected for data communication if there are no incumbent activities. The SU pauses transmission and goes for fast sensing at the middle of the data window. If it finds incumbent activity in the channel, it stops sending packets immediately and buffers the packets. The node sends an emergency message to the receiver in the CCC to inform that the current channel is not usable. The nodes overhearing this message will update their CST and will not sense the channel at least for the next BI. In the next BI, the data transreceiver begins sensing new channels according to the sensing rule. Meanwhile, control transceiver negotiates new channel sending CN/CN-ACK/CN-RES and starts communication in the newly negotiated channel.
4.4 Channel Access Delay in CN Window
In this section we analyze channel access delay in CN window. The channel access delay is the time a node spends to obtain access to the channel. This is also called contention delay. For this analysis we assume that CCC is not free from PUs intervention. Let X denote the MAC layer access delay. m represents the station short retry count and m is also the maximum backoff stage. This paper considers the contention model where the contention window size \(W_i\) in the backoff stage i is determined to be
where, W is the minimum contention window size. The expectation of X can be expressed as
We model the behavior of PUs on the channel as follows. PUs arrive at the channel according to a Poisson process with a rate of \(\beta \). The sojourn time of each PU is exponentially distributed with an average of 1/\(\alpha \). The number of PUs on the channel at an arbitrary time (\({N}\)) can be analyzed as a traditional birth-and-death process. N has the following distribution [26].
If p denotes the probability that a transmitted packet encounters a collision, then
i.e.
where \({p_{_1}}\) is the probability that a packet transmitted from a SU encounters a collision with any packet from PU. \({p_{_2}}\) is the probability that a transmitted packet encounters a collision with any packet from SU and \({p_{_2}}\) can be obtained using the formulae described in Sect. 3 of [25].
A SU will experience a collision if the channel is used by PUs when the SU attempts to use the channel. Thus, \({p_{_1}}\) can be approximated by \({1-Pr(N=0)} = 1 - {e^{ - {\beta \over \alpha }}}\) of Eq. (8), if the mini-slot interval in the CN window is negligibly short compared to the ON period of the PU.
Let \({p_{bp}}\) represents the probability that a SU senses PU’s presence on the channel during fast sensing period (refer Fig. 1). Assuming that the duration of the fast sensing period is negligibly small compared to the duration of the data window, then \({p_{bp}}\) can be approximated by
i.e.
Also,
Combining Eqs. (7) and (11) yields
Let \({\tilde{W}_j}\) denote the sojourn time in stage j measured in number of mini-slots, and \(W_i^*\) represents the summation of \({\tilde{W}_j}\) ’s up to stage i, i.e.\(W_i^* = \sum \nolimits _{j = 0}^i {{{\tilde{W}}_j}} \). \(s_0\) denotes the time when stage 0 begins in the given CN window, i.e. when the MAC layer access attempt starts. When \(N_s\) and \(\varDelta \) denote the number of mini-slots in a single CN window and the width of one mini-slot, respectively, for simplicity, let’s assume that \(s_0\) is distributed uniformly as follows
If \(\textit{E}_i\) represents the event that the transmission succeeds in stage i, then we can obtain
By assuming independence between \(s_0\) and \(W_i^*, \mathrm{{E}}[X|W_i^* = j,{E_i}]\) can be expressed as follows
where, \(I_{data}\) is the data window time.
In case of no PU attempting to access the channel, then \(E[X|W_i^* = j,{E_i},{s_0} = k\varDelta ]\) of Eq. (15) can be simplified to
If PU is sensed during the fast sensing, SUs do not attempt to access the channel during that BI. Thus, when \(p_{bp}\) is not zero, \(E[X|W_i^* = j,{E_i},{s_0} = k\varDelta ]\) can be expressed by the expectation of negative binomial distribution as
Combining Eqs. (15) and (16) yields,
Combining Eqs. (14) and (17) yields
\(\Pr (W_i^* = j|{E_i})\) can be expressed as follows
where, \(A(n,i)\) counts the number of solutions for the below integer indeterminate equation under the condition, \(X_j \ge 1\) and \(X_j \le W_j(0 \le j \le i\)).
A closed form formula for \(A(n,i)\) is difficult to derive but it is possible to evaluate the value of \(A(n,i)\) numerically for given values of n, i and \(W_j\) using the following recursive formula and initial conditions
The following can be obtained by combining Eqs. (12), (18) and (19)
Figure 2 shows an evaluation of the proposed model and simulation results when the maximum retry limit is three, \( \varDelta \) is 1.27 ms, \(I_{data}\) is 80 ms, and minimum CW size is 16.
In the simulation, if a CR node losses contention for channel access, it tries next time until it wins contention or reaches the maximum retry limit. The SU node can win contention in any subsequent BI. For simplicity, it is assumed that \({s_0}\) is distributed uniformly over a single CN window in the analysis. In Fig. 2, the gap between the analysis and simulation results is due to these assumptions. Furthermore, in the analysis, the beacon time is not considered, as shown in the beginning of the CN window in Fig. 1. The CR nodes synchronize with other CR nodes; they sense the channel status and report during this time. This also helps increase the gap between the analysis and simulation results.
5 Evaluation and Simulation Results
This section describes the simulation setup and observed results. The efficiency of this protocol is validated by simulations with various parameters. The goodput and per-packet delay are used as performance metrics. In the evaluations, the goodput is the amount of data delivered to the MAC layer per second excluding overheads. Two approaches, MMAC-CR [11] and DCSS [10], are selected for the comparison with the proposed protocol because MMAC-CR is similar to the proposed approach and DCSS is based on DCA [9]. DCA is a popular CCC-based approach to manage multiple channels, adding the available data channel list to the RTS and CTS, as described in Sect. 2.
5.1 Simulation Setup
Extensive simulations are performed using ns-2 [27]. The transmission range of the nodes is approximately 250 m. One control channel is used for each category with data channels varying from 3 to 9 with the same bit rate of 2 Mbps. The constant bit rate (CBR) traffic with the offered load varied from 10 to 1,000 packets per second. The number of SU communication pairs also varied from 2 to 32, and is distributed over a 400 m by 400 m area. Each data packet is 512 bytes. The channel switching delay is 224 \(\upmu \)s. The ON/OFF channel usage model is considered. If an incumbent in the channel is active or idle, it is in the ON or OFF state, respectively. Each simulation is run for approximately 40 s. The BI is set to 100 ms and the CN window size is 1/4 of the data window size. The results are an average of 10 iterations.
5.2 Simulation Results and Discussion
Figure 3 shows the aggregated goodput of P-MAC with and without the HPM measured every 40 BIs. The graph shows that the protocol with the HPM is superior to the protocol without the HPM. The results are from a 100 packets per second offered load, six nodes and a three data channel scenario. Initially, P-MAC with and without the HPM show similar aggregated goodput. However, after certain BIs, when there is sufficient data in the CST, P-MAC with the HPM begins selecting the channels intelligently, which gives higher aggregated goodput. The higher gap between the two protocols is attributed to the channel behavior learning method of the HPM. The fluctuations in the graph are attributed to the arbitrary arrival of the incumbents’ and are not consistent successful packets every 40 BIs.
Figure 4 shows the aggregated goodput versus the number of channels. The results in the graph show that aggregated goodput of P-MAC in the six node scenario is far better than the other protocols. In MMAC-CR, the nodes have to wait until expiration of the CN window to send data packets because the CN window size is fixed and there are only six nodes. On the other hand, nodes begin sending data packets immediately after a successful CN in the proposed approach. In addition, they select the channel for communication based on the incumbents’ behavior in the channel. Therefore, the proposed approach achieves approximately 13.6 % more aggregate goodput than the other two protocols.
Figure 5 shows that the aggregated goodput of P-MAC is significantly higher than DCSS in the sixteen node scenario because in DCSS, the management cost increases with increasing number of channels and nodes. In DCSS, the nodes exchange CN packets for every data packet, which suffers from the channel bottleneck problem. In addition, frequent channel switching occurs if the communication pair selects another channel than the current channel in each negotiation. This is more probable if there are a larger number of channels available. In Fig. 5, when the number of channels increases from 6 to 9 channels, the aggregated goodput decreases in the same offered load and number of nodes. This takes a long time to resolve after the incumbents reclaim the channel in DCSS.
Figure 6 shows the aggregated goodput of P-MAC with the offered load varying from 10 to 1,000 packets per second in the six channel scenarios. The value in parenthesis after the name of the protocols in the legends is the number of nodes. They reached the saturation point in a similar offered rate when there are only six nodes. Nevertheless, when there are sixteen nodes, DCSS is saturated earlier and the goodput is much lower than the other two protocols. Again, this is attributed to the same reasons mentioned earlier. The proposed protocol performed better than MMAC-CR even in the six node scenario.
Figure 7 compares the performance of P-MAC with and without fast sensing in the middle of the data window. This is the result of three channels and different node densities. To protect the incumbents’ right on the channel, P-MAC performs rapid sensing in the middle of the data window. Figure 7 shows that in a sparse network there is no advantage of having fast sensing in the middle of data window, because the fast sensing pauses transmission and decreases the goodput. But, in a dense network, there is a higher probability of collision with incumbents’. When a SU finds incumbent in the channel, it stops transmission in that channel and handoff spectrum and resumes transmission in the new channel. Therefore, P-MAC with fast sensing has a higher aggregated goodput when there are more than 25 nodes.
Figure 8 shows the average packet delay in the three channels and six nodes scenario. P-MAC has a smaller delay than the MMAC-CR due to its strategy of not waiting until finishing the CN window to transmit data. In addition, it uses HPM, which predicts the future incumbents’ arrival and protects the incumbents. Therefore, it saves channel renegotiation and connection reestablishment time. Nevertheless, it has slightly more delay than DCSS due to P-MAC and MMAC-CR using the CN time to protect the incumbent users and there is no data transfer during the CN time. P-MAC incurs a reasonable delay cost because the main goal is to protect the incumbents and utilize the spectrum efficiently.
6 Conclusion and Future Work
This paper presented a MAC protocol that utilizes white spaces efficiently in CR networks. The protocols for CR networks are simulated and compared to evaluate the performance of the approach at various numbers of channels, number of nodes, offered load, etc. An analytical model is also developed to analyze the channel access delay in a CN. The simulation results show that the P-MAC protocol increases the goodput and decreases the delay. The reasons behind the higher goodput are—(a) unlike any other CN window-based protocol, the proposed protocol begins data communication (RTS/CTS, data/ACK) immediately after successful CN. The protocol does not wait until the CN window is complete. From this strategy, \({1 \over 8}\left( {{{{\Pr }_s}} \times {I_{data}} \times {C_N}} \right) \) additional throughput is achieved. (b) P-MAC uses HPM to predict the incumbents’ arrival in the channel, protecting incumbent-SU collision. This decreases the renegotiation and retransmission delay. (c) P-MAC renegotiates for the data channel if the incumbent reclaims the channel and does not wait to send data until the end of the BI. Hence, it increases the SU goodput. Although P-MAC uses two transceivers, it turns off the transceivers to conserve energy without decreasing SU performance. This also does not increase the probability of collision with incumbents. The control transceiver is active only for 60 % of the time for synchronization, CN, better protection of incumbents and reconnection of the broken communications links. Finally, P-MAC protects the incumbents’ rights on the channel with a small delay cost, which is what is needed to make CR networks feasible in the real world. The analysis results show that the CN window becomes a bottleneck as the number of active nodes increases. More study will be needed to address the CCC bottleneck problem.
References
Chiang, R. (2009). Feasibility investigation of cognitive radio systems. PhD dissertation. New Zealand: The University of Auckland.
Renk, T., Kloeck, C., & Jondral, F. K. (2007). A cognitive approach to the detection of spectrum holes in wireless networks. In IEEE consumer communications and networking conference. Las Vegas, USA.
Cabric, D., Mishra, S. M., Willkomm, D., Broderson, R. W., & Wolisz, A. (2005). A cognitive radio approach for usage of virtual unlicensed spectrum. In 14th IST mobile wireless communications summit. Dresden, Germany.
Walko, J. (2005). Cognitive radio. IEE Review, 51(5), 34–37.
FCC. (2002). Spectrum policy task force report. In FCC, Technical Report Series. ET Docket No. 02–155, Nov 2002.
De Domenico, A., Strinati, E. C., & Di Benedetto, M. (2012). A survey on MAC strategies for cognitive radio networks. IEEE Communications Surveys & Tutorials, 14(1), 21–44.
Cormio, C., & Chowdhury, K. R. (2009). A survey on MAC protocols for cognitive radio networks. Ad Hoc Networks, 7(7), 1315–1329.
IEEE Standard for Information Technology-Telecommunications and information exchange between systems-Wireless Regional Area Networks (WRAN)-Specific requirements-Part 22: Cognitive Wireless RAN Medium Access Control (MAC) and Physical Layer (PHY) Specs.: Policies and Procedures for Operation in the TV Bands. 16 June 2011.
Wu, S.-L., Lin, C.-Y., Tseng, Y.-C., & Sheu J.-P. (2000). A new multi-channel MAC protocol with on-demand channel assignment for multi-hop mobile ad hoc networks. In ISPAN 2000 (pp. 232–237). Texas, USA.
Nan, H., Hyon, T., & Yoo, S. (2007). Distributed coordinated spectrum sharing MAC protocol for cognitive radio. In IEEE symposium on new Frontiers in DySpan 2007 (pp. 240–249). Dublin, Ireland.
Timmers, M., Pollin, S., Dejonghe, A., Van der Perre, L., & Catthoor, F. (2010). A distributed multichannel MAC protocol for multihop cognitive radio networks. IEEE Transactions on Vehicular Technology, 59(1), 446–459.
So, J., & Vaidya, N. (2004). Multi-channel MAC for ad hoc networks: Handling multi-channel hidden terminals using a single transceiver. In MobiHoc 2004 (pp. 222–233). New York, USA.
IEEE Standard for Information Technology-Telecommunications and Information Exchange Between Systems-Local and Metropolitan Area Networks-Specific Requirements Part II: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specs., TG 802.11, 2003.
Kamruzzaman, S. M., Hamid, M. A., & Abdullah-Al-Wadud, M. (2010). An energy-efficient MAC protocol for QoS provisioning in cognitive radio ad hoc networks. Radioengineering, 19(4), 567–578.
Krunzj, M., & Manzi, D. (2011). Channel access and traffic control for dynamic-spectrum networks with single-transmit, dual-receive radios. Computer Communications, 34(8), 935–947.
Jia, J., Zhang, Q., & Shen, X. (2008). HC-MAC: A hardware-constrained cognitive MAC for efficient spectrum management. IEEE Journal on Selected Areas in Communications, 26(1), 106–117.
Su, H., & Zhang, X. (2008). Cross-layer based opportunistic MAC protocols for QoS provisionings over cognitive radio wireless networks. IEEE Journal on Selected Areas in Communications, 26(1), 118–129.
Ma, L., Han, X., & Shen, C.-C. (2005). Dynamic open spectrum sharing for wireless ad hoc networks. In IEEE DySPAN 2005 (pp. 203–213). Baltimore, USA.
Mitola, J., & Maguire, G. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6(4), 13–18.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Song, J., Xue, J., Feng, Z., Zhang, P., & Liu, Z. (2010). Optimal cooperative spectrum sensing strategies in cognitive radio networks. In IEEE VTC 2010 (pp. 1–6). Taipei.
Quan, Z., Cui, S., & Sayed, A. H. (2007). An optimal strategy for cooperative spectrum sensing in cognitive radio networks. In IEEE GLOBECOM 2007 (pp. 2947–2951). Washington DC, USA.
Ganesan, G., & Li, Y.G. (2005). Cooperative spectrum sensing in cognitive radio networks. In IEEE DySPAN 2005 (pp. 137–143). Baltimore, USA.
Zhu, X., Shen, L., & Yum, T.-S. P. (2007). Analysis of cognitive radio spectrum access with optimal channel reservation. IEEE Communications Letters, 11(4), 304–306.
Barowski, Y. D., & Biaz, S. (2004). The performance analysis of IEEE 802.11 under unsaturated traffic conditions. Technical Report, CSSE04-09. (pp. 1–12). Alabama, USA: Auburn University.
Ross, S. M. (2002). Probability models for computer science. New York: Academic Press.
The network simulator—ns-2. Internet: http://www.isi.edu/nsnam/ns/. Accessed 17 June 2009.
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT & Future Planning (NRF-2012R1A1B4000536).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Joshi, G.P., Nam, S.Y. & Kim, S.W. Decentralized Predictive MAC Protocol for Ad Hoc Cognitive Radio Networks. Wireless Pers Commun 74, 803–821 (2014). https://doi.org/10.1007/s11277-013-1322-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1322-6