Abstract
Energy is vital parameter for communication in Internet of Things (IoT) applications via Wireless Sensor Networks (WSN). Genetic algorithms with dynamic clustering approach are supposed to be very effective technique in conserving energy during the process of network planning and designing for IoT. Dynamic clustering recognizes the cluster head (CH) with higher energy for the data transmission in the network. In this paper, various applications, like smart transportation, smart grid, and smart cities, are discussed to establish that implementation of dynamic clustering computing-based IoT can support real-world applications in an efficient way. In the proposed approach, the dynamic clustering-based methodology and frame relay nodes (RN) are improved to elect the most preferred sensor node (SN) amidst the nodes in cluster. For this purpose, a Genetic Analysis approach is used. The simulations demonstrate that the proposed technique overcomes the dynamic clustering relay node (DCRN) clustering algorithm in terms of slot utilization, throughput and standard deviation in data transmission.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
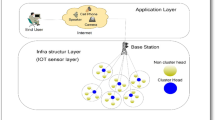
Among the constant developments in technology a prospective invention, IoT is a forthcoming road which is escalating as a universal worldwide computing system where billions of devices will be linked to the Internet [1]. IoT is constantly growing and is a latest exploration area where openings are countless. Due to its countless imaginations, it is placed into an updated and incorporated version instead of the existing procedure of the internet. The count of objects consuming internet facilities is developing each day and connecting all of them by wireless or wire will set as an influential base of evidence at our finger commands. The notion of empowering communication among smart devices and machines is an innovative technology; however, the IoT enabled technologies are not rather original for people [2]. IoT is the term and the method of joining data, acquired from diverse types of objects to any assumed platform on the online network organization [3]. The IoT delivers novel contestants and heritage wireless operators with additional opportunity for transporting connectivity to their clients as shown in Fig. 1.
There are numerous conceivable upcoming presentations that can be of excessive benefit. Following are some of the applications of IoT:-
- (a)
Intelligent transportation system (ITS): Traffic due to vehicles is a significant issue of a society. Therefore, all associated difficulties with it must be correctly given attention. ITS has an essential feature for a system which could reform the transportation cases based on the traffic material retrieved through objects by deployment of IoT technologies [4]. For such innovating schemes, an understanding of a novel methods for automatic monitoring of vehicles and other transportation parameters is very important. For its deployment, there is a requirement of IoT framework with enabling technologies rather than general image processing techniques [5].
- (b)
Smart environment: Forecasting of natural catastrophes such as fire, floods, air pollution, land-sliding, earthquakes, volcanoes, etc. is possible by the use of inventive technologies of IoT. Environment monitoring systems will be available to predict the certain parameters of the disasters which will be helpful in determining the danger beforehand.
- (c)
Smart home: IoT can deliver DIY (Do-It-Yourself) explanations for Smart Home Automation by which remotely controlled appliances will be available as per people’s requirements. Careful monitoring of efficacy meters, water and energy usage will aid in conserving resources and sensing unforeseen overfilling, water leakages, etc.
- (d)
Smart hospitals: Doctors and other supporting staff will be capable of monitoring the blood rate, temperature, heart rate and other patient’s health conditions outside or inside the buildings of the hospital on the time of admission using smart malleable wearable embedded devices with RFID tags that make hospital smart and well-furnished [6].
- (e)
Smart agriculture: Soil nutrition, Humidity, Temperature, etc. can be observed and can help in the improvement of the green housing experiences by automatic adjustment of various parameters to exploit production. Precise fertilization and watering will support in refining the water conserving and quality composting respectively [7].
For large-scale WSNs, the clustering is a key routing method which effectively broadens the network’s lifetime. In this paper, a reactive routing algorithm and neuron structure with transmission principle on the basis of dynamic clustering is proposed. Cluster head is efficiently elected in the occurrence region on the basis of residual energy after the amplification of the event.
The cluster head transmits the collected data back to the end nodes along with the network backbone information. Two types of accumulation methods are devised to increase the efficiency of data collection. In a designed method, data should be periodically transmitted by nodes outside the region if fluctuation is faced by the cluster head. By this cluster head can track the varying speed of the incident due to fluctuation raised in action-threshold. At last the results received from simulation verify that the DCRR algorithm boost ups the life duration of network and changes are adaptable as well as this algorithm has more significant merits under the middle and low load. Numerous fields and applications such as general engineering, disaster and hazards management, biomedical health and habitat monitoring, forest fire detection, animal tracking, commercial applications, seismic detection, homes applications, underwater applications etc. [8] are developed for WSNs. According to article [9] WSNs are considered as the rapid growing technology along with a most leading IoT technologies [10]. The motes known as sensor or sensing nodes are substantial entities characterized by: (1) a battery with defined energy; (2) a processor with restricted processing proficiency; (3) and a transceiver [11]. The sensor nodes can be disposed in supervising areas to collect diversified types of information (e.g., wind, humidity, light, temperature) and then transfer the assembled information to the sink using routing mechanism via multi-hop or single hop communication [12]. The access points or sensor nodes relay that gathered information to the users. However, when WSNs are deployed in distant areas; it is arduous to replace drained batteries [13], which lead to extend WSN lifetime durability crucially. The transceiver is the source of higher energy consumption that used in sensor nodes, and many papers or articles also discussed it in literature [14]. For minimal consumption of energy and the usage of transceiver in an attractive manner, strategies are in development. Clustering is grouping of sensors in numerous clusters in which individual cluster have a respective cluster-head including various cluster members. In dynamic clustering, a sensor node having high energy becomes the cluster head which makes the wireless network more stable. Contribution of the papers is outlined as below:
A literature survey of the existing integration of WSN with IoT is carried out.
Comparative Protocols of WSN are analyzed.
Usage and importance of Genetic Algorithms for Data Transmission is realized and new algorithm is proposed for IoT applications based on routing in WSN.
The proposed approach is validated in terms of throughput and standard deviation.
Rest of the paper is organized as: Sect. 2 throws light on the work done in the recent past by the researchers which is followed by the proposed algorithm in Sect. 3. Results and Discussions are done in the Sect. 4. Lastly, paper is concluded in Sect. 5.
2 Related work
There are many clustering algorithms and mechanisms used in literature such as Hierarchical Clustering [15], Distributed Clustering Algorithm (DCA) [16], Spanning Tree (or BFS Tree) [17], on-Demand Clustering Routing [18], Degree or Lowest Identifier Heuristics [19], Cognitive Routing Protocol for IoT [20], Energy Efficient Clustering Routing [21], Power Efficient And Adaptive Clustering Hierarchy (PEACH) [22], Optimal Energy Aware Clustering [21], Genetic algorithm for IoT [23], Hybrid based Energy- Efficient Distributed Clustering (HEED) [24], Power Aware Dynamic Clustering Protocol (PADCP) [21, 25].
Arboleda et al. [26] reflected some key approaches and gave comparability analysis among the various clustering protocols. In this paper, authors analyzed cluster structure, LEACH-based protocols, cluster types and its advantages along with reactive routing WSNs algorithms. The comparative analysis of these protocols’ characteristics and their uses in different applications were defined.
Kumarawadu et al. [27] identified the feasible clustering WSNs algorithms with CH election norms and cluster formation parameters. The authors also surveyed the challenges and issues related to neighborhood information, biologically inspired, probabilistic that depends on the identity-based clustering algorithms classification.
Jiang et al. [28] introduced clustering schemes and classification methods in WSN to examine three notable merits such as easy maintenance, fewer overheads, and more scalability thorough eight clustering attributes. The authors also figured out various algorithms in clustering such as PEGASIS, HEED, LEACH etc. and comparison of these algorithms was done with numerous attributes.
Authors in [29] presented a study on a simple clustering routing protocol classification to attain energy efficiency from the perspectives of data routing in WSNs. Along with some future research directions, pre-established and on-demand classes of nine clustering algorithms were summarized by authors in this research paper.
In [30] authors discussed the operations, advantages, and demerits of each clustering protocol algorithm briefly. In terms of energy utilization and network’s lifespan, authors surveyed the seven algorithms such as APTEEN, TEEN, LEACH and EEUC etc.
In [31] authors have proposed a survey to summarize nine leading clustering algorithms with their challenges such as EECS, HEED, LEACH, TL-LEACH, EEUC etc. The comparative analysis of these algorithms was done on the behalf of merits such as hop distance, cluster size, CH distribution uniformity, cluster formation approach, residual energy and delay.
To stabilize energy utilization among CHs, a distributed energy-effective unequal (DEU) cluster routing protocol presented in [32]. The DEU clustering protocol integrated the uneven clustering and multi-hop routing methods along with to select highly energy efficient nodes in the network to save energy. CHs considered factors like optimal hop count of candidate nodes, intra-cluster, residual energy and inter-cluster communication and transmission cost to elect RNs.
The above approaches have worked on the parameters of energy, delay, network stability etc. i.e. quality of metrics (QoS) for WSN. They have not considered the network throughput, scalability and reliability for transmitting the data which is required for IoT applications.
Certainly, literature exists in abundance for WSN software platforms related to the various domains of IoT applications. In [33] an architectural reference model (ARM) is specified within the project named IoT-A. The key concepts and functional groups of truly existing IoT platforms and scenarios are defined in [33] and have discussed about developing a domain and a functional model. For example, authors [34, 35] went through interoperability in IoT based scenarios with the use of designed guidelines of IoT based ARM and by defining acceptable IoT web-enabled technologies.
In the above approaches of IoT, authors have not considered the scalability, fault tolerance and load balancing. The proposed approach has shown the network throughput and slot utilization over 800 data transmissions which can be increased as per the network area. Moreover, it is considering standard deviation in the data transmission to validate it for the IoT.
As interoperability is an important facet, undeniably heterogeneity or cross-section is also one of the main threats to be directed in IoT environments. To virtualize the real-world entities, IoT ARM-based platform is introduced in this research. Data collected by the latent sensors or actions performed by underlying actuators exposed entities in a conceptual manner. A case is defined, in which Parking lots and holding space is monitored by sensors. Scalability is another issue that becomes the important aspect of IoT based platforms and scenario is also proposed. In [36] this approach works within the VITAL project. According to smart city scenario, authors have [37] considered an approach to define the main challenges namely; homogenization, resources management, and services exposure arise by these resources. Authors are working on the integration of WSN and IoT protocols [38, 39] which is raising challenge for the already existing protocols. Despite these facts, the proposed approach presented in only as a design concept. However, it does not give the working of each component of architecture, their implementation and deployed nature. The work proposed in the paper has elaborated the results retrieved after the implementation of the proposed algorithm.
3 Proposed algorithm
Recent work or research in IoT classified in terms of platform, network, devices and layers. For WSNs integrated with IoT, we focused on design and network planning with the use of dynamic clustering approach based genetic algorithm (GA). An IoT application performs well and seamlessly with well-designed IoT network architecture. Without it, IoT devices do not provide useful information and services to the end users. A novel architecture with some predictable techniques such as grouping, security and privacy, network and connection management is introduced in this research. Many other technologies as WSN, near field communications (NFC), machine-to-machine (M2M), personal area networks (PAN) such as Wi-Fi, cellular, Bluetooth etc. and body area networks (BAN) are also included in the IoT era.
3.1 Challenges and prospect of IoT
As IoT nodes should be united, extensive and flawless so it needs set up of high scale services formation within agreed standards to gives high impacts to the services related to different applications or scenarios and user requirements. Although IoT application development is a continuous process, still there are plentiful issues such as cost, power, computing, low latency, self-organization, dispersed intelligence and systems technology which need to be solved.
- (a)
Challenges of IoT
Though IoT brings many new connections and opportunities to end users as well as to the industry insights to various application areas, still it lacks in efficient architecture and technology set of standards that connects the real and virtual world in an allied framework [38]. Some of the key challenges are listed as following.
- (1)
Architecture challenge: Emerging of various sensors (e.g. physical, chemical, biometric and camera sensors), smart interlinked devices and intense far-reaching technologies involved in IoT applications depend on various fields and their architecture or scenario. Moreover, the communications between these interconnected devices are in a wireless, ad hoc and in an automatic manner. It makes the architecture services more decentralized, mobile and complicated.
- (2)
Technical challenge: Although different application areas need different scenarios and architectures, therefore, different technologies are to be developed, related to the services that make the IoT complex. In this way, heterogeneous becomes one of the major challenges in smart IoT environments.
- (3)
Hardware challenge: IoT equips smart systems with smart devices. To exploit the communication between the devices, speedy deployment and services of IoT applications are required. For this reason, researchers focus on hardware design like a wireless trackable system which is cost-effective, low size and highly functional.
GA is generally used to achieve high-quality solutions for search. To optimize the problems with historical data and to address the search for better performance is mostly accomplished by the efficient GAs as these algorithms are based on genetics and natural selection. The term natural selection means completion of tasks by those species who can adapt to changes occurring in an environment for surviving in next generation and to reproduce the new species. These algorithms pretend “survival of the fittest” as each generation consists of a population of individuals and each individual depicts a search space point along with attainable manner of integer/floats/string/bits/character, similar to the chromosome.
The GAs preserved the population of n individuals in addition to their fitness scores, means who has the ability to compete; a fitness score is given to that individual. Those who have better scores, mate and generate better descendant by bringing together chromosomes of parents. They are selected to reproduce more as compared to other individuals. As the size of a population is static and some of the individuals die, so a room has to be formed for the new generation for replacement of the old ones with new arrivals when all mating opportunities are expanded. When a least fit dies, it is assumed that superior solutions will be succeeded as each new generation has better genes.
Better genes are more efficient than the average genes besides having partial solutions as compared to the solutions of former generations. The population is said to converge when there is no considerable difference originated by off-springs comparable to previous populations. Therefore, the GA is also said to converge as a set of solutions for the problem.
- (b)
Operators of Genetic Algorithms
The following operators are involved in algorithm for new generation of off-springs after the creation of primary generation:–
(1) Selection operator: In this, the one who has finer fitness scores, are selected to transmit their heredity to the succeeding generations. Preferences are given to the fittest off-spring.
(2) Crossover operator: This gives the idea of mating between individuals based on crossover sites and selection operator which are chosen randomly. Thus to create a completely new offspring, the genes at crossover sites are need to exchanged. For example:
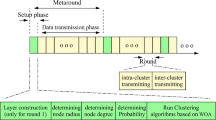
These operations determine an efficient solution of exploration of all-around search space and focus to cover to the global space (Fig. 2). A fitness function is used to measure the quality of solution. The system flow chart is shown in Fig. 3.
3.2 Fitness of heredity
The fitness of heredity is introduced to reduce consumption of energy along with this, the network existence is also expanded. In this section, some of the fitness related parameters are described.
- (1)
Direct distance (DD) to base station (BS): The term DD to BS is defined as the aggregation of the overall area or gap from sensing nodes to the BS (Eq. 1). This gap or distance is defined as follows (Eq. 1):
$$DD = \sum\limits_{i = 1}^{m} {d_{is} }$$(1)whereas d = distance, i = ith node and s = base station sth node. dis is the distance among two nodes, node i and node s respectively. To make nodes as energy efficient in larger networks, the distance should be minimized to avoid wastage of energy of nodes.
- (2)
Cluster distance (C): The total area covered by nodes to the cluster head and the area covered from the head or top to BS node is defined as the term cluster distance (Eq. 2). The C is defined as following with member of K collection of nodes (Eq. 2).
$$C = \sum\limits_{i = 1}^{k} {d_{ih} } + d_{hs}$$(2)d = distance, i = node i and h = head of cluster. C is defined as the distance and gap covered from i to the h, Hence dhs defined as the distance between these two nodes.
- (3)
Cluster distance—standard deviation (SD): The cluster distances deviations should be small for consistently placed and structural distribution of sensor nodes. But for node allocations at random and in non-uniformly areas, distances must not be same. The computation of cluster gaps, SD (Eqs. 3 and 4), along with µ deviation done as follows:
$$\mu = \frac{{\sum\nolimits_{i = 1}^{h} {d_{cluster} } }}{h}$$(3)$$SD = \sqrt {\sum\limits_{i = 1}^{h} {(\mu - d_{clusteri}^{{}} } } )^{2}$$(4) - (4)
Transfer energy (E): Transfer energy E; define as the consumed energy to pass the entire message from the cluster head node to the BS node. With amount of K member cluster nodes, transfer energy is described as follow (Eq. 5)
$$E = \sum\limits_{j = 1}^{k} {E_{Tjh} } + k + E_{R} + E_{ths}^{{}}$$(5)The first term of Eq. 5 depicts the absorbed energy to transfer messages from K nodes to head. The term second shows the energy carried by the head node of cluster to receive number of K messages from the cluster representative nodes. Finally, the third one term presents the transmission energy absorbed through BS node to the cluster head point.
- (5)
Number of transmissions (T): For each stage for transferring data, BS assigns the number of transmissions T and the value of transmissions should be adapted in accordance to the presented energy levels and network conditions. In this way the values of T is not determined and the GA outcome will be used for longest time duration.
- (6)
Fitness function: All the introductory fitness parameters and aspects of genes fitness function F is defined below as (Eq. 6):
$$F = \sum\limits_{i} {w_{i} } *f_{i,\forall } f_{i} \varepsilon (C,DD,E,SD,T)$$(6)The primary fitness aspects can be ascribed the erratic impact, wi. The best fit chromosome is assessed after every generation.
4 Results and discussion
In our simulation system, 100 nodes of a network are systematically dispersed in a region of 100 × 100 m2. Simulations are carried out in MATLAB. Let t0 denotes the transmission time to begin. The transmission said to be successful as long as there is no other transmission begins during (t0 − 1, t0 + 1). Setting s = 2 (since the interval length is 2) and k = 0 in our Poisson formula1 we have P0 = \(e^{ - 2G}\) (Eq. 7):-
Setting \(ds/dG = 0\), we say S is maximum when G = 0.5, and on that time period S = 1/2e.
It is evident from the Fig. 3 that the best-case utilization of DCRN –GA(Curve in green)is best as compared to Previous methods i.e. LEACH And DCRN.
Comparison results in terms of a number of packets received to cluster head and a base station are shown in graphs (Figs. 4, 5 and 6). Figure 4 shows that in DCRN-GA protocols’ cluster head receives 3*104 packets from nodes as equating to DCRN packets to cluster head are 2*104. In basic LEACH packets to cluster head decreased to 1*104. It is noticed that DCRN-GA protocol executes much better than DCRN and LEACH protocols. Packets received at the base station are 1400 in case of DCRN-GA and 1000 packets are received at a base station in case of DCRN while only 800 packets are received in case of leach protocol as shown in Fig. 5. Therefore, it is observed that Dynamic clustering routing using Genetic algorithm is best for Network planning and design in Wireless Sensor Networks for IoT applications.
Figure 7 shows the standard deviation (SD) in terms of slot utilization, transmission of data packets to the BS and transmission of data packets to the cluster head. SD of DCRN is higher in slot utilization and packets transmission to the BS which is not suitable for IoT applications. Sensor nodes should be equally capable of utilizing the data transmission channels. However, comparison shows that newly proposed algorithm works efficiently and its SD is less as compare to both traditional approaches except in data transmission to the CH. Data transmitted to the CHs is sent to the BS only, therefore SD should not be high in later case. In IoT applications data is transmitted through the huge amount of heterogenous devices where each device should be able to use the channel in efficient manner. High SD affects the channel utilization in adverse manner while transmitting data to the BS. This case makes the proposed scheme more suitable to the IoT applications.
5 Conclusion
In this work, to optimize the performance metric of WSNs, a generic Dynamic clustering routing approach based on GA is proposed which aid the escalation of both theoretical analyses as well as the models based on simulations for IoT applications. On the basis of Fitness function performance metrics, high availability and efficiency have been improved in the framework and the results received are compared via inexhaustive simulations. It is observed that DCRN-GA is a far better approach as compared to previously used approaches and will be a new revolution in IoT applications in the term of network planning. In the further work, to make each metric strictly at the same scale is still a challenge on the basis of optimization of weighted sum. Besides, the whole assessment process of framework could enhance with the expansion of System C-based simulations where a huge size of population and generations are employed.
References
Rafiullah, K., & Sarmad, U. K., Rifaqat, Z., & Shahid, K. (2012). Future internet: The internet of things architecture, possible applications and key challenges. In Proceedings of frontiers of information technology (FIT), 2012, pp. 257–260.
Guicheng, S., & Bingwu, L. (2011). The visions, technologies, applications and security issues of internet of things. E-Business and E -Government (ICEE), 2011, pp. 1–4.
Ling-yuan, Z. (2012). A security framework for internet of things based on 4G communication. In Computer science and network technology (ICCSNT), 2012, pp. 1715–1718.
Cao, Y., Li, W., & Zhang, J. (2011). Real-time traffic information collecting and monitoring system based on the Internet of Things. In Pervasive computing and applications (ICPCA), 2011, 6th international conference, pp. 45–49.
Xiao, L., & Wang, Z. (2011). Internet of Things: A new application for intelligent traffic monitoring system. Journal of Networks,6(6), 887.
Fuhrer, P., & Guinard, D. (2006). Building a smart hospital using RFID technologies: Use cases and implementation. Fribourg: Department of Informatics-University of Fribourg.
TongKe, F. (2013). Smart agriculture based on cloud computing and IoT. Journal of Convergence Information Technology (JCIT), 8(2).
Wu, H., Chen, X., Xiao, Y., & Xu, M. (2012). An acoa-afsa fusion routing algorithm for underwater wireless sensor network. International Journal of Distributed Sensor Networks,8(5), 4110–4118.
Ilyas, M., & Mahgoub, I. (2012). Handbook of sensor networks: Compact wireless and wired sensing systems. Boca Raton, FL: CRC Press LCC.
Jianbin, X., Ting, Z., Yan, Y., Wenhua, W., & Songbai, L. (2013). Cooperation-based ant-colony algorithm in wsn. Journal of Networks, 8(4).
Mekkaoui, K., & Rahmoun, A. (2011). Short-hops versus long-hops—energy efficiency analysis in wireless sensor networks. In CIIA 2011: Proceedings of the third international conference on computer science and its applications (CIIA11), University of Saida, Algeria, pp. 13–15.
Akyildiz, I. F., & Vuran, M. C. (2010). Wireless sensor networks. (Vol. 4). Hoboken: Wiley. https://doi.org/10.1002/9780470515181
Chakraborty, A., Mitra, S. K., & Naskar, M. K. (2011). A genetic algorithm inspired routing protocol for wireless sensor networks. International Journal of Computational Intelligence Theory and Practice, 6(1).
Odey, A. J., & Li, D. (2012). Low power transceiver design parameters for wireless sensor networks. Wireless Sensor Network,4(10), 243–249.
Mahmood, D., Javaid, N., Mahmood, S., Qureshi, S., Memon, A. M., & Zaman, T. (2013). MODLEACH: A variant of LEACH for WSNs, pp. 123–128.
Angel Latha Mary, S., Sivaganesan, D., & Vinothkumar, R. (2015). An empirical research of dynamic clustering algorithms. ARPN Journal of Engineering and Applied Sciences,10(9), 33–35.
Ma, W., Cao, Y., Wei, W., Hei, X., & Ma, J. (2015). Energy-efficient collaborative communication for optimization cluster heads selection based on genetic algorithms in wireless sensor networks. International Journal of Distributed Sensor Networks,2015, 396121.
Baranidharan, B., & Santhi, B. (2015). GEACH: Genetic algorithms based energy efficient clustering hierarchy in wireless sensor networks. Hindawi Publishing Corporation Journal of Sensors,2015,715740.
Eiben, A. E., & Smith, J. E. (2003). Introduction to evolutionary computing., Natural Computing Series Berlin: Springer.
Al-Turjman, F. (2019). Cognitive routing protocol for disaster-inspired internet of things. Future Generation Computer Systems,92, 1103–1115.
Huyuh, T. T., Dinh-Due, A., & Tran, C. H. (2013). Balancing latency and energy efficiency in wireless sensor networks: A comparative study. In IEEE international conference on computing, management and telecommunication, pp. 181–186.
Akojwar, S. G., & Patrikar, R. M. (2008). Improving life time of wireless sensor networks using neural network based classification technique with cooperative routing. International Journal of Communications,2(1), 75–86.
Deng, X., Jiang, P., Peng, X., & Mi, C. (2019). An intelligent outlier detection method with one class support tucker machine and genetic algorithm toward big sensor data in Internet of Things. IEEE Transactions on Industrial Electronics,66(6), 4672–4683.
Deepak, G., & Malay Ranjan, T. (2012). Routing protocols in wireless sensor networks: A survey. In IEEE international conference on advanced computing and communication technologies, pp. 474–480.
Suraj, S., & Sanjay Kumar, J. (2011) A survey on secure hierarchical routing protocols in wireless sensor networks. In ICCCS, 11 February 12–14, pp. 146–151.
Arboleda, L. M. C., & Nasser, N. (2006). Comparison of clustering algorithms and protocols for wireless sensor networks. In Proceedings of IEEE CCECE/CCGEI, Ottawa, ON, Canada, 7–10 May 2006, pp. 1787–1792.
Kumarawadu, P., Dechene, D. J., Luccini, M., & Sauer, A. (2008). Algorithms for node clustering in wireless sensor networks: A survey. In Proceedings of 4th international conference on information and automation for sustainability, Colombo, Sri Lanka, 12–14 December 2008, pp. 295–300.
Jiang, C., Yuan, D., & Zhao, Y. (2009). Towards clustering algorithms in wireless sensor networks—a survey. In Proceedings of IEEE wireless communications and networking conference, Budapest, Hungary, 5–8 April 2009, pp. 1–6.
Maimour, M., Zeghilet, H., & Lepage, F. (2010). Cluster-based routing protocols for energy-efficiency in wireless sensor networks. Sustainable Wireless Sensor Networks, INTECH, 167–188.
Lotf, J. J., Hosseinzadeh, M., & Alguliev, R. M. (2010). Hierarchical routing in wireless sensor networks: A survey. In Proceedings of 2010 2nd international conference on computer engineering and technology, Chengdu, China, 16–18 April 2010, pp. 650–654.
Boyinbode, O., Le, H., & Mbogho, A. (2010). A survey on clustering algorithms for wireless sensor networks. In Proceedings of 2010 13th international conference on network-based information systems, Takayama, Japan, 14–16 September, 2010, pp. 358–364.
Zhang, C., Liu, F., & Wu, N. (2014). A distributed energy-efficient unequal clustering routing protocol for wireless sensor networks. International Journal of Computational Information Systems,10(6), 2369–2376.
Bassi, A., Bauer, M., Fiedler, M., Kramp Van Kranenburg, T., et al. (Eds.). (2013). Enabling things to talk: Designing IoT solutions with the IoT architectural reference model. Berlin/Heidelberg: Springer.
Krco, S., Pokric, B., & Carrez, F. (2014). Designing IoT architecture(s): A European perspective. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, pp. 6–8 March 2014.
Kiljander, J., D’elia, A., Morandi, F., Hyttinen, P., et al. (2014). Semantic interoperability architecture for pervasive computing and internet of things. IEEE Access,2, 856–873.
Petrolo, R., Loscri, V., & Mitton, N. (2014). Towards a cloud of things smart city. IEEE COMSOC MMTC E Lett,9, 44–47.
Vögler, M., Schleicher, J. M., Inzinger, C., Dustdar, S., & Ranjan, R. (2016). Migrating smart city applications to the cloud. IEEE Cloud Computing,3, 72–79.
Kuo, Y. W., Li, C. L., Jhang, J. H., & Lin, S. (2018). Design of a wireless sensor network-based IoT platform for wide area and heterogeneous applications. IEEE Sensors Journal,18(12), 5187–5197.
Kim, J. W., Yi, J. H., & Seo, C. (2018). Distributed quality of service routing protocol for multimedia traffic in WiMedia networks. Wireless Networks,24(8), 2835–2849.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rani, S., Ahmed, S.H. & Rastogi, R. Dynamic clustering approach based on wireless sensor networks genetic algorithm for IoT applications. Wireless Netw 26, 2307–2316 (2020). https://doi.org/10.1007/s11276-019-02083-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-019-02083-7