Abstract
Mainly because of resource restrictions in wireless sensor networks (WSNs), extending the lifetime of the network, has gained significant attention in the last several years. As energy becomes a quite challenging issue in these networks, clustering protocols are employed to deal with this problem. One of the main research areas in cluster-based routing protocols is fair distribution and balancing the overall energy consumption in the WSN, by selecting the most suitable cluster heads (CHs). In order to reduce the energy consumption and enhancing the CHs selection process a new routing protocol based on fuzzy logic has been proposed. There exist several algorithms based of fuzzy logic to select the most proper CHs for the network. But these algorithms do not consider all the important parameters and information of the sensor nodes in order to guarantee the optimal selection of the CHs. In The proposed algorithm, a two-step fuzzy logic system is used to select the appropriate CHs. The selection of CHs is based on six descriptors; residual energy, density, distance to base station, vulnerability index, centrality and distance between CHs. The result of the simulation indicates that, the proposed algorithm performs better comparing with some other similar approaches in case of fair distribution and balancing of the overall energy consumption.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Wireless sensor networks (WSNs) mainly because of wide variety of applications [1] as well as future potential such as integration into ‘Internet of Things’ [2–7] has received a significant attention over the past decade. Typically these type of networks, which might have different topologies [8, 9], are made of a large number of tiny battery-powered sensor nodes (SNs). The primary task of the SNs is to sense and collect data from their surrounding environment. The collected data by the SNs are needed to be sent to the base station (BS) which acts as a bridge between remote users and WSN. Due to huge number of SNs, distributed usually in inaccessible locations, recharging or replacing of sensors’ batteries are impractical. Therefore the energy management and extending the lifetime of network could be addressed as the main challenges associated with these type of networks. In [10] authors designed and implemented a house-build experimental platform, called energy management system for wireless sensor networks (EMrise) for management of the energy and exploration on WSNs.
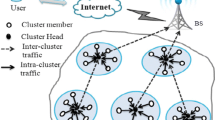
Transmission of data to the BS is undoubtedly one of the major energy consuming task [11]. Consequently in this regard various energy efficient algorithms [12–18] have been designed and improved. Clustering is one of the popular techniques which is adopted to reduce the energy consumption of the WSNs by decreasing the number of transference within the network. In clustering the WSN is divided into number of clusters and each cluster is allocated a cluster head (CH) which receives the data from its members and forwards them to the BS. Figure 1 gives a picture of a typical WSN along with the components of a SN.
Choosing appropriate CHs by carefully considering various factors associated with each SN could result in minimizing the energy consumption to a significant degree and consequently prolonging the network’s lifetime. Low energy adaptive clustering hierarchy (LEACH) [19] is the earliest and most propounded clustering algorithms which was introduced more than a decade ago. In LEACH the network area is randomly divided into pre-determined number of clusters and each cluster is assigned a CH. CHs are elected and changed randomly after specific time intervals. A node will be re-elected only if all the other candidates have been elected. Due to random selection of CHs in LEACH without considering vital information of nodes such as location, remaining energy, distance from base station etc. it might result in improper distribution (CHs will be close to one another) or inappropriate selection (e.g. Nodes with low energy) of CHs.
Popular methods such as fuzzy logic (FL) and genetic algorithm (GA) have been employed in various novel and existing algorithms to enhance the process of CHs election. In this paper a new routing protocol based on fuzzy logic is proposed, where a two-step FL system is used to select the appropriate CHs in order to reduce the energy consumption and extending the lifetime of the network. In first-step of the proposed algorithm, the main factors of each SN such as residual energy, density and distance to BS are checked and according to the output, most suitable candidates are selected. Furthermore in the second-step of FL system the vulnerability index, centrality and distance between CHs are checked and according to the output the CHs will be elected. In the proposed fuzzy system the usage of vulnerability index as a parameter for each sensor node has been introduced which assures the availability of the network as the nodes with high vulnerability index has a fewer chance to be chosen as the CHs. Centrality and distance between CHs are other factors which are checked to promise proper distribution of CHs within the network. The result of the simulation indicates that the proposed algorithm performs better in case of fair distribution and balancing of the overall energy consumption comparing with other famous existing protocols.
The reminder of paper is as follows. The related work is discussed in Sect. 2, system model is clarified in Sect. 3, the Sect. 4 includes the proposed model, the result of our simulation is given in Sect. 5 and finally conclusion of our work is presented in Sect. 6.
2 Related work
Several works regarding the wireless sensor and wireless networks are found in the literature [20–25]. In an effort to enhance the energy consumption of WSNs various techniques, such as data communication protocols [26–31], data collection [32–35], data aggregation [36–38] and coverage of the network [39–41] have been employed. LEACH protocol [19] which is the most primitive clustering-based algorithm was designed to reduce the energy consumption and prolonging the WSNs lifetime. In LEACH protocol, SNs are randomly arranged into pre-determined number of clusters and each cluster is allocated a CH at each round. To become a CH, a random number (between 0 and 1) is generated by each SN. SNs having generated numbers less than the threshold T(n) (Eq. 1), will become CHs for that specific round. Randomized rotation of CHs are used to avoid draining the energy of a single SN. Re-election of a SN as a CH will be possible only if all the other candidates have been elected.
where, p stands for ratio of CHs in the WSNs (the value of p is obtained through dividing the expected number of CHs in the current round by the number of nodes in WSN), r indicates the round number and M represents the set of SNs which have not been chosen as CH in the last 1/p rounds (if n ∉ M, it won’t become a CH for that specific round as the T(n) value for that node would be set to 0).
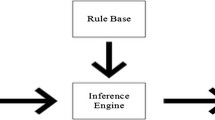
As it was mentioned earlier, because the CHs are randomly chosen in LEACH without considering important characteristics of SNs, it could result in inappropriate distribution or improper selection of CHs. FL is a decision system technique which works similar to human logic [42] offers a simple method to reach at a confident decision based upon unclear, vague, imprecise, or absent input information. FL system with its essential components are shown in Fig. 2.
In [43], FL is used to select CHs based on three fuzzy variables, node’s energy, concentration and centrality. In each round there is only one chosen CH whereas balancing the energy consumption and extending the network lifetime required more CHs to be selected.
Based on FL control in [18] a new routing protocol to extend the lifetime and throughput of WSNs has been proposed. The distance between cluster heads is not considered which might lead into improper distribution of CHs within the network. Nodes’ density, nodes’ battery level and distance of nodes form the base station are the only parameters used to select the CHs. Similarly authors in [44] present a fuzzy decision-making approach to select the appropriate CHs by using three criteria including density, distance from the BS and energy level of the nodes. In [45] authors propose a FL based energy-aware dynamic clustering technique which uses just only two inputs (node’s centrality and residual energy) and not considering many of other possible parameters (such as distance between cluster heads, vulnerability index etc.), in order to improve lifetime of the WSN in terms of last node dies (LND).
More in [46], an energy efficient clustering algorithm has been proposed for WSNs based on FL concept. The selection of CHs is done according to a threshold value. Then among the selected CHs based on some fuzzy input parameters (remaining battery power, mobility and centrality) a CH will be selected as a super cluster head (SCH) which will be responsible for sending data to the BS. The main issue with this algorithm is the absent of checking the vulnerability of the SCH as it acts as the main node to send data to BS.
In [47], to compute the chance for a node to become the CH, two fuzzy parameters, node’s energy and local distance are computed. In every round, SNs generate a random number and if the generated number is smaller than predefined threshold, the chance is calculated for the SNs. Therefore, some suitable nodes may not get selected because of this random number.
In this paper a new routing protocol based on LEACH is proposed, where a two-step FL based algorithm is used to select the appropriate CHs. The main difference of this algorithm with the existent ones, is the number of parameters involved to select the ideal CHs. the proposed algorithms uses six parameters (residual energy, density and distance to BS, vulnerability index, centrality and distance between CHs) which guarantees the ideal selection of CHs. Consideration of vulnerability index for each SN enhances the availability of the WSN as SNs having high vulnerability index have less chance to be chosen as the CHs.
3 System model
Few basic assumptions are made about the sensor nodes, which are deployed to monitor an environment. These assumptions are as follows:
-
1.
WSN contains homogeneous SNs, having equivalent initial energy.
-
2.
SNs are deployed randomly.
-
3.
SNs and BS are kept stationary once deployed.
-
4.
All the SNs have battery-limited power and battery recharge is impractical.
-
5.
The distance of SNs from BS and other nodes is computed based on the strength of signals.
A simplified model [48] for radio energy dissipation is used which has been depicted in Fig. 3 and explained next.
Radio energy dissipation model [48]
The consumed energy for transmitting an l-bit message over the distance d, can be calculated with Eq. (2).
The Eelec, ℰfs and ℰmp are the electronics energy and the amplifier energy in free space and multipath respectively. And receiving this message will consume:
4 Proposed algorithm
Proposed algorithm uses FL system that is composed of two main steps in order to select the CHs. In the first step of FL system nodes are selected if they are in the proper locations with respects to the energy concerns. Furthermore in the second step, the level of vulnerability, centrality and desired distance between CHs of all the nodes (selected in the first step) are checked and according to the output, CHs will be elected. The second-step of the FL system enhances the availability of the network as the node with high vulnerability have less chance to be elected as CHs. The proposed FL system is explained in details as follows:
4.1 First-step of FL system
As we mentioned before the first step of the FL system selects the nodes based on their location and energy level. This step attempts, that nodes with adequate residual energy and proper location will be selected for further consideration. The input functions named, residual energy, node density and distance to BS are used to convert the crisp inputs into fuzzy sets. Different membership function is used to illustrate the different level of the input functions as shown in Table 1 as well as Figs. 4, 5 and 6.
The output (fuzzy cost) of the first-step FL system, shows the probability level for each node to be chosen for further consideration in next step. The output function along with its membership functions are shown in Table 2 and Fig. 7.
The fuzzy if–then rules which are mostly based on experience and knowledge of experts in that domain, and relationship among the fuzzy input variables are given in Table 3 and Fig. 8 respectively.
4.2 Second-step of FL system
In the second-step of FL system the qualified nodes (selected in first-step) are re-evaluated and checked based on three parameters: vulnerability index, centrality and distance between CHs. The main purpose of this step is to enhance the availability of network by considering vulnerability index (Nodes with high vulnerability index have lesser chance to be elected as CHs) and proper distribution of CHs by checking their distances. Input functions of second-step of FL system along with their different membership functions are given in Table 4, Figs. 9, 10 and 11 as well.
The output (fuzzy cost) of second-step FL system, shows the possibility of SNs to be chosen as CHs. Figure 12 and Table 5 depict the output function along with its membership functions.
The relationship among the fuzzy input variables (vulnerability index, centrality and distance between CHs), and fuzzy if–then rules in the second-step FL system have been given in Fig. 13 and Table 6 respectively.
5 Simulation and evaluation
Simulations are performed in order to verify the efficiency of the proposed algorithm. The simulation environment comprises of two different scenarios, 60 homogenous SNs deployed randomly over 120 × 120 and 60 × 60 m2 networks. Each SN has an initial energy of 0.1 J. In our experiment the communication energy parameters are set as Eelec = 50 nJ/bit, ε fs = 10 pJ/bit/m2 and ε mp = 0.0013 pJ/bit/m4 and energy for data aggregation is set as E DA = 5 nJ/bit/signal. The proposed algorithm has been compared against LEACH [19], GUPTA [43] and CHEF [47] in case of network’s lifetime, energy dissipation and variance of energy.
The number of alive nodes with regard to network’s operation for each scenario, have been given in Figs. 14 and 15. Regarding the death time of first node, it’s well observed that, the proposed algorithm performs much better in both of the cases. However while the network size is 120 × 120 m2, the CHEF algorithm achieves slightly better performance than the proposed and other algorithms regarding the death of last node as it’s shown in Fig. 15.
To verify the energy effectiveness of the proposed algorithm, the residual energy of the WSN in each round has been analysed. The Figs. 16 and 17 compare the energy dissipation of different protocols. Considering these figures it’s found that in both of the situations (network size of 60 × 60 and 120 × 120 m2) the curve of the proposed algorithm is smother than the rest of protocols, which verifies its better performance in case of fair distribution and balance of the overall energy.
Another way to validate the reasonable consumption of the energy within the WSNs, is to study the variance of overall energy with regard to network’s operation. Having slighter variance of residual energy confirms a reasonable energy consumption. The Figs. 18 and 19 depict the variance of energy in both of the scenarios in different rounds. In both of the cases, the proposed algorithm appears to have smaller variance of energy.
6 Conclusion
In this paper, a new routing protocol based on fuzzy logic is proposed, where a two-step FL system is used to select the most appropriate sensor nodes as CHs. The cluster heads nodes selection is based on six descriptors; residual energy, density and distance to BS, vulnerability index, centrality and distance between CHs. Conceptually There exist several algorithms based of fuzzy logic. But it is realized that they do not take into account all the significant information of the sensor nodes in order to guarantee the optimal selection of the CHs. Comparison of our proposed routing protocol against some other similar approaches indicates that, the proposed algorithm performs better in case of fair distribution and balancing of the overall energy consumption. Additionally the result shows a smaller variance of energy for the proposed algorithm which also validates its reasonable consumption of the energy.
References
Arampatzis, T., et al. (2005). A survey of applications of wireless sensors and wireless sensor networks. In Proceedings of the 2005 IEEE International Symposium on Intelligent Control, 2005, Mediterranean Conference on Control and Automation (pp. 719–724), 27–29 June 2005.
Qin, Y., et al. (2016). When things matter: A survey on data-centric internet of things. Journal of Network and Computer Applications, 64(2016), 137–153.
Gubbi, J., et al. (2013). Internet of things (IoT): A vision, architectural elements, and future directions. Future Generation Computer Systems, 29(7), 1645–1660.
Sheng, Z., et al. (2013). A survey on the ietf protocol suite for the internet of things: Standards, challenges, and opportunities. IEEE Wireless Communications, 20(6), 91–98.
Jing, Q., et al. (2014). Security of the internet of things: Perspectives and challenges. Wireless Networks, 20(8), 2481–2501.
Whitmore, A., et al. (2015). The internet of things—A survey of topics and trends. Information Systems Frontiers, 17(2), 261–274.
Yan, Z., et al. (2014). A survey on trust management for internet of things. Journal of Network and Computer Applications, 42(2014), 120–134.
Li, M., et al. (2013). A survey on topology control in wireless sensor networks: Taxonomy, comparative study, and open issues. Proceedings of the IEEE, 101(12), 2538–2557. doi:10.1109/JPROC.2013.2257631.
Zhang, X. M., et al. (2015). Interference-based topology control algorithm for delay-constrained mobile ad hoc networks. IEEE Transactions on Mobile Computing, 14(4), 742–754. doi:10.1109/TMC.2014.2331966.
Zhu, N., & Vasilakos, A. V. (2015). A generic framework for energy evaluation on wireless sensor networks. Wireless Networks. doi:10.1007/s11276-015-1033-x.
Tamandani, Y. K., & Bokhari, M. U. (2015). The impact of sink location on the performance, throughput and energy efficiency of the WSNs. In 2015 4th International Conference on Reliability, Infocom Technologies and Optimization (ICRITO) (Trends and Future Directions), Noida (pp. 1–5). doi:10.1109/ICRITO.2015.7359244.
Yao, Y., et al. (2015). EDAL: An energy-efficient, delay-aware, and lifetime-balancing data collection protocol for heterogeneous wireless sensor networks. IEEE/ACM Transactions on Networking, 23(3), 810–823.
Chilamkurti, N., et al. (2009). Cross-layer support for energy efficient routing in wireless sensor networks. Journal of Sensors. Article ID 134165. doi:10.1155/2009/134165.
Liu, Y., et al. (2010). Multi-layer clustering routing algorithm for wireless vehicular sensor networks. IET Communications, 4(7), 810–816. doi:10.1049/iet-com.2009.0164.
Li, P., et al. (2014). Reliable multicast with pipelined network coding using opportunistic feeding and routing. IEEE Transactions on Parallel and Distributed Systems, 25(12), 3264–3273. doi:10.1109/TPDS.2013.2297105.
Saleem, M., et al. (2012). BeeSensor: An energy-efficient and scalable routing protocol for wireless sensor networks. Information Sciences, 200, 38–56.
Bhuiyan, M. Z. A., et al. (2015). Local area prediction-based mobile target tracking in wireless sensor networks. IEEE Transactions on Computers, 64(7), 1968–1982. doi:10.1109/TC.2014.2346209.
Tamandani, Y. K., & Bokhari, M. U. (2016). SEPFL routing protocol based on fuzzy logic control to extend the lifetime and throughput of the wireless sensor network. Wireless Networks, 22(2), 647–653.
Heinzelman, W., et al. (2000). Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, 2000. IEEE.
Xiao, Y., et al. (2012). Tight performance bounds of multihop fair access for MAC protocols in wireless sensor networks and underwater sensor networks. IEEE Transactions on Mobile Computing, 11(10), 1538–1554. doi:10.1109/TMC.2011.190.
Dvir, A., & Vasilakos, A. (2010). Backpressure-based routing protocol for DTNs. ACM SIGCOMM Computer Communication Review, 40(4), 405.
Vasilakos, A., et al. (2011). Delay tolerant networks: Protocols and applications. Boca Raton: CRC Press.
Lopez-Perez, D., et al. (2013). On distributed and coordinated resource allocation for interference mitigation in self-organizing LTE networks. IEEE/ACM Transactions on Networking, 21(4), 1145–1158.
Vasilakos, A., et al. (2015). Information centric network: Research challenges and opportunities. Journal of Network and Computer Applications, 52(2015), 1–10.
Yang, M., et al. (2014). Software-defined and virtualized future mobile and wireless networks: A survey. Mobile Networks and Applications., 20(1), 4–18.
Sindhwani, N., & Vaid, R. (2013). VLEACH: An energy efficient communication protocol for WSN. Mechanica Confab, 2(2), 79–84.
Zeng, Y., et al. (2012). Directional routing and scheduling for green vehicular delay tolerant networks. Wireless Networks, 19(2), 161–173.
Mehmood, A., et al. (2015). Energy-efficient multi-level and distance-aware clustering mechanism for WSNs. International Journal of Communication Systems, 28(5), 972–989.
Han, K., et al. (2013). Algorithm design for data communications in duty-cycled wireless sensor networks: A survey. IEEE Communications Magazine, 51(7), 107–113. doi:10.1109/MCOM.2013.6553686.
Ganesh, S., & Amutha, R. (2013). Efficient and secure routing protocol for wireless sensor networks through SNR based dynamic clustering mechanisms. Journal of Communications and Networks, 15(4), 422–429.
Meng, T., et al. (2015). Spatial reusability-aware routing in multi-hop wireless networks. IEEE TMC. doi:10.1109/TC.2015.2417543.
Xiang, L., Luo, J., & Rosenberg, C. (2013). Compressed data aggregation: Energy-efficient and high-fidelity data collection. IEEE/ACM Transactions on Networking (TON), 21(6), 1722–1735.
Yao, Y., Cao, Q., & Vasilakos, A. V. (2015). EDAL: An energy-efficient, delay-aware, and lifetime-balancing data collection protocol for heterogeneous wireless sensor networks. IEEE/ACM Transactions on Networking, 23(3), 810–823. doi:10.1109/TNET.2014.2306592.
Martinez-de, D., et al. (2013). Cooperation between uas and wireless sensor networks for efficient data collection in large environments. Journal of Intelligent and Robotic Systems, 70(1-4), 491–508.
Liu, X., et al. (2015). CDC: Compressive data collection for wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems, 26(8), 2188–2197.
Xiang, L., et al. (2011). Compressed data aggregation for energy efficient wireless sensor networks. In 2011 8th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON), Salt Lake City, UT (pp. 46–54). doi:10.1109/SAHCN.2011.5984932.
Wei, G., et al. (2011). Prediction-based data aggregation in wireless sensor networks: Combining grey model and Kalman Filter. Computer Communications, 34(6), 793–802.
Prabhavathi, S., et al. (2016). Energy efficient dynamic reconfiguration of routing agents for WSN data aggregation. In N. R. Shetty, N. H. Prasad, & N. Nalini (Eds.), Emerging research in computing, information, communication and applications (pp. 291–301). Springer India.
Sengupta, S., et al. (2012). An evolutionary multiobjective sleep-scheduling scheme for differentiated coverage in wireless sensor networks. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 42(6), 1093–1102.
Yuning, S., et al. (2014). A biology-based algorithm to minimal exposure problem of wireless sensor networks. IEEE Transactions on Network and Service Management, 11(3), 417–430. doi:10.1109/TNSM.2014.2346080.
Liu, L., et al. (2015). Physarum optimization: A biology-inspired algorithm for the Steiner tree problem in networks. IEEE Transactions on Computers, 64(3), 818–831. doi:10.1109/TC.2013.229.
Acampora, G., et al. (2010). Interoperable and adaptive fuzzy services for ambient intelligence applications. ACM Transactions on Autonomous and Adaptive Systems, 5(2), 1–26.
Gupta, I., et al. (2005). Cluster-head election using fuzzy logic for wireless sensor networks. In Communication Networks and Services Research Conference, 2005. Proceedings of the 3rd Annual. IEEE.
Puneet, A., & Sharma, V. (2013). Cluster head selection in wireless sensor networks under fuzzy environment. ISRN Sensor Networks. doi:10.1155/2013/909086.
AbdulAlim, M. A., et al. (2013). A fuzzy based clustering protocol for energy-efficient wireless sensor networks. Advanced Materials Research, 760–762, 685–690.
Nayak, P., & Devulapalli, A. (2016). A fuzzy logic-based clustering algorithm for WSN to extend the network lifetime. IEEE Sensors Journal, 16(1), 137–144.
Kim, J., et al. (2008). CHEF: Cluster head election mechanism using fuzzy logic in wireless sensor networks. In 10th International Conference on Advanced Communication Technology, 2008. ICACT 2008 (Vol. 1). IEEE.
Heinzelman, W., et al. (2002). An application-specific protocol architecture for wireless microsensor networks. IEEE Transactions on Wireless Communications, 1(4), 660–670.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tamandani, Y.K., Bokhari, M.U. & Shallal, Q.M. Two-step fuzzy logic system to achieve energy efficiency and prolonging the lifetime of WSNs. Wireless Netw 23, 1889–1899 (2017). https://doi.org/10.1007/s11276-016-1266-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1266-3