Abstract
The Internet of Things (IoT) devices gather a plethora of data by sensing and monitoring the surrounding environment. Transmission of collected data from the IoT devices to the cloud through relay nodes is one of the many challenges that arise from IoT systems. Fault tolerance, security, energy consumption and load balancing are all examples of issues revolving around data transmissions. This paper focuses on energy consumption, where a priority-based and energy-efficient routing (PriNergy) method is proposed. The method is based on the routing protocol for low-power and lossy network (RPL) model, which determines routing through contents. Each network slot uses timing patterns when sending data to the destination, while considering network traffic, audio and image data. This technique increases the robustness of the routing protocol and ultimately prevents congestion. Experimental results demonstrate that the proposed PriNergy method reduces overhead on the mesh, end-to-end delay and energy consumption. Moreover, it outperforms one of the most successful routing methods in an IoT environment, namely the quality of service RPL (QRPL).
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The Internet of Things (IoT) plays an increasingly significant role in our daily lives, as it maintains better service quality through continuous data collection [1, 2]. Sustainable IoT is a system of interconnected smart mechanical machines, computing devices, digital machines and objects with the capability of transmitting data on a network of connected intermediate nodes to a cloud data center. Stationary and mobile IoT devices aid in the provisioning of both simple and complex services for cloud environments and big data applications [3]. However, as the size of an IoT application grows, the limitations of such IoT devices can be noticed. Fault tolerance, security, energy consumption and load balancing are all examples of challenges that face data transmissions within large-scale IoT applications. Among these challenges, energy consumption has gained particular attention in the recent literature [4, 5].
Energy-aware IoT applications in the light of consumption, harvesting, computing as well as energy optimization are becoming a critical industry issue [6, 7]. IoT has paved the path for low-power devices to become part of the Internet and contribute to the collection and exchange of data to meet the requirements of the deployed systems. The deployment of such systems has revolutionized the exchange of information and services in a variety of fields including health and environmental monitoring. Therefore, energy-aware routing is of utmost importance for IoT applications.
Most IoT applications focus on monitoring discrete events that generate an excessive amount of data [8]. Mining big data that have been gathered by sensors and other IoT components is a challenge for IoT systems. With the wide range of IoT applications that use wireless sensor network (WSN) as a means of communication and data transformation, the related security issues become more critical. Hence, different security mechanisms have been proposed [9]. It is worth noting that WSNs have many other challenges due to their small coverage area, hardware and connectivity capabilities [10]. Obviously, the inherent challenges of such type of networks are the aggregation, transmission and routing of data from the source node to the final destination [11]. For example, collecting a large amount of big data (containing ‘videos’ and ‘images’) results in a high traffic load in the main network. Network congestion results in an unreliable and unpredictable behavior of the network. Therefore, nodes in the environment can be harvested for their energy while routing data [12].
Smart devices and sensors continuously send data to the cloud in which the cloud must analyze the data and make a prompt decision, especially when considering dynamic environments [13]. Therefore, to avoid data congestion and overhead, developing an appropriate and energy-efficient routing protocol is a must.
In this paper, a priority-based and energy-efficient routing method is presented that is based on the low-power and lossy network (RPL) model for sustainable IoT, where routing is determined by the content type. In the proposed RPL model, if an error occurs in a parent member node, its members will remain alive until the convergence and configuration of the parentless parenthesis and their packets expire due to the time lapse. In addition, we attempt to select the parent node and prevent delay. We use content-based routing technology alongside the RPL protocol in which content determines routing. By combining roaming data related to transitional relay nodes for processing, aggregation of data can be achieved at a higher rate; hence, the traffic in the main network is effectively reduced. Therefore, a considerable reduction in the delay could be obtained besides satisfying the requirements of quality of service (QoS).
The main contributions of this paper are summarized as follows:
-
Proposing a priority-based and energy-efficient RPL routing model for IoT systems that can reduce traffic, delay and node energy consumption.
-
Selecting the appropriate parent member node in the RPL protocol to prevent the creation of inappropriate branches and reduce delay and energy consumption.
-
Increasing network efficiency in terms of optimal speed of packet transmission in the IoT environment.
The remainder of this article is organized as follows: In the next section, studies related to the proposed method are reviewed in terms of their limitations and advantages. In Sect. 3, the proposed routing method is presented. Section 4 provides the implementation of the proposed method, and its evaluations are carried out. Finally, Sect. 5 concludes the paper with suggestions for future work.
2 Related work
This section presents a discussion on the recent studies of routing protocols for priority-based and energy-efficient methods in IoT environments.
2.1 Priority-based routing
Routing models and data aggregation methods in wireless sensor networks (WSNs) are of great interest [6, 7]. Two approaches are widely proposed: centralized and distributed. Before the network starts to work, a pre-computation is performed and the optimal routing structure is created. For example, the authors in [14] proposed a merger tree solution for maximum network lifetime. An energy-aware data aggregation approach was considered in [15] that minimizes the number of packets in a WSN environment. The above methods incur significant control packet overhead; hence, distributed clustering approaches are used to reduce the overhead [16, 17]. Such approaches resort to hierarchical topologies through localized message distribution. Nevertheless, shortest path which is a simple topology was used in [18]. An approach of dynamic clustering was presented in [19]. In any application or event, the clustering process should be performed. This imposes a huge transfer cost to form clusters. Moreover, tree-based approaches [20, 21], or directed acyclic graph (DAG) [6], also need a particular routing topology to run, and therefore, the ability to handle dynamic network situations is limited. The reason for this is that whenever a change in the network dynamics occurs, such as a failure of the initial energy link or discharge of some of the critical IoT nodes, the network topology must be updated to reflect the circumstances of the ruling. At the same time, this will introduce additional traffic control costs and imposes additional delays.
2.2 Energy-efficient routing
Baker et al. [22] presented an energy-aware routing model to manage power consumption for data transfer to cloud data centers. The experimental results have been evaluated with linear programming methods. In [10], a routing approach for IoT environments has been proposed. This method is based on the ant colony-inspired algorithm for solving complex problems. The solution creates a decentralized ant-based algorithm using the ability to navigate naturally in order to discover the shortest route from a source to a destination. Similarly, a specially optimized target function for RPL is provided that allows more nodes to be used as routing nodes in the choice of the parent to create a destination-oriented DAG (DODAG) structure. In this method, after receiving an IPv6 routing protocol for RPL from a neighbor, a score for each of the unnamed nodes is calculated.
Baker et al. [23] proposed a power-aware routing protocol based on the ad hoc on-demand distance vector (AODV) protocol for vehicular networks. Moreover, Baker et al. [24] presented an autonomic director architecture based on energy consumption for cloud computing. Finally, to cope with the mentioned problems, the content-centric routing (CCR) method proposed in [25] was used to deliver content-based information flow and optimal data integration within a network with the aim of reducing network delay, protecting energy sources, preventing duplicate network traffic and increasing life span.
Dhumane et al. [26] presented an energy-aware deduction routing method based on a many-objective algorithm for IoT networks. Three important factors including lifetime of node, energy and distance rate were considered in the evaluation of the routing protocol. The authors applied the c-means method for cluster head selection to minimize the number of IoT nodes. Experimental results show that the proposed routing method has feasible and optimal feedback in comparison with other heuristic algorithms. In another research [27], the authors proposed a fuzzy clustering approach to enhance energy efficiency of routing protocols in IoT environments. This research presented an immune-inspired routing algorithm with high reliability and minimal energy consumption for IoT nodes. The minimization of energy consumption for cluster communication is the primary contribution of this research. Simulation results showed that the packet loss ratio and jitter ratio for the proposed algorithm are less than the other optimized algorithms used for the same scenario.
Wang et al. [28] presented a partial energy-aware routing approach to balance energy consumption of WSN nodes in the ad hoc on-demand distance vector (AODV) protocol. This research focused on the partial energy level of each node to recognize optimal link information of neighboring nodes. Simulations were conducted using the NS2 tool, and results showed efficiency of the proposed approach. In another work [29], a Markov chain process and an energy-efficient routing protocol were presented for unmanned aerial vehicles (UAVs) in IoT environments. A probabilistic communication graph method was proposed to support semi-deterministic communications between UAV nodes with the aim of reducing delay ratio and energy consumption using the proposed routing protocol.
3 Proposed methods
IoT systems are developed for various applications such as health care, urban services and smart city infrastructure [5, 8]. However, collecting large amounts of big data for multimedia content from such networks often results in traffic congestion in the main network. To solve such an issue, we have developed PriNergy: a priority-based routing method based on the RPL protocol. In the proposed PriNergy routing method, the timing pattern is used such that the time and distance data are sent to the destination in each network slot, in addition to the type of network traffic and data type. This process increases the quality of routing and ultimately prevents congestion.
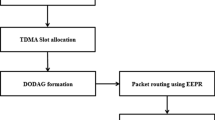
Figure 1 depicts the proposed PriNergy’s framework. A number of different sensors are used to collect data from all the electronic devices that exist in an IoT environment (A). Data transmission between nodes and finding the best route between the nodes to transmit are one of the challenging issues in the area of IoT. Therefore, the RPL protocol is employed to look for an appropriate route. In an IoT environment, objects have severe resource constraints, and hence, resource management is necessary to achieve optimal node connection and communication with other devices over the Internet. However, collecting large volumes of data from a network, specifically images and videos, results in traffic congestion in the main network area. Therefore, we have developed a routing method, which determines the proper route according to the content of the object. In low-traffic scenarios, video packets are put in time division multiple access (TDMA) slots. On the contrary in high traffic scenarios, audio packets are put in TDMA slots (B and C). In RPL, a node employs a DODAG information solicitation (DIS) message to find its next node for neighboring DODAGs (D). Each node makes DODAG detection, creation and maintenance. Detailed explanation on the framework is provided in the following subsections.
3.1 Low-power and lossy network (RPL)
The RPL routing protocol is developed and standardized by the Internet Engineering Task Force (IETF) for lossy and low-power networks to enable connectivity in Internet mesh networks [30]. RPL employs an active process to create and maintain a routing topology of a destination-oriented, directed, non-circular graph. In this graph, the data are concentrated on the root of DODAG. The edges make a path from each node to the root of DAG. If the network is happened to be in a constant situation, a low-rate DODAG information object (DIO) beacon process is used by RPL to preserve the topology of the DODAG routing. Trickle timer controls the DIO beacon.
Generating RPL messages is based on the trickle timer. Trickle timers allow nodes to reduce the transmission of their control messages while preserving network stability. As long as a node receives messages that are compatible with its own data, the node expands the sending of its control packets exponentially until reaching a maximum value [31].
The proposed DODAG is defined as the input of routing with \({\text{DODAG}} = \left( {V, N} \right)\), such that \(V\) is the set of nodes and \(N\) is the set of bits to transmit in a packet according to Eq. (1):
where V0 is the DODAG root, Ns is the initial bit, \(N_{i}^{0}\) and \(N_{i}^{1}\) are independently used to show the value of 0 and 1 of the ith bit in binary coding video or voice packets.
3.2 Proposed priority-based routing protocol
In the proposed PriNergy routing technique, each node in the network has two properties: ‘priority’ and ‘transmission rate.’ Node priority is a random digit of 0 or 1 (0 for high priority and 1 for low priority). Each packet of the node being generated has a single-bit field, which takes 0 or 1 at the source and is sent to the destination node.
The input packets in the network are mostly video and audio types. As shown in the PriNergy Algorithm, video data transmitting nodes have high priority (0) and audio data transmitting nodes have low priority (1). When there is network congestion, nodes with smaller data, such as audio and text, have the priority for sending packets. When the network has no congestion, nodes with more packets such as videos have priority for transmitting their packets.
The TDMA time slot is used to synchronize between the sender and receiver and reduce energy consumption. In order to place the data in a TDMA slot, traffic is checked first. Provided that the traffic is high, audio packets are sent; otherwise, video packets are sent. Dedicating a time slot to send the packets is based on node priorities and transmission rates. The coordinator is responsible for dedicating time slots. If several nodes have the same priorities, selecting TDMA would be based on the transmission rate.
Using the information processing unit, frame values could be modified to put a frame in an inactive mode. Preamble bits are used in the first part of the frame to synchronize between the sender and receiver. For example, the receiver finds that valid data are located on the channel by receiving a sample of 01010101 when no data are available on the channel. When the receiver receives 10101011, which includes the two sequential bits of 1, it will indicate that the valid data start after the two sequential 1 s and should be ready for receiving. The module adjusts its preamble bits in order to receive the rest of the bits.
The number of iterations depends on the initial settings made by the information processing unit for the module in the preamble bits. After validation of the data on the channel, i.e., after receiving the sequential bits 11 of the sample 10101011 in the preamble bits, the subsequent bits are sent as the address.
The source address represents the sender's address of the frame. In the receiver's address field, the address of the device to which the frame is sent is stored to indicate which frame the sensor node should be sent to. In the control part of the packet, it is determined how much the length of the payload part is. If a confirmation is needed to be sent, then the Ack bit is activated in the packet control section. The payload is also the space used by the data processing unit to receive data from the sensor using serial communication between the data processing unit and the module. In the module setting section, the length of the payload can be configured from 0 to 32 bytes.
The cyclic redundancy check (CRC) at the end of the frame is responsible for the correctness of the frame. When the error detection code is enabled, the frame's validity is checked; otherwise, if the CRC does not match the frame, then the frame is invalid.

4 Experiment discussion
The evaluation of PriNergy is presented in this section. We first highlight the experimental setup and the parameters used, namely energy consumption, end-to-end delay and routing overhead. Then, a discussion on the results obtained using the proposed method is given.
4.1 Simulation setup
NS2 [32] was adopted for the simulation tests. The parameters used in the experiment are tabulated (Table 1).
To evaluate the energy consumption factor that includes the energy used to store and retrieve data, two equations were formulated as shown below. The energy required to be transmitted is depicted in Eq. (2), and the energy necessary for receiving the data by the node is obtained in accordance with Eq. (3):
Moreover, total energy consumption for all nodes at the sending and receiving procedure in the RPL model is calculated according to Eq. (4), where k is the number of nodes in the RPL path:
Table 2 outlines the parameters used in the energy consumption Eqs. (1) and (2).
The ratio of the total size of control packets to the total size of data packets delivered to the destination is identified as the routing overhead. The control packet includes packets sent to request a route and the packet sent back because of a route error, denoted by Rreq and Rerr, respectively, to the total packet size of data packets delivered to the destinations (Table 3). The overhead of the routing bandwidth is another important parameter. However, routing overhead is non-measurable in the simulation environment; hence, our experiments neglected routing overhead. For clarity reasons, we show how the routing overhead is calculated:
End-to-end delay (EED) is composed of three parameters dtrans, dprio, and dtraf, where dtrans is the time for transmitting a packet's bits, dprio is the time for checking a packet's priority in a TDMA slot, and dtraf is the time required to check the network traffic (Table 4). EED is calculated as stated in Eq. 6:
We evaluated the priority-based algorithm (PriNergy) in different scenarios using various criteria. The proposed algorithm is compared with a QoS-based routing protocol for RPL (QRPL) [33] in terms of energy consumption, routing overhead, end-to-end delay against maximum speed of the nodes and pause time of the nodes. This comparison shows the efficiency and functionality between our proposed model and the QRPL method.
4.2 Energy consumption
A comparison between the PriNergy algorithm and the QRPL is given in this section in terms of energy consumption. Each node consumes energy for storing and retrieving data. In a network, the energy of a node is very important and depends on the battery, which has a limited energy source. The energy consumption adopted within our proposed algorithm considers three criteria: the pause time of a node, the number of nodes and the maximum speed of the nodes.
4.2.1 Energy consumption versus pause time of the nodes
As shown in Fig. 2, for each node provided, the pause time is increased and the energy consumption is reduced. It shows that the packets are well managed and uploaded for different traffic types, and the need to rebuild the links is reduced; hence, the lifetime of the algorithm is increased. The trend of reducing energy consumption in the proposed algorithm is higher than that of the QRPL algorithm.
4.2.2 Energy consumption versus the number of nodes
In Fig. 3, we compare our proposed technique against QRPL in terms of energy consumption against the number of nodes. By increasing the number of nodes, energy consumption of the network for both algorithms decreases; when the number of nodes increases in the entire network, the frequency of a node in a sample space is greater. It can be said that when the network density increases, nodes consume less energy for routing. Such reduction in energy consumption using the PriNergy algorithm is due to the use of supplementary nodes. This confirms the scalability of the proposed algorithm. The reduction in energy consumption in the proposed algorithm is higher than that in the QRPL algorithm.
4.2.3 Energy consumption versus maximum speed of the nodes
As shown in Fig. 4, for both algorithms, when the maximum speed of the nodes is increased, the average energy consumption increases as well. This is due to the network topology dynamics; when the nodes move more quickly, the network topology changes faster. Therefore, there is a need for more routing, which will increase the overall energy consumption.
4.3 Routing overhead
Simulation results of routing overhead are illustrated in Fig. 5 for the PriNergy algorithm and compared with that of the QRPL algorithm. Routing overhead is the total number of control packets in the network layer that were sent during the simulation time, including packets requesting a path, packets responding with the path requested and packets announcing path failure. The maximum speed of nodes is set to 25 m/s, the number of nodes is set to 100, and the energy of each node is set to 2 J.
As depicted in Fig. 5, as the pause time of the nodes increases and node mobility decreases, the routing overhead is reduced. In the PriNergy algorithm, given the prioritization of the coordinates and the sending packets regarding the type of traffic, the longer the nodes pause, the less the need for the redesign of the proposed algorithm. Therefore, fewer requests for paths are sent to the network, resulting in a decrease in routing overhead.
4.4 Average end-to-end delay
A comparison between the PriNergy algorithm and QRPL is presented in terms of end-to-end delay in this section. The end-to-end delay is the average time needed for packets to reach their destinations. In the simulation settings, the maximum speed of the nodes was set to 25 m/s and the number of nodes was set to 100.
4.4.1 The average end-to-end delay versus maximum speed of the nodes
For the simulation, the pause time was set at 1 s. As shown in Fig. 6, as the maximum speed of nodes increases, the average end-to-end delay also increases in both algorithms. This is the effect of the dynamics of network topology and the breakdown rate of the paths. However, the average end-to-end delay in the proposed method is lower than QRPL.
4.4.2 The average end-to-end delay versus pause time of the nodes
As can be seen in Fig. 7, with increasing pause time of the nodes, network dynamics decreases and the network becomes more stable. Therefore, there is no need for re-routing. In this situation, as the pause time increases, the delay and the link loss decrease. Because of the prioritization and scheduling for sending packets in the proposed method, delay reduction is more noticeable.
4.4.3 The average end-to-end delay versus number of nodes
In Fig. 8, two algorithms are compared in terms of the average end-to-end delay when the maximum speed of the nodes is set to 25 m/s, the energy of each node is 2 J and the pause time is equal to 1 s. As shown in the figure, increasing the number of nodes does not have a very significant effect on end-to-end delay in comparison with other parameters studied. However, by increasing the number of nodes and increasing network density, the mean end-to-end delay in both algorithms decreases, which is in fact due to the increase in the number of paths between the source and the destination, and the selection of auxiliary nodes.
5 Conclusion and future work
IoT applications require excessive bandwidth usage and cause traffic congestion in the network core. Routing packets from the source to the destination proves to be a challenging issue for IoT systems [34], especially in densely crowded environments [35]. With the increase in the number of wireless IoT devices, energy consumption has become a critical issue [36]. A new RPL-based method is proposed in this article to minimize IoT device energy consumption. Our method considered the QoS of IoT applications, where TDMA time slot is used to synchronize between the sender and receiver and reduce energy consumption. Moreover, the DODAG routing topology was controlled by the trickle timer. The evaluation of the proposed method was conducted using NS-2 to compare the energy consumption, routing overhead and end-to-end delay of the proposed and traditional methods. Experimental results illustrated that the proposed priority-based routing method using the TDMA model does decrease node energy consumption efficiently and provide significant minimization of the end-to-end delay for the selection of the communication nodes in the IoT network. In future work, we plan to apply the proposed solution in vehicular networks [37]. Moreover, we plan to introduce a meta-heuristic algorithm used to manage the transferring frames for routing in IoT nodes.
References
Park S et al (2014) IoT routing architecture with autonomous systems of things. In: 2014 IEEE world forum on internet of things (WF-IoT). IEEE
Dhumane A et al (2019) Context awareness in IoT routing. In: 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA). IEEE
Kotb Y et al (2019) Cloud-based multi-agent cooperation for iot devices using workflow-nets. J Grid Comput 17:1–26
Al Ridhawi I et al (2019) A profitable and energy-efficient cooperative fog solution for IoT services. IEEE Trans Ind Inf
Souri A et al (2019) A systematic review of IoT communication strategies for an efficient smart environment. Trans Emerg Telecommun Technol electronic version e3736
Kharrufa H, Al-Kashoash H, Kemp A (2019) RPL-based routing protocols in IoT applications: a review. IEEE Sens J 19:5952–5967
Zikria YB et al (2018) A survey on routing protocols supported by the Contiki Internet of things operating system. Future Gener Comput Syst 82:200–219
Souri A, Norouzi M (2019) A state-of-the-art survey on formal verification of the internet of things applications. J Serv Sci Res 11(1):47–67
Musaddiq A, Zikria YB, Kim SW (2018) Energy-aware adaptive trickle timer algorithm for RPL-based routing in the internet of things. In: 2018 28th International Telecommunication Networks and Applications Conference (ITNAC). IEEE
Ganesh D, Patil KK, Suresh L (1997) Two to tango: the role of government in fisheries co-management. Marine Policy 105(1):267–292
Yahiaoui S et al (2018) An energy efficient and QoS aware routing protocol for wireless sensor and actuator networks. AEU-Int J Electron Commun 83:193–203
Raoof A, Matrawy A, Lung C-H (2018) Routing attacks and mitigation methods for RPL-based internet of things. IEEE Commun Surv Tutor 21:1582–1606
Souri A, Navimipour NJ, Rahmani AM (2018) Formal verification approaches and standards in the cloud computing: a comprehensive and systematic review. Comput Stand Interfaces 58:1–22
Kumar M, Azad M, Agrawal N (2019) Comparative analysis of tree-based data aggregation protocols to maximize lifetime of wireless sensor networks. In: Pervasive computing: a networking perspective and future directions. Springer, pp 153–163
Ambigavathi M, Sridharan D (2018) Energy-aware data aggregation techniques in wireless sensor network. In: Advances in power systems and energy management. Springer, pp 165–173
Gilbert EPK et al (2018) Trust based data prediction, aggregation and reconstruction using compressed sensing for clustered wireless sensor networks. Comput Electr Eng 72:894–909
Petrovic D et al (2003) Data funneling: routing with aggregation and compression for wireless sensor networks. In: Proceedings of the First IEEE International Workshop on Sensor Network Protocols and Applications, 2003. IEEE
Karkazis P et al (2012) Design of primary and composite routing metrics for rpl-compliant wireless sensor networks. In: 2012 International Conference on Telecommunications and Multimedia (TEMU). IEEE
Wang S et al (2018) CRPD: a novel clustering routing protocol for dynamic wireless sensor networks. Pers Ubiquit Comput 22(3):545–559. https://doi.org/10.1577/1548-8667(1998)010xxaaa0160:FIITDOxxbbb2.0.CO;2
Aldabbas H (2018) LPBR: location prediction based routing protocol for mobile IoT systems. In: Proceedings of the 2nd International Conference on Future Networks and Distributed Systems. ACM
Han Z, Li Y, Li J (2018) A novel routing algorithm for IoT cloud based on hash offset tree. Future Gener Comput Syst 86:456–463
Baker T et al (2015) GreeDi: an energy efficient routing algorithm for big data on cloud. Ad Hoc Netw 35:83–96
Baker T et al (2018) GreeAODV: an energy efficient routing protocol for vehicular ad hoc networks. In: Intelligent computing methodologies. Springer, Cham
Baker T et al (2013) Energy efficient cloud computing environment via autonomic meta-director framework. In: 2013 Sixth International Conference on Developments in eSystems Engineering
Cai Y et al (2018) Software defined status aware routing in content-centric networking. In: 2018 International Conference on Information Networking (ICOIN). IEEE
Dhumane AV, Prasad RS (2019) Multi-objective fractional gravitational search algorithm for energy efficient routing in IoT. Wirel Netw 25(1):399–413
Preeth SKSL et al (2018) An adaptive fuzzy rule based energy efficient clustering and immune-inspired routing protocol for WSN-assisted IoT system. J Ambient Intell Human Comput 1–13
Wang Y, Wang Z (2018) Routing algorithm of energy efficient wireless sensor network based on partial energy level. Clust Comput 22:8629–8638
Yuan P et al (2019) Markov decision process-based routing algorithm in hybrid Satellites/UAVs disruption-tolerant sensing networks. IET Commun 13:1415–1424
Umamaheswari S, Negi A (2017) Internet of things and RPL routing protocol: a study and evaluation. In: 2017 International Conference on Computer Communication and Informatics (ICCCI). IEEE
Gara F et al (2019) A new scheme for RPL to handle mobility in wireless sensor networks. Int J Ad Hoc Ubiquitous Comput 30(3):173–186
Issariyakul T, Hossain E (2009) Introduction to network simulator 2 (NS2). In: Introduction to network simulator NS2. Springer, pp 1–18
Mohamed B, Mohamed F (2015) Qos routing rpl for low power and lossy networks. Int J Distrib Sens Netw 11(11):971545
Salameh HB, Otoum S, Derbas R, Aloqaily M, Al Ridhawi I, Jararweh Y (2020) Intelligent Jamming-aware Routing in Multi-hop IoT-based Opportunistic Cognitive Radio Networks, Ad Hoc Networks, vol. 98
Aloqaily M, Al Ridhawi I, Salameh HB, Jararweh Y (2019) Data and Service Management in Densely Crowded Environments: Challenges. Opportunities, and Recent Developments, IEEE Communications Magazine 57(4):81–87
Ridhawi IA, Aloqaily M, Boukerche A (2019) Comparing Fog Solutions for Energy Efficiency in Wireless Networks: Challenges and Opportunities. IEEE Wireless Communications 26(6):80–86
Balasubramanian V, Otoum S, Aloqaily M, Al Ridhawi I, Jararweh Y ((2020)) Low-Latency Vehicular Edge: A Vehicular Infrastructure Model for 5G. Simul Model Pract Theory 98:101968
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Safara, F., Souri, A., Baker, T. et al. PriNergy: a priority-based energy-efficient routing method for IoT systems. J Supercomput 76, 8609–8626 (2020). https://doi.org/10.1007/s11227-020-03147-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03147-8