Abstract
This paper proposes a new chaotic system based on sine map, i.e., the coupled piecewise sine map (CPSM), which utilizes piecewise mechanism to obtain more uniform probability density distribution of state values, and enhances the complexity of chaotic system by coupling parameters between sub-systems. Then, from the view of resisting the chosen ciphertext attack, a ciphertext sensitive diffusion structure is presented. Based on the CPSM and the ciphertext sensitive diffusion structure, this paper proposes a new image encryption algorithm. Since the CPSM can generate chaotic sequences with good cryptographic properties and the diffusion structure has good diffusion performance in both the encryption process and the decryption process, the proposed encryption algorithm is extremely sensitive to the ciphertext tampering. Thus, it can effectively resist the chosen ciphertext attacks. Experimental results and security analysis also confirmed that the proposed algorithm has good security and can ensure the secure transmission of image in the Internet.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
With the increasing application of multimedia, more and more images are transmitted and stored through the network. Due to the openness and sharing of the network, the transmission and storage of plaintext images in the network are very easy to leak the privacy content of the images. Encrypting images can effectively protect the security of private content [40]. The traditional encryption algorithms such as DES, AES and RSA are designed to encrypt text information, which are not very suitable for encrypting images. The main reason is that images contain a lot of redundant information and have strong correlation between pixels [21, 41]. In recent years, chaotic image encryption has attracted the interest of many researchers [25, 33, 43].
The typical chaotic image encryption algorithms include chaotic system and permutation-diffusion operations [7]. The chaotic system generates pseudo-random sequences to drive the permutation-diffusion operations. Permutation operation can change the position of pixels and make an image meaningless. Diffusion operation makes pixels interact with each other, and spread the information of a pixel to all pixels as much as possible.
The security of chaotic image encryption algorithm highly depends on the characteristic of the chaotic system [22]. It is more difficult for the attackers to predict the orbits of the chaotic system with uniform distribution and complex dynamic behaviors [14]. In recent years, some chaotic systems for image encryption have been proposed. By utilizing the power mechanism to generate chaotic sequence, a one-dimensional sine powered chaotic system is proposed, which has good randomness and sensitivity [26]. In [34], a three-dimensional heuristic map is proposed, which has excellent chaotic characteristics in each dimension. To enhance the chaotic characteristics and expand key space, some new methods are proposed, such as coupling two chaotic maps [36] and improving simple chaotic map with more parameters [11]. Zhu et al. proposed a two-dimensional compound homogeneous hyper-chaotic system, which has good hyper-chaotic behaviors [45]. Hussein et al. combined Logistic map and Hénon map to propose a new 2D Hénon-Logistic Map, which has a wider distribution in the phase plane space than both Logistic map and Hénon map [15]. Although these methods have improved the complexity of chaotic systems, most of the chaotic systems have uneven distribution of state values [6, 12]. From the view of cryptographic application, low chaotic complexity and uneven distribution of state values have negative impact on chaos-based encryption algorithms. Thus, when chaotic systems are applied to encrypt images, enhancing their complexity becomes particularly important.
As we know, diffusion operation is a very important for encryption algorithms and is regarded as the basis for evaluating the ability against differential attacks [23]. In [20, 36], the chain structure controlled by the key stream is used to diffuse the image pixels. The latter pixel is affected by the diffusion value of the previous pixel, which in turn affect the diffusion value of subsequent pixels. In [4, 18, 41], the DNA coding is used to achieve diffusion operation. Zhu et al. designed an improved two-dimensional diffusion structure, which can spread slight change in plain image to the whole cipher image [44]. In order to further enhance the security of diffusion, two different diffusions, chain diffusion and XOR diffusion, are used in [9]. In [29], three different level operators, i.e., bit-level diffusion, pixel-level diffusion and block-level diffusion, are combined together. A large number of researchers have shown that the security of encryption algorithm heavily depends on diffusion structure [5, 17]. However, to the best knowledge of us, quite a few image encryption algorithms based on chaotic systems only emphasize resisting differential attack and statistical attack, and omit the influence of cipher tampering, which possibly bring convenience to chosen ciphertext attack. For the commonly used chain diffusion structure in [8, 24, 32, 36, 37], the information loss is evenly distributed in the decrypted image if the ciphertext image is tampered. This similar phenomenon also exists in some algorithms that use other diffusion structures [1, 17, 19, 28, 30, 38]. Due to the high redundancy of image data, the attacker can still extract some useful information from the decrypted images, which means that the insensitivity to ciphertext tampering possibly makes the encryption algorithms be broken by chosen ciphertext attack.
To design a strong image encryption algorithm based on chaotic system, two measures should be considered. One is to construct a chaotic system with good cryptographic property, and the other is to improve the ability of diffusion structure to resist cipher tampering. This paper first constructs a coupled piecewise sine map and designs a diffusion structure sensitive to ciphertext. Then, a secure image encryption algorithm based on chaos is proposed, which is very sensitive to both plaintext and ciphertext, and has good ability to prevent ciphertext tampering. The remaining sections of the paper are organized as follows. In Sect. 2, the problem of common chain diffusion structure is analyzed. In Sect. 3, the coupled piecewise sine map is proposed. In Sect. 4, the sensitive diffusion structure is proposed. In Sect. 5, the chaotic image encryption algorithm that can prevent ciphertext tampering is described in detail. In Sect. 6, the experimental results and security analysis are performed. Finally, the conclusion is drawn in Sect. 7.
2 The problem of common chain diffusion structures
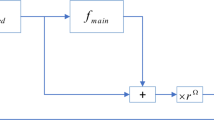
Owing to simple structure and fast computing speed, chain diffusion structures have been widely used in many image encryption algorithms. Figure 1 is an illustration of chain diffusion structure, and it can be described as:
where \(OP(\cdot )\) represents the diffusion operator, \(P_i\), \(X_i\) and \(C_i\) represent the i-th elements of the plaintext, the key stream and the ciphertext, respectively. XOR and modular addition are two typical diffusion operators and the corresponding diffusion structures can be described as:
In the above chain diffusion methods, the image pixels are diffused from the first one to the last one, which means that a tiny change in one pixel will influence all the subsequent pixels. However, the two diffusion methods are difficult to resist chosen ciphertext attack in the decryption stage. Here is an example to further illustrate it.
Suppose that an attacker has a ciphertext image C. The attacker randomly modifies the value of a pixel in the ciphertext image and then decrypts the modified ciphertext image. Assume that the j-th pixel \(C_j\) is modified as \(C'_j\). Here take the diffusion structure based on XOR operation as an example to analyze the influence on decryption result. The decryption operation of which is
It can be seen that only at most two pixels are changed in the decrypted image, when \(C_j\) is tampered to \(C'_j\). By modifying ciphertext pixels one by one, the attacker has high possibility to construct the one-to-one relation between ciphertext pixels and plaintext pixels. Thus, the lack of sensitivity to ciphertext tampering is a loophole in the encryption algorithms. The same problem is also existed in the encryption algorithms using the diffusion structure based on modular addition. Figure 2 shows a tampering test on the encrypted image, which is produced based on a modular addition diffusion structure. It can be seen that although the quality of the recovered image decreases with the increase in the tampered pixels, the useful information in the image still can be identified. It means that the encryption algorithm using this diffusion structure is not sensitive to ciphertext tampering.
3 The coupled piecewise sine map
In order to solve the problem in Sect. 2, this paper takes measures from two aspects. Firstly, a coupled piecewise sine map is designed to ensure the key stream used in the diffusion structure has good cryptographic properties. Secondly, a new diffusion structure is designed to enhance the sensitivity to ciphertext modification, which will be discussed in Sect. 4.
3.1 The piecewise sine map
Sine map is a classical one-dimensional chaotic system with high speed, which has been used in many chaos-based encryption algorithms. It is defined as:
Figure 3(a-d) is the Lyapunov exponent, bifurcation diagram and probability density distribution, respectively. According to Fig. 3a and b, it can be seen that the Lyapunov exponent is not always positive, which means the complexity of the system is insufficient, and the sine map is chaotic only when parameter \(\mu \) is in [0.87, 1]. Figure 3(c-d) is the density probability distribution of sine map when \(\mu =0.9\) and \(\mu =1\). It can be seen that the distribution of sine map is not uniform, which is not suitable for cryptographic application.
To improve chaotic performance of sine map, this paper proposes a piecewise sine map (PSM), which is defined as:
Here, the parameter \(\mu \in (0, 0.5)\) is used to determine the segment intervals. Figure 4 illustrates the Lyapunov exponent and the bifurcation diagram of the PSM. It can be seen from Fig. 4 that the PSM has the positive Lyapunov exponents all the time and has more complicated bifurcation diagram than the sine map. Thus, the PSM enhances the chaotic performance and has more complicated dynamic behavior. Moreover, Fig. 5 shows the density probability distribution of PSM with different parameter values. When \(\mu \in (0, 0.1]\), the density probability distribution of PSM is relatively uniform, and the difference between the maximum and the minimum values of density probability is less than 0.3%. To obtain good ergodicity and randomness, it is recommended to set the value of \(\mu \) in the interval (0, 0.1].
3.2 The presented chaotic system
Although fixing \(\mu \) in (0, 0.1] can make the PSM generate chaotic sequences with uniform probability density distribution, this strategy reduces the parameter space of \(\mu \). Since parameters are usually used as secrete keys in a chaos-based encryption algorithm, limiting the value of parameter \(\mu \) is not conducive to the security of the encryption algorithm. To overcome this problem and further enhance the complexity of chaotic system, the CPSM is proposed. By parameter coupling, the one-dimensional PSM can be extended to multi-dimensional. Take four-dimensional for example, which can be defined as:
Here, \(\lambda \) is the coupling parameter and its value is in [0, 1]. Since the CPSM has more different dimensional variables and each dimensional variable has its own control parameters, the total parameter space of the CPSM is extended.
By experiment analysis, it is found that the CPSM can generate the chaotic sequences with a relatively uniform probability density distribution, when setting \(\lambda \in [0.99, 1]\) and \(\mu \in (0, 0.1]\). Figure 6 shows the density probability distribution of each dimension variable of the CPSM, when \(\mu \) is 0.05 and \(\lambda \) is 0.995. The maximum and the minimum value of the density probability is calculated, and its value is less than 0.3%. Therefore, as a high-dimensional chaotic map, the CPSM has complicated structures, good complex dynamic behavior and uniform probability density distribution, which lays a good base for the design of encryption algorithms.
4 The sensitive diffusion structure
In order to prevent attackers from recovering any useful information from a tampered ciphertext, this paper proposes a new chain diffusion structure which is sensitive to ciphertext tampering.
The structure consists of two rounds of diffusion, each of which contains one forward diffusion and one backward diffusion. In the first round, the forward diffusion and the backward diffusion are controlled by two different key streams, which makes the change of any plaintext pixel can be diffused to all ciphertext pixels. In the second round, the forward diffusion and backward diffusion are controlled by another two different key streams, which make the change of any pixel in the ciphertext can be diffused to all the pixels of the decrypted image.
4.1 The first round of diffusion
In the first round of diffusion, modular addition and cyclic shift operation are used to guarantee the plaintext sensitivity of the proposed diffusion structure. Assuming that A is a one-dimensional array extracted from a grayscale image with the size of \(M \times N\), Q is an integer, S and T are two chaotic sequences with length \(M \times N\), the first round of diffusion is described as follows:
Forward diffusion stage: the pixel values are diffused from front to back. The operation is described as:
where \(i = 0, 1, \cdots , M \times N-1\), \(s_i\) is the i-th value in the chaotic sequence S. \(A'\) is the array after forward diffusion. \(A_i\) and \(A'_i\) are the i-th elements of A and \(A'\), respectively. Function CSR(X, Y) represents right cyclic shift the binary of X by Y bit.
Backward diffusion stage: the pixel values are diffused from back to front. The operation is formulated as:
where \(t_i\) is the i-th value in the chaotic sequence T. \(A''\) is the array after backward diffusion. \(A''_i\) is the i-th element of \(A''\). CSL(X, Y) represents left cyclic shift the binary of X by Y bit.
After the first round of chain diffusion, the information of any pixel in A is diffused to all pixels in \(A''\). It means that a tiny change in any pixel can be diffused to all the other pixels.
4.2 The second round of diffusion
The purpose of the second round is to make the diffusion structure sensitive to ciphertext. The second round consists of two diffusion stages. For the one-dimensional array \(A''\) obtained from the first round of diffusion, given two chaotic sequences U and V of length \(M \times N\), the diffusion operations are described as follows:
Backward diffusion stage: This stage is the reverse operation of the forward diffusion in the first round. It performs as:
where \(u_i\) is the i-th value in the chaotic sequence U, \(B'\) is the array after backward diffusion, and \(B'_i\) is the i-th element of \(B'\).
Forward diffusion stage: This stage is the reverse operation of backward diffusion in the first round. It performs as:
where \(v_i\) is the i-th value in the chaotic sequence V, \(B''\) is the diffused array, and \(B''_i\) is the i-th element of \(B''\).
5 The proposed image encryption algorithm
Based on the CPSM and the sensitive diffusion structure, a chaotic image encryption algorithm is proposed, which is described as follows, and the flowchart is shown in Fig. 7.
Step 1. Convert a \(M \times N\) color image P into a \(M \times 3N\) grayscale image \(P_1\) according to
where R(j, k), G(j, k) and B(j, k) represent the red, green and blue components of color pixel P(j, k), respectively. Then, the pixels of \(P_1\) are converted into a one-dimensional array \(D_1\) with the length of \(M \times 3N\) according to the order from left to right and top to bottom.
Step 2. The initial values w, x, y, z and the parameters \(\mu \) and \(\lambda \) of CPSM are used as the secrete keys. Then, iterate the CPSM for 200 times to get rid of the transient effect. Continue to iterate the CPSM for \(M \times 3N\) times and extract the state values in each iteration to generate four sequences of length \(M \times 3N\), which are denoted as \(W=\left\{ w_i\right\} \), \(X=\left\{ x_i\right\} \), \(Y=\left\{ y_i\right\} \), \(Z=\left\{ z_i\right\} \), \( i= 0,1,\cdots ,M \times 3N-1\).
Step 3. The pixel confusion operation is performed on each value in \(D_1\) according to \(D_2(i)=((D_1(i)+\left\lfloor w_i \times Q\right\rfloor \ mod\ 256)\ mod\ 256) \oplus (\left\lfloor x_i \times Q\right\rfloor \ mod\ 256)\). Here, \(D_2\) represents the confused array. \(D_1(i)\) and \(D_2(i)\) are the i-th elements of \(D_1\) and \(D_2\), respectively. Q is a large constant integer.
Step 4. Perform the first round of diffusion in Sect. 4.1 on \(D_2\) by using the chaotic sequences W and X as S and T, respectively. The diffused result of \(D_2\) is denoted as \(D_3\).
Step 5. Permute the element positions in \(D_3\). For the i-th element \(D_3(i)\) in \(D_3\), calculate its new position j according to \(j=\left\lfloor x_i \times Q\right\rfloor \ mod\ (M \times 3N)\), and exchange the positions of \(D_3(i)\) and \(D_3(j)\) to obtain \(D_4\).
Step 6. Perform the second round of diffusion in Sect. 4.2 on the permutated \(D_4\) by using the chaotic sequences Y and Z as U and V, respectively. The diffused result is denoted as \(D_5\).
Step 7. The same method in Step 5 is used to permute the element positions in \(D_5\). The only difference to Step 5 is that the chaotic sequence Y is used to replace the chaotic sequence X. The permuted result is denoted as \(D_6\).
Step 8. The same method in Step 3 is used to confuse the element values in \(D_6\). The only difference to Step 3 is that the chaotic sequences Y and Z are used to replace the chaotic sequences W and X. The output result is denoted as \(D_7\).
Step 9. According to the reverse operation in Step 1, the array \(D_7\) is rearranged into an \(M\times N\) color image C, i.e., the ciphertext image.
6 Experimental results and security analysis
6.1 Experimental results
In the experiment, the keys are randomly set as \(w=0.226598532502152\), \(x=0.715260198702623\), \(y=0.271238570940165\), \(z=0.619035721685213\), \(\mu =0.041235269853856\) and \(\lambda =0.996429875231052\). Two classic images “Lena” and “Pepper” are used to test the result. The encryption and decryption results are shown in Fig. 8. As can be seen, the ciphertext images are similar to random noise without any visual information of the plaintext images, and it effectively hides all useful information of plaintext images. Moreover, the decrypted images are the same as the plaintext images. Thus, the experimental results verify the correctness of the algorithm.
6.2 Key security analysis
6.2.1 Key space analysis
The key space is the collection of all possible keys. For a secure encryption system, the key space should be large enough to resist brute force attacks. The key space of the proposed algorithm is determined by the initial values and parameters of CPSM. Here, w, x, y and z can be any real value in interval (0, 1), \(\mu \) can be any real value in interval (0, 0.1], and \(\lambda \) can be any real value in interval [0.99, 1]. According to the IEEE standard of floating-point numbers, the precision is \(10^{-15}\) in a 64-bit double precision number [46]. Thus, the key space of our scheme is about \(10^{15} \times 10^{15} \times 10^{15} \times 10^{15} \times (0.1 \times 10^{15})\times (0.01 \times 10^{15})\approx 2^{285} \) , which is much larger than the general requirements of \(2^{100}\) to resist brute force attack [3]. Therefore, our scheme can effectively prevent brute force attacks.
6.2.2 Key sensitivity analysis
A secure algorithm should be sensitive to the keys. Key sensitivity means that any subtle change of the keys not only generates great changes in the encryption results, but also fails to restore the original image from the encrypted image.
First, in the key sensitivity test of encryption process, the initial keys are the same values as in Sect. 6.1. Then, one part of the keys is slightly changed and the changed keys are used to encrypt image “Lena” again. Figure 9 shows the cipher images with different slightly changed keys. To measure the differences between these cipher images, number of pixels change rate (NPCR), unified average changing intensity (UACI) and block average changing intensity (BACI) [42] are used. They are defined as:
Here, \(C_1\) and \(C_2\) are two cipher images with size \(M \times N\), whose plaintext images are the same except for only 1 bit, Sign(x) and m(i, j) are defined as:
where \(D(i, j)=|C_1(i, j) - C_2(i, j)| \).
Table 1 shows the difference of ciphertext images in Fig. 9. It can be seen that the NPCR, UACI and BACI in Table 1 are very close to the ideal values, i.e., NPCR = 99.6094%, UACI = 33.4635% and BACI = 26.7712%, which means that these images are very different. The result indicates that any slight change in the keys will produce a completely different cipher image.
Second, some tiny changed keys are used to decrypt the cipher image of Fig. 8b. The decrypted results are shown in Fig. 10. As can be seen, all decrypted images do not show any useful information contained in the plaintext image. NPCR, UACI and BACI are also used to measure the differences among the decrypted images. The results are shown in Table 2. As can be seen, the results are very close to the ideal values, which means that the decrypted images are obviously different. It indicates that any slight change in the keys will decrypt a completely different image. Therefore, our algorithm has good key sensitivity.
6.3 Statistical analysis
6.3.1 Histogram analysis
Histogram reflects the distribution information of image pixels. A good encryption algorithm should produce cipher images with uniform histograms to prevent attackers from finding useful statistical information. The histograms of plaintext image “Lena” and its cipher image in Fig. 8 are shown in Fig. 11. As can be seen, the histograms of red, green and blue components of plaintext image show very obvious statistical information. On the contrary, the histograms of the ciphertext image are evenly distributed and do not show any useful statistical information. The test on histogram analysis shows that our algorithm can effectively resist the histogram statistical attack.
6.3.2 Correlation coefficient analysis
Generally, a meaningful plaintext images have strong correlations between adjacent pixels in the vertical, horizontal, diagonal and anti-diagonal directions. For a good image encryption algorithm, it produces cipher image whose pixels like random noise and have no any correlations. The correlation coefficient of adjacent pixels is calculated by
where x and y are randomly selected adjacent pixels, and K is the total number of pixel pairs.
Some classical color images are encrypted by our algorithm. Then, set \(K = 10000\), and calculate the correlation coefficients of adjacent pixels in vertical, horizontal, diagonal and anti-diagonal directions. The results are shown in Table 3. As can be seen, the correlation coefficients of adjacent pixels of the ciphertext images are very small, which indicates that the proposed algorithm effectively removes the correlation between adjacent pixels and can resist the statistical attack.
Moreover, to visually display the correlation distribution of adjacent pixels, 5000 pixel pairs are randomly selected from the ciphertext and plaintext of “Lena” in vertical, horizontal, diagonal and anti-diagonal directions and draw its distribution. Figure 12 is the distributions of blue component. The distributions of the red and green components are almost the same as the results in Fig. 12. So, they are omitted for space reason. It can be seen that the distributions of plaintext image are concentrated in all directions, indicating they have strong correlation. While the distributions of ciphertext image are evenly distributed in all directions, it means that the ciphertext image has approximately non-correlation. The analyses show that the algorithm can effectively remove the correlations between pixels and has good ability to resist statistical analysis.
6.3.3 Information entropy analysis
Information entropy is often used to measure the randomness of information, which is calculated by
Here, p(i) represents the probability of the grayscale value i, and L represents the grayscale level of the image C. For a ciphertext of 8-bit grayscale image, the ideal value of information entropy is 8.
Some typical images are encrypted by the proposed algorithm. The information entropy of plaintext images and ciphertext images is shown in Table 4. It can be seen that the information entropy of the red, green, and blue components of each ciphertext image is very close to the theoretical value of 8, which means that the risk of ciphertext information leakage is neglected. Table 5 compares the information entropy of proposed algorithm with other image encryption algorithms based on chaos. As can be seen, the proposed algorithm is superior to them in terms of information entropy, which also confirms that the proposed algorithm performs well.
6.3.4 Local Shannon Entropy analysis
Local Shannon entropy (LSE) overcomes some weakness of traditional information entropy and can be used to further measure the randomness of ciphertext. The LSE is described as:
where \(C_1, C_2,\cdots , C_k\) are k non-overlapping image blocks randomly selected from C, and each block contains \(T_B\) pixels.
Set \(k=30\), \(T_B=1936\) and the significant \(\alpha \) as 0.05, the ideal LSE value is 7.902469317. If the LSE of the image is in the interval (7.901901305, 7.903037329), it is considered to pass the test. Table 6 shows the LSE result. Moreover, the LSE result of proposed scheme is compared with some recent schemes [2, 13], which is also listed in Table 6. It can be seen that the passing rate of proposed scheme is better than that in Ref. [2] and Ref. [13], indicating that the proposed algorithm has high security.
6.4 Differential attacks analysis
A good encryption algorithm should be highly sensitive to any slight change of plaintext image, i.e., has enough ability to resist differential attack. Generally, NPCR, UACI, and BACI are used to measure the ability of encryption algorithms to resist differential attack.
Firstly, the original image is encrypted to generate a ciphertext image. Then, only 1 bit in the original image is randomly changed, and the changed image is encrypted with the same key to get another ciphertext image. For the two ciphertext images, calculate the NPCR, UACI and BACI values. The test is repeated for 30 times, and the average values of NPCR, UACI and BACI are calculated as the final results. Table 7 lists the test results on four different typical images. All the test results are very close to the theoretical values. It means that the ciphertext images are completely different and indicates that the proposed diffusion structure makes our algorithm resist differential attacks effectively.
6.5 Tampering attack analysis
To prevent the chosen ciphertext attack, it requires that any tiny change in the ciphertext image will cause completely different decrypted image. It means that the algorithm is extremely sensitive to ciphertext tampering. With this feature, the algorithm can effectively verify the integrity of the ciphertext image and prevent cipher-tampering attack.
To evaluate the ability of resisting tampering attack, the following modifications are made to the ciphertext image of “Lena”:
-
Modify the most significant bit of C(0, 0);
-
Add 1% salt and pepper noise;
-
Cut \(32\times 32\) pixels;
-
Reverse all pixel values.
Then, the above-modified ciphertext images are decrypted and compared with plaintext. The decrypted images are shown in Fig. 13. It can be seen that the decryption results are all similar to the random noisy images. It means that our algorithm is also sensitive to the content of ciphertext image.
To measure the amount of useful information contained in these decrypted images, their peak signal-to-noise ratio (PSNR) with the plaintext image is calculated. PSNR is calculated by
Here, n is the number of sampling bits, \(P_1\) and \(P_2\) are two images with size of \(M \times N\). The calculated PSNR values are shown in Table 8. As shown, all PSNR values of decrypted images are very small, indicating that the decrypted images are quite different from the plaintext image and do not contain any useful information.
To further quantize the effect of resisting tampering attack, the NPCR, UACI and BACI are used to measure the differences between the decrypted images of tampered ciphertext. The differences are shown in Table 9. The result shows that the decryption results of different tampered ciphertext images are significantly different. Thus, it is hard to find any useful information by comparing the decrypted results from different tampered ciphertext images. It means that the proposed diffuse structure makes our algorithm own good ability to prevent the tampering attacks on ciphertext image.
6.6 Computational complexity and speed analysis
To evaluate the computational complexity of the proposed algorithm, the time complexity of chaotic sequences generation, pixel confusion, permutation and sensitive diffusion are given by referring to Ref. [35]. Encrypting a color image with size of \(M \times N\), the time complexity of generating four chaotic sequences with length of \(3M \times N\) is \(O(12M \times N)\). In the pixel confusion stage, XOR operation is performed one by one for each pixel, and the time complexity is \(O(3M \times N)\). In permutation stage, pixels are scrambled in turn, and the time complexity is \(O(3M \times N)\). The sensitive diffusion structure contains two rounds of diffusion process; each round contains two cyclic shift operations of all pixels. So, the time complexity of diffusion structure is \(O(12M \times N)\). Therefore, the total time complexity of the algorithm is \(O(30M \times N)\).
The algorithm is implemented with VC++ 6.0 on Intel Core i7-4710MQ @ 2.5 GHz CPU, 8 GB RAM, and Windows 10 operating system. In the speed test, the color images of different sizes are encrypted and decrypted 100 times, and then, the average speed is calculated. The result is shown in Table 10. Furthermore, in Table 11, the speed of encrypting 256 \(\times \) 256 image is compared with other algorithms. Among them, [10] and [20] also used cyclic shift operation. As can be seen from Table 10 and 11, the proposed algorithm has a fast running speed and can meet the requirements of daily confidential communication.
7 Conclusion
In this paper, based on the proposed CPSM and the sensitive chain diffusion structure, a chaotic image encryption scheme is presented. Among them, the CPSM extends the one-dimensional sine map to multidimensional based on segmentation and coupling mechanism, and each dimension had good chaotic characteristics. The sensitive chain diffusion structure not only has a good diffusion effect on plaintext, but also has good sensitivity to ciphertext tampering, and can diffuse the information of ciphertext tampering to the whole decrypted image. Theoretical analysis and experimental results demonstrate that the proposed image encryption scheme is secure and can resist various attacks. Therefore, the algorithm has good application value in communication environment.
Data availability statements
All data generated or analyzed during this study are included in this published article.
References
Aboughalia, R.A., Osama, A.A.: Color image encryption based on chaotic block permutation and xor operation. In: Libyan International Conference on Electrical Engineering and Technologies (LICEET2018) (2018)
Alawida, M., The, J.S., Samsudin, A., Alshoura, W.H.: An image encryption scheme based on hybridizing digital chaos and finite state machine. Signal Process. 164, 249–266 (2019)
Alvarez, G., Li, S.: Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurcation Chaos 16(08), 2129–2151 (2006)
Belazi, A., Talha, M., Kharbech, S., Xiang, W.: Novel medical image encryption scheme based on chaos and dna encoding. IEEE Access 7, 36667–36681 (2019)
Broumandnia, A.: The 3d modular chaotic map to digital color image encryption. Futur. Gener. Comp. Syst. 99, 489–499 (2019)
Chen, Z., Yuan, X., Yuan, Y., Iu, H., Fernando, T.: Parameter identification of chaotic and hyper-chaotic systems using synchronization-based parameter observer. IEEE Trans. Circuits Syst. I-Regul. Pap. 63(9), 1464–1475 (2016)
Fridrich, J.: Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurcation Chaos 8(6), 1259–1284 (1998)
hua Gan, Z., li Chai, X., jun Han, D., ran Chen, Y.: A chaotic image encryption algorithm based on 3-d bit-plane permutation. Neural Comput. Appl 31, 7111–7130 (2019)
Geetha, P., Jayanthi, V.S., Jayanthi, A.N.: Multiple share creation based visual cryptographic scheme using diffusion method with a combination of chaotic maps for multimedia applications. Multimed. Tools Appl. 78, 18503–18530 (2019)
Girdhar, A., Kapur, H., Kumar, V.A.: A novel grayscale image encryption approach based on chaotic maps and image blocks. Appl. Phys. B 127, 39 (2021)
Herbadji, D., Derouiche, N., Belmeguenai, A., Herbadji, A., Boumerdassi, S.: A tweakable image encryption algorithm using an improved logistic chaotic map. Traitement du Signal 36(5), 407–417 (2019)
Hua, Z., Zhou, B., Zhou, Y.: Sine-transform-based chaotic system with fpga implementation. IEEE Trans. Ind. Electron. 65(3), 2557–2566 (2018)
Hua, Z., Zhou, Y.: Image encryption using 2d logistic-adjusted-sine map. Inf. Sci. 339, 237–253 (2016)
Hua, Z., Zhou, Y., Pun, C.M., Chen, C.P.: 2d sine logistic modulation map for image encryption. Inf. Sci. 297, 80–94 (2015)
Hussein, W.A., Al-Saidi, N.M.G., Natiq, H.: A new 2d hénon-logistic map for producing hyperchaotic behavior. In: 2018 Third Scientific Conference of Electrical Engineering, p. 265–269 (2018)
Kang, X., Guo, Z.: A new color image encryption scheme based on dna encoding and spatiotemporal chaotic system. Signal Process. Image Commun 80, 115670 (2020)
Kaur, M., Singh, D., Sun, K., Rawat, U.: Color image encryption using non-dominated sorting genetic algorithm with local chaotic search based 5d chaotic map. Futur. Gener. Comp. Syst. 107, 333–350 (2020)
Khan, J.S., Ahmad, J., Ahmed, S.S., Siddiqa, H.A., Abbasi, S.F., Kayhan, S.K.: Dna key based visual chaotic image encryption. J. Intell. Fuzzy Syst. 37, 2549–2561 (2019)
Khedmati, Y., Parvaz, R., Behroo, Y.: 2d hybrid chaos map for image security transform based on framelet and cellular automata. Inf. Sci. 512, 855–879 (2020)
K.U., S., Mohamed, A.: A novel image encryption scheme using both pixel level and bit level permutation with chaotic map. Appl. Soft. Comput. 90, 106162 (2020)
Lahdir, M., Hamiche, H., Kassim, S., Tahanout, M., Kemih, K., Addouche, S.A.: A novel robust compression-encryption of images based on spiht coding and fractional-order discrete-time chaotic system. Opt. Laser Technol. 109, 534–546 (2019)
Li, C., Tan, K., Feng, B., Lü, J.: The graph structure of the generalized discrete arnold’s cat map. IEEE Trans. Comput. (2021). https://doi.org/10.1109/TC.2021.3051387
Li, C., Zhang, Y., Xie, E.Y.: When an attacker meets a cipher-image in 2018: A year in review. J. Inf. Secur. Appl. 48, 102361 (2019)
Liu, H., Wang, X.: Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Opt. Commun. 284, 3895–3903 (2011)
Liu, Z., Wang, Y., Zhao, Y., Zhang, L.Y.: A stream cipher algorithm based on 2d coupled map lattice and partitioned cellular automata. Nonlinear Dyn. 101(2), 1383–1396 (2020)
Mansouri, A., Wang, X.: A novel one-dimensional sine powered chaotic map and its application in a new image encryption scheme. Inf. Sci. 520, 46–62 (2020)
Naseer, Y., Shah, D., Shah, T.: A novel approach to improve multimedia security utilizing 3d mixed chaotic map. Microprocess. Microsyst. 65, 1–6 (2019)
Parvaz, R., Zarebnia, M.: A combination chaotic system and application in color image encryption. Opt. Laser Technol. 101, 30–41 (2018)
Patro, K.A.K., Acharya, B., Nath, V.: Secure multilevel permutation-diffusion based image encryption using chaotic and hyper-chaotic maps. Microsyst. Technol. 25, 4593–4607 (2019)
ur Rehman, A., Liao, X.F.: A novel robust dual diffusion/ confusion encryption technique for color image based on chaos, dna and sha-2. Multimed. Tools Appl. 78, 2105–2133 (2019)
Slimane, N.B., Aouf, N., Bouallegue, K., Machhout, M.: A novel chaotic image cryptosystem based on dna sequence operations and single neuron model. Multimed. Tools Appl. 77, 30993–31019 (2018)
Sui, L., Duan, K., Liang, J., Zhang, Z., Meng, H.: Asymmetric multiple-image encryption based on coupled logistic maps in fractional fourier transform domain. Opt. Lasers Eng. 62, 139–152 (2014)
Teh, J.S., Tan, K., Alawida, M.: A chaos-based keyed hash function based on fixed point representation. Cluster Comput. 22(2), 649–660 (2019)
Valandar, M.Y., Barani, M.J., Ayubi, P.: A fast color image encryption technique based on three dimensional chaotic map. Optik 193, 162921 (2019)
Wang, X., Sun, H.: A chaotic image encryption algorithm based on improved joseph traversal and cyclic shift function. Opt. Laser Technol. 122, 105854 (2020)
Wang, X., Wang, Y., Zhu, X., Luo, C.: A novel chaotic algorithm for image encryption utilizing one-time pad based on pixel level and dna level. Opt. Lasers Eng. 125, 105851 (2020)
Wang, X., Zhang, J., Cao, G.: An image encryption algorithm based on zigzag transform and ll compound chaotic system. Opt. Laser Technol. 119, 105581 (2019)
Wu, X., Wang, D., Kurths, J., Kan, H.: A novel lossless color image encryption scheme using 2d dwt and 6d hyperchaotic system. Inf. Sci. 349–350, 137–153 (2016)
Xiang, H., Liu, L.: A new perturbation-feedback hybrid control method for reducing the dynamic degradation of digital chaotic systems and its application in image encryption. Multimed. Tools Appl. (2021). https://doi.org/10.1007/s11042-021-10680-y
Ye, G., Jiao, K., Wu, H., Pan, C., Huang, X.: An asymmetric image encryption algorithm based on a fractional-order chaotic system and the rsa public-key cryptosystem. Int. J. Bifurcation Chaos 30(15), 2050233 (2020)
Ye, G., Zhao, H., Chai, H.: Chaotic image encryption algorithm using wave-line permutation and block diffusion. Nonlinear Dyn. 83, 2067–2077 (2016)
Zhang, Y.: The unified image encryption algorithm based on chaos and cubic s-box. Inf. Sci. 450, 361–377 (2018)
Zhou, L., Tan, F., Yu, F.: A robust synchronization-based chaotic secure communication scheme with double-layered and multiple hybrid networks. IEEE Syst. J. 14(2), 2508–2519 (2020)
Zhu, H., Dai, L., Liu, Y., Wu, L.: A three-dimensional bit-level image encryption algorithm with rubik’s cube method. Math. Comput. Simul. 185, 754–770 (2021)
Zhu, H., Zhang, X., Yu, H., Zhao, C., Zhu, Z.: An image encryption algorithm based on compound homogeneous hyper-chaotic system. Nonlinear Dyn. 89, 61–79 (2017)
Zuras, D., Cowlishaw, M., Aiken, A., et al.: Ieee standard for floating-point arithmetic. IEEE Std 754–2008, 1–70 (2008)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (No. 61772215), the MOE Layout Foundation of Humanities and Social Sciences (No. 20YJAZH102), the Foundation of Guangxi Key Laboratory of Cryptography and Information Security (No. GCIS201908), and the Doctoral Talent Training Project of Chongqing University of Posts and Telecommunications (No. BYJS202008).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, J., Wang, Y., Liu, Z. et al. A chaotic image encryption algorithm based on coupled piecewise sine map and sensitive diffusion structure. Nonlinear Dyn 104, 4615–4633 (2021). https://doi.org/10.1007/s11071-021-06576-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-021-06576-z