Abstract
Recently, intelligent transportation systems (ITSs) have emerged. These systems can improve traditional transportation systems and provide traffic information to travelers. In the area of transportation, wireless sensor networks (WSNs) can replace the existing wired sensors and expensive traffic monitoring systems to mitigate the time and costs of installing such systems. However, accurate and on-time traffic information delivery is a major challenge, considering the energy constraints of sensor nodes. In this paper, we propose a two-tier architecture that includes a network of mobile objects (vehicles) in the upper layer and a hierarchical WSN in the bottom layer. Using this approach, a portion of loads on the low-power static sensor nodes can be transferred to mobile objects, such as powerful mobile devices. Moreover, to provide accurate and timely traffic information, a QoS-aware link cost function has been proposed and used for data transmission between the static sensor nodes. In addition, due to the mobility of the objects and the probability of losing packets in the mobile object tier, a reliable data forwarding mechanism has been proposed for this tier. In this mechanism, data packets are forwarded to the neighbors, which enhance the probability of the packets’ being received. The performance evaluation results indicate the effectiveness of the proposed architecture and data reporting mechanism for use in ITS applications.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In recent years, intelligent transportation systems (ITSs) have appeared as an efficient solution for enhancing the performance and safety of transportation systems (Chen et al. 2010; Crainic et al. 2009; Qin and Khan 2012; Simroth and Zahle 2011; Zografos et al. 2009). ITSs integrate advanced electronics, sensors, information technology and communication to improve the convenience and security of transportation systems (Lin et al. 2014; Chen et al. 2013). In ITSs, various important and helpful types of information, such as safety warnings and traffic and traveler information can be retrieved using advanced monitoring technology (Chang et al. 2010; Hickman and Hanowski 2011; Miranda-Moreno and Fu 2006; Rupi et al. 2014). In such systems, using an efficient communication method allows drivers to receive relevant information at the right time. Hence, the drivers can make appropriate decisions based on the relevant situation, which may, for instance, prevent potential accidents and save drivers time (Jin 2014; Xie and Levinson 2009).
However, in most ITSs, safety and traffic data are gathered through wired sensors, communication wires and power-hungry devices. The cost and time required for deployment and maintenance of such systems make widespread deployment of traffic monitoring systems a serious issue.
Wireless sensor networks (WSNs) (Akyildiz and Kasimoglu 2004; Yick et al. 2008) can be considered an appropriate solution to this problem. In fact, WSNs are an economical and low-power wireless monitoring method that is capable of supporting ubiquitous ITS applications. WSNs are a collection of several small sensor nodes with computational, sensing and wireless communication capabilities. In addition to the advantages of lower costs and easy deployment, they allow automated, flexible, scalable and powerful monitoring for ITSs. WSNs are able to aggregate, fuse and complement the perceived information of sensors through data processing and provide improved dynamic results (Anisi et al. 2012). Moreover, as a distributed monitoring system comprised of several sensor nodes, WSNs are robust against the failures of nodes (Lee and Younis 2010) and can be adapted to the traffic infrastructure. However, depending on the application, different quality of service (QoS) parameters including energy of the sensor nodes, reliable data transmission and delay must be satisfied. On the other hand, less security, lower speed and more complex configuration comparing to wired networks can be considered as some disadvantages which need more improvement (Bhattacharyya et al. 2010).
In this area, some research has focused on collecting real-time information in ITSs using WSNs (Coleri et al. 2004; Karpinski et al. 2006; Lee and Ghosh 2008; Tang et al. 2006; Zhao and Guibas 2004). In addition, there are several approaches offering the advantage of a mobile sink in WSNs. Nevertheless, in none of these works, users are in direct contact with the WSN, querying the network and dynamically receiving relevant results. In (Tacconi et al. 2010), the authors proposed an architecture to address this problem. In this architecture, mobile users query the network, and the query responses are sent back to one of the nodes, which acts as an intermediate node between sensor nodes and mobile users (called a vice sink). Then, when the target mobile user reaches the vice sink, it sends the response to the mobile user. However, if this packet transmission is unsuccessful, considerable delays from re-tracking and retransmitting the packet are imposed on the system. In addition, the loss of response packets during data transmission among the sensor nodes can cause the same problem. Moreover, due to the energy constraints of WSNs, such packet overheads consume more energy for the sensor nodes and may cause node failure.
In this paper, we have proposed a two-tier architecture for ITSs using WSNs in which data communication between static sensor nodes and mobile objects is separated in each tier. This process eases the tasks of static sensors and helps them conserve their energy. For further energy conservation, the sensor nodes have been organized into several clusters in which data are delivered to the cluster heads using a tree structure. Moreover, to meet the required quality of service in data delivery, a link cost function has been proposed and applied for data transmission between the senor nodes. Using the proposed link cost function, the energy of the nodes is balanced, and delays and congestion are reduced. Furthermore, in the mobile object tier, a reliable data forwarding mechanism has been proposed for mobile objects that can considerably reduce packet loss.
2 Related Works
The authors in (Munaka et al. 2005) proposed a reliable multicast system as the advanced-join (AJ) system, against network traffic congestion. This paper states that in the conventional data-transmission broadcasting method, Mobile hosts (MHs) are not able to receive information completely within the limited time. Hence, they consider a data-retransmission method and data-recovery-processing method to solve this problem in the AJ system. The advantages of this system are the reduction of message traffic and the elimination of packet loss during the movement of MHs. The data-retransmission method determines the movement of MHs of the same multicast group and performs data retransmission by coordinating retransmission requests from MHs. The data-recovery-processing method carries out data recovery between base stations by retransmitting the requested data at the designated base stations.
The approach proposed in (Huang et al. 2008) suggests network planning of deploying access points (APs) to improve throughput and the quality of service and extend the coverage of the ITS network. In this paper, an analytical model was developed to evaluate throughput, frame delay, and jitter for the considered wireless mesh network (WMN) using the carrier-sense multiple-access medium access control protocol. The advantages of this study include considering the user throughput of WMNs and QoS (delay and jitter). The authors also suggest using different channels for each AP to reduce contention collisions and improve the throughput and scalability of WMSs.
The authors in (Li et al. 2007) proposed a sensor network with a mobile station (SNMS), which is a two-tiered network architecture based on a wireless sensor network and peer-to-peer (P2P) network. The lower tier of the SNMS is a single-hop network in which mobile stations directly receive data from sensors in one hop rather than the conventional multi-hop sensor networks. Meanwhile, in the upper tier, the data fusion network is a decentralized P2P network.
In (Güner et al. 2012), an alternative model was proposed to estimate delay caused by incidents. This model can be integrated with routing methods to reduce the latency of packet delivery, which causes negative effects on Just-In-Time (JIT) manufacturing operations. In this paper, a dynamic vehicle routing model based on the Markov decision process (MDP) formulation was developed to solve the non-stationary stochastic shortest path problem by considering delivery delay reasons, including non-recurrent and recurrent congestion. The dynamic routing model uses traffic information regarding speeds and incidents from ITS sources to improve the delivery performance.
The authors in (Laborczi et al. 2010) proposed an Integer Linear Programming (ILP) to predict the optimum position where vehicles should send queries to collect information about congested roads. The focus of this paper is to solve the optimization problem that arises in distributed Traffic and Travel Information (TTI) dissemination approaches, which use broadcasting to spread traffic information.
The proposed ITS system in (Tacconi et al. 2010) uses wireless sensor networks and enables cars to send queries to the deployed wireless sensor network and receive required traffic information. In this system, the network is built upon three different nodes, are vice sinks (VSs), mobile sinks (MSs) and sensor nodes (SNs). A vehicle, acting as a mobile sink (MS), queries the WSN while moving along the network. SNs communicate in a multi-hop manner to deliver information to the VSs, and VSs, which are the closest nodes to the streets, communicate directly with the MS.
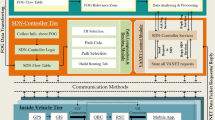
3 System Architecture
The system architecture consists of two tiers, a static sensor tier and mobile object (user) tier. Thousands of sensor nodes are densely deployed over the environment to monitor the area, sense phenomena of interest and aid mobile users, who are equipped with mobile sensors and connected to each other through a peer-to-peer network. As an application scenario, mobile users (vehicles) trying to find free parking spots can be considered. A vehicle could be connected to the network, transmit a query and ask for the desired area. Then, the query results provided by the static sensor nodes can be sent back to the querying mobile objects through relay by other objects. This type of two-tier network has a broad range of applications for high numbers of mobile objects, such as in highways or urban environments. In the following section, the system architecture tiers are described.
3.1 Static Sensors Tier
This tier consists of several static sensor nodes that have limited battery power and are deployed around the area of interest with a high density. Additionally, it is assumed that each node is aware of its location. To specify the locations, a distributed localization scheme can be used (Lee et al. 2013).
The whole network is assumed to be organized by a number of clusters, and, in each cluster, one of the nodes is selected as the Cluster Head (CH). In the proposed scheme, because of the energy constraints of WSNs, to conserve energy for the static sensor nodes, both cluster-based and tree-based approaches have been utilized. Clustering mitigates energy consumption by improving bandwidth utilization and reducing overheads. In addition, by using a tree topology, data can be transmitted and collected without much data redundancy. Furthermore, the network coverage area can be enhanced by adding new nodes to the network. In the proposed scheme, referring to the direct relation of energy consumed in wireless transmission to the square of the distance between nodes in communication (Cordeiro and Agrawal 2006), a tree-based approach has been used inside each cluster. In the tree formation mechanism, similar to TAG (Madden et al. 2002), each epoch is divided to several time slots and the time slots are assigned to different levels of a routing tree in reversal form. Therefore, each node depends on its level in the tree, transmits its data to its parent in its own time slot. Using this idea, because cluster-member nodes send their data packets to their neighbor nodes instead of the cluster head, their transmission distance is reduced, and, as a result, the overall energy consumption of the sensor nodes in each cluster is reduced.
3.2 Mobile Object Layer
Mobile objects (i.e., cars) move along the area of interest in this tier of the network. Generally, mobile objects have high communication and computation capabilities. Such mobile nodes can use rechargeable batteries and localization devices, such as GPSs, which also provide a global clock. Thus, information about speed, direction and position are assumed to be permanently available. The mobile objects can have two radios performing in dissimilar frequency bands (Kottapalli et al. 2003), for instance, a 915 MHz for communication with cluster heads and 2.4 GHZ band for inter-communication. Such mobile objects collect data from the cluster heads within their coverage area, process the data and forward it to the target node. By using this mechanism, more mobile objects can be added to the network or some can be removed without much impact on the whole network. In addition, the failure or departure of mobile sensors will not disturb the process of data collection. Hence, scalability and robustness for the network can be ensured.
4 Communication Framework
The proposed communication and routing framework is also based on a two-layer network structure that includes a static sensor layer and mobile object layer. In the layered framework, the static sensor layer relates to QoS-aware data routing between the static sensor nodes deployed in the area of interest, and the mobile object layer addresses the reliable data communication of the mobile objects.
In this framework, after a mobile object injects a query into the network, the node (cluster head) closest to the mobile object receives the query. Then, the query is routed toward the query region target by static sensors; however, in the return route, the response packet reaches the cluster head closest to the query region target. Next, the packet is sent to a mobile object that is in the local proximity of the cluster head. Here, based on the proposed data forwarding mechanism for mobile objects, the response packet is forwarded to the querying object through other mobile objects considering their mobility issue.
An applicable scenario for the proposed communication framework is depicted in Fig. 1.
When a mobile object wants some information about the environment (e.g., free parking spaces), it injects a query into the network. The nearest CH in the radio range of the mobile object receives the query. After receiving the query, the CH checks whether the area of interest in the query matches the area it covers. If the answer is yes, it disseminates the query to its cluster and forwards it to its neighboring CH. The reason for this forwarding is that sometimes the area of interest can be covered by other clusters, too. For instance, the area might be large, and part of it may be covered by another cluster. By contrast, when a CH receives a query and the area of interest is outside the area of the cluster, it forwards the query to other cluster heads. This process continues until all the CHs receive the query.
For data delivery from static sensor nodes to CHs, each node considers the cost of the links and forwards its data packet using a link cost function that ensures reliable and energy-efficient data transmission. When a CH receives a query result, to save time, it sends the result to the first mobile object that enters its radio range.
When a mobile object receives a query result from a CH, it first checks whether it is the sender of the query. If not, to address the mobility issue of the object, it selects the mobile object in its radio range, which is more reliable and nearer to the destination than others, and forwards the packets to it. This process is repeated until the querying mobile object receives the result. The details of the proposed routing framework are described in the following sections.
4.1 Link Cost Function
Similar to (Anisi et al. 2013), we used a link cost function to calculate the link cost of the next hop neighbors (parent nodes) during the initialization phase. However, due to the necessity of timely information delivery in ITSs, in the proposed link cost function, as in (Misra et al. 2009), we use absolute time rather than the hope count to reduce both latency and congestion. Hence, the proposed link cost function considers the remaining energy of the static sensor nodes, their available buffer size and the time needed to reach the CH. As a result, the network lifetime can be extended, packet loss is controlled and delays and congestion are reduced.
The cost of transmitting packet (C) from node y to node x is defined as follow:
Table 1 shows the notations of the function. In the proposed equation, the values of \( \left(1 - \frac{E_{rem(x)}}{E_{ini(x)}}\right) \) and \( \left(1 - \frac{B_{ava(x)}}{B_{total}(x)}\right) \) can be 1 in the worse case (no remaining energy or no enough space in the buffer size) and 0 in the best case.
In addition, \( \left(\frac{T_{CH(x)}}{T_{MAX}}\right) \) is the proportion of the time required to reach CH from node x to the maximum time required to reach CH. T MAX is a constant value which is given a priori. C is the total cost of transmitting a packet from node y to node x. In conclusion, the neighbor node with the lowest C will be selected as the next hop neighbor. α, β and μ are the weight of the factors which can change the effect of energy, buffer size and time to reach CH. Therefore, based on the aim, requirements and issues of the scenario, they can get different value. In the proposed mechanism, by considering the value of μ, greater then α, β, the effect of energy and buffer size comparing to time to reach CH are reduced; thereby, the probability of selecting the candidate neighbors nearer to the CH is increased and the chance of using a detour will be decreased. For instance, among the candidate neighbors if one of them is considerably closer to the CH, it gets higher value and finds more chance to be selected; otherwise, when the differences between time to reach CH is not much, energy and buffer size could be determinant factors. The above description has been added to Section 4.1.
4.2 Initialization
An initialization algorithm is needed to choose the most eligible neighbor as the next hop based on the proposed link cost function. Therefore, in the proposed approach, an initialization algorithm is executed immediately after deploying the nodes. The neighbor table is initially empty and initialized by this process. In this process, an initialization packet, which consists of the remaining energy of the nodes, the time needed to reach the CH and the available buffer size of the nodes with the general fields of a packet, is broadcast to the network. When a sensor node receives the initialization packet, it keeps the information about its neighbors, which are candidates of the next hop, in its routing table.
Table 2 presents the packet header of our algorithm. To compute the effectiveness of the routing paths, the time to reach CH (T CH(x)), remaining energy of the node (E rem(x)) and available buffer size (B ava(x)) are the main parameters used in the link cost function. The whole mechanism works as follow:
After deploying the static sensor nodes, the CHs broadcast an initialization packet to their clusters in which Pkt_st is set to zero, the available buffer size is considered maximum and the node energy is set to the actual value. When a node receives the initialization packet, it carries out the following tasks:
-
Calculate the time required for a packet to reach the mobile object from the information sent by the previous node, and update T CH(x).
-
Calculate the remaining energy after one transmission and update the E rem(x).
-
Calculate the available buffer size and update B ava(x).
-
Propagate the initialization packet to other cluster members.
This process continues until all the static sensor nodes receive the initialization packet. After this phase, each node knows the specifications of its neighbors as its possible parent nodes. Algorithm 1 illustrates this process.
Algorithm 1 Initialization
The cluster head broadcasts the initialization packet
For each initialization message receiver:
-
1.
insertNeighbourtable (T CH(x) , E rem(x) , B ava(x) , Node_ID)
-
2.
reception_time = current_time – start_time
-
3.
T CH(y) = T CH(x) + reception_time
-
4.
Pkt_st = current_time
-
5.
E rem(y) = E rem(y) - 1
-
6.
packetBroadcast (T CH(y) , E rem(y) , B ava(y) , Node_ID)
In the algorithm, node y, as the node that receives the initialization packet, maintains the information of its neighbors (such as node x) in the neighbor table, updates the information of the initialization packets and rebroadcasts the packet.
4.3 Query Injection
When a mobile object wants some traffic information from the environment, such as free parking spaces in the surrounding area, a query is injected into the network. After the nearest CH in the radio range of the mobile object receives the query, it checks whether it can totally or partially cover the area of interest in the query. If possible, the CH, as the root of a tree in the cluster, transmits the packets to its children; otherwise, it sends the query packet to its neighboring CHs. The child nodes also repeat this process until all the nodes in the cluster receive the query.
4.4 Query Response Routing
After all the nodes in the cluster receive the query, the results of the nodes are sent back to the querying mobile object. In the proposed scheme, the query result routing is performed on two levels. The first level relates to the routing response packet in the static sensor layer, and the second level is performed between mobile objects.
4.4.1 Query Result Routing on the Static Sensor Layer
When transmitting a query result, based on the computed link cost of the possible parents, the query responder selects the parent with the lowest link cost and transmits the response packet to it. Similarly, when an intermediate node receives a query response, it selects the parent with the lowest link cost and forwards the packet to it. This process continues until the head of the cluster receives the results of the cluster members. When a CH receives a query result, to reduce the power required for transmission and saving more energy, it immediately sends the result to the nearest mobile object in its radio range. Then, the mobile object forwards the packet toward the destination using the nodes closest to the querying vehicle. If the CH cannot find a mobile object in its communication ranges, it forwards the packet to one of its neighboring CHs which is the closest to the querying object to send the result to a mobile object.
4.4.2 Query Result Routing on the Mobile Object Layer
On this layer, the packet is sent toward the initial position of the query sender and forwarded by the intermediate mobile objects until it can be received by the query sender. In the proposed scheme, when a mobile object in the data forwarding route receives a query result packet, it first checks the query source of the packet to find whether it is the sender of the query. If it is the sender, the process of data delivery is finished; otherwise, it forwards the packet toward the querying object. However, in ITSs, due to the mobility of the vehicles, packet loss is one of the main issues, causing delays and energy consumption.
In previous approaches (Faouzi et al. 2011; Tacconi et al. 2010; Zhang et al. 2011), this issue is not completely taken into consideration. In conventional routing mechanisms for ITSs, data packets are always transmitted to the node or vehicle that is the closest to the destination. However, based on the movement of the objects, an object may leave the radio range of its previous hop object before receiving the transmitted packet, which results packet loss. Therefore, in addition to considering the length of the paths, the reliability of the paths should also be taken into consideration.
In the proposed algorithm, of the possible neighbors as the next hop, the data packet is forwarded to the mobile object (with a speed of v) that is the closest to the destination and does not leave the radio range of the previous hop object after time t. Here, ‘t’ is a constant value considered based on the defined scenario. In another words, “t” is the time duration in which a mobile object does not leave the radio range of the previous hop object (it can be set through consultation with experts, or by statistical analysis of real trace data). In fact, “t” has an opposite relation with “v”. When the vehicles have high speeds, they can leave the radio range of the previous hop object faster; thereby, the value of “t ” must be considered lower. On the other hand, when their speed is not high, there is more time to leave the radio range of the previous hop object and “t” must be considered higher.
Figure 2 illustrates the proposed algorithm, where the small circles represents the mobility area of the nodes and the large circle represents the radio range of object s. Suppose that mobile object s wants to forward its packet to one of its neighbors. In conventional algorithms, node f will be selected as the next hop node because it is the closest to the destination. However, due to the movement of the mobile objects (where x = vt), it may leave the radio range of s. Hence, in the proposed algorithm, the data packet is forwarded to the node that can satisfy both mentioned conditions. For instance, in this example, based on the speed and radio range of the objects, the objects (such as object e) that is the closest to the destination and does not leave the radio range of s will be selected as the next hop object.
In algorithm 2, the data forwarding process has been detailed. In the algorithm, neighbor_list is the list of the single hop neighbors of the transmitter object, nexthop is the next hop neighbor candidate and nexthop_dis is its distance, correspondingly.
Algorithm 2 Data forwarding in mobile object layer
For each transmitter object
nexthop_dis =0;
For (i = 0; neighbor_list [i] != -1 ; i++)
{
If ( distance (neighbor_list [i].destination) < nexthop_dis &&
distance (neighbor_list [i].transmitter )+ vt <= radio_range){
nexthop_dis = distance (neighbor_list [i].destination);
nexthop = neighbor_list [i];
}
}
ForwardData (nexthop);
Figure 3 shows another example of data forwarding between mobile objects in the proposed and conventional algorithms, where the small circles represent the mobility areas of the nodes and the large circles represent the radio range of the nodes. In addition, the solid line is the selected route represents the proposed mechanism, and the dotted line represents the data routing route in conventional algorithms.
In conventional algorithms, object s selects object j as the next hop based on the distance of the neighbors to the destination. Next, node b is selected by node j. Node b then chooses node x. This process continues until the destination node is reached. By contrast, in the proposed algorithm, after s selects node j, object b is not selected as the next hop because it may leave the radio range of object j. Instead, object q, which can satisfy both conditions of the proposed algorithm, is selected as the next hop.
While data packets are forwarded toward the initial position of the querying mobile object, the position of the querying mobile object might have been changed. Therefore, when a mobile object (last node on the geographic routing path), cannot find any node nearer to destination (where the querying object was first located), the query result is broadcasted to other mobile objects. However, to cope with overhead problem of such flooding, it is controlled and restricted to the travelling area of the querying object using the query parameters. Hence, The radius of the controlled flooding centered as initial position of the query object is calculated as r = v∆t, Δt = t loc − t i where t loc is the local time, t i is the time of query injection and v is the maximum velocity of the mobile object. Therefore, by broadcasting the query result in the region with the radius of r, it will be received by the querying mobile object.
The proposed mechanism is mainly for high traffic situations. As it is demonstrated in Fig. 6, increasing the number of mobile objects can improve the efficiency of the proposed mechanism as it can increase the number of eligible candidates and result in a larger number of successfully received packets. On the other hand, the problem which the proposed mechanism deals with is more considerable and serious when there are more number of users (mobile objects). For example, finding free parking slot becomes more demanding when more vehicles are searching for free slots; Otherwise, using such system does not seem necessary as empty slots can be seen (i.e. few cars and several free parking slots). Nevertheless, low traffic density cannot stop the proposed mechanism. When a mobile object is not able to locate a next-hop object nearer to destination in its communication range (void node), similar to (Stojmenovic and Lin 2001; Chen and Varshney 2006), a void handling function will be invoked in which the void node broadcasts the packets to its one-hop neighboring nodes. Every mobile object which receives the packet acts independently and forwards the packets toward the querying object using the proposed mechanism in Section 4.4.2. In a completely separated neighborhood, similar to (Tonguz et al. 2007), carry and forward recovery strategy is used in which a node buffers the packet until another node enters the transmission range. Otherwise, the packet is dropped when the time expires.
5 Performance Evaluation
The proposed approach was simulated and evaluated using J-SIM (Java-based simulator) (Sobeih et al. 2006). Similar to (Tacconi et al. 2010), sensor nodes uniformly surround a square with a hole in the center of the square. The distance between two adjacent nodes is 25 m. The size of the hole is considered 500 m_ 500 m, the initial energy of the nodes is 50 J and IEEE 802.15.4 is selected for the MAC protocol.
The movement of mobile objects is based on the random waypoint (RWP) mobility model (Camp et al. 2002; Bettstetter et al. 2003; Tacconi et al. 2010) and is limited to the area of WSN deployment. This consists of the case of mobile objects moving (driving) around a city block, and looking for a free parking spot as depicted in Fig. 4. Mobile objects move along the outer road at a minimum speed of 5 m/s and a maximum speed of 20 m/s and can only communicate with CHs with a communication range of 25 m. The reason of selecting RWP model is that it is a random mobility model in which the mobile object moves randomly and freely without restriction. In another word, the destination, speed and direction are all chosen randomly and independently of other objects; hence, it could be the best choice for the simulation of vehicles’ movement.
For cluster formation, we have used a simple clustering mechanism similar to LEACH protocol (Heinzelman et al. 2000; Xiangning and Yulin 2007); however, any other advanced cluster formation technique can be used. In the cluster formation mechanism, CHs with an enhanced energy capacity (Soro and Heinzelman 2005; Choe et al. 2010) which are disseminated along the WSN network perimeter, broadcast an advertisement message (ADV) using a non-persistent carrier-sense multiple access (CSMA) MAC protocol to notify other nodes of their role in the network. Then, each node determines its cluster by choosing the CH that can be reached using the least communication energy, based on the received signal strength (RSS) of ADV from each CH.
To evaluate the performance of the proposed approach, several metrics have been measured and compared with (Tacconi et al. 2010).
Figure 5 compares the total number of transmitted packets needed for the delivery of a response message in the proposed approach and in Geo-routing. When the number of nodes increases, the total number of packets increases correspondingly. However, in (Tacconi et al. 2010), when data packets are lost during data transmission among the sensor nodes due to congestion or node failure, more packets are sent in the network. In addition, when vice sinks lose a mobile object, rerouting the packets toward the most likely position of the mobile object increases the total number of transmitted packets. By contrast, the proposed approach avoids sending extra packets by controlling the number of lost packets, which is performed by using the proposed link cost function for data transmission between the sensor nodes and the proposed reliable mechanism for data transmission between mobile objects.
Figure 6 presents the packet delivery ratio (PDR) of the proposed approach in comparison with Geo-routing.
The packet delivery ratio (PDR) is the number of data packets delivered to the mobile object to the number of packets generated by the source nodes. In the following equations, i = 1 to n is the number of iteration in measuring the factor.
Hence, due to the larger number of transmitted packets and lost packets in Geo-routing, its PDR is less than the proposed approach. Moreover, in Fig. 7, the number of retransmitted packets is compared with Geo-routing. In the proposed mechanism, in the static sensor layer, the lost packets in the clusters are retransmitted using retransmission mechanism of TAG approach (Madden et al. 2002). Therefore, when a node is not successful in transmitting its data to its parent in its own time slot, the lost packet is retransmitted to the parent. In addition, in the mobile object layer, using the proposed reliable mechanism in packet transmission among the mobile objects, the chance packet loss has been effectively reduced. Nevertheless, in case of packet loss, the lost packet is retransmitted using the default retransmission mechanism of MAC layer.
Figure 8 demonstrates the effect of the number of mobile objects on the PDR. In Geo-routing, because data routing is performed only between static sensor nodes and there is no data communication between mobile objects, changing the number of mobile object has no effect on its performance. By contrast, a larger number of mobile objects can positively affect the performance of the proposed approach. According to the proposed data forwarding mechanism among mobile objects, data packets are forwarded to the neighbors that are the closest to the destination and the most reliable. Therefore, increasing the number of mobile objects can increase the number of eligible candidates and result in a larger number of successfully received packets.
Figure 9 shows the performance of the proposed approach in comparison with Geo-forwarding, Delay-forwarding and Energy-forwarding in terms of the time to first failure. According to the diagram, the proposed approach has the longest time to first failure. In the proposed approach, clustering reduces the energy consumption of the nodes by improving bandwidth utilization. In addition, the proposed link cost function considers the residual energy of the nodes; therefore, the time to failure of the nodes is delayed.
In Figure 10, the packet latency of the proposed approach, i.e., the duration between sending a query and receiving the response, is compared with other approaches. According to the diagram, the delay-forwarding mechanism, by using a cross-layer strategy based on an adaptive duty cycle at each sensor node, has a lower latency than the others. The proposed approach also performs properly in term of latency; instead of the hop count, the absolute travel time between a node and mobile object is considered in the approach to minimize packet latency. Moreover, by considering the residual energy and available buffer size of the nodes in the static sensor layer and using the proposed reliable mechanism in the mobile object layer, node failure and packet loss are mitigated, and, correspondingly, the required time for retransmissions of the lost packets is reduced.
Figure 11 presents a comparison between the energy consumption of the proposed approach and the energy-forwarding mechanism. In WSNs, most of the energy consumption is related to transmission, which consumes considerably more than reception and computation. Hence, like (Misra and Thomasinous 2010), we measured energy consumption based on the number of packets transmitted in the network. Therefore, to calculate the energy consumption, the following formula has been used:
where P t denotes the required energy for transmission, which was considered as 50 nj, ∑ n i = 1 n P total is the total number of packets transmitted in the network and N is the total number of nodes. According to the diagram, the evaluation results demonstrate that the proposed approach outperforms the energy-forwarding mechanism. In the proposed approach, clustering and the tree topology mitigate energy consumption by improving bandwidth utilization and reducing overheads. Moreover, by using the proposed link cost function in the static sensor layer, the energy of the nodes is balanced, and the data are routed toward the mobile objects through less congested routes. As a result, node failure and packet loss are prevented, and additional energy is not used to re-route the lost packets. Similarly, the proposed mechanism in the mobile sensor layer reduces the number of packet retransmissions by forwarding the nodes to the most reliable neighbors, which can result in additional energy saving.
6 Conclusions
In ITSs, the large-scale deployment of an advanced monitoring system with a low cost and installation time is a considerable challenge. WSNs can be considered an appropriate solution to this problem. In this paper, a two-tier architecture composed of a WSN and mobile objects has been proposed for ITS applications. In this architecture, the WSN monitors the area, and mobile objects (vehicles) are able to send queries and receive required traffic information. This strategy simplifies the function of sensor nodes and reduces their energy consumption. In the static sensor layer, sensor nodes have been organized into several clusters, and data are transmitted toward the cluster heads using a QoS-aware link cost function. After receiving a query response from a cluster head, a data packet is forwarded toward the querying object using a reliable mechanism capable of reducing packet loss. According to the simulation experiments, the proposed approach is capable of providing required traffic information with a high packet delivery ratio and low latency while conserving the energy of the sensor nodes and extending their lifetimes.
References
Akyildiz IF, Kasimoglu IH (2004) Wireless sensor and actor networks: research challenges. Ad Hoc Netw 2(4):351–367
Anisi MH, Abdullah AH, Razak SA, Ngadi MA (2012) Overview of data routing approaches for wireless sensor networks. Sensors 12(4):3964–3996
Anisi MH, Abdullah AH, Razak SA (2013) Energy-efficient and reliable data delivery in wireless sensor networks. Wirel Netw 19(4):495–505
Bettstetter C, Resta G, Santi P (2003) The node distribution of the random waypoint mobility model for wireless ad hoc networks. Mobile Comput IEEE Trans 2(3):257–269
Bhattacharyya D, Kim TH, Pal SA (2010) A comparative study of wireless sensor networks and their routing protocols. Sensors 10:10506–10523
Camp T, Boleng J, Davies V (2002) A survey of mobility models for ad hoc network research. Wirel Commun Mob Comput 2(5):483–502
Chang BR, Tsai HF, Young CP (2010) Intelligent data fusion system for predicting vehicle collision warning using vision/GPS sensing. Expert Syst Appl 37(3):2439–2450
Chen D, Varshney PK (2006) On demand geographic forwarding for data delivery in wireless sensor networks. Comput Commun 30(14–15):2954–2967
Chen S, Chen F, Liu J, Wu J, Bienkiewicz B (2010) Mobile mapping technology of wind velocity data along highway for traffic safety evaluation. Trans Res C Emerg Technol 18(4):507–518
Chen YB, Lam WHK, Sumalee A, Li Q, Shao H, Fang Z (2013) Finding reliable shortest paths in road networks under uncertainty. Netw Spat Econ 13(2):123–148
Choe HJ, Ghosh P, Das SK (2010) QoS-aware data reporting control in cluster-based wireless sensor networks. Comput Commun 33:1244–1254
Coleri S, Cheung SY, Varaiya P (2004) Sensor networks for monitoring traffic. In: Proc. of Allerton Conf
Cordeiro CDM, Agrawal D (2006) Ad-hoc & sensor networks: theory and application. World scientific Publisher, USA
Crainic TG, Gendreau M, Potvin J-Y (2009) Intelligent freight-transportation systems: assessment and the contribution of operations research. Trans Res C Emerg Technol 17(6):541–557
Faouzi N-EE, Leung H, Kurian A (2011) Data fusion in intelligent transportation systems: progress and challenges – A survey. Inf Fusion 12(1):4–10
Güner AR, Murat A, Chinnam RB (2012) Dynamic routing under recurrent and non-recurrent congestion using real-time ITS information. Comput Oper Res 39(2):358–373
Heinzelman WB, Chandrakasan AP, Balakrishnan H (2000) Energy efficient communication protocol for wireless microsensor networks. In: Proceedings of the 33rd Hawaaian Interantional Conference on System Science, Hawaii
Hickman JS, Hanowski RJ (2011) Use of a video monitoring approach to reduce at-risk driving behaviors in commercial vehicle operations. Transport Res F: Traffic Psychol Behav 14(3):189–198
Huang JH, Wang LC, Chang CJ (2008) QoS provisioning in a scalable wireless mesh network for intelligent transportation systems. IEEE Trans Veh Technol 57(5):3121–3135
Jin W-L (2014) Advances in dynamic traffic assgmnt: TAC. Netw Spat Econ. doi:10.1007/s11067-014-9250-x
Karpinski M, Senart A, Cahill V (2006) Sensor networks for smart roads. In: Proc. of IEEE PerCom Workshops, Pisa, Italy
Kottapalli V, Kiremidjian A, Lynch J, Carryer E, Kenny T, Law K, Lei Y (2003) Two-tiered wireless sensor network architecture for structural health monitoring, in: The 10th Annual International Symposium on Smart Structures and Materials, San Diego, USA, March 2003
Laborczi P, Mezny B, Török A, Ruzsa Z (2010) Query-based information gathering in intelligent transportation systems. Electron Notes Discrete Math 36:1201–1208
Lee S, Ghosh DYA (2008) Intelligent parking lot application using wireless sensor networks. In: Proc. of CTS, Irvine, CA, USA
Lee S, Younis M (2010) Recovery from multiple simultaneous failures in wireless sensor networks using minimum Steiner tree. J Parallel Distrib Comput 70(5):525–536
Lee J, Chung W, Kim E (2013) A new kernelized approach to wireless sensor network localization. Inf Sci 243:20–38
Li LI, Liu YA, Tang BH (2007) SNMS: an intelligent transportation system network architecture based on WSN and P2P network. J China Univ Posts Telecommun 14(1):65–70
Lin X, Tampere CMJ, Immers B (2014) The cost of environmental constraints in traffic networks: assessing the loss of optimality. Netw Spat Econ. doi:10.1007/s11067-014-9228-8
Madden S, Franklin MJ, Hellerstein JM, Hong W (2002) TAG: a tiny aggregation service for ad-hoc sensor networks. In: ACM SIGOPS Operating Systems Review, Boston, MA, USA, Dec 2002
Miranda-Moreno LF, Fu L (2006) A comparative study of alternative model structures and criteria for ranking locations for safety improvements. Netw Spat Econ 6(2):97–110
Misra S, Thomasinous PD (2010) A simple, least-time, and energy-efficient routing protocol with one-level data aggregation for wireless sensor networks. J Syst Softw 83(5):852–860
Misra S, Tiwari V, Obaidat MS (2009) LACAS: learning automata-based congestion avoidance scheme for healthcare wireless sensor networks. IEEE J Sel Areas Commun 27(4):789–817
Munaka T, Yamamoto T, Watanabe T (2005) A reliable advanced-join system for data multicasting in ITS networks. IEEE Trans Intell Transp Syst 6(4):424–438
Qin X, Khan AM (2012) Control strategies of traffic signal timing transition for emergency vehicle pre-emption. Trans Res C Emerg Technol 25:1–17
Rupi F, Bernardi S, Rossi G, Danesi A (2014) The evaluation of road network vulnerability in mountainous areas: a case study. Netw Spat Econ. doi:10.1007/s11067-014-9260-8
Simroth A, Zahle H (2011) Travel time prediction using floating car data applied to logistics planning. IEEE Trans Intell Transp Syst 12(1):243–253
Sobeih A, Hou J, Kung L-C, Li N, Zhang H, Chen W-P, Tyan H-Y, Lim H (2006) J-Sim: a simulation and emulation environment for wireless sensor networks. IEEE Wirel Commun 13(4):104–119
Soro S, Heinzelman WB (2005) Prolonging the lifetime of wireless sensor networks via unequal clustering. In: Proceedings of the 19th IEEE International Parallel and Distributed Processing Symposium (IPDPS’05), 260–264, Denver, Colorado
Stojmenovic I, Lin X (2001) Loop-free hybrid single-path/flooding routing algorithms with guaranteed delivery for wireless networks. IEEE Trans Parallel Distrib Syst 12(10):1023–1032
Tacconi D, Miorandi D, Carreras L, Chiti F, Fantacci R (2010) Using wireless sensor networks to support intelligent transportation systems. Ad Hoc Netw 8(5):462–473
Tang V, Yuan Z, Jiannong C (2006) An intelligent car park management system based on wireless sensor networks. In: Proc. of ISWPC, Phuket, Thailand
Tonguz O, Wisitpongphan N, Bai F, Mudalige P, Sadekar V (2007) Broadcasting in VANET. In: Proceedings of 2007 mobile networking for vehicular environments 7–12, Anchorage, Alaska
Xiangning F, Yulin S (2007) Improvement on LEACH protocol of wireless sensor network. In: Proceedings of international conference on sensor technologies and applications (SENSORCOMM 2007), 260–264, Valencia, Spain
Xie F, Levinson D (2009) Modeling the growth of transportation networks: a comprehensive review. Netw Spat Econ 9(3):291–307
Yick J, Mukherjee B, Ghosal D (2008) Wireless sensor network survey. Comput Netw 52(12):2292–2330
Zhang J, Wang FY, Wang K, Lin WH, Xu X, Chen C (2011) Data-driven intelligent transportation systems: a survey. IEEE Trans Intell Transp Syst 12(4):1624–1639
Zhao F, Guibas L (2004) Wireless sensor networks: an information processing approach. Elsevier/Morgan-Kaufmann, Boston
Zografos KG, Androutsopoulos KN, Spitadakis V (2009) Design and assessment of an online passenger information system for integrated multimodal trip planning. IEEE Trans Intell Transp Syst 10(2):311–323
Acknowledgement
The authors thank University of Malaya for the financial support (UMRG grant RG325-15AFR) and facilities to carry out the work.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Anisi, M.H., Abdullah, A.H. Efficient Data Reporting in Intelligent Transportation Systems. Netw Spat Econ 16, 623–642 (2016). https://doi.org/10.1007/s11067-015-9291-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11067-015-9291-9