Abstract
Sharing or transmitting the digital information in online is increasing day by day since the usage of internet has become a habituation for everyone, which led to the large-scale violation of copyright issues. Now a days, majority of the data is being shared in the form of digital images which is quite easy for the copyright violators to forge and fake those images and then shared for profit. To deal with these copyright violations, digital watermarking came into existence as a potential solution that utilizes the concept of data hiding. This article proposed an approach for a non-blind color image watermarking (NB-CIW) by employing the algorithm named as singular value decomposition in translation invariant wavelet (SVD-TIW) domain. In addition, to further optimize the proposed SVD-TIW algorithm, enhanced grey-wolf optimizer (E-GWO) is presented which is an efficacious optimization approach in meta-heuristic algorithms. Further, to disclose the robustness and effectiveness of proposed NB-CIW using SVD-TIW-EGWO approach, different sort of attacks is enforced on watermarked image and extracted the accurate watermark image. Simulations on various test images with comparison to the state-of-art NB-CIW methodologies demonstrate the superiority of proposed NB-CIW using SVD-TIW-EGWO approach with respect to quality evaluation metrics like normalized cross correlation (NCC), root mean square error (RMSE), structural similarity (SSIM) index and even that of peak signal-to-noise ratio (PSNR) as well.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Now a day’s internet innovation has become unavoidable domain of everybody’s life. Massive measure of information is being traded through messages, social sites, and corporate sites in assortment of structures. This multimedia information can be as images, sound records, video documents, content reports and so on. This information is at extraordinary hazard by aggressors at different phases of its transmission. One of the potential strategies for ensuring information is scrambling the information for example changing over the information in some ambiguous organization with the goal that it gets hard to decipher. Anyway, if attacker can figure out how to get key source of encryption, unscrambling the message will disclose the information to him. Therefore, securing the multimedia information from the copyright violators is quite challenging and difficult task. To deal with these copyright violations, digital watermarking came into existence as a potential solution that utilizes the concept of data hiding [3, 9, 11], where a message information which is in the form of digital image is embedded into the cover image without degrading its quality. Thus, it is quite hard for the attackers to identify that the cover images comprise of a message image which is known as watermark. Main objective of digital watermarking is to provide an assurance for the information of copyright owners and authorized people from the copyright violators. Practically, digital watermarking can be obtained in two forms, which includes spatial and spectral domains. In spatial domain-based digital watermarking the message will be embedded into the cover image by altering the pixel information directly. Beside its simplicity and easiness, it has several flaws like lack of imperceptibility, lesser robust against few attacks like rotation, scaling and translation. Spectral domain is also called as transform domain-based digital watermarking, which first converts both cover and watermark images into another form then applies different sort of algorithms to embed the watermark into cover image. This is very robust and provides higher imperceptibility as compared to spatial domain-based digital watermarking approaches. Robustness is referred as the capability to secure any multimedia information modification before the information destruction. This robustness can be computed through NCC values. Imperceptibility is cited as the hidden information detection, which can be defined by the values of PSNR. From the past decades, lots of research was done on both spatial and transform domain watermarking techniques. Among those, discrete wavelet transform (DWT)-based approaches [7, 19] are most popular due to their simplicity in implementation. However, they were failed to obtain higher imperceptibility and accurate extraction of watermark as well. There are few methods, which utilized the concept of singular value decomposition (SVD) [7], the combo of DWT with SVD [13] and hidden markov model (HMM) [1]. But they suffered from lack of robustness and more sensitive against the attacks. To achieve the non-blind watermarking properties, NB-CIW approaches are developed using the DCT transformation. In the [4], authors discussed about Arnold transform for implementing the watermarking with the utilization of DFT-DCT transformation, which reduces the phase hazards of the DCT method. But while implementing this approach to higher resolution images, those are not able to fulfil the robustness to that of compression ratio. As compression ratio not achieving, the images are easily affected by the random attacks. Thus, it provides the ineffective security levels. To overcome these consequences, DCT method needs to be enhanced or replaced. Thus, DWT incorporated with DCT and used by the authors in [16]. This method solves most of the problems, but still robustness is needed to be achieved. Especially it is not applicable to biometric applications. Thus in [12], the authors discussed about watermarking approach for fingerprint and iris datasets, for protecting the confidential image information. They achieved the robustness with the innovation of DWT bases fusion methodologies into it. But artifacts might be introduced while fusing the property features of images. To solve this problem, authors in [25] discussed DT-CWT based multi-resolution transforms, in which different features such as textures, edges and region of lines considered for both cover and watermark images and fused using different levels of orientations to achieve the efficacious watermarked image. Still, these methods were failed to provide the enhanced imperceptibility with higher robustness while performing the extraction procedure at another end. Further, they suffered from restricted direction in their filtering structure. Thus, to defeat above-mentioned issues, different types of subsample-based filters like contourlets, ridgelets [6], curvelets and shearlets [17] are implemented to achieve the smoothness by implementing these transforms into filters. But the problem arises due to ridgelets and curvelets implementation, as they are not categorized under the multi-resolution watermarking. So, the artifacts can be generated into the cover image, which is unwanted consequence for the application of NB-CIW. In [21] authors have proposed a robust watermarking scheme for biometric applications using redundant discrete wavelet transform (R-DWT), which is an extension for DWT and produces the filter coefficients as same size of input after decomposing it into subbands. However, NB-CIW needs to be enhanced to improve the watermarking efficiency. To overcome this problem, several researchers addressed RDWT with SVD implementation in [8, 15, 23] to obtain further enhanced watermarking capacity with higher imperceptibility and robustness against various attacks. But computational complexity is the major issue in [8, 15, 23] as the authors did not considered any optimization techniques. In [2], authors anticipated image hiding system based on DCT domain with the optimization of message using Arnold transform before embedding into the cover image. Further, they combined both DCT and its variance functions. However, they used binary image as watermark, but in recent days most of the images are in color or RGB. In addition, the quality of extracted watermark is degraded due to the usage of finite set of rules. Author in [24] presented DWT-SVD based approach with oppositional fruit fly optimization algorithm for selecting the optimal position of chosen blocks with lower variance. In addition, gold-code is employed for both embedding and extraction process which can be easily hacked by the attackers. In [14] authors developed DT-CWT-based watermarking through pixel-wise masking. It is based on masking watermark according to characteristics of HVS. The watermark is added to the largest detail bands and weighing function of the watermark is calculated as a simple product of data extracted from HVS model thus it is applicable to only geometrical attacks and results in extremely poor PSNR values. In [20] authors introduced copyright authentication for images using both blind and non-blind embedding methods and developed a hybrid scheme with the help of multi-level DWT transformation. The major drawback of this approach is time complexity and embedding complexity with high execution period. Most of the approaches presented in the literature suffering from poor imperceptibility, robustness and they suited for only several attacks. Further, only few researchers considered color watermark image for embedding. Therefore, this article proposed a NB-CIW methodology which employs SVD-TIW-EGWO approach to achieve enhanced robustness, higher imperceptibility with more confidentiality towards attacks compared to the conventional approaches. The main contributions are summarized as follows:
-
Implementation of TIW decomposition for generating the frequency subbands and decomposes the low frequency subband using SVD approach with the utilization of EGWO algorithm. As per authors knowledge, this combining approach has not been applied for the applications of NB-CIW before.
-
A novel framework on NB-CIW approach using new embedding and extraction algorithms is presented. In addition, EGWO is employed for the first time for the applications of NB-CIW.
-
An enhanced approach of NB-CIW methodology as compared to existing R-DWT [21], RDWT-SVD [8, 15, 23].
-
Further, comparative evaluation against various attacks also presented to show the robustness and effectiveness of proposed NB-CIW using SVD-TIW-EGWO approach as compared to existing NB-CIW approaches.
The remaining sections of this article are as follows: section 2 deals about implementation of TIW and its background. Section 3 explains about proposed new embedding and extraction procedure for NB-CIW applications. Section 4 deals about the implementation results and its discussions and comparative analysis using the various qualitative metrics. Section 5 describes the conclusion and possible future works of the proposed approach followed by references.
2 Translation invariant wavelet decomposition
Wavelets are finite energy and limited duration functions generated from one single function called basis function mother wavelet by scaling and shifting in time-frequency domain. Mother wavelet integrates to zero and is square integrable having finite energy. The wavelet function can be scaled and translated over input function. DWT is a type of non-redundant wavelet representation and suitable for images. This is achieved by discretization of dilation and translation parameters. With wavelet based multi-resolution analysis, image can be represented at more than one resolution level. The advantage is that features in an image that might go undetected at one resolution level may be easily located at another level. It is especially useful for processing nonstationary signals. Good time resolution and poor frequency resolution at high frequencies is achieved whereas good frequency resolution and poor time resolution is achieved at low frequencies. This is possible using adjustable window width in DWT but keeping area of the window constant.
Initially consider the DWT filter analysis, to generate the approximate coefficients; the input signal x[n] will be passed through low-pass filter (LPF) with g as its impulse response. Finally, convolution operation will be performed between the input and impulse response is given as
Similarly, to generate the detailed coefficients, the input signal x[n] will be passed through the high-pass filter (HPF) with h as its impulse response and convolution operation will be performed between the input and impulse response. It is noted that HPF and LPF both depends on each other and their response contains inverse properties. Figure 1 represents the filter analysis of conventional DWT operation, but this method suffering with the shift variance phenomenon generated by down sampling. Less shifts in the source image caused to more alter in wavelet coefficients. Thus, more fluctuations in wavelet coefficients to the input samples will be induced and causes to generation of improper energy distribution. Thus, DWT is ineffective for embedding and extraction of feature-based subband modelling and this problem can be overcome by modifying the operation of filtering procedure by compensating the down sampling. Therefore, the TIW decomposition is adapted with synthesis and analysis filter banks as shown in Fig. 2. These filter banks are capable of providing the orthogonality to the input subbands which results in less shifts and more redundant, thus the input samples are less affected by the various sources of noises and more immune to various types of attacks in the field of image processing. Thus, the TIW decomposition is prominent method for NB-CIW as compared to other transformations like fast fourier transform (FFT), DWT and DCT. The operation of TIW transform is as follows:
Consider, the X(n) and X ’ (n) signals as source data samples and recovered data samples and the input data samples are applied to the LPF with a[−k] response and HPF with d[−k] response. Synthesis filters shows time frequency inverse operation with that of analysis filters and their responses are represented as the a[k] for LPF and d[k] for HPF correspondingly. The coefficients generated from output these filters at jth level will be represented as Aj and Dj. Now this filter performs only convolution operation between the next state output to the frequency response but there will be no down-sampling operation in TIW decomposition. The analysis filter operation of DWT is expressed as follows
where ∗ denotes the convolution operation α denotes the down sampling.
Similarly, the outputs of the analysis filter coefficients are applied to synthesis with β as its up-sampling factor as follows:
As stated in Eq. (4), TIW decomposition does not contain the any sampling operation due to shift variant problems, thus it will be removed from DWT and TIW decomposition can be formed utilizing the LPF and HPF will be formulated as follows:
By eliminating the down sampling from analysis filter bank as given in Eq. (2) and Eq. (3), TIW decomposition can be formed as follows:
Similarly, by eliminating the up sampling from Eq. (4), synthesis can be formed as follows:
TIW decomposition maintains the fixed unchangeable sampling rate; thus, it is immune to the time fluctuations in filters. This constant nature of sampling rate generates the reliable frequency samples followed by its coefficients; thus, it is more suitable for image processing applications especially for watermarking based encryption standards in which data embedding capacity will be induced significantly. The major drawback presented in the DWT is reducing the resultant image size by half of its original image size due to the down sampling environment. Thus, the TIW will generate the resultant image with its actual image size and the resultant sub-bands also maintain the original size so inhibits perfect data embedding standards. The images consist of texture features in every sub band and it is necessarily to maintain these features with respect to their features. As the TIW provides for perfect data embedding capacity by maintain the size, thus it will maintain the texture features prominently. This property leads to implement the TIW operation for watermarking applications by maintaining the HVS by providing the highest embedding capacity.
3 Proposed model
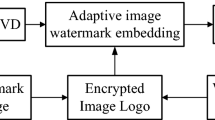
This section describes the proposed NB-CIW using SVD-TIW-EGWO approach. Figure 3 demonstrate embedding process of SVD-TIW-EGWO approach (discussed in section 3.1. in detail), which produces a prominent quality of watermarked image by embedding watermark image into the cover image. Similarly, extraction process (discussed in section 3.2. in detail) is shown in Fig. 4 for an extraction of watermark image from watermarked image which is obtained using embedding process.
3.1 RGB to YCbCr conversion
Practically, YCbCr color space frequently utilized to carry out vantage of the HVS’s low-resolution capability for color regarding luminosity. Hence, this conversion is being utilized widely in the applications of image processing. Assume, a pixel is represented in RGB format with 8-bits/sample and the range of pixel values is from 0 to 255, which is also known as gray range. RGB to YCbCr conversion is done as follows:
3.2 Embedding process
-
Step 1: Select and read the watermark and cover image as well (both are RGB images).
-
Step 2: Apply YCbCr colour space conversion to cover image as given in Eq. (10), Eq. (11), and Eq. (12), respectively. YCbCr colour space consists of luminance components, chroma red and chroma blue components. Generally, both chroma components consisting of low intensity components. Thus, in this low intensity pixels, the watermark image information can be perfectly stored without losing its properties.
-
Step 3: Apply TIW decomposition on components of YCbCr image like luminance, chroma blue and chroma red separately, now it decomposes the image into four subbands named LL, HL, LH, and HH.
-
Step 4: Separate R, G, and B components from obtained LL and denote as LLr, LLg and LLb. Apply SVD to get a columns of a matrix with left singular vectors \( {U}_{LL_{r,g,b}} \), diagonal matrix with singular values \( {S}_{LL_{r,g,b}} \), and columns of a matrix with right singular vectors \( {V}_{LL_{r,g,b}} \) for separated R, G, and B components.
-
Step 5: Apply TIW decomposition to the watermark as well to obtain four subbands named LL1, LH1, HL1 and HH1.
-
Step 6: Separate R, G and B components and apply SVD to obtain singular components like columns of a matrix with left singular vectors \( {U}_{LL{1}_{r,g,b}} \), diagonal matrix with singular values \( {S}_{LL{1}_{r,g,b}} \), and columns of a matrix with right singular vectors \( {V}_{LL{1}_{r,g,b}} \) of decomposed LL1 of watermark image.
-
Step 7: Now, use watermark embedding as below:
where \( {S}_{LL_r} \), \( {S}_{LL_g} \)and \( {S}_{LL_b} \) denotes the R, G, B components of obtained diagonal matrix with singular values from step 4 while \( {S}_{LL{1}_r} \), \( {S}_{LL{1}_g} \)and \( {S}_{LL{1}_b} \)are R, G, B components of obtained diagonal matrix with singular values from step 6. Now, combine Equation (13), Equation (14), and Equation (15) to obtain a modified diagonal matrix \( {S}_{W_{r,g,b}} \) with singular values.
-
Step 8: Now multiply the altered diagonal matrix with singular values \( {S}_{W_{r,g,b}} \) with columns of a matrix with left singular vectors \( {U}_{LL_{r,g,b}} \) and columns of a matrix with right singular vectors \( {V}_{LL_{r,g,b}} \) obtained from step 4 to get modified LL subband as given below
-
Step 9: Apply TIW reconstruction to Equation (16) and LH, HL and HH from step 3. Finally, apply YCbCr to RGB color space to get a watermarked image.
3.3 Extraction process
The proposed NB-CIW extraction process on watermarked image is as follows:
-
Step 1: Read watermarked image obtained by embedding process and converts it into YCbCr color space using Equation (10), Equation (11), and Equation (12) respectively.
-
Step 2: Apply TIW decomposition to decompose the components of YCbCr it into four subbands named LL2, HL2, LH2, and HH2 separately.
-
Step 3: Separate R, G and B components from obtained LL2 and apply SVD to get columns of a matrix with left singular vectors \( {U}_{LL{2}_{r,g,b}} \), diagonal matrix with singular values \( {S}_{LL{2}_{r,g,b}} \), and columns of a matrix with right singular vectors \( {V}_{LL{2}_{r,g,b}} \) for separated R, G, and B components.
-
Step 4: Now, use watermark extraction as below:
where \( {S}_{LL{2}_r} \), \( {S}_{LL{2}_g} \)and \( {S}_{LL{2}_b} \) denotes the R, G, B components of obtained diagonal matrix with singular values from step 3 while \( {S}_{LL_r} \), \( {S}_{LL_g} \)and \( {S}_{LL_b} \)are R, G, B components of obtained diagonal matrix with singular values from step 4 in embedding process (refer section 3.2.). Now, combine Equation (17), Equation (18), and Equation (19) to obtain extracted diagonal matrix with singular values \( {S}_{E_{r,g,b}} \).
-
Step 5: Now multiply the extracted diagonal matrix with singular values \( {S}_{E_{r,g,b}} \) with columns of a matrix with left singular vectors \( {U}_{LL{1}_{r,g,b}} \) and columns of a matrix with right singular vectors \( {V}_{LL{1}_{r,g,b}} \) obtained from step 6 in embedding process (refer section 3.2.) to get extracted LL1 subband as given below
-
Step 6: Apply the TIW reconstruction to Equation (20) and LH1, HL1 and HH1 from step 5 in embedding process (refer section 3.2.) to get extracted watermark.
-
Step 7: Apply EGWO algorithm given in Table 1 to optimize the performance of proposed NB-CIW.
3.4 Enhanced Grey wolf optimizer (EGWO)
From [10], by utilizing the fundamental behaviour of Grey wolves’, a new algorithm is proposed named as grey wolf optimizer (GWO). In this approach, the properties of image patches are done based on the properties of Beta, Gamma and Alpha. The finest optimization solution is achieved by the Alpha property, which is a leading initiator. The second and third optimization solutions are achieved by the Gamma, Beta, respectively. Initially GWO is utilized to train the weights of multi-layers. Later, [18] explains the use of evolutionary population dynamics (EPD) with GWO, thus the low reliable search agents of GWO method are optimized, respectively. Now this searching procedure is effectively monitored by Beta, Gamma and Alpha parameters and calculation of these parameters on the source data is performed by selectively using the GWO approach [22]. Thus, amazingly fast searching capacity is achieved by maintaining the cumulative adjustment between global and local search procedures [5].
4 Results and discussion
This section deals about the detailed discussion on the obtained results of proposed NB-CIW using SVD-TIW-EGWO embedding and extraction process as compared to existing NB-CIW methodologies. Figure 5 shows that input RGB images used as cover images for NB-CIW which includes ‘vegetables’, ‘fruits’, ‘penguins’, ‘bike’, ‘raccoon’, ‘plants’, ‘pathenon’, ‘parrot’, ‘hat’, ‘girl’, ‘flower’ and ‘butterfly’. The watermark images are demonstrated in Fig. 6. For evaluating the performance of existing and proposed NB-CIW methodologies, image quality metrics like PSNR, SSIM, RMSE and NCC are utilized where PSNR performance discloses the imperceptibility, RMSE, SSIM and NCC values demonstrate the robustness and effectiveness of NB-CIW algorithm. Further, no attack and attack scenarios are considered for quality assessment of proposed NB-CIW using SVD-TIW-EGWO approach as compared to existing NB-CIW using R-DWT and R-DWT + SVD approaches.
4.1 Performance of proposed NB-CIW using SVD-TIW-EGWO approach
4.1.1 No attack scenario
In this, we utilized R-DWT [21] and R-DWT + SVD [8, 15, 23] methodologies for the comparative analysis. Figure 7 demonstrate the obtained results of NB-CIW using R-DWT approach, where 1st column represents all the cover images used for testing, 2nd column discloses the watermark image used for embedding and extraction process. Watermarked images are given in 3rd column and extracted watermark images are shown in 4th column, respectively. It is shown that all the obtained watermarked images are suffering from lack of imperceptibility as the watermark message is clearly visible in watermarked images which results in lesser PSNR values. Further, extracted watermark image also not accurate as the embedded watermark image which results in lower robustness. Similarly, test results for various cover images using R-DWT + SVD [8, 15, 23] is given in Fig. 8. However, the watermarked images obtained using R-DWT + SVD discloses superior performance over R-DWT, the extracted watermark is suffering due to lesser RMSE and SSIM values, which results in lower robustness. Further, it also has some amount of distortion on it. Practically, one can easily identify the watermark image which is embedded into cover image if there is lack of imperceptibility and robustness.
Results obtained using R-DWT [21] with various cover images
To overcome the limitations of existing R-DWT and R-DWT + SVD by enhancing the imperceptibility and robustness as well, our proposed NB-CIW methodology using SVD-TIW-EGWO approach results is depicted in Fig. 9, which provides an excellent imperceptibility for both watermarked image and extracted watermark image as well (see 3rd and 4th column in Fig. 9). As compared with existing NB-CIW methodologies, the effectiveness and robustness of proposed NB-CIW methodology using SVD-TIW-EGWO is quite superior and can be adopted easily with the applications of NB-CIW in real-time as well since it utilizes RGB images as watermark whereas most of the existing NB-CIW methodologies employed for binary watermark images. Quality analysis of these methods with respect to watermarking quality evaluation metrics is shown in Figs. 10, 11 and 12, respectively where PSNR is calculated for the obtained watermarked images to the cover images and displayed the graphical analysis in Fig. 10. The values of PSNR are just above 74 dB with the proposed SVD-TIW-EGWO approach whereas the existing R-DWT got just above 58 dB and R-DWT + SVD got just near to 60 dB. This shows that proposed NB-CIW methodology using SVD-TIW-EGWO obtained higher imperceptibility and robustness against the existing NB-CIW presented in the literature.
Figure 11 shown the graphical analysis of RMSE values from R-DWT, R-DWT + SVD and proposed NB-CIW methodology using SVD-TIW-EGWO. It is observed that values of SVD-TIW-EGWO got lower error values as compared to existing NB-CIW methodologies using R-DWT [21] and R-DWT + SVD [8, 15, 23]. The values of RMSE for the displayed output results in Figs. 7, 8 and 9 are 0.521 with [21], 0.069 with [8, 15, 23] and with SVD-TIW-EGWO is 0.00211, respectively. Similarly, another quality metric, SSIM index values are shown in Fig. 12, where the proposed SVD-TI-EGWO achieved a value of 1 for almost every tested RGB image. The values of R-DWT and R-DWT + SVD are slightly lower than the proposed values. All the three-quality metrics tabular forms demonstrated in Tables 2, 3 and 4, respectively. And we also highlighted the best value in bold letter for identification purpose.
4.1.2 Attack scenario
This subsection describes the performance evaluation of existing and proposed NB-CIW methodologies with several attacks like geometrical attacks like rotation, scaling, and translation. Further, non-geometrical attacks like Gaussian noise, compression, median filtering, motion blur, sharpening, flipping and histogram equalization also considered to disclose the effectiveness and robustness of proposed NB-CIW using SVD-TIW-EGWO approach as compared to existing NB-CIW using R-DWT and R-DWT + SVD approaches. Tables 5 and 6 demonstrate the performance analysis of proposed NB-CIW using SVD-TIW-EGWO approach under various sources of attacks. Usually these attacks will be generated by the attackers to detect the original information, so here we are considering prototype of those attacks. In Table 5, the NCC outcome of the proposed NB-CIW using SVD-TIW-EGWO approach is compared to existing NB-CIW methods like R-DWT [21] and R-DWT + SVD [8, 15, 23]. The comparison results show that the proposed method has maximum accuracy and improved by 15% with conventional schemes. In Table 6, the PSNR metric of the proposed NB-CIW using SVD-TIW-EGWO approach is compared with the existing NB-CIW methods like R-DWT [21] and R-DWT + SVD [8, 15, 23]. The comparison results show that proposed SVD-TIW-EGWO approach has maximum quality for both the watermarked image and extracted image as well even in case of attack scenario and improved the imperceptibility by 20% with comparison to the existing NB-CIW methods.
5 Conclusions
This article proposed a new NB-CIW approach based on SVD in TIW domain. Additionally, EGWO algorithm also implemented which is a metaheuristic approach for optimizing the performance of proposed NB-CIW methodology. Further, to show the robustness and effectiveness of proposed NB-CIW, different types of attacks also applied on to the watermarked image and extracted the watermark almost similar quality as embedded. Simulation result shown the superiority of proposed NB-CIW using SVD-TIW-EGWO approach with compared to the state-of-art NB-CIW methodologies for various test images. The quality evaluation metrics like NCC, RMSE, SSIM and PSNR also computed and shown that proposed NB-CIW methodology with SVD-TIW-EGWO holds more embedding capacity.
References
Amini M, Ahmad MO, Swamy MNS (2017) A new locally optimum watermark detection using vector-based hidden markov model in wavelet domain. Signal Process 137:213–222
Ariatmanto D, Ernawan F (2020) An improved robust image watermarking by using different embedding strengths. Multimed Tools Appl 79:12041–12067
Berghel H, O’Gorman L (1996) Protecting ownership rights through digital watermarking. Computer 29(7):101–103
Hamidi M, Haziti ME, Cherifi H, Hassouni ME (2018) Hybrid blind image watermarking technique based on DFT-DCT and Arnold transform. Multimed Tools Appl 77(20):27181–27214
Kapoor S, Zeya I, Singhal C, Nanda SJ, Kapoor S, Zeya I, Singhal C, Nanda SJ (2017) A grey wolf optimizer based automatic clustering algorithm for satellite image segmentation, In: 7th International Conference on Advances in Computing & Communications, Cochin, India, vol. 115 of Procedia Computer Science, Elsevier, pp. 415–422
Kim WH, Nam S, Lee HK (2017) Blind curvelet watermarking for high-quality images. Electron Lett 53(19):1302–1304
Lee YS, Seo YH, Kim DW (2019) Blind image watermarking based on adaptive data spreading in n-level DWT subbands, Security and Communication Networks, Article ID 8357251 https://doi.org/10.1155/2019/8357251
Loukhaoukha K, Rafaey A, Zebbiche K (2017) Ambiguity attacks on robust blind image watermarking scheme based on redundant discrete wavelet transform and singular value decomposition. J Electric Syst Inform Technol 4(3):359–368
Macq B, Quisquater JJ (1995) Cryptology for digital TV broadcasting. IEEE 83:944–957
Mirjalili S, Mirjalili SM, Lewis A (2014) Grey wolf optimizer, in: advances in engineering software. Vol. 69:46–61
O’Ruanaidh JJK, Dowling WJ, Boland FM (1996) Watermarking digital images for copyright protection, in: IEEE Proceedings- Vision, Image and Signal Processing , IET, vol. 143, IET, pp. 250–256.
Paunwala M, Patnaik S (2014) Biometric template protection with DCT-based watermarking. Mach Vis Appl 25(1):263–275
Poonam S, Arora M (2018) A DWT-SVD based robust digital watermarking for digital images. Proced Comput Sci 132:1441–1448
Rai S, Boghey R, Shahane D, Saxena P (2019) Digital image watermarking against geometrical attack. In: Shukla R, Agrawal J, Sharma S, Singh TG (eds) Data, Engineering and Applications. Springer, Singapore
Rassem TH, Makbol NM, Khoo BE (2016) Performance analysis of RDWT-SVD and DWT-SVD watermarking schemes, in: International Conference on Advanced Science, Engineering and Technology, Vol. 1774 of 1, AIP Publishing, pp. 050021–1–050021–9
Saadi S, Merrad A, Benziane A (2019) Novel secured scheme for blind audio/speech norm-space watermarking by Arnold algorithm. Signal Process 154:74–86
Sadreazami H, Amini M (2019) A robust image watermarking scheme using local statistical distribution in the contourlet domain. IEEE Transact Circ Syst II: Express Briefs 66(1):151–155
Saremi S, Mirjalili SZ, Mirjalili SM (2015) Evolutionary population dynamics and grey wolf optimizer. Neural Comput & Applic 26(5):1257–1263
Savakar DG, Ghuil A (2019) Robust invisible digital image watermarking using hybrid scheme. Arab J Sci Eng 44(4):3995–4008
Savakar DG, Ghuli A (2019) Robust invisible digital image watermarking using hybrid scheme. Arab J Sci Eng 44:3995–4008. https://doi.org/10.1007/s13369-019-03751-8
Singh P, Raman B, Roy PP (2017) A multimodal biometric watermarking system for digital images using redundant discrete wavelet transform. Multimed Tools Appl 76(3):3871–3897
Song X, Tang L, Zhao S, Zhang X, Li L, Huang J, Cai W (2015) Grey wolf optimizer for parameter estimation in surface waves. Soil Dyn Earthq Eng 75:147–157
Srinivas K, Kumar PM, Rao AJ (2019) A new video watermarking using redundant discrete wavelet in singular value decomposition domain. J Mech Cont Mathematic Sci 14(5):476–486
Veni M, Meyyappan T (2019) Digital image watermark embedding and extraction using oppositional fruit Fly algorithm. Multimed Tools Appl 78:27491–27510
Zebbiche K, Khelifi F, Loukhaoukha K (2018) Robust additive watermarking in the DTCWT domain based on perceptual masking. Multimed Tools Appl 77(16):21281–21304
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Dappuri, B., Rao, M.P. & Sikha, M.B. Non-blind RGB watermarking approach using SVD in translation invariant wavelet space with enhanced Grey-wolf optimizer. Multimed Tools Appl 79, 31103–31124 (2020). https://doi.org/10.1007/s11042-020-09433-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09433-0