Abstract
In this study, a novel delayed coupled chaotic model to reduce the dynamical degradation of digital chaotic maps is firstly proposed. In this model, we introduce the delayed state variables in digital maps and use the state variable of one map to vary the control parameter of the other map. Numerical experimental results demonstrate that the delayed coupled system can effectively reduce the dynamical degradation of digital chaotic maps, and retain the phase space structure of the original system. Furthermore, we propose a simple image encryption algorithm based on the coupled model as a simple application. Numerical experiments show that our algorithm has high security level and can resist various attacks, which is competitive with some other chaotic image encryption algorithms.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
On the basis of certain complex dynamics characteristics, including sensitivity to initial conditions and parameters, topological transitivity, unpredictability, aperiodicity, and pseudo-randomness, chaotic systems/maps are widely used in various scientific and social fields, including communications, economics, chemistry, networking, and cryptography [5, 10, 27]. Particularly, chaos-based cryptography has received considerable attention from researchers since the 1990s due to its consistency of chaotic characteristics and cryptographic requirements [9, 22, 24, 25, 30]. Although various chaotic encryption algorithms have been proposed to date, their security is usually not as high as indicated.
The chaos theory is defined on a real number field. However, the computer is a finite precision device. When chaotic systems/maps are implemented on a computer, their state space will be finite and their dynamics will suffer degradation [11]. Therefore, the chaotic maps are no longer mathematically chaotic. We call them digital chaotic maps. The trajectory of digital chaotic maps will finally enter a cycle due to the finite state space, and other ideal performances of chaos, including sensitivity, transitivity, unpredictability, and ergodicity, will degenerate simultaneously, thereby no longer satisfying the requirements of cryptography. In most chaotic encryption algorithms, the chaotic maps are implemented on a computer; hence, security may be at risk. Therefore, the chaotic dynamics of digital chaotic maps should be improved to enhance the security of chaotic algorithms. In other words, the dynamical degradation of digital chaotic maps must be reduced.
Attempts to reduce the dynamical degradation of digital chaotic maps have been widely studied [3, 4, 13, 14, 16,17,18,19, 26, 30, 32]. [30] used high precision to extend the period of digital chaotic maps and improve their dynamics. [3, 32] cascaded multiple chaotic maps to extend the period of digital chaotic maps. [18, 26] reduced the dynamical degradation of digital chaotic maps by switching multiple chaotic maps. [13, 16, 19] improved the dynamics of chaotic maps by (pseudo)-random perturbation. [4, 17] introduced an analog chaotic system to improve the dynamics of digital chaotic maps. Recently, [14] extended the period of digital chaotic maps by using delayed state variables. Although these methods can reduce the dynamical degradation to some extent, they still possess limitations. Using a high precision will certainly increase the implementation cost. Cascading or switching multiple chaotic maps can extend the period of digital chaotic maps. However, the dynamical complexity of the remedied system is completely determined by the cascading or switching rules, which are always ignored and difficult to control. The perturbation method is better than the first three methods. Introducing a good perturbation source will considerably improve the dynamics of digital chaotic maps. The analog–digital mixed control method is a novel method in this field. However, the introduction of analog chaotic system constantly warrants additional resources, and the hybrid system is difficult to realize. The delay-introducing method proposed in [14] is a novel and feasible method; however, its dynamical complexity and universality should be further improved.
These past studies have motivated us to propose a novel delayed coupled chaotic model that reduces the dynamical degradation of digital chaotic maps. In our model, two digital chaotic maps are coupled. We use the state variable of one map to vary the control parameter of the other map. Therefore, the coupled system is time varying, and the output trajectories are non-stationary, resulting in high complexity. Furthermore, we introduce the delayed state variables in digital maps to extend the periods. As far as we know, combining both delay introducing method and coupling method to reduce the dynamical degradation of digital chaotic maps has not been studied yet. While improving these characteristics, this method still retains the phase space structure of the original system rather than constructing a new random source. The advantages of our model can be described as follows.
-
1)
The model can greatly reduce the dynamical degradation of digital chaotic maps.
-
2)
The model introduces a delay state, which relates the output of the system not only to the current state but also to the previous state.
-
3)
The model couples two systems. The parameters of each sub-system are affected by the output of the other sub-system and are constantly varying.
-
4)
This method can be applied to all digital chaotic systems.
We take two examples to show the effectiveness of our delayed coupling method. The trajectories, phase diagrams, auto-correlation function, and complexity, including approximate entropy (ApEn) and permutation entropy (PE), are analyzed in each example. Simulation results show that the coupled model can considerably improve the dynamical complexity of original digital chaotic maps, which implies the effectiveness of our delayed coupling method. As chaos-based encryption algorithm has been widely used in several areas [9, 22, 24, 25, 28,29,30], therefore, in this paper, we also apply the delayed coupled digital chaotic model to a simple image encryption algorithm as an application. Several numerical experiments show that our algorithm has high security level and can resist various attacks, which is competitive with some other chaotic image encryption algorithms.
The rest of this paper is organized as follows. The new delayed coupled chaotic model is introduced in Section 2. The logistic–logistic coupled model and logistic–Chebyshev coupled model with their complexity analysis are shown in Sections 3 and 4, respectively. In Section 5, we apply a simple image encryption algorithm based on the delayed coupled model. Finally, Section 6 concludes the paper.
2 Delayed coupled chaotic model
The general chaotic map can be described as follows:
where x is the state variable, and p is the control parameter. Once the parameter p is selected in the suitable chaotic region, the map f will be chaotic. However, when this chaotic map is simulated on a computer (or other finite precision device), its dynamics will suffer degradation due to the finite phase space. In order to improve the dynamics of digital chaotic map, we provide the following delayed coupled model:
where h1 and h2 are parameter control functions. The chaotic functions F1 and F2 are two chaotic maps. In this model, the control parameter of each sub-system is controlled by the state from other sub-systems, and the delayed state is introduced to construct functions F1 and F2. These two functions can reduce the dynamical degradation of the delayed coupled chaotic model. The following two conditions should be satisfied in this model:
-
1)
The parameter of a map should be in a particular region called the chaotic region to make the map chaotic. In our model, the parameter is affected by the coupled state variable, which is continuously varied. Therefore, the valued field of parameter control functions h1 and h2 should be a subset of the chaotic region. The varied parameter not only can improve the dynamics of digital chaotic map but also make the output sequence non-stationary, thereby resisting such statistical attacks.
-
2)
In the original chaotic map, its current state xi is completely determined by its previous state xi − 1. Therefore, the digital chaotic sequence will fall into a cycle if two states xp and xq are identical. We introduce more delayed state variables in the chaotic map of our model to extend the period. In this case, state xi is not completely determined by xi − 1 but by vector (xi − 1, xi − 2, … , xi − k). Therefore, the digital chaotic sequence will not fall into a cycle unless the previous k states xp − 1, xp − 2, … , xp − k and xq − 1, xq − 2, … , xq − k are identical. A large k implies that the digital chaotic sequence has a large resistibility to enter a cycle. We consistently select k = 2 to reduce the implementation cost; thus, state xi is determined by its previous two states xi − 1 and xi − 2. Furthermore, with the introduction of delayed states, the chaotic attractor should not be destroyed completely. Similar to other studies [4, 17], the digital chaotic attractors are entirely different from their original chaotic maps, which cannot be regarded as dynamical degradation remedies but methods of constructing new random sources.
Here, we propose a delayed coupling method to reduce the dynamical degradation of digital chaotic maps. The delayed state coupling and parameter control functions are uncertain, which are selected due to different chaotic maps. We recommend using simple linear functions to reduce implementation costs.
Remark 1
Our method is effective for all chaotic maps. We can couple any two identical chaotic maps, as well as two different chaotic maps. Moreover, the dimensions of these two maps can be different. All digital chaotic systems can apply our coupling method as long as the above construction rules are followed. We take two examples to show the effectiveness of our delayed coupling method in the subsequent sections.
Remark 2
Reducing the dynamical degradation of digital chaotic systems should not completely disturb the phase space of original systems. Some methods, such as [4, 17], have completely disrupted the structure of original chaotic map, which cannot be regarded as a remedy, but rather to generate new random sources.
3 Example 1
In this example, we couple two identical logistic maps, the mathematical model of which can be described as
where r1 is the control parameter, which should be in the interval (3.5699, 4) to make the map chaotic. Here, we select the following delayed state coupling and parameter control functions:
Then, the delayed coupled model can be written as
In this model, the parameters of sub-systems X and Y are coupled and controlled by the states of Y and X, respectively. Thus, the coupled model is parameter varied. Next, we analyze certain characteristics to validate the efficiency of our method.
3.1 Trajectories and phase diagrams
The trajectory of an ideal chaotic system should be random-like and without any regular structural features. Let the largest precision be 2−12. Set a = 0.999, r1 = 3.99, and the initial values x1 = 0.23245, x2 = 0.512242109, y1 = 0.30863, and y2 = 0.41074 for Eqs. (6) and (3), respectively. The trajectories of the two maps are shown in Fig. 1. Figure 1(a) represents the trajectories of x-dimensional sequences of Eq. (6), whereas Figs. 1(b) and 1(c) represent the y-dimensional sequences of Eqs. (6) and (3), respectively. Figure 1 indicates that the trajectory of Eq. (3) quickly falls into a cycle after approximately 110 iterations, whereas that of Eq. (6) appears randomly after 400 iterations; no apparent period can be detected, which implies that the original system has a regular structure, whereas the improved system has none. Therefore, the period of delayed coupled digital chaotic maps has been extended with good randomness. Figures 2(a) and 2(b) plot the phase diagrams of Eqs. (3) and (6), respectively. The points of the improved chaotic sequences are denser than the original points, which indicates that the improved map is remarkably similar to the traditional logistic map and is active in the phase space.
3.2 Auto-correlation analysis
Auto-correlation function is an important measure of randomness. The auto-correlation of an ideal chaotic sequence should be delta function. Let the largest precision be 2−16. The auto-correlation functions of sequences generated by Eqs. (6) and (3) are shown in Figs. 3(a) and 3(b), respectively. The waveform of auto-correlation function of a good performance sequence should be sharp needle-like without prominent side lobe, which can be used to detect and identify the signal accurately. As shown in Fig. 3, the main peak of auto-correlation function of the original system sequence is thick, and the side lobe is extremely high. However, the improved system sequence’s auto-correlation function has a small main peak, and the side lobes are rarely low and virtually invisible, which implies that the improved system has good randomness.
3.3 Complexity analysis and comparison
ApEn and PE are widely applied in measuring the complexity of time series. Here, we use these two complexity measures to evaluate and compare the complexity of our proposed model (Eq. (6)) and the original chaotic model (Eq. (3)).
3.3.1 ApEn analysis
ApEn was first proposed by Pincus to measure the complexity of time series [20]. ApEn measures the probability of the new pattern generated in sequences with an embedding dimension growth. A greater probability of generating a new pattern implies greater ApEn. In this test, we set a = 0.999 and r1 = 3.99 to calculate the ApEn of sequences generated by Eqs. (6) and (3), as shown in Fig. 4. From the figure, the ApEn of the sequence generated by Eq. (6) (red line) is always larger than that by Eq. (3) (blue line) under the same precision, which indicates that our coupled model (Eq. (6)) is relatively more complex than the original chaotic model (Eq. (3)). This finding indicates that the proposed method (Eq. (6)) can enhance the complexity of the traditional logistic map without disrupting its structure and even improve the dynamic degradation to a certain extent. In comparison with other proposed methods, the ApEn of Eq. (6) is also larger than the methods in [7, 12, 16], whose ApEn is approximately 0.479, 0.613, and 0.615 under the same parameters, respectively. While comparing with the methods in [4, 17], the ApEn in these studied are larger than 1, which are both larger than our method. That is because the methods in [4, 17] completely disrupt the phase space structure of the original digital systems. Therefore, these methods can not be regarded as the method to reduce the dynamical degradation of digital chaotic maps, but to construct new random sources.
3.3.2 PE analysis
PE is another widely used complexity measure for time series [2]. This measure compares the size of certain consecutive values in the time series, sums up different order types, and then uses Shannon’s entropy to measure the uncertainty of the order. As suggested in [2], we set the ordinal pattern length L = 6 and the embedding delay D = 2 in this test. We measure the PE of sequences generated by Eqs. (6) and (3) with the method of changing the precision. The parameters are selected to be the same as those in Section 3.3.1, and the PE of sequences generated by Eqs. (6) and (3) under the same precision are shown in Fig. 5, where −logp starts at 12 and increases by 4; thus, the PE of the sequence generated by Eq. (6) (red line) is larger than that by Eq. (3) (blue line) with one accord. The complexity measure fully demonstrates that the proposed model has a higher complexity and stronger anti-jamming capabilities, such as applying to the encryption algorithm, compared with the original chaotic model. Furthermore, under the same precision, the PE complexity of the systems in [7, 12, 16] are 0.813, 0.882, and 0.885, respectively; hence, our method is competitive in improving the complexity of digital chaotic maps.
4 Example 2
In this example, we couple two different chaotic maps, namely, logistic and Chebyshev maps, to demonstrate the effectiveness of our method. The Chebyshev map model can be described as follows:
where r is the control parameter. In this example, the delayed state coupling functions are the same as Eq. (4), and the parameter control functions are selected as follows:
Then, the delayed coupled model can be written as
Certain numerical simulations are provided in this study to present the characteristics of Eq. (9).
4.1 Trajectories and phase diagrams
Given that the second model couples the traditional logistic map and the Chebyshev map, we compare the performances of different characteristics. For the sake of guaranteeing the persuasiveness of the numerical experiment, we select the same precision, parameters, and initial values as those in Section 3.1 for Eqs. (9), (3), and (7), respectively. The trajectories of the three maps are shown in Fig. 6; Figs. 6(a) and 6(b) are the trajectories of Eqs. (3) and (7), respectively, and Figs. 7(c) and 7(d) are the trajectories of the x- and y-dimensional sequences of Eq. (9). Figure 6(a) shows the same result as that in Section 3.1. However, Fig. 6(b) reveals that the trajectories of Eq. (7) quickly fall into a cycle after approximately 120 iterations, which manifests a regular structure. The x- and y-dimensional sequences of Eq. (9) have no cycles after 400 iterations and no regular structure. Therefore, the period of the improved delayed coupled digital chaotic model is extended with good randomness. Similarly, Figs. 7(a)–7(d) plot the phase diagrams of Eqs. (3), (7), and (9). In comparison, the results in Figs. 7(a) and 7(c) are similar to those of Section 3.1, whereas the points in Fig. 7(d) are denser and more widely distributed than those in Fig. 7(b). Hence, the period of Eq. (9) is further improved.
4.2 Auto-correlation analysis
The auto-correlation functions are shown in Fig. 8; Figs. 8(a) and 8(b) represent the auto-correlation functions of the x- and y-dimensional sequences of Eq. (9), respectively, and Fig. 8(c) is the auto-correlation function of Eq. (7). From the figure, the side lobes generated by Eq. (9) are almost absent. The main peak is extremely thin, whereas the characteristics of Eq. (7) are the opposite. Moreover, the auto-correlation functions of the sequence generated by Eq. (9) are closer to delta function and more random than those by Eqs. (3) and (7).
4.3 Complexity analysis and comparison
4.3.1 ApEn analysis
We select the y-dimensional state variables in the following experiments because the results of the x-dimensional variables are similar to Section 3, which we omitted to avoid redundancy. Furthermore, we set the same precision, parameters, and initial values as those in Section 3.1. The results shown in Fig. 9 indicate that the ApEn of the sequence generated by Eq. (9) (red line) under the same precision is consistently larger than that of the sequence generated by Eq. (7) (blue line). Therefore, our method can greatly improve the complexity of the digital Chebyshev map.
4.3.2 PE analysis
PE analysis is used for this numerical experiment to compare the complexity of sequences generated by Eqs. (9) and (7). Figure 10 shows that the PE of the y-dimensional sequence generated by Eq. (9) (red line) is consistently larger than that of the sequence generated by Eq. (7) (blue line) under the same precision. Hence, our model is more complex than the traditional Chebyshev map.
5 Simple image encryption algorithm based on example 1
In this section, we propose a simple image encryption algorithm based on logistic–logistic coupled model (Eq. (6)) to show the practicability of our delayed coupled chaotic model. The model (Eq. (6)) has a high complexity and good randomness. Thus, we do not need to design a tedious encryption algorithm to ensure its security. Here, the encryption algorithm is relatively simple, and the numerical analysis shows that the algorithm is comparatively secure and competitive with other algorithms.
5.1 New image encryption algorithm
5.1.1 Shuffling algorithm
The purpose of the shuffling algorithm is to scramble the pixel position of the plaint image. Its core idea is to arrange the generated chaotic sequence according to a certain algorithm and then rearrange the plaint image in this order to achieve the result of scrambling. Our simple shuffling algorithm can be described as follows. First, we convert a plain image into Aij, which is the M × N pixel matrix. Then Bij, which is the pixel matrix of the grayscale image, is transformed by Aij into the pixel sequence {B}, whose length corresponds to M × N.

Our shuffling algorithm is based on a shuffling sequence. Suppose that {Cy} is the y-dimensional chaotic sequence generated by Example 1. Our method is to rearrange {Cy} into \( \left\{\overset{\acute{\mkern6mu}}{C_y}\right\} \) in ascending order, and the sequence {B} of the plaint image is disturbed accordingly by the subscript of \( \left\{\overset{\acute{\mkern6mu}}{C_y}\right\} \). Thus, we can obtain sequence {\( \overset{\acute{\mkern6mu}}{B} \)} after shuffling. The specific process is as follows:

The purpose of the shuffling algorithm is to scramble.
The shuffled image matrix \( \overset{\acute{\mkern6mu}}{B} \) reshaped by {\( \overset{\acute{\mkern6mu}}{B} \)} can be written as follows:
5.1.2 New image encryption algorithm
The steps of our encryption algorithm are described in detail as follows.
-
Step 1:
Read the plain image A, supposing that the size of plain image A is M × N and Bij is the grayscale pixel matrix of image A.
-
Step 2:
Calculate the average value (Ave) of all the pixels in the matrix Bij and obtain the fractional part (b) as follows:
-
Step 3:
Set initial values and parameters (\( \overset{\acute{\mkern6mu}}{x_1\ }\overset{\acute{\mkern6mu}}{,{x}_2},\overset{\acute{\mkern6mu}}{y_1}\ \overset{\acute{\mkern6mu}}{,{y}_2},{r}_1,\mathrm{and}\ a \)) of Eq. (6), where the initial values assigned and the b in Step 2 are added to the final initial values, such that the generated chaotic sequence is associated with the plain image-related information.
-
Step 4:
Generate x- and y-dimensional chaotic sequences based on Example 1 by iteration M × N times with the initial values obtained in Step 3. Then, the chaotic sequences of {Cx} and {Cy} can be obtained.
-
Step 5:
Use {Cy} as the shuffling sequence. According to Section 5.1, B will be disordered into matrix \( \overset{\acute{\mkern6mu}}{B} \).
-
Step 6:
{Cx} will be normalized to (0, 255) and then converted to M × N matrix E. The specific conversion method is as follows:

-
Step 7:
Use chaotic matrix E to obtain the encrypted image D by executing XOR with \( \overset{\acute{\mkern6mu}}{B} \).
The flowchart of our algorithm is shown in Fig. 11. The initial values and parameters (x1, x2, y1, y2, r1, and a) can be used as the security keys. The decryption of image is the inverse process of using the security keys to encrypt the chaotic matrix, and the steps are described as follows.
-
Step 1:
Read the encrypted image D, supposing that the size of encrypted image D is M × N and Gij is the grayscale pixel matrix of image D.
-
Step 2:
Generate x- and y-dimensional chaotic sequences based on Example 1 by iteration M × N times with the secret keys (x1, x2, y1, y2, r1, and a). Then, the chaotic sequences of {Cx} and {Cy} can be obtained.
-
Step 3:
{Cx} will be normalized to (0, 255) and then converted to M × N matrix E. The specific conversion method is as follows:

-
Step 4:
Use chaotic matrix E to obtain the decrypted image \( \overset{\acute{\mkern6mu}}{B} \) by executing XOR with D.
-
Step 5:
Use {Cy} as the reverse shuffling sequence. According to Section 5.1, \( \overset{\acute{\mkern6mu}}{B} \) will be restored into sequence B.

Then the {Cy} will be sorted in ascending order.

-
Step 6:
At last, convert the {B} to the Bij, which is the grayscale pixel matrix of plain image A.

5.2 Security performances
In this section, different types of security analysis methods are used to demonstrate the security performance of our algorithm. The experimental image is a 256 × 256 “Lena” image. All the tests are produced by Matlab R2016a on a computer with 2.40 GHz CPU and 8.00 GB memory. The initial values and parameters are selected as follows: x1 = 0.43245, x2 = 0.51224, y1 = 0.30863, y2 = 0.41074, r1 = 3.9901563, and a = 0.00321. The average value of all pixels of the original image is 99.8142. After adding the information of the original image, the security keys are as follows: x1 = 0.2466, x2 = 0.3264, y1 = 0.1228, y2 = 0.2249, r1 = 3.9901563, and a = 0.00321. The precision is 10−14 in our numerical experiments.
5.2.1 Encryption and decryption experiment tests
The encryption and decryption results of the plain image, the encrypted image by the x-dimensional sequence of Eq. (6), the decrypted Lena with correct keys, and the decrypted Lena with wrong keys are shown in Figs. 12(a)–12(d), respectively. A comparison of these four images shows that the Lena becomes unrecognizable and extremely noisy after encryption. When decrypting with the wrong key, the plain image cannot be recognized unless the key is properly restored.
5.2.2 Histogram analysis
The distribution of the ciphered image is a major concern. Figs. 13(a) and 13(b) show the statistical histograms of Lena and the x-dimensional sequence of Eq. (6), respectively. The histogram of the original image is unevenly distributed and has special features, whereas that of the encrypted image is almost uniformly distributed, whose horizontal distribution is advantageous in resisting statistical and ciphertext-only attacks.
5.2.3 Key space analysis
The key space should be sufficiently large to resist brute force attacks for a strong encryption algorithm. In our proposed encryption algorithm, initial values (x1, x2, y1, y2) and the parameter r1 can be security keys. Let the precision of a real number be 10−14 and the key space be approximately 0.4 × 1014 × 1014 × 1014 × 1014 × 1014 = 0.4 × 1070 ≈ 2231, which is considerably larger than 2128, and is also larger than 2160 of [25], 2140 of [23], and 2184 of [15] under the same precision. Therefore, our proposed algorithm with such a large key space can sufficiently resist all types of brute force attacks.
5.2.4 Correlation analysis
For a good image encryption algorithm, the correlation coefficient of the encrypted image should be considerably weaker than that of the original image. The correlation coefficient between adjacent pixels of an image can be obtained as follows:
where xi and yi are two data sequences, and N is the length of the sequences. If two sequences have high correlation, then their correlation values are close to 1; if they are close to 0, then the correlation between the two sequences is weak.
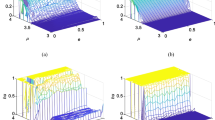
The distribution results of the pixel sequence pairs are shown in Fig. 14. In this test, 2704 pairs of two adjacent pixels along with the horizontal, vertical, and diagonal directions are selected randomly from the original and the encrypted images. Figures 14(a)–14(c) show the distributions of the pixel sequence pairs of the plain image in the horizontal, vertical, and diagonal directions, respectively. The figures indicate that these points are clustered around the diagonal; thus, the correlation between adjacent pixels in the original image is extremely strong. Figures 14(d)–14(f) show the distribution of the pixel sequence pairs of the encrypted image by the x-dimensional sequence of Eq. (6) in the horizontal, vertical, and diagonal directions, respectively. The figures imply that all points are randomly distributed within the range; thus, after breaking the mutuality between the adjacent pixels of the plain image, no correlation exists between the adjacent pixels of the encrypted image.
The value of Eq. (10) for each pair is shown in Table 1. The correlation coefficients of the original image are all close to 1 in each direction, and the correlation coefficients of the encrypted image are all smaller than 0.01. This finding implies that our method successfully breaks the correlations between adjacent pixels of the plain image. The absolute values of the correlation coefficients of the encrypted image with our algorithm in the horizontal, vertical, and diagonal directions are far less than those of other proposed algorithms [1, 6, 8, 15, 23, 25], which implies that our algorithm is more competitive to a certain extent.
5.2.5 Key sensitivity analysis
A secure encryption algorithm should have extreme key sensitivity, which is divided into two aspects,
-
1)
The security keys should be sensitive in the encryption process. The encrypted images for the same plain image should be entirely different with a small change of the key.
-
2)
The security keys should be sensitive in the decryption process. The decrypted images for the same encrypted images should be entirely different with a small change of the key.
We introduce the mean square error (MSE) to measure key sensitivity and make the results more intuitive. The MSE between two images can reflect their degree of difference, as shown as follows:
where f(x, y) and \( \overline{f}\left(x,y\right) \) are the pixel values at point (x, y) of two test images. M × N denotes the image size. The MSE is extremely large with a slight deviation from the correct keys and is extremely small only when the main keys are completely correct. Figure 15 shows the MSE curves between the encrypted images generated by correct and wrong keys. Figure 16 shows the MSE curves between the decrypted images generated by correct and wrong keys. These results show that all the security keys have sensitivity in the encryption and decryption processes.
5.2.6 Resistance to differential attack analysis
The differential attack, also called the chosen-plaintext attack, is an effective image analysis method. A good image encryption algorithm should have good performance to resist the differential attack.
The number of changing pixel rate (NPCR) and the unified average changing intensity (UACI) are important factors in evaluating the performance against differential attacks of an image encryption algorithm.
NPCR and UACI represent the percentage and the degree of change in the number of encrypted image pixel values after randomly changing a certain pixel value of the original image, respectively. If a pixel change can cause a complete change in the cipher image, then this algorithm has a good performance against a differential attack.
For the random grayscale image, the ideal values of NPCR and UACI are 0.9961 and 0.3346, respectively. We randomly add 1 pixel to the original image. The NPCR and UACI generated by Eq. (6) are shown in Table 2. From the table, the cipher image completely changes after randomly changing a certain pixel value of the original image. Thus, this algorithm exhibits good performance against differential attack, and is competitive to other recent proposed chaos-based encryption algorithms.
5.2.7 Information entropy analysis
Information entropy is the most significant measure of disorder, or unpredictability. The information entropy can be calculated as
where, n is the total number of symbols, and p(xi) is the probability of the symbol xi. For a completely random image with 256 Gy levels, its entropy should ideally be 8.
The information entropies of the original and encrypted images are shown in Table 3. From the table, the entropy of the encrypted image using our method is extremely close to the ideal value of 8; thus, the pixels of the encrypted image are extremely random. Table 3 also indicates that the information entropy of our encrypted image is competitive compared with other proposed encryption algorithms.
5.2.8 Robustness analysis
Images will be destroyed due to various reasons in the process of spreading. Therefore, a good algorithm should have strong robustness against noise and data loss; hence, the cipher image can also be decoded even if some information is lost. Figure 17 shows the robustness analysis results of our algorithm against noise and data loss. The results demonstrate that the damaged cipher image can still be decoded and that the decrypted image can still be recognized with some noise. Therefore, our method is robust enough to resist the attack of noise and data loss.
Robustness analysis (a1) Ciphertext image with 0.5% speckle noise; (a2) Decrypted result with 0.5% speckle noise; (b1) Ciphertext image with 1% speckle noise; (b2) Decrypted result with 1% speckle noise; (c1) Ciphertext image with 1% data loss; (c2) Decrypted result with 1% data loss; (d1) Ciphertext image with 5% data loss; (d2) Decrypted result with 5% data loss
6 Conclusions
On the basis of previous research, this study proposes a new delayed coupled chaotic model to reduce the dynamical degradation of digital chaotic maps. The characteristic analysis implies that the coupled system is time varying and that the output sequences are non-stationary with high complexity. In comparison with other methods, the proposed method has simple coupling rules that can be applied to all chaotic systems. The results confirm that our method has greater future potential in the area of information encryption. Furthermore, the proposed method is applied to image encryption. The image encryption algorithm is considerably simple, and the security of the encrypted image completely depends on the selected delayed coupled digital chaotic system. The experimental tests demonstrate that the image encryption algorithm has high security and is more competitive than other algorithms.
References
Amin M, Faragallah OS (2010) A chaotic block cipher algorithm for image cryptosystems. Commun Nonlinear Sci Numer Simulat 15:3484–3479
Bandt C, Pompe B (2002) Permutation entropy: a natural complexity measure for time series. Phys Rev Lett 88(17):174102
Dascalescu AC, Boriga R, Racuciu C (2012) A new pseudorandom bit generator using compounded chaotic tent maps. 2012 9th International Conference on Communications (COMM), Bucuresti, 339–342
Deng YS, Hu HP, Xiong NX, Xiong W, Liu LF (2015) A general hybrid model for chaos robust synchronization and degradation reduction. Inform Sci 305:146–164
Dogan S (2016) A new data hiding method based on chaos embedded genetic algorithm for color image. Artif Intell Rev 46(1):129–143
Francois M, Grosges T, Barchiesi D, Erra R (2012) A new image encryption scheme based on a chaotic function. Image Commun 27:249–259
Hu H, Xu Y, Zhu Z (2008) A method of improving the properties of digital chaotic system. Chaos, Solitons Fractals 38:439
Hua ZY, Zhou YC, Pun CM, Philip Chen CL (2015) 2D sine logistic modulation map for image encryption. Inf Sci 297:80–94
Jawad LM, Sulong G (2015) Chaotic map-embedded blowfish algorithm for security enhancement of colour image encryption. Nonlinear Dynam 81(4):2079–2093
Kalouptsidis N (1996) Signal processing systems, in Telecommunications and signal processing series. New York: Wiley
Kocarev L, Szczepanski J, Amigo JM, Tomovski I (2006) Discrete chaos—part I: theory. IEEE Trans Circuit Syst I 53:1300–1309
Li S, Mou X, Cai Y (2001) Improving security of a chaotic encryption approach. Phys Lett A 290:127–133
Li CY, Chen YH, Chang TY, Deng LY, To K (2012) Period extension and randomness enhancement using high-throughput reseeding-mixing PRNG. IEEE Trans Very Large Scale Integrat Syst 20(2):385–389
Liu LF, Miao SX (2017) Delay-introducing method to improve the dynamical degradation of a digital chaotic map. Inf Sci 396:1–13
Liu LF, Miao SX (2017) An image encryption algorithm based on baker map with varying parameter. Multimed Toolds Appl 76:16511–16527
Liu SB, Sun J, Xu ZQ, Liu JS (2009) Digital chaotic sequence generator based on coupled chaotic systems. Chin Phys B 18:5219–5227
Liu L. F., Hu H. P. and Deng Y. S., An analog-digital mixed method for solving the dynamical degradation of digital chaotic systems, IMA J Math Control Inf, 2015, 32(4), 703–715.
Nagaraj N, Shastry MC, Vaidya PG (2008) Increasing average period lengths by switching of robust chaos maps in finite precision. Eur Phys J Spec Topics 165(1):73–83
Persohn KJ, Povinelli RJ (2012) Analyzing logistic map pseudorandom number generators for periodicity induced by finite precision floating-point representation. Chaos, Solitons Fractals 45:238–245
Pincus SM (1991) Approximate entropy as a measure of system complexity. Proc Nat Acad Sci 88:2297–2301
Sun F, Lu Z, Liu S (2010) A new cryptosystem based on spatial chaotic system. Opt Commun 283:2066–2073
Talarposhti KM, Jamei MK (2016) A secure image encryption method based on dynamic harmony search (DHS) combined with chaotic map. Opt Lasers Eng 81:21–34
Tong XJ, Wang Z, Zhang M, Liu Y, Xu H, Ma J (2015) An image encryption algorithm based on the perturbed high-dimensional chaotic map. Nonlinear Dynam 80:1493–1508
Vaferi E, Nadooshan RS (2015) A new encryption algorithm for color images based on total chaotic shuffling scheme. Optik 126(20):2474–2480
Wang XY, Guo K (2014) A new image alternate encryption algorithm based on chaotic map. Nonlinear Dynam 76(4):1943–1950
Wang Y, Wong K, Liao X, Xiang T, Chen G (2009) A chaos-based image encryption algorithm with variable control parameters. Chaos Soliton Fract 41(4):1773–1783
Wang XM, Zhang WF, Zhang JS (2013) Secure chaotic system with application to chaotic ciphers. Inf Sci 221:555–570
Wang W, Tan H, Pang Y, Li Z (2016) A novel encryption algorithm based on DWT and multichaos mapping. J Sens 5:2646205
Wang W, Si M, Pang Y, Ran P (2017) An encryption algorithm based on combined chaos in body area networks. Comput Electric Eng 65:282–291
Zhang M, Tong XJ (2014) A new chaotic map based image encryption schemes for several image formats. J Syst Softw 98:140–154
Zhou Q, Liao X (2012) Collision-based flexible image encryption algorithm. J Syst Softw 85:400–407
Zhou Y, Hua Z, Pun C, Chen CLP (2015) Cascade chaotic systems with applications. IEEE Trans Cybernet 45(9):2001–2012
Acknowledgements
This work is supported by the National Natural Science Foundation of China (61601215, 61862042).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tang, J., Yu, Z. & Liu, L. A delay coupling method to reduce the dynamical degradation of digital chaotic maps and its application for image encryption. Multimed Tools Appl 78, 24765–24788 (2019). https://doi.org/10.1007/s11042-019-7602-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-7602-8