Abstract
In this research, we propose the thermal power generation fault diagnosis and prediction model based on deep learning and multimedia systems. The application of multimedia technology in the power dispatching communication system not only greatly enhances the stability and reliability of the power system, but also enriches the application of science and technology in the power system. It is one of the main directions for the development of power communication and information processing systems. The paper’s novelty and contribution are major reflected from the three aspects. First, we optimize the traditional neural network model to fix it more suitable for multimedia applications. We improve the forecasting accuracy; and then for each type of sample of B-neural network model, the up-front of meteorological data. Second, the deep neural network is optimized for better evaluation efficiency. The number of convolution kernels in each convolutional layer in the network is different. The more the number of the post-convolution kernels, the more efficient the model will be. Therefore, the multi-kernel structure is proposed. Third, we integrate the multimedia into the prediction scenario to visualize the data and results. The experiment result is conducted to validate the performance of the proposed method. Results compared with the other state-of-the-art models demonstrate the robustness of our method.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The main electrical systems in thermal power plants are generator sets, lead-out lines, factory connections, transformers, power distribution equipment, main wiring and switches, power supplies, and communications equipment. The safe and stable operation of electrical systems not only ensures the continuity of electrical energy. Supply, and have a positive role in the realization of the economic benefits of power plants. Therefore, during the electrical operation of the power plant, it is necessary to be able to quickly detect the occurrence of electrical faults and take appropriate measures in time to reduce the accident losses. In the course of electrical operation of a power plant, once an electrical operation failure occurs, it will have a greater impact on power generation efficiency and affect the operation of the power system. Therefore, it is not only necessary to accurately locate electrical faults, but also to take various preventive measures in advance to quickly eliminate the faults. Thermal power of the electric system is mainly composed of power plant main connection, steam turbine generator, main transformer, power distribution equipment, switchgear, generator pinout, factory with connection, factory with transformer and reactor and motor factory, security power supply, battery dc system and a few parts of communication equipment, lighting equipment, etc. The basic function of the thermal power system is to ensure the power supply to the load or power system according to the power quality. However, the actual operation of electrical equipment is often subjected to the dual pressure of electrical load and mechanical load. These pressures will have a fatal impact on the operating efficiency, safety, and service life of electrical equipment. Sometimes, the consequences are the same from the perspective of phenomena. But it is a failure of the electrical system caused by different reasons [1,2,3]. It is necessary to solve the problem through different solutions. Specifically, the problems and causes of the failure of the electrical equipment in thermal power generation mainly include the following aspects. (1) In the thermal power plants, power generation units are very prone to temperature is too high. The alternator is running over a period of time, sometimes the temperature will rise very high, so that the alternator produces a copper consumption as well as iron consumption and the consumption of energy and a portion of the converted to heat energy, causing the generation of higher temperature, resulting in a vicious circle, and the long-term if the generators at high temperatures, and it is very possible that the aging of insulation, temperature, the higher the burn speed, long-term prior to the alternator in grave danger. In generator set temperature is mainly caused by long hours of running hot consumption increase, the heat is not released, the engine cooling system is not ideal or cooling temperature settings are not ideal, etc. (2) The slip ring generator carbon brushes in the alternator failure, the high-speed operation, the slip ring carbon brush can be prone to fire, if this is the case, if we are not able to take timely and effective measures will result in the entire carbon brush all on fire, it has the high possibility of causing the generator in high-speed running downtime to allow the generator has been seriously damaged, while at the same time, bringing in huge economic losses. (3) In the thermal power plant, the number of installed power plants, the number of single machines and the main connection mode will affect the selection level of the backup power supply. Generator at work, if for some reason, high and low voltage power to stop the work, you need to take the standby power, before the standby power use, on the bus all motor equipment to run the slowdown, the standby power supply switch after success, for the motor is suddenly increased a large voltage, the voltage will cause serious influence to electrical equipment, the influence of different capacity of generating sets are also have some different [5,6,7, 9]. Moreover, if the standby power switch takes a long time, it will also then reduce the operating speed of the motor and even affect the operation of the boiler. (4) Electrical equipment operation process, if maintenance and inspection work is not timely, or cannot do bit, it will cause a short circuit problem occurs, not only will the electrical equipment to bring greater damage, but also jeopardize personnel safety, the need to make a good electrical ground [4, 8]. When the electrical short-circuit fault occurs, the fault occurrence point is more subtle, this will give the detection work brought certain difficulty, therefore the need for a DC ground or AC ground for the distinction, and the ground connection line to be checked, do good investigation work, in order to reduce economic losses. (5) Export short-circuit fault, in the transformer fault type, where the problem of export short circuit is the greatest harm, once a short circuit fault occurs. It can make a large current in the winding of the transformer, and this current is often dozens of times the normal current rating of the transformer. Such a large amount of current energy will have a certain impact on the insulation strength of the windings in the transformer, and even worse, it will destroy its insulation layer and damage the entire transformer.
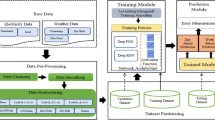
To deal with the mentioned challenges, this paper designs and implements the multimedia system for thermal power generation fault diagnosis with deep neural network and fuzzy prediction scenario. To begin with, the Fig. 1 presents the general thermal power generation fault diagnosis framework [10,11,12,13,14,15].
The application of multimedia technology in the power dispatching communication system not only greatly enhances the stability and reliability of the power system, but also enriches the application of science and technology in the power system. It is one of the main directions for the development of power communication systems. As a core part of the multimedia technology, soft switching system for the entire power dispatch communication system’s main support for soft switching system can not only promote the use of electric power, as well as records of full control, we can also make the instruction in the communication terminal to display. The map is a multi-media technology is the most obvious characteristic of the electric power dispatch as an integral part of the information mapping has become a key reference information, in order to support multiple communication system, communication terminal, the mapper is also required. The information is mapped to the role, whether the call forwarding or call redirection and can work together in a mobile terminal. Based on the literature review, we can summarize the background application of the multimedia assisted system from the following aspects [16,18,18]. (1) The application of power dispatching communication system in the switching system can not only transmit the protocol and instruction in time, but also realize the information sharing of communication network and computer network. At the same time, the transmission of data and language will also be speeded up with the use of switching technology, and the use of open network structures can facilitate the use of files. (2) The most distinct feature of multimedia technology is information mapping, which is also an important part of the power scheduling. The same information mapping is the main reference of information positioning. And it is necessary to support multiple communication systems at the same time. The information mapper is also necessary for the communication terminal. (3) In the visual scheduling system, the more common of the functions is call processing and call forwarding, wherein the call processing belonging to the pending function, and the call transfer is maximum respect for the needs of users, this is a visual scheduling a concentrated expression. (4) In the digital recording system, the data record and the visualization operation are equally important, which is the important guarantee to realize the reliability and stability of the power dispatching communication system. The Fig. 2 demonstrates the data analysis framework for the multimedia systems.
Therefore, in this paper, the thermal power generation fault diagnosis and prediction model based on deep learning and multimedia systems is studied. In the section 2, we study the theoretical background of the neural network, deep learning and the multimedia security model to serve as the basis of the research. In the section 3, the multimedia and power generation combination pattern is studied. In the section 4, we finalized model is proposed. The section 5 is the experimental verification of the proposed idea and in the section 6, we summarize the whole contributions.
2 Theoretical basis for the proposed model
2.1 Neural network and the inner organization modelling
Artificial neural network is a functional model based on the structure and function of human brain. Figure 2 demonstrates the inner organization of the traditional multi-layer neural network [19].
In our scenario, we take the prediction of power with the neural network, the impact of photovoltaic power generation system the output power of many factors, with solar radiation, the inverter conversion efficiency, the solar panel mounting angle, temperature, barometric pressure, etc. If each of the factors are as predictive inputs to the model will increase model complexity, and input variables of the increase will also improve the photovoltaic power generation system historical data collection the difficulty of the job, so accurate analysis of the output power of the strong relevance factor and use it as the input quantity, the direct relationship between the prediction model’s usability and accuracy. We improve forecasting accuracy; and then for each type of sample of B-neural network model, the up-front of meteorological data and historical information on small hydropower running as a model, and taking into account the dynamics of power stations and units in operation, in order to take advantage of the small hydropower less hours as part of the B-network model output, the treatment of the test sample identification classified forecast. In our proposed network, the transmission function is presented as Eq. 1.
Where the exp.() operation is adopted to calculate the transmission efficiency, the method of determining the training samples depends on the similar day selection algorithm. Training samples are formed according to the historical records of the first k days in ascending order of temperature Euclidean distance. The training samples can be used to train the neural network, and then the trained neural network is used and can then predict output power. The neural network contains an input layer, one hidden layer and an output layer, the layer of the neural one-way connection, the layer of neural independently of each other, the output layer can access any value based on the output of the network looks forward to calculate the Inverse error, the value of the right to make corrections, the network of learning and training process is to adjust the value of the process until error is less than the value of the end of learning.
Equations 2 and 3 are the detailed transmission function for operating the model. The parameter definitions can be found in [3, 34]. The detailed calculation steps can be summarized as the follows. (1) Accumulate PV power data as a time series to generate accumulative sequences [20,21,22,23]. (2) First, the prediction accuracy and the walk constant of the combined model are set, then the data after the photovoltaic power generation are input, then the nonlinear mapping relation is established by neural network, and the network is trained, in which the center and width of the Gauss function can be obtained according to the clustering algorithm, and the output weights can be determined by the least second multiplication method. (3) Compared with the other neural network, GNDH network structure to dynamically determine during training, there is no need to consider the BP neural network is the number of nodes in the hidden layer to determine the problem. The training process, the number of neural layers, each with a layer will increase the number of new neural, while at the same time, the performance of the neural will be discarded. The training process, by continuing to adjust the neural weight and neural choices, wait until the map accuracy [37, 42]. (4) The artificial neural networks precision enhancement may through use a concealed level to increase his/her neuron the method to realize, this must be simpler than in the structure realization the increase concealment level number, therefore the light bends down the generating system output forecast model to use the list concealed level structure. The concealed level neuron integer choice relates the neural network directly the scale and the precision. The light bends down the generating system output forecast model input variable unit to be different, the magnitude difference is also big, but the neuron output all is usually limited in certain scope. (5) The final predicted PV power and actual data are analyzed, and the accuracy that meets the actual needs is obtained through constant adjustment. Figures 3 and 4 demonstrates the sample simulation results for reference.
2.2 Multimedia intrusion detection
Network intrusion detection system is the network resources of malicious behavior is identified and processing system. He may be a network capture of the packets with the rules in the library thousands of multi-rule pattern matching, found that there may be attacks. In the past using way to much is the firewall policy, it can prevent the use of protocol vulnerability, source routing, address phishing and other attacks, and provide safe data channel. But it is for the application layer to the back door, inside the user’s unauthorized operation as a result of the attack or theft, destruction of information are powerless. In addition, due to the location of the firewall in the network in the daylight, its own design flaws are also inevitably exposed to a multitude of attackers, so just by virtue of the firewall is difficult to resist the many endless network attack, but from inside the system attacks more is helpless. The media packet processing method there are two that are released and the corresponding media type detection. The release of the identified multimedia data packets over the system general rule matching process, this method is simple and efficient, but security low. The corresponding media type detection methods can be based on the media type select the type of the corresponding rules of the pre-test, if there is no problem, we can release, into the normal detection process, because the number of pre-test rules is far less than the number of conventional detection rules, so this method for most secure multimedia packets can significantly improve test efficiency, security and release method than high.
Anomaly intrusion detection is the major premise intrusion activities set as a subset of the abnormal activity. The ideal situation is that the abnormal activities set with intrusion activities set is the same. In this way, detecting abnormal activity is precisely the invasive activity [24, 25]. The result will not result in a misrepresentation, omission of invasion. However, the invasion activity set is not always consistent with abnormal activity sets. In the Table 1, we present the components.
The identification module of the server of the multimedia data identification method is from the server-side sent with the request packet belong to a session data packet is checked, and if found load the front with the multimedia features it can be concluded that the data packets with a multimedia data, and in this session, from the server end sends the sequence number of a connected relationship and with the load of the data packets may carry the multimedia data. However, there are some server issues the data packet in the multimedia feature of the position is not fixed.
As shown in the Fig. 5, intrusion information detection with soft computing models can effectively deal with this challenge. The cloud-based intrusion detection method generally uses the qualitative reasoning of the cloud to convert the qualitative detection rules expressed by the security experts using natural language into the quantitative rules that the computer can process. Such methods lack the facts and standards. Our primary focuses are the databases used for the system, and the target objectives could be separated into two major aspects. (1) When multimedia data to identify modules that a packet with a multimedia data, the processing module is based on the type of multimedia data in two-dimensional chain table, from going to the order after you find the corresponding media type junction and the junction with the link on the right side of the character string to match. (2) Carrying some attack information of multimedia data packets are relatively concentrated in a specific phase, so the character string node list for dynamic scheduling will also reduce the matching time. Dynamic scheduling method is the same as above, if we find a character string matching, with the characteristics of the nodes and before a string switch position [26,32,28].
These algorithms in the network intrusion detection field have achieved good detection results, but these methods are based on empirical risk minimization principle in machine learning algorithms, the detection accuracy obtained with the number of samples of a great relationship, the fluctuation is large. Support vector machine as a new machine learning method, it can through risk minimization principle to solve small sample, nonlinear, high-dimensional problems, very suitable for application in network intrusion detection. Based on the SVM, lots of models are presented, and therefore, we summarize some in the Table 2.
2.3 Deep learning model and the application scenario discussions
Deep learning process refers to the characteristics of the learning process, which is the essence of the original data through some simple non-linear model to a more senior and more abstract form. It is important that the demand for classification of high-level and abstract forms to strengthen the capacity of the original data classification, while at the same time weakening the raw data that is not associated with the classification of the characteristics of the component. First, by having a plurality of hidden layer of the neural network layer by layer feature transformation, a large number of high-dimensional, nonlinear label-free original data for feature dimensionality reduction, thereby obtaining the original data of the optimal low-dimensional representation, significantly reducing the data dimension, not only retains the data of the key important features, while removing redundant features; then, using the binary tree structure multi-class support vector machine classifier, and to obtain the optimal low-dimensional representation of the network attack behavior recognition [29, 30].
Equation 4 is the standard neural network expression, as the \( \mathit{\exp}\left[-\frac{{\left({\mathbf{y}}_j-{Z}_j{\mathbf{b}}_j\right)}^{\prime}\left({\mathbf{y}}_j-{Z}_j{\mathbf{b}}_j\right)}{2{\sigma}_j^2}\right] \) is the network transmission weight and the \( \prod \limits_{j=1}^m\;{\left({\sigma}_j\right)}^{-\left(n+1\right)} \)is the size control parameter. We designed a highly efficient convolutional neural network. The entire network consists of 3 hidden layers. Each hidden layer contains a convolutional layer and a pooling layer. The number of convolution kernels in each hidden layer is different. The network uses 3*3 convolution kernels and 3*3 pooled cores to enhance performance by continuously deepening the network structure. The number of convolution kernels in each convolutional layer in the network is different. The more the number of the post-convolution kernels, the more efficient the model will be. We thought each convolution nucleus is actually a unique characteristic extractor also the more high-level convolution operation gains a more abstract characteristic. In order to can catch to data many kinds of important characteristics, has all established many convolution nucleus for each convolution level, simultaneously considered the attack the hierarchical and the complexity, have used the deeper network architecture that lets the network have the enough capacity to produce the multi-level characteristic expression. After the general process multi-layer convolution and the pond operation produces the new characteristic often is more robust and dense lowers the dimension characteristic, this time stretches this matrix for the unidimensional characteristic vector inputs the entire connection the Softmax level.
Equation 5 is the enhanced presentation of the Eq. 4. Where the \( {\left({\sigma}_1^2\right)}^{-\left(n+1\right)/2}\exp \left[-\frac{{\left({\mathbf{y}}_1-{X}_1{\mathbf{b}}_1\right)}^{\prime}\left({\mathbf{y}}_1-{Z}_1{\mathbf{b}}_1\right)}{2{\sigma}_1^2}\right] \) and \( {\left({\sigma}_2^2\right)}^{-\left(n+1\right)/2}\exp \left[-\frac{{\left({\mathbf{y}}_2-{Z}_2{\mathbf{b}}_2\right)}^{\prime}\left({\mathbf{y}}_2-{Z}_j{\mathbf{b}}_2\right)}{2{\sigma}_2^2}\right] \) are the revised template. Similar to the deep network, ML-ELM creates a multilayer neural network by stacking on top of ELM-AE. The first feature of the ML-ELM is that it does not require fine-tuning compared to deep learning networks. The hidden layer weights of ML-ELM are initialized, while ELM-AE uses layer-by-layer greedy unsupervised learning algorithms. Multi-layer extreme learning machine for intrusion detection algorithm by layer-by-layer unsupervised learning using a large number of unlabeled samples for training the hidden layer the weights of the output matrix, and then use the output matrix to be detected network data classification, so as to achieve to distinguish between normal data and attack data.
Equation 6 is the statistical expression of the proposed framework. We use an unsupervised and greedy learning method to train each RBM network layer by layer from bottom to top, and map a large number of high-dimensional, non-linear, unlabeled data raw data to low-dimensional representations to obtain a better initial model parameter. Figure 6 presents the structure of the mentioned model.
3 Multimedia and power generation combination pattern
The multimedia monitoring system of a power plant is mainly composed of a front-end image acquisition unit, a signal transmission unit, a central control unit, etc. It can transmit the conditions of each monitoring point to the central control unit in real time and quickly so that the managers can observe at any time. What happens in all aspects of the power generation system can be easily detected through the framework design and analysis. In addition, the status of the scene can be analyzed according to the preset settings, and it can be used as a site monitoring function. Therefore, improving the safety and reliability of substations, the intelligence and sensitivity of transmission and distribution adjustments is very important for the realization of integrated automation of distribution systems. Based on the literature reviews, the applications scenarios can be separated into following aspects. (1) After the application of multi-media technology, it is possible to combine the industrial television system of a hydropower plant with a computer monitoring system, and to use the Internet and share screens. So far the hydroelectric power plant’s industrial television network and monitoring system are completely independent of the two systems. There is no connection between the two. The length of the image recorded here depends on the need to analyze the accident and the capacity of the CD-ROM or hard disk.
Also we can combine the information such as voice, image, status, value measurement, through the integrated services digital network to realize remote transmission of film and television image information, and may have with the hydraulic power plants of hydrologic meteorological computer telemetry system networking, display, store, or reproduce meteorological satellite, etc. (2) Voice alarm has been applied to computer monitoring system of hydropower plant and has gained successful experience. After using multi-media technology, as one of the internal functions, voice alarm can also be easily realized. In the voice operation or the voice control aspect, the first can achieve the voice tone screen or the like operations, the operator can largely throw off the function keys and freely send password tone picture. (3) The visualization technology also is in the graphics a very remarkable domain. Technical and so on union animation applications besides use the digital result to express the test result or the computed result, but also the available graph expresses vividly. For example the automatic electricity generation control and the economical load assignment computed result and the intermediate result, the water-turbine generator set current capacity or the efficiency test result, pilots in the steel pipe the speed of flow and the fluid state distribution, the hydraulic turbine in its synthesis characteristic operating position, the water-turbine generator set or some micro increases rate curve movement in its efficiency characteristic curve and so on, all has the possibility to use the visualization technology vividly expresses in two-dimensional or three dimensional spatial. (4) Digital recording system mainly, and visualization dispatcher station cooperate with each other, and the visualization dispatcher station is mainly from the visual operation principle of the digital recording system is using the technology of artificial intelligence. Under the action of digital recording system, the power dispatching communication system can check and record the visual materials with the relevant execution instructions. In digital recording system, visual operation and data recording are equally important, which are important guarantee for the stability and reliability of power dispatching communication system. (5) The use of multimedia technology to optimize power dispatch communication system, the main problem is that the new system and the system of communion, especially in soft switching system to adapt to the problem. In order to achieve the communication system robust business transfer feature, the system on the network Tandem technology transformation, while at the same time to take advantage of the tandem level to exchange software to function. Signal conversion and information delivery needs the new and legacy systems integration. In the Figs. 6 and 7 we demonstrate the multimedia and power generation combination pattern sample [31,37,33].
In can be reflected in the Fig. 6 that the scheduling model should be optimized. For dealing this challenge, we present the objective function in the Eq. 7. Where the \( \frac{1}{2}{\boldsymbol{\upalpha}}^{\ast }{\Lambda_i}^{-1}\boldsymbol{\upalpha} +\frac{1}{2}{\left\Vert {\boldsymbol{\upalpha}}_i\right\Vert}_1\ge {\left\Vert \boldsymbol{\upalpha} \right\Vert}_1 \) and \( \frac{1}{2}{\boldsymbol{\upalpha}}_i^{\ast }{\Lambda}_i^{-1}{\boldsymbol{\upalpha}}_i+\frac{1}{2}{\left\Vert {\boldsymbol{\upalpha}}_i\right\Vert}_1={\left\Vert {\boldsymbol{\upalpha}}_i\right\Vert}_1 \) are boundary conditions.
While using multimedia technology to optimize power dispatch communications system, the most important issue of the system and the new system integration and, in particular, to the soft switching and if we want a better communication system for powerful business features, you will need to transform the existing network tandem technology, while the use of tandem level for the purposes of the exchange software features. Information delivery and signal the need for the conversion of the old and new systems to achieve the beneficial integration between them. Therefore, the additional boundary condition is proposed as Eq. 8.
Where the wi is the basic weight set from the users, and the \( \sum \limits_{j=1}^{l_{x_i}}{\left|{h}_A^{\sigma (j)}\left({x}_i\right)-{h}_B^{\sigma (j)}\left({x}_i\right)\right|}^{\lambda } \) is the detection condition. Through the above model, we can consider the three major application scenarios as follows.
-
1)
In the motor main control room Control screen is placed in front of a camera, a camera with PTZ can be by the monitoring center of its focus and direction adjustment. Image transmission to the monitoring center, so that we can monitor the center of the main control room control panel for viewing, and may be in the control center select the observation area and adjust the image quality.
-
2)
In the remote site, there are usually two main transformers that need to be monitored and monitored by the main transformer fans. Each main transformer fan is equipped with a camera that monitors the area to cover the monitored fan. The image is transmitted from the camera to the monitoring center.
-
3)
There can be multiple separate areas in the equipment room. In order to increase the efficiency of equipment use and reduce costs, each of the four adjacent and adjacent separation areas can be used as a monitoring area. A camera is suspended above the corridor for monitoring and the images are transmitted to the monitoring center [34, 35].
For the area between the power controls, soft-switching mode of application, we can achieve a large capacity installation of the machine running. In the gateway terminal, each region between the trunking gateway and softswitch equipment can control the province’s electricity. At the same time, different parts of the power equipment use, maintenance and scrap processing can also take advantage of soft switching technology. Partitioning the centralized control mode of the application can greatly enhance the regional power dispatch communication system operation efficiency, the soft switch number is to ensure that the area between the power stable supply of important factors. The top-down (PC) to complete the media monitoring, real-time database, network communications and Internet telephony (IP phone) and it is currently the most advanced multimedia and computer communication technologies are introduced into the RTU, make video surveillance, security, defense, and other new technologies with base RTU features subtle blend together, but also IP phone to power dispatch communication system, using existing scheduling network resources and enterprise’s own IP network for voice and data integration. The access gateway is located at the edge access layer in the softswitch architecture and provides an analog subscriber line interface for direct access of ordinary telephone users to the IMS switching network. For units that do not have IP user cabling conditions and have a large user size, the user’s analog access can be implemented by arranging the AG. The integrated access device is the access point of the remote user, which can make full use of the characteristics of IMS and the access resources of the existing data network, and connect the remote users to the IMS system. The original administrative switching system uses the remote module and the PCM release user, which can realize analog user access by deploying IAD in IMS administrative switching network (Fig. 8).
Figure 6 presents the multimedia tracking simulation as the proposed system. The place is a high-precision GPS IPPS pulse synchronization full data sampling, and apply differential algorithms for high-precision, and output a message to the host. Analog acquisition module is used for high-speed synchronous sampling ac analog, the module has a synchronous sample-and-Hold feature, in the high-accuracy GPS pulse-driven synchronous latch acquisition instantaneous value, and then handed over to the high-precision low temperature drift-amplifier circuit amplified, then the use of high speed A/D chip analog to digital conversion [36,42,43,39].
4 Thermal power generation fault diagnosis and prediction
In the operation of the DCS system, the software failure is mainly caused by its own. This type of fault usually occurs during commissioning and commissioning of the DCS system. Due to the heavy workload and complicated procedures of the application software, application software errors are inevitable [40,46,42]. This requires that during the DCS commissioning phase, the operating personnel and configuration personnel must Take it seriously, discover it in time and cooperate with DCS system debugger to solve the problem. In addition, it is in normal operation of the system, should increase control, and the increase of the corresponding control points, online error or modify the program result in system crash, which requires the DCS configuration programming staff very familiar with system pre-made control scheme for implementation, backup must be ready before the implementation of the program, can avoid error occurs in time to save unnecessary loss. In the DCS system, usually in the thermal control system was added to the BMS, CCS, DEH and other important process control point, to guarantee the safety of the unit the ability to run, to achieve the associated fault shutdown protection. But during operation, hot working automatic control system as the security and reliability very easily affected. Such as a network communication failure in the traffic breakpoint problems can easily lead to traffic overload, in the absence of flow restriction protection condition, the entire system control network and the input and output of the circuit will appear blocking phenomenon, resulting in system-related equipment cannot make the right action. In addition, the DCS system also will be affected by the Setting Value fault, the output module is defective, the signal processing speed and other causes of impact that is demonstrated in the Fig. 9.
Special electromagnetic environment in power plant, by serious electromagnetic interference, relay protection device for microcomputer protection device, the CPU is under the control of the clock work at high speed, cannot avoid interference by simple delay circuit, so for microcomputer protection, improve the anti-interference ability is an important work. To a large power plant 500 MW power generating units, for example, due to the manufacturing of the generator neutral point side can only lead to the three terminals, the alternator and the variable set of differential protection can only be used with the traditional full vertical deviation of the alternator stator winding circle a short circuit between the branch and the solder without the protection function, in response to the structural characteristics of the generators can only be for the alternator stator testing of short circuit protection, and the circle of protection works complex, the actual protection effect is yet to be verified. If the generator is the generator neutral point side out four to six terminals, the situation is not the same, generators and the Variable Group Home protection can be incomplete longitudinal differential protection, the generator can also be configured highly sensitive transverse differential protection, so that the alternator stator windings are all failures (including the alternator stator winding circle a short circuit between the branch and the solder) has a dual set of triple protection, coupled with the transformer completely longitudinal differential protection, can already meet the requirements, you do not need to configure the generator testing and anti-time over load protection reliability increased significantly [43,44,45,46]. From here we can see that the device structure parameter on the characteristics of the secondary device selection, design and reliability of the impact is enormous.
For the prediction, we should consider following major aspects. (1) Since the original power generators in the role, function, power failure, the alternator’s own protection system to protect the device, so all of the machine will gradually decrease in speed, then switch to the standby power, all of the equipment started operating, be given a driving force, but the driving forces for those who already have lower rate of electrical equipment, an additional voltage, may result in equipment damage, long in the past, it will be difficult to repair the equipment while reducing life. (2) Cable circuit problems are usually caused by unreasonable layout of the cable specification mouth water, such as wiring insulation aging or damage, cable in laying cable and other reasons are likely to cause high temperature section line empty pick up, the phenomenon of break eventually led to the thermal control equipment mis-operation phenomenon appeared in the process of running. (3) In the DCS system normal operation, often due to part of the function is difficult to effectively apply and lead to some of the control link cannot be successfully carried out, and the DCS system itself does not present any problems, these problems are usually because the operator did not fully understand the DCS system of functional role, lack of skilled operation and bring.
For the diagnosis, we should consider following major aspects. (1) Thermoelectric power generation electrical automation systems, as well as their associated distribution control systems usually reserve a portion of the hard wiring. In particular, we work to protect the power plant electrical full communication control mode for the specific needs related to the fire, thermal power generation process chain of problem-solving in place so as to effectively improve the thermal power generation process, the background of the electrical system application level, in the initial stages of the basic operation monitoring functions to be rich. (2) Conditional power plant DCS system shall be network instead of double network topology, whereby to make two separate network management and system, which is beneficial to improve the stability and reliability of DCS operation network. (3) We must carry out regular inspections and inspections, and focus on the following links: Regularly check the fans of the DCS system to see if it is operating normally, whether the air ducts are clogged or not; check all communication lines. See if the interface is abnormal and the connection is firm and reliable; test and test each module and terminal regularly to ensure that it can always be in the best operating condition; strengthen the inspection and maintenance of the equipment during operation of the unit, and carefully check Communication status to avoid system failure due to communication failure. (4) The optimization of DCS control system to improve the overall system prevention and softening failure capability is the optimization goal, focusing on the optimization of hardware quality and software self-diagnosis ability. (5) In order to extend the equipment service life and stability of the optimization objectives, focus on optimizing the vibration, dust, temperature, temperature and other working conditions of the system and operating conditions, to reduce environmental thermal control equipment.
5 Experiment design and validation
This section validates the proposed method. In the Fig. 10, we present the prediction accuracy rate simulation. In the Tables 3 and 4, we demonstrate the detection rate changes before and after the systematic processing and the experimental simulation on different datasets on detection accuracy, respectively. The prediction accuracy rate has reached 95.75% and the detection rate changes before and after the systematic processing is validated.
6 Conclusion
The paper discusses the thermal power generation fault diagnosis and prediction model based on deep learning and multimedia systems. The safe and stable operation of electrical systems not only ensures the continuity of electrical energy. Supply, and have a positive role in the realization of the economic benefits of power plants. Therefore, during the electrical operation of the power plant, it is necessary to be able to quickly detect the occurrence of electrical faults and take appropriate measures in time to reduce the accident losses. Therefore, this paper combines the deep learning model and the multimedia to propose the novel systematic framework. Our future research will be focused on the implementation of the system.
Change history
20 September 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s11042-022-13980-z
References
Abbas NI, Ilkan M, Ozen E (2015) Fuzzy approach to improving route stability of the AODV routing protocol. EURASIP J Wirel Commun Netw 2015(1):235
Akram M, Umair M, Iqbal A (2017) Failure analysis of fire resistant fluid (FRF) piping used in hydraulic control system at oil-fired thermal power generation plant. Case Studies in Engineering Failure Analysis 8:21–27
Berrhazi S, Ahmed O, Benchrifa R, Zejli D (2017) Optimal design with materials selection for thermal energy storages in high temperature concentrating solar power. IET Renew Power Gen 12(1):37–44
Boru D, Kliazovich D, Granelli F, Bouvry P, Zomaya AY (2015) Energy-efficient data replication in cloud computing datacenters. Clust Comput 18(1):385–402
Bottrell N, Lang P, Green T (2017) Algorithm for soft open points to solve thermal and voltage constraints in low-voltage distribution networks. CIRED-Open Access Proceedings Journal 2017(1):1567–1570
Chakraborty S, Singh SK, Chakraborty P (2017) Local directional gradient pattern: a local descriptor for face recognition. Multimed Tools Appl 76(1):1201–1216
Chen H, Kang JN, Liao H, Tang BJ, Wei YM (2017) Costs and potentials of energy conservation in China’s coal-fired power industry: a bottom-up approach considering price uncertainties. Energy Policy 104:23–32
Chen Q, Zhang G, Yang X et al (2017) Multimed Tools Appl. https://doi.org/10.1007/s11042-017-5299-0
Conrado LS, Rodriguez-Pulido A, Calderón G (2017) Thermal performance of parabolic trough solar collectors. Renew Sust Energ Rev 67:1345–1359
Delavar AG, Aryan Y (2014) HSGA: a hybrid heuristic algorithm for workflow scheduling in cloud systems. Clust Comput 17(1):129–137
Fateh MF, Zameer A, Mirza NM, Mirza SM, Raja MAZ (2017) Biologically inspired computing framework for solving two-point boundary value problems using differential evolution. Neural Comput Applic 28(8):2165–2179
Feng Y, Wang GG, Deb S, Lu M, Zhao XJ (2017) Solving 0–1 knapsack problem by a novel binary monarch butterfly optimization. Neural Comput Applic 28(7):1619–1634
González-Roubaud E, Pérez-Osorio D, Prieto C (2017) Review of commercial thermal energy storage in concentrated solar power plants: steam vs. molten salts. Renew Sust Energ Rev 80:133–148
Huang Z, Siniscalchi SM, Lee CH (2017) Hierarchical Bayesian combination of plug-in maximum a posteriori decoders in deep neural networks-based speech recognition and speaker adaptation. Pattern Recogn Lett 98:1–7
Javed K, Gouriveau R, Zerhouni N (2015) A new multivariate approach for prognostics based on extreme learning machine and fuzzy clustering. IEEE T Cybernetics 45(12):2626–2639
Jiao J, Venkat K, Han Y, Weissman T (2015) Minimax estimation of functionals of discrete distributions. IEEE Trans Inf Theory 61(5):2835–2885
Khankari G, Karmakar S (2017) 4-E analysis of a Kalina cycle system 11 integrated 500MWe combined thermal power plant. In Region 10 Conference, TENCON 2017–2017 IEEE (pp 93–98). IEEE
Kumaresan G, Sudhakar P, Santosh R, Velraj R (2017) Experimental and numerical studies of thermal performance enhancement in the receiver part of solar parabolic trough collectors. Renew Sust Energ Rev 77:1363–1374
Lawan SM, Abidin WAWZ, Masri T, Chai WY, Baharun A (2017) Wind power generation via ground wind station and topographical feedforward neural network (T-FFNN) model for small-scale applications. J Clean Prod 143:1246–1259
Li Z, Dey N, Ashour AS, Cao L, Wang Y, Wang D, McCauley P, Balas VE, Shi K, Shi F (2017) Convolutional neural network based clustering and manifold learning method for diabetic plantar pressure imaging dataset. J Med Imaging Health Inform 7(3):639–652
Liu L, Hejazi M, Li H, Forman B, Zhang X (2017) Vulnerability of US thermoelectric power generation to climate change when incorporating state-level environmental regulations. Nat Energy 2(8):17109
Liu M, Shi J, Li Z, Li C, Zhu J, Liu S (2017) Towards better analysis of deep convolutional neural networks. IEEE Trans Vis Comput Graph 23(1):91–100
Lu T, Guan Y, Zhang Y, Qu S, Xiong Z (2018) Robust and efficient face recognition via low-rank supported extreme learning machine. Multimed Tools Appl 77(9):11219–11240
Mansouri I, Gholampour A, Kisi O, Ozbakkaloglu T (2018) Evaluation of peak and residual conditions of actively confined concrete using neuro-fuzzy and neural computing techniques. Neural Comput Applic 29(3):873–888
Meng L, Li J, Li Q (2017) A miniaturized power generation system cascade utilizing thermal energy of a micro-combustor: design and modelling. Int J Hydrog Energy 42(27):17275–17283
Miyake M, Iwami M, Goto K, Iwamoto K, Morimoto K, Shiraishi M, Takatori K, Takeuchi M, Nishimoto S, Kameshima Y (2017) Intermediate-temperature solid oxide fuel cell employing reformed effective biogas: power generation and inhibition of carbon deposition. J Power Sources 340:319–324
Oh SY, Chung KY (2014) Target speech feature extraction using non-parametric correlation coefficient. Clust Comput 17(3):893–899
Olatomiwa L, Mekhilef S, Shamshirband S, Petković D (2015) Adaptive neuro-fuzzy approach for solar radiation prediction in Nigeria. Renew Sust Energ Rev 51:1784–1791
Ouaarab A, Ahiod B, Yang XS (2014) Discrete cuckoo search algorithm for the travelling salesman problem. Neural Comput Applic 24(7–8):1659–1669
Pang M, Zhang L, Liang S, Liu G, Wang C, Hao Y, Wang Y, Xu M (2017) Trade-off between carbon reduction benefits and ecological costs of biomass-based power plants with carbon capture and storage (CCS) in China. J Clean Prod 144:279–286
Pathak N, Bhatti TS, Verma A, Nasiruddin I (2018) AGC of two area power system based on different power output control strategies of thermal power generation. IEEE Trans Power Syst 33(2):2040–2052
Pettinau A, Ferrara F, Tola V, Cau G (2017) Techno-economic comparison between different technologies for CO2-free power generation from coal. Appl Energy 193:426–439
Raju M, Saikia LC, Sinha N, Saha A (2017) AGC of multi-area ST—thermal—hydro system incorporating redox flow batteries. In: Power and Advanced Computing Technologies (i-PACT), 2017 Innovations in (pp 1–6). IEEE
Saba T, Rehman A, Altameem A, Uddin M (2014) Annotated comparisons of proposed preprocessing techniques for script recognition. Neural Comput Applic 25(6):1337–1347
Saini P, Patil DV, Powar S (2018) Review on integration of solar air heaters with thermal energy storage. In: Applications of solar energy (pp 163–186). Springer, Singapore
Siar H, Kiani K, Chronopoulos AT (2015) An effective game theoretic static load balancing applied to distributed computing. Clust Comput 18(4):1609–1623
Singh N, Arya R, Agrawal RK (2017) A novel position prior using fusion of rule of thirds and image center for salient object detection. Multimed Tools Appl 76(8):10521–10538
Sun C, Wang Z, Liu S, Jiang X, Sheng G, Liu T (2017) Research on operation strategy for bundled wind-thermal generation power systems based on two-stage optimization model. In: IOP conference series: materials science and engineering (Vol. 199, No. 1, p 012058). IOP Publishing
Sundar LS, Sharma KV, Singh MK, Sousa ACM (2017) Hybrid nanofluids preparation, thermal properties, heat transfer and friction factor–a review. Renew Sust Energ Rev 68:185–198
Valencia F, Collado J, Sáez D, Marín LG (2016) Robust energy management system for a microgrid based on a fuzzy prediction interval model. IEEE T Smart Grid 7(3):1486–1494
Wang X, Lu L, Shin HC, Kim L, Bagheri M, Nogues I, Yao J, Summers RM (2017) Unsupervised joint mining of deep features and image labels for large-scale radiology image categorization and scene recognition. In: Applications of Computer Vision (WACV), 2017 IEEE Winter Conference on (pp 998–1007). IEEE
Wu S, Zhong S, Liu Y (2018) Deep residual learning for image steganalysis. Multimed Tools Appl 77(9):10437–10453
Wulandhari LA, Wibowo A, Desa MI (2015) Condition diagnosis of multiple bearings using adaptive operator probabilities in genetic algorithms and back propagation neural networks. Neural Comput Applic 26(1):57–65
Zhang S, Wang H, Huang W (2017) Two-stage plant species recognition by local mean clustering and weighted sparse representation classification. Clust Comput 20(2):1517–1525
Zhang S, Wang H, Huang W, You Z (2018) Plant diseased leaf segmentation and recognition by fusion of superpixel, K-means and PHOG. Optik-International Journal for Light and Electron Optics 157:866–872
Zhao BC, Cheng MS, Liu C, Dai ZM (2017) Cyclic thermal characterization of a molten-salt packed-bed thermal energy storage for concentrating solar power. Appl Energy 195:761–773
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
About this article
Cite this article
Chen, F., Fu, Z. & Zhen, L. RETRACTED ARTICLE: Thermal power generation fault diagnosis and prediction model based on deep learning and multimedia systems. Multimed Tools Appl 78, 4673–4692 (2019). https://doi.org/10.1007/s11042-018-6601-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6601-5