Abstract
In this paper, an improved wavelet based medical image watermarking algorithm is proposed. Initially, the proposed technique decomposes the cover medical image into ROI and NROI regions and embedding three different watermarks into the non-region of interest (NROI) part of the transformed DWT cover image for compact and secure medical data transmission in E-health environment. In addition, the method addressing the problem of channel noise distortion may lead to faulty watermark by applying error correcting codes (ECCs) before embedding them into the cover image. Further, the bit error rates (BER) performance of the proposed method is determined for different kind of attacks including ‘Checkmark’ attacks. Experimental results indicate that the Turbo code performs better than BCH (Bose-Chaudhuri-Hochquenghem) error correction code. Furthermore, the experimental results validate the effectiveness of the proposed framework in terms of BER and embedding capacity compared to other state-of-the-art methods. Therefore, the proposed method finds potential application in prevention of patient identity theft in e-health applications.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The development and implementation of newer e-health models demands secure medical data transmission, access and storage [9, 12, 14, 20, 23]. Recently, implementing tele-medicine solutions has become a great potential amongst the various research community at globally [6]. This refers to the use of modern information and communication technologies to meet the needs of citizens, patients, healthcare professionals and providers as well as policy makers [19]. However, maintaining medical confidentiality, preventing unauthorized access and integrity control are still open research challenges in the implementation of secure e-health/tele-medicine solutions [1, 5, 6, 12, 14, 19, 20, 23]. Further, the medical identity theft is an immediate concern and this criminal act has been reported in various surveys [3, 17]. Various noted researcher are addressing these potential issues by medical data/image watermarking schemes. The potential advantages of watermarking techniques for e-health applications are save bandwidth, maintained the confidentiality of medical as well as patient data, fast retrieval of medical information and provide protection against tempering [1, 5, 6, 14, 20, 23]. Other potential application for the watermarking are digital forensic, military, cyber-physical systems, fingerprinting, secure e-voting and different ID cards, remote education, media file archiving, information security solutions in smart cities, broadcast monitoring, real time audio/video and robotics [15, 16, 22, 26]
Researchers are using wavelet based watermarking in recent time to achieve the greater robustness. In addition, wavelets offer space frequency localization, multi-resolution representation, multi-scale analysis and compatible with the JPEG 2000 image standards [22, 23, 26]. The medical/digital image consists of region of interest (ROI) and non-region of interest (NROI) [18, 21,22,23]. The ROI area of an image contains the useful information and this area cannot be allowed to be modified. However, NROI is an area of image which presents the background information of the image. Researchers have concluded that the proper selection of the NROI area of an image for watermarking is crucial for medical images where the area under concern has to be the least required portion conveying any information [18]. It will give better protection if the data is embedded in NROI region of an image [18, 22].
Some recent and relevant wavelet based watermarking techniques are discussed below:
In [23], the authors have proposed a DWT, DCT and SVD based multiple watermarking technique is proposed for medical applications. Further, encryption is applied on electronic patient record (s) (EPR) watermark before embedding into the medical cover image. The authors investigated that the technique is robust for different kind of attacks including checkmark attacks. However, the method can embed only ‘50’ characters of text watermark data.
Pandey et al. [18] proposed a multiple watermarking using fusion of DWT and SVD. Four different watermarks in the form of signature, index, caption and reference are embedding into the NROI part of the cover image simultaneously. Further, SHA-512 encryption method is applied to enhance the security of the medical watermarking method. Simulation results demonstrated that the method is robust for Checkmark and other attacks. However, the method has not addressed the false positive detection problem which is very common in SVD based schemes. An ECC based text watermarking technique using DWT is proposed by Terzija et al. [27]. The experimental results show that the Reed-Solomon code offers better error correction performance than Hamming and BCH code. However, the considered ECCs is not able to handle bit error rates (BER) greater than 10–20%.
In [24], a DWT based robust and secure digital watermarking method using spread-spectrum technique is presented. The method embeds medical text information into selected DWT coefficients of the cover medical image. In addition, BCH error correcting code is applied to the ASCII representation of the text watermark and encoded text watermark is finally embedded into the cover medical image. The experimental results show that the method is robust for different known attacks. The method can embed only ‘381’ bits information only and offer better peak signal to noise ratio (PSNR) and BER performance than the method proposed in [10]. However, these methods have very limited watermarking capacity as each bit of the text watermark is represented by a pair of Pseudo-Noise (PN) sequences of the sizes identical to column vectors lengths of different embeddable DWT coefficient sub-band matrices. The method proposed in [7] embedded multiple watermarks and enhanced the robustness by quantized wavelet coefficients and BCH error correcting code. The experimental results show that the method is evaluated for different medical imaging modalities and JPEG compression attacks. Performance of this method against various other attacks such as filtering, sharpening, scaling etc. was not evaluated. Dhanalakshmi et al. [4] proposed a DWT-SVD based dual watermarking method using chaos encryption. Two different watermarks (primary and secondary) are embedded in the cover image. The secondary watermark is embedded into primary watermark before embedding into the cover and the watermarked image is encrypted by chaos based logistic map. Finally, the encrypted watermarked image is embedded in to cover image. Robustness of the method is tested for different known attacks. Hajjaji et al. [8] proposed a DWT based medical image watermarking method using K-L transform. The method determined the visibility factor using fuzzy inference system. A binary signature followed by the hospital centre is generated by secure hash algorithm (SHA)-1 hash function and the rest of patient data in a binary sequence concatenated with the binary signature. Further, robustness of the patient data is enhanced by using serial Turbo code. Singh et al. [25] presents encryption based multilevel text watermarking method using DWT and spread-spectrum. The watermark information first encrypted then it embedded into the selected sub-bands of the DWT coefficients. The method is robust for various kinds of attacks. Although encryption of the text watermarks adds very high level of security to the information but the capacity of watermark is very limited due to addition of long sequence of overhead bits. Muhammad et al. [21] presented a mobile-cloud assisted framework for selective encryption of medical images. A detection model is used to determine the ROI from medical image and this ROI is embedded within cover image. The watermarked image is outsourced to cloud for the encryption. Further, the cloud forwards the encrypted watermarked image to client where the encrypted data is decrypted and combined with NROI, forming a selectively encrypted medical image.
Potential issues of digital watermarking for health data management are medical confidentiality protection, patient and diagnostic information hiding, access and integrity control, maintaining high quality of cover medical/radiological image has been little explored. This paper attempts to simultaneously address potential issues of digital image watermarking relevant to health data management perspective:
-
(a)
Non region of interest (NROI) watermarking so as to protect the diagnostically important region of interest from any modification during information embedding
-
(b)
Robust embedding of ‘text watermark’ is much more challenging as compared to image watermark as error on any single bit is not acceptable.
-
(c)
Embedding of multiple watermarks with different degree of robustness and capacity requirements is a challenging task.
-
(d)
Use of Error Correcting Codes (ECCs) for enhancing the robustness of embedded text information is one of the better options. This paper tries to analyze the performance of powerful Turbo codes for achieving enhanced robustness.
Key based random selection of DWT coefficients belonging to NROI and their efficient quantization for embedding of multiple medical text watermarks incorporating all above mentioned issues is the main challenging task that has been carried in the proposed work. In this paper, the proposed method is using magnetic resonance imaging (MRI) image as cover image is decomposed in wavelet transform domain. The text watermark considered as the patient information is divided in three parts: signature, index and caption watermark, which are embedded in random DWT coefficients belonging to NROI. This is achieved by applying efficient quantization of embeddable selected discrete wavelet coefficients belonging to NROI. Security of the embedding is enhanced by random selection of DWT coefficients for embedding using a secret key. Additional protection of embedding medical data is provided through channel coding techniques. This paper applies BCH and Turbo error correcting codes for encoding the text watermark before embedding into the cover medical image. Out of these two ECCs, it is found that the Turbo code shows the better performance in terms of Bit error rates (BER).
The rest of the paper is organized as follows. The different watermark information is allocated in Section 2. Section 3 reported the proposed framework followed by watermark embedding and extraction algorithms. The experimental results and brief analysis of the work is reported in Section 4. Next, our conclusions and future directions of the work are presented in Section 5.
2 Allocation of watermark information
In this section, the proposed multilevel watermarking method is addressing health data management issues. According to importance of robustness requirements, three different text watermarks are allocated for different DWT sub-bands [7] as shown in Table 1.
-
(i)
Signature watermark: This is the smallest watermark (182 bits) among all. It contains doctor’s signature which is used for authentication purpose. It is embedded at third level (LL3) sub-band as it has highest energy so it will be less affected by any attack.
-
(ii)
Index watermark: This watermark of size ‘483’ bits provides an index for each type of disease. Further, it will reduce the amount of information for embedding. However, the index watermark is consumed more space than signature watermark (s). It will be embedded at second level (HL2) sub-band because horizontal detail coefficients have more energy than vertical and diagonal coefficients.
-
(iii)
Caption watermark: This watermark contains patient information. It provides details about patient’s personal information, testing results, hospital details, diagnostic report etc. Due to its long size, caption watermark will be embedded at first level (HL1) sub-band.
3 Proposed framework
The detail of proposed method is represented in section 3.1 and section 3.2 as embedding and extraction algorithm, respectively. The proposed multiple watermarks embedding scheme is based on efficient quantization of selected DWT coefficients belonging to NROI obtained through subband decomposition of image. The selected DWT coefficients are modified during embedding process. Real values obtained after applying inverse DWT must be rounded off to integer values in order to generate watermarked image. The rounding operation is an image modification which is undesired. This modification is prevented by selecting Haar wavelet as a mother wavelet which exploits the dyadic rationality of resulting coefficients, i.e. their denominators are power of 2 [11]. In the proposed scheme modification of DWT coefficients is done by adding or subtracting a multiple of 2l where ‘l’ represents embedding level. The new quantization procedure proposed in this paper assigns binary values to the selected embeddable coefficients. According to the algorithm, any DWT coefficient f selected to embed a watermark bit, is assigned a binary value through the following quantization function:
Where‘s’ is an offset value defined by user. ‘Sign’ is an odd mathematical function that extracts the sign of a real number.
3.1 Embedding algorithm for text watermark
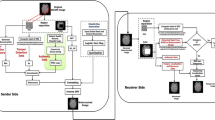
The embedding algorithm is proposed to implement text watermark in NROI part of the cover MRI image. Figure 1 shows the watermark embedding process. The steps for the embedding text watermark are as follows
-
1.
Read cover image of size M × N.
-
2.
Define seed points to select ROI and a key (K) which has following property:
-
3.
Transform image by applying third level subband decomposition and get DWT coefficients of different sub-bands.
-
4.
Read text watermarks and convert them into binary sequences.
-
5.
Apply error correcting codes to binary sequences of text watermarks.
-
6.
Select wavelet coefficients randomly of 3rd level approximation band (LL3), second level horizontal band (HL2) and first level horizontal band (HL1) for embedding encoded text watermarks, considering the value of K equal to 1.
-
7.
Quantize selected wavelet coefficients according to eq. (1).
-
8.
If quantized DWT coefficient has same value as encoded watermark bit then it remains same otherwise it is modified by eq. (3) and define an embedding key for those wavelet coefficients which are used for watermark embedding:
Here Δ is a parameter defined for each level. Its value is 2l where ‘l’ represents embedding level.
-
9.
Apply inverse DWT to generate watermarked image.
3.2 Extraction algorithm for text watermark
Extraction algorithm is a reverse process of embedding algorithm. Steps for watermark extraction are:
-
1.
Decompose watermarked image up to third level of subband decomposition using DWT.
-
2.
Use embedding key to select wavelet coefficients which are modified by embedding process.
-
3.
Extract binary sequenced watermark from these coefficients using eq. (1) and (3).
-
4.
Decode extracted watermark to generate original binary sequence.
-
5.
Convert generated binary sequence into character.
4 Experimental results and analysis
This section explains in detail the experiments conducted for the performance evaluation of the proposed framework. The magnetic resonance (MR) image of size 512 × 512 [13] and watermark of size 5145 bits are using as cover and text watermark respectively. For the experimental purposes, MATALB R2015a has been used. Figure 2 shows the (a) Cover image (b) Watermarked image (c) ROI part of the cover and (d) NROI part of the cover image. Figure 3 shows the extracted considered text watermarks (Signature, Index and Caption watermark). The metrics employed to evaluate the perceptual quality of the watermarked image, as well as the robustness of the extracted watermark, are: peak signal-to-noise ratio (PSNR) and bit error rate (BER) was utilized to determine the performance of the proposed framework. These performance metrics are defined as follows:
The visual quality of the watermarked (stego) image is measured by the parameter PSNR. It is defined as [15, 16]:
B max is the maximum pixel intensity among cover and stego images.
The BER is defined as the ratio of the number of incorrectly decoded bits and total number of bits [23]. This parameter is suitable for random binary sequence watermark. Ideally BER value should be equal to 0.
The BER performance of the proposed framework is determined for different kind of attacks including checkmark attacks. Further, the robustness of the watermark is enhanced by applying powerful error correcting codes such as BCH and Turbo codes [2] is applied to the ASCII representation of the text watermark before embedding in to the cover medical image. In addition, the effectiveness of the proposed framework in terms of BER is compared to other state-of-the-art methods [23, 25]. It is noticed that larger gain factor results in stronger robustness whereas smaller gain factor provides better visual quality of the watermarked medical images. Based on the experimental results as shown in Tables 2 and 4, the performance is greatly depends on gain, size of the watermarks and the noise variation.
The PSNR of watermarked image is 47.46 dB when BCH code is used and it slightly reduces to 45.23 dB. In both the cases PSNR is well above 35 dB which is the benchmark value for imperceptibility. In Table 2, performance of the proposed method is tested for compression attacks at different quality factors (QF). This table shows the comparative analysis of the BER performance as obtained by the two different error correcting codes. The Turbo code show better result than BCH (31, 16) code. In this table, the maximum BER value of 4.34 has been obtained by the proposed method for compression attacks (QF = 55) using BCH code. However, the maximum BER value is 0.2747 for the same attack using Turbo code. With Turbo code, all the BER values have been found ‘0’ except the compression attacks (QF = 55) which are 0.2747. The BER performance of the proposed method for Checkmark attacks is presented in Table 3. The results confirm that the maximum BER value of 11.08 has been obtained for Scaling (factor = 2) attacks using BCH code. However, the BER value is 4.17 for the same attack using Turbo code. With Turbo code, the maximum BER value is 5.97 for Rotation attacks. However, the BER value is 8.178 for the same attack using BCH code.
Table 4 shows the BER performance comparison of the proposed method with other reported techniques [23, 25]. Referring this table it is observed that the highest BER value has been obtained by the reported techniques [23, 25] is 0.96 and 0.4326 for JPEG (QF = 10) attack respectively. However, the highest BER value obtained with proposed method is 0.3214 for the same attack. The methods reported in [23, 25] can embeds only ‘50’ and ‘104’ characters respectively. However, the proposed method can embed ‘217’ characters. The results confirm that the robustness and embedding capacity of the proposed method is better than the other state-of-the-art techniques [23, 25] at acceptable quality of the watermarked image.
5 Conclusions and future directions
This paper proposed an efficient quantization based multiple watermarking technique in wavelet domain considering medical watermarks in the form of text. The suggested method used wavelet based watermarking where the encoded text watermarks were embedded into the NROI part of the DWT cover gray image. The BER performance of the developed scheme was tested for different attacks. The robustness of the three different text watermarks is enhanced by using BCH and Turbo error correcting codes. Out of the two ECCs, it was found that the Turbo code showed the better performance in terms of BER. In recent years, Turbo Codes are the one of the best error correction codes that has been rapidly adopted for application in various commercial transmissions systems. Researcher has been concluded that the performance of the turbo code is better than BCH and Hamming code. In this research, the gray scale images have been considered for the experimental purpose. However, the embedding capacity of color image is better than gray image. The robustness and imperceptibility performance of the watermarking method will greatly depends on the choice of color space and selection of embedding color channel. The quantization index modulation (QIM), directional wavelet transforms and neural networks are also a future consideration for integration with the proposed framework to make it more resilience against attacks and improve the performance of the work.
References
O M Al-Qershi and B E Khoo (2010) ROI–based tamper detection and recovery for medical images using reversible watermarking technique, in: IEEE International Conference on Information Theory and Information Security, Beijing pp. 151–155
MH Alwan, M Singh and HF Mahdi (2015) Performance comparison of turbo codes with LDPC codes and with BCH codes for forward error correcting codes, Kuala Lumpur, pp. 556–560
D Bowma (2012) http://www.fiercehealthit.com/story/researchers-use-digital-watermarks-protect- medical-images
Dhanalakshmi R, Thaiyalnayaki K (2010) Dual watermarking scheme with encryption. International Journal of Computer Science and Information Security 7:248–253
Eswaraiah R, Reddy ES (2015) Robust medical image watermarking technique for accurate detection of tampers inside region of interest and recovering original region of interest. IET Image Process 9(8):615–625
A Giakoumaki, K Perakis, A Tagaris, and D Koutsouris (2006) “Digital watermarking in telemedicine applications - towards enhanced data security and accessibility”, proceedings of the 28th IEEE EMBS annual international Conference new York City, USA
Giakoumaki A, Pavlopoulos S, Koutsouris D (2006) Secure and efficient health data management through multiple watermarking on medical images. Medical Biological Engineering & Computing 44:619–631
Hajjaji MA, El-Bay B, Abdelali AB, Mtibaa A (2014) Combining Haar wavelet and Karhunen Loeve transforms for medical images watermarking. Biomed res Int 2014:1–15
Katzenbeisser S, Petitcolas F (2000) Information hiding techniques for steganography and digital watermarking. Artech House, London
B Kumar, SB Kumar and DS Chauhan (2014) Wavelet based imperceptible medical image watermarking using spread-spectrum, 37th International Conference on telecommunications and signal processing, Berlin Germany, 660–664
Kundur D, Hatzinakos D (1999) Digital watermarking for telltale tamper proofing and authentication, proc. IEEE Special Issue on Identification and Protection of Multimedia Information 87(7):1167–1180
J Maˇsek, R Burget, J Karásek, V Uher, S Güney (2013) Evolutionary improved object detector for ultrasound images, 36th International Conference on Telecommunications and Signal processing Rome, Italy, pp. 586–590
MedPix™Medical Image Database available at http://rad.usuhs.mil/medpix/medpix.html
Mohanty SP (2000) Watermarking of digital images. M.S. thesis, Indian Institute of Science, India
Muhammad K, Sajjad M, Mehmood I, Rho S, Baik SW (2016) A novel magic LSB substitution method (M-LSB-SM) using multi-level encryption and achromatic component of an image. Multimed Tools Appl 75(22):14867–14893
Muhammad K, Ahmad J, Rehman NU, Jan Z, Sajjad M (2017) CISSKA-LSB: color image steganography using stego key-directed adaptive LSB substitution method. Multimed Tools Appl 76(6):8597–8626
M Ollove (2014) www.usatoday.com/story/.../stateline-identity- thefts-medical.../5279351
Pandey R, Singh AK, Kumar B, Mohan A (2016) Iris based secure NROI multiple eye image watermarking for Teleophthalmology. Multimed Tools Appl 75(22):14381–14397
A Pavelin, I Klapan, M Kovač, M Katić, R Stevanović, M Rakić and N Klapan, (2006) “A Functional Telemedicine Environment in the Framework of the Croatian Healthcare Information System”, 79–93, Volume 372: Remote Cardiology Consultations Using Advanced Medical Technology, ios press
Rocek A, Slavicek K, Dostal O, Javornik M (2016) A new approach to fully-reversible watermarking in medical imaging with breakthrough visibility. Biomedical Signal Processing and Control 29:44–52
Sajjad M, Muhammad K, Baik SW, Rho S, Jan Z, Yeo SS, Mehmood I (2016) Mobile-cloud assisted framework for selective encryption of medical images with steganography for resource-constrained devices. Multimed Tools Appl 76(3):3519–3536
Singh AK, Dave M, Mohan A (2014) Wavelet based image watermarking: futuristic concepts in information security. Proceedings of the National Academy of Sciences, India Section A: Physical Sciences 84(3):345–359
Singh AK, Dave M, Mohan A (2015) Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimed Tools Appl 75(14):8381–8401
Singh AK, Kumar B, Dave M and Mohan A (2015) Robust and imperceptible spread-Spectrum watermarking for telemedicine applications, proc. Natl. Acad. Sci., India, Sect a Phys Sci 85(2):295–301.
Singh AK, Dave M, Mohan A (2015) Multilevel encrypted text watermarking on medical images using spread-Spectrum in DWT domain. Wireless Personal Communications, 83(3):2133–2150
AK Singh, B Kumar, M Dave, SP Ghrera and Anand Mohan (2016) Digital image watermarking: techniques and emerging applications, handbook of research on modern cryptographic solutions for Computer and cyber security, IGI global, USA, pp. 246–272
N Terzija, M Repges, K Luck and W Geisselhardt (2002) Digital image watermarking using discrete wavelet transform: performance comparison of error correction codes, In: Proceedings of International Association of Science and Technology for Development (IASTED), pp. 1-5
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chauhan, D.S., Singh, A.K., Kumar, B. et al. Quantization based multiple medical information watermarking for secure e-health. Multimed Tools Appl 78, 3911–3923 (2019). https://doi.org/10.1007/s11042-017-4886-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4886-4