Abstract
This paper presents a new efficient embedding algorithm in the wavelet domain of digital images based on the diamond encoding (DE) scheme. Current discrete wavelet transform (DWT) steganography adds an unacceptable distortion to the images and is considered as an ineffective in terms of security. Applying the DE scheme to the current DWT steganographic methods solves the problems of these methods, and reduces the distortion added to the images, and thus improves the embedding efficiency. The proposed algorithm first converts the secret image into a sequence of base-5 digits. After that, the cover image is transformed into the DWT domain and segmented into 2 × 1 coefficient pairs. The DE scheme is used then to change at most one coefficient of each coefficient pair to embed the base-5 digits. Experimental results depict that the proposed algorithm is more efficient in embedding compared to other methods in terms of embedding payload and image quality. Moreover, the proposed algorithm is attacked by well-known steganalysis software. Results are showing that the proposed algorithm is secure against the powerful universal steganalyzer “ensemble classifier” and the histogram attack. The results also reveal that the proposed algorithm is robust against different image processing attacks such as compression, added noise, and cropping attacks.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Steganography maintains the existence of communication secret through the concealment of information within other information (image, text, audio, video, etc.) [2, 18]. A recent classification of steganography methods is specified by [23]. Digital image steganography refers to the practice of hiding secret messages into digital images with the intention of secret communication [4]. Incidents such as modification and forgery have reached significant extents, thus making digital security critical. Moreover, in certain scenarios, secret messages must be discreetly embedded in digital images to keep such information inconspicuous. This approach of discreetly embedding is taken by image steganography. Digital images act as mediums for the purpose of hiding secret messages as we can see today that millions of images passing through to the Internet and readily available online [12]. However, different factors are used to characterize the performance of an image steganographic method; the most important factors are imperceptibility and embedding payload [16]. Imperceptibility indicates difficulties confronted by the human visual system (HVS) in recognizing any difference between an original cover image and its stego-image (after embedding the secret message). Better imperceptibility means that the stego-image is of high quality [1] and the difference would be unnoticed. The size of the secret message being embedded in the image is known as the embedding payload. The image steganography system that possesses high payload is a preferable steganography.
Image steganography works in spatial and frequency domains. Spatial-domain image steganographic methods, such as least significant bit (LSB) [7] and diamond encoding (DE) [8], can embed large payload sizes [3, 15]. On the other hand, frequency-domain steganographic methods embed secret messages in the coefficients of cover images and satisfies the criteria of imperceptibility and robustness [9]; examples include DWT steganography [2, 17, 22] and discrete cosine transform steganography (DCT) [16, 21]. LSB steganography embeds secret message bits in the LSBs of the cover image pixels. It possesses a greater payload compared to other embedding methods. However, LSB steganography is ineffective in terms of information hiding security [15]. DE scheme relies on pixel pairs as embedding units and digits in base b are embedded in pixel pairs, where b = 2 k 2 + 2 k + 1, and k ≥ 1 is the embedding parameter. The DE scheme offers high embedding payload while preserving a very acceptable image quality. The DE scheme is exploited as an embedding method in the proposed algorithm.
Nag et al. [17] proposed a DWT hiding method that replaces three LSBs of wavelet coefficients in high-frequency sub-bands by three bits from the secret bit stream. However, embedding in the HH sub-band is not robust against attacks such as lossy compression [13]. Differently, in [25], rather than embedding the entire secret image, the authors decided to embed the most important parts of the secret image in the DWT coefficients of the approximation sub-band. The p MSBs of the secret image are embedded in p LSBs of the coefficients using the LSB substitution technique, where p > 4. While this technique reduces the number of DWT coefficients to be changed, the amount of distortion added to each coefficient is high. In a different manner, Hemalatha et al. [11] proposed a hiding method based on the DWT transform. In this method, rather than embedding the actual secret image in the cover image, the cover and secret images are decomposed into DWT sub-bands and the LL sub-bands of both images are divided into disjointed 2 × 2 blocks. Then, every block s i in the LL sub-band of the secret image is compared with all blocks c i of the LL sub-band of the cover image and the block c i that gives the lowest Root Mean Square Error (RMSE) is then saved. A key to holding all saved locations is then generated and embedded in the LSBs of the integer wavelet transform (IWT) coefficients of the cover image. A very similar work to Hemalatha et al.’s work has been recently proposed in [5], where only the LL sub-band of the secret image is embedded into the cover image. Pol [19] presented a DWT-based embedding method that hides secret messages by altering the DWT coefficients in the high-frequency sub-bands of the image. The k LSBs of the DWT coefficients, c ij , are replaced by k secret bits from the encoded payload using the equation: c’ ij = mod (c ij , 2 k) + k’, where k’ represents the decimal value of k.
The security of steganographic methods can be directly influenced by the number of modifications to the cover image. It is clear that current discrete wavelet transform (DWT) steganographic methods add an unacceptable distortion to the stego-images and are ineffective in terms of information-hiding security. This unacceptable distortion is added to the stego-images because these current methods modify more than one LSB in each coefficient to embed large secret data (large capacity). However, embedding large secret data by modifying more than one LSB in each coefficient leaves high differences between the cover image and the stego-image, subsequently, reducing the information-hiding security. Applying the DE scheme to the DWT steganography can reduce the distortion added to the stego-image and thus improve the embedding efficiency. This reduction in distortion is achieved because the DE scheme reduces the changed embedding locations in the cover image. Moreover, reducing the modified locations in the cover image can improve the embedding method security [15]. However, the current problems of the DE scheme, such as the unacceptable distortion added to the stego-images when preventing the overflow and underflow problems, must be solved in the DWT domain.
This paper proposes a new secure steganographic algorithm (called DE-DWT) to enhance the embedding performance in terms of imperceptibility and embedding payload. This algorithm uses the DE scheme to solve the problems of current DWT-base embedding methods. The proposed algorithm also improves the overflow/underflow strategy used in the plan of DE, thereby removing the unacceptable distortion added to the image. The rest of the paper is organized as follows: Section 2 briefly reviews the DE scheme that is used as the embedding process in the proposed algorithm. Section 3 presents the proposed algorithm. Experimental results and analysis are shown in Section 4. Section 5 presents the steganalysis of the proposed algorithm. Section 6 presents the robustness of the proposed algorithm. Section 7 gives the limitations of the proposed algorithm, and finally, Section 8 presents the conclusions.
2 Related work
This section reviews the DE scheme [8] that is exploited as the embedding method in the proposed DE-DWT algorithm. In DE scheme, neighboring pixel pairs (p, q) of the cover image are employed as embedding units where digits in base b are embedded, b = 2 k 2 + 2 k + 1, while k ≥ 1 is the embedding parameter. The DE scheme embeds secret digits by modifying the pixel pair values. This step modifies the difference value of each pixel pair. The maximum embedding payload is equal to (1/2)log2 b bit per pixel (bpp) because every pixel pairs of the stego-image carry log2 b bits. The smallest value of the embedding parameter k is determined using the following equation:
where M × N represents the size of the host image, and \( \left|S\right| \) represents the size of the secret data S. A neighborhood set φ(p, q) is defined according to Eq. (2) after calculating the embedding parameter k. The diamond characteristic value (DCV) for each pixel pair (a, b) in φ(p, q) is computed using Eq. (3).
The neighborhood set φ(p, q) has two essential features. First, no two DCV values are the same. Second, the DCV value of any pixel pair (a, b) is a member of the neighborhood set φ(p, q) and belongs to {0, 1, 2, …, b − 1}. The DCV values of the set φ(p, q) are investigated when embedding secret digit \( {s}_b \) in base b into a pixel pair (p, q) to locate coordinates (p’, q’), such that DCV(p’, q’) = \( {s}_b \). The pixel pair (p, q) is then substituted by (p’, q’). To overcome the overflow/underflow problem that can occur, the DE scheme changes p ' to p ' ' and q ' to q ' ' using Eqs. (4) and (5):
In extracting the secret digit \( {s}_b \) embedded in the pixel pair (p’, q’), the DCV of (p’, q’) is calculated; then \( {s}_b \) is calculated using \( {s}_b \) = DCV(p’, q’). The DE scheme ensures that the distortion occurred due to embedding \( {s}_b \) in the pixel pair (p, q) does not exceed k. A simple example is used to illustrate how the DE scheme works. Suppose that k = 3 and a pixel pair (p, q) = (13, 20) is used to embed a digit \( {6}_{25} \) in base 25. Fig. 1 shows the neighborhood set φ(13, 20). Given that DCV(12, 22) = 6 In φ(13, 20), the pixel pair (13, 20) is substituted with (12, 22). To extract the embedded digit, the DCV of (12, 22) is calculated to obtain 625. Thus, the embedded secret digit is 625.
Although the DE scheme can embed large payload sizes [15], larger distortion is added to the stego-image when the embedding parameter k is large. Therefore, the embedding method can be detected by the steganalysis software.
3 Proposed work
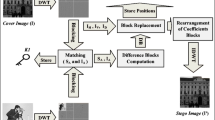
In this section, a new algorithm (called DE-DWT) that exploits the DE scheme to improve the embedding efficiency of DWT-based image steganography is presented. The proposed DE-DWT algorithm embeds secret images into coefficient pairs of cover images by adjusting the values of these coefficient pairs. The proposed algorithm reduces the distortion added to the stego-image, and thus improve the embedding efficiency, by adopting the DE scheme. This reduction in distortion is achieved because the DE scheme reduces the changed embedding locations in the cover image. Accordingly, the value of at most one coefficient of any cover image coefficient pair is changed during the embedding process. Moreover, reducing the modified locations in the cover image can improve the embedding method security. The major components of DE-DWT are expressed graphically in Fig. 2. As shown in this figure, the major components are fragmented into two main phases: the embedding and extraction phases. The embedding phase embeds the secret image into the DWT coefficients of the cover image to produce the stego-image, whereas the extraction phase is used later to extract the embedded image from the stego-image.
During the embedding phase, the proposed DE-DWT algorithm converts the secret bits into a sequence of base-5 digits (shown as B5D in Fig. 2). Then, the cover image is transformed into the DWT domain to produce DWT sub-bands. After that, each sub-band used in the embedding is divided into non-overlapping coefficient pairs. Subsequently, the converted digits (B5D) are embedded into the coefficient pairs using DE scheme. Finally, the inverse DWT is applied to obtain the stego-image. The stego-image is transmitted to the receiver to extract the embedded secret bits.
The extraction phase extracts the secret image from the DWT coefficients of the stego-image. Once the receiver receives the stego-image, the stego-image is transformed into the DWT domain to produce DWT sub-bands. Then, each sub-band used in the embedding is divided into non-overlapping coefficient pairs. An embedded sequence of digits is then extracted from the coefficient pairs. Finally, the extracted sequence of digits is converted into pixel values to generate the secret image. The details of the proposed method is presented in the remaining parts of this section.
3.1 Converting the secret image into base-5 digits
As mentioned previously, the DE scheme embeds digits in base b, b = 2 k 2 + 2 k + 1, and k ≥ 1. For example, when k = 1, the base b = 5. The proposed algorithm converts the secret image into a sequence of base-5 digits (shown as B5D in Fig. 2). The secret image is scanned from left to right and top to bottom. Each pixel value of the scrambled image is converted into four base-5 digits since the largest pixel value, that is (255)10, has the value (2010)5 which consists of 4 digits. After the process of base-5 conversion completes, the resulting sequence of digits (B5D) is embedded into the coefficient pairs of the sub-bands using the DE scheme. The DE-DWT algorithm can increase the embedding payload by embedding digits using the DE scheme with larger bases such as digits in base-13 or base-25 instead of digits in base-5. However, as any DWT-based embedding method, any simple modification in the coefficient values of the stego-image, due to an attack, can lead to extract digits which have values different from the embedded digits and hence an error in extracting the embedded digits occurs. Therefore, to put the extraction error at a minimum, the smallest DE embedding parameter (i.e. k = 1) is used in the embedding. That is, the scrambled image is converted into base-5 digits.
3.2 DWT transforming of cover image
The DE-DWT algorithm transforms the cover image from the spatial domain into the DWT domain using the Haar-DWT. Upon applying the Haar-DWT on a cover image, the cover image is decomposed into LL, LH, HL, and HH sub-bands [6]. For a grayscale image of size N × N, each sub-band has N/2 × N/2 coefficients. The coefficients of the sub-bands are used to embed the secret image. However, embedding in the HH sub-band is unsuitable because attacks, such as lossy compression, can easily eliminate this sub-band [13]. Thus, the DE-DWT algorithm uses only the LL, HL, and LH sub-bands in the embedding process.
After the cover image is transformed into the DWT domain to produce the DWT sub-bands, the produced LL, HL, and LH sub-bands are scanned from left to right and top to bottom then divided into 2 × 1 non-overlapping blocks of coefficient pairs (\( {c}_i,\;{c}_{i+1} \)). After segmentation, three random seeds \( {r}_1 \), \( {r}_2 \), and \( {r}_3 \) are used to randomly generate three sequences of embedding places in the LL, HL, and LH sub-bands, respectively. The resulting embedding places are used to conceal the sequence of base-5 digits (B5D).
3.3 Adopting the DE scheme
The sequence of base-5 digits (B5D) that was generated in Section 3.1 is here embedded into the coefficient pairs of the sub-bands using the DE scheme. The coefficient pairs are selected based on the randomly generated embedding places in the previous step. Also, the sequence of the sub-bands used in embedding is as follows: LL sub-band, HL sub-band, and then LH sub-band.
During the embedding of the sequence B5D into the coefficient pairs, the DE scheme is used to embed each digit d i of B5D into a coefficient pair (\( {c}_i,\;{c}_{i+1} \)) to obtain a new coefficient pair (\( c{'}_i,\;c{'}_{i+1} \)). By adopting the DE scheme, the embedding of each digit d i of B5D happens by changing the value of at most one coefficient of each coefficient pair used in the embedding process. In the DE-DWT algorithm, only the integer elements of the coefficients carry the secret digits, whereas the precision of the coefficients (i.e. the fraction parts) is left intact. Moreover, for better extraction of the embedded secret image, the 2nd LSBs of the coefficients are selected to embed the digits of B5D instead of the 1st LSBs. The embedding process happens as follows:
Since the embedding occurs in the 2nd LSBs of the DWT coefficients, then for each secret digit, d i , in the base-5 sequence (B5D), the values v i and v i + 1 for each coefficient pair (\( {c}_i,\;{c}_{i+1} \)) are computed using Eqs. 6 and 7:
The DE scheme is used then to embed the secret digit, d i , into (\( {c}_i,\;{c}_{i+1} \)) based on the values v i and v i+1. A neighborhood set φ(\( {c}_i,\;{c}_{i+1} \)) is defined according to Eq. (8). Then, for each pair (a, b) in φ(\( {c}_i,\;{c}_{i+1} \)), the diamond characteristic value (DCV) is computed using Eq. (9).
To embed the secret digit d i , one pair (a 1 , b 1 ) of the neighborhood set φ(\( {c}_i,\;{c}_{i+1} \)) replaces the pair (v i , v i+1). The new coefficient pair (\( c{'}_i,\;c{'}_{i+1} \)) is then obtained by computing Eqs. 10 and 11:
If c’ i or c’ i+1 is out of the range [c l , c h ], which is the range of the lowest and the largest coefficient values in the current sub-band, then an overflow/underflow problem occurs. Applying the same overflow/underflow strategy used in the DE scheme adds an unacceptable distortion to the stego-image. The reason can be explained as follows: if the embedding of a secret digit \( {s}_5 \) into a coefficient pair (\( {c}_i,\;{c}_{i+1} \)) results in an overflow/underflow problem, then a coefficient value exceeding c l or c h is added (if the coefficient value is less than c l ) or subtracted (if the coefficient value is greater than c h ) by 5 to remain the coefficient value within the range [c l , c h ]. This modification increases the embedding distortion added to the stego-image by an unacceptable amount. To reduce such distortion, the DE-DWT algorithm applies an improved overflow/underflow strategy to obtain an alternative coefficient pair (\( c{"}_i,\;c{"}_{i+1} \)) to replace (\( c{'}_i,\;c{'}_{i+1} \)). This happens by identifying an alternative pair (a’ 1 , b’ 1 ) from the coefficient pairs surrounding (v i , v i+1) to substitute the pair (a 1 , b 1 ). As shown in Eq. (9), the alternative coefficient pair (\( c{"}_i,\;c{"}_{i+1} \)) satisfies the condition DCV (a’ 1 , b’ 1 ) = d i , and \( c{"}_i \) and \( c{"}_{i+1} \) ∈ [c l , c h ].
For illustration, assume that the range of the lowest and the largest coefficient values [c l , c h ] in the current sub-band is [54, 476]. Suppose the coefficient pair (\( {c}_i,\;{c}_{i+1} \)) = (451, 476) is used to embed the digit d i = (4)5. Eqs. 6 and 7 are used to calculate the pair (\( {v}_i \), \( {v}_{i+1} \)) = (225, 238). Fig. 3 shows the neighborhood set φ(451, 476). Since in φ(451, 476), the DCV of (225, 239) is equal to 4, the pair (\( {v}_i \), \( {v}_{i+1} \)) = (225, 238) is substituted with the pair (a 1 , b 1 ) = (225, 239). Equations 10 and 11 are used to obtain the coefficient pair (\( c{'}_i,\;c{'}_{i+1} \)) = (451, 478). However, since the value 478 is out of the range [54, 476], an alternative coefficient pair is obtained to replace (451, 478). As shown in Fig. 3, the pair (a’ 1 , b’ 1 ) = (224, 237) has n224, 237) = 4. The Eqs. 10 and 11 are used again to obtain the coefficient pair (\( c{"}_i,\;c{"}_{i+1} \)) = (449, 474). The coefficient pair (\( c{"}_i,\;c{"}_{i+1} \)) = (449, 474) satisfies the condition DCV (a’ 1 , b’ 1 ) = 4, and \( c{"}_i \) and \( c{"}_{i+1} \) ∈ [c l , c h ] = [54, 476]. Thus the coefficient pair (451, 476) is replaced by (449, 474). The embedding process continues for all secret digits in the sequence B5D.
3.4 Embedding secret image
Let C be a grayscale image of size M × N, and S be a secret image of size m × n. The embedding steps are given below.
-
Input: Cover image C of size M × N, secret image S of size m × n, and random seeds \( {r}_1 \), \( {r}_2 \), and \( {r}_3 \).
-
Output: Stego-image C’.
-
Step 1:
Convert the pixels of the secret image S into a sequence of base-5 digits B5D. Each pixel in S is represented by four base-5 digits in B5D.
-
Step 2:
Use the Haar-DWT to transform a cover image C from its spatial domain into the DWT domain. Use the LL, HL, and LH sub-bands in the embedding process.
-
Step 3:
Based on the size of the sequence B5D, scan the sub-bands LL, HL, and LH from left to right and top to bottom, divide them into 2 × 1 non-overlapping blocks of coefficient pairs (\( {c}_i,\;{c}_{i+1} \)). Use random seeds of \( {r}_1 \), \( {r}_2 \), and \( {r}_3 \), to randomly generate three sequences of embedding places in the LL, HL, and LH sub-bands, respectively.
-
Step 4:
For each digit, d i , in the base-5 sequence B5D, use Eqs. 6 and 7 to obtain the values \( {v}_i \) and \( {v}_{i+1} \) from a coefficient pair (\( {c}_i,\;{c}_{i+1} \)).
-
Step 5:
Use the DE scheme to embed each digit, d i , into (\( {c}_i,\;{c}_{i+1} \)) based on the values v i and v i+1. Obtain the new coefficient pair (c ’ i , c ’ i + 1) by using Eqs. 10 and 11.
-
Step 6:
If \( c{'}_i \) or \( c{'}_{i+1} \) are out of the range of the lowest and the largest coefficient values [c l , c h ] in the current sub-band, then an alternative coefficient pair (\( c{"}_i,\;c{"}_{i+1} \)) is obtained to replace (\( c{'}_i,\;c{'}_{i+1} \)) as explained in section 3.3.
-
Step 7:
Apply the inverse Haar-DWT (IDWT) to obtain the stego-image C’.
Notably, the 2nd LSB with only one coefficient in each coefficient pair (\( {c}_i,{c}_{i+1} \)) is changed by at most one to embed each digit d i .
3.5 Retrieving secret image
Once the stego-image C’ and the embedding parameters such as the size of the secret sequence B5D, and the random seeds \( {r}_1 \), \( {r}_2 \), and \( {r}_3 \) are obtained; the secret image can be readily extracted from C’. The extraction steps are listed as follows:
-
Input: A stego-image C’, |B5D|: size of the secret sequence B5D, and random seeds \( {r}_1 \), \( {r}_2 \), and \( {r}_3 \).
-
Output: Secret image S.
-
Step 1:
Use the Haar-DWT to transform the stego-image C’ from its spatial domain into the DWT domain and obtain the LL, HL, and LH sub-bands.
-
Step 2:
Based on the size of the sequence B5D, scan the sub-bands LL, HL, and LH from left to right and top to bottom, divide them into 2 × 1 non-overlapping blocks of coefficient pairs (\( {c}_i,\;{c}_{i+1} \)). Use the random seeds \( {r}_1 \), \( {r}_2 \), and \( {r}_3 \), to generate the same sequences of embedding places in the LL, HL, and LH sub-bands, respectively, which was generated during the embedding phase. Use the same sequence of the sub-bands used in the embedding phase (i.e. LL, HL, and then LH)
-
Step 3:
Use Eqs. 6 and 7 to obtain the values \( {v}_i \) and \( {v}_{i+1} \) from each coefficient pair (\( {c}_i,\;{c}_{i+1} \)) employed in the embedding.
-
Step 4:
Use the DE scheme and the values \( {v}_i \) and \( {v}_{i+1} \) to extract the embedded base-5 digit, d i , from each coefficient pair (\( {c}_i,\;{c}_{i+1} \)) used in the embedding. The sequence B5D is obtained.
-
Step 5:
Obtain the pixels of the secret image S by converting each 4 base-5 digits of the sequence B5D into one pixel value. The original cover image is evidently not required for extracting the secret image.
3.6 Example
A simple example that shows how the DE-DWT algorithm works is provided as follows. Assume that the pixel value to be embedded is (22)10. Suppose that the LL sub-band of the cover image C is composed of four coefficients (i.e. 224, 220, 152, and 181). The to-be-embedded pixel is converted into its base-5 equivalent value of (42)5 (the sequence B5D) and the LL sub-band is divided into two coefficient pairs, namely, (224, 220) and (152, 181). Assume the embedding occurs in the first coefficient pair before the second coefficient pair. For the first coefficient pair (224, 220), the values \( {v}_i \) and \( {v}_{i+1} \) are calculated for 224 and 220 using Eqs. 6 and 7. Given that (224)10 = (11100000)2, the value \( {v}_i \) = (1110000)2 = (112)10. Similarly, given that (220)10 = (11011100)2, the value \( {v}_{i+1} \) = (1101110)2 = (110)10. Using the DE scheme, the two values (i.e. 112 and 110) are used to embed the first secret digit d 1 = (4)5 to obtain the new values 113 and 110. Equations 10 and 11 are used after that to obtain (226, 220). For the second coefficient pair (152, 181) and the secret digit d 2 = (2)5, the value \( {v}_i \) = (1001100)2 = (76)10, whereas the value \( {v}_{i+1} \) = (1011010)2 = (90)10. The values 76 and 90 are now used by the DE scheme to embed d 2 = (2)5 and obtain the values 76 and 89. Equations 10 and 11 are used again to obtain (152, 179). The coefficient pairs (224, 220) and (152, 280) are now modified to (226, 220) and (152, 179), respectively.
During the extraction phase, with the knowledge of the size of the secret sequence B5D, the embedded information can be readily extracted from the LL sub-band of the stego-image C’. The LL sub-band is divided into two coefficient pairs (226, 220) and (152, 179). For the first coefficient pair (226, 220), the values v i and v i + 1 are obtained using Eqs. 6 and 7. This gives the values \( {v}_i \) = 113 and \( {v}_{i+1} \) =110. The DE scheme is then used to extract the secret digit (4)5 using Eq. (9) based on the values \( {v}_i \) and \( {v}_{i+1} \). Similarly, the values \( {v}_i \) and \( {v}_{i+1} \) are obtained for the second coefficient pair (152, 179). This gives the values \( {v}_i \) = 76 and \( {v}_{i+1} \) = 89. The DE scheme is used again to extract the secret digit (2)5. Converting d = (42)5 into a decimal integer yields the pixel value of (22)10.
4 Experimental results and analysis
Four well-known benchmark images in the image-based steganography field were used to evaluate the performance of the proposed DE-DWT algorithm. Other four non-benchmark images were also used for conducting the experiments. The benchmark images were downloaded from the SIPI [24] and CVG [10] databases; the non-benchmark images were selected from the RSP database [20], which contains 1,000 images and includes indoor and outdoor scenes. All test images are 2D grayscale images sized 512 × 512. For conducting all the experiments, two secret images (Fig. 4) were used to evaluate the efficiency of the proposed DE-DWT algorithm. A random secret message was also generated by a PRNG to show that the DE-DWT algorithm does apply to any secret message and yields similar quality results. The quality of stego-images is measured by computing the peak signal-to-noise-ratio (PSNR) and the structural similarity index metric (SSIM). In addition, the payload and image quality comparisons for the DE-DWT algorithm and other techniques were included in the experiments. Results are presented in the following subsections.
4.1 Comparison of payload and image quality
This subsection tests the payload and image quality of the resulting stego-images produced by the DE-DWT algorithm. All test images previously mentioned were used in these experiments as well. The secret images “Logo” and “Fingerprint” at two payload sizes (i.e. 64 × 128 and 128 × 128) were used to evaluate the efficiency of the proposed DE-DWT algorithm. Random secret message of sizes 65,536 and 131,072 were also used to demonstrate that the DE-DWT algorithm applies to any secret message and yields similar quality results. Accordingly, the collected results for the used images varied slightly, and the differences among images were negligible. Thus, the effectiveness of the DE-DWT algorithm is not influenced by the number of images used. The results are reported in Tables 1 and 2.
Table 1 and Table 2 reveal that the DE-DWT algorithm produces stego-images with highly acceptable qualities under different payloads. For example, in Table 1, when the payload was 65,536 bits, the averaged PSNR values were all equal to 52.11 dB using the secret messages “Logo”, “Fingerprint”, and the randomly selected message. Similarly, when the payload was 131,072 bits, the averaged PSNR values were 49.12, 49.15, and 49.11 dB using the secret messages “Logo”, “Fingerprint,” and the randomly selected message, respectively. Similarly, in Table 2, the averaged MSSIM (mean SSIM) values were 0.9878 and 0.9845 when the payload was 65,536 and 131,072 bits, respectively. Therefore, the DE-DWT algorithm generates stego-images have high image quality.
The test images with their corresponding stego-images, which were generated by the DE-DWT algorithm, were used to demonstrate the visual quality of the resulting stego-images (Fig. 5). In this study, the embedding payload used was a 128 × 128 secret image (i.e. 131,072 bits). As addressed earlier in this subsection, the results for other images were similar. In Fig. 5, the image “Logo” was used for the benchmark images, whereas the image “Fingerprint” was used for the non-benchmark images. The produced stego-images clearly do not contain any artifact that can be identified by HVS. In consequence, the DE-DWT algorithm is imperceptible.
Fig. 6 illustrates examples of the extracted secret images sized 64 × 128 (i.e. 65,536 bits) and 128 × 128 (i.e. 131,072 bits) from the stego-images. The extracted secret images are clearly detectable.
4.2 Comparison with other techniques
This subsection compares the proposed DE-DWT algorithm and other DWT-based approaches. Recent techniques were selected for comparison. Namely, the methods suggested by Nag et al. [17], Hemalatha et al. [11], Verma et al. [25], and Pol [19]. These techniques have been reviewed in Section 1. In the experiments, the embedding parameter in the method used by Verma et al. was set to p = 5, whereas the embedding parameter was set to k = 4 in the method used by Pol. Two payload sizes (i.e. 65,536 and 131,072) were used in conducting the experiments. The results of these experiments are presented in Tables 4 and 5 in Appendix 1.
The comparison results reveal that the averaged PSNR values of DE-DWT were about 4.0, 6.0, 14.1, and 9.4 dB higher than those of the techniques of Nag et al., Hemalatha et al., Verma et al., and Pol, respectively, when the payload was set to 65,536 bits. The results also show that the averaged PSNR values of the proposed DE-DWT algorithm were about 4.2, 6.6, 14.1, and 9.5 dB higher than those of the Nag et al., Hemalatha et al., Verma et al., and Pol techniques, respectively, when the payload was set to 131,072 bits. Thus, the experimental results show that the DE-DWT algorithm has better embedding efficiency (i.e. the highest averaged PSNR values) among all compared techniques at different payload sizes.
5 Steganalysis of DE-DWT
The ensemble classifier [14] and the histogram attack were used in this section to attack the DE-DWT algorithm. For the ensemble classifier, a total of 1,000 grayscale images sized 512 × 512 from the RSP database [20] were used as original covers. The DE-DWT and the four compared methods in Section 4.2 were performed on the original covers to generate 5 sets, each consisting of 1,000 stego-images, one set per each steganographic technique. DE-DWT security was compared with that of other compared methods for two different payloads (i.e. 65,536 and 131,072 bits) generated pseudo-randomly to test the performance of the proposed DE-DWT algorithm. For this process, the DE-DWT algorithm was steganalyzed using the ensemble classifier version 2.0 (http://dde.binghamton.edu/download/ensemble/) with a fully automatized search for dimensional subspace, d sub , and basic learners L. All cover images and stego-images obtained from DE-DWT were represented using the CC-PEV feature set with 548 features. For each payload, the covers and stego-images were divided pseudo-randomly into two sets: the training set of 800 covers and their associated stego-images, as well as the testing set of 200 covers and their associated stego-images. The division was repeated 10 times as suggested by the authors of the ensemble classifier. The final test error was averaged over the ten runs. Table 3 shows the obtained steganalysis results for the DE-DWT algorithm and the compared methods.
Table 3 shows that DE-DWT has better security than other methods for the payloads of 65,536 and 131,072 bits. This condition can be attributed to DE-DWT embedding the secret message by changing only the 2nd LSB of at most one DWT coefficient for each coefficient pair used in the embedding process. For example, at a payload of 65,536 bits, the test error of DE-DWT was approximately 30.12 %, whereas it was only 11.20 %, 8.20 %, 3.23 %, and 5.48 %, for the methods Nag et al., Hemalatha et al., Verma et al., and Pol, respectively. Accordingly, significant differences exist in DE-DWT security and those of the compared methods. Similarly, the test error of DE-DWT is larger than those of other methods at a payload of 131,072 bits. The DE-DWT test error is approximately 29.65 % compared with 5.78 %, 4.55 %, 0.35 %, and 2.07 % for the other techniques. Therefore, DE-DWT has better security than other methods. Among all of the compared methods, the method of Verma et al. is indicated as the least secure method because it uses a large embedding parameter (p = 5), which adds a significant amount of distortion to the stego-images.
The DE-DWT algorithm was also tested by the histogram attack. Fig. 7 shows the histogram attack results for only four of the images because of the extreme similarity in the analysis results for other images. The images “Tiffany”, “Jet”, “Peak-2,” and “Building-3” were used in these experiments, where a payload size of 65,536 bits was used for “Tiffany”, “Peak-2” and a payload size of 131,072 bits was used for “Jet” and “Building-3”. If a histogram difference of the cover and its stego-image is observed, then the image is considered suspicious. Based on the experimental results shown in Fig. 7, the DE-DWT algorithm is undetectable through a histogram attack.
6 Robustness of DE-DWT
This section discusses the robustness of DE-DWT against image processing attacks. A set of common attacks was used to evaluate the robustness of DE-DWT. These attacks are compression, salt and pepper, Gaussian noise, cropping, and half-transparent frame. Fig. 8 shows the results of these experiments using the stego-images of “Jet” (benchmark image) and “369 (Building-3)” (non-benchmark image) selected randomly among all stego-images. The results of the other stego-images were similar. For conducting these experiments, the two secret images “Logo” and “Fingerprint” sized 128 × 128 (i.e. 131,072 bits) were used. DE-DWT can resist these mentioned attacks, so the secret images can be readily extracted from the attacked stego-images.
7 Limitations of DE-DWT
The experimental results of this research revealed that the proposed steganographic algorithm is capable of presenting better embedding efficiency than other compared methods in terms of image quality and security. However, the proposed method has some limitations to be addressed in near future. The first limitation is the limited embedding payload available by targeting the second LSBs of the DWT coefficients of cover images in the proposed DE-DWT algorithm. The full embedding payload of the cover image for the proposed algorithm is 0.75 bits per coefficient (bpc) because this algorithm uses the LL, HL, and LH sub-bands. Each sub-band has a size of 256 × 256. Extending the proposed algorithm to be applied on digital video files can overcome the mentioned limitation and thus, increasing the embedding payload. The second limitation is the destruction of the embedded secret image if the stego-image is attacked by a lossy compression attack with a quality factor less than 95 %. This happens because the proposed algorithm relies on pixel pairs to embed and extract the secret bits, and modifying these pixel pairs by a compressing attack leads to destroying the secret bits.
8 Conclusion
This paper proposed an efficient information embedding algorithm based on the DE scheme in wavelet domain (DE-DWT). The proposed algorithm first converts the secret bits into a sequence of base-5 digits. After that, the cover image is transformed into the DWT domain and segmented into set of coefficient pairs. The DE scheme is used thereafter to change at most one coefficient of each coefficient pair to embed one base-5 digit of the secret bits. Finally, the inverse DWT is applied to obtain the stego-image. The main contributions of the proposed algorithm are summarized as following: (1) The proposed algorithm reduces the embedding distortion of current DWT-base embedding methods by adopting the DE scheme. (2) The proposed algorithm improves the overflow/underflow strategy used in the plan of DE scheme, thereby reducing the distortion added to the image when solving the overflow/underflow problem. (3) The proposed algorithm enhances the embedding performance compared with other state-of-art embedding techniques, and is secure from recent steganalysis attacks, such as the powerful universal steganalyzer “ensemble classifier” and the histogram attack. The experimental results revealed that the proposed algorithm has better embedding efficiency compared to other techniques in terms of imperceptibility and embedding payload. The results also reveal that the proposed algorithm is robust against different image processing attacks such as compression, salt and pepper, Gaussian noise, and cropping attacks.
References
Al-Ani ZK et al (2010) Overview: main fundamentals for steganography. J Comput 2(3):158–165
Al-Dmour H, Al-Ani A (2016) A steganography embedding method based on edge identification and XOR coding. Exp Syst Appl 46:293–306
Al-Korbi HA, Al-Ataby A, Al-Taee MA, Al-Nuaimy W (2015) High-capacity image steganography based on Haar DWT for hiding miscellaneous data. IEEE Jordan Conf Appl Electrical Eng Comput Technol (AEECT) 1:1–6
Atawneh S, Almomani A, Sumari P (2013) Steganography in digital images: common approaches and tools. IETE Tech Rev 30(4):344–358
Baby D, Thomas J, Augustine G, George E, Michael NR (2015) A novel DWT based image securing method using steganography. Procedia Comput Sci 46:612–618
Barve S, Nagaraj U, Gulabani R (2011) Efficient and secure biometric image stegnography using discrete wavelet transform. Int J Comput Sci Commun Netw 1(1):96–99
Chan C-K, Cheng L-M (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37(3):469–474
Chao RM et al (2009) A novel image data hiding scheme with diamond encoding. EURASIP J Inf Secur 2009(1):1–9
Chen M et al (2006) Analysis of current steganography tools: classifications & features. International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP’06), California, USA
CVG image database. Available: http://decsai.ugr.es/cvg/dbimagenes/g512.php, accessed Apr. 2014
Hemalatha S et al (2013) A secure color image steganography in transform domain. Int J Cryptography Inf Secur 3(1):17–24
Kanso A, Own HS (2012) Steganographic algorithm based on a chaotic map. Commun Nonlinear Sci Numer Simul 17(8):3287–3302
Keyvanpour M, Bayat FM (2013) Blind image watermarking method based on chaotic key and dynamic coefficient quantization in the DWT domain. Math Comput Model 58(1):56–67
Kodovsky J, Fridrich J, Holub V (2012) Ensemble classifiers for steganalysis of digital media. IEEE Trans Inf Forensics and Secur 7(2):432–444
Li B et al (2011) A survey on image steganography and steganalysis. J Inf Hiding Multimed Signal Process 2(2):142–172
Mali SN, Patil PM, Jalnekar RM (2012) Robust and secured image-adaptive data hiding. Digital Signal Process 22(2):314–323
Nag A et al (2011) A novel technique for image steganography based on DWT and Huffman encoding. Int J Comput Sci Secur 4(6):561–570
Ndoundam R, Ekodeck SGR. PDF Steganography based on Chinese Remainder Theorem. J Information Security Appl, ISSN 2214–2126, Available online February 2016
Pol K (2014) Image steganography based on DWT using Huffman LWZ encoding. Int J Eng Technical Res (IJETR) 2(3):100–103
RSP image database. Available: http://dud.inf.tu-dresden.de/~westfeld/rsp/rsp.html. Accessed Feb 2014
Singh AK, Dave M, Mohan A (2014) Hybrid technique for robust and imperceptible image watermarking in DWT–DCT–SVD domain. Natl Acad Sci Lett 37(4):351–358
Singh AK, Dave M, Mohan A (2015) Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimedia Tools and Applications, pp. 1-21
Sun S (2016) A novel edge based image steganography with 2k correction and Huffman encoding. Inf Process Lett 116(2):93–99
USC-SIPI image database. Available: http://sipi.usc.edu/database/, accessed Jan. 2013
Verma A et al (2013) Implementation of image steganography using 2-level DWT technique. Int J Comput Sci Bus Inf 1(1):1–14
Author information
Authors and Affiliations
Corresponding author
Appendix 1
Appendix 1
Table 4
Table 5
Rights and permissions
About this article
Cite this article
Atawneh, S., Almomani, A., Al Bazar, H. et al. Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimed Tools Appl 76, 18451–18472 (2017). https://doi.org/10.1007/s11042-016-3930-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3930-0