Abstract
In this paper, a novel reversible data hiding algorithm for encrypted images is proposed. In encryption phase, chaotic sequence is applied to encrypt the original image. Then the least significant bits (LSBs) of pixels in encrypted image are losslessly compressed to leave place for secret data. With auxiliary bit stream, the lossless compression is realized by the Hamming distance calculation between the LSB stream and auxiliary stream. At receiving terminal, the operation is flexible, that is, it meets the requirement of separation. With the decryption key, a receiver can get access to the marked decrypted image which is similar to the original one. With data-hiding key, the receiver can successfully extract secret data from the marked encrypted image. With both keys, the receiver can get secret data and the exactly original image. Compared with existing methods, experiments show the feasibility and efficiency of the proposed method, especially in aspect of embedding capacity, embedding quality and error-free recovery with increasing payload.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Reversible data hiding (RDH) in images is a technique, by which the original image can be losslessly recovered after the extraction of the secret data. This important technique can be applied to many scenarios, such as law forensics, military imagery and medical imagery, where no distortion of the original image is allowed. For this reason, RDH has attracted considerable research interest.
Many reversible data hiding methods have been proposed recently. In literature [7, 8, 15], the differences between two adjacent pixels is expanded to generate a new LSB plane for accommodating secret data. In literature[10, 13, 14], spare space is saved for data embedding by shifting the histogram of cover data from its peak point towards its zero points. Another strategy for RDH is based on lossless compression, in which a data hider makes use of redundancy of the original cover to create a blank space for embedding the secret data [1, 12].
With the increasing demand of privacy protection, encryption [2, 3, 16] becomes an effective and popular means, which converts original image into unintelligible one. There are some applications while RDH can be applied for encrypted images. For instance [18], to protect the privacy of the patient, the medical images should have been encrypted, a database administrator may aim to embed the personal data into encrypted medical images. With the personal data, the database administrator can manage the images without knowing the original content. On the other hand, a doctor, having both the data-hiding and the encryption keys, can extract the personal data and recover the original content without any error. That means a RDH scheme for encrypted image is attractive.
Some attempts on RDH for encrypted images have been proposed. In literature [11], AES algorithm was applied to encrypt original image, and each block of an encrypted image can carry one secret bit by simple substitution, at the decryption stage, an analysis of local standard deviation of the marked encrypted image is used to extract the embedded data. However, the embedding capacity is low and the quality of image decrypted from the marked encrypted version is unsatisfactory. In literature [18], a data hider divided the encrypted image into several blocks, by flipping 3 LSBs of specific pixels in each block, one secret bit can be embedded into each block. The data extraction and image recovery proceed with the aid of spatial correlation in natural image. Hong et al. [6] improved the method in literature [18] by further exploiting the spatial correlation using a different estimation equation and side match technique to reduce the error rate. However, in literature [6, 18], encrypted image should be decrypted first before data extraction, that is, if a receiver has the data-hiding key only, he can not extract any data from the marked encrypted image. Aiming for separating data extraction from image decryption, Zhang [19] compressed the LSBs of encrypted image by finding the syndromes of a low-density parity check matrix to create an extra space for secret data. These methods achieve low embedding capacity or generate marked decrypted image with poor quality for high embedding capacity. Besides that, all of them are subject to some error rates on data extraction and /or image recovery [6, 18, 19]. In [20], Zhang embedded the additional data into various bit planes by using a reversible manner, and a parameter optimization method is used to ensure a good payload- distortion performance. the data insertion/extraction can be performed in both the plain and encrypted domains.
Since it is difficult to losslessly vacate room from the encrypted images. Ma et al. [9] and Zhang [21] both emptied out room before image encryption, and achieved excellent performance. However, the operating of image encryption and data embedding is inseparable, which can not satisfy the application requirement of privacy protection.
This paper proposes a novel RDH for encrypted images based on lossless compression with high capacity. Not only does the proposed method separate data extraction from image decryption but also achieves excellent performance in two different prospects:
-
1.
Reversibility is realized, that is, data extraction and image recovery are free of any error. Moreover, image encryption and data hidden process is separable in the proposed method, which meets the demand of digital image for privacy protection.
-
2.
For given embedding rates, the PSNR of marked decrypted image is significantly improved; and for acceptable PSNR, the range of embedding rates is greatly enlarged.
The rest of the paper is organized as follows. The scheme of the proposed method is elaborated in Section 2. Experimental results with analysis and comparison are shown in Section 3. The paper is concluded in Section 4.
2 Proposed method
To enable data embedding in the encrypted image, we propose a novel method to significantly improve the performance in terms of the data embedding capacity and image quality of the marked decrypted image by using the Hamming distance to compress the encrypted image for data embedding. In this proposed scheme, we vacate room after encryption.
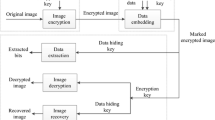
The procedure of reversible data hiding in encrypted images is composed of three steps: image encryption, data hiding, data extraction and image recovery, as illustrated in Fig. 1. The content owner first converts the original image A into its encrypted version B with encryption key r 0. Then the data hider compresses the LSBs of B with data-hiding key k 0 to reserve blank space for additional data, and the data hider produces marked encrypted image C. At the receiver side, since the data hiding only affects the LSBs, decryption without data extraction can result in a marked decrypted image similar to A. With k 0, the secret data can be extracted successfully. With both of k 0 and r 0, the additional data can be correctly extracted and the original image can be exactly recovered.
2.1 Image encryption
Chaos [4] has several good properties including the ease of its generation, its sensitive dependence on initial condition and noise like, so that it is very suitable for image encryption. Meanwhile, it also indicate the trait of certainty, and can be completely reconstructed for image decryption as long as the system parameters and initial conditions are the same.
Logistic mapping is a classical model, which is used to studying the behavior of complex system of dynamic system, chaos, fractal ect. the encryption key as a initial value of Logistic mapping, a chaotic sequence is produced, and after the corresponding treatment, each element of the chaotic sequence is between 0 and 255.
Furthermore, the exclusive-or operation has reversibility. Combined with the Logistic mapping and the exclusive-or operation, a substitute encryption method is designed [5, 17].
In encryption phase, assume the original image A with a size of N 1×N 2 is in uncompressed format and each pixel with gray value falling into [0,255] is represented by 8 bits. Denote the bits of pixel as b i, j (0), b i, j (1),..., b i, j (7) where 1 ≤ i ≤ N 1, 1 ≤ j ≤ N 2, the gray value as p(i, j), and the number of pixels as N(N = N 1×N 2). Thus
The encrypted bits \({b^{\prime }_{i,j}}\left (k \right )\) can be calculated through exclusive-or operation
where r i, j (k) are created using the Logistic mapping with the encryption key r 0. Then, \({b^{\prime }_{i,j}}\left (k \right )\) are concatenated orderly as the encrypted data.Chaos system can be used here to ensure that anyone without r 0, such as a potential attacker or a data hider, can not obtain any data about original content from the encrypted data.
2.2 Data hiding
In data hiding phase, once the data hider acquires the encrypted image B, he can embed secret data into it by modifying a proportion of encrypted data without having any information about the original image content, as shown in Fig. 2. The detailed procedure of data hiding is given as follows:
-
1.
First, segment B into a number of non-overlapping blocks with the size of l × l, l is a positive integer. Then, with the data-hiding key k 0, a random sequence is generated, and select t image blocks by using random interval method or random permutation method. t is a positive integer less than ⌊N/l 2⌋.
-
2.
For each block B i (1 ≤ i ≤ t), extract m LSBs from per pixel to generate a sequence X i = {x i1, x i2, ..., x i n }, n = (m × l × l)/3, x i j is composed of each three consecutive bits of X i , j ∈ [1, n]. Then a corresponding sequence Y i = {y i1, y i2,..., y i n } is generated, which should meet the condition that Hamming distance between x i j and y i j is no more than 1. Here Y i is introduced as auxiliary bit sequence. For example, if X i = {000,001,010,100}, a corresponding sequence Y i = {001,001,011,100}, that is to say, if x i j = {000}, a corresponding stream y i j = {000}. m is a small positive integer less than 4.
-
3.
The following (3) defines a set, denoted by C o s e t1−4, in which a stream containing two bits can replace two types of stream, each of them including three bits and the Hamming distance between them is three. On the basis of C o s e t1 − 4, x i j can be compressed as two bits, so the third bit of x i j is to leave for secret bit. Repeat this way, n bits are embedded into each block at most. For example, if x i j = {000}, the compressed x i j is {00−}, shown in Fig. 2c.
-
4.
Repeat above process until all the secert bits are embedded, a marked encrypted image is generated, denoted by C.
In practice, C o s e t1−4 plays an important role in data embedment and image recovery process. Since the total t × n bits can be accommodated in all blocks at best, the maximum embedding rate, a ratio between the bit amount of secret data and the total number of cover pixels, is (4).
With the data-hiding key k 0 , the data hider randomly selects the blocks and makes proper extraction, thus anyone who does not possess the data-hiding key could not extract secret data.
2.3 Data extraction and image recovery
In this phase, since data extraction is completely independent from image decryption, there are three cases that a receiver has only the data-hiding key k 0, only the decryption key, here r 0, and both k 0 and r 0, respectively, demonstrated in Fig. 3.
Case 1
Data extraction from C
To manage and update personal information and ensure clients’ privacy, a receiver may only get access to k 0. The operation of data extraction before image decryption ensures the feasibility of our work in this case. The receiver should do following three steps:
-
1.
Divide the received image into blocks with the size of l × l,according to the same way in data hiding phase.
-
2.
With k 0, select blocks for data extraction by exploiting random interval method or random permutation method.
-
3.
For each block, extract m LSBs from all pixels, generate a sequence \(X^{\prime }_{i} = \left \{ {x^{\prime }_{i1} ,x^{\prime }_{i2} ,...,x^{\prime }_{in} } \right \}\) which is the same as the generation of X i in data hiding phase and extract bit from the third bit of \(x^{\prime }_{ij}\) successively. Finally, concatenate the extracted bits to form the secret bits. The whole process avoids the leakage of original image content.
-
4.
Repeat the third step mentioned above, until all the secret data is extracted.
Furthermore, because each encrypted block is randomly selected and recombined, which makes any malicious attackers cannot obtain the embedded data under the absence of k 0.
Case 2
Generating the marked decrypted image D
Consider the case that the receiver has only r 0, he can generate r i, j (k) by Logistic mapping and r 0, and calculate the exclusive-or r i, j (k) and received data to decrypt the received image. The gray values of marked decrypted pixels \({p^{\prime \prime \prime }_{i,j}}\left (k \right )\) can be calculated by (5).
where \({b^{\prime \prime \prime }_{i,j}}\left (k \right )\) are the binary bits of D.
Since the (8−m) most significant bits (MSBs) of D are kept unchanged in data hidden process. Clearly, the original (8−m) MSBs are retrieved correctly, the content of D is similar to the original image. However, the receiver is unable to obtain the secret data.
Case 3
Data extraction and image restoration
With the marked encrypted image C, if the receiver has both k 0 and r 0, he can further extract the secret data and recover the original image.
The data extraction process is essentially identical to Case 1, and the receiver can extract the secrte data successfully. After extracting the secret data, the receiver need to recover the original image, the following outlines the specific steps:
-
1.
After data extraction, segment the remaining bits of \(X^{\prime }_{i}\) into a number of streams \(x^{\prime \prime }_{ij}\) successively, \(x^{\prime \prime }_{ij}\) containing two bits. Then, find the corresponding streams x(i,1) and x(i, 2) in C o s e t1−4, and the Hamming distance between x(i,1) and x(i, 2) is three.
-
2.
According to the corresponding sequence y i j , the receiver need to calculate the Hamming distance between y i j and x(i,1), x(i, 2), respectively.
-
3.
If the Hamming distance between x(i,1) and y i j is no more than 1, x(i,1) is the bits of encrypted pixels; Similarly, if the Hamming distance between x(i, 2) and y i j is less than or equal to 1, x(i, 2) is the bits of encrypted pixels.
-
4.
Continue doing Step1 to Step3 and merger all encrypted bits to form the encrypted image.
-
5.
With the encrypted image and r 0, obtain the original pixels via (2) and (5).
3 Experiments and comparisons
The proposed method will be tested on a number of standard images, which include Baboon, Boat, Barbara, Lake, Man and Lena. The size of all images is 512×512. The criteria PSNR is used to evaluate the quality of marked decrypted image. Moreover, the embedding rate is employed to evaluate the amount of the additional data. Note that in this section, the listed PSNR is the PSNR of the marked decrypted image versus the original image.
The standard image Lena shown in Fig. 4a is used as the original image in the experiment. Figure 4b is the encrypted image. Then, we let m = 1, l = 40, and embed 1.1×104 additional bits into the encrypted image, the marked encrypted image is given as Fig. 4c, and the embedding rate is 0.041 bit per pixel (b p p). With the marked encrypted image, we can generate the marked decrypted image using the encryption key, the PSNR of the marked decrypted image is 55.00d B. The marked decrypted image is illustrated in Fig. 4d. Figure 4e depicts the recovery image which is identical to the original image. By both using the data-hiding and encryption keys, the embedded data can be successfully extracted and the original image can be recovered from the marked encrypted image.
Without loss of generality, the use of multiple LSBs takes into account the fact that the values of PSNR can be reduced with an increase in embedding rates. For different standard images, the comparison results measured by PSNR for three different choices of LSBs, i.e. the number of LSBs m, are presented in Table 1, where the embedding rate is measured by bits per pixel (bpp). It is observed that when embedding rate is small, one or two LSBs can be introduced. With a growing embedding rate, we prefer using three LSBs to single one. In practice, we can flexibility choose m in the light of the length of secret bits for acceptable PSNR.
In the proposed scheme, the higher the embedding rate, the worse the quality of the marked decrypted image, therefore, we should not only improve the embedding capacity but also ensure good quality of the marked decrypted image. The quality of marked decrypted images is compared in the term of PSNR. Figure 5 plots the PSNR of different marked decrypted images under given embedding rates. We modify the embedding way and embedding positions of the secret data: we randomly select a certain number of encrypted blocks with the size of 40×40. In the following, according to C o s e t1−4, every 3 LSBs of encrypted pixels are compressed as two bits, and a blank space is generated for secret data. At the same time, 5 MSBs of each encrypted pixel are kept unchanged. We have compared the proposed method with the state-of-the-art work [6, 18, 19]. In Fig. 5, the X-coordinate represents the embedding rate R, the Y-coordinate is the PSNR of the marked decrypted images. Take standard image Baboon for instance, the PSNR of the marked decrypted image using our method is about 15.36 dB higher than the methods in [6, 18, 19]. From Fig. 5, it can be observed that all range of the embedding rates, the PSNR of marked decrypted image is improved about 15 dB than the methods in [6, 18, 19]. The gain in terms of PSNR is significantly higher at same embedding rate than state-of-the-art reversible data hiding algorithms [6, 18, 19]. In addition, another advantage of the proposed method is the much wider range of embedding rate for acceptable PSNRs. In fact, the proposed method can embed more than 5 times as large capacity for the same acceptable PSNR, e.g., PSNR=45dB, as the methods in [6, 18, 19].
In [6, 18], schemes of reversible data hiding for encrypted images are proposed. [6] made improvement on the basis of the work in [18] in order to achieve much lower error rate. these two methods only accommodated one secret bit in each block. However, our proposed method can embed one secret bit into each pixel at most. In [19], the least significant bits of the encrypted image are compressed to create a sparse space to accommodate the additional data, the embedding rate is relatively low, and with the decrease of block size, the original image can not be recovered perfectly.
As mentioned in Section 1, all methods in [6, 18, 19] maybe introduce some error on data extraction and/or image restoration, while the proposed method is free of any error for a number of images.
Our algorithm not only can hide a large number of the secret data, but also can recover the original image losslessly. Whats more, the operation sequence in receiving terminal is flexible, meanwhile it meets the requirement of privacy protection. All these make the proposed algorithm has better competitiveness.
4 Conclusion
A novel scheme for reversible data hiding for encrypted images based on lossless compression with a high capacity is presented, which consists of image encryption, data hiding, and data extraction/image recovery phases. In encryption phase, a chaotic sequence is used to encrypt the original bits. In data hiding phase, although the data hider does not get access to the original image, he makes use of the Hamming distance between streams to generate a blank space for secret data. With marked encrypted image, since the data hiding only affects LSBs, a decrypted version with the decryption key is similar to the original image. According to the data-hiding key, secret data can be correctly extracted. When using both of the data-hiding and the decryption keys, the secret data can be correctly extracted and the original image can be restored perfectly. Experimental results show that the proposed method can achieve reversibility, separate data extraction from image decryption, and effectively improvement on the embedding rate and the quality of marked decrypted images. In this work, one secret bit can be embedded into one encrypted pixel at most.
References
Celik MU, Sharma G, Tekalp AM, Saber E (2005) Lossless generalized-lsb data embedding. IEEE Trans Image Process 14:253–266
Chen G, Zhao X, Li J (2011) A self-adaptive algorithm on image encryption. J Softw 16:1975–1982
Fu Z, Sun X, Liu Q, Zhou L, Shu J (2015) Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting Parallel Computing. IEICE Transactions on Communications E98-B(1):190–200
Gao H, Zhang Y, Liang S, Li D (2006) A new chaotic algorithm for image encryption. Chaos, Solitons and Fractals 29:393–399
Gu Q, Yao M (2003) A research of digital image encryption based on logistic chaotic sequence. Computer Engineering and Applications 39:114–116
Hong W, Chen T-S, Wu H-Y (2012) An improved reversible data hiding in encrypted images using side match. IEEE Signal Proc Letters 19:199–202
Hu Y, Lee H-K, Li J (2009) De-based reversible data hiding with improved overflow location map. IEEE Trans Circuits and Systems for Video Technology 19:250–260
Joong KH, Sachnev V, Qing SY, Jeho N, Nam J, Choo H-G (2008) A novel difference expansion transform for reversible data embedding. IEEE Trans Information Forensics and Security 3:456– 465
Ma K, Zhang W, Zhao X (2013) Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans Information Forensics and Security 8:553–562
Ni Z, Shi Y-Q, Ansari N, Su W (2006) Reversible data hiding. IEEE Trans Circuits and Systems for Video Technology 16:354–362
P W C M, S O (2008) A reversible data hiding method for encrypted images, International Society for Optics and Photonics, San Jose, CA, USA, 68191E-68191E-9
Qin C, Chang CC, Chen YC (2013) Efficient reversible data hiding for VQ-compressed images based on index mapping mechanism. Signal Process 93:2687–2695
Qin C, Chang CC, Huang YH, et al. (2013) An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Trans Circuits and Systems for Video Technology 23:1109–1118
Tai W-L, Yeh C-M, Chang C-C (2009) Reversible data hiding based on histogram modification of puxel differences. IEEE Trans Circuits and Systems for Video Technology 19:906–910
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circuits and Systems for Video Technology 13:890–896
Xia Z, Wang X, Sun X, Qian Wang (2015) A Secure and Dynamic Multi-keyword Ranked Search Scheme over Encrypted Cloud Data. IEEE Transactions on Parallel and Distributed Systems. doi:10.1109/TPDS.2015.2401003
Zhang L, Liao X, Wang X (2005) An image encryption approach based on chaotic maps. Chaos, Solitons and Fractals 24:759–765
Zhang X (2011) Reversible data hiding in encrypted image. IEEE Signal Proc Letters 18:255–258
Zhang X (2012) Separable reversible data hiding in encrypted image. IEEE Trans Information Forensics and Security 7:826–832
Zhang X (2013) Commutative reversible data hiding and encryption. Security and Communication Networks 6:1396–1403
Zhang W, Ma K, Yu N (2014) Reversiblility improve data hiding in encrypted images. Signal Process 94:118–127
Acknowledgments
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61272540,61272453 and 61232016) , the Anhui Provincial Natural Science Foundation(Grant No. 1508085MF115) and the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zheng, S., Li, D., Hu, D. et al. Lossless data hiding algorithm for encrypted images with high capacity. Multimed Tools Appl 75, 13765–13778 (2016). https://doi.org/10.1007/s11042-015-2920-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2920-y