Abstract
Objective
This article explores patterns of terrorist activity over the period from 2000 through 2010 across three target countries: Indonesia, the Philippines and Thailand.
Methods
We use self-exciting point process models to create interpretable and replicable metrics for three key terrorism concepts: risk, resilience and volatility, as defined in the context of terrorist activity.
Results
Analysis of the data shows significant and important differences in the risk, volatility and resilience metrics over time across the three countries. For the three countries analysed, we show that risk varied on a scale from 0.005 to 1.61 “expected terrorist attacks per day”, volatility ranged from 0.820 to 0.994 “additional attacks caused by each attack”, and resilience, as measured by the number of days until risk subsides to a pre-attack level, ranged from 19 to 39 days. We find that of the three countries, Indonesia had the lowest average risk and volatility, and the highest level of resilience, indicative of the relatively sporadic nature of terrorist activity in Indonesia. The high terrorism risk and low resilience in the Philippines was a function of the more intense, less clustered pattern of terrorism than what was evident in Indonesia.
Conclusions
Mathematical models hold great promise for creating replicable, reliable and interpretable “metrics” to key terrorism concepts such as risk, resilience and volatility.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
One of the goals of terrorism is the generation of fear as a means of coercion and achieving political influence (Corsi 1981; Crenshaw 1986; Thornton 1964). Fear is one of the reasons terrorist attacks have such a powerful social and psychological effect. A primary component in the generation of fear is the seemingly unpredictable nature of terrorist attacks (Hutchinson 1972). This uncertainty is especially disruptive as it creates an environment in which people perceive themselves as potential victims at any time (Bandura 1990; Thornton 1964). Reducing the uncertainty surrounding terrorist attacks and mitigating the social and psychological effects of the uncertainty are goals of policy makers and government agencies. To this end, the use of empirical methods for assessing the patterns of terrorist acts and making accurate predictions have multiple benefits. First, empirical methods allow for a more objective evaluation and comparison of patterns of activity for both tactical and strategic intelligence analyses, and for assessing the effectiveness of counterterrorism interventions. Second, reducing the uncertainty around the timing of the next attack allows for a more appropriate response and preparation. Third, reducing uncertainty can lessen the psychological and social impact of the initial attack.
This article presents an empirical method for understanding patterns of terrorist activity in terms of three concepts: risk, resilience and volatility. We establish a mathematical modelling framework, using a self-exciting model, for describing the temporal patterns of terrorist activity, including the observed clustering of terrorist events in time. Self-exciting models assume that the occurrence of a terrorist event “excites” the overall terrorist process and elevates the probability of future events as a function of the times since the past events. This model is grounded in both the theoretical literature on the clustering of terrorist activity as well as the mathematical theory of point process clustering. The resulting framework provides an empirical platform for measuring and comparing fluctuations in terrorist activity over time using three parameters (risk, resilience and volatility) that are easily estimated and interpreted. We apply our framework using data from the Global Terrorism Database (GTD) (LaFree and Dugan 2007) from 2000 through 2010 in three Southeast Asian countries: Indonesia, the Philippines and Thailand.
The rest of this article proceeds as follows: the “Background Literature” section contains a review of the current literature and theory surrounding the concepts of risk, resilience and volatility. In the “Data” section, the terrorism data are introduced, the definitions of risk, resilience and volatility are given, and the terrorist activity for Indonesia, the Philippines and Thailand is examined. In the “Methods” section, the self-exciting point process model is derived and the parameters related to risk, resilience and volatility are explained. The “Results” Section examines the modelling results across the three countries, and the “Discussion” section concludes with a discussion of the implications arising from these results.
Background Literature
Although terrorist attacks might appear to occur independently at random times, a sizeable body of theoretical and empirical research suggests that terrorist incidents actually occur in non-random clusters in space and time. Midlarsky (1978), for example, examines politically motivated violence as a series of related events, where each event influences the probability of subsequent events. This hypothesis is also accepted in criminological and sociological interpretations of terrorism. Clustering effects and contagious behaviour have been identified in military coups (Li and Thompson 1975), international terrorism (Behlendorf et al. 2012; Midlarsky et al. 1980), airline hijackings (Dugan et al. 2005; Holden 1986), race riots (Myers 2000) and insurgent activity (Braithwaite and Johnson 2012; LaFree et al. 2009; Telesca and Lovallo 2006; Townsley et al. 2008). Observers identify consistent cycles in the frequency of terrorist incidents (Enders and Sandler 1999; Enders et al. 1992; Im et al. 1987), proposing reasons for this phenomenon, ranging from economic arguments that the cost–benefit ratio of striking multiple times is more favourable than striking once (Enders and Sandler 2004), to a natural process of organisational growth and learning within a particular terrorist group (Clauset and Gleditsch 2011; Jackson et al. 2005). Clarke and Newman (2006) use the “copy-cat” analogy to describe how one terrorist incident seems to spark the onset of more terrorist incidents shortly after.
Other social, political and environmental phenomena also cluster in time. Cluster-based analyses have provided accurate descriptions of political change actions in the Middle East (Schrodt and Gerner 1996, 2000), gang rivalries and disputes in Los Angeles (Egesdal et al. 2010), and youth suicide (Gould et al. 1990). Criminological research also describes crime hot spots (see Pierce et al. 1988; see Sherman et al. 1989; see Spelman 1993), areas where repeat victimisation occurs (Townsley 2008), and locality rhythms, the predictable periodicity at which criminal events occur in a specific place (see Johnson et al. 2007; see Mohler et al. 2011). Researchers observe that different types of crimes cluster somewhat differently, both temporally and spatially (see Johnson 2008; see Johnson et al. 2009; see Ratcliffe and Rengert 2008; see Short et al. 2009). For example, Johnson et al. (2007) examined space–time patterns of burglary across 10 independent geographic areas in 5 different countries and found that houses within 200 metres of a burgled home were at an elevated risk of burglary for a period of at least 2 weeks. This kind of information allows police to decide on the most efficient allocation of resources to prevent further burglaries.
In many instances, terrorism follows a clustering pattern similar to crime clusters. The clustering explanation for terrorist activity posits that, for any particular location, there is a background risk of terrorism; however, once an incident does occur, it increases the short-term risk of subsequent attacks. This self-exciting behaviour can be modelled using a generalisation of the Hawkes point process model (Hawkes 1971).
The proposed parametric form of the model allows for direct measures of risk, resilience and volatility. These models generalise the contagion models for hijacking presented in Holden (1986, 1987). Similar models are used to model burglary (Mohler et al. 2011) and civilian deaths in Iraq (Lewis et al. 2011). A heuristic interpretation of this model is given in Berrebi and Lakdawalla (2007), which notes that long periods without an attack signify lower risk. In addition, the point process framework bears a similarity to the series hazard model used in Dugan (2011), although the specific terms to handle the clustering are different.
Risk
Modelling risk is not with out its challenges; indeed “risk” has many definitions across different disciplines. In finance, the concept of risk was first formalised by Markowitz (1952) and refers to the uncertainty of outcomes associated with financial activity. Risk in engineering is defined in terms of the expected outcome, that is, the probability of a failure times the cost of the failure (Mannan 2005). In other fields risk is defined as a combination of a hazard, a situation that has potential for negative impact, and vulnerability, or the potential for a negative outcome (Thywissen 2006). In the context of terrorism, the definitions of risk are widely varied. According to Willis et al. (2005), there are no good frameworks for assessing or defining terrorism risk, and no testing of the existing frameworks. This situation is further exacerbated by the tendency of people to overestimate the risk of terrorist attacks by focusing on the potential outcomes of such attacks (Sunstein 2003). Traditional risk managers suchs as Ezell et al. (2010) favour a probabilistic approach to risk assessment, a view that is echoed in Sarewitz et al. (2003), which further distinguishes between vulnerability as the inherent potential for harm, and risk as the probability. Willis et al. (2005) suggest that conceptually risk can be divided into three parts: threat, the probability of a terrorist attack; vulnerability, the uncertainty associated with the cost or damage; and consequences, the actual outcome. This view is echoed by Brunschot and Kennedy (2008), who propose distinguishing between hazard, or potential for harm, and risk, or probability of attack, when considering security threats. The common element in the literature and these approaches is a distinction between the probabilistic component of uncertainty in risk and the consequential component.
Resilience
Like risk, resilience as a concept exists in many fields. In mathematics and the physical sciences, it describes the ability of a material or system to recover from a displacement or perturbation. Resilient materials are able to absorb energy, temporarily deform and then return to their original state. A resilient system is able to absorb shocks or unexpected inputs and return to a state of equilibrium (Bodwin and Wiman 2004; Gordon 1978). In physics, the added component of time is factored in, where resilience is defined in terms of the time required to return to equilibrium. This is a fitting analogy and has since been anthropomorphised to describe individuals (e.g., Bonanno 2004; Butler et al. 2007; Rutter 1993); here the definitions become more fluid and diverse depending on context. In psychology, the definitions are tied in to the pathology of trauma. In this context, resilience can be defined as a separate entity from recovery (Bonanno 2004). Resilience is also extended to describe a characteristic of communities (Brown and Kulig 1996/1997; Sonn and Fisher 1998; Wickes et al. 2010). The multi-faceted conceptualisations of resilience bely easy definition. Kimhi and Shamai (2004) provide a good review and summary of the literature addressing this complexity, identifying three main components: the ability to retain structural and functional integrity in the face of disruption, recovery and adaptation. A more general synthesis of these components is given in Norris et al. (2008), as “a process linking a set of adaptive capacities to a positive trajectory of function and adaptation after a disturbance”. This definition is consistent across the literature, but also emphasises resilience as a process rather than a static trait. In general, resilience can be conceptualised as a measure of the processes in place in a community, or communities, to facilitate recovery from adversity, possibly incorporating economic or physical aspects (as discussed in Rose and Liao 2005, for example). Wickes et al. (2010) also provide a more thorough discussion of how different literatures deal with the concept of resilience in a community. The definition of community resilience is most apropos in the case of terrorism, as we consider the effects of terrorism as applied to a population as a whole. In this instance, discussions of a community’s responses to mass trauma such as natural disasters or terrorist attacks (Pfefferbaum et al. 2007) provide an appropriate context.
Volatility
Volatility is another concept relevant to the study of terrorism risk. Volatility can broadly be defined as a measure of how likely a process is to experience changes. In a financial context, volatility is defined as the variability of the outcome associated with an investment or financial instrument (Taylor 2005). In this definition, a highly volatile investment would have a highly diverse set of outcomes (e.g., a “make or break” investment such as betting on a long shot at the race track), whereas a low volatility investment would have less variability in outcomes (e.g., a government issued bond, or a certificate of deposit). In political science, volatility is defined as the “net change within the electoral party system resulting from individual vote transfers” (Ascher and Tarrow 1975). This definition addresses the sensitivity of a political system to small changes in the status quo, that is, if one vote is changed how is the overall outcome altered. The majority of the literature on volatility and terrorism addresses volatility from one of these two perspectives: the economic or political volatility as influenced by terrorist activity. May et al. (2009) argue that volatility due to terrorist attacks can be manifest in disruptions to the policy making apparatus and governance capabilities, reducing the ability of the government to respond to and prevent future attacks. Volatility in popular opinion, due to people’s responses to terrorism, is seen in drastic swings of public opinion and views (Berrebi and Klor 2008; Jenkins-Smith and Herron 2005). Examples of this can be seen in the Spanish elections in 2004 (van Biezen 2005), where the 11 March 2004 train bombings in Madrid led to an upset of the March 14 elections. The ruling party and election favourite, Partido Popular (PP), is viewed as having mismanaged the investigation of the bombings in order to manipulate public opinion. In the elections 3 days after the bombings, PP was defeated and the Spanish Socialist Workers Party (PSOE) gained power. There are many examples of terrorism increasing volatility in financial markets, including stock markets (Ahmed and Farooq 2008; Arin et al. 2008; Renò and Rizza 2003), and in commodities, most notably fuel prices (Vedenov et al. 2006).
Modelling
This paper explores the properties of a self-exciting model as a means of providing more concrete definitions for the concepts of risk, resilience and volatility. In order to apply the proposed mathematical model and definitions of risk, resilience and volatility to the results, the exact cause of the clustering behaviour does not need to be known. The descriptive models presented in the paper provide a clear basis for comparisons and evaluations without additional factors. While factors such as attack type, casualties, group or response may provide valuable information about the terrorism process, they are excluded here to focus on a equitable comparison between the three countries. In effect, the pattern of terrorism for each country is examined under the assumption of no outside influences in order to remain focused on the conceptual relationships of risk, resilience and volatility to the model specification. Once the conceptual relationship between the model parameters and these concepts is well-understood, the next step is to consider how specific variables can be incorporated into the model to effect which characteristics. It is hoped that future research, beyond the scope of this paper, is undertaken to provide an in-depth exploration of the effects of including additional variables to the models and concepts presented herein.
By focusing analysis in this manner, the severity or impact of the attacks is not considered, partially because of the difficulties in defining the impact of a terrorist attack (see Enders 2007), but also because previous investigations have provided evidence that the severity of terrorist attacks is rather stable over time (Clauset et al. 2007), independent from their frequency (Clauset and Gleditsch 2011), and that the frequency is considered more important than their severity for measurable impacts (Mueller and Stewart 2011; Pizam and Fleischer 2002). However, see Porter et al. (2012) for an approach to incorporate measures of impact and severity in a marked point process framework.
There is a great deal of interaction between risk, resilience and volatility, both conceptually and mathematically. Despite the complexities, the conceptual framework built from the notions of risk, resilience and volatility and self-excitation is a useful tool for comparing and contrasting the terrorist activity between nations and regions.
Data
The data used in our paper are extracted from the Global Terrorism Database (GTD). The GTD is an open-source publicly available database containing information on worldwide terrorist incidents occurring from 1970 through 2010 (http://www.start.umd.edu/gtd/). It is based on a hard-copy dataset originally collected by The Pinkerton Global Intelligence Service (PGIS). In 2001, the National Consortium for the Study of Terrorism and Responses to Terrorism (START) at the University of Maryland obtained and began computerising the database with funding from National Institute of Justice (LaFree and Dugan 2007). Each record in the GTD database includes the date of the incident along with several other attributes such as weapons used, target characteristics, outcome of attack, location and group responsible when this information is available.
We consider the daily count of terrorist activity across the countries of Indonesia, the Philippines and Thailand for the time period 2000 through 2010. We choose three Southeast Asian countries to compare and contrast in order to assess the face validity of the mathematical models used to generate measures of risk, resilience and volatility. The time period 2000–2010 was chosen for analysis for a number of reasons. The turn of the millennium marked several changes in terrorist activity across the world. While one of the most potent events is the attacks of 11 September 2001, this period is also marked by the rise of Jemaah Islamiyah (ICG 2002) along with the resurgence of the Free Aceh Movement in Indonesia (Ross 2005). Around this same time, there was an increase in separatist terrorist activity in the Patani province in Thailand (Croissant 2005). In the Philippines, there was an increase in the prominence of the Moro Islamic Liberation Front as a terrorist group, and increased activity by the Abu Sayyaf Group (Labrador 2002). The approximate co-occurrence across these three countries of an increase in terrorist activity allows for a more equitable comparison between them by, in a sense, controlling for sources of variation on a global scale.
The focus of this paper is on forming a conceptual and analytical model for risk, resilience and volatility based on the notion of self-excitation or contagion. While this could be developed at the terrorist group level, the choice of a country-level analysis is motivated by several factors. First, as many terrorist attacks are “unclaimed”, the GTD has limited information on the group responsible for the attacks. This could bias the results in a group-level analysis if many unattributed events were actually committed by the group. While inferring attribution shows promise, it is still in its infancy for practical use (Stomakhin et al. 2011). The country-level analysis allows a consistent time period for comparison, while the groups were active during different times. The use of these models and the ensuring measures of risk, resilience and volatility provides a tool for policy makers for making decisions at the country level. For example, the measure of resilience can help determine when travel to a particular country is safe, or determining appropriate counterterrorism measures. More strategic uses might include the use of these tools for benchmarking based on historical data and to serve as the basis for forecasting models.
The exact measure of terrorist activity allows for some latitude in interpretation. In Porter and White (2012), Indonesian terrorism is modelled by treating attacks that occur on the same day as individual events. In this approach, a self-exciting hurdle model is used to account for the extreme variation in the level of activity per day. The hurdle model is used for jointly modelling the probability of an attack day (at least one attack) as well as the number of attacks given an attack day. While this approach provides some measure of severity beyond just accounting for an attack occurring or not, it does not distinguish between one coordinated attack that uses several methods and several different attacks, perhaps by different terrorist groups.
A similar but alternative approach is to only group coordinated attacks as a single event but otherwise treat every attack individually. Each GTD record contains the indicator multiple identifying whether it was part of a coordinated attack. Based on this indicator, the approach used in this paper is to consider a unique terrorist event to be any non-coordinated attack as well as all same-day attacks that are part of a coordinated series. This greatly reduces the number of events per day and permits the use and interpretability of standard discrete distributions (e.g., Poisson and Negative Binomial) instead of the hurdle approach. The parameters of the model can be used to define measures of risk, resilience and volatility in a mathematical context that allows statistical inference and comparison across countries. Table 1 summarises the GTD attack data for Indonesia, the Philippines and Thailand for 2000–2010.
The only other modification was to account for missing or invalid values for the event date. The data for the Philippines and Thailand each contained four events with missing day of month values. Four of these were substituted with the day of month value from approxdate, the GTD approximate date field, and the other four were assigned a value of 15. This had no significant effect on the estimated parameters or interpretation.
Indonesia
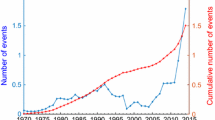
Terrorism and political violence in Indonesia during this period stem from two main sources. In the first half of this period, much of the activity is attributed to sectarian violence in the Poso and Ambon provinces. This abated in 2004 and 2005 when the government reached an accord with the Free Aceh Movement (GAM) that ended violence surrounding issues of self-determination in that region by agreeing to amnesty for several hundred GAM members and facilitating the formation of Aceh-based political parties. In this same period, the Islamic terrorist group Jemaah Islamiyah (JI) entered into the Western consciousness with several high-profile attacks across Indonesia and the region with major attacks occurring with an almost annual frequency (Abuza 2010). Despite this, 2001 marks the start of a steady decrease in the frequency of terrorist activity in Indonesia (Porter et al. 2012). Overall for this period, there were 309 attacks making up 231 unique events on 196 days between 2000 and 2010 in Indonesia. Footnote 1
From Fig. 1, the overall pattern of unique events from 2000 through 2010 in Indonesia appears to have irregular clusters of activity, which is consistent with the self-exciting model.
The 3-month cumulative counts demonstrate a larger-scale pattern of activity that emerges from the clustering process. This shows an overall downward trend in activity punctuated with various periods of increases occurring at irregular intervals in time.
The Philippines
The history of sectarian violence and terrorism in the Philippines can be traced back over four centuries (Banlaoi 2007), with much of the violence related to larger-scale conflicts involving self-determination or other political rights. As a result, the pattern of violence in the Philippines looks much different to that of either Indonesia or Thailand. As forecast by Labrador (2002), the period of 2000 through 2010 marks a period of increased violence across the Philippines. In this period, there were 1,207 attacks, 1,086 unique events on 807 days in the Philippines. Figure 1 shows the unique daily events for the Philippines from 2000 through 2010. The clustering behaviour is also present in the Philippines where short periods of heightened activity are interspersed throughout the time period. There are minor peaks of activity in 2000 and 2003 and a substantial increase in activity from 2008 through 2010. The single lull in the period from 2003 through 2006, where the amount of activity appears to decrease, can be attributed in part to a tentative peace agreement between the Moro Islamic Liberation Front (MILF) and the government in Manila (Hedman 2006) as well as to the increased US supported counterterrorism efforts against MILF on Mindanao (Collier 2006). As opposed to Indonesia, the decrease in terrorism was not long lived, but rather starting increasing during 2006 with a major increase in 2008. The differences between the countries are possibly due to differences in the groups conducting the activity or in the nature of the conflict between these groups and the governments (Banlaoi 2007).
Thailand
Thailand has a long history of conflict between the government in Bangkok and the predominantly Malay-Muslim provinces of Narathiwat, Pattani and Yala (Liow 2006). While over time the intensity of this conflict has ebbed and flowed, in 2001 the intensity of the conflict escalated considerably after the election of the Thai Rak Thai party, which overturned or reversed many of the existing government policies concerning the treatment of Malay-Muslims in the region. Thai involvement in the US-led invasion of Iraq in 2003 was also unpopular with the region’s Muslim population (Chongkittavorn 2004). Other factors contributing to an escalation of violence include ineffective policies and poor handling of the situation by the Thai government (Croissant 2005) and the increased presence of JI in Thailand (Chongkittavorn 2004). While terrorist activity began to increase in 2001, 2004 marks a significant escalation in the tempo and severity of attacks, with several attacks on military and police targets, culminating with the Krue Se siege (Chalk 2008).
In the period from 2000 through 2010, there are 1,472 attacks, 1,304 unique events on 832 days recorded in the GTD. Although most of these are individual attacks, there are a few coordinated multiple attacks that are identified as unique events. The activity in Thailand seems to lack central organisation and is a result of independent actors from a variety of established groups (Chalk 2008). The pattern of activity in Fig. 1 illustrates this escalation, with the same type of irregular ebb and flow as seen in Indonesia and the Philippines.
Methods
The goal of this paper is to establish a modelling framework for understanding the behaviour of terrorist activity that both accounts for the clustering in the temporal attack pattern and also provides a set of conceptual interpretations that are directly related to the properties of risk, resilience and volatility. To account for clustering in the terrorist attack timing, self-exciting point process models are proposed and presented in this section. A process that generates random event times is said to be self-exciting if the occurrence of past events increases the short-term probability of future events. Self-exciting models have been used to model how major earthquakes lead to aftershocks (Ogata 1988), how contagious individuals can infect others (Daley and Vere-Jones 2003; Meyer et al. 2011), near-repeat burglary crimes (Mohler et al. 2011), civilian deaths in Iraq (Lewis et al. 2011), and aircraft hijacking (Holden 1986, 1987). We draw from the extant literature to define the concepts of risk, resilience and volatility and their relationship to the self-exciting model parameters.
Self-Exciting Models for Clustering
Hawkes (1971) introduced a class of self-exciting point processes, now known as the Hawkes process, that have a stochastic intensity determined, in part, by the timing of previously occurring events. Hawkes and Oakes (1974) describe the Hawkes process in terms of a clustering construction. From this perspective, the Hawkes model gives rise to two (unobserved) types of events: immigrant events that arise from a background point process and offspring events that are generated by previously occurring events. Each event, whether immigrant or offspring, is able to generate a cluster of future events and thus excite the process.
In the context of terrorism, the Hawkes model can be used to explain the clustering observed in the data, and the principle of having the event history influencing the future event rate agrees with the theoretical framework describing terrorist activity. Besides being able to represent clustering, the parameters of a Hawkes model also give rise to useful information on the risk, resilience and volatility of the terrorist process. We present a slightly generalised Hawkes model that can incorporate discrete-time observations, a non-constant immigrant rate and a negative binomial likelihood for modelling terrorist activity.
Construction of the Self-Exciting Model
The number of terrorist events per day is modelled as a self-exciting (discrete-time) point process where the expected number of events on a particular day is excited (increased) by the occurrence of events occurring on previous days. Specifically, let Y(t) be the observed number of terrorist events on day t and H t−1 be the history of events up to time t. It is assumed that Y(t) is a random variable with conditional mean, E(Y t |H t−1) = λ(t), and
where B(t) is the baseline process, S(t) is the self-exciting component, and conditioning is based on all historic events that occurred prior to time t.
The baseline process can be a function of any exogenous variables that could have an effect on the event rate (e.g., social, political or economic conditions and events, counter-terrorism efforts), but it will not include any information coming from the history of the event process. The self-exciting term, on the other hand, will be a function of past events in the process. Following the clustering description of the Hawkes process, it is assumed that each event can generate additional offspring events. Specifically, it is assumed that event i will generate an expected
number of extra events on day t, where t must be greater than the event time t i to ensure that an event can only produce future offspring events. The magnitude parameter α ≥ 0 determines the expected total number of direct offspring an event will produce, and the decay function \(g(\cdot)\) specifies the timing of the offspring events as a function of the elapsed time from the event. Combining the contribution from all past events, the self-exciting term
represents the expected number of events on day t due to all of the self-excitation. It is important to include events that occurred prior to the analysis period (e.g., prior to 2000) as these can have an effect on the self-exciting term.
To aid in parameter interpretation and estimation, the decay function is specified to be a proper probability mass function with strictly positive support such that \(\sum\nolimits_{u=1}^{\infty} g(u) = 1. \) This ensures that the influence of an event will eventually diminish and makes the magnitude parameter, α, solely responsible for the total number of offspring contributed by the event. While any discrete distribution can be used for the decay function, provided its support is limited to the set of positive integers, we use the shiftedFootnote 2 negative binomial distribution (described in Porter and White 2012) because it can accommodate a variety of shapes (like the ones specified in Holden 1987), can be reduced to the geometric or Poisson, and is easy to implement. Figure 2 shows an example of the geometric and negative binomial decay functions along with the corresponding self-exciting processes corresponding to eight events. This illustrates how the form of the self-exciting process is similar to kernel intensity estimation (Diggle 1985), but with weights and one-sided (predictive) kernels. The results of applying several decay functions to the data are provided in Table 2 in section “Results”.
While the baseline function can accommodate predictor variables, the models used in this analysis consider a constant baseline function, that is, B(t) = μ. While recent analysis shows that letting B(t) vary over time can have beneficial effects (Lewis et al. 2011), and there are several nonparametric approaches to fitting such models (Mohler et al. 2011; Veen and Schoenberg 2008; Zhuang et al. 2002), there is no standard approach for determining how much complexity to allow in the baseline function. In addition, the small number of events (Indonesia only has 231 events) will limit the identifiability of a model with time varying baseline function (Wang et al. 2010). For a small number of events, the process of fitting the model cannot distinguish between variation in λ(t) due to the self-exciting process S(t) and variation due to the baseline B(t) [see Casella and Berger (2001); Christensen (2002), for a more thorough discussion of identifiability]. While model fit could be improved if the baseline was allowed to be non-constant, in order to make comparisons between countries the baseline function is restricted to the constant μ (which still must be estimated for each country). In Porter and White (2012), a comparison of models using non-constant values for μ shows that the model with the constant μ is the preferred model.Footnote 3
To help accommodate the uncertainty in the baseline function and excess variation in the daily counts, we assume that the daily number of events Y(t) come from a negative-binomial distribution (instead of the Poisson distribution used in the original Hawkes model). The negative-binomial distribution incorporates an extra dispersion parameter θ to allow excess variation in the counts. Thus, the probability that day t has y events is
and \({Y}(t)\) has an expected value λ(t) and variance of \(\lambda\left(1+\frac{\lambda}{\theta}\right). \) As \(\theta\rightarrow\infty, \) (4) converges to a Poisson distribution, giving the negative-binomial the designation of an over-dispersed Poisson distribution. Because the dispersion parameter θ is independent from the mean term λ(t), some of the issues surrounding weak identifiability are alleviated.
This leads to the model for the expected number of events on day t:
This model has five parameters: the baseline mean μ, the magnitude α, the two parameters for the shifted negative-binomial decay function η (size) and γ (mean), and the dispersion parameter for the negative binomial count likelihood, θ. While there is no closed-form maximum likelihood solution, Ozaki (1979) shows how numerical optimisation techniques can be used to obtain the maximum likelihood parameter estimates. R ’s numerical optimisation routines nlminb and optim (R Development Core Team 2011) were used to obtain estimates. For all models, the estimates converged within seconds from a variety of starting points.
Risk
The definition of risk in this paper derives from the statistical assessment of uncertainty as opposed to a purely probabilistic approach. We define risk as a function of the expected number of terrorist events. This is a natural and intuitive definition: the higher the expected number of events, the greater the risk. While on the surface it may seem that this approach seeks to combine the probabilistic and consequential elements of risk into a single measure, it can be shown that this measure can be interpreted in a purely probabilistic fashion by considering its relationship to
As Y(t) is assumed to follow a distribution where λ(t) = E(Y(t)), the larger the value for λ(t), the greater P(Y(t) > 0).
The relationship form of (6) for the Poisson distribution is used in Porter and White (2012), to create a separable model for the probabilistic and consequential components of risk. In this paper, no attempt is made to assess the consequential component of risk, and the formulation given here is a mathematical convenience to allow a link between the model parameters and a conceptual definition of risk. Instead, the focus of this paper is on capturing the dynamic nature of risk and providing a model with easily interpretable parameters that relate directly to the conceptual framework of risk, resilience and volatility.
If we consider that risk can vary greatly over small periods of time, as suggested in the literature, the concept of risk can be viewed from three different perspectives, or scales. Average risk is defined as the average number of terrorist events expected over a period of time, typically on a large scale (e.g., average daily number of attacks over a year). The transient risk is the risk at any given point in time, such as the risk for a given day. We define the transient risk at λ(t). If, as we propose, the level of transient risk is increased after a terrorist attack (i.e., self-excitation), then it is reasonable to assume that after a suitable period of time with no attacks, the risk would return to some constant value. This quantity is defined as the baseline risk and represented by μ in our model. It is important to be clear when discussing risk which of these three perspectives are the focus of discussion.
As observed from Eq. (5), the overall attack intensity (transient risk) is a function of both the baseline and self-exciting functions. While the transient risk of an attack due to the self-excitation can be highly variable over time, the baseline risk, or the level of risk given no effects due to attack history, will likely be more stable and is directly represented in the model by the constant term μ.
Resilience
The characteristics of resilience are neither easily nor directly observable. In order to provide directly measurable and quantifiable measures, we examine the observable impacts of these characteristics, defining resilience in terms of the variation in transient risk. Specifically, resilience is defined as the length of time after an initial event for the risk to return to a pre-event level, defined as a proportion of the increase in risk caused by the event.
While this is more in line with the traditional physical sciences definition of resilience, it is logical that increased traits of resilience such as structural integrity, adaptability and recovery would all manifest themselves as a decreased period of time before return to “normalcy”, that is, the baseline risk. For example, in the immediate aftermath of a terrorist attack, there is typically a good deal of confusion and uncertainty. It is reasonable to assume that in this period there is an increased risk for another terrorist event. Terrorists may have planned multiple attacks to be either simultaneous or closely spaced in time, while others may see the confusion as creating a climate where attacks may be carried out more easily. Resilience as a measure of the strength of community structure or institutions, the adaptability of the community, and the capacity to recover is manifest in how quickly a community is able to restore order and reduce this level of risk. The ability of law enforcement to identify and neutralise the responsible parties, or the ability of civil authorities to restore order, treat the casualties and repair physical damage can all contribute to the reduction in risk of further terrorist events, reflecting the conceptual characteristics of resilience. As a result, it is reasonable to assume that in a strongly resilient community, terrorist incidents would be relatively isolated events, reflecting very brief periods of increased risk. This would be indicative of a community’s or society’s ability to recover from an attack, and prevent any future attacks, regardless of cause (i.e., copy-cat attacks or further planned events). It is important though to recognise that there is some ambiguity associated with attributing a community’s resilience in the face of a terrorist attack as solely a function of the community’s inherent characteristics. In truth, the absence of further acts of terrorism may be as much a function of limitations to terrorists’ ability to act, such as limited physical resources, limited personnel, or strategic planning or tactical reasons. All of this is characterised by a rapid return to pre-event conditions, measured in the model as the baseline risk.
Resilience is defined as a measure of the amount of time for the effect of an event to subside. In the context of the model in (5), this measure will be a function of the decay function \(g(\cdot). \) The decay function can be thought of as assigning a weight to events in the past; the more time that has elapsed, typically the less weight or influence that past event has on the current outcome at current time. As the time from a previous event, u, grows longer, the decay g(u) grows smaller along with the corresponding risk due to self-excitation. As the decay may only reach 0 in the limit (as with the negative binomial decay), we relate resilience to the time it takes the decay function to decrease to the point where the effect of a previous attack is some small proportion of its maximum effect. Specifically, we define resilience as the largest number of days u such that the following condition is met
This is the number of days until the effect of an attack is 5 % of its maximum effect. In the case of using a decay function that does not have its largest value at 1 (e.g., if the shifted negative binomial decay function has a size parameter greater than oneFootnote 4), the resilience measure is restricted to be greater than the peak value.
This measure is based on the concept of settling time in engineering. Settling time is defined as the time it takes for a dynamic system to return to near equilibrium after it is disturbed by a unit input (Franklin et al. 1994). This near-equilibrium state is defined in engineering as a percentage of the maximum variation from equilibrium. In this case, the definition in (7) considers a theoretical state where there is no local increase in risk due to terrorist activity. In reality, resilience or return to an equilibrium state after a terrorist event will depend on the current state of the dynamic risk at the time of the event as well as the volatility. In the interest of clarity and for illustration, resilience is deliberately defined in a way to make it independent of both μ and α. The choice of 5 % as a level to attain is somewhat arbitrary, but not unheard of in engineering practice. Franklin et al. (1994) mention values of 1, 2 and 5 % as being used depending on the application. The specific choice of level has no real theoretical justification other than tradition in the statistical literature, which regards the 5 % level as an accepted level for statistical tests.
Volatility
In the context of the proposed self-exciting model, volatility is defined in our paper as the expected number of events spawned by a previous terrorist event. This measure is represented by the single parameter, α in the model. This definition refers to the total increase in risk caused by the terrorist attack. This is in contrast to resilience, which is related to the temporary increase in risk attributable to the terrorist attack. In more pure mathematical terms, this term refers to the number of events directly caused by a terrorist attack, regardless of how soon after the “original” event they occurred. Because offspring events can generate offspring of their own, it is also interesting to consider the total number of events each background event will generate. In the Hawkes process, the average cluster size is given by 1/(1 − α) (for 0 ≤ α < 1) and refers to the total number of events associated with each baseline event (i.e., the total number of offspring events over all generations plus one) (Hawkes and Oakes 1974). As such, the volatility measure can also be described as the average number of extra events each background event is expected to generate. This is a good reflection of volatility as a measure of the overall de-stabilising effect of terrorism. Thus, larger values of α correspond with more volatility and values of α > 1 indicate an “explosive” situation where the intensity is increasing in a chaotic manner.
In summary, the distinction between risk, resilience and volatility can be clarified as follows: risk is the expected number of terrorist events (represented by μ), volatility is the amount of increase in risk after an event (represented by α), and resilience is how quickly the increase in risk abates after the event (represented by (7)). Fitting the self-exciting model to the counts of unique events, the parameters of the model can be used to define the concepts of risk, resilience and volatility in a mathematical context that can provide the means of statistical inference prediction for these quantities.
Results
In order to make our comparisons between the three countries of Indonesia, the Philippines and Thailand, the self-exciting model as specified in the “Methods” section is implemented and the model parameters are estimated by maximum likelihood. Table 2 shows the model fit for three different decay functions (the shifted negative-binomial, Poisson and geometric) and for two likelihoods (negative-binomial and Poisson) via the AIC metric. AIC, or Akaike information criterion, is calculated as 2k − 2log(L) where L is the likelihood and k is the number of estimated model parameters.Footnote 5 The smallest AIC value indicates the best model in terms of goodness of fit and parsimony.
The results in Table 2 show that the negative-binomial likelihood and decay function is the best fit; this result is reasonable and makes sense considering that both the Poisson and the geometric distributions are special cases of the negative-binomial. This result also suggests that the negative-binomial decay function is a good default to start modelling, where the other cases can be selected if results indicate it prudent.
The results from using the model with negative-binomial likelihood and decay function portray a distinctly different pattern of activity across the three countries for all three dynamic processes: risk, resilience and volatility. A comparison of the model results, coupled with our review of the extant literature, reveals the usefulness of this approach. Results for the parameter estimates and model estimates of risk, resilience and volatility are displayed in Tables 3 and 4 and Figs. 3 and 4.
Results in Table 3 include standard errors for the parameters. These are taken from the Hessian matrix and should be interpreted with caution (Wang et al. 2010), particularly in the case of γ (see Magnus and Neudecker 1999; Yuen 2010, for a more thorough discussion of the relationship between the Hessian and covariance matrices).
In Table 4, the average risk m is defined as the number of events divided by the total number of days in the analysis and is a basic measure of the expected number of attacks on a given day not accounting for any variation in rate. This is contrasted with the model results that show how the risk can vary over time and in response to past attacks. Cluster size in Table 4 is defined as 1/(1 − α). This is the expected number of events in each cluster. The results in Table 4 for the resilience period and the cluster size do not include standard errors as these are difficult to estimate analytically.
Indonesia
Our summary of what is known about terrorism in Indonesia from the “Indonesia” section is reflected in the model results. The fitted model for risk in Fig. 3 shows that the risk of terrorism in Indonesia fluctuates greatly over very short periods of time but that there are still some larger scale trends evident. The peak risk is in the later half of 2001, followed by a steady decrease until a slight increase beginning in 2009. These results are consistent with the analysis summarised from Abuza (2010). The baseline risk (μ) is approximately 0.005, which is almost a tenth of the average risk over the period from 2000 through 2010, of 0.057. In the “Methods” section, we define the parameter α, or the expected number of children from an event, as a measure of volatility. For Indonesia, there are α = 0.820 expected children per event. The resilience is calculated to be 19 days. The function in (7) for Indonesia is shown at the top in Fig. 4 plotted over 50 days with the resilience of 19 days marked by a vertical broken line. The horizontal broken line displays the value of 0.05 for (7). The context for understanding these parameters is as a purely comparative measure; thus, any absolute interpretation of these numerical results is not appropriate.
The Philippines
Model results for the estimated risk in Fig. 3 portray a clear picture of the peaks and valleys of the risk over time in the Philippines. The same peaks evident in the raw data in Fig. 1 are still captured by the model, but further patterns emerge. The sharp increase in risk around 2008–2009 is not strictly the product of any single day with a large number of unique attacks but rather primarily the result of several days with a small to medium number of attacks, all occurring in a very short period of time. In fact, it is the increase in density of attacks rather than the number of attacks that is driving this increase. Despite two peaks in the period since 2009, the risk has been overall trending downwards.
The nature of the excitation effects is shown in Table 4. As in the case of Indonesia, the baseline risk (μ) is much less than the average risk (0.032 vs. 0.270). This difference highlights the disadvantage of using the average risk as a tool for prediction. The self-exciting model can indicate which days carry the most risk. The volatility (α) of 0.881 is greater than that of Indonesia, and the resilience for the Philippines is markedly less than that of Indonesia (39 vs. 19 days), as illustrated at the centre in Fig. 4. In comparing the two countries, we can say that the Philippines is riskier (0.005 vs. 0.032), more volatile (0.820 vs. 0.881) and less resilient (19 vs. 39 days) than Indonesia. These statistics, including the average risk in the Philippines as compared to Indonesia, reveal that the two countries are experiencing truly different phenomena when it comes to terrorism.
Thailand
The estimated risk for Thailand shown in Fig. 3 indicates a fairly steady level of activity until 2004. Throughout 2004, there is a sharp increase in frequency and intensity until 2005, when the level of activity appears to ebb, with risk dropping in 2006. After 2006, the risk increases more slowly with smaller ebbs in 2007 and 2009. The peak risk as estimated by the model occurs in either late 2009 or early 2010 as a result of a period of both frequent and intense activity. The average risk and the parameter estimates in Table 4 relate a distinct story of the nature of the conflict in Thailand. The baseline risk (μ = 0.010) is much less than the average risk of 0.324, with a ratio of the baseline risk to average risk that is much smaller than that for Indonesia or the Philippines. The baseline risk for Thailand also falls below the values for both those countries. The volatility (α = 0.994) is greater than the values for either Indonesia or Thailand. These are indicative of a higher degree of variability in risk over the period from 2000 through 2010 in Thailand and is reflected in the data, the literature review and the parameter estimates. The resilience for Thailand is shown at the bottom of Fig. 4 and with a value of 31 days ranks between that of Indonesia and the Philippines. From these results, we can conclude that Thailand is somewhere in the middle of these three countries for risk and resilience, but is much more volatile than the other two.
Discussion
These results in Table 4 show that self-exciting models can be successfully applied to better understand and compare patterns of risk, resilience and volatility, etc. Our results show that there are different styles of conflict or sources of terrorism in these three countries. Indonesia is the least risky, least volatile and most resilient of the three countries; this is consistent with the most recent patterns of terrorism attributable mainly to Islamist terrorists and, possibly, the effectiveness of the government’s counterterrorism efforts. The Philippines is the riskiest and least resilient of the three countries; the violence there stems from a long legacy of separatist struggle against the national government. Thailand, the most volatile of the three countries, is experiencing a recent drastic increase in separatist violence, exacerbated by government responses and policies.
Of these three countries, Indonesia has the lowest average risk and volatility, and the highest resilience. The lower risk and volatility are a reflection of the lower number of attacks in Indonesia and the short resilience period is indicative of the relatively sporadic nature of terrorist activity in Indonesia. The high risk and low resilience in the Philippines indicates a more intense, less clustered pattern of terrorism. The high average risk and volatility in Thailand is consistent with the recent dramatic increase in the level of terrorist activity.
We recognise the varying histories and contexts leading to terrorist activity across the three countries. The situation in Indonesia, for example, has chiefly arisen from Indonesia’s status as a moderate Muslim state, prompting activity by violent extremists attempting to establish a fundamentalist Muslim state (Craigin 2007), as well as the ongoing conflict arising from Aceh’s attempted secession in 1953 (Crotty 2005). In addition, Indonesia has implemented a number of strong initiatives to combat terrorism in recent years, including special units for terrorist apprehension and de-radicalisation programmes (Jones 2008). Conversely, the Philippines has been plagued by inter-religious conflict stemming from the incorporation of the Muslim south into the country decades ago, combined with an ineffective police force (Craigin 2007). The Thai situation is different again, with largely ethnic and nationalist tensions between the Malay-descent Muslims in the south of Thailand and the Buddhist government increased by central government mismanagement, with an upsurge in violence since 2004 (Jones 2008; Rahimmula 2004).
These differences may have a substantial impact on any causal explanations for the differences observed between the three countries in terms of the modelling framework presented here. In addition, the current analysis does not explore variations in terrorist activities within each country, both in terms of modus operandi and internal spatial patterns, which may be accounted for by other exogenous variables. It is advisable to consider these variations when comparing countries or making substantive conclusions based on this analysis (see LaFree et al. 2011).
Despite these limitations, the descriptive power of this model has the potential to inform policy and practice in a number of ways. The most important is the provision of benchmark indicators for terrorist activity in each country in terms of risk, resilience and volatility. These can be used to evaluate the success of past and future counterterrorism intervention strategies in a far more accurate way than the commonly used simple absence of attacks (Perl 2007). Additional advantages exist in using these measures and this model in a predictive context for forecasting or assessing future risk of terrorist attack. These measures also provide a useful summary to evaluate large amounts of data and describe complex patterns of terrorist activity in a more easily understood manner.
The results of this model can also inform policy in areas similar to the above three countries. Indonesia’s success in combating its terrorism problems is evident in its low risk, low volatility and high resilience. The high risk and volatility and low resilience in the Philippines are indicative of a largely ineffective government programme to combat violence, and the nature and duration of the conflict. The recent outbreak of intense terrorist activity in Thailand, and the government’s ineffective response, is reflected in its high risk and volatility.
The use of an appropriate modelling technique allows more certainty in understanding and predicting terrorist activity. For example, model selection and modelling approach is important when considering various techniques to assess the effectiveness of interventions (Dugan 2011). This paper introduces a new class of models (i.e., self-exciting models) for terrorism modelling that can provide additional insight into the nature of terrorism. In this paper, we restricted ourselves to relatively simple self-exciting models and do not intend them to be definitive. The examples in this paper are presented to show that the relative change in model parameters between populations can define substantive differences in the observed patterns of activity that have an interpretation aligned with the more nuanced quantitative understanding of those patterns.
By reducing uncertainty, policy makers can ensure a more accurate understanding of terrorism, more efficient deployment of resources to combat terrorism (Price and Forrest 2009) and more effective evaluations of counterterrorism strategies (Chalk 2010). A better informed government can also reduce the public’s fear of victimisation by more effectively and accurately informing them as to the nature of the risk (Shapiro and Cohen 2007).
Notes
In this instance, we define Indonesia as including East Timor.
The shifting is necessary so no mass is given to 0. The shifted decay function g(u) has the same value as a negative binomial pmf at u − 1. Zero-truncated distributions are another suitable option for the decay function.
In addition, Table 2 in Porter and White (2012) shows that letting μ vary over time has little effect on the estimates of the self-exciting component parameters. This is intuitive considering the relative small magnitude of μ as compared to λ(t). In order for variations in μ to significantly alter the values of the self-exciting component parameters B(t) would have to be a function that closely replicated the fitting capabilities of the self-exciting component. Thus, as B(t) approaches the self-exciting component, the self-exciting component becomes redundant, and the issues of identifiability and inestimability become evident.
An example of this is shown in Fig. 2b.
Defining T as the total number of days in the period of analysis (2000–2010), from (4) the log-likelihood is \(\log(L)=T[\theta\log(\theta)-\log(\Upgamma(\theta))]+ \sum_{t=1}^T\log(\Upgamma(\theta)+y_t)-\log(y_t!)-(\theta+y_t)\log(\lambda(t)+\theta) +y_t\log(\lambda(t)).\)
References
Abuza Z (2010) Indonesian counter-terrorism: the Great Leap forward. Terror Monit 8(2):6–8
Ahmed S, Farooq O (2008) The effect of 9/11 on the stock market volatility dynamics: empirical evidence from a front line state. Int Res J Financ Econ 16:71–83
Arin KP, Ciferri D, Sagnolo N (2008) The price of terror: the effects of terrorism on stock market returns and volatility. Econ Lett 101:164–167
Ascher W, Tarrow S (1975) The stability of communist electorates: evidence from a longitudinal analysis of French and Italian aggregate data. Am J Political Sci 19:475–499
Bandura A (1990) Mechanisms of moral disengagement. In: Reich W (ed) Origins of terrorism: psychologies, ideologies, theologies, states of mind. Cambridge University Press, Cambridge, pp 161–191
Banlaoi RC (2007) Radical muslim terrorism in the Philippines. In: Tan ATH (ed) A handbook of terrorism and insurgency in Southeast Asia. Edward Elgar, Cheltenham
Behlendorf B, LaFree G, Legault R (2012) Microcycles of violence: evidence from terrorist attacks by ETA and FMLN. J Quant Criminol 28:49–75
Berrebi C, Klor EF (2008) Are voters sensitive to terrorism? Direct evidence from the Israeli electorate. Am Political Sci Rev 102(3):279–301
Berrebi C, Lakdawalla D (2007) How does terrorism risk vary across space and time? An analysis based of the Israeli experience. Def Peace Econ 18:113–131
Bodwin P, Wiman B (2004) Resilience and other stability concepts in ecology: notes on their origin, validity and usefulness. ESS Bull 2:33–43
Bonanno G (2004) Loss, trauma, and human resilience: have we underestimated the human capacity to thrive after extremely aversive events? Am Psychol 59:20–28
Braithwaite A, Johnson S (2012) Space-time modeling of insurgency and counterinsurgency in Iraq. J Quant Criminol 28:31–48. http://dx.doi.org/10.1007/s10940-011-9152-8
Brown D, Kulig J (1996/1997) The concept of resiliency: theoretical lessons from community research. Health Can Soc 4:29–52
Brunschot EGV, Kennedy LW (2008) Risk, balance and security. Sage, New York
Butler L, Morland L, Leskin G (2007) Psychological resilience in the face of terrorism. In: Bongar B, Brown L, Beutler L, Breckenridge J, Zimbardo P (eds) Psychology of terrorism. Oxford University Press, Oxford, pp 400–417
Casella G, Berger R (2001) Statistical inference, 2nd edn. Duxbury, North Scituate
Chalk P (2008) The malay-muslim insurgency in Southern Thailand: understanding the conflict’s evolving dynamics. Tech. rep., The RAND Corporation
Chalk P (2010) Personal communication
Chongkittavorn K (2004) Thailand: international terrorism and the muslim South. Southeast Asian Aff 32:267–275
Christensen R (2002) Plane answers to complex questions: the theory of linear models, 3rd edn. Springer, New York
Clarke R, Newman G (2006) Outsmarting the terrorists. Praeger, Westport
Clauset A, Gleditsch KS (2011) The developmental dynamics of terrorist organizations. ArXiv e-prints 0906.3287v2
Clauset A, Young M, Gleditsch KS (2007) On the frequency of severe terrorist events. J Confl Resolut 51(1):58–87
Collier K (2006) Terrorism: evolving regional alliances and state failure in Mindanao. Southeast Asian Aff 2006:26–38
Corsi JR (1981) Terrorism as a desperate game. J Confl Resolut 25(1):47–85
Craigin K (2007) Sharing the dragon’s teeth: terrorist groups and the exchange of new technologies. Tech. rep., RAND Corporation, Santa Monica, CA
Crenshaw M (1986) Political psychology: contemporary problems and issues. Jossey-Bass, chap The Psychology of Political Terrorism, pp 379–413. Reprinted in Jost JT, Sidanius J (eds) Political psychology: key readings (Taylor and Francis, 2004)
Croissant A (2005) Unrest in Thailand: contours, causes and consequences since 2001. Strateg Insights 4(2):21–41, online Journal
Crotty WJ (2005) Democratic development and political terrorism: the global perspective. Northeastern University Press, Boston
Daley DJ, Vere-Jones D (2003) An introduction to the theory of point processes, vol I, 2nd edn. Springer, New York
Diggle P (1985) A kernel method for smoothing point process data. J R Stat Soc Ser C Appl Stat 34(2):138–147
Dugan L (2011) The series hazard model: an alternative to time series for event data. J Quant Criminol 27:379–402
Dugan L, LaFree G, Piquero A (2005) Testing a rational choice model of airline hijackings. Criminology 43(43):1031–1066
Egesdal M, Fathauer C, Louie K, Neuman J (2010) Statistical and stochastic modeling of gang rivalries in Los Angles. SIAM Undergraduate Research Online 3
Enders W (2007) Handbook of defense economics, vol 2, Elsevier, Amsterdam, The Netherlands, chap Terrorism: An Empirical Analysis, pp 815–866
Enders W, Sandler T (1999) Transnational terrorism in the post-Cold War Era. Int Stud Q 43(1):145–167
Enders W, Sandler T (2004) Transnational terrorism 1968–2000: thresholds, persistence and forecasts. South Econ J 71(3):467–482
Enders W, Parise GF, Sandler T (1992) A time-series analysis of transnational terrorism: trends and cycles. Def Peace Econ 3(2):305–320
Ezell BC, Bennett SP, von Winterfeldt D, Sokolowski J, Collins AJ (2010) Probabilistic risk analysis and terrorism risk. Risk Anal 30(4):575–589
Franklin GF, Powel JD, Emami-Naeini A (1994) Feedback control of dynamic systems, 3rd edn. Addison-Wesley, Reading
Gordon J (1978) Structures. Penguin Books, Harmondsworth
Gould MS, Wallenstein S, Kleinman M (1990) Time-space clustering of teenage suicide. Am J Epidemiol 131(1):71–78
Hawkes AG (1971) Spectra of some self-exciting and mutually exciting point processes. Biometrika 58(1):83–90
Hawkes AG, Oakes D (1974) A cluster process representation of a self-exciting process. J Appl Probab 11(3):493–503, http://www.jstor.org/stable/3212693
Hedman ELE (2006) The Philippines in 2005: old dynamics, new conjuncture. Asian Survey 46(1):187–193
Holden R (1986) The contagiousness of aircraft hijacking. Am J Sociol 91(91):874–904
Holden R (1987) Time series analysis of a contagious process. J Am Stat Assoc 82(400):1019–1026
Hutchinson MC (1972) The concept of revolutionary terrorism. J Confl Resolut 16(3):383–396
ICG (2002) Indonesia backgrounder: how the Jemaah Islamiyah terrorist network operates. Tech. Rep. 43, International Crisis Group
Im EI, Cauley J, Sandler T (1987) Cycles and substitutions in terrorist activities: a spectral approach. Kyklos 40(2):238–255
Jackson BA, Baker J, Cragin K, Parachini J, Trujillo HR, Chalk P (2005) Aptitude for destruction volume 2: case studies of organizational learning in five terrorist groups. Tech. rep., Rand Corporation, Santa Monica CA
Jenkins-Smith HC, Herron KG (2005) United States public response to terrorism: fault lines or bedrock? Rev Policy Res 22:599–623
Johnson S (2008) Repeat burglary victimisation: a tale of two theories. J Exp Criminol 4(3):215–240
Johnson S, Summers L, Pease K (2009) Offender as forager? A direct test of the boost account of victimization. J Quant Criminol 25(2):181–200
Johnson SD, Bernasco W, Bowers KJ, Elffers H, Ratcliffe J, Rengert G, Townsley M (2007) Space-time patterns of risk: a cross national assessment of residential Burglary victimization. J Quant Criminol 23:201–219
Jones S (2008) Briefing for the new president: the terrorist threat in Indonesia and South-east Asia. Ann Am Acad Political Soc Sci 618:69–78
Kimhi S, Shamai M (2004) Community resilience and the impact of stress: adult response to Israel’s withdraw from Lebanon. J Community Psychol 32:439–451
Labrador MC (2002) The Philippines in 2000: In search of a Silver Lining. Asian Stud 41(1):221–229
LaFree G, Dugan L (2007) Introducing the global terrorism database. Terror Political Violence 19:181–204
LaFree G, Dugan L, Korte R (2009) The impact of British counter terrorist strategies on political violence in Northern Ireland: comparing deterrence and Backlash models. Criminology 47:17–45
LaFree G, Mazerolle L, Denning R, Miller E, White G, Yang SM (2011) Modeling the effectiveness of counter-terrorism strategies in Indonesia, the Philippines and Thailand. Research report, The National Consortium for the study of terrorism and responses to terrorism and The Australian Research Council Centre of Excellence in Policing and Security, US Department of Homeland Security Grant Award 2009-ST-108-000008 and the Australian Department of Prime Minister and Cabinet Grant Award PR09-0007
Lewis E, Mohler G, Brantingham PJ, Bertozzi AL (2011) Self-exciting point process models of civilian deaths in Iraq. Secur J. http://dx.doi.org/10.1057/sj.2011.21. Advance online publication 19 September
Li RP, Thompson WR (1975) The “Coup Contagion” hypothesis. J Confl Resolut 19:63–88
Liow JC (2006) Muslim resistance in Souther Thailand and Southern Philippines: religion, ideology and politics. Policy Studies 24, East-West Center, Washington DC, USA
Magnus JR, Neudecker H (1999) Matrix differential calculus with applications in statistics and econometrics. Wiley, New York
Mannan S (2005) Lees’ loss prevention in the process industries, 3rd edn. Butterworth-Heinemann, Oxford
Markowitz H (1952) Portfolio selection. J Finanac 7(1):77–91
May PJ, Sapotichne J, Workman S (2009) Widespread policy disruption: terrorism, public risks, and homeland security. Policy Stud J 37:171–194
Meyer S, Elias J, Höhle M (2011) A space-time conditional intensity model for invasive meningococcal disease occurrence. Biometrics doi:10.1111/j.1541-0420.2011.01684.x
Midlarsky MI (1978) Analyzing diffusion and contagion effects: the urban disorders of the 1960s. Am Political Sci Rev 72:996–1008
Midlarsky MI, Crenshaw M, Yoshida F (1980) Why Violence spreads: the contagion of international terrorism. Int Stud Q 24:341–365
Mohler GO, Short MB, Brantingham PJ, Schoenberg FP, Tita GE (2011) Self-exciting point process modeling of crime. J Am Stat Assoc 106(493):100–108
Mueller J, Stewart MG (2011) Terror, security, and money balancing the risks, benefits, and costs of homeland security. Oxford University Press, Oxford
Myers DJ (2000) The diffusion of collective violence: infectiousness, susceptibility, and mass media networks. Am J Sociol 106(1):178–208
Norris FH, Stevens SP, Pfefferbaum B, Wyche KF, Pfefferbaum RL (2008) Community resilience as a metaphor, theory, set of capacities, and strategy for disaster readiness. Am J Community Psychol 41:127–150
Ogata Y (1988) Statistical models for earthquake occurrences and residual analysis for point processes J Am Stat Assoc 83(401):9–27. http://www.jstor.org/stable/2288914
Ozaki T (1979) Maximum likelihood estimation of Hawkes’ self-exciting point processes. Ann Inst Stat Math 31:145–155
Perl R (2007) Combating terrorism: the challenge of measuring effectiveness. Report RL33160, Congressional Research Services
Pfefferbaum BJ, Reissman DB, Pfefferbaum RL, Klomp RW, Gurwitch RH (2007) Building resilience to mass trauma events. In: Doll LS, Bonzo SE, Sleet DA, Mercy JA (eds) Handbook of injury and violence prevention. Springer, New York, pp 347–358
Pierce GL, Spaar S, Briggs L (1988) The character of police work strategic and tactical implications. Tech. rep., Center for Applied Social Research, Boston, MA
Pizam A, Fleischer A (2002) Severity versus frequency of acts of terrorism: which has a larger impact on tourism demand? J Travel Res 40(3):337–339
Porter MD, White G (2012) Self-exciting hurdle models for terrorist activity. Ann Appl Stat 6(1):106–124
Porter MD, White G, Mazerolle LM (2012) Evidence-based counterterrorism policy. Springer, New York, NY, chap Innovative methods for terrorism and counterterrorism data, pp 91–112
Price JC, Forrest JS (2009) Practical aviation security: predicting and preventing future threats. Butterworth-Heinemann, Oxford
R Development Core Team (2011) R: A language and environment for statistical computing. R Foundation for Statistical Computing, Vienna, Austria. http://www.R-project.org, ISBN 3-900051-07-0
Rahimmula C (2004) Peace resolution: a case study of separatist and terrorist movement in Southern border provinces of Thailand. Songklanakarin J Soc Sci Humanit 10(1):97–112
Ratcliffe J, Rengert G (2008) Near-repeat patterns in Philadelphia shootings. Secur J 21(1):58–76
Renò R, Rizza R (2003) Is volatility lognormal? Evidence from Italian futures. Phys A 332:620–628
Rose A, Liao SY (2005) Modeling regional economic resilience to disasters: a computable general equilibrium analysis of water service disruptions. J Reg Sci 45(1):75–112
Ross ML (2005) Rebellion and resources in Aceh, Indonesia. In: Collier P, Sambanis N (eds) Understanding civil war: evidence and analysis, vol 2, The World Bank
Rutter M (1993) Resilience: some conceptual considerations. J Adolesc Health 14:626–631
Sarewitz D, Pielke R, Keykhah M (2003) Vulnerability and risk: some thoughts from a political and policy perspective. Risk Anal 23(4):805–810. doi:10.1111/1539-6924.00357
Schrodt PA, Gerner DJ (1996) Using cluster analysis to derive early warning indicators for the middle east, 1976–1979, paper presented at the American Political Science Association, San Francisco, 28 August–1 September 1996
Schrodt PA, Gerner DJ (2000) Cluster-based early warning indicators for political change in contemporary levant. Am Political Sci Rev 94(4):803–817
Shapiro JN, Cohen DK (2007) Color bind: lessons from the failed homeland security advisory system. Int Secur 32(2):121–154. doi:10.1162/isec.2007.32.2.121
Sherman L, Gartin P, Buerger M (1989) Hot spots of predatory crime: routine activities and the criminology of place. Criminology 27:27–56
Short MB, D’Orsogna MR, Brantingham PJ, Tita GE (2009) Measuring and modeling repeat and near-repeat burglary effects. J Quant Criminol 3:335–339
Sonn C, Fisher A (1998) A sense of community: community resilient response to oppression and change. J Community Psychol 26:457–472
Spelman W (1993) Abandoned buildings: magnets for crime? J Crim Justice 21:481–495
Stomakhin A, Short MB, Bertozzi AL (2011) Reconstruction of missing data in social networks based on temporal patterns of interactions. Inverse Probl 27(11). http://stacks.iop.org/0266-5611/27/i=11/a=115013
Sunstein CR (2003) Terrorism and probability neglect. J Risk Uncertain 26:2/3 121-136 2003 26:121–136
Taylor S (2005) Asset price dynamics, volatility, and prediction. Springer, New York
Telesca L, Lovallo M (2006) Are global terrorism attacks time-correlated? Phys A 362:480–484
Thornton TP (1964) Internal war, Free Press, New York, chap Terror as a weapon of political agitation, pp 71–99
Thywissen K (2006) Components of risk: a comparative glossary. SOURCE 2, United Nations University Institute for Environment and Human Security
Townsley M (2008) Visualising space time patterns in crime: the hotspot plot. Crime Patterns Anal 1:61–74
Townsley M, Johnson SD, Ratcliffe JH (2008) Space time dynamics of insurgent activity in Iraq. Secur J 21:139–146
van Biezen I (2005) Terrorism and democratic legitimacy: conflicting interpretations of the Spanish elections. Mediterr Politics 10:99–108
Vedenov DV, Duffield JA, Wetzstein ME (2006) Entry of alternative fuels in a volatile US gasoline market. J Agric Resour Econ 31:1–13
Veen A, Schoenberg F (2008) Estimation of space-time branching process models in seismology using an EM-type algorithm. J Am Stat Assoc 103(482):614–624
Wang Q, Schoenberg FP, Jackson DD (2010) Standard errors of parameter estimates in the ETAS model. Bull Seismol Soc Am 100(5A):1989–2001. doi:10.1785/0120100001, http://www.bssaonline.org/content/100/5A/1989.abstract, http://www.bssaonline.org/content/100/5A/1989.full.pdf+html
Wickes R, Zahnow R, Mazerolle L (2010) Community resilience: current approaches, challenges and opportunities. In: Mendis P, Yates A (eds) Recent advantages in national security technology and research, research network for a secure Australia, Australian security research centre
Willis HH, Morral AR, Kelly TK, Medby JM (2005) Estimating terrorism risks. Tech. rep., RAND Corporation
Yuen KV (2010) Appendix A: Relationship between the Hessian and covariance matrix for Gaussian random variables, Wiley, New York, pp 257–262. doi:10.1002/9780470824566.app1
Zhuang J, Ogata Y, Vere-Jones D (2002) Stochastic declustering of space-time earthquake occurrences. J Am Stat Assoc 97(458):369–380
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
White, G., Porter, M.D. & Mazerolle, L. Terrorism Risk, Resilience and Volatility: A Comparison of Terrorism Patterns in Three Southeast Asian Countries. J Quant Criminol 29, 295–320 (2013). https://doi.org/10.1007/s10940-012-9181-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10940-012-9181-y