Abstract
Nowadays, connected health care applications are used more and more in the world. Service through the applications can save the patients’ time and expense, such as telecare medical information system (TMIS) and integrated electronic patient record (EPR) information system. In the applications, preserving patients’ privacy, transmitting messages securely and keeping mutual authentication should all be paid attention. Many authentication schemes have been proposed to make a secure communicating environment. Recently Xie et al. showed that Wen’s scheme was insecure because it was under the off-line password guessing attack and without user anonymity and forward security. They gave a new three-factor authentication scheme and claimed that it was secure. However, we find that Xie et al’s scheme is vulnerable to the De-synchronization attack and the server has too much storage burden in the scheme. Then we present an improved scheme which overcomes the usual weaknesses and keeps ordinary security characters. Compared with recent schemes of the same kind, our scheme is secure and practical.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
Introduction
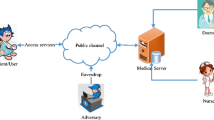
With the popularity of Internet, connected health care takes up a large slice in medical field. It is used to provide opportunities for patients to engage with clinicians remotely and conveniently. Connected health concentrates on self-care and remote care. Some applications, like TMIS and integrated EPR information system, draw attention of researchers. They have been applied widely in e-healthcare, home monitoring facility, distant nursing and so on. In order to protect the patients’ private information, or electronic medical record, authentication schemes play an important part in connected health care applications. There are two basic participants in those systems: one is the user at the public end and the other is the server which ensures the services for connected health care. Naturally, the server should check every user and hinder the illegal access. We show the simply structure of connected health care in Fig. 1.
Many two-factor authentication schemes [8, 10, 11, 15–20] have appeared to solve the security problem. Besides the user’s password, the smart card is added into the scheme. A user registers on the remote server and the server issues a smart card including some secret data to the user. When the user wants to login the system for service, he should use both his password and the smart card. Sometimes a USB stick or a mobile device which contains necessary information of the user is used, instead of the smart card. Nowadays, three points attract the researchers for this kind of schemes. The first is a security character called user anonymity, which keeps the attacker from getting the user’s identity directly in the process of authentication. The second is that according to [14, 23], the information in the smart card may be stolen. So the off-line password guessing attack appears. The attacker may steal the data in a legal user’s smart card first and then guess the password with the messages he eavesdropped from the communication channel. The last is the De-synchronization attack. It is applied in [26, 30, 33]. In [30, 33], it is called DoS attack. To avoid misunderstanding, we use ”De-synchronization attack” as in [26]. It means that the compared data are inconsistent in a legal user’s normal authentication process. For example, the attacker may forge or hinder messages in the communication in order to prevent a legal user’s latter logins. After the attacker’s disturbance, the legal user has no corresponding information to the storage of the server.
A lot of authentication schemes like [2, 3, 6, 22, 28, 30, 31] have been proposed for TMIS or integrated EPR system. In 2012, Chen et al.[3] proposed a new identity based authentication scheme with smart cards for TMIS. However, papers [2, 6, 22, 31] all pointed out that scheme in [3] had disadvantages such as the off-line password guessing attack and without user anonymity. Later, Wu et al. [30] pointed out that the scheme in [6] was still insecure because it was under the off-line password guessing attack, the user impersonation attack and the De-synchronization attack. But Wen et al. [28] showed that Wu et al.’s scheme was not really anonymous for user, and under the server spoofing attack with the off-line password guessing attack.
Recently, human biometrics becomes a hot issue used for authentication [4, 5, 9, 12, 27, 32]. It is hard to be forged, lost or forgotten. With the password and the smart card mentioned above, three-factor authentication appears. Fan et al. [5] enhanced the standard of security: even two of the three factors are stolen by the attacker, the scheme should still be secure. In 2013, Das et al.[4] presented a new uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care with three-factor authentication. But papers [13, 27] pointed out that Das et al.’s scheme had many weaknesses like no user anonymity, under the off-line password guessing attack, the user impersonation attack and no forward security. Also, one improved scheme was proposed in [27] by Wen. But Xie et al.[32] showed that Wen’s scheme was vulnerable to the off-line password guessing attack and without user anonymity and forward security. Unfortunately, we find that Xie et al.’s scheme is under the De-synchronization attack and with too much storage burden in server. Then we propose a new user authentication scheme used for connected health care to satisfy the security requirements.
The remainder of the paper is organized as follows: in Section Preliminaries, we briefly introduce the notations and some cryptographic notions. Then we show Xie et al.’s scheme and point out the weaknesses in Section Review and Cryptanalysis of Xie et al.’s scheme. Our scheme is in Section Outline of our scheme. The security analysis and performance comparison with other schemes are in Section Security analysis and Section Performance comparison respectively. Finally, we give the conclusion in Section Conclusion.
Preliminaries
In this section, we first list the notations used throughout the paper. Then we briefly express the way to cope with biometrics in the system.
Notations
-
U i , I D i , P W i : the i − t h user, identity and password
-
B i : U i ’s biometric information
-
S : the server
-
X s : the secret key stored in S
-
A : the malicious attacker
-
h(.): a secure hash function
-
H(.): a Biohash function
-
E k (.)/D k (.): a symmetric encryption and decryption function with key k
-
a? = b : whether a equals b
-
a ⊕ b : the X-OR computation with a and b
Biometrics treatment
The collected biometrics B i appears to be different in different collections. According to [7], Biohashing function is proposed to produce a set of specific compact code of user. So in Das et al. and Wen’s schemes [4, 27], the researchers use it to dealing with the input biometrics. But in Xie et al.’s [32], a usual one-way hash function is used. That is one of the reasons of the De-synchronization attack. We employ Biohashing to avoid the wrong processing way in [32].
Review and Cryptanalysis of Xie et al.’s scheme
Xie’s scheme
Xie et al’s scheme includes three phases: registration, login and verification and password change. The last phase has no weakness, so we omit it. At first the server S selects a secret key X s , a symmetric encryption/decryption algorithm E k (.)/D k (.), a one-way hash function h(.) and an elliptic curve E over a finite field F p with a generator P and a large order q.
Registration
-
1.
U i selects I D i and P W i freely and imprints his biometrics B i with a collection device. Then U i computes R P W i = h(B i ||I D i ||P W i ) and f i = h(R P W i ) and sends I D i to S through a secure channel.
-
2.
S checks I D i after receiving the message and chooses a random identity N I D i . Then S computes e i = h(I D i ||X s ), y i = E X s (I D i , c t r U i = 0) and stores (N I D i , y i ) as a record in database. Here \(ctr_{U_{i}}\) is a record number for login times.
-
3.
S injects P, N I D i , e i , \(ctr_{U_{i}}\) and h(.) into a smart card and issues it to U i via a secure channel.
-
4.
U i computes T I D i = R P W i ⊕ e i = h(B i ||I D i ||P W i ) ⊕ h(I D i ||X s ), stores f i in the smart card and replaces e i with T I D i .
Login and verification
Once U i wants to login in the system, he inserts the smart card and inputs his information I D i , P W i and B i .
-
1.
The smart card computes R P W i = h(B i ||I D i ||P W i ) and checks f i ? = h(R P W i ). If it is wrong, U i should input the information again. Otherwise, the card generates a nonce a, computes
$$\begin{array}{@{}rcl@{}} & e_{i}=& RPW_{i}\oplus TID_{i} \\ & r_{1} = &aP \\ & ctr_{U_{i}}^{\prime} =& ctr_{U_{i}}+1 \\ & M_{1} =&E_{e_{i}}(r_{i}||ctr_{U_{i}}^{\prime}) \\ & M_{2} =& h(ID_{i}||r_{1}||ctr_{U_{i}}^{\prime}||NID_{i}) \end{array} $$and sends \(\{M_{1},M_{2},ctr_{U_{i}}^{\prime },NID_{i}\}\) to S.
-
2.
After receiving the message from U i , S verifies N I D i in the database, finds the corresponding y i and computes
$$\begin{array}{@{}rcl@{}} & \{ID_{i},ctr_{U_{i}}\}=&D_{X_{s}}(y_{i}) \\ & \{r_{1},ctr_{U_{i}}^{\prime}\}=&D_{h(ID_{i}||X_{s})}(M_{1}) \end{array} $$Then S checks if \(ctr_{U_{i}}^{\prime }>ctr_{U_{i}}\) and M 2 = h(I D i ||r 1||c t r U i ||N I D i ). S will reject the session if either of them is incorrect. Otherwise, S chooses a random number b and a new random identity \(NID_{i}^{\prime }\), computes
$$\begin{array}{@{}rcl@{}} & r_{2} =&bP \\ & r =&br_{1}=baP \\ & M_{3} =& h(r_{1}||r)\oplus NID_{i}^{\prime} \\ & M_{4} =& h(r_{2}||r_{1}||r||NID_{i}^{\prime}) \end{array} $$and sends M 3, M 4 and r 2 to U i .
-
3.
U i computes r = a r 2 = a b P, \(NID_{i}^{\prime }=h(r_{1}||r)\oplus M_{3}\) and checks \(M_{4}?=h(r_{2}||r_{1}||r||NID_{i}^{\prime })\). Then U i computes \(M_{5}=h(NID_{i}^{\prime }||r)\), the session key \(SK=h(r_{2}||r_{1}||r||ctr_{U_{i}}^{\prime })\), and replaces (N I D i , c t r U i ) with \((NID_{i}^{\prime },ctr_{U_{i}}^{\prime })\) in the smart card. At last, M 5 is sent to S from U i .
-
4.
S checks \(M_{5}?=h(NID_{i}^{\prime }||r)\). If it is not true, S sends M 6 = E h(I D i ||X s)(M 5 i s n o t c o r r e c t) and rejects the session. Otherwise, S computes the session key \(SK=h(r_{2}||r_{1}||r||ctr_{U_{i}}^{\prime })\) and \(y_{i}^{\prime }=E_{X_{s}}(ID_{i}||ctr_{U_{i}}^{\prime })\) and substitutes \((NID_{i}^{\prime },y_{i}^{\prime })\) for (N I D i , y i ). If U i receives M 6, he has to re-authenticate with S and does not update (N I D i , c t r U i ).
Weaknesses of Xie et al.’s scheme
De-synchronization attack
We divide it into two cases:
-
1.
Like we has explained in Section 2, Xie et al.’s scheme does not employ Biohash to deal with users’ biometrics. It is normal that B i in login is different from the original information collected in registration, then f i ≠ h(R P W i ) and the login will be denied.
-
2.
At step 3 of login and verification, U i updates (N I D i , c t r U i ) with \((NID_{i}^{\prime },ctr_{U_{i}}^{\prime })\). In Xie et al’s paper, they only say that if U i receives M 6, (N I D i , c t r U i ) will not be updated. But if M 5 is delayed or blocked by the attacker A in the communication, S will abandon this message. Then the session is terminated and the step 4 will not occur. U i will not receive M 6, either. It leads to the result that the record in S has not been changed while U i has already updated his data. So next time S can not find \(NID_{i}^{\prime }\) submitted by U i from the database and then the login will be rejected.
Heavy storage burden in server
In Xie et al.’s scheme, S has a verifier table containing records (N I D i , y i ). That takes up a lot of space. The same thing happens in Das et al. and Wen’s schemes [4, 32], as the server in them must store a record table for users.
Outline of our scheme
In this section we show our new scheme. It has three phases and at first S also chooses X s , E k (.)/D k (.) h(.) and P, like Xie et al.’s. Also, a Biohash function H(.) is selected.
Registration
-
1.
U i chooses I D i , P W i and a random number r i , imprints his biometrics B i and computes N I D i = h(I D i ||r i ) and H P W i = h(P W i ||r i ). Then U i only sends N I D i to S via a secure channel.
-
2.
S computes e i = h(N I D i ||X s ), stores P, h(.) and H(.) into a smart card and sends the smart card with e i to U i through a secure channel.
-
3.
U i computes B 1 = e i ⊕ h(H P W i ||I D i ) and B 2 = H(P W i ||I D i ||B i ) ⊕ r i , and stores B 1 and B 2 into the smart card.
Login and verification
This phase is shown in Fig. 2.
-
1.
U i inserts his smart card and inputs I D i , P W i and B i while he wants to login. The smart card computes r i = B 2 ⊕ H(P W i ||I D i ||B i ) and H P W i = h(P W i ||r i ).
-
2.
U i selects random numbers \(a,r_{i}^{new}\), calculates
$$\begin{array}{@{}rcl@{}} & C_{1}=&B_{1}\oplus h(HPW_{i}||ID_{i}) \\ & NID_{i}=&h(ID_{i}||r_{i}) \\ & C_{2}=&aP \\ & C_{3}=&E_{C_{1}}(ID_{i}||r_{i}||r_{i}^{new}) \\ & C_{4}=&h(C_{1}||C_{2}||ID_{i}||NID_{i}||r_{i}||r_{i}^{new}) \end{array} $$and sends M 1 = {C 2, C 3, C 4, N I D i } to S.
-
3.
After receiving M 1, S computes C 1 = h(N I D i ||X s ) and decrypts C 3 to get I D i , r i and \(r_{i}^{new}\). Then S checks N I D i ? = h(I D i ||r i ) and \(C_{4}?=h(C_{1}||C_{2}||ID_{i}||NID_{i}||r_{i}||r_{i}^{new})\). If either of them is wrong, the session is terminated. Moreover, if three errors for U i happen in a defined short time span, S will freeze U i ’s account. Otherwise, S selects a random number b, computes
$$\begin{array}{@{}rcl@{}} \,\,& NID_{i}^{new}=&h(ID_{i}||r_{i}^{new}) \\ & C_{5}=&h(NID_{i}^{new}||X_{s}) \\ & C_{6}=&bP \\ & C_{7}=&NID_{i}^{new}\oplus C_{5} \oplus r_{i} \\ & C_{8}=&bC_{2} \\ & sk_{s}=&h(C_{2}||C_{6}||C_{8}) \\ & C_{9}=&h(NID_{i}^{new}||C_{5}||C_{6}||C_{7}||sk_{s}||r_{i}) \end{array} $$and sends M 2 = {C 6, C 7, C 9} to U i . Finally S uses s k s as the session key.
-
4.
U i computes \(NID_{i}^{new}=h(ID_{i}||r_{i}^{new})\), \(C_{5}=NID_{i}^{new}\oplus C_{7}\oplus r_{i}\), C 8 = a C 6 and s k u = h(C 2||C 6||C 8) and checks \(C_{9}?=h(NID_{i}^{new}||C_{5}||C_{6}||C_{7}||sk_{u}||r_{i})\). If it is incorrect, U i rejects the session. Otherwise, U i computes \(HPW_{i}^{new}=h(PW_{i}||r_{i}^{new})\), \(B_{1}^{new}=C_{5}\oplus h(HPW_{i}^{new}||ID_{i})\) and \(B_{2}^{new}=H(PW_{i}||ID_{i}||B_{i})\oplus r_{i}^{new}\) and then replaces (B 1, B 2) with \((B_{1}^{new},B_{2}^{new})\) respectively. At last U i uses s k u as the session key.
Password change
-
1.
This step is the same as step 1 of the login and verification phase.
-
2.
U i selects a new random number \(r_{i}^{new}\), computes
$$\begin{array}{@{}rcl@{}} & C_{1}=&B_{1}\oplus h(HPW_{i}||ID_{i}) \\ & NID_{i}=&h(ID_{i}||r_{i}) \\ & C_{10}=&E_{C_{1}}(r_{i}^{new}||ID_{i}||r_{i}) \\ & C_{11}=&h(ID_{i}||NID_{i}||r_{i}||r_{i}^{new}) \end{array} $$and sends M 3 = {C 10, C 11, N I D i } with a password change request to S.
-
3.
S computes C 1 = h(N I D i ||X s ) and decrypts C 10 to obtain \(r_{i}^{new}\), I D i and r i . Then S checks N I D i ? = h(I D i ||r i ) and \(C_{11}?=h(ID_{i}||NID_{i}||r_{i}||r_{i}^{new})\). If either of them is wrong, the request will be rejected. Otherwise, S calculates
$$\begin{array}{@{}rcl@{}} & NID_{i}^{new} =&h(ID_{i}||r_{i}^{new}) \\ & C_{12}=& h(NID_{i}^{new}||X_{s}) \\ & C_{13}=&C_{12}\oplus h(r_{i}^{new}||r_{i}||NID_{i}||ID_{i}) \\ & C_{14}=&h(NID_{i}^{new}||C_{12}||h(r_{i}^{new}||r_{i}||NID_{i}||ID_{i})) \end{array} $$and sends M 4 = {C 13, C 14} with a grant to U i .
-
4.
U i computes \(NID_{i}^{new}=h(ID_{i}||r_{i}^{new})\) and \(C_{12}=h(r_{i}^{new}||r_{i}||NID_{i}||ID_{i})\oplus C_{13}\) and checks \(C_{14}?=h(NID_{i}^{new}||C_{12}||h(r_{i}^{new}||r_{i}||NID_{i}||ID_{i}))\). If it is right, U i is asked to input a new password \(PW_{i}^{new}\) and a new biometrics \(B_{i}^{new}\). Then the following computations happen:
$$\begin{array}{@{}rcl@{}} & HPW_{i}^{new}=&h(PW_{i}^{new}||r_{i}^{new}) \\ & B_{1}^{new}=&C_{12}\oplus h(HPW_{i}^{new}||ID_{i}) \\ & B_{2}^{new}=&H(PW_{i}^{new}||ID_{i}||B_{i}^{new})\oplus r_{i}^{new} \end{array} $$Finally, U i substitutes \((B_{1}^{new},B_{2}^{new})\) for (B 1, B 2) respectively.
Security analysis
In this section, we show that our scheme resists various attacks and keeps security characters. Also we compare the results with some recent schemes [1, 4, 21, 25, 28, 32] in Table 1.
Resistant to the insider attack
In the registration phase of our scheme, the user only submits a random identity N I D i to S. The malicious administrator can not get any information of the password or the identity from the submitted information. So our scheme can avoid this attack perfectly.
Resistant to the off-line guessing attack
At first A gets B 1, B 2 and P from U i ’s smart card and C 2, C 3, C 4, \(NID_{i}^{old}\), C 6, C 7 and C 9 in the last session from the channel. Obviously \(NID_{i}^{old}\) is U i ’s dynamic identity in the last session. According to Section 2, if A compromises P W i or B i , he can try to guess the third one. We suppose A gets B i and tries to break the privacy of P W i . A may guess a password P W ∗. Even if A obtains I D i by accident, he will compute r ∗ = B 2 ⊕ H(P W ∗||I D i ||B i ) and \(C_{5}^{*}=B_{1}\oplus h(h(PW^{*}||r^{*})||ID_{i})\). Only \(C_{7}=h(ID_{i}||r^{*})\oplus C_{5}^{*}\oplus r^{old}\) can be used, but A can not guess the random number r old. So A has no way to check if P W ∗ is right. Similar thing happens while A is trying to guess B i . Thus our scheme is robust to the off-line guessing attack.
Resistant to the user impersonation attack
Like Section Resistant to the off-line guessing attack, suppose A gets the data from U i ’s smart card with either P W i or B i , he may try to produce M 1 to login. However, A does not know I D i and it is hard for A to compute h(N I D i ||X s ) to produce C 1. Moreover, A has only three chances to try. So this attack will not affect our scheme.
Resistant to the server spoofing attack
If A wants to forge a message M 2, he must know X s to get r i and \(r_{i}^{new}\) from M 1. The two numbers are generated by U i and A can not forge them. However, X s is the secret key stored in S. So A has no ability to pretend to be a server.
Resistant to the replay attack
If A replays an old message \(M_{1}^{old}\) to S, S will generate a new C 6 in M 2. Thus A only knows \(C_{2}^{old}\) and faces ECCDH problem to compute the session key s k u and the session can not go on. If A replays an old \(M_{2}^{old}\), r i and \(r_{i}^{new}\) are incorrect. So A can not succeed by replaying old messages.
Resistant to the De-synchronization attack
This attack can be divided into three cases:
-
Our scheme employs the Biohashing function to cope with biometric information. The scheme can deal with the biometrics suitably. Here we must point out that Tan’s scheme in [25] does not use Biohashing function and it is under the De-synchronization attack, like Xie et al.’s [32].
-
In our scheme, S does not keep any verification table about the users. So changes of stored data only occur on the client side. Unlike Xie et al.’s scheme, S is not affected in the process.
-
Before changing password, U i is authenticated by S. The checking avoids inputting incorrect password by mistake.
User anonymity
It is clear that U i uses N I D i = h(I D i ||r i ) as a dynamic identity. r i is a new number for each session. A can not know the real identity I D i from N I D i . So our scheme makes user anonymous.
Light storage in server
In [4, 28, 32], there are verification tables in S. Furthermore, in [1], S stores the users’ identity list, and in [21], S stores the list of the users’ identity and registration time. They make the server store much more information than our scheme. While in our scheme, only X s and P are stored in S and the server is lightweight.
Strong forward security
According to [33], strong forward security means that even if all data owned by both session participants are stolen by A, A still can not compute the past session keys. The session key of our scheme is based on ECCDH problem. A can not get a b P from a P and b P, not to say s k u = s k s = h(a P||b P||a b P). So our scheme achieves strong forward security.
Performance comparison
We discuss the performance of our scheme in this section. First we list the time cost for referred cryptographic operations in Table 2. T m , T s and T h are tested on a laptop. T H is the result of Biohashing verification in [24]. And we add T eg , T mp , T mg and T i to make comparison with [1, 21]. Also, we demonstrate the lengths of parameters in Table 3. In Table 4, we list the comparison results between schemes in Table 1. Here we point out that papers [1, 21] both refer the comparison between the stored template and the input biometric information. The step needs some time. So the time cost on the client side is ”greater than” a lower bound in [1, 21], respectively.
From Table 4, we can see that
-
For the time of login and authentication phase, our scheme costs less time than [1, 25] on client side and less than [1, 25, 32] on the server side. The reason is that we employ scalar multiplication on elliptic curve which needs much more time than other cryptographic operations. Strictly speaking, the scheme in [21] has three modular exponentiations for each side while ours only has two scalar multiplications on the elliptic curve for each side. But [21] employs different problem basis. T m is much more than T e g . So it seems that [21] has the advantage with its time cost bound. Schemes in [4, 28] has no problem basis and they need much less time.
-
For the index of communication cost, our scheme is only better than [1, 21].
-
The quantity of transmitted messages for our scheme is lower than [1, 4, 28, 32] and same as [21, 25].
-
The most important thing is that our scheme satisfies all security properties in Table 1 while each of others has at least one disadvantage referred in Table 1.
So our scheme performs well among the schemes in Table 4.
Conclusion
In this paper, we point out that Xie et al’s scheme is under the De-synchronization attack and with heavy storage burden in server. We propose a new scheme to overcome the shortcomings. Through our analysis, it is secure and practical for Connected Health Care applications.
References
Arshad, H., and Nikooghadam, M., Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 38(12):136, 2014.
Cao, T., and Zhai, J., Improved dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):9912, 2013. doi:10.1007/s10916-012-9912-5.
Chen, H. M., Lo, J. W., Yeh, C. K., An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. J Med Syst 36(6):3907–3915, 2012.
Das, A. K., and Goswami, A., A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(3):9948 , 2013.
Fan, C. I., and Lin, Y. H., Provably secure remote truly three-factor authentication scheme with privacy protection on biometrics. IEEE Trans. Inf. Forensics Sec. 4(4):933–945, 2009.
Jiang, Q., Ma, J., Ma, Z., Li, G., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37(1):9897, 2013. doi:10.1007/s10916-012-9897-0.
Jin, A. T. B., Ling, D. N. C., Goh, A., Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern Recogn. 37(11):2245–2255, 2004.
Khan, M. K., and Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):9954 , 2013a.
Khan, M. K., and Kumari, S., An improved biometrics-based remote user authentication scheme with user anonymity. BioMed. Res. Int. 2013(2013):491289, 2013. doi:10.1155/2013/491289.
Khan, M. K., and Kumari, S., Cryptanalysis and improvement of an efficient and secure dynamic id-based authentication scheme for telecare medical information systems. Secur. Commun. Netw. 7(2):399–408, 2014a.
Khan, M. K., and Kumari, S., An improved user authentication protocol for healthcare services via wireless medical sensor networks. Int. J. Distrib. Sens. Netw. 2014(2014):347169, 2014.
Khan, M. K., Kumari, S., Gupta, M. K., More efficient key-hash based fingerprint remote authentication scheme using mobile device. Computing 96(9):793–816, 2014.
Kim, K. W., and Lee, J. D., On the security of two remote user authentication schemes for telecare medical information systems. J. Med. Syst. 38(5):17, 2014. doi:10.1007/s10916-014-0017-1.
Kocher, P., Jaffe, J., Jun, B., Differential power analysis. In: Advances in Cryptology(CRYPTO99), pp. 388–397: Springer, 1999.
Kumari, S., and Khan, M. K., Cryptanalysis and improvement of ’a robust smart-card-based remote user password authentication scheme’. Int. J. Commun. Syst. 27(12):3939–3955, 2014. doi:10.1002/dac.2590.
Kumari, S., and Khan, M. K., More secure smart card-based remote user password authentication scheme with user anonymity. Secur. Commun. Netw. 7(11):2039–2053, 2014. doi:10.1002/sec.916.
Kumari, S., Gupta, M.K., Khan, M. K., Li, X., An improved timestamp-based password authentication scheme: comments, cryptanalysis, and improvement. Secur. Commun. Netw. 7(11):1921–1932, 2014. doi:10.1002/sec.906.
Kumari, S., Khan, M. K., Kumar, R., Cryptanalysis and improvement of ’a privacy enhanced scheme for telecare medical information systems’. J. Med. Syst. 37(4):9952, 2013b. doi:10.1007/s10916-013-9952-5.
Kumari, S., Khan, M. K., Li, X., An improved remote user authentication scheme with key agreement. Comput. & Electr. Eng,. 40(6):1997–2012, 2014a.
Kumari, S., Khan, M. K., Li, X., Wu, F., Design of a user anonymous password authentication scheme without smart card. Int. J. Commun. Syst., 2014b. doi:10.1002/dac.2853.
Li, X., Wen, Q., Li, W., Zhang, H., Jin, Z., Secure privacy-preserving biometric authentication scheme for telecare medicine information systems. J. Med. Syst. 38(11):139, 2014.
Lin, H. Y., On the security of a dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):9929, 2013. doi:10.1007/s10916-013-9929-4.
Messerges, T. S., Dabbish, E. A., Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Nanni, L., and Lumini, A., Random subspace for an improved biohashing for face authentication. Pattern Recogn. Lett. 29(3):295–300, 2008.
Tan, Z., A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J. Med. Syst. 38(3):16, 2014. doi:10.1007/s10916-014-0016-2.
Wang, D., Wang, P., He, D., Anonymous two-factor authentication: Certain goals are beyond attainment. IEEE Trans. Dependable Secure Comput, 2014. doi:10.1109/TDSC.2014.2355850.
Wen, F., A robust uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(6):9980, 2013. doi:10.1007/s10916-013-9980-1.
Wen, F., and Guo, D., An improved anonymous authentication scheme for telecare medical information systems. J. Med. Syst. 38(5):26, 2014.
Wu, F., and Xu, L., An improved and provable self-certified digital signature scheme with message recovery. Int. J. Commun. Syst., 2013a. doi:10.1002/dac.2673.
Wu, F., and Xu, L., Security analysis and improvement of a privacy authentication scheme for telecare medical information systems. J. Med. Syst. 37(4):9958, 2013b. doi:10.1007/s10916-013-9958-z.
Xie, Q., Zhang, J., Dong, N., Robust anonymous authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):9911, 2013. doi:10.1007/s10916-012-9911-6.
Xie, Q., Liu, W., Wang, S., Han, L., Hu, B., Wu, T., Improvement of a uniqueness-and-anonymity-preserving user authentication scheme for connected health care. J. Med. Syst. 38(9): 91, 2014. doi:10.1007/s10916-014-0091-4.
Xu, L., and Wu, F., An improved and provable remote user authentication scheme based on elliptic curve cryptosystem with user anonymity. Secur. Commun. Netw., 2014. doi:10.1002/sec.977.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interests
The authors declare that they have no conflict of interest.
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Xu, L., Wu, F. Cryptanalysis and Improvement of a User Authentication Scheme Preserving Uniqueness and Anonymity for Connected Health Care. J Med Syst 39, 10 (2015). https://doi.org/10.1007/s10916-014-0179-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-014-0179-x