Abstract
Asymmetric entanglement could provide a crucial layered key structure for quantum cryptography. A new symmetrical tripartite quantum key distribution scheme based on the simplest layered quantum key distribution (L-QKD) model is devised. With an interesting rotational symmetrical key distribution scheme, the proposed tripartite QKD protocol could establish a more integrated key system, which expands the number of conference keys for secure broadcast and distribute layered secret keys among any legitimate participants simultaneously. The proposed scheme is more flexible, robust and efficient to guarantee the fairness among communication parties than the original L-QKD protocol, and our scheme also could be applied to encryption in the butterfly network precisely. Moreover, based on three asymmetric (4, 4, 2) entangled state, a novel symmetric (4, 4, 4) entangled state to implement L-QKD scheme is discussed. Finally, the security of L-QKD scheme is analyzed via information-theoretic proof.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Quantum key distribution (QKD) is the most concerned branch of quantum cryptography [1]. The goal of QKD is to allow authenticated parties to create a random and secure key under the quantum no-cloning theorem [2] or the non-classical properties of entanglement [3]. BB84 protocol [4], Ekert protocol [5] and several variations of these original protocols together with their security, have been widely investigated [6,7,8].
With the advent of QKD, entanglement has become a crucial resource as quantum information carrier frequently. Thus, substantial entangled states have been widely exploited in conventional entanglement-based QKD protocols [9,10,11] and quantum networks [12,13,14,15]. However, it is known that the dimension of quantum states plays a vital role on actual key rate, the robustness of such protocols against noise [16,17,18] and capability of tolerating quantum bit error [19]. Therefore, the generalization or preparation of multi-particle entanglement [20] and high-dimensional entanglement, especially high-dimensional multipartite entanglement becomes topical [21,22,23,24].
Surprisingly, multipartite high-dimensional quantum states are readily available in experiment [18]. A particular multipartite high-dimensionally entangled quantum state with multiple particles and high dimensions has been demonstrated experimentally [23]. Such a state has an asymmetric entanglement structure, which is not only significant in increasing the efficiency of quantum communication but also interesting for “layered” key structure. Based on this idea, a novel layered quantum key distribution (L-QKD) was proposed [18], where the asymmetric entangled states provide multiple keys between arbitrary agents simultaneously. However, it is noticed that the original layered key structure is powerless to guarantee the fairness among communication parties, since the particular nature of the asymmetric entanglement structure. To raise a more integrated key system, a new symmetrical tripartite quantum key distribution scheme is devised by adopting a rotational symmetrical layered key structure. Furthermore, the communication network via connections among the source party and agents also have been considered.
The paper is structured as follows: the idea behind the L-QKD protocol with the simplest mode is introduced in Sect. 2. Tripartite layered quantum key distribution scheme with rotational symmetrical key structure is presented in Sect. 3. Additionally, in Sect. 4, the strategy to connect the source party with agents is presented, and a simple application scenario is introduced briefly. A novel scheme via symmetric (4, 4, 4) entangled state to implement L-QKD is discussed in Sect. 5. In addition, the security analysis and a brief comparison with the original L-QKD protocol is arrived at in Sect. 6. Finally, a brief conclusion will be drawn in Sect. 7.
2 Ideal Tripartite L-QKD Protocol
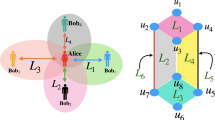
The model for tripartite layered quantum distribution is shown in Fig. 1(a). An authorized Source (S) distributes asymmetric entangled states for three agents, i.e., Alice (A), Bob (B) and Charlie (C). These asymmetric entangled states enable two parties to share an additional layer of secure information and build a conference key among all the three parties. Therefore, agents could share keys in two layers, i.e., KABC and kBC.
Tripartite layered quantum key distribution model. a In this model, an authorized Source (S) distributes asymmetric entangled states to three agents Alice (A), Bob (B), Charlie (C). Hence, two keys KABC and kBC could be shared among three agents simultaneously. KABC (blue area) is a conference key among three agents, while kBC (red dotted line) is a layered secret key only shared between B and C. b A novel asymmetric (4, 4, 2) entangled state \( \left|{\varPsi}_{442}\right\rangle =\frac{1}{2}\left(\left|000\right\rangle +\left|111\right\rangle +\left|220\right\rangle +\left|331\right\rangle \right) \) shared among three parties. Here the first two photons live in a four-dimensional space, while the third photon lives in a two-dimensional space
The first L-QKD protocol, as well as the first such an asymmetric (3, 3, 2) entangled state \( \left|{\varPsi}_{332}\right\rangle =\frac{1}{\sqrt{3}}\left(\left|000\right\rangle +\left|111\right\rangle +\left|221\right\rangle \right) \), was proposed in [14]. The local dimensions for |Ψ332〉 are 3 for the first two photons and 2 for the third photon. Since the idealized key rate based on |Ψ332〉 is not perfect in the first L-QKD protocol, recently, Pivoluska M, et al. proposed a simple motivating tripartite asymmetric (4, 4, 2) entangled state [18]. Such an ideal state \( \left|{\varPsi}_{442}\right\rangle =\frac{1}{2}\left(\left|000\right\rangle +\left|111\right\rangle +\left|220\right\rangle +\left|331\right\rangle \right) \) guarantees perfect idealized key rate and beautiful key structure, as shown in Fig. 1(b). Firstly, let us introduce the L-QKD protocol with the asymmetric (4, 4, 2) entangled state briefly.
- (a)
State preparation: Source S distributes |Ψ442〉 to three agents A, B and C, as shown in Fig. 1(b).
where the subscript BCA denotes that the first two particles are assigned to agents B and C, while the third particle is assigned to A.
- (b)
Measurement: After measuring the state |Ψ442〉BCA locally in the computational basis respectively, the outcomes of three agents will exhibit peculiar correlations: the outcomes of B and C (00, 11, 22, and 33) are correlated and independent of the ones of A (0 and 1).
- (c)
Key generation: Agents B and C could encode bit strings KABC and kBC according to their outcomes.
It is known that KABC is correlated to Alice’s measurement outcomes correctly and kBC is independent of Alice’s data entirely. On one hand, Alice, Bob and Charlie develop a conference key KABC, which has interesting secure broadcast applications. On the other hand, Bob and Charlie share a layered secret key kBC that is unknown to Alice.
- (d)
After parameter estimation and post-processing in raw keys, key strings could be used to encrypt messages among all three agents with one-time pad (OTP). More details can be found in [18].
In the L-QKD protocol, a layered key structure is more efficient in term of the number of quantum channels used. However, it is noticed that the power of the three-party agents to possess key information is unequal. In other words, the original layered key structure is incapable of guaranteeing the fairness among agents. For example, a secret layered key could be built only between Bob and Charlie in the above case, while distributing layered keys between Alice and Bob (Charlie) is not allowed.
To resolve this problem, an improved scheme with rotational symmetrical key structure could be considered.
3 Tripartite L-QKD Scheme with the Rotational Symmetrical Key Structure
To achieve fairness among three agents, first of all, three rounds of asymmetric entangled states are needed, as shown in Fig. 2.
Tripartite layered key distribution with rotational symmetrical structure. Here, after three rounds distribution shown in (a-c), all three parties could share three conference keys \( \left\{{K}_{ABC}^{R_1},{K}_{ABC}^{R_2},{K}_{ABC}^{R_3}\right\} \), at the same time, any two of parties could build a secure channel shared only among themselves equally shown in (d)
Formally, the authorized Source S produces three asymmetric (4, 4, 2) entangled states, then agents A, B and C share |Ψ442〉 states as shown in Fig. 2(a)-(c).
After processing the necessary L-QKD steps mentioned in Sect. 2, ideally, conference keys could be shared among three agents three times, and bipartite keys between any pairs of agents could be built simultaneously, as shown in Fig. 2(d). Thus, the key system for three agents is obtained, as listed in Table 1.
Therefore, the unfairness among three parties is overcome by using the rotational symmetrical key structure, where any two parties could build a layered secure channel to share bipartite keys only among themselves equally.
4 An Implementation Strategy for Connecting the Source Party with Agents
As is known, it is necessary to connect central source router with agents for building communication network. Therefore, to improve the integrity of system structure, the strategy connecting the source party with agents is presented in our scheme.
Apart from building a layered key structure in three agents as shown in Sect. II, similarly, the layered key structure among source party and agents is constructed, as shown in Fig. 3.
Note that the authorized Source S prepares six-round asymmetric (4, 4, 2) entangled states, and the entangled states are distributed as follows:
Likewise, after necessary L-QKD steps performed, a greater key system could be obtained, as shown in Table 2.
Conference keys for any tripartite have been shared, as well as layered secret keys for any bipartite. Thus key system grows more extensive and more integrated, which could enrich our symmetrical L-QKD scheme more flexible and more robust. Furthermore, this layered key system with central source could implement a quantum communication network. As an ideal application, our scheme will be discussed in the butterfly network [25,26,27] briefly.
Suppose Alice wants to send bits a and b to both Bob and Charlie. The classical case can be shown in Fig. 4(a). To ensure the security of bits a and b, an alternative encryption structure with asymmetric entangled states could be designed, as shown in Fig. 4(b).
The butterfly network. In the classical case, Alice wants to send bits a and b to both Bob and Charlie by employing the linear network code given by the transmitted symbols written onto the channels (⊕ means XOR) [6]. a Classical linear network. b An encryption structure with asymmetric entangled states
Firstly, the Source produces two asymmetric (4, 4, 2) entangled states for AC and AB, respectively, i.e., \( {\left|{\varPsi}_{442}\right\rangle}_{ACS}=\frac{1}{2}{\left(\left|000\right\rangle +\left|111\right\rangle +\left|220\right\rangle +\left|331\right\rangle \right)}_{ACS} \) and \( {\left|{\varPsi}_{442}\right\rangle}_{ABS}=\frac{1}{2}{\left(\left|000\right\rangle +\left|111\right\rangle +\left|220\right\rangle +\left|331\right\rangle \right)}_{ABS} \). As mentioned, the conference key KACS could be shared among Alice, Charlie and Source, so could KABS. Furthermore, the layered secret keys kAB and kAC could be distributed simultaneously. Hence, Alice possesses {KACS, KABS, kAB, kAC}, Bob and Charlie hold {KABS, kAB} and {KACS, kAC}, respectively.
Encryption: Alice encrypts bits a and b via bitwise XOR operation with her keys, i.e., a ⊕ kAC, (a ⊕ b) ⊕ KACS, b ⊕ kAB and (a ⊕ b) ⊕ KABS. Then Alice transmits the encrypted messages a ⊕ kAC and (a ⊕ b) ⊕ KACS to Charlie, while sends messages b ⊕ kAB and (a ⊕ b) ⊕ KABS to Bob.
Decryption: After receiving encoded messages, Charlie and Bob decrypt the bits with their keys respectively. i.e., Charlie computes kAC ⊕ (a ⊕ kAC) and KACS ⊕ ((a ⊕ b) ⊕ KACS), while Bob operates kAB ⊕ (b ⊕ kAB) and KABS ⊕ ((a ⊕ b) ⊕ KABS).
Therefore Charlie obtains bits a and a ⊕ b, while Bob obtains bits b and a ⊕ b. Performing simple XOR operation on their outcomes, i.e., a ⊕ (a ⊕ b) → b and b ⊕ (a ⊕ b) → a, both Bob and Charlie could receive bits a and b finally.
It is known that the security is guaranteed by the layered key structure and one-time pad encryption algorithm, even if the source is under the control of eavesdropper, only the result of a ⊕ b could be leaked.
5 A Symmetric L-QKD Scheme Via Symmetric (4, 4, 4) Entangled State
Apart from the above, another scheme to achieve fairness among three agents is discussed below. Based on three asymmetric (4, 4, 2) entangled state|Ψ442〉, a novel symmetric (4, 4, 4) entangled state |Ψ444〉 is considered for our protocol.
It is noted any individual agent could distribute the layered keys to others by the partially entangled states |0〉A/B/C ⊗ (|00〉 + |22〉)BC/AC/AB and |1〉A/B/C ⊗ (|11〉 + |33〉)BC/AC/AB, which is equal to the asymmetric (4, 4, 2) entangled state. Besides, the rest of entangled states |2〉A/B/C ⊗ (|20〉 + |02〉)BC/AC/AB and |3〉A/B/C ⊗ (|31〉 + |13〉)BC/AC/AB also could be of benefit to build conference keys. The implementation of the scheme is described briefly below.
Similarly, three agents A, B and C share N three symmetric (4, 4, 4) entangled states \( {\left|{\varPsi}_{444}\right\rangle}_{ABC}^{\otimes N} \). After performing measurements on the states in order, each of the eight possible combinations 000, 111, 220, 331, 202, 313, 022, 133 is distributed uniformly. Then three agents label the N outcomes with 0, 1, 2 and 3 individually.
Suppose they intend to achieve L-QKD scheme shown in Fig. 2(a), i.e., A, B and C share KABC while B and C share kBC secretly. In this case, firstly agent A only announces the labeled number of outcomes 0 and 1 publicly, then B and C picks up corresponding labeled particles from A's announcement, according to the correlation of |Ψ444〉 and the key generation in Sect. 2, three agents could implement the L-QKD scheme. Furthermore, the remaining unselected particles, could also be applied to generate conference key string KABC.
where KABC is correlated to agent’s measurement outcomes correctly. Similarly, after parameter estimation and post-processing in raw keys, key strings could be used to encrypt messages among all three agents with one-time pad (OTP). Moreover, it is easy to achieve fairness among three agents, for example, if agents desire to implement the scheme shown in Fig. 2(c), only few steps need to be changed, where B firstly announces the labeled number of outcomes 0 and 1 in his hand publicly, then A and C select the same marked particles to build the layered key structure.
It is noted that since only half outcomes of N entangled states |Ψ444〉 could contribute to L-QKD scheme, the implementation results of a three symmetric (4, 4, 4) entangled states in the idealized key rates are \( {R}_{K_{ABC}}=1 \) and \( {R}_{k_{AB}/{k}_{BC}/{k}_{AC}}=1/2 \).
6 Security Analysis and Comparison
As stated above, the proposed symmetrical tripartite quantum key distribution scheme is based on the L-QKD model (see Fig. 1). Therefore, the primary issue is the security of the L-QKD protocol, wherein the asymmetric (4, 4, 2) entangled state |Ψ442〉i, j, u, i, j, u ∈ {A, B, C}, is a crucial process.
It is known that |Ψ442〉i, j, u guarantees the key strings Ki, j, u and ki, j independently, i.e., I(Ki, j, u ; ki, j) = 0, and the idealized key rate of the L-QKD protocol could achieve 100%, which is better than the conventional EPR- and GHZ- QKD protocols. Here, by employing the composable security definition in [6], we principally discuss the security of the key under the most general eavesdropping attack, i.e., coherent attack [28].
Suppose that the agents i, j and u share N asymmetric (4, 4, 2) entangled states. The eavesdropper E is given to hold a purification of the global state. After performing respective computational measurement of three agents, the total quantum state is expressed by the density operator,
where the strings of measurement outcomes Mi, Mj and Mu of agents i, j and u, which occur with probability \( {P}_{K_i{k}_i,{K}_j{k}_j,{K}_u,E}\left({M}_i,{M}_j,{M}_u\right) \), are stored in key systems Kiki, Kjkj and Ku, respectively.
Similar to the classical post-processing in the bipartite scheme, in the error correction step, agent u pre-processes the random key string Ku according to the channel V ← Ku and sends classical error correction information W (W is same as three agents) to i and j, who calculate their individual guesses Vi and Vj for V from Ki, Kj and W. Moreover, in the privacy amplification step, agent u randomly chooses hash function h, computes his key Su = h(V) and announces the description of h, then i and j also perform Si = h(Vi) and Sj = h(Vj). Therefore, the total quantum state could be described as \( {\rho}_{S_i{S}_j{S}_u{E}^{\varepsilon }} \). As is known from [6], the key system (Si, Sj, Su) is called ε-secure, if it is ε-close to the ideal state, i.e., \( \mathrm{tr}\left|{\rho}_{S_i{S}_j{S}_u{E}^{\varepsilon }}-{\rho}_{SSS}\otimes {\rho}_{E^{\varepsilon }}\right|\le 2\varepsilon \).
According to [29], the length \( {\varsigma}_{K_{i,j,u}}^{(N)} \) of the conference key Ki, j, u generated from N asymmetric (4, 4, 2) entangled states will then be denoted as
where V ← Ku denotes a bitwise preprocessing channel on raw key bit Ku of agent u, \( {S}_{\alpha}^{\varepsilon}\left(\rho \right) \) is a smooth Rényi entropy, and the last term \( \underset{i,j}{\max }{H}_0^{\varepsilon}\left(\left.V\right|{K}_{i,j}\right) \) denotes the maximal leakage to eavesdropper in the error correction step.
Without considering parameter estimation step, for the limit N → ∞, the secret fraction \( {r}_{K_{i,j,u}}^{\infty } \)is given by
where S(V|E) is the conditional Von-Neumann entropy of the key variable, E denotes the system state of eavesdropper, H(V|Ki, j) is the conditional Shannon entropy, which denotes agents i and j's guess of Ku, and Γ is the set of all density matrices σi, j, u of all agents, which are consistent with the parameter estimation.
It is easy to access the length \( {\zeta}_{k_{i,j}}^{(N)} \) of the layer secret key ki, j and the secret fraction \( {r}_{k_{i,j}}^{\infty } \) between i and j, which are given by
Likewise, U ← ki denotes a bitwise preprocessing channel on agent i‘s raw key bit ki, H(U|kj) denotes agents j‘s guess of ki, and Λ is the set of all density matrices σi, j of agents i and j.
Finally, the conference secret key rate and the layer secret key rate are \( R={r}_{K_{i,j,u}}^{\infty }/{t}_{\mathrm{rep}} \) and \( R={r}_{k_{i,j}}^{\infty }/{t}_{\mathrm{rep}} \), respectively. Note that trep is the repetition time when one round protocol takes, generally we assume that trep = 1.
Additionally, to immune to the intercept-and-resend attack, extra techniques such as decoy state technique [30,31,32,34] could be used. In a practical implementation of the proposed scheme, the participants can also use of the methods given in [35, 36] to avoid the Trojan horse attack and in-visible-photon attack. The necessary post-processing, such as the parameter estimation results, error correction and privacy amplification, is inevitably involved.
With respect to the original L-QKD protocol, our rotational symmetrical L-QKD scheme has a more integrated key system, where one could perform authentication to resist dishonest participant attacks via the secure bipartite channel (i.e., kSA, kSB, kSC, kAB, kAC, kBC). Besides, our scheme enhances the capacity of the original layered key system by consuming more high-dimensional entangled states.
Herein, a brief comparison for the proposed protocols with the original L-QKD protocol is described.
For the rotational symmetrical L-QKD scheme in Sect. 3, a more integrated key system in a three-party case is established. Different from the original case, it exploits three rounds entanglement distribution to expand the type of keys from 2 (Kiju, kij) to 4 (Kiju, kij, kiu, kju), and all idealized key rates are 100% similarly. More importantly, this scheme is immune to the participant attack via the fairness key structure among three parties.
Moreover, for the symmetric L-QKD scheme in Sect. 5, the layered key structure could be accomplished by half outcomes by utilizing symmetric (4, 4, 4) entangled states. Compared with the original protocol, the fairness among three agents could be achieved. The idealized key rates are \( {R}_{K_{iju}}=1 \), \( {R}_{k_{ij}/{k}_{iu}/{k}_{ju}}=1/2 \). It should be pointed out that the tripartite layered key distribution with rotational symmetrical structure is an application of the original L-QKD protocol, but it enhances the quality of the final key system.
7 Conclusion
A new symmetrical quantum key distribution scheme for three parties based on layered key structure is proposed. To raise a more integrated key system and guarantee the fairness among communication parties, an interesting rotational symmetrical key structure is generalized. Moreover, the strategy to implement a quantum communication network via the layered key system with a central source is presented, which could be employed to encrypt information in the butterfly network correctly. Furthermore, according to the three asymmetric (4, 4, 2) entangled states, a novel symmetric (4, 4, 4) entangled state is discussed for our L-QKD scheme. It is easy to achieve fairness among three agents via a different method. Finally, the security of our scheme via information-theoretic proof is analyzed.
In summary, our scheme expands the number of conference keys for secure broadcast and distributes the bipartite keys for any two participants. Such high dimension entangled states could be used for many cryptographic tasks. Furthermore, the idea of layered key structure could be extended to other quantum information fields, such as semi-quantum key agreement [37], quantum group authentication [38], quantum-information splitting [39], continuous-variable quantum key distribution [39], quantum networks communication, and so forth.
References
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature. 299, 802 (1982)
Coffman, V., Kundu, J., Wootters, W.K.: Distributed entanglement. Phys. Rev. A. 61, 052306 (2000)
Bennett, C. H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. Proceedings of IEEE International Conference on Computers. Systems and Signal Processing. Bangalore, India, 175–179 (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991)
Epping, M., Kampermann, H., Bruß, D.: Multi-partite entanglement can speed up quantum key distribution in networks. New J. Phys. 19, 093012 (2017)
Scarani, V., Bechmann, P.H., Cerf, N.J.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM. 48, 351 (2001)
Greenberger, D.M., Horne, M.A., Shimony, A., Zeilinger, A.: Bell’s theorem without inequalities. Am. J. Phys. 58, 1131 (1990)
Schön, C., Solano, E., Verstraete, F.: Sequential generation of entangled multiqubit states. Phys. Rev. Lett. 95, 110503 (2005)
Huang, P., Huang, J., Zhang, Zeng, G.H.: Quantum key distribution using basis encoding of Gaussian-modulated coherent states. Phys. Rev. A. 97, 042311 (2018)
Acín, A., Cirac, J.I., Lewenstein, M.: Entanglement percolation in quantum networks. Nat. Phys. 3, 256 (2007)
Luo, M.X.: Computationally efficient nonlinear bell inequalities for quantum networks. Phys. Rev. Lett. 120, 140402 (2018)
Yang, Y., Yang, J., Zhou, Y., Shi, W., Chen, X.: Quantum network communication: a discrete-time quantum-walk approach. Science China Inf. Sci. 61, 042501 (2018)
Leung, D., Oppenheim, J., Winter, A.: Quantum network communication—the butterfly and beyond. IEEE Trans. Inf. Theory. 56, 3478 (2010)
Bechmann, P.H., Tittel, W.: Quantum cryptography using larger alphabets. Phys. Rev. A. 61, 062308 (2000)
Cerf, N.J., Bourennane, M., Karlsson, A., Gisin, N.: Security of quantum key distribution using d-level systems. Phys. Rev. Lett. 88, 127902 (2002)
Pivoluska, M., Huber, M., Malik, M.: Layered quantum key distribution. Phys. Rev. A. 97, 032312 (2018)
Wang, X.B.: Quantum key distribution with two-qubit quantum codes. Phys. Rev. Lett. 92, 077902 (2004)
Xiu, X.M., Li, Q.Y., Lin, Y.F., Dong, H.K., Dong, L., Gao, Y.J.: Preparation of four-photon polarization-entangled decoherence-free states employing weak cross-Kerr nonlinearities. Phys. Rev. A. 94, 042321 (2016)
Erhard, M., Malik, M., Krenn, M., Zeilinger, A.: Experimental GHZ entanglement beyond qubits. arXiv. 1708, 03881 (2017)
Hiesmayr, B.C., De Dood, M.J.A., Löffler, W.: Observation of four-photon orbital angular momentum entanglement. Phys. Rev. Lett. 116, 073601 (2016)
Malik, M., Erhard, M., Huber, M.: Multi-photon entanglement in high dimensions. Nat. Photonics. 10, 248 (2016)
Huber, M., de Vicente, J.I.: Structure of multidimensional entanglement in multipartite systems. Phys. Rev. Lett. 110, 030501 (2013)
Ahlswede, R., Cai, N., Li, S.Y., Yeung, R.W.: Network information flow. IEEE Trans. Inf. Theory. 46, 1204 (2000)
Epping, M., Kampermann, H., Bruss, D.: Robust entanglement distribution via quantum network coding. New J. Phys. 18, 103052 (2016)
Li, D., Gao, F., Qin, S., Wen, Q.: Perfect quantum multiple-unicast network coding protocol. Quantum Inf. Process. 17, 13 (2018)
Bechmann-Pasquinucci, H., Gisin, N.: Incoherent and coherent eavesdropping in the six-state protocol of quantum cryptography. Phys. Rev. A. 59, 4238 (1999)
Renner, R., Gisin, N., Kraus, B.: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A. 72, 012332 (2005)
Li, C.Y., Zhou, H.Y., Wang, Y.: Secure quantum key distribution network with bell states and local unitary operations. Chin. Phys. Lett. 22, 1049 (2005)
Lo, H.K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Lucamarini, M., Patel, K.A., Dynes, J.F.: Efficient decoy-state quantum key distribution with quantified security. Opt. Express. 21, 24550 (2013)
Xiu, X.M., Dong, L., Gao, Y.J.: Secure four-site distribution and quantum communication of χ− type entangled states. Opt. Commun. 284, 2065–2069 (2011)
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A. 74, 054302 (2006)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A. 351, 23–25 (2006)
Zhou, N.R., Zhu, K.N., Zou, X.F.: Multi-party semi-quantum key distribution protocol with four-particle cluster state. Ann. Phys. 531, 1970031 (2019)
Liao, L., Peng, X., Shi, J., Guo, Y.: Graph state-based quantum group authentication scheme. J. Phys. Soc. Jpn. 86, 024403 (2017)
Wang, X.W., Xia, L.X., Wang, Z.Y., Zhang, D.Y.: Hierarchical quantum-information splitting. Opt. Commun. 283, 1196–1199 (2010)
Chai, G., Cao, Z.W., Liu, W.Q., Wang, S.Y., Huang, P., Zeng, G.H.: Parameter estimation of atmospheric continuous-variable quantum key distribution. Phys. Rev. A. 99, 032326 (2019)
Acknowledgements
The authors would like to thank the anonymous reviewers for their valuable comments and suggestions that help improve the quality of this manuscript. This work is supported by the National Natural Science Foundation of China (Grant Nos. 61871205 and 61561033), the China Scholarship Council (Grant No. 201606825042), the Major Academic Discipline and Technical Leader of Jiangxi Province (Grant No. 20162BCB22011), and the Natural Science Foundation of Jiangxi Province (Grant No. 20171BAB202002).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhang, XH., Yan, XY., Wang, YQ. et al. Tripartite Layered Quantum Key Distribution Scheme with a Symmetrical Key Structure. Int J Theor Phys 59, 562–573 (2020). https://doi.org/10.1007/s10773-019-04349-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-019-04349-4