Abstract
Four methods of groundwater vulnerability mapping have been applied in a Slovene karst catchment and validated by tracer tests. The test site is characterised by high water table fluctuations, manifested in intermittent lakes and variable drainage divides. A first multi-tracer test (two injections) allowed subdivision of the catchment into zones of different degrees of contribution (‘inner zone’ and ‘outer zone’). For vulnerability mapping, only methods that consider the specific nature of karst aquifers such as heterogeneity and duality of infiltration processes, were selected: EPIK, PI, the ‘Simplified Method’ and the ‘Slovene Approach’. For validation, a second multi-tracer test (four injections) was carried out. The time of first detection and the normalised recovery were used as validation criteria. The results suggest that EPIK and the Simplified Method sometimes overestimate vulnerability, while PI and the Slovene Approach tend to deliver more realistic results, at least during low-flow conditions. The Slovene Approach gives the clearest guidance on how to deal with hydrologic variability, for example by assigning lower vulnerability to occasionally active sinking surface waters than to permanent ones. As a conclusion, commonly accepted validation techniques are needed and should be applied by default to evaluate different vulnerability mapping methods and the resulting maps.
Résumé
Quatre méthodes de cartographie de la vulnérabilité des eaux souterraines ont été appliquées sur un bassin karstique de Slovénie et validées par des tests de traçage. Le site expérimental est caractérisé par de fortes variations du niveau d’eau, qui se manifestent par des lacs intermittents et changements de limites de drainage. Le premier test multi-traceurs (deux injections) a permis de diviser le bassin en deux sous-bassins avec différents degrés de contribution (‘zone interne’ et ‘zone externe’). Pour la cartographie de la vulnérabilité, seules les méthodes qui considèrent la nature spécifique des systèmes karstiques, comme l’hétérogénéité et la dualité des processus d’infiltration, ont été sélectionnées: EPIK, PI, la Méthode Simplifié et l’approche Slovène. Pour la validation, un second test multi-traceurs (quatre injections) a été réalisé. Les temps de la première détection et de récupération ont été utilisés comme critères de validation. Les résultats suggèrent que EPIK et la méthode simplifiée surestiment quelques fois la vulnérabilité alors que PI et l’approche Slovène tendent à donner des résultats plus réalistes au moins en conditions de basses eaux. L’approche Slovène donne les plus clairs conseils sur la manière de gérer la variabilité hydrologique, par exemple en assignant une vulnérabilité plus basse aux eaux de surface occasionnelles qu’à celles permanentes. Comme conclusion, les techniques de validation communément acceptées sont nécessaires et doivent être appliqués par défaut pour évaluer les différentes méthodes de cartographie de la vulnérabilité et les cartes ainsi établies.
Kurzfassung
Vier Methoden zur Kartierung der Grundwasserverschmutzungsempfindlichkeit (Vulnerabilität) wurden in einem Karsteinzugsgebiet in Slowenien angewandt und durch Markierungsversuche validiert. Das Untersuchungsgebiet zeichnet sich durch starke Schwankungen des Grundwasserspiegels aus, die sich in intermittierenden Seen und variablen Wasserscheiden manifestieren. Ein Markierungsversuch mit zwei Eingaben ermöglichte eine Unterteilung in zwei Zonen, die unterschiedlich stark zur Quellschüttung beitragen (‘innere Zone’ und ‘äußere Zone’). Zur Vulnerabilitätskartierung wurden nur solche Methoden verwendet, die die speziellen Eigenschaften von Karstgrundwasserleitern berücksichtigen, wie beispielsweise Heterogenität und die Dualität von Infiltrationsprozessen: EPIK, PI, die Vereinfachte Methode und der Slowenische Ansatz. Zur Validierung wurde ein zweiter Markierungsversuch mit vier Eingaben durchgeführt. Die Zeit bis zum Ersteinsatz und der normierte Wiedererhalt wurden als Validierungskriterien verwendet. Die Ergebnisse legen nahe, dass EPIK und die Vereinfachte Methode die Vulnerabilität manchmal überschätzen, während PI und der Slowenische Ansatz tendenziell realistischere Werte liefern, zumindest bei Niedrigwasserbedingungen. Der Slowenische Ansatz gibt die klarsten Hinweise zur Bewertung hydrologischer Variabilität, beispielsweise indem gelegentlich aktiven Schwinden, an denen Oberflächengewässer im Untergrund versinken, eine geringere Vulnerabilität zugeordnet wird, als ständig aktiven. Eine Schlussfolgerung der Studie lautet, dass allgemein akzeptierte Validierungstechniken notwendig sind und standardmäßig angewandt werden sollten, um verschiedene Methoden zur Vulnerabilitätskartierung sowie die resultierenden Karten zu bewerten.
Resumen
Se aplicaron cuatro métodos de mapeo de la vulnerabilidad del agua subterránea en una Cuenca cárstica eslovena, y se validaron mediante ensayos de trazadores. El sitio de estudio está caracterizado por elevadas fluctuaciones de niveles freáticos, que se manifiestan en lagos intermitentes y divisorias de agua variables. Un primer ensayo con multi-trazadores (dos inyecciones) permitió dividir la cuenca en zonas con diferentes grados de contribución (‘zona interna’ y ‘zona externa’). Para el mapeo de la vulnerabilidad, se consideraron sólo métodos que tienen en cuenta la naturaleza cárstica del acuífero, tal como la heterogeneidad y la dualidad en los procesos de infiltración. Por ende se seleccionaron: EPIK, PI, el Método Simplificado y el Enfoque Esloveno. Para la validación se realizó un segundo ensayo multi-trazador (cuatro inyecciones). El tiempo hasta la primera detección y la recuperación normalizada fueron usados como criterios de validación. Los resultados sugieren que EPIK y el Método Simplificado a veces sobre estiman la vulnerabilidad, mientras que PI y el Enfoque Esloveno brindan resultados más realistas, al menos para condiciones de flujos bajos. El Enfoque Esloveno proporciona la guía más clara acerca de cómo manejar la variabilidad hidrológica, por ejemplo asignando una vulnerabilidad menor a las aguas superficiales que ocasionalmente disminuyen en comparación con aguas superficiales permanentes. En conclusión, las técnicas comúnmente aceptadas para validación son necesarias y deberían ser aplicadas por defecto para evaluar diferentes métodos de mapeo de la vulnerabilidad y los mapas resultantes.
摘要
将四种地下水脆弱性制图方法应用于斯洛文尼亚某喀斯特流域, 并通过示踪试验加以验证。试验场地地下水位波动很大, 显示为间歇湖和变动的分水岭。根据首次多元示踪试验 (两次注入) 将流域划分为具有不同贡献程度的子区 (“内区”或“外区”) 。脆弱性制图时只选用考虑喀斯特含水层特性 (如非均质性和入渗过程的二重性) 的方法 : EPIK、PI、简化方法和斯洛文尼亚方法。为进行验证, 实施了第二次多元示踪试验 (四次注入) 。以首次检出时间和归一化回收率作为验证标准。结果表明, EPIK和简化方法有时会高估脆弱性, 而PI和斯洛文尼亚方法则趋向于给出更为真实的结果, 至少在枯水径流情况下是如此。斯洛文尼亚方法为如何处理水文变化提供了最为清晰的引导, 例如, 对于偶尔发生快速下降的地表水体设置较永久性地表水体更低的脆弱性值。总之, 需要采用公认的验证技术对不同的脆弱性制图方法及其生成图件进行评估。
Resumo
Quatro métodos de cartografia de vulnerabilidade das águas subterrâneas foram aplicados numa bacia cársica da Eslovénia e validados através de ensaios com traçadores. O local estudado é caracterizado por grandes flutuações no nível freático, manifestadas em lagos intermitentes e divisórias de águas subterrâneas de localização variável. Um primeiro ensaio com traçadores múltiplos (duas injecções) permitiu a subdivisão da bacia em zonas de diferentes graus de contribuição (‘zona interior’ e zona exterior’). Para a cartografia da vulnerabilidade apenas foram seleccionados métodos que consideram a natureza específica dos aquíferos cársicos, como a heterogeneidade e a dualidade dos processos de infiltração: EPIK, PI, Método Simplificado (Simplified Approach) e Método Esloveno (Slovene Approach). Para validação, foi realizado um segundo ensaio com traçadores múltiplos (quatro injecções). O tempo da primeira detecção e a recuperação normalizada foram utilizados como critérios de validação. Os resultados sugerem que o método EPIK e o Método Simplificado por vezes sobrestimam a vulnerabilidade, enquanto o método PI e o Método Esloveno tendem a produzir resultados mais realistas, pelo menos durante períodos de escoamento reduzido. O Método Esloveno fornece as indicações mais claras sobre como abordar a variabilidade hidrológica, por exemplo atribuindo menor vulnerabilidade a zonas de infiltração ocasional de água superficiais do que a zonas de infiltração permanente. Como conclusão, técnicas de validação de aceitação generalizada são necessárias e devem ser aplicadas para avaliar diferentes métodos de cartografia e os mapas de vulnerabilidade resultantes.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
In many countries or regions, karst groundwater is a valuable source of water for drinking, irrigation and other agricultural and industrial use. However, the special character of karst aquifers such as rapid infiltration and transport over long distances, makes them more vulnerable to contamination than other hydrogeological environments. Therefore, karst groundwater requires appropriate and careful managing.
The concept of groundwater vulnerability mapping represents a basis for protection zoning and land-use planning, as it helps to find a balance between water protection on one hand and economic interests on the other hand. Groundwater vulnerability cannot be measured or directly obtained in the field (Vrba and Zaporozec 1994). Vulnerability maps are simplifications of natural conditions and their reliability is influenced by the availability, quality and interpretation of the data.
Several studies have already shown that whenever different methods are tested in the same area, using the same database, the resulting maps were different and sometimes contradictory. Therefore, it is debatable, which method produces the most reliable and consistent results (Gogu and Dassargues 2000; Gogu et al. 2003; Neukum and Hötzl 2007).
Some of the most frequently used methods, like DRASTIC (Aller et al. 1987), GOD (Foster 1987), AVI (Van Stempoort et al. 1993) and SINTACS (Cività and De Maio 1997) do not provide tools for karst groundwater vulnerability assessment. For example, these methods do not consider the existence of allogenic recharge and infiltration into swallow holes. The application of these methods to karst can thus lead to inappropriate protection zoning (Gogu et al. 2003; Goldscheider 2005).
The first method taking into account the specific properties of karst was EPIK (Doerfliger and Zwahlen 1998; Doerfliger et al. 1999). Later on, COST Action 620 proposed a “European approach to vulnerability and risk mapping for the protection of karst aquifers” (Daly et al. 2002; Zwahlen 2004). Several methods of intrinsic vulnerability mapping were developed within this framework such as the PI method (Goldscheider et al. 2000), which served as a basis for the conceptual model of the European Approach, and the COP Method, a fairly complete implementation of this approach (Vías et al. 2006). Recently, Nguyet and Goldscheider (2006) proposed a simplified methodology of vulnerability and risk mapping for the application in data-poor environments; Ravbar and Goldscheider (2007) developed a more detailed methodology for the application in Slovene karst areas. These two methodologies include guidelines for vulnerability, hazard and risk assessment; the Slovene Approach also considers the value or importance of a groundwater source or resource.
In a Slovene karst catchment, four different methods of intrinsic vulnerability mapping were applied using the same database. The maps were validated by means of tracer tests. For the delineation and characterisation of the catchment and for vulnerability assessment, a comprehensive investigation program was carried out, including detailed structural, lithological and geomorphological mapping, geophysical surveys (electrical resistivity imaging), a first multi-tracer test with two injection sites, and continuous monitoring of spring discharge and physicochemical parameters. Only vulnerability mapping methods that consider the specific nature of karst aquifer systems were used: EPIK, the Simplified Method, PI and the Slovene Approach, ranging from relatively simple to sophisticated. Finally, a second multi-tracer test with four different injection sites was carried out in order to simulate the impact of a contaminant release on the spring water quality and so to validate the vulnerability assessment provided by the different methods and maps.
The practical, site-specific purpose of this study was to provide optimum water protection zones in the catchment of the studied water source, which is used for local drinking water supply. However, the broader scientific goal was to test and compare the four different methods and the resulting maps, and to validate the vulnerability assessment by verifying the previsions provided by the maps with the results of simulated contaminant releases.
Description of the test site
The test site is the catchment of the Podstenjšek springs (525 m) in the Upper Pivka valley in southwestern Slovenia and covers an area of about 9 km2. A detailed geomorphological and hydrogeological description of the test site can be found in Ravbar (2007). The springs are located at the contact between carbonate rock and flysch. There are five permanent springs and numerous small overflows which join in a common stream flowing into the Reka River after about 3 km. One of the springs is used for local drinking water supply.
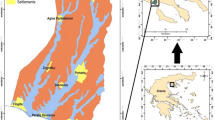
The catchment occupies moderately karstified Cenomanian limestones and breccias, as well as Palaeocene limestones that are thrusted over impermeable Eocene flysch (Šiki and Pleničar 1975). The thrust is clearly expressed in a geomorphological step which in places rises 200–400 m above the Reka River. A tectonic window near Knežak village, where Palaeocene limestone surrounds flysch, confirms the thrust structure (Fig. 1).
Generalized geological map of the studied area, location of the injection sites of the two multi-tracer tests during high-water (A, B) and low-water conditions (1–4) and proven connections. t1 time of first tracer detection, R tracer recovery. The first tracer test made it possible to delimitate the inner zone and outer zone of the spring catchment; the second tracer test was used to validate the vulnerability maps (Map based on DMR 12.5, Surveying and Mapping Authority of the Republic of Slovenia, 2005, modified after Šiki and Pleničar 1975; Ravbar and Goldscheider 2007)
The shallow karst aquifer is characterised by fast and strong responses to precipitation and snowmelt. The water table fluctuates several tens of metres in a short time period, which can be observed in a water cave near the springs. There is no permanent surface stream in the catchment, but there are two intermittent lakes, Šembijsko Jezero (559 m) and Nariče (571 m). When groundwater level is rising, water pours out through innumerable fissures and voids at the bottoms or edges of these two depressions. In periods of water level decrease, it sinks underground through the same fissures and voids, which consequently act as small estavelles. However, the lakes do not show systematic periodicity. Their appearance does not only depend on the quantity of precipitation, but also on the previous groundwater level and saturation of the soils. The lower lying Šembijsko Jezero appears a few times per year, but remains empty in dry years, whereas the appearance of the Nariče has only been observed twice during the twentieth century (Kovačič and Habič 2005).
In the area of the intermittent lakes, alluvial deposits can be found. In the uplifted dry valley at the southeastern outskirts of the catchment, periglacial material fills the dolines. The thickest soils can be found in the bottom of dolines, while the rest of the surface is rocky. Forest and meadows cover most of the area, and low-intensity agriculture prevails. The annual precipitation ranges between 1,500 and 1,600 mm, relatively equally distributed throughout the year.
For catchment delineation, a tracer test during high-water conditions was performed (Ravbar 2007; Ravbar and Goldscheider 2007). The results proved the connections between Šembijsko Jezero (injection point A in Fig. 1) and the area below Milanka Mountain (B) with the Podstenjšek springs. However, the tracer recoveries demonstrate that the area below Milanka Mountain (948 m), which is morphologically uplifted, only contributes a small portion to the Podstenjšek springs, but is directly connected to and mainly drained by the nearby Bistrica spring (420 m).
Based on these observations, the catchment was subdivided into an ‘inner zone’ and an ‘outer zone’. The inner zone is the area that always contributes to the investigated spring and is directly connected to and drained by the spring. The outer zone comprises the morphologically uplifted part of the area that contributes only a small portion of the spring discharge, as well as the parts where it is not clear if they contribute to the Podstenjšek springs or not (Fig. 1).
Vulnerability mapping
Overview of the four methods
The four applied methods of groundwater vulnerability assessment are based on different type of information about the soil and unsaturated zone, recharge conditions and aquifer characteristics. This information is categorized in different factors. Their nomenclature differs and they require diverse data sources and different amount of input data (Table 1).
The EPIK method (Doerfliger and Zwahlen 1998; Doerfliger et al. 1999) takes into account four factors: epikarst development (E), protective cover (P), infiltration conditions (I) and karst network development (K). Each factor is given a ranking index, and a weighting coefficient is then attributed to each of the indexed factors according to their degree of protection. EPIK can only be used in karst areas.
The PI method (Goldscheider et al. 2000) considers the protective function of the layers above the saturated zone (P) and the infiltration conditions (I). The P factor is applicable for all type of aquifers and is based on an assessment scheme initially proposed by Hölting et al. (1995), while the I factor accounts for the karst specific recharge and infiltration processes.
The Simplified Method (Nguyet and Goldscheider 2006) has been developed for mapping groundwater vulnerability, hazards and risk in areas with limited data and economic resources, particularly Vietnam or other developing countries. The vulnerability assessment is based on the same two factors as the PI method (although the naming is different): overlying layers (O) and concentration of flow (C). The required amount of data has been reduced and the assessment scheme simplified.
The Slovene Approach (Ravbar 2007; Ravbar and Goldscheider 2007) is so far the most complete interpretation of the European approach. It can be used for vulnerability mapping and also includes an assessment of contamination hazards, an evaluation of the importance or value of the groundwater, and different types of risk maps. Groundwater vulnerability mapping is founded on the assessment of all four factors proposed by the European COST Action 620 (Daly et al. 2002): overlying layers (O), concentration of flow (C), precipitation regime (P) and karst saturated zone (K).
Adaptation and application of the methods
There are two general approaches to groundwater protection and vulnerability mapping: resource protection aims to protect the entire aquifer, and the resource vulnerability map consequently considers the vertical percolation of water and contaminants from the land surface (origin) through the unsaturated zone (pathway) towards the water table (target); source vulnerability assessment focuses on a particular spring or well and additionally considers the lateral pathway within the saturated zone (Daly et al. 2002).
EPIK and the Slovene Approach have been developed for source vulnerability mapping, while PI and the Simplified Method are made for resource vulnerability assessment (Table 1). In order to enable comparison among the resulting maps, these methods were extended for source vulnerability assessment by including a K factor, which considers the characteristics of groundwater flow in the saturated zone of the aquifer towards a well or spring. For PI, the same K factor that is used in the Slovene Approach was applied, because both methods use a similar conceptual model and require a comparable amount of data.
For the Simplified Method, a simplified K factor is proposed, which considers two aspects: first, differentiation between aquifers that are karstified and those that are only fractured; second, the catchment can be subdivided into an inner zone and an outer zone. The inner zone is the area that always, directly and fully contributes to the spring; the outer zone includes areas that are only temporally or indirectly connected to the spring, areas where a connection is not clear and very remote parts of the aquifer system. In many typical karst settings, the entire catchment will belong to the inner zone. The source vulnerability map is obtained by combining resource vulnerability (after Nguyet and Goldscheider 2006) and the K factor (Fig. 2).
Assessment scheme for source vulnerability, which is obtained by combining resource vulnerability (after Nguyet and Goldscheider 2006) and the simplified K factor
Evaluation of the protective function of the layers overlying the groundwater (E and P or O factors, respectively), was based on information from geological and soil maps and verified in the field by means of detailed structural, lithological and geomorphological mapping, as well as soil and sediment depth measurements using hand auger and electrical resistivity tomography. Additional information was obtained from topographic maps, digital orthographic photographs and the national cave database. The thickness of the unsaturated zone was determined by subtracting the grid of the estimated groundwater level from the grid of the digital elevation model.
The infiltration conditions and concentration of flow (I or C factors, respectively) were evaluated on the basis of the digital elevation model, topographic maps and land use database. Flow processes were assessed by means of geological information and direct field observations. For the precipitation and recharge characteristics, the yearly and daily precipitation and evaporation data were used.
The K factor, characterising groundwater flow in the saturated zone of the karst aquifer, was assessed on the basis of geological and geomorphological characteristics, hydrograph analyses of the springs and interpretation of the first multi-tracer test. Additional information was gained from the national cave database. For complete investigation techniques, results and maps see Ravbar (2007).
Comparison of the resulting maps
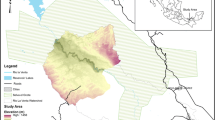
The four resulting vulnerability maps show some similarities as well as notable differences (Figs. 3 and 4). The EPIK map shows large areas (93%) classified as moderately vulnerable. High vulnerability is mostly assigned to dolines, karren, fractured areas and outcrops along roads, occupying 5% of the total area. Extreme vulnerability is assigned to the estavelle at the bottom of the Šembijsko Jezero and the lake itself, and to some other small patches. Altogether, extreme vulnerability occupies 1.9% of the total area. Low vulnerability occupies only 0.01%.
Source vulnerability maps obtained with the a EPIK, b PI, c Simplified Method and d Slovene Approach; the map prepared according to the Slovene Approach is taken from Ravbar and Goldscheider (2007)
According to the PI map, high vulnerability areas embrace 6.2% of the catchment in the inner zone where groundwater is shallow and not protected by sediments or soil, as well as the area above the active cave conduit, the Šembijsko Jezero and its estavelle. The bare karst areas or areas of insignificant soil cover within the inner zone, and with shallow unsaturated zone within the outer zone, covering 40.4% of the catchment are moderately vulnerable. Low vulnerability is assigned to areas of thicker unsaturated zone, soil or sediment cover. Within the outer zone, also karst areas with patchy soils are of low vulnerability, which, altogether, covers 53.3% of the catchment.
On the map pertaining to the Simplified Method, areas of extreme vulnerability occupy 1.4% and extend over the Šembijsko Jezero and the estavelle. Most of the catchment area (54.6%) is classified as highly vulnerable and corresponds to the karst covered by shallow soils within the inner zone. Moderate vulnerability, extending over 42.7% of the catchment, occupies dolines and the Nariče within the inner zone, as well as most of the outer zone except the dolines filled with soil and periglacial deposits. These are classified as low vulnerability covering 1.2% of the catchment.
The Slovene Approach classifies only 0.5% of the catchment as highly vulnerable. These areas correspond to karst geomorphological features, including the estavelle at the bottom of the Šembijsko Jezero. Moderate vulnerability embraces most of the inner zone, as well as karren and dry valleys in the outer zone. Low vulnerability is assigned to the areas covered by sediments or soil and to the rest of the outer zone. Moderate vulnerability extends over 46.5% and low vulnerability over 53% of the area.
Validation
Conceptual basis and proposed method
Vulnerability maps can serve as a basis for protection zoning and land use restrictions, which often go along with equalisation payments to farmers. Therefore, a vulnerability map should be reliable, and that can only be checked by validating it. However, until now, validation has not been a standard practice and there is no commonly accepted method.
Various validation techniques exist: hydrographs, chemographs, bacteriological analyses, tracer techniques, water balances, numerical simulations and analogue studies (Daly et al. 2002; Gogu et al. 2003; Neukum et al. 2008). Artificial tracers can be considered as surrogates for contaminants and are consequently the most straightforward and most commonly used validation technique. Goldscheider et al. (2001) proposed and applied three criteria for the validation of vulnerability maps that can be obtained from tracer breakthrough curves: peak time, recovery (R), and maximum concentration normalised by the injected tracer mass (c/M). Jeannin et al. (2001) proposed to use the duration of tracer appearance above a critical concentration threshold as an additional criterion. Perrin et al. (2004) and Andreo et al. (2006) also used tracers for the validation of vulnerability maps.
These approaches have some minor drawbacks:
-
The time of first arrival is often more relevant for problems of water contamination (on the other hand, it depends on the detection limit, while peak time is a more robust parameter);
-
R and c/M are interdependent
-
R is directly proportional to the spring discharge Q
-
The duration of tracer appearance depends on many other aspects that are difficult to control, e.g. the employed injection and flushing techniques
Therefore, here it is proposed to use only two modified validation criteria: the time of first tracer detection, and the normalized tracer recovery R N, which is defined as:
This is a way of expressing tracer recovery independent of spring discharge. When R N is used for validation, the same degree of vulnerability would be attributed to a small spring and to a large spring if the tracer breakthrough curves at both springs were similar, i.e. similar maximum concentrations and shape of the curve. High normalized tracer recoveries and short transit times indicate high groundwater vulnerability, while lower normalized recoveries and longer transit times mean a lower degree of vulnerability (Ravbar and Goldscheider 2007).
Evaluation of the vulnerability maps
By carrying out the second multi-tracer test in the studied area, the four vulnerability maps were examined and additional information on the mechanism of potential contaminant transport was gained.
The injections were carried out in November 2006 under low-water conditions (Ravbar and Goldscheider 2007). Four tracers were injected at four locations (see Fig. 1). On the bottom of the Šembijsko Jezero, 500 g of uranine was spread over several metres of thick soil and sediment cover (injection site 1). This area is indicated as extremely or highly vulnerable on three of the four vulnerability maps, because it contributes to the estavelle (swallow hole) draining the lake during periods of falling water table. Only the Slovene Approach classifies it as an area of low vulnerability, because this situation occurs only occasionally (most of the year, the lake and estavelle are dry).
Over the Nariče, where soil and sediments occur in pockets and the limestone outcrops in places, 400 g of sulforhodamine G was spread (injection site 2). For this area, significantly different results were obtained: EPIK classifies it as highly vulnerable and the Simplified Method as moderately vulnerable, whereas PI and the Slovene Approach classify it as of low vulnerability.
Two tracers were spread over the limestone surface, partially covered by scarce soil and vegetation cover. A total of 5 kg of lithium chloride (LiCl) was released at injection site 3, and 5 kg of potassium iodide (KI) at injection site 4. EPIK classifies both areas as moderately vulnerable. PI and the Slovene Approach classify injection site 3 as of low vulnerability, whereas the Simplified Method classifies it as moderate vulnerability. PI and the Slovene Approach classify the injection site 4 as moderately vulnerable and the Simplified Method as highly vulnerable. The fluorescent dyes were analysed by spectorfluorometry, iodide was analysed by an iodide-specific probe and lithium was analysed by means of ICP-MS.
At the Podstenjšek springs, only iodide, used in injection site 4, was detected. It was first detected 2 days after the injection and its appearance lasted for additional 2 days with maximal concentration of 3.2 μg/L. Altogether, 0.63% of the injected iodide was recovered. Lithium was only detected in the Pivka spring (558 m) and even after 6 months of sampling no fluorescent tracers were detected in any of the observed springs.
The tracer breakthrough curve at the Podstenjšek spring was evaluated based on the proposed validation concept. Thus, injection site 4 was validated as moderately vulnerable. The tracer injected there rapidly reached the spring, the concentrations were high, but the recovered quantity was very low. Injection sites 1, 2 and 3 were evaluated as zones of low vulnerability. The tracers injected in these areas did not arrive at the observed spring (Fig. 5).
Summary and conclusions
The applied methods of karst groundwater vulnerability mapping take into account similar factors that control the infiltration of water and contaminants from the land surface towards the source. However, their application to a test site in Slovenia shows that they produce different results. The main difference concerns the consideration of temporal hydrologic variations, which have important implications for contaminant transport. In the test site, large fluctuation of the groundwater level in response to hydrologic conditions result in variable catchment boundaries and induce intermittent lakes. However, previously existing methods, including EPIK, PI and the Simplified Method, do not sufficiently address hydrologic variability.
EPIK provides vague guidelines on temporal hydrologic variations, whereas PI and the Simplified Method use the concept of “predominant flow processes” considering average storm rainfall conditions. Consequently, these methods classify frequently or permanently active swallow holes, sinking streams and their catchments as zones of high or extreme vulnerability, but have no clear guidance how swallow holes and sinking streams active only during exceptional events should be classified. Therefore, there is some degree of subjective judgement. Conversely, the Slovene Approach integrates temporal hydrological variability by reducing vulnerability in dependence on frequency and duration of sinking water.
Variable flow rates and drainage divides are crucial for source vulnerability mapping. This issue is considered in the recently proposed K factor (Ravbar and Goldscheider 2007), which distinguishes between an inner zone that is always or most often part of the catchment area, and an outer zone that contributes only during extreme events (the K factor also considers other aspects).
The maps differ also in other details. EPIK is the only method that classifies karst zones covered by shallow soils as less vulnerable than dolines covered with thick soils and sediments. The validation demonstrated that this assessment is inappropriate, at least in the studied test site and during low-water conditions.
In comparison to other maps, the PI map shows a higher percentage of highly vulnerable areas due to the classification of the unsaturated zone thickness. Furthermore, EPIK and the Slovene Approach give high importance to karst geomorphological features as zones of preferential infiltration, whereas PI and the Simplified Method do not.
Simple methods (e.g. EPIK, Simplified Method) frequently require only general information and the number of considered parameters is reduced. Such methods enable rapid applications, are more flexible but also more subjective. The present study shows that, in general, the results obtained by EPIK and the Simplified Method suggest higher degrees of vulnerability as validated by the multi-tracer test during low-flow conditions at the representative sites.
On the contrary, the usage of sophisticated methods (e.g. PI, Slovene Approach) may be more legitimate if more data, time, financial and technical resources are available. As pertains to this study, PI gives satisfactory results and shows higher vulnerability as validated only at one site. The newly proposed Slovene Approach gives the most reliable results, at least during low-water conditions: the validation confirmed the vulnerability assessment at all representative sites that were selected for tracer injection. The tracers injected in sites of occasional direct infiltration during low-flow conditions were not detected in any of the springs, but were absorbed by the soil and sediments, while the tracer injected in karst surface covered by scarce soil and vegetation arrived at the springs in a short time period. The tracer injected in the outer zone was not detected in the investigated spring.
However, the maps were only validated under low-flow conditions. In karst systems, much higher flow and transport velocities, and also higher maximum contaminant concentrations, may occur under high-flow conditions (e.g. Göppert and Goldscheider 2008). Therefore, the Slovene Approach may not be entirely valid for high-flow conditions. Additional experiments such as repeated tracer tests under high-flow conditions using the same injection points, would be required to better evaluate the different maps and methods.
In some countries, vulnerability mapping is used according to law for protection zoning, e.g. Switzerland (mainly for karst aquifers) and Ireland (for all type of aquifers). Since protective measures result in land-use restrictions and equalisation payments, the vulnerability assessment needs to be reliable. To avoid subjectiveness in vulnerability assessment and to ensure reliable interpretation of vulnerability indices, the validation of vulnerability maps should be done by default. Therefore, common validation procedures such as the one applied in this report, should be employed.
References
Aller L, Bennett T, Lehr JH, Petty RH, Hackett G (1987) DRASTIC: a standardised system for evaluating groundwater pollution potential using hydrogeologic settings. US Environmental Protection Agency, Oklahoma City, OK, 622 pp
Andreo B, Goldscheider N, Vadillo I, Vías JM, Neukum C, Sinreich M, Jiménez P, Brechenmacher J, Carrasco F, Hötzl H, Perles JM, Zwahlen F (2006) Karst groundwater protection: first application of a Pan-European approach to vulnerability, hazard and risk mapping in the Sierra de Líbar (southern Spain). Sci Total Environ 357:54–73
Cività M, De Maio M (1997) SINTACS: un sistema parametrico per la valutazione e la cartografia della vulnerabilita degli acquiferi all’inquinamento: metodologia e automatizzazione [SINTACS: a parametric system for the assessment and mapping of the groundwater vulnerability to contamination: methodolgy and automation]. Pitagora, Bologna, 208 pp
Daly D, Dassargues A, Drew D, Dunne S, Goldscheider N, Neale S, Popescu IC, Zwahlen F (2002) Main concepts of the “European approach” to karst-groundwater-vulnerability assessment and mapping. Hydrogeol J 10:340–345
Doerfliger N, Zwahlen F (1998) Practical guide: groundwater vulnerability mapping in karstic regions (EPIK). Swiss Agency for the Environment, Forests and Landscape, Bern, 56 pp
Doerfliger N, Jeannin PY, Zwahlen F (1999) Water vulnerability assessment in karst environments: a new method of defining protection areas using a multi-attribute approach and GIS tools (EPIK method). Environ Geol 39(2):165–176
Foster S (1987) Fundamental concepts in aquifer vulnerability, pollution risk and protection strategy. In: Van Duijvenbooden W, Van Waegeningh HG (eds) Vulnerability of soil and groundwater to pollutants. TNO Committee on Hydrological Research, The Hague, pp 69–86
Gogu RC, Dassargues A (2000) Current trends and future challenges in groundwater vulnerability assessment using overlay and index methods. Environ Geol 39(6):549–559
Gogu RC, Hallet V, Dassargues A (2003) Comparison of aquifer vulnerability assessment techniques: application to the Neblon River basin (Belgium). Environ Geol 44(8):881–892
Goldscheider N (2005) Karst groundwater vulnerability mapping: application of a new method in the Swabian Alb, Germany. Hydrogeol J 13:555–564
Goldscheider N, Klute M, Sturm S, Hötzl H (2000) The PI method: a GIS-based approach to mapping groundwater vulnerability with special consideration of karst aquifers. Z Angew Geol 46(3):157–166
Goldscheider N, Hötzl H, Fries W, Jordan P (2001) Validation of a vulnerability map (EPIK) with tracer tests. In: Mudry J, Zwahlen F (eds) 7th Conference on Limestone Hydrology and Fissured Media, Besançon, France, 20–22 September 2001, University de Franche-Comté, Besançon, pp 167–170
Göppert N, Goldscheider N (2008) Solute and colloid transport in karst conduits under low- and high-flow conditions. Ground Water 46(1):61–68
Hölting B, Haertlé T, Hohberger KH, Nachtigall KH, Villinger E, Weinzierl W, Wrobel JP (1995) Konzept zur Ermittlung der Schutzfunkzion der Grundwasserüberdeckung [Concept for the determination of the protective function of the layers overlying the aquifer]. Geol Jb C63:5–20
Jeannin PY, Cornaton F, Zwahlen F, Perrochet P (2001) VULK: a tool for intrinsic vulnerability assessment and validation. In: Mudry J, Zwahlen F (eds) 7th Conference on Limestone Hydrology and Fissured Media, Besançon, France, 20–22 September 2001, University de Franche-Comté, Besançon, pp 185–190
Kovačič G, Habič Š (2005) Karst periodical lakes of Pivka (SW Slovenia) during high waters in November 2000. Acta Carsol 34(3):619–649
Neukum C, Hötzl H (2007) Standardization of vulnerability maps. Environ Geol 51:689–694
Neukum C, Hötzl H, Himmelsbach T (2008) Validation of vulnerability mapping methods by field investigations and numerical modelling. Hydrogeol J 16(4):641–658
Nguyet VTM, Goldscheider N (2006) A simplified methodology for mapping groundwater vulnerability and contamination risk, and its first application in a tropical karst area, Vietnam. Hydrogeol J 14:1666–1675
Perrin J, Pochon A, Jeannin PY, Zwahlen F (2004) Vulnerability assessment in karstic areas: validation by field experiments. Environ Geol 46:237–245
Ravbar N (2007) Vulnerability and risk mapping for the protection of karst waters in Slovenia: application to the catchment of the Podstenjšek springs (in English). PhD Thesis, University of Nova Gorica, Slovenia
Ravbar N, Goldscheider N (2007) Proposed methodology of vulnerability and contamination risk mapping for the protection of karst aquifers in Slovenia. Acta Carsol 36(3):461–475
Šiki D, Pleničar M (1975) Osnovna geološka karta Jugoslavije. Tolmač za list Ilirska Bistrica [Elementary geological map of Yugoslavia. Commentary of the Ilirska Bistrica sheet]. Zvezni geološki zavod Beograd, Belgrade, Serbia, 51 pp
Van Stempoort D, Ewert L, Wassenaar L (1993) Aquifer vulnerability index (AVI): a GIS compatible method for groundwater vulnerability mapping. Can Water Res J 18:25–37
Vías JM, Andreo B, Perles JM, Carrasco F, Vadillo I (2006) Proposed method for groundwater vulnerability mapping in carbonate (karstic) aquifers: the COP method: application in two pilot sites in southern Spain. Hydrogeol J 14(6):912–925
Vrba J, Zaporozec A (1994) Guidebook on mapping groundwater vulnerability. IAH, International Contributions to Hydrogeology, 16, Heise, Hannover, 131 pp
Zwahlen F (ed) (2004) Vulnerability and risk mapping for the protection of carbonate (Karstic) aquifers. Final report COST action 620. European Commission, Directorate-General for Research, Brussels, 297 pp
Acknowledgements
The study was founded by the Slovene Ministry of Higher Education, Science and Technology within the framework of the Young Researchers Programme, and is a contribution to the UNESCO/IUGS IGCP 513 Project “Global Study of Karst Aquifers and Water Resources”. Special thanks to P-A. Schnegg (University of Neuchâtel), H. Krafft (Nationalpark Berchtesgaden) and B. Peric (Park Škocjanske jame) for lending us field fluorometers and an automatic sampler. The authors also acknowledge the help of S. Guglielmetti (University of Neuchâtel) and G. Kovačič (University of Primorska).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ravbar, N., Goldscheider, N. Comparative application of four methods of groundwater vulnerability mapping in a Slovene karst catchment. Hydrogeol J 17, 725–733 (2009). https://doi.org/10.1007/s10040-008-0368-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10040-008-0368-0