Abstract
The development of the Internet of Things (IoT) is predicted to change the healthcare industry and might lead to the rise of the Internet of Medical Things. The IoT revolution is surpassing the present-day human services with promising mechanical, financial, and social prospects. This paper investigated the security of medical images in IoT by utilizing an innovative cryptographic model with optimization strategies. For the most part, the patient data are stored as a cloud server in the hospital due to which the security is vital. So another framework is required for the secure transmission and effective storage of medical images interleaved with patient information. For increasing the security level of encryption and decryption process, the optimal key will be chosen using hybrid swarm optimization, i.e., grasshopper optimization and particle swarm optimization in elliptic curve cryptography. In view of this method, the medical images are secured in IoT framework. From this execution, the results are compared and contrasted, whereas a diverse encryption algorithm with its optimization methods from the literature is identified with the most extreme peak signal-to-noise ratio values, i.e., 59.45 dB and structural similarity index as 1.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
IoT makes incorporated communication circumstances of interconnected devices and stages by drawing in both practical and substantial worlds simultaneously [1]. In terms of IoT, a number of associated smart devices, sensors, and actuators work together to screen and deal with the physical condition and human frameworks [2]. IoT is likely predicted to accomplish novel and creative arrangements with negligible human involvement [3]. As the next era in information technology, IoT brings ‘telemedicine,’ an additional attempt, in which the sensors and systems [4, 5] are applied to customary medicinal devices which can appoint the knowledge to such devices and execute further communication and collaboration among patients to remote pros [6]. Further, the examination of IoT security and data integrity holds down to realistic importance in IoT advancement [7]. With best patient handling, gaining patient satisfaction and treatment at home rendered by the medicinal service suppliers is one more vital possible application in this area. In this way, different therapeutic devices, sensors, and analytical as well as imaging devices can be seen as shrewd devices or articles constituting a center portion of the IoT [8].
In this scenario, it is important to frame an effective model to guarantee the safety and trustworthiness of the patients’ symptomatic data that were transmitted and received from IoT condition [9]. ‘Encryption cryptography’ is the way in which the messages are encoded such that the programmers cannot read it, yet that can be approved by the available faculty. The two principle algorithms that were utilized for data encryption in this work are Advanced Encryption Standard (AES) and the Rivest–Shamir–Adleman (RSA) algorithm [10]. Thus, the IoT could offer ascent to various restorative applications including remote health observing [11]. For instance, in light of the patients’ health data, a social insurance specialist cooperative can improve [12] a lot by analyzing the patient’s conditions and can suggest the optimum treatment and early intercession [13]. Conventional security systems will not be able to oblige IoT devices totally in light of the fact that a large portion of these devices has battery limitations and restricted assets; in any case, these components require more assets [14]. Evidently, longer keys make the figure harder to break, yet in addition, it authorizes a more systematic ‘scramble and decodes’ process [15]. Generally, RSA is an open key calculation which is broadly utilized as a part of business and individual communication areas [16]. The research [17] conducted earlier aimed at enhancing the security of medical data transmission in view of the incorporation of a hybrid encryption plan to get an exceedingly anchored medical services framework [18, 19].
In the current proposed work, an ideal private and open key-based security is used for therapeutic images using IoT. To get the optimal key hybrid (GO-PSO) optimization, various methods are considered, from which the researchers of the study distinguished and examined the vital open difficulties in fortifying the security in IoT. The data about the optimal key-based security process is supplied with authentication examination. The rest of the organized are as follows: Sect. 2 discusses the review of the literature, whereas the challenges faced in medical image security are presented in Sect. 3. Section 4 explains the current proposed model in-depth followed by the results of the security model in Sect. 5. The manuscript is concluded with a note on the future scope.
2 Literature review
In 2017, Hossain et al. [20] proposed a security framework that guaranteed user verification and ensured access to assets and administrations. The security framework validated a client based on OpenID standard. An entrance control system was installed in place to avoid unapproved access to restorative devices. Once the confirmation was successful, the client will be issued with an approval ticket which is described as security access token (SAT). A model of this framework has been executed to tentatively break down and analyze the asset productivity of various SAT check approaches as far as various execution measurements that included calculation and communication overhead.
The ransomware assaults and security worries in IoT were examined by Yaqoob et al. in 2017 [21]. The study recommended a scientific categorization by characterizing and sorting the writing in light of imperative parameters (e.g., dangers, necessities, IEEE norms, sending level, and advancements). Besides, a couple of valid contextual analyses were performed to alarm the individuals with respect to how truly IoT devices are helpless against dangers. A few fundamental open research challenges (e.g., data honesty, lightweight security systems, the absence of security programming upgradability, fixation of capacity highlights, and physical assurance of trillions of devices, protection, and trust) were recognized and discussed in this study.
In 2018, Elhoseny et al. [22] proposed a hybrid encryption pattern which was manufactured as a mix of AES and RSA calculations. The model begins by encoding the mystery data; at that point, it conceals the outcome in a cover image utilizing 2D-DWT-1L or 2D-DWT-2L. Both shading and dark scale images were utilized as cover images to disguise diverse content sizes. The PSNR esteems were generally differed from 50.59 to 57.44 in the event of shading images and from 50.52 to 56.09 in case of dark scale images. MSE esteems differed from 0.12 to 0.57 for the shading images and from 0.14 to 0.57 for the dim scale images. When compared to the available and best-in-class techniques, the proposed pattern demonstrated its capacity to shroud the classified patient’s data into a transmitted cover image with high subtlety, limit, and insignificant weakening in stegoimage.
Healthcare Monitoring for the Internet of Things (HERMIT) was developed by Limaye et al. in 2018 [23] to encourage research into new micro-architectures and enhancements that would empower productive execution of developing IoMT applications. Its dissect HERMIT on an IoT prototyping stage to infer experiences into IoMT applications’ figure and memory qualities. Likewise, contrast HERMIT with three normally utilized benchmark suites, such as MiBench, SPEC CPU2006, and PARSEC, demonstrated that the attributes of IoMT applications’ vary from existing benchmarks.
In 2018, Lakshmanaprabu et al. [24] presented a multi-level structure to include extraction in SIoT huge data with the help of map-diminished system alongside a directed-classifier display. In addition, a Gabor channel was utilized to diminish the commotion and undesirable data from the database, whereas Hadoop MapReduce was also used for mapping and decreasing huge databases and to enhance the effectiveness of the proposed work. Besides, the component determination has been performed on a shifted data set using elephant herd optimization. The proposed framework engineering was made into reality using linear kernel support vector machine-based classifier in arranging the data and predicting the productivity of the proposed work.
An enhanced variant of grasshopper optimization algorithm (GOA) in light of the opposition-based learning (OBL) technique called OBLGOA was proposed by Ewees et al. in 2018 [25]. The study aimed at examining the execution of the proposed OBLGOA in which six arrangements of test arrangement were performed and they incorporated twenty-three benchmark capacities with four building issues. The tests uncovered that the aftereffects of the proposed calculation were better than those often through precise calculations in this area. In the end, the researchers inferred that OBLGOA calculation can lead to aggressive outcomes in optimization designing issues when compared and contrasted with cutting-edge algorithms.
In 2017, Shankar et al. [26] utilized the elliptic curve cryptography approach to enlarge the security and well-being of the image. This novel strategy was used to produce various offers that were subjected to encryption and decryption by methods of elliptic curve cryptography system. The test results showed that the peak signal-to-noise proportion is 58.0025, mean square blunder esteem is 0.1164 and the relationship coefficient is 1 for the unscrambled image with no kind of bending of the first image.
In 2018, Mukhtar M. E. Mahmoud et al. [27] proposed the investigations CoT models and stages and in addition the usage of CoT with regard to brilliant smart health care. Thusly, the paper clarifies some related issues of CoT, including the absence of institutionalization. In addition, it centers on vitality effectiveness with an inside and out investigation of the most pertinent proposition accessible in the writing. An assessment of all the vitality productivity arrangements examined in this paper appears there is as yet a need to enhance vitality effectiveness, particularly with respect to QoS and performance.
A survey of strategies in light of IoT for medicinal services and encompassing helped living, characterized as the Internet of Health Things (IoHT), in view of the latest distributions and items accessible in the market from industry for this section by Joel J. P. C. Rodrigues et al. [28]. Likewise, this work recognizes the mechanical advances made up until now, breaking down the difficulties to be survived, and gives an approach of future patterns. In spite of the fact that those works, it is conceivable notice that further investigations are vital to enhancing current strategies and that novel idea and advances of the Internet of Health Things are expected to conquer the recognized difficulties.
3 IoT challenges
A decent IoT stage makes it simple to interface with devices and achieves device administration capacities scaled through cloud-based administrations. Its other activities are concerned with the investigation to pick up knowledge and accomplish hierarchical change [28,29,30]. At some instance, the data are gathered at the device level to the point so that they are transmitted to its last goal and anchoring that data is basic. During the crisis, if a patient can contact a specialist, who is inaccessible due to distance, with brilliant portable applications, the surgeons can check the patients in a flash with portability arrangements and distinguish the afflictions in a hurry. Although the world’s demand for medical services has risen in recent years, we still live in the traditional model of hospital-centric care, in which citizens visit doctors when they fall sick. With an intelligent IoT healthcare solution, a usage-optimized product integrated with the next wave of performance is possible.
3.1 Research gap
The IoT security makes network an extremely complex framework. Because of this reality, disappointment in the IoT system may prompt more opportunity for rebuilding of the service to customers. The security of the data hiding strategy ought to give security to information to such an extent that lone the expected client can access it in view of the security technique [31]. All together words, it refers to the inability of unapproved client to identify concealed data. Therefore a same information will be ciphered to a similar esteem in may security technique like cryptography, AES homomorphic encryption like that. A significant disadvantage of symmetric key image is that it requires the private key to share by each combine of imparting parties, and furthermore the key itself to be partaken in an anchored medium. Any unintended client having the mystery key has a risk of figuring the image. These existing security systems are also using encryption or steganography, or their mixes. There is distinctive securable and perfect course of action of image encryption that can be all around protected from unapproved contact [1, 32,33]. For enhancing IoT advancements require anchored answers for avert spillage of private data and destructive inciting exercises by methods for peer validation and secure information transmission between the IoT centers and servers.
4 Methodology
To receive IOT innovation, it is important to make clients aware and certain about its security and protection and convey strongly that there would not be any genuine risk of their data integrity, secrecy, an expert in the medical system. The instant progression of security and protection in expansive scale are the determining variables of IOT to anchor the medical images’ transmission.
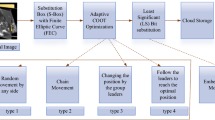
The primary motivation behind the network security and data protection is to accomplish classification and integrity. This paper creates a hybrid encryption system for IOT security in which the calculation recommended possesses unique highlights in encryption and decoding as far as speed is concerned even in optimal keys. It can also enhance the web security. The proposed model utilizes asymmetric encryption, i.e., ECC strategy to anchor the information in the framework. This cryptography is an exceptionally secure type of encryption as long as the public and private keys are completely secure and it is used in order to enhance the security level of the proposed model hybrid optimization (GO-PSO) connected for the key in encryption procedures. The security of encryption lies in the capacity of an algorithm to produce a ciphered image that is not effectively returned to the first plain image. The chosen encryption procedures and optimization strategy are discussed in the sections below. Moreover, Fig. 1 illustrates the proposal model.
4.1 Medical image transmission in IOT
The screening of lungs is essential since the lung cancer death rate is found to be elevated among other cancer types. Among the chest imaging techniques, a radiograph is a typical and early screening strategy which has benefits such as low measurement and minimal effort [6, 7]. When a specialist observes the medical image, he or she endorses a quick methodology alongside the prescriptions and sends it back to the source core instantly. Along these lines, the inspiration of the proposed philosophy takes care of its demand, i.e., giving medical safeguard in catastrophic time utilizing IOT as the primary weapon.
4.2 Contrast enhancement process
The histogram equalization routinely offers to ascend the worldwide difference of few images, particularly when the user data of the image are symbolized by close complexity esteems. Besides, it is likewise conceivable to successfully allow the powers on the histogram by methods for this direction.
4.3 Elliptic curve cryptography (ECC) with optimization
ECC is a new technique to deal with public key cryptography in light of the arithmetical structure of elliptical bends over limited fields. It is considered as a productive method with low key size for image security, and it is exceptionally challenging in terms of break time. This section additionally briefs the IOT medical images in the medical part where ECC is added [34]. This cryptographic security algorithm has little defaulting steps like key generation, encryption, decryption, and investigation and is illustrated in Fig. 2. To enhance the security level of IOT frameworks, an optimization model is considered for key generation. ECC institutionalization is pivotal for accomplishing down-to-earth and proficient execution.
4.3.1 Key generation stage
The tasks of Elliptic Curve Cryptography are clarified as two foreordained stages, i.e., prime stage and binary stage. For cryptographic activities, the reasonable field is chosen with a limited number of points. The prime stage tasks choose a prime number, and limited substantial quantities of fundamental focuses are created on the elliptic curve. Creating the public keys and the private key is critical for ‘ECC,’ and these keys are chosen from prime numbers [35]. The sender encrypts the image with the recipient’s public key, and the beneficiary decrypts the private key. These private and public keys are optimized for better security, and the current study’s proposed optimization method is discussed in the following section.
4.4 Optimization for ECC-key selection
The mathematical optimization method, which is a best method to choose an element from a group of obtainable alternatives, is used in mathematics, computer science, and operation research [36,37,38]. It is finding the best accessible value of target function from a defined domain or variety of target functions from different types of domain [39, 40]. This ECC security algorithm optimizes the underlying key generation stage. The hybrid swarm-based optimization is associated therewith which is the combination of GO and PSO. In light of this optimization model, the key solution gets private and public keys. The sender encrypts the image with the receiver’s public key, whereas the receiver decrypts it using the private key [41]. This GO procedure is nothing but how grasshopper swarms work. The numerical model is utilized to mimic the swarming behavior of grasshoppers and PSO algorithm; here, every potential solution is considered as a particle. All particles have their own fitness values and velocity. These particles fly through the dimensional issue space by gaining momentum from the recorded data of the considerable number of particles. The expand of hybrid optimization is examined in the following section.
4.4.1 General steps for optimal key selection
Initialization process When the key solution is inducted, the prime numbers are considered to produce new populace size for the ideal key selection process.
4.4.1.1 The objective function for key selection
Optimal key selection process considers the ‘fitness function’ as max key with PSNR to scramble and unscramble data from the medical image in IOT. The arrangement is created by the system of hybrid optimization to assess the goal of every arrangement. It is depicted in the following condition (2).
4.4.2 Grasshopper optimization (GO)
Grasshoppers are creepy crawlies and are classified as a bug. It usually harms the crop production and accordingly the agribusiness due to which it is prompt to classify it as a bug. The grasshopper swarm has one exceptional trademark, i.e., the swarming behavior in both nymphs and adults [31]. The swarm nymph has moderate development when they are in the larval stage. The little advancement of the grasshopper is the major characteristic for the swarm in the larval stage. The primary position of grasshopper is signified through Eq. (3).
where Soci s the social interaction, Gravityi is the gravity force on ith a grasshopper, and Windi denotes the wind advection. For solving the grasshopper function, some functions need to be simulated such as social interaction, the impact of gravitational force, and wind advection.
-
1.
Social interaction The parts completely reenact the development of grasshoppers, yet the primary segment starts from grasshoppers themselves. Notwithstanding the benefits of the capacity, it is unable to make different solid powers between grasshoppers with vast separations between them. To determine this issue, the separation between grasshoppers ought to be mapped or standardized into the interim of [1, 4]. The social connection examined is given here.
$$ Soc_{i} = \sum\limits_{\begin{subarray}{l} j = 1 \\ j \ne i \end{subarray} }^{N} {S\left( {p_{ij} } \right)\overset{\lower0.5em\hbox{$\smash{\scriptscriptstyle\frown}$}}{p}_{ij} } $$(4)Above process \( \overset{\lower0.5em\hbox{$\smash{\scriptscriptstyle\frown}$}}{p}_{ij} = \frac{{q_{j} - q_{i} }}{{p_{ij} }};\;p_{ij} = \left| {q_{j} - q_{i} } \right| \) where \( p_{ij} \) is the distance between \( i{\text{th}} \) and \( j{\text{th}} \) grasshopper, \( Soc \) is a function to define the strength of social forces and \( \overset{\lower0.5em\hbox{$\smash{\scriptscriptstyle\frown}$}}{p}_{ij} \) is a unit vector from \( i{\text{th}} \) grasshopper to the \( j{\text{th}} \) grasshopper. N is the number of grasshoppers. The s function, which defines the social forces, is calculated as follows:
$$ Soc\_force = f{\text{e}}^{{{\raise0.7ex\hbox{${ - k}$} \!\mathord{\left/ {\vphantom {{ - k} l}}\right.\kern-0pt} \!\lower0.7ex\hbox{$l$}}}} - {\text{e}}^{ - k} $$(5)where f indicates the intensity of attraction, l denotes the attractive length scale, and the capacity is illustrated to outline how it affects the social interaction (repulsion and attraction) of grasshoppers [31].
-
2.
Gravity force and Wind advection The gravitational force (Gravityi) of the grasshopper is computed using the conditions 6 and 7. Nymph grasshoppers have no wings, and so, their developments are exceedingly associated with wind direction.
$$ Gravity_{i} = - gr\_con_{g} $$(6)$$ Wind_{i} = z\lg r\_drift $$(7)where g is the gravitational constant, \( gr\_con \) shows a unity vector toward the center of the earth, l is a constant drift, and \( gr\_drift \) is a unit vector in the direction of the wind. To take care of optimization issues, a stochastic algorithm must execute exploration and exploitation successfully to decide the exact approximation of the global optimum. The above model is extended by the function.
$$ G_{i}^{{}} = \sum {\left\{ {S(|q_{j} - q_{i} |)\frac{{q_{j} - q_{i} }}{{p_{ij} }} - gr\_con_{g} + z\lg r\_drift} \right\}} $$(8)In GOA, it is accepted that the grasshopper with the best objective esteem is the fittest grasshopper amid optimization. This will spare the best solution for every single cycle in the calculation. The mathematical model displayed above ought to be ready with unique parameters to demonstrate exploration and exploitation in various phases of optimization.
4.4.3 Particle swarm optimization (PSO)
Particle swarm optimization is a heuristic worldwide optimization strategy, and it is created from swarm insight and depends on the exploration of feathered creature and fish rush development behavior. Every molecule has a key function esteem which is dictated by a fitness function. In the first place, the particles are introduced arbitrarily with position and velocity [42]. This PSO displays essential parameters as global best (G-best) and particle best (P-best), and in view of these things, the velocity and new refreshed solutions are assessed for optimal key selection in ECC.
4.4.3.1 Velocity and position updating process
The optimal one is deemed as the \( G\_best\,{\text{and}}\,P\_best \) value among the fitness values. Subsequent to that iteration, the current optimal fitness value as \( \,P\_best \) is selected as the current optimal fitness value and \( G\_best\,\, \) is chosen as the overall best fitness value. The velocity vector for a particle is updated according to \( G\_best\,\, \) and \( \,P\_best \) value. The formulation for updating the velocity and position is as follows.
Here, \( V_{i} \,\, \) is the particle velocity; \( r_{i} \) is the present particle, and rand is an arbitrary number between 0 and 1; and \( g_{1} ,\,\,g_{2} \) are learning factors in which \( g_{1} = \,g_{2} = 2 \). As per the refresh strategy laid on the conditions like 9 and 10, the \( i{\text{th}} \) particle position is coordinated by the situation of global best arrangement and position best arrangement. The method is preceded to the point that the accomplishment of the solution with prevalent fitness esteem, in view of this refreshing model, locates the ideal key to anchor medical image in IOT.
4.4.4 Proposed optimization (GO-PSO) for security
The hybridization of GO with PSO is performed in order to take care of the optimal key of ECC with the most extreme key, i.e., PSNR, by which the idea of developing the consolidation of certain means of these strategies is discussed in the above segments. The evolutional procedure of the GO, together with the impulse of organic product flies, in finding the most limited course, to look for food is completely joined and detailed as the new optimization technique [42, 31]. The best solution decides the ideal outcome, and the flowchart for this hybrid optimization is illustrated in Fig. 3.
This hybrid procedure achieves the undertaking of learning the greatest emphasis here in hybridization shape; the best solution is picked from the two algorithms. Until the point, the optimal key is secured for the medical image, and the procedure is repeated.
4.5 Image encryption stage
Encryption is the way toward encoding images or data such that it can be approved. At one point, when the input image that was sent by the sender was spoken to a curve; at that point, the curvature point is discovered to scramble the plain images into ciphered image using which the public keys are chosen. ‘Conditions’ associated with this ECC method are discussed at the end of this section.
4.6 Image decryption stage
Decryption is the conflicting philosophy to encryption, i.e., the method of moving over the encrypted substance into its extraordinary plain image. Following this procedure, the scrambled data or image is shown and the rest of the image is lost and in this way, securing the unauthorized access. In light of the ECC [31] methodology, the image will be decrypted, i.e., ciphering the image using the private key.
4.7 Analysis stage
The authenticated image is transmitted in an encrypted form for powerful and secure communication. It keeps an opponent to perform pernicious activities and improves classification. To fortify the security prerequisites of the Internet of Things and cloud model, elliptic curve cryptosystems is embraced. Optimal key-based medical image encryption and decryption are illustrated in Fig. 4.
From the method of elliptic curves, the security in IoT is enhanced, and if the qualifications are coordinating, the protected conveyance of the service is started. This guarantees the access to the administration for the legitimate user to goodness client to the keen gateway, in an encoded frame secrecy.
4.7.1 Mathematics expression and Steps for ‘ECC’
Let us take input information as \( o \), elliptic curve values m, n, and prime number y.
Elliptic curve function is as follows:
The curve function computes by the following equation
Key generation The integer values for the private key \( \Pr_{k} \) are selected.
Generate public key \( Pub_{k} = \Pr_{K} *R \).
Here R denotes the random values between 1 and n−1.
Apply optimization to get optimal \( \Pr_{k} \) and \( Pub_{k} \).
Update the grasshopper solutions and particle solution.
The process is repeated until getting optimal.
Finally, get \( Opt\_Pub_{k} \;{\text{and}}\;Opt\_\Pr_{K} \).
Encryption model Assume the sender is sending o the image to the receiver. A takes a plain image o and encodes it onto a point from the elliptic group.
To choose the random integer values k from the range of n and n-1, the test converts the ciphered images as C1 and C2.
This encrypted cipher information to the receiver side.
Decryption model Using the private key, the cipher image is decrypted. The receiver computes the product of the first point from \( C_{1} \;{\text{and}}\;C2 \).
4.8 Authentication analysis
On the off chance, the cipher image needs to be validated by sending a signature, and for this, the recipient must have sender’s ideal public keys, and at that point, the random values \( R \) must be checked. At last, figure out the HASH capacity to enhance the security level for medical images in IoT.
5 Results and analysis
The proposed optimal key-based security strategy is actualized in MATLAB 2016 with an i5 processor and 4 GB RAM. In the investigation of medical images’ security, the researchers considered diverse medical scans like brain, lung, glaucoma, and cancer as illustrated in Fig. 5. These are gathered from web cloud storage of hospitals. The hidden image was examined ahead of being transmitted and in the wake of being received by the normal recipient. This is done to ensure there is only less distortion inside to the first cover record subsequent to disguising the secret image.
This proposed model contrasted with standard ECC and other encryption algorithms, i.e., AES, DES. These measurements ascertain the proportion between the first image and the encoded images, for example PSNR, SSI, MSE, and BER [41, 43] (Table 1), whereas the computational time and considered database are discussed in the sections below.
Table 2 demonstrates the proposed (ECC with GO + PSO) approach results from the measures such as PSNR, MSE, BER, SSI and time of various images. The ideal key is chosen so that it isolates the message into three equivalent amounts with the most extreme fitness function, and then, the whole input is encrypted. The highest PSNR of these test images is 58.22 dB and comparatively higher than MSE and BER which are 0.09 and 0 with the most extreme SSI being 1. In addition, this table demonstrates the histograms of the cover image and encrypted images.
The convergence of fitness function (PSNR) is shown in Fig. 6 which differentiates with standard optimization, GO, PSO, and hybrid optimization model [44, 45]. Through this diagram, the hybrid (GO + PSO) technique undergoes minimum iteration to yield the perfect outcome. Along these lines, it is boosted to 59.45 which was achieved in 78 cycles. In the starting cycle, the fitness estimation of hybrid is 11.36, and in other methods, the underlying fitness esteem is 9.48. Then, the emphasis is changed according to the execution additionally with fluctuations in light of the strategies. The greatest fitness of the proposed model contrasted with PSO and GO where the distinction is 12.56 to 13.5%, and comparatively, the other algorithm has an additional distinction, i.e., 14.85%. Through the diagram, the (GO + PSO) technique just determines the perfect fitness esteem with effective outcomes.
Figure 7 (a–e) demonstrates similar examination with various measures, and here, distinctive ways are considered to deal with correlation part, i.e., AES, RSA, ECC, ECC + CS, ECC + PSO, ECC + GO, and ECC with hybrid improvement. Figure 7(a) demonstrates the examination of PSNR measure in which the normal and the most extreme value is 59.56 dB in ECC with a hybrid approach which contrasted with existing strategy. Through images and by their PSNR esteems, the recommended approach is connected with the image and output images are identified. It contradicts with ECC + CS and PSO with 2.89% distinction. At this point, Fig. 7(b) and (c) demonstrates MSE and BER and it has the least esteem in all images of the proposed model. There was no variety between the considered images in the BER, where its qualities were zero for the two images. The MSE value, i.e., 0.68, is the greatest for the proposed hybrid encryption strategy. SSI (d), as auxiliary discernment, is made in light of the pixels reliable toward the neighboring pixels and improving it as a measure than PSNR and MSE which ascertain the apparent blunder in particular pixels. The neighboring pixel conditions contain essential data about the structural content of the image. Figure 7(e) denotes the least time required for this security procedure, i.e., 1.5 min to finish the encryption and decryption process in this long-lasting contrast and computational time. From these current works, it can be stated that the proposed RSA and ECC with GO + PSO strategy decrease the encryption and decryption time when compared with an existing technologies.
Comparative analysis. a PSNR comparison of proposed method with existing methods. b MSE comparison of proposed method with existing methods. c BER comparison of proposed method with existing methods. d SSI comparison of proposed method with existing methods. e Time comparison of proposed method with existing methods
Table 3 demonstrates the attack predicted for the proposed model in which two attacks are considered like salt; it is connected with all input medical images to assess the security execution. Nonetheless, the conditions are: at first assault the watermarked image with any assault and afterward recuperate the security procedure. The PSNR of salt noise is 42.33 dB and 44.52 dB; likewise, different measures yielded additional outcomes, and at that point, the execution investigation parameters are least for the attacks applied in the image contrasted with the proposed work.
Figure 8 (a, b, c, and d) shows the resultant images of with assault and without assault in medical image security. When the assaults are connected to diverse images, the PSNR estimation of ‘without assault image’ is best executed. When there is an increment in noise density, the PSNR value changes is described visually. It can be seen as the noise density expanded, there is a quick debasement in PSNR values for the two procedures. In the event that the limits rate is profoundly expanded in all the three modalities at that point, clear image quality gets diminished in light of high distortion in the reconstructed image.
6 Conclusion
From the precise discussions made above, it is important perception to elaborate on the few ideas discussed and bring further advances in medical image security process. Additionally, the current study has considered the proposed technique in hybrid encryption algorithm utilized as a part of IoT. The study also recommended a strategy that can enhance IoT by the hybrid encryption algorithm. This proposed model, i.e., ECC with PSO and GO, comes with multinomial use in encryption and decoding to accomplish a right message. This algorithm utilizes less memory on account of less financial unpredictability. While demonstrating the current work with diverse measurements, the researchers utilized the imperative measures such as PSNR and SSI which have indicated control image quality against all the tests. It is clear that the procedure is not secure enough as it never furnished great impalpability; so it needs to be investigated additionally to increment the security level. The proposed algorithm takes less time for both encryption and decryption process. The future work should fundamentally focus on tamper localization scheme in order to have content-based respectability as opposed to the strict-integrity functionality executed in the current algorithms.
Change history
14 December 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s00521-022-08143-y
References
Gaber T, Abdelwahab S, Elhoseny M, Hassanien AE (2018) Trust-based secure clustering in WSN-based intelligent transportation systems. Comp Netw. https://doi.org/10.1016/j.comnet.2018.09.015
Safi A (2017) Improving the security of the internet of things using encryption algorithms. World Acad Sci Eng Technol Int J Comput Electr Autom Control Inf Eng 11(5):546–549
Islam SR, Kwak D, Kabir MH, Hossain M, Kwak KS (2015) The internet of things for health care: a comprehensive survey. IEEE Access 3:678–708
Thibaud M, Chi H, Zhou W, Piramuthu S (2018) Internet of things (IoT) in high-risk environment, health, and safety (EHS) industries: a comprehensive review. Decis Support Syst 108:79–95
Elhoseny M, Abdelaziz A, Salama AS, Riad AM, Muhammad K, Sangaiah AK (2018) A hybrid model of internet of things and cloud computing to manage big data in health services applications. Future Gener Comput Syst 86:1383–1394
Pizzolante R, Castiglione A, Carpentieri B, De Santis A, Palmieri F, Castiglione A (2017) On the protection of consumer genomic data on the internet of living things. Comput Secur 74:384–400
Tankard C (2015) The security issues of the internet of things. Comput Fraud Secur 2015(9):11–14
Rahmani AM, Gia TN, Negash B, Anzanpour A, Azimi I, Jiang M, Liljeberg P (2018) Exploiting smart e-health gateways at the edge of healthcare internet-of-things: a fog computing approach. Future Gener Comput Syst 78:641–658
Kothmayr T, Schmitt C, Hu W, Brünig M, Carle G (2013) DTLS based security and two-way authentication for the internet of things. Ad Hoc Netw 11(8):2710–2723
Al Hasib A, Haque AAMM (2008) A comparative study of the performance and security issues of AES and RSA cryptography. In: Third international conference on convergence and hybrid information technology, 2008, ICCIT’08, vol 2. IEEE, pp. 505–510
Sharma R, Sandhu C (2015) Hyper spectral image restoration using low-rank matrix recovery and neural network. J Adv Res Comput Eng Technol 4(7):3312–3318
da Cruz MA, Rodrigues JJP, Al-Muhtadi J, Korotaev VV, de Albuquerque VHC (2018) A reference model for internet of things middleware. IEEE Internet Things J 5(2):871–883
Zhang J, Duong TQ, Woods R, Marshall A (2017) Securing wireless communications of the internet of things from the physical layer, an overview. Entropy 19(8):420
Kuppuswamy P, Al-Khalidi SQ (2014) Hybrid encryption/decryption technique using new public key and symmetric key algorithm. Int J Inf Comput Secur 6(4):372–382
RebouçasFilho PP, Cortez PC, da Silva Barros AC, Albuquerque VHC, Tavares JMR (2017) Novel and powerful 3D adaptive crisp active contour method applied in the segmentation of CT lung images. Med Image Anal 35:503–516
Alshammari FH (2017) An efficient approach for the security threats on data centers in iot environment. Int J Adv Comput Sci Appl 8(4):73–80
Usman M, Ahmed I, Aslam MI, Khan S, Shah UA (2017) Sit: a lightweight encryption algorithm for secure internet of things. arXiv preprint arXiv:1704.08688
Moraes JL, Rocha MX, Vasconcelos GG, Vasconcelos Filho JE, de Albuquerque VHC (2018) Advances in photopletysmography signal analysis for biomedical applications. Sensors (Basel, Switzerland) 18(6):1–26
Shehab A, Elhoseny M, Muhammad K, Sangaiah AK, Yang P, Huang H, Hou G (2018) Secure and robust fragile watermarking scheme for medical images. IEEE Access 6:10269–10278
Hossain M, Islam SR, Ali F, Kwak KS, Hasan R (2017) An internet of things-based health prescription assistant and its security system design. Future Gener Comput Syst 1–26
Yaqoob I, Ahmed E, ur Rehman MH, Ahmed AIA, Al-garadi MA, Imran M, Guizani M (2017) The rise of ransomware and emerging security challenges in the internet of things. Comput Netw 129:444–458
Elhoseny M, Ramírez-González G, Abu-Elnasr OM, Shawkat SA, Arunkumar N, Farouk A (2018) Secure medical data transmission model for IoT-based healthcare systems. IEEE Access 6:20596–20608
Limaye A, Adegbija T (2018) ERMIT: a benchmark suite for the internet of medical things. IEEE Internet Things J 1–10
Lakshmanaprabu SK, Shankar K, Khanna A, Gupta D, Rodrigues JJ, Pinheiro PR, De Albuquerque VHC (2018) Effective features to classify big data using social internet of things. IEEE Access 6:24196–24204
Ewees AA, Elaziz MA, Houssein EH (2018) Improved grasshopper optimization algorithm using opposition-based learning. Expert Syst Appl 1–31
Shankar K, Eswaran P (2017) RGB based multiple share creation in visual cryptography with aid of elliptic curve cryptography. China Commun 14(2):118–130
Mahmoud MM, Rodrigues JJ, Ahmed SH, Shah SC, Al-Muhtadi JF, Korotaev VV, De Albuquerque VHC (2018) Enabling technologies on cloud of things for smart healthcare. IEEE Access 6:31950–31967
Rodrigues JJ, Segundo DBDR, Junqueira HA, Sabino MH, Prince RM, Al-Muhtadi J, De Albuquerque VHC (2018) Enabling technologies for the internet of health things. Ieee Access 6:13129–13141
Abdelaziz A, Elhoseny M, Salama AS, Riad AM (2018) A machine learning model for improving healthcare services on cloud computing environment. Measurement 119:117–128
Darwish A, Hassanien AE, Elhoseny M, Sangaiah AK, Muhammad K (2017) The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: opportunities, challenges, and open problems. J Ambient Intell Humaniz Comput 1–16
Neve AG, Kakandikar GM, Kulkarni O (2017) Application of grasshopper optimization algorithm for constrained and unconstrained test functions. Int J Swarm Intell Evol Comput 6(165):2
Shankar K, Lakshmanaprabu SK (2018) Optimal key based homomorphic encryption for color image security aid of ant lion optimization algorithm. Int J Eng Technol 7(9):22–27
Elhoseny M, Yuan X, El-Minir HK, Riad AM (2016) An energy efficient encryption method for secure dynamic WSN. Secur Commun Netw 9(13):2024–2031
Shankar K, Eswaran P (2016) RGB-based secure share creation in visual cryptography using optimal elliptic curve cryptography technique. J Circuits Syst Comput 25(11):1650138
Shankar K, Eswaran P (2016) An efficient image encryption technique based on optimized key generation in ECC using genetic algorithm. Adv Intell Syst Comput Springer 394:705–714
DiazCortes MA, OrtegaSanchez N, Hinojosa S, Oliva D, Cuevas E, Rojas R, Demin A (2018) A multi-level, thresholding method for breast thermograms analysis using dragonfly algorithm. Infrared Phys Technol. https://doi.org/10.1016/j.infrared.2018.08.007
Hinojosa S, Avalos O, Oliva D, Cuevas E, Pajares G, Zaldivar D, Galvez J (2018) Unassisted thresholding based on multi-objective evolutionary algorithms. Knowl Based Syst. https://doi.org/10.1016/j.knosys.2018.06.028
Oliva D, Hinojosa S, Osuna-Enciso V, Cuevas E, Pérez-Cisneros M, Sanchez-Ante G (2017) Image segmentation by minimum cross entropy using evolutionary methods. Soft Comput. https://doi.org/10.1007/s00500-017-2794-1
Oliva D, Hinojosa S, Cuevas E, Pajares G, Avalos O, Gálvez J (2017) Cross entropy based thresholding for magnetic resonance brain images using crow search algorithm. Expert Syst Appl 79:164–180. https://doi.org/10.1016/j.eswa.2017.02.042
Avudaiappan T, Balasubramanian R, Sundara Pandiyan S, Saravanan M, Lakshmanaprabu SK, Shankar K (2018) Medical image security using dual encryption with oppositional based optimization algorithm. J Med Syst 42(11):1–11. https://doi.org/10.1007/s10916-018-1053-z
Shankar K, Eswaran P (2016) A New k out of n secret image sharing scheme in visual cryptography. In: 10th international conference on intelligent systems and control (ISCO). IEEE, pp 369–374
Dhanalakshmi L, Ranjitha S, Suresh HN (2016) A novel method for image processing using particle swarm optimization technique. In: International conference on electrical, electronics, and optimization techniques (ICEEOT). IEEE, pp 3357–3363
Shankar K, Eswaran P (2015) Sharing a secret image with encapsulated shares in visual cryptography. Procedia Comput Sci 70:462–468
Shankar K, Eswaran P (2015) A secure visual secret share (vss) creation scheme in visual cryptography using elliptic curve cryptography with optimization technique. Aust J Basic Appl Sc 9(36):150–163
Shankar K, Eswaran P (2015) ECC based image encryption scheme with aid of optimization technique using differential evolution algorithm. Inte J Appl Eng Res 10(5):1841–1845
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
This article has been retracted. Please see the retraction notice for more detail:https://doi.org/10.1007/s00521-022-08143-y
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Elhoseny, M., Shankar, K., Lakshmanaprabu, S.K. et al. RETRACTED ARTICLE: Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput & Applic 32, 10979–10993 (2020). https://doi.org/10.1007/s00521-018-3801-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-018-3801-x