Abstract
Risks from intentional releases of organisms to agriculture, the food chain or the environment must be assessed to ensure proportionate planning, just as accidental releases from trade or natural spread must be predicted so that management can be organised. Pest risk assessment methods are well established for trade related introductions and it is efficient to build on these and adapt available risk assessment components from agricultural and environmental assessment tools. Some additional risk considerations, particularly related to the motivation, capacity and intended impact of a perpetrator should be included, and some key elements of trade related assessments, such as the volume of trade, may be irrelevant for intentional targeted releases. Risk levels from the various causes and impacts should be comparable to allow authorities to direct responses appropriately. Preventative actions, for both intentional and unintentional introductions, are particularly important. For intentional release this puts emphasis on motivation, capacity and sources. A scenario based approach to assessing intentional release risks is taken to develop a pest risk assessment tool that can cover the range of levels of potential activity. A risk assessment framework is illustrated and a range of example scenarios is described.
Access provided by CONRICYT-eBooks. Download chapter PDF
Similar content being viewed by others
Keywords
- Risk assessment
- Intentional release
- Plant health
- Agroterrorism
- Bioterrorism
- Biocrime
- Biowarfare
- Pest risk analysis
- Risk model
6.1 Introduction
Traditionally, crop biosecurity efforts have focused on preventing and responding to the natural or unintentional introduction, establishment and spread of pests or pathogens. Government agencies and industries take steps to limit these accidental introductions through quality standards in trade, official rules on risk mitigation measures, public and private surveillance for new organisms, and control planning and capacity. This approach to biosecurity has driven standardised approaches to Pest Risk Analysis (PRA), which have been developed to enable risk managers to identify, assess, manage and communicate risks of this kind (IPPC 2004, 2007; EPPO 2011). Some European countries, such as the United Kingdom and France, have developed extensive national catalogues of conventional plant health risk (Baker et al. 2014; Defra 2015) and methodology for prioritizing plant pests (Moignot and Reynaud 2013), in order to comply with the requirements of the new EU plant health regulation (now agreed for implementation in 2019). However, in recent years there has been growing concern about the possible deliberate misuse of biological agents against agriculture and the food supply with a view to causing economic losses, generating fear and/or undermining social stability (European Commission 2007).
Referred to broadly as agroterrorism,Footnote 1 this possibility has, in turn, motivated calls at the national and international level to ensure that public and private responses to possible threats from harmful organisms include both unintended and intentional releases. This requires a reassessment and revision of standard approaches to PRA to explicitly account for the motives and capabilities of potential attackers who might choose to deliberately misuse biological agents in pursuit of particular political or ideological goals. As a consequence, security becomes yet another consideration, in addition to biosecurity, that should be incorporated within a Pest Risk Analysis framework. Agroterrorism and other ecologically based security risks should be assessed and managed within a common framework along with more conventional pest risks to ensure that proportionate responses are taken across the full range of risks.
This common framework should be consistent with conventional assessments of unintentional risks from pests and pathogens and should reflect technical values for factors that have been identified as components of risk, as well as an indication of the uncertainty for each component. The outcome of such risk assessments is a distribution of the likelihood and consequences of the threat.
6.2 Agent-Pathway-Receptor Framework
Assessing and managing risks posed by agroterrorism requires thinking differently about potential threats to agriculture and the food supply. Traditional approaches to crop biosecurity have focused on the natural or unintentional introduction of pests or pathogens. Agroterrorism, although it poses similar ecological threats from potential harmful species (European Commission 2007), introduces the further dimension of a rational actor who chooses (to the extent possible) the conditions whereby risks of this kind are generated (Mair and Mair 2003). For example, the choice of biological agent, the specific crops that are targeted, and the location, scale and timing of the potential outbreak are all outcomes that can be determined by the perpetrator of an attack. In this light, biosecurity efforts must not only consider the biological characteristics of harmful invasive species, but also the motives and capabilities of individuals, non-governmental groups or state-sponsored organizations that may attempt to exploit vulnerabilities in agricultural, environmental and social systems with a view to achieving particular political, economic or personal goals. The ‘biological’ and ‘human’ dimensions are characteristic of such an ‘hydrid threat’ (Barbier 2008), is also discussed in Chap. 2.
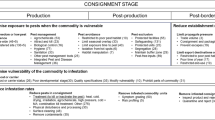
With this context in mind, in this section we consider how the threat of agroterrorism complicates existing approaches to crop biosecurity. While the threat of agroterrorism shares aspects in common with naturally occurring and unintentional pest and disease outbreaks, in as much as agroterrorism can be viewed as an alternative source of harmful invasive species, the rational actor in the risk calculation presents new challenges to risk assessment and risk management. In particular, risk analysis should consider the motive and capabilities of perpetrators and the vulnerability of receptor targets in more detail than would occur in conventional PRA. In Fig. 6.1, we illustrate the components that make up this expanded range of biosecurity risks. Therefore, although existing PRA standards can be used as a basis for analysing the biological and environmental aspects of agroterrorism risks, they must nonetheless be adapted to reflect the novel aspects associated with the threats from intentional misuse of biological agents against agriculture and the food supply. Closer attention to the novel aspects of agroterrorism can provide a clearer understanding of the risk assessment and risk management strategies needed to account for the possibility of deliberate misuse, and can help to overcome vulnerabilities in existing biosecurity control measures.
6.3 Risk Paradigms for Crop Biosecurity
Pest Risk Analysis attempts to assess the probability of introduction, establishment and spread of a particular pest or pathogen in a specified PRA area and the resulting consequences, usually measured in terms of direct and indirect economic costs, of a potential outbreak (IPPC 2007). In this context, biosecurity risks are represented as the outcome of a unidirectional process that links potential agents (insects, fungi, bacteria or viruses) with vulnerable receptors (crops, forests or broader social and economic systems). Illustrated in Fig. 6.2, the ‘Agent-Pathway-Receptor’ (A-P-R) model is central to PRA outlined in the international standard by the International Plant Protection Convention (IPPC 2004). Stakeholders may have different priorities in relation to the implementation of biosecurity controls. For example, the IPPC is concerned primarily with facilitating safe trade, recommending export restrictions as a last resort, whereas the Convention on Biological Diversity (CBD) (1992) is concerned primarily with protecting vulnerable ecosystems, habitats and species, advocating a precautionary approach to biosecurity. However, the overriding view of biosecurity risks remains much the same. Biosecurity risks are perceived to arise when vulnerable receptors are brought into contact with harmful biological agents by way of natural or unintentional processes.
This risk paradigm, however, does not fully account for the case of agroterrorism. Agroterrorism, a deliberate act of political, economic or personally motivated violence, is determined by the choices of rational actors (Mair and Mair 2003) or ‘intelligent adversaries’ (National Research Council 2008). These perpetrators attempt to identify and bypass biosecurity controls that would limit the outcome of the A-P-R process. The probabilities that apply to inspections or quality standards in a conventional pest risk assessment would no longer be valid in an agroterrorism risk assessment. Perpetrators may also be opportunistic, choosing targets based on perceived vulnerabilities, selecting the agents, pathways and receptors that are best suited to achieving their particular goals, within the limits of their capabilities (Mair and Mair 2003; National Research Council 2008; Radosavljevic and Belojevic 2009). Therefore, while a biological agent, once it has been introduced to a particular PRA area, will behave in the same manner regardless of whether it has been unintentionally or deliberately released, the steps that lead up to the point of introduction depend upon several considerations that are beyond the scope of the standard risk paradigm associated with natural or unintentional outbreaks.
Recent work by agricultural scientists and security experts has helped demonstrate how traditional approaches to PRA can be revised to account for the novel aspects of agroterrorism (European Commission 2007; Latxague et al. 2007; Radosavljevic and Belojevic 2009; Suffert et al. 2009; Ancona et al. 2010). For example, according to Latxague et al. (2007), standard PRA schemes should be amended to account for at least five further variables or criteria, including: (1) the ease of use of the pathogen, (2) the epidemic potential of the pathogen, (3) the importance of the target crop, (4) potential obstacles to swift and effective response, and (5) potential regional or global consequences of a planned attack. These considerations illustrate that in adapting a PRA to the problem of deliberate misuse, risk managers must take into account not only the biological characteristics of a harmful invasive species, but also the motive and capabilities of perpetrators (Fig. 6.1).
In terms of motive, for example, if the primary objective of a terrorist group is to destabilise a national economy, the group will likely target a key agricultural commodity with a view to generating trade restrictions on valuable export markets. Alternatively, if the primary objective is to generate casualties, the group will attempt to release a pathogen that is capable of generating illness in humans.
In relation to capability, a terrorist group would also take into account the feasibility of an attack given their perceived scientific and technical skills and facilities. Although it may be desirable from the point of view of a terrorist group to undermine a national economy by causing damage to a key agricultural commodity, possibly including large areas of cultivated land, it may not be within the scope of their capabilities to produce and disseminate a biological weapon that is capable of generating large-scale losses of this kind. In practice, there exist significant barriers to acquiring a sui biological agent, culturing sufficient quantities of infectious material, and developing an effective delivery system that is capable of disseminating this material over a large area (Office of Technology Assessment 1993). Based on the principle that the non-proliferation of chemical biological, radiological and nuclear (CBRN) weapons aims to protect the human population worldwide, an international list of biological agents was established for export control, considering that they could be misused as bioweapon against crops (see Chap. 2). The impact of such export controls in the dissemination of these problematic species should not be dismissed, but it cannot completely prevent a malicious, competent perpetrator to procure them. During this multi-step process, referred to as a proliferation pathway, there exist multiple avenues for failure, each of which would undermine the realisation of a particular attack. Consequently, in the absence of significant financial and technical resources, terrorist groups are most likely to pursue relatively simple proliferation pathways, producing a more localised impact on agriculture, the food supply or the environment.
A further dimension of agroterrorism that complicates standard approaches to PRA is the potential for perpetrators to identify and exploit vulnerabilities in agricultural, environmental, and social systems. The concept of vulnerability is used to express that some receptors (for example, a particular crop) are more prone to ecological and/or economic damage than others (Mumford et al. 2011). While this observation also applies to natural or unintentional outbreaks, it is especially relevant in relation to agroterrorism. This is because perpetrators can choose (within the limits of their capabilities and motives) specific agents, pathways and receptors, and are thus able to adjust their tactics in relation to perceived vulnerabilities. This means, for example, that a terrorist group might target a crop that is relatively isolated, lacking adequate biosecurity controls, or target a species of tree that is especially valuable or of symbolic significance to a country, or introduce a pathogen for which vaccines are unavailable. Although one cannot account for an infinite range of contingencies, identifying vulnerabilities of this kind is an essential component of PRA adapted to the case of agroterrorism. It also illustrates a significant difference in security and biosecurity risks. The focal points of trade risks are the probabilistic relationship between the quality of the imported material and the efficiency of the controls and inspections on the delivery pathway. For security risks, there is much more emphasis on the possible relationships between perpetrator motives and receptor vulnerabilities, while the delivery aspects are relatively certain, since they are in the hands of the perpetrators unless they are thwarted.
In light of these considerations, it is apparent that standard approaches to PRA cannot be directly applied to the case of deliberate misuse. Although these approaches can be used to understand the mechanisms of disease outbreaks, informing the choice of phytosanitary measures, they do not account for the role played by rational actors in influencing the outcome of the A-P-R process. Therefore, an alternative risk paradigm is needed, one that accounts for the motives and capabilities of potential attackers, as well as for their capacity to identify and to exploit vulnerabilities. Conceptually, this new paradigm can once again be represented as a unidirectional process linking potential agents with vulnerable receptors. However, in this instance, as illustrated in Fig. 6.3, this process is driven by rational choices and the motives and capabilities of potential attackers who pursue particular goals in light of perceived vulnerabilities in agricultural, environmental, and social systems.
6.4 Real and Perceived Risk: Understanding the ‘Impact’ of Agroterrorism
A distinctive feature of agroterrorism is that even an ‘unsuccessful’ attack or a ‘successful’ hoax (if made public) could generate fear, reduce consumer confidence, and possibly undermine social stability (Chalk 2001; Turvey et al. 2003; Cupp et al. 2004; Byrne 2006; Eggers et al. 2011). Fischhoff (2011) has observed that terrorist attacks of this kind not only have the potential to “inflict direct damage to the people they injure, to the economies they disrupt, and to the leaders they discredit”, but also to “inflict indirect damage by instilling fear over who will be next, by undermining investors’ confidence in future economic activity, and by eroding faith in governments that cannot protect their people”. Therefore, in addition to the direct and indirect economic costs associated with diminished crop yields, compensation to farmers, export restrictions, and so on, an agroterrorism attack has the potential to generate costs to society that are disproportionate to the actual magnitude of a disease outbreak. In other words, the anticipated ‘impact’ of agroterrorism needs to take into account the manner in which individuals and communities perceive and respond to attacks on agriculture and the food supply.
Work on risk perception also illustrates how the public might respond to an (anticipated) agroterrorism attack. Slovic (1987) suggests that hazards tend to be assessed on the basis of intuitive judgments that do not necessarily correlate with expert assessments of expected annual fatalities, economic costs, and so on. In particular, hazards that are perceived to be uncontrollable, catastrophic, new or highly uncertain (for example, nuclear accidents) tend to generate considerable concern, even though the hazard itself may be infrequent and of limited magnitude. Consequently, Slovic suggests, risk assessments must take into consideration not only anticipated losses to life, to property, and so on, but also the particular characteristics of an event, which, for many, serve as indicators or signals for the event itself.
Like the threat of nuclear accidents, agroterrorism attacks (both real and foreseen) have the potential to elicit considerable societal alarm. Indeed, research has shown that threats to the food supply, especially when linked with terrorism, strongly resonate with perceptions of catastrophic harm, evoking heightened anxiety comparable to perceptions of natural disasters (Eggers et al. 2011). Moreover, it is necessary to differentiate between different types of attack. For example, agroterrorism attacks employing zoonotic disease agents are likely to be of greater concern than attacks that affect only plant health, due to fears about human contagion and disease (Chalk 2001). An attack (or the threat of an attack) not only represents a source of societal concern, it would also likely have significant repercussions for the agriculture sector and for the food industry, changing consumer buying behaviour, as well as diminishing public confidence in government’s capacity to protect the food supply (Turvey et al. 2003).
In this light, if PRA is to be successfully adapted to the case of agroterrorism, expert assessments must take seriously the manner in which individuals and communities understand threats to agriculture and the food supply, and how perceived risks influence individual and collective behaviour. Whereas PRA has traditionally focused on calculating the economic costs (resulting from diminished crop yields, export restrictions, and so on) of natural or unintentional disease outbreaks based on scientific knowledge and statistics (Dahlstrom et al. 2011), PRA adapted to the case of agroterrorism must take into account both the scientific facts about pest or disease transmission and the social ramifications of potential attacks on agriculture and the food supply. Although these social values may be more challenging to assess by strict adherence to probabilistic models, they must nonetheless be accounted for in the risk calculation.
Finally, a more nuanced understanding of how individuals and communities perceive and respond to threats to agriculture and the food supply is also essential for developing communication strategies that limit public anxiety and concern during an agroterrorism event (including a publicised hoax). Terrorist groups may be well aware of the psychological impact of their actions and before, during and after an attack may seek to generate fear, create confusion, and foment dissent in an effort to “advance their cause even when their operations fail” (Fischhoff 2011). In turn, the success of communication strategies will depend upon the capacity of government authorities to provide timely information on the nature of agroterrorist threats, helping to maintain (or restore) public trust and enable rapid recovery.
6.5 Agroteterrorism Scenarios and Risk Analysis
Having highlighted how agroterrorism challenges the standard approaches to PRA and traditional understandings of biosecurity in agriculture, in this section we describe the development of a risk analysis model that can explicitly account for the problem of deliberate misuse or intentional introductions in agriculture, the food chain or the environment, while retaining features of conventional trade related pest risk assessment.
6.5.1 The Role of Scenarios and Why They Were Developed
Agroterrorism is considered in the broad sense to include anti-crop bioterrorism and the use of bioweapons against crops through the “intentional use (as well as the threat or simulation of use) of plant pathogens (fungi, bacteria, viruses) by any human individual or group in order to cause direct damage to crops or forests, or to indirectly affect the agricultural sector” (Latxague et al. 2007). The only modification of this definition is that the term ‘plant pathogens’ may be extended to ‘plant pests’ (fungi, viruses, bacteria, nematodes, insects, and so on) in the framework described in the PLANTFOODSEC project.
In the earlier CROPBIOTERROR project, a three-step methodology was developed for risk assessment, involving: (1) building a list of 50 candidate pathogens, (2) a scenario-based investigation of potential deliberate misuse events, and (3) the design of a risk evaluation scheme (RES), derived from a standard Pest Risk Analysis (PRA) scheme, originally used to decide whether an organism should be placed on plant health quarantine lists. In the PLANTFOODSEC project, we developed a risk assessment tool consisting of a foresight exercise (assigning 51 key pests and pathogens to different motive-receptor scenarios and comparing these based on specific criteria) and an analytical assessment (application of an adapted RES to the key agent-pathway options and qualitative analysis resulting in scenario specific risk profiles). Building these scenarios was an important part of the methodology developed to assess agroterrorism risks in Europe, because we cannot experiment with dangerous pests and because there are very limited historical precedents (beyond the activities of former biological weapons programmes) for agroterrorism, which could otherwise have been analysed. Suffert et al. (2009) give a list of biological weapons threats to agriculture in the twentieth century, most relating to the (alleged) activities of former biological weapons programmes. The historical review of anti-crop bioweapons given in Chap. 2 is the starting point of the characterization and context of the threat in Europe (Table 6.1).
Nine different, non-overlapping scenarios of agroterrorism attacks (Latxague et al. 2007) were developed. These general scenarios were demonstrated by selecting a pest or pathogen taken from the list of candidate organisms, together with a motive-pathway related to the nature of the acts and the agent-receptor relationship that results in their potential consequences. For each scenario, INRA scientists experienced in conventional PRA took the role of an imagined perpetrator: they defined a tangible target and selected the most appropriate pest or pathogen from the list of candidate organisms. Based on this, the risk analysts wrote a brief scenario describing the hypothetical agroterrorist attack and its expected consequences.
The three sections of the scenarios: ‘Synopsis’ (mode of operation and expected consequences), ‘Justification’ (geopolitical context and perpetrator motivations), and ‘Feasibility’ (perpetrator capability to succeed and technical constraints) were substantiated with information extracted from relevant documents or materials that cannot be found easily through conventional systems of publication, bibliographic review, or subscription.
The nine key pathogens used in the demonstration scenarios were Tilletia indica (the wheat Karnal bunt fungus), Phytophthora infestans (the potato late blight Oomycete) and Pleospora papaveracea (a potential opium poppy mycoherbicidal fungus) as biowarfare agents, Fusarium graminearum (a grain-infecting, toxinogenic fungus), Mycosphaerella populorum (the poplar stem canker fungus) and Ceratocystis fagacearum (the oak wilt fungus) as bioterrorism agents, and Xylella fastidiosa (the grapevine Pierce’s disease bacterium), Puccinia triticina (the wheat brown rust fungus) and Phakopsora pachyrhizi (the soybean rust fungus) as biocrime agents.
The nine scenarios involving these pathogens were then ranked for specific features and salient components consistently highlighted in the literature on agroterrorism: diversity of impacts (on production, trade, society), motive for a perpetrator to claim responsibility for the attack, availability of technical capabilities (origin of the scientific information and inoculum), possible delivery by air (considered as a classical mode of operation), and potential countermeasures (early detection, and availability of control measures). This was an initial step in choosing appropriate criteria for a risk assessment tool.
6.5.2 The Use of Scenarios in PLANTFOODSEC
In the PLANTFOODSEC project, we used the categorization of scenarios (category Biowarfare BW, Bioterrorism BT, and Biocrime BC, each with three subcases) to describe a sufficient set of cases to cover the wide range of potential threats (described in Table 2 in Chap. 2). For each of the nine subcategories we identified at least three scenarios (only one was considered in CROPBIOTERROR), including organisms encompassing all main pest groups (fungi, viruses, bacteria, nematodes, insects) to ensure the scenarios covered a broad range of threats. Only pathogens (fungi, viruses, bacteria) were considered in the earlier CROPBIOTERROR project. These scenarios (27 in total) were briefly described (with 3–4 lines) rather than the more detailed ‘Synopsis’, ‘Justification’ and ‘Feasibility’ descriptions used in the scenario reports developed in CROPBIOTERROR. These scenarios were used in the subsequent development of a model to serve as a consistent risk assessment framework.
6.5.3 Building and Validating a Novel Risk Comparison Tool Using Scenarios
Building the risk assessment tool involved three sets of experience. UNICRI and INRA experience was used to identify a range of intentional release motives. Imperial College London partners developed a Rule-based Network Model (R-bNM) using GENIE softwareFootnote 2 to assess the relative risk posed by a given scenario (not by a given pest, an important distinction, as it included more than just the agent organism itself). INRA scientists contributed to the development and testing of the model. The tool is described in detail in the next section.
The model has subsequently been tested on 98 Motive-Agent-Pathway-Receptor scenarios and an evaluation has been conducted based on comparison between the assessment of a scenario by an expert (rating + uncertainty) and the output of the model. The expertise required to parameterise the model for the scenarios was already present in the French institutions, INRA and ANSES.
Some example illustrative scenarios include:
-
BW1a – Ralstonia solanacearum in potato (Solanum tuberosum) for localised release of R. solanacearum in water (contamination of river water used for irrigation) in Northwest France in seed potatoes (plant for planting).
-
BW2a – Puccinia graminis strain Ug99 in wheat (Triticum aestivum) with mass production of inoculum and release of spores in Italy.
-
BT2b – Microcyclus ulei in rubber (Hevea brasiliensis) for contamination of Indonesian rubber plantations.
-
BT2c – Bursaphelenchus xylophilus in maritime pine (Pinus pinaster) for mass release of pine nematode (artificially multiplied in contaminated wood samples collected in Portugal) by air in pine plantations of Southwest France.
-
BT3a – Ceratocystis fagacearum in oak (Quercus robur) in simultaneous terrorist attacks against English oaks in a forest and an urban park.
-
BC2c – Leptosphaeria maculans in oilseed rape (Brassica napus) for deliberate release of a hyper-resistant and aggressive strain in experimental fields performed by a plant pathologist in response to their recent dismissal.
-
BC3a – Phakopsora pachyrhizi in soybean (Glycine max) through introduction of inoculum in Southwest France by an agrochemical company, to make farmers dependent on both tolerant soybean cultivars and a fungicide.
-
BC3c – Puccinia striiformis in wheat (Triticum aestivum) in simultaneous deliberate introductions of a new virulent P. striiformis strain in several European countries by a breeder company to modify the European panel of cultivated cultivars and promote the sale of one of its resistant cultivars.
Based on a preliminary characterization and contextualization of the threat resulting from plant pathogens misuse as anti-crop bioweapons in Europe (Chap. 2), we determined that the most problematic agroterrorism scenarios for Europe are BW1 (state-sponsored threat to export trade), BW2 (state-sponsored threat to domestic production), BT1 (terrorism threat to domestic production and health), and BC1 (attack by activists or other groups against local production).
6.6 A Rule-Based Network Model to Integrate the Components of Risk Associated with Pathogens or Arthropods Used as Crop Bioterrorism Agents
In this section we provide a description of the process outlined above, in which the development of a model and its parameterisation is explained for a set of selected scenarios. A method for integrating PRA components (Holt et al. 2012), developed in the PRATIQUE project and adopted by the European and Mediterranean Plant Protection Organization (EPPO), has been adapted for the paradigms of biowarfare, bioterrorism and biocrime in PLANTFOODSEC. The system uses a combination of logical rules in a Bayesian–type network to simulate how experts express and integrate risks (Holt et al. 2013).
Aspects of pest or pathogen biology, local climate and ecology, ease of introduction and culture are combined with the pest/pathogen potential impact on crops, human health and public alarm to give an overall rating of impact. The use of a Bayesian approach allows expert uncertainty of various inputs to be expressed and explicitly incorporated in the overall summary. It also allows for a variety of rules to be used in combining component values leading to intermediate and final conclusions. Some examples of these combinations are given later in this section. A template for collecting expert ratings was also developed in which ratings of 15 input questions (and associated uncertainty) have been collected for a wide range of scenarios.
6.6.1 Components of Risk
There are 15 components of risk distinguished in the model, and an overall subjective assessor rating by a pest risk analyst can be used as a comparator in calibrating the system (Table 6.1).
These components are rated nodes in which the user is required to select or rate the most appropriate choice from a list that describes that component (from very low to very high likelihood or impact, or very difficult to very easy). An expression of uncertainty is also incorporated such that the assessors should first give a rating that is judged most appropriate and then describe their uncertainty (low, moderate or high) that this chosen rating is in fact the correct one. Inputs are elicited from experts using a specifically designed template (Table 6.2). A frequency distribution (Holt et al. 2013) is then generated which describes that component, low uncertainty implies a narrow distribution and high uncertainty, a wider one. For both the scoring for the rating and the uncertainty the expert is expected to provide documentation or comments that allow independent review of the scores.
6.6.2 Combining Risk Components
The components are integrated two at a time in a sequence of nodes describing more aggregated concepts. They are combined two at a time to make it easier to describe the logic of the way the components should come together to affect the final result. Figure 6.4 shows the topology of the model as a screenshot of the working tool, with some demonstration results with parameters estimated for pine wood nematode in maritime pine.
The combination logic is as follows:
-
‘Entry and production’ takes the lower of its two inputs (‘01 Ease of importation’, ‘02 Ease of pathogen culture’), the logic being that both are required for the pathogen to pose a risk, so the lower of the two is the limiting factor. The same logic applies when combining the result with ‘03 Ease of release and inoculation’; the result ‘Feasibility’ is constrained by the minimum of the three components: 01, 02 and 03.
-
‘Establishment’ takes the larger of its two inputs (‘04 Pathogen infectivity in the environment’, ‘05 Persistence of pathogen in the environment’) so whichever is the higher of these two properties is taken as the best indicator of likelihood of establishment.
-
Successful introduction requires both ‘Feasibility’ and ‘Establishment’, so the node ‘Likelihood of successful introduction’ takes the lower of its two inputs. ‘Extent of infection’ also requires spread, so again this node takes the lower of its two inputs.
-
The other main branch of the network concerns impact and two aspects are considered, impact on trade and non-trade values. For non-trade ‘10 Pathogen toxicity to host plant consumers’ (due to mycotoxins) and ‘08 Pathogen severity to host plant’ (impacting on food supply) are considered, while it is necessary to consider ‘07 Host importance’ in both cases. For trade values ‘07 Host importance’ and’09 Introduction would damage trade’ are also considered. The impact on health or on the commodity is determined by the toxicity/severity when the crop importance is greater and not regarded as limiting. Otherwise the impact is reduced by lower crop importance with toxicity or severity and commodity importance having equal weights and the nodes take the average of their two inputs.
-
The potential impact combines the impacts on health and on the commodity to reflect the greatest in combination.
-
Whether this impact actually occurs or not is calculated in the node called ‘Scientifically assessed impact’ which is a conditional node integrating the ‘Potential Impact’ and the ‘Likelihood of successful introduction’. The Impact is determined by its potential when the extent of infection is greater than the potential impact and so regarded as not limiting. Otherwise the impact is reduced by the likelihood of introduction and, assuming a uniform distribution, the result lies in the interval between the ratings for potential impact and the extent of infection.
-
We incorporate the impact of alarm entirely separately from the branch of the network concerned with technical issues. Two interest groups are distinguished: those directly concerned with the problem, ‘15 Primary stakeholder alarm’, and the general public, ‘14 Public alarm’. These are brought together by a node which indicates whether either group is alarmed.
-
Finally, alarm and impact are integrated using a conditional logic. The final impact including public and stakeholder alarm is at least as great as the calculated impact so the final impact is determined by the calculated scientific impact if its value is greater than that of social alarm. If scientific impact is less than social alarm then the result is the average; in effect, therefore, a lower level of impact is augmented in response to public alarm.
-
In addition to the ratings for the individual model components, assessors were also asked to provide an overall rating and uncertainty for the risk posed by the pathogen. This provides a basis for comparison between expert opinion and model logic.
The underlying calculation in each node determines the joint distribution of rating frequencies and according to the node rule or logic, calculates the resulting distribution seen in that node. The logic used in combining the components is both deterministic and constant. The same logic therefore applies to all cases (to aid direct comparisons between scenarios) and uncertainty is expressed in the risk components but not in the logic of their integration. The model is parameterised individually for each pathogen/host scenario and required 15 ratings (one for each rated node) and 15 expressions of uncertainty, one associated with each rating.
The underlying mechanism of the Bayesian model is consistent with expert thinking for many of the scenarios tested and for others it stimulated valuable discussion which prompted changes to the model as well as re-evaluation of inputs by the experts. The system presents a visual description of the mechanisms involved and a rational and consistent basis for the evaluation of preventative or risk mitigation strategies. A framework that is applicable to a broad set of possible scenarios has been developed and provides a benchmark to improve consistency of biosecurity assessments.
6.6.3 Overall Classification of Generic Scenarios by Integration on a Set of Pest-Crop Pairs
We undertook a systematic exploration of the nine general classes of scenarios by considering each case with a range of agent-receptor pairs to test the applicability of the criteria in the risk assessment and to evaluate outcomes against subjective assessments by expert assessors across all the scenarios. The goal was to assess the threat posed by each of these scenarios, irrespective of the pest and crop that is chosen. We selected 15 crop-pest pairs, from a list of 51 harmful organisms and a comprehensive list of European crops and environments of high value (Chap. 2 gives lists of pests and crops/trees). For each of these nine generic scenarios we considered plausible examples that could include each of the 15 agent and receptor combinations, although not all were relevant. There were 98 cases where some of the 15 pest-crop pairs fit into one of the nine general scenarios. Criteria included those most feasible for a perpetrator to use, and that would result in the highest impact; the 15 selected crop-pest pairs could be different for each scenario. The input data used by the PLANTFOODSEC Rule-based network model was elicited from experts for each of the 15 crop-pest pairs, in the context of each of the 98 scenarios. It was necessary to identify relevant panels of experts for each crop-pest pairing and to ensure linguistic uncertainty is minimized through a formal elicitation process. Of the 98 cases, 23 were Biowarfare, 31 were Bioterrorism, and 44 were Biocrime (Fig. 6.5). The smaller scale of biocrime scenarios may account for the greater applicability of these cases. While these cases were not selected as being representative, the range of cases allows some general observations. Biowarfare scenarios had the highest median risk score, both in terms of scientific assessment as well as with public/stakeholder impacts included. These scenarios involve high impact with substantial resources and capability. Biocrime scenarios figure prominently in the top 10 risks, probably because their small scale increases their practicality and hence likelihood. Bioterrorism scenarios had the lowest median risk scores. The risk scores take into account the full set of 15 criteria listed above.
6.7 Conclusion
There is a need for an agroterrorism risk assessment method that is consistent with pest risk assessments for introductions of pests through conventional trade or natural spread of pest organisms. This would allow agroterrorism risks to be prioritised in a proportionate manner to similar biosecurity risks. A modified Agent-Pathway-Receptor risk model adds Motive as a consideration. Agroterrorism risks are characterised by the Motive-Receptor relationship, which is best described in a risk scenario, rather than as either an agent or pathway based analysis, which is common in conventional pest risk analysis. Various agents and pathways may fit within a scenario. A broad series of hypothetical agroterrorism scenarios has been described, built on past experience from the CROPBIOTERROR project and further elaborated in PLANTFOODSEC, in which specific ‘Motive-Agent-Pathway-Receptor’ sets can be analysed as examples. A rule-based network model was developed to process relevant scoring and confidence values to rate and give a preliminary demonstration of how agroterrorism scenarios could be assessed using skills, experience, methods and terms common to plant health risk assessors. This has shown that agroterrorism risks can be assessed within a comprehensive risk analysis framework that is broadly compatible with other plant health risks.
The creation of a broad list of scenarios across the spectrum of potential threat types and calculation of risk scores from elicitations of common component values from expert assessors establishes a base of risk scores. The PLANTFOODSEC project built up a base collection of 98 such scenarios relevant across participating countries. New scenarios can be added individually, and relatively quickly, as threat scenarios arise and their relative positions can be set against the background of the scenarios already established. Scenarios can be compared across the full set of cases, or within narrower threat types, as a guide to the severity of the risk and proportionality of possible responses. The performance of management actions can be estimated against relevant components in the model to evaluate the likely return on mitigation efforts, and the addition of cost functions could provide an economic evaluation of management effort. Any of these analyses require a fundamental core that uses a standardised risk assessment framework.
Notes
- 1.
The term ‘agroterrorism’ is commonly used to refer to the ‘deliberate misuse of biological agents against agriculture by non-state actors’ (that is, a subset of ‘bioterrorism’). However, in this chapter, we also include ‘biocrime’ and ‘biowarfare’ under this general definition. Our rationale is that each of these ‘agro-risks’ represents a mode of ‘deliberate misuse’, distinct from traditional views of risk in agriculture, which focus on natural or unintentional outbreaks. Each of these risks possess some specific characteristics, so ‘bioterrorism’, ‘biocrime’, and ‘biowarfare’ are defined in legal terms (see Chap. 7) and we consider a range of deliberate misuse scenarios in our analysis.
- 2.
References
Ancona V, Appel D, Figueiredo P (2010) Xylella fastidiosa: a model for analyzing agricultural biosecurity. Biosecurity and Bioterrorism: Biodefense strategy, practice, and science. Mary Ann Leibert, Inc. http://online.liebertpub.com/doi/pdf/10.1089/bsp.2009.0021
Baker RHA, Anderson H, Bishop S, MacLeod A, Parkinson N, Tuffen MG (2014) The UK plant health risk register: a tool for prioritizing actions. EPPO Bulletin 44:187–194
Barbier M (2008) Expertise in the making about agroterrorism: issues and paradox of rationalizing hybrid threats. Presented at the Society for Social Studies of Science (4S) & European Association for the Study of Science and Technology (EASST), Rotterdam
Byrne R (2006) Horizon scanning rural crime – agroterrorism an emerging threat? Paper presented at the University of New England, Armidale, NSW, Australia, 30 November 2006
CBD (1992) Convention on biological diversity. United Nations Environment Program, New York, USA. 1760 UNTS 79; 31 ILM 818 (1992)
Chalk P (2001) Terrorism, infrastructure protection, and the U.S. Food and Agricultural Sector. RAND Testimony before the Subcommittee on Oversight of Government Management, Restructuring and the District of Columbia, US Senate, Washington, DC, USA
Cupp OS, Walker DEII, Hillison J (2004) Agroterrorism in the U.S.: key security challenge for the 21st century. Biosecur Bioterror: Biodefense Strateg Pract Sci 2(2):97–105
Dahlstrom A, Hewitt CL, Campbell ML (2011) A review of international, regional and national biosecurity risk assessment frameworks. Mar Policy 35:208–217
Department for Environment, Food and Rural Affairs (Defra) (2015) UK plant health risk register. Defra, London, UK. https://secure.fera.defra.gov.uk/phiw/riskRegister/
Eggers S, Verrill L, Bryant CM, Thorne SL (2011) Developing consumer-focused risk communication strategies related to food terrorism. Int J Food Saf Nutr Public Health 4:45–62
European and Mediterranean Plant Protection Organisation (EPPO) (2011) Decision-support scheme for quarantine pests. PM 5/3(5). EPPO, Paris, France. http://www.eppo.int/QUARANTINE/Pest_Risk_Analysis/PRA_intro.htm
European Commission (EC) (2007) Green paper on biopreparedness, 11 July 2007, Brussels. Report available at: http://ec.europa.eu/food/resources/gp_bio_preparedness_en.pdf
Fischhoff B (2011) Communicating about the risks of terrorism (or anything else). Am Psychol 66:520–531
Holt J, Leach AW, Knight JD, Griessinger D, MacLeod A, van der Gaag DJ, Schrader G, Mumford JD (2012) Tools for visualising and integrating pest risk assessment ratings and uncertainties. EPPO Bull 42:35–41
Holt J, Leach AW, Schrader G, Petter F, MacLeod A, van der Gaag DJ, Baker RHA, Mumford JD (2013) Eliciting and combining decision criteria using a limited palette of utility functions and uncertainty distributions: illustrated by application to Pest Risk Analysis. Risk Anal 34:4–16. doi:10.1111/risa.12089
International Plant Protection Convention (IPPC) (2004) Pest risk analysis for quarantine pests, including analysis of environmental risks and living modified organisms. International Standard for Phytosanitary Measures no. 11. FAO, Rome, Italy (later updates can be checked at www.ippc.int)
International Plant Protection Convention (IPPC) (2007) Framework for pest risk analysis. International Standard for Phytosanitary Measures no. 2. FAO, Rome, Italy (later updates can be checked at www.ippc.int)
Latxague E, Sache I, Pinon J, Andrivon D, Barbier M, Suffert F (2007) A methodology for assessing the risk posed by the deliberate and harmful use of plant pathogens in Europe. EPPO Bull 37:427–435
Mair M, Mair JS (2003) A complementary approach to bioterrorism prevention. Nonproliferation Rev Fall-Winter 2003:1–11
Moignot B, Reynaud P (2013) Developing a methodology for the prioritisation of pests in plant health. Euroreference 9:5–9
Mumford J, Baker R, Bremmer J (2011) Enhancement of pest risk analysis techniques: a manual and computerized consistent framework for assessing the vulnerability of receptor environments. PRATIQUE Deliverable number: 2.4. https://secure.fera.defra.gov.uk/pratique/publications.cfm#fldr_D2
National Research Council (NRC) (2008) Department of homeland security bioterrorism risk assessment: a call for change. National Academies Press, Washington, DC
Office of Technology Assessment (OTA) (1993) Technologies underlying weapons of mass destruction, OTA-BP-ISC-115. US Government Printing Office, Washington, DC
Radosavljevic V, Belojevic G (2009) A new model of bioterrorism risk assessment. Biosecur Bioterror: Biodefense Strateg Pract Sci 7(4):443–451
Slovic P (1987) Perception of risk. Science 236(4799):280–285
Suffert F, Latxague É, Sache I (2009) Plant pathogens as agroterrorist weapons: assessment of the threat for European agriculture and forestry. Food Secur 1:221–232
Turvey CG, Mafoua E, Schilling B, Onyango B (2003) Economics, hysteresis and agroterrorism. Principal paper presented at the Canadian Agricultural Economics Society 2003 Annual Meeting Montreal, Quebec, 27–30 July 2003
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this chapter
Cite this chapter
Mumford, J.D. et al. (2017). Integrating Crop Bioterrorism Hazards into Pest Risk Assessment Tools. In: Gullino, M., Stack, J., Fletcher, J., Mumford, J. (eds) Practical Tools for Plant and Food Biosecurity. Plant Pathology in the 21st Century, vol 8. Springer, Cham. https://doi.org/10.1007/978-3-319-46897-6_6
Download citation
DOI: https://doi.org/10.1007/978-3-319-46897-6_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-46896-9
Online ISBN: 978-3-319-46897-6
eBook Packages: Biomedical and Life SciencesBiomedical and Life Sciences (R0)