Abstract
Graph Neural Network based Vertical Federated Learning (GVFL) facilitates data collaboration while preserving data privacy by learning GNN-based node representations from participants holding different dimensions of node features. Existing works have shown that GVFL is vulnerable to adversarial attacks from malicious participants. However, how to defend against various adversarial attacks has not been investigated under the non-i.i.d. nature of graph data and privacy constraints. In this paper, we propose RDC-GVFL, a novel two-phase robust GVFL framework. In the detection phase, we adapt a Shapley-based method to evaluate the contribution of all participants to identify malicious ones. In the correction phase, we leverage historical embeddings to rectify malicious embeddings, thereby obtaining accurate predictions. We conducted extensive experiments on three well-known graph datasets under four adversarial attack settings. Our experimental results demonstrate that RDC-GVFL can effectively detect malicious participants and ensure a robust GVFL model against diverse attacks. Our code and supplemental material is available at https://github.com/zcyang-cs/RDC-GVFL.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Graph Neural Network (GNN) has gained increasing popularity for its ability to model high-dimensional feature information and high-order adjacent information on graphs [17]. In practice, privacy constraints prevent GNNs from learning better node representations when node features are held by different participants [6]. To enable collaborative improvement of node representation while protecting data privacy, GNN-based Vertical Federated Learning (GVFL) [2, 3, 12] employs GNNs locally for representation learning and Vertical Federated Learning (VFL) globally for aggregated representation.
An motivating example: an adversary can conduct various adversarial attacks: (a) manipulate the local connection relationship for fraudulent loan purposes by adding a connection from a low-credit user (user 1) to a high-credit user (user 0); and (b) upload the malicious embedding to deliberately misclassify the bank. To mitigate lending risks, the bank must implement effective defense measures.
In real-world applications, GVFL model is vulnerable to adversarial attacks [3]. For example, in Fig. 1, The adversary could compromise lending platform A and modify the uploaded embedding information to manipulate the bank’s eventual prediction of the user’s credit. Therefore, it is crucial for the bank to incorporate robust defensive measures, as failure to do so could result in loans being granted to users with lower credit.
However, neither graph defenses nor federated learning defenses against adversarial attacks can be directly applied in GVFL. On one hand, privacy restrictions prevent graph defenders from accessing training data and models in GVFL, which are essential for effectively implementing defense mechanisms [7, 8]. On the other hand, federated learning defenses encounter challenges when dealing with inter-dependencies among node embeddings within a graph structure. Existing approaches, such as Copur’s robust autoencoder [10, 11], assume no dependency between embeddings of each sample, but the presence of inter-dependencies among node embeddings poses a hurdle for defenders to accurately learn the appropriate feature subspace.
To address the issues above, we propose a novel Robust Detection and Correction Framework for GNN-based Vertical Federated Learning (RDC-GVFL) to enhance the robustness of GVFL. RDC-GVFL has a detection phase and prediction phase. In the detection phase, the server first requires each participant to generate local embeddings to upload. Then, the server computes each participant’s contribution to the validation set based on the Shapley Value, and identifies the participant with the lowest contribution as the malicious participant. In the correction phase, the server retrieves the relevant embeddings from historical embedding memory to correct malicious embeddings. Extensive experiments on three datasets against four adversarial attack settings confirm the effectiveness of RDC-GVFL.
The main contributions of our work can be summarized as follows:
-
We propose RDC-GVFL, a novel robust framework for GVFL, which can enhance the robustness of GVFL under various attack scenarios. To the best of our knowledge, this is the first work dedicated to defending against adversarial attacks in GVFL.
-
We present a Shapley-based detection method, enabling the effective detection of malicious participants in GVFL. Additionally, we propose a correction mechanism that utilizes historical embeddings to generate harmless embeddings, thereby obtaining accurate predictions.
-
We conduct extensive experiments on three well-known graph datasets under four types of adversarial attacks. Experimental results demonstrate the effectiveness of the RDC-GVFL for a robust GVFL system.
2 Related Works
2.1 Attack and Defense in Graph Neural Networks
Extensive studies have demonstrated that GCNs are vulnerable to adversarial attacks [17]. These attacks can be classified into two categories based on the attack stage and goal. Evasion attacks (test-time) aim to deceive the GCN during inference, and they have been studied in works such as [20]. On the other hand, poisoning attacks (training-time) occur during the training process and aim to manipulate the GCN’s learned representations, as explored in works like [19]. To enhance the robustness of GCNs, many defenses are proposed and they can be classified into three categories including improving the graph [8], improving the training [5], and improving the architecture [4] based on their strategy. However, all of these existing defenses require the defender to inspect either the training data or the resulting model, which is impractical in GVFL.
2.2 Attack and Defense in Vertical Federated Learning
Existing attacks on VFL have been shown to undermine model robustness [13]. For instance, the passive participant can launch adversarial attacks with different objectives. In targeted attacks, specific labels are assigned to triggered samples [14]. On the other hand, in non-targeted attacks, noise is added to randomly selected samples, or missing features are introduced to impair the model’s utility [11]. For defense, RVFR [10] and Copur [11] is designed to defend against adversarial attacks. These defense approaches utilize feature purification techniques. However, they can not be directly applied to GVFL since the inter-dependencies among node embeddings in a graph structure makes it challenging to learn an appropriate feature subspace for defense purpose.
2.3 Attack and Defense in GNN-Based Vertical Federated Learning
GVFL has been found to be vulnerable to adversarial attacks, as highlighted in recent studies. One such attack method, called Graph-Fraudster, was proposed to perform evasion attacks in GVFL [3]. This attack assumes that a malicious participant can infer additional embedding information of a normal participant from the server. By inferring a perturbed adjacency matrix from normal embedding, the adversary can generate malicious embeddings. In practice, the adversary can employ various attack vectors to threaten GVFL and the defense against adversarial attacks in GVFL remains an open research issue.
3 Methodology
In this section, We first describe the GVFL system and threat models of GVFL. Next, we provide an overview of the proposed RDC-GVFL framework. Finally, we present the detection and correction methods of our framework. For convenience, the definitions of symbols used in this paper are listed in the Section A of Supplemental Material.
3.1 GNN-Based Vertical Federated Learning
As described in [2], GVFL involves M participants and a server that collaboratively train a model based on a graph dataset \(G = \{G_1,..., G_M, Y\}\). Here, \(Y = \{y_j\}_{j=1}^{N}\) denotes labels of |N| nodes held by the server, and \(G_i = (V, E_i, \textbf{X}_i)\) represents the subgraph held by participant i, where \(\textbf{X}_i=\{\textbf{x}_j^i\}_{j=1}^N\) denotes the features associated with nodes V and edges \(E_i\). The training process of GVFL is similar to VFL. Firstly, each participant i extract features and obtains the local embedding \(\textbf{h}_j^i = f_i(A_i, \textbf{X}_i; \theta _i)\) of node j using its local Graph Neural Network \(f_i\). Then, the server aggregates the node embeddings from all participants and generates the label prediction \(\hat{y}_j\) for node j using its global classifier \(f_0\).
3.2 Threat Model
Adversary. There are M participants which possess distinct subsets of features from the same set of N training instances, along with one adversary attempting to compromise the GVFL system. For simplicity, we assume the adversary is one of the participants in GVFL, referred to as the malicious participant.
Adversary’s Goal. The malicious participant aims to induce the GVFL model to predict the wrong class. This may serve the malicious participant’s interests, such as earning profits by offering a service that modifies loan application results at a bank or disrupting the normal trading system.
Adversary’s Capability. We assume the training process is well-protected (attack-free). However, during the inference phase, the malicious participant can manipulate local data to send specific poisoning-embedded features to the server or send arbitrary embedded features to the server. As described in [3, 11], we characterize the malicious participant’s attack vector into the following four types and assume each malicious participant performs the same attack per round:
-
(a)
Graph-Fraudster attack [3]: The malicious participant first steals normal embeddings from other participants. Then, the malicious participant adds noise to the stolen embeddings and computes an adversarial adjacency matrix \(\hat{A}\) by minimizing the Mean Squared Error loss between the embedded features \(f(\hat{A}, \textbf{x})\) and the noise-added embedding \(\textbf{h}^m\). Finally, the malicious participant sends the poisoning embedded features based on the adversarial adjacency matrix.
$$\begin{aligned} \hat{A} = \mathop {\arg \min }\limits _{\hat{A}} MSE(f(\hat{A}, \textbf{x}), \textbf{h}^m) \end{aligned}$$(1)$$\begin{aligned} h_{gf} = f(\hat{A}, \textbf{x}) \end{aligned}$$(2) -
(b)
Gaussian feature attack: The malicious participant sends malicious feature embedding which is added by Gaussian noise.
 (3)
(3) -
(c)
Missing feature attack [11]: The malicious participant don’t send any embedded feature to the server. This can occur when the participant’s device is damaged or disconnected.
$$\begin{aligned} \textbf{h}_{miss} = \textbf{0 }\end{aligned}$$(4) -
(d)
Flipping feature attack [11]: The malicious participant sends adversarial feature embedding \(\textbf{h}_{flip}\) to mislead the server, whose magnitude \(\lambda \) can be arbitrarily large.
$$\begin{aligned} \textbf{h}_{flip} = -\textbf{h}* \lambda \end{aligned}$$(5)
3.3 Framework Overview
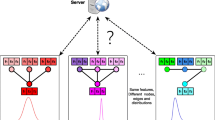
As shown in Fig. 2, we propose a two-phase framework called RDC-GVFL to enhance the robustness of GVFL. The Detection phase takes place between the model training and inference phases. During the Detection phase, the server collects the embeddings of participants from the validation dataset. Subsequently, the server calculates the contribution of each participant and identifies the one with the lowest contribution as the malicious participant. The Correction phase replaces the original model inference phase, and the server maintains an embedding memory that stores the embeddings of all training nodes. In this phase, the server utilizes normal embedding set as a query to retrieve the most similar embedding from historical embedding memory to correct the malicious embedding, thereby obtaining accurate predictions and sending them to all participants. The pseudo-code for RDC-GVFL is given in Algorithm 1.
Overview of the RDC-GVFL framework including two phases: (a) detection phase: the server using a validation dataset to evaluate contribution and identify the malicious participant; and (b) correction phase: the server leveraging the historical embeddings to retrieve the relevant embedding to correct the malicious embedding for accurate predictions sent to all participants.
3.4 Malicious Participant Detection
In addition to the training and testing processes of GVFL, we introduce a Detection phase to detect the malicious participant. In this phase, we propose a Shapley-based method to detect the malicious participant and it consists of three stages: embedding collection, contribution evaluation and malicious participant detection.
-
(a)
Embedding collection. The server maintains a validation dataset \(\mathcal D_{val} = \{V_{val},Y_{val}\}\), which is used to mandate each participant generates a local embedding and sends it to the server. A normal participant i will send the embedding \(\textbf{h}_v^i\) of node \(v \in V_{val}\) to the server while the malicious participant m, unaware of the server’s detection process, will upload a poisoning embedding \(\textbf{h}_v^m\). As a result, the server collects a set of local embeddings aligned with its validation set.
-
(b)
Contribution evaluation. We leverage Shapley Value, a fair contribution valuation metric derived from cooperative game theory, to evaluate contribution in GVFL. Specifically, we define the value function of a set of embeddings \(F_v(S)\), which indicates whether the correct classification of node v can be achieved by making prediction using only the set S. The server then considers the total marginal value of each embedding \(\textbf{h}_v^i\) across all possible sets S as the contribution of participant i. This can be formalized as follows:
$$\begin{aligned} F_v(S) = \mathbb {I}(f_0(Agg(S), \theta _0)=y_v) \end{aligned}$$(6)$$\begin{aligned} \phi _v^i(\{\textbf{h}_v^i\}_{i=1}^M)=\sum _{S\subseteq (\textbf{h}_v^1,...\textbf{h}_v^M)\backslash {\textbf{h}_v^i}}\frac{|S|!(M-|S|-1)!}{M!}(F_v(S\cup {\textbf{h}_v^i})-F_v(S)) \end{aligned}$$(7) -
(c)
Malicious participant detection. After the embedding collecting stage and contribution computation stage, the server accumulates the contributions of each participant on the validation set and identifies the participant with the lowest total contribution as a potential malicious participant \(\hat{m}\). Based on this identification, the server may impose penalties on the malicious participant. This can be formalized as follows:
$$\begin{aligned} \hat{m} = \mathop {\arg \min }\limits _{i} \sum _{v=1}^{|\mathcal D_{val}|} \phi _v^i(\{\textbf{h}_v^i\}_{i=1}^M) \end{aligned}$$(8)
3.5 Malicious Embedding Correction
In the Correction phase, we leverage historical node embedding for correcting malicious embedding, which relies on the inter-dependency between nodes in the inference phase and nodes in the training phase. Specifically, during this phase, the server is already aware of the identity of the malicious participant, and it maintains a node embedding memory \(\textbf{M}\in \mathbb R^{N \times M}\) that stores the embeddings of all training nodes from all participants. When the GVFL model performs inference, i.e. each participant i sends its embedding \(\textbf{h}_j^i\) of node j to the server requesting prediction, the server will utilizes normal embedding set \(\{\textbf{h}_j^k\}\) where \(k \in [M]\setminus m\) as a query to retrieve the most similar embedding \(\textbf{h}_{\ell }^m\) from the node embedding memory \(\textbf{M}\). Subsequently, the malicious embedding \(\textbf{h}_j^m\) is corrected or adjusted according to the \(\textbf{h}_{\ell }^m\). This process can be formulated as follows:

4 Experiment
In this section, we carefully conduct comprehensive experiments to answer the following three research questions.
RQ1 Does the Shapley-based detection method within the RDC-GVFL framework have the capability to detect malicious participants?
RQ2 How does the performance of the RDC-GVFL framework compare to that of other defense methods?
RQ3 How does discarding the malicious embedding directly without correcting it affect the robustness?
4.1 Experiment Settings
Datasets. We use three benchmark datasets, i.e., Cora, Cora_ML [15] and Pubmed [16]. Dataset statistics are summarized in Table 1. The details of partition and evaluation strategies are described in the Section B of Supplemental Material.
Baseline Methods. We compare with 1) Unsecured: no defense. 2) Krum [1]: As no prior research has focused on robust GVFL, We borrow the idea of Krum which is the most well-known robust algorithm in FL to identify the participant with the highest pair-wise distance as the malicious participant, and discard its embedding for defense. 3) RDC w/o Cor.: We employ the RDC-GVFL framework to detect malicious participants, and subsequently, we directly discard the embedding associated with the identified malicious participant as a defense measure. 4) Oracle: where there is no attack. We use GCN [9] and SGC [18] as the local GNN model, the details of these models and parameter settings are shown in the Section B of Supplemental Material.
4.2 Detection Performance(RQ1)
To answer Q1, we measured the detection rate of our detection method under the various attack settings, where the detection rate is calculated as the ratio of detected malicious participants to the total number of potential cases of malicious participants. We summarized the results in Table 2. Based on this results, we can draw several conclusions.
-
RDC-GVFL can effectively detects malicious participants across different attack scenarios: Our detection method exhibits a high detection rate for identifying malicious participants in diverse scenarios. Specifically, our method achieves a 100% recognition rate against Missing attack and Flipping attack, while in other attack scenarios, the recognition rate remains above 78%.
-
RDC-GVFL is more effective against more significant attacks: The effectiveness of identification increases as the attacks become more significant. For example, GF and Gaussian attacks exhibit higher effectiveness when the local model is SGC, and RDC-GVFL is capable of identifying the malicious participant in all these scenarios.
To better illustrate the effectiveness of the detection method, we visualize the contribution of each participant before and after the attack. These results can be found in Section C of Supplemental Material.
4.3 Defense Performance(RQ2-RQ3)
To answer Q2-Q3, we conducted a series of experiments with different defense methods against various attack scenarios. The results based on GCN are summarized in Tabel 3 and the other results based on SGC can be found in Section D of Supplemental Material. Observations are concluded in this experiments.
-
RDC-GVFL exhibits a higher level of robustness compared to other defense methods: RDC-GVFL consistently outperforms unsecured and Krum under various attack scenarios. For instance, on the GVFL based on two participants with Cora dataset, when a malicious participant performs Flipping attack, our RDC-GVFL framework demonstrates a remarkable accuracy improvement from 20.50% to 70.76%, while Krum only manages to enhance the accuracy to 28.01% from the same starting point of 20.50%.
-
Discarding malicious embeddings harms GVFL: RDC-GVFL without correction does not generally improve accuracy compared to unsecured. This observation suggests that malicious embeddings contain information useful for model prediction, emphasizing the importance of their correction.
-
Negligible loss of accuracy with RDC-GVFL: In the absence of an adversary, the use of the RDC-GVFL framework results in a maximum accuracy degradation of less than 10%. However, in the presence of an adversary, the RDC-GVFL framework can significantly enhance model accuracy and ensure the robustness of the GVFL system.
5 Conclusion
In this work, we introduced a novel robust framework of GVFL integrated with the Shapley-based detection and the correction mechanism to effectively defend against various attacks during inference in GVFL. In addition, the proposed detection method may have much wider applications due to the post-processing property. Through extensive experiments, we have demonstrated that our framework can achieve high detection rates for malicious participants and enhance the robustness of GVFL. For future work, we plan to extend our method to more scenarios and explore more effective defense methods for robust GVFL.
References
Blanchard, P., El Mhamdi, E.M., Guerraoui, R., Stainer, J.: Machine learning with adversaries: byzantine tolerant gradient descent. In: Advances in Neural Information Processing Systems, vol. 30 (2017)
Chen, C., et al.: Vertically federated graph neural network for privacy-preserving node classification. arXiv preprint arXiv:2005.11903 (2020)
Chen, J., Huang, G., Zheng, H., Yu, S., Jiang, W., Cui, C.: Graph-Fraudster: adversarial attacks on graph neural network-based vertical federated learning. IEEE Trans. Comput. Soc. Syst. 10, 492–506 (2022)
Chen, L., Li, J., Peng, Q., Liu, Y., Zheng, Z., Yang, C.: Understanding structural vulnerability in graph convolutional networks. arXiv preprint arXiv:2108.06280 (2021)
Feng, W., et al.: Graph random neural networks for semi-supervised learning on graphs. Adv. Neural. Inf. Process. Syst. 33, 22092–22103 (2020)
Fu, X., Zhang, B., Dong, Y., Chen, C., Li, J.: Federated graph machine learning: a survey of concepts, techniques, and applications. ACM SIGKDD Explor. Newsl. 24(2), 32–47 (2022)
Jin, W., Ma, Y., Liu, X., Tang, X., Wang, S., Tang, J.: Graph structure learning for robust graph neural networks. In: Proceedings of the 26th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, pp. 66–74 (2020)
Jin, W., Zhao, T., Ding, J., Liu, Y., Tang, J., Shah, N.: Empowering graph representation learning with test-time graph transformation. arXiv preprint arXiv:2210.03561 (2022)
Kipf, T.N., Welling, M.: Semi-supervised classification with graph convolutional networks. arXiv preprint arXiv:1609.02907 (2016)
Liu, J., Xie, C., Kenthapadi, K., Koyejo, S., Li, B.: RVFR: robust vertical federated learning via feature subspace recovery. In: NeurIPS Workshop New Frontiers in Federated Learning: Privacy, Fairness, Robustness, Personalization and Data Ownership (2021)
Liu, J., Xie, C., Koyejo, S., Li, B.: CoPur: certifiably robust collaborative inference via feature purification. Adv. Neural. Inf. Process. Syst. 35, 26645–26657 (2022)
Liu, R., Xing, P., Deng, Z., Li, A., Guan, C., Yu, H.: Federated graph neural networks: Overview, techniques and challenges. arXiv preprint arXiv:2202.07256 (2022)
Liu, Y., et al.: Vertical federated learning. arXiv:2211.12814 (2022)
Liu, Y., Yi, Z., Chen, T.: Backdoor attacks and defenses in feature-partitioned collaborative learning. arXiv preprint arXiv:2007.03608 (2020)
McCallum, A.K., Nigam, K., Rennie, J., Seymore, K.: Automating the construction of internet portals with machine learning. Inf. Retrieval 3, 127–163 (2000)
Sen, P., Namata, G., Bilgic, M., Getoor, L., Galligher, B., Eliassi-Rad, T.: Collective classification in network data. AI Mag. 29(3), 93–93 (2008)
Wu, B., et al.: A survey of trustworthy graph learning: reliability, explainability, and privacy protection. arXiv preprint arXiv:2205.10014 (2022)
Wu, F., Souza, A., Zhang, T., Fifty, C., Yu, T., Weinberger, K.: Simplifying graph convolutional networks. In: International conference on machine learning, pp. 6861–6871. PMLR (2019)
Zhang, S., Chen, H., Sun, X., Li, Y., Xu, G.: Unsupervised graph poisoning attack via contrastive loss back-propagation. In: Proceedings of the ACM Web Conference 2022, pp. 1322–1330 (2022)
Zügner, D., Akbarnejad, A., Günnemann, S.: Adversarial attacks on neural networks for graph data. In: Proceedings of the 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, pp. 2847–2856 (2018)
Acknowledgement
This work was supported by Natural Science Foundation of China (62272403, 61872306), and FuXiaQuan National Independent Innovation Demonstration Zone Collaborative Innovation Platform (No.3502ZCQXT2021003).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
1 Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Yang, Z., Fan, X., Wang, Z., Wang, Z., Wang, C. (2024). A Robust Detection and Correction Framework for GNN-Based Vertical Federated Learning. In: Liu, Q., et al. Pattern Recognition and Computer Vision. PRCV 2023. Lecture Notes in Computer Science, vol 14427. Springer, Singapore. https://doi.org/10.1007/978-981-99-8435-0_8
Download citation
DOI: https://doi.org/10.1007/978-981-99-8435-0_8
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-8434-3
Online ISBN: 978-981-99-8435-0
eBook Packages: Computer ScienceComputer Science (R0)