Abstract
In this research, a high capacity reversible data concealing strategy has been developed for secure data transfer utilizing multi-level pixel value ordering (MPVO) and center-folding strategy. Center-folding strategy was first used to insert hidden information into an interpolated cover picture, creating dual marked images (DMI). Subsequently, multi-level pixel value ordering uses to incorporate more hidden information on dual marked images. The center-folding approach has been used in this case because it offers the benefit of compressing important hidden information via averaging. By using neighboring and reference pixels, MPVO, on the other hand, offers the ability to embed an image block with more than two pixels. The secret data’s changing size and the varying picture block sizes required for effective embedding make the suggested technique very adaptable. In comparison with the previous state-of-the-art approaches, the experimental results reveal that the suggested method is particularly suited for embedding more concealed data without degrading the visual quality of the picture. The expected outcome brought to light several outstanding capabilities in the fields of covert data transmission, tamper detection, and digital forgery detection, without which the development of technology would be severely hindered. This program greatly benefits several aspects of the public and corporate sectors, such as health care, business security, defense, and rights to intellectual property.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Reversible data hiding
- Multi-level pixel value ordering
- Center-folding
- Embedding capacity
- PSNR
- Steganography
1 Introduction
The secret information is hidden under text documents, cover pictures, or any other types of multimedia as a data carrier in the data concealing technique in order for the recipient to effectively decipher the message. Reversible and irreversible information concealment techniques are based on the reconstruction of the original picture. Reversible data concealing techniques, also known as lossless information hiding, should always be used in sectors that are particularly susceptible to picture distortion, such as the medical, military, and scientific ones. Although non-reversible data hiding techniques normally have high embedding capacities, there are several limitations in the application domains since the cover image was irreparably lost after stuffing the secret information. After the extraction procedure is successfully finished, the secret data and the cover picture may be rebuilt. This study fixes secrets into image pixels using the RDH technique as its foundation. Reversible approaches can recreate the true cover picture after data extraction, whereas irreversible methods are insufficient to do so. In order to integrate hidden messages into cover graphics, this research explores reversible data concealing techniques.
In 2003, Tian [17] wrote up a method for hiding information within a pair of pixels called difference expansion (DE). It outlines how the picture was produced in order to get high embedding data with little distortion. A lossless information concealing approach that allows distortion to be completely erased from the annotated picture was presented by Lee et al. [3] in 2005. Additionally, the secret data was extracted from the marked picture. Li et al. [4] presented pixel value ordering-based information concealing techniques in 2013 where minimum and maximum pixels are regulated by information embedding. This demonstrates a high-fidelity RDH system for pictures using a novel approach that incorporates the information via prediction error expansion (PEE). Peng et al. [15] improved the PVO that Li et al. had shown by computing additional pixel differences and using new histogram modifications. Jana [1] has described a high payload-based data concealing approach using sub-sample.
The remainder of the study is organized as follows: Sect. 2 explores the literature review. Section 3 explores the suggested embedding and extraction procedure. In Sect. 4, the comparisons and observational findings are discussed. The conclusions of the suggested approach are examined in Sect. 5.
2 Literature Review
Several reversible data hiding methods have recently been published by researchers. The center-folding method was used by Lu et al. [5] to approach reversible data concealing. It employs two copies of the original picture to achieve high embedding. The hidden message is folded and after that embedded into dual marked-images in this approach. In 2018, a technique [2] was put out to reduce distortion and preserve the authenticity of forgery alteration in dual stego-images. Meikap et al. [9,10,11] spoke about PVO-based RDH methods that improved the high data bit capability. In 2021, the [5] was changed from having a single layer to having numerous levels in order to present an improved interpolation-based concealment strategy [7]. Center-folding-based reversible information hiding methods [12, 13] were introduced in the year 2021. In 2022, [14] employed dual-image to build a shift technique that enables secret data to be inserted in those pixels that were previously exclusively altered in PVO-based schemes. The difficulty is to enhance payload by thinking about embedding in more than two pixels using references and neighboring pixels inside an image block after folding the message and inserting it into image pixels. To address these issues, we developed an improved multi-level PVO (IMPVO) with various block size information concealing mechanism based on center-folding. The strength of security is increased by our recommended approach. The q data set is used to translate the secrets into decimal values during the first embedding. Second, during second embedding, the embed procedure depends on the quantity and size of picture blocks. Third, the data is split across two pictures. The size of the image block, the quantity of image blocks, the value of q, and two stego-images are necessary for message retrieval. The aforementioned criteria are required if an unauthorized individual wants to view the message. Unauthorized individuals may find it challenging.
3 Proposed Method
In this part, we suggested the process of improved multi-level PVO (IMPVO) secret embedding and extraction using the center-folding approach. By maintaining picture quality along with our recommended improved multi-level PVO method, we seek to maximize the embedding capacity. The following stages are used to organize the whole procedure.
3.1 Data Embedding Phase
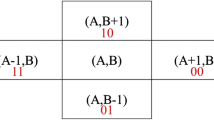
Step 1: By averaging the neighboring pixels, we enlarge these pictures using the interpolation technique presented in Fig. 1. If the picture size is \((w \times w)\), the interpolated image will be \((w+(w-1))\times (w+(w-1))\), where \((w-1)\) is the interpolated row/column. For making rows and columns even, one is added to each, and the previous row’s and column’s value is copied.
Step 2: The cover picture is \(IC=\{pix_{1,1},\ldots ,pix_{w,h}\}\), where w as well as h stand for width and height of image, respectively. Every q bit is taken as a set by the secret information, which is then modified to a decimal using the hidden symbol \(d_{s}\). The symbol range is then adjusted from \(Q=\{0,1,\ldots ,2^{q}-1\}\) to \(R^{'}=\{-2^{q-1},-2^{q-1}+1,\ldots ,-1,0,1,\ldots ,2^{q-1}-2,2^{q-1}-1\}\) using the concealed symbol \(d_{s}\). The following formula may be used to determine the folded hidden symbol \(d_{s}^{'}\):
where \(2^{q-1}\) denotes in-between values. The process of inserting concealed data can be done by
Here, \(d_{s1}^{'}\) as well as \(d_{s2}^{'}\) are obtained from \(d_{s}^{'}\). The following equations create dual marked pixels \(pix_{i,j}^{1}\) and \(pix_{i,j}^{2}\) by inserting these values into the pixel \(pix_{i,j}\).
The hidden data is concealed in pixels between \(2^{q-1}\) and \(256-2^{q-1}\).
Step 3: The dual interpolated stego pictures are divided into separate, overlapping K blocks in this stage. All pixels are arranged in ascending order inside each block. The threshold T value between 0 and 255 is set to have the least amount of distortion throughout the data embedding procedure. If pixels are close together, median and neighbor pixel differences are modest. When \(CL \le T\), data may be hidden, and the picture block is viewed as smooth. The picture block will be handled as a rough block if complexity level \(CL > T\) since it cannot conceal the contents. The median value is calculated from a block’s sorted pixels. The reference pixel M used to represent this median value. The n pixels that surround the current block in the left, bottom, right, and top positions are referred to as its neighbor pixels \(O_{P}\). The complexity level CL is calculated as the sum of the absolute differences between each neighboring pixel and the reference pixel. This is produced using the formula (4).
It has two median values for even-numbered pixels. For this, the median value with the high positioned is chosen as M. It comprises one median value that is chosen for M for pixels with an odd number. Equations (6) and (5) are used to produce the reference pixel M and its location ml from an image block \((wbl \times hbl)\) comprising n pixels.
The arrangement of the pixels in a block is hampered since the secrets are integrated into more than one minimum and/or maximum pixel in this instance. We introduce the \(\eta \) value to keep the order. Maximum pixels are increased by eta, while minimum pixels are decreased. The value of \(\eta \) changes after each repetition. Lemma 1 and Lemma 2 affect how much \(\eta \) is worth.
Lemma 1
If the number of pixels of a block is \(bl_{w\times h}\)=ODD and increasing wise sorted pixels are \((pix_{1},pix_{2},\ldots ,b_{(w\times h)})\) where the range of i is \(1\le i\le (w\times h)\). Then, the altered pixels are \((pix_{1}-\eta _{\text {fix}(\frac{w\times h}{2})-1}, pix_{2}-\eta _{\text {fix}(\frac{w\times h}{2})-1-1},\ldots , pix_{(w\times h)-1} +\eta _{\text {fix}(\frac{w\times h}{2})-1-1} , pix_{(w\times h)}+\eta _{\text {fix}(\frac{w\times h}{2})-1})\), where, the \(\eta _{\text {fix}(\frac{w\times h}{2})-1}=\text {fix}(\frac{w\times h}{2})-1\). The maximal and minimal values of \(\eta \) are \((\text {fix}(\frac{w\times h}{2})-1)\) and 0, respectively.
Lemma 2
If the number of pixels of a block is \(bl_{w\times h}\) = even_number and ascending order sorted pixels are \((pix_{1},pix_{2},\ldots ,pix_{(w\times h)})\) where the range of i is \(1\le i\le (w\times h)\). Then, the altered pixels are \((pix_{1}-\eta _{\text {fix}(\frac{w\times h}{2})-1}, pix_{2}-\eta _{\text {fix}(\frac{w\times h}{2})-1-1}, \ldots , pix_{(w\times h)-1}+\eta _{\text {fix}(\frac{w\times h}{2})-2-1} , pix_{(w\times h)}+\eta _{\text {fix}(\frac{w\times h}{2})-2})\), where the \(\eta _{\text {fix}(\frac{w\times h}{2})-1}=\text {fix} (\frac{w\times h}{2}) -1\). The maximal and minimal \(\eta \) are \((\text {fix}(\frac{w\times h}{2})-1)\) and 0 respectively for minimal numbered pixels and the maximal and minimal \(\eta \) are \((\text {fix}(\frac{w\times h}{2})-2)\) and 0 respectively for maximal numbered pixels.
The pixels in an image block contain the relevant data. The following is the embedding approach:
Embedding in Minimum-Modification Assume that a sub-block bl has n pixels in it. All pixels in the sub-block are sorted in a rising-up order to produce \((pix_{\sigma (1)}, \ldots , pix_{\sigma (n)})\). We compute
Rounding the output data toward 0 is done using the \(\text {fix}()\). The smallest pixels are now converted to \(pixel^{'}\). Each action involves a modification to \(\eta \). The changed minimum pixels are obtained by
where pixels with the value \(D \in \{0,1\}\) are added.
Embedding in Maximum-Modification The following is a discussion of the data that is inserted into pixels for maximum-modification: Determine,
The maximum pixels are now converted to \(pixel^{'}\). Each action involves a modification to \(\eta \). The changed maximum pixels are obtained by
where pixels with the value \(D\in \{0,1\}\) are added. Figure 2 shows the whole embedding procedure.
3.2 Extraction Phase
Step 1: The cover image and secret data are retrieved in the reverse order at the receiver end using the same process. The stego pictures are transformed into the overlapping K blocks. The arrangement of the pixels in each block remains the same after sorting. Equations (6) and (4) reused to create the M and CL, respectively. The same threshold value is used in the data extraction. The data in this case are taken from many minimum and/or maximum values. Pixel order may thus vary. The value of \(\eta \) maintains the order of the pixels. Lemma 3 and Lemma 4 both have an impact on the value of \(\eta \).
Lemma 3
If the number of pixels of a block is \(bl_{w\times h}\)=ODD and increasing wise sorted pixels are \((pix_{1},pix_{2},\ldots ,pix_{(w\times h)})\) where the range of i is \(1\le i\le (w\times h)\). Then, the altered pixels are \((pix_{1}+\eta _{\text {fix}(\frac{w\times h}{2})-1}, pix_{2}+\eta _{\text {fix}(\frac{w\times h}{2})-1-1}, \ldots , pix_{(w\times h)-1} -\eta _{\text {fix}(\frac{w\times h}{2})-1-1} , pix_{(w\times h)}-\eta _{\text {fix}(\frac{w\times h}{2})-1})\), where the \(\eta _{\text {fix}(\frac{w\times h}{2})-1}=\text {fix}(\frac{w\times h}{2})-1\). The maximal and minimal values of \(\eta \) are \((\text {fix}(\frac{w\times h}{2})-1)\) and 0, respectively.
Lemma 4
If the number of pixels of a block is \(bl_{w\times h}\) = EVEN and increasing wise sorted pixels are \((pix_{1},pix_{2},\ldots , pix_{(w\times h)})\) where the range of i is \(1\le i\le (w\times h)\). Then, the altered pixels are \((pix_{1}+\eta _{\text {fix}(\frac{w\times h}{2})-1}, pix_{2}+\eta _{\text {fix}(\frac{w\times h}{2})-1-1}, \ldots , pix_{(w\times h)-1} -\eta _{\text {fix}(\frac{w\times h}{2})-2-1} , pix_{(w\times h)}-\eta _{\text {fix}(\frac{w\times h}{2})-2})\), where the \(\eta _{\text {fix}(\frac{w\times h}{2})-1}=\text {fix}(\frac{w\times h}{2})-1\). The maximal and minimal \(\beta \) are \((\text {fix}(\frac{w\times h}{2})-1)\) and 0, respectively, for minimal numbered pixels and the maximal and minimal \(\eta \) are \((\text {fix}(\frac{w\times h}{2})-2)\) and 0, respectively, for maximal numbered pixels.
Extraction in Minimum-Modification The extraction of message as well as reconstruction of the picture are done with the minimum-pixel alteration. Assume that the value has changed to \((cpixel_{1},cpixel_{2}, \ldots ,cpixel_{n})\). The mapping \(\sigma \) is constant. We derive the equation \(d_{\text {min}_{r}}^{'}=cpixel_{E}-cpixel_{F}\), where (E, F, r) are described in Eq. (7).
-
When \(d_{\text {min}_{r}}^{'}>-1\), then \(cpixel_{E}\ge cpixel_{F}\). Here, \(E=\sigma (ml)\), \(F=\sigma ((1)+r)\) and \(\sigma ((1)+r)<\sigma (ml)\):
-
When \(d_{\text {min}_{r}}^{'}\in \{0,1\}\), the data is \(D=d_{\text {min}_{r}}^{'}\). The smallest pixel is \(cpixel_{\sigma ((1)+r)}=(cpixel_{F}+\eta )+D\);
-
When \(d_{\text {min}_{r}}^{'}>1 \), their is no data. The smallest pixel is \(cpixel_{\sigma ((1)+r)}=(cpixel_{F} +\eta )+1\).
-
-
When \(d_{\text {min}_{r}}^{'}\le -1\), then \(cpixel_{E}< cpixel_{F}\). Here, \(E=\sigma ((1)+r)\), \(F=\sigma (ml)\) and \(\sigma ((1)+r)>\sigma (ml)\):
-
When \(d_{\text {min}_{r}}^{'}\in \{-1,-2\}\), the data is \(D=-d_{\text {min}_{r}}^{'}-1\). The smallest pixel is \(cpixel_{\sigma ((1)+r)}=(cpixel_{E}+\eta )+D\);
-
When \(d_{\text {min}_{r}}^{'}<-2\), their is no data. The smallest pixel is \(cpixel_{\sigma ((1)+r)}=(cpixel_{E}+\eta )+1\).
-
Extraction in Maximum-Modification We find that \(d_{\text {max}_{r}}^{'} = cpixel_{G}-cpixel_{H}\). Where (G, H, r) is a list in the Eq. (9).
-
When \(d_{\text {max}_{r}}^{'}>-1\), then \(cpixel_{G}\ge cpixel_{H}\). Here, \(G=\sigma ((n)-r)\), \(H=\sigma (ml)\) and \(\sigma (ml)<\sigma ((n)-r)\):
-
When \(d_{\text {max}_{r}}^{'}\in \{0,1\}\), the data is \(D=d_{\text {max}_{r}}^{'}\). The largest pixel is \(cpixel_{\sigma ((n)-r)} = (cpixel_{G}-\eta )-D\);
-
When \(d_{\text {max}_{r}}^{'}>1\), their is no data. The largest pixel is \(cpixel_{\sigma ((n)-r)}=(cpixel_{G}-\eta )-1\).
-
-
When \(d_{\text {max}_{r}}^{'}\le -1\), then \(cpixel_{G}<cpixel_{H}\). Here, \(G =\sigma (ml)\), \(H=\sigma ((n)-r)\) and \(\sigma (ml)>\sigma ((n)-r)\):
-
When \(d_{\text {max}_{r}}^{'}\in \{-1,-2\}\), the data \(D=-d_{\text {max}_{r}}^{'}-1\). The largest pixel is \(cpixel_{\sigma ((n)-r)}=(cpixel_{H}-\eta )-D\);
-
When \(d_{\text {max}_{r}}^{'}<-2 \), their is no data. The largest pixel is \(cpixel_{\sigma ((n)-r)} = (cpixel_{H}-\eta )-1\).
-
Now, recovered the secret message as well as images of \(MC_{{1}_{(2w-1)\times (2h-1)}}\) and \(MC_{{2}_{(2w-1)\times (2h-1)}}\).
Step 2: In this stage, using the following formulas, we extract the message from the stego pixels \(pix_{i,j}^{1}\) and \(pix_{i,j}^{2}\) of the interpolated marked pictures \(MC_{{1}_{(2w-1)\times (2h-1)}}\) and \(MC_{{2}_{(2w-1)\times (2h-1)}}\), respectively.
where q represents how many concealed bits make up a group. The following is the reconstruction of the actual pixel, \(pix_{i,j}\).
Now construct the interpolated cover image \(IC_{(2w-1)\times (2h-1)}\).
Step 3: Now, rebuild the cover image \(C_{w\times h}\) from interpolated cover image \(IC_{(2w-1)\times (2h-1)}\) by removing any interpolated columns and rows.
4 Experimental Results and Comparisons
This paragraph compares the proposed scheme’s execution to those of the previous dual-image-based secrets concealment systems developed by Authors [2, 5, 6, 16]. Peppers, Lena, Baboon, Fishing boat, Airplane F 16, and Barbara were selected from [18] database, while CXR1000_IM-0003-1001 and CXR1025_IM-0020-1001 were obtained from the [8] database as test inputs for study. All gray-scale image size is \((256\times 256)\). Only USC-SIPI photos are shown in Fig. 3.
The embedding of secrets depends on q and block size. The picture quality is found to be higher in small values of q with large blocks but not much larger block size than in large values of q, but the message embedding rate is low. For instance, in the Lena image, 601,341 bits are added with an average peak signal-to-noise ratio (PSNR) of 52.57 dB when \(q=2\). In the picture Lena presented in Table 1, when \(q=\) 3,794,725 bits are inserted with an average PSNR of 49.75, whereas when \(q=\) 41,012,536 bits are placed with an average PSNR of 44.97.
Table 2 shows the PSNR (dB) comparisons between the suggested and previous techniques. The new approach improves the secrets capacity (EC) calculated using other PVO-based approaches. While the value of q is 2 as stated in Table 2, the hidden message capacity is 442,89, 77,053, 77,053, and 82,161 bits larger than that of Qin et al.’s [16], Lu et al.’s [6], Lu et al.’s [5] and Jung [2], respectively, for the picture Lena. The capacity of information concealment in input images is increased by the proposed approach. It has been determined that our approach outperforms existing PVO techniques in terms of payload while maintaining the same level of picture quality. Additionally, it is obvious that the picture quality is superior to other current schemes, as illustrated in Fig. 4.
5 Conclusion
With varied sizes for the q (set of data) and picture block, this work suggested an improved multi-level PVO (IMPVO) utilizing the center-folding technique. Huge messages are put into and taken from image pixels using the algorithms for inserting and retrieving, respectively. The proposed approach enables safe message transmission by inserting secrets between two pictures. When q is 2, our technique produces a PSNR value over 51 dB and an embedding capacity over 585,000 bits. The suggested approach yields successful outcomes. It is found that the recommended system looks to perform better than other PVO efforts.
References
Jana B (2017) Reversible data hiding scheme using sub-sampled image exploiting Lagrange’s interpolating polynomial. Multimedia Tools Appl 1–17
Jung KH (2018) Authenticable reversible data hiding scheme with less distortion in dual stego-images. Multimedia Tools Appl 77:6225–6241
Lee SK, Suh YH, Ho YS (2004, November) Lossless data hiding based on histogram modification of difference images. Pacific-Rim conference on multimedia. Springer, Berlin, Heidelberg, pp 340–347
Li X, Li J, Li B, Yang B (2013) High-fidelity reversible data hiding scheme based on pixel-value-ordering and prediction-error expansion. Sig Process 93(1):198–205
Lu TC, Wu JH, Huang CC (2015) Dual-image-based reversible data hiding method using center folding strategy. Sig Process 115:195–213
Lu TC, Tseng CY, Wu JH (2015) Dual imaging-based reversible hiding technique using LSB matching. Sig Process 108:77–89
Lu TC, Huang SR, Huang SW (2021) Reversible hiding method for interpolation images featuring a multilayer center folding strategy. Soft Comput 25:161–180
The National Library of Medicine presents MedPix Superscript Registered MedPix®. https://openi.nlm.nih.gov/gridquery.php?q= &it=x
Meikap S, Jana B (2017) Extended directional IPVO for reversible data hiding scheme. Communication, devices, and computing. Springer, Singapore, pp 47–58
Meikap S, Jana B (2018) Directional PVO for reversible data hiding scheme with image interpolation. Multimedia Tools Appl 77(23):31281–31311
Meikap S, Jana B (2019) Directional pixel value ordering based secret sharing using sub-sampled image exploiting Lagrange polynomial. SN Appl Sci 1(6):645
Meikap S, Jana B (2021) Improved center-folding based directional pixel value ordering for reversible data hiding scheme. Multimedia Tools Appl 80(4):5617–5652
Sudipta M, Biswapati J, Prasenjit B, Kumar SP (2021) High payload RDH through directional PVO exploiting center-folding strategy. In: Proceedings of international conference on frontiers in computing and systems. Springer, Singapore, pp 659–670
Niu Y, Shen S (2022) A novel pixel value ordering reversible data hiding based on dual-image. Multimedia Tools Appl 81(10):13751–13771
Peng F, Li X, Yang B (2014) Improved PVO-based reversible data hiding. Digital Sig Process 25:255–265
Qin C, Chang CC, Hsu TJ (2015) Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimedia Tools Appl 74(15):5861–5872
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circuits Syst Video Technol 13(8):890–896
University of Southern California. The USC-SIPI Image Database. http://sipi.usc.edu/database/database.php?volume=misc
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Meikap, S., Jana, B., Singh, P.K., Bera, D., Lu, T.C. (2024). Secure Data Communication Through Improved Multi-level Pixel Value Ordering Using Center-Folding Strategy. In: Mandal, J.K., Jana, B., Lu, TC., De, D. (eds) Proceedings of International Conference on Network Security and Blockchain Technology. ICNSBT 2023. Lecture Notes in Networks and Systems, vol 738. Springer, Singapore. https://doi.org/10.1007/978-981-99-4433-0_10
Download citation
DOI: https://doi.org/10.1007/978-981-99-4433-0_10
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-4432-3
Online ISBN: 978-981-99-4433-0
eBook Packages: EngineeringEngineering (R0)