Abstract
Recently, Islam and Basu presented a password-based three-party authenticated key agreement protocol for mobile devices in post-quantum environment and claimed that the protocol is resistant to several attacks in order to satisfy the demands of three-party communication secure. After examining Islam and Basu’s protocol, we find that the PB-3PAKA protocol is vulnerable to dishonest user’s attack, signal leakage attack (SLA).
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Recently, Islam and Basu [3] proposed a password-based three-party authenticated key agreement protocol for mobile devices in a post-quantum environment (PB-3PAKA) protocol. The formal security of the PB-3PAKA protocol is demonstrably secure in Random Oracle Model (ROM). The PB-3PAKA [3] protocol establishes a session key between two mobile users using fresh pair of keys in every session.
Key computation and communication costs are costly, so the key reuse is known to enhance performance during real-world deployments to cut the cost. The resumption mode in TLS v1.2 permits key reuse which drastically decreases online computations. An efficient 0-round-trip time (RTT) resumption mode is suggested in TLS v1.3 draught version 7 [5]. It allows TLS to establish a secure connection without incurring round-trip costs. According to TLS v1.3 version 7, the majority of key exchange computations and communication costs are saved by reusing public and private key pairs. Resumption mode is used to establish the overwhelming majority of TLS connections in the real world. But, this feature-induced security vulnerability in the existing post-quantum key exchange protocol. The key reuse vulnerability has been first identified by Kirkwood et al. [4] in the post-quantum environment. In their work, the reuse of public/private keys is shown to break the security of the protocol. Therefore, authors [4] advise that public-key validation is necessary for the RLWE-based key agreement protocol.
Ding et al. [1] proposed an attack. This attack is known as a signal leakage attack (SLA) and it is against the RLWE-based reconciliation schemes where the public/private keys are reused. In this approach, the adversary initiates multiple sessions with the honest party to recover the honest party’s private key. Using a 2.q number of queries with the honest party, the adversary can recover the honest party’s secret key.
Continuing the above work, Ding et al. [2] improved signal leakage attack (SLA), and this improved attack is known as i-SLA, in which 2.q number of queries is reduced to q number of queries. Now, the secret of the reused public key of the honest party can be recovered with fewer queries.
Influenced by these researchers, we found that Islam and Basu’s [3] proposed protocol is vulnerable to dishonest user’s attack, signal leakage attack.
2 Review of Islam and Basu’s Protocol
In this section, we introduce Islam and Basu’s PB-3PAKA protocol [3]. The PB-3PAKA protocol has four phases: initialization phase, user registration phase, authenticated key agreement phase, and password change phase.
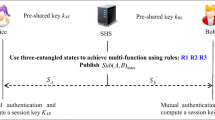
Table 1 shows the notations of Islam and Basu’s PB-3PAKA protocol. Figures 1 and 2 describe the user registration and authenticated key agreement phase, respectively.
-
1.
Initialization phase:
During initialization phase, the server S selects three one-way hash function, \(H_{1},\ H_{2}, \ H_{3} : \ \{0,1\}^* \rightarrow \{0,1\}^{l}\) as well as public parameters \(\{n,q,a,\chi _{\beta }\}\). Also, server S selects a secret key s, where \(s \in \mathbb {Z}_q\).
-
2.
User registration phase:
In user registration phase, the user \(\{A,B\}\) chooses a identity \(ID_{i}\), password \(PW_{i}\) from the dictionary D and \(b_{i} \in \mathbb {Z}_{q}\) and compute \(L_{i}\). After that sends \(\{ID_{i},L_{i}, personal \ information \}\) to server S. On the server’s side, server S verifies the personal information of the user \(\{A,B\}\) and computes \(D_{i},X_{i},N_{i}\) and \(V_{i}\).
-
3.
Authenticated key agreement phase:
In authenticated key agreement phase, the user \(\{A, B\}\) computes his public keys \(x_{A}\) and \(x_{B}\) and the parameters \(\Sigma _A\) and \(\Sigma _{B}\). \(\{ID_{A},T_{A},x_{A},\sigma _{A}\}\) and \(\{ID_{B},T_{B},x_{B},\sigma _{B}\}\) are sent to the server.
On the server side, the server authenticates the user \(\{A, B\}\) and sends its identity and parameters \(\Sigma _{S_{A}}\), \(\Sigma _{S_{B}}\) to users A and B, respectively.
User \(\{A, B\}\) authenticates to the server and computes \(t_{A},t_{B}\) as well as signal functions \(w_{A},w_{B}\). Lastly, User A and User B send messages to each other, authenticate each other, and finally generate a session key.
User registration phase of Islam and Basu’s [3] PB-3PAKA protocol
Authenticated key agreement phase of Islam and Basu’s [3] PB-3PAKA protocol
3 Cryptanalysis of Islam and Basu’s Protocol
In this section, we describe the cryptanalysis of Islam and Basu’s [3] protocol based on a password-based three-party authenticated key agreement protocol for mobile devices in post-quantum environment. After examining the protocol, we find that the protocol is vulnerable to dishonest user’s attack and signal leakage attack. These attacks are described below as follows.
3.1 Dishonest User’s Attack
Dishonest user’s attack is feasible due to the registration phase of Islam and Basu protocol (see Fig. 1 for a complete description of the registration phase). We show that the adversary correctly recovers the server’s secret key s where \(s \in \mathbb {Z}_q\). Here, there are two users and one server. The first is user A and the second is user B. We assume that either of these two users is an adversary (Eve). The following steps of dishonest user’s attack are as follows:
-
Step 1:
First of all, the adversary \(\mathcal {A}\) chooses its \(ID_{A}\) and password \(PW_{A}\) and along with it also chooses a random element \(b_{A} \in \mathbb {Z}_q\). Now, the adversary computes the parameter \(L_{A}=H_{1}(PW_{A},b_{A})\) using the hash function on its password \(PW_{A}\) and random element \(b_{A}\) (see Fig. 1). After this, \(\mathcal {A}\) sends her \(\{ID_{A}, L_{A}\}\), and personal information to the server through a secure network.
-
Step 2:
The server receives the \(\{ID_{A}, L_{A}\}\) and personal information of the adversary and verifies the adversary’s personal information. Now, the server computes a parameter \(D_i\) using the hash function on his master secret key s where \(s \in \mathbb {Z}_{q}\) and the adversary’s \(ID_{A}\). With this, the server computes a parameter \(X_i\) using the hash function on the adversary’s \(ID_{A}\) and \(L_{A}\).
Lastly, the server computes the parameters \(V_i=H_{1}(X_{i},D_{i}), N_i=X_{i} \oplus D_{i}\) and sends these parameters \({V_{i},N_{i}}\) to the adversary.
-
Step 3:
Now, the adversary has the knowledge of \({V_{i},N_{i}}\) as well as the value of \(X_i=H_{1}(ID_{A},L_{A})\) because the server has computed the parameter \(X_i\) using the hash function on \((ID_{A}, L_{A})\) (see Fig. 1). Further, Adversary \(\mathcal {A}\) can easily find the value of \(D_i\) by using \(X_{i}\) and \(N_{i}\) parameters.
In the protocol, the master secret key of server s belongs to \(\mathbb {Z}_q\), and the adversary puts the value of s from 0 to \(q-1\) in \(H_{1}(ID_{i},s)\) to match the value of \(D_i\). If adversary guesses the correct value of s, then adversary recovers the server’s master secret key s.
3.2 Signal Leakage Attack and Improved Signal Leakage Attack
In TLS v1.3, the key exchange computations and communication costs are saved by reusing public and private key pairs. Resumption mode is used to establish the overwhelming majority of TLS connections in the real world. The security is compromised when keys are reused in TLS, due to this the PB-3PAKA [3] protocol is vulnerable to a signal leakage attack and improved signal leakage attack. Therefore, the adversary can retrieve the user’s secret key (see Fig. 2 for a complete description of the signal leakage attack).
Attack overview:
Islam and Basu’s PB-3PAKA protocol has two parties, A and B and one server S. As of TLS v1.3, we reuse the secret keys \(r_A\) and \(r_B\), respectively, of both parties, A and B in the Islam and Basu’s PB-3PAKA protocol. Suppose party A plays the role of an adversary (Eve) and party B is an honest party. Adversary wants to recover the secret key \(r_B\) of the honest party B. She generates her malicious public key \(x_{A}\) and sends it to party B. Party B computes \(t_{B}=r_{B}.x_{A}\) and signal function \(w_{B}\) using the adversary’s malicious public key and sends the signal function \(w_{B}\) to the adversary. So, the adversary retrieves the secret key \(r_{B}\) by observing the signal function \(w_{B}\) sent by the party B. For detailed description, see below attack.
Signal Leakage Attack:
Let the value of the adversary’s secret key \(r_{A}\) is 0 and the value of adversary’s error term \(f_A\) to be 1. By which the public key of the adversary will be \(x_{A}=k\), where the value of \(k \in \mathbb {Z}_{q}\). Now, the adversary sends its \(ID_A\), public key \(x_{A}\), and other parameters \(T_A\) (Timestamp), \(\Sigma _A=H_{2}(ID_{A},T_{A},x_{A},D_{A})\) to the server.
Similarly, party B also derives its public key and other parameters and sends them to the server. Also, sends its \(<ID_B \ and \ response>\) to the adversary.
Now, the server sends the public key of the adversary to party B and the public key of party B to the adversary.
After receiving the public key of the adversary sent by the server, party B computes \(t_B\) where \(t_B=r_{B}.x_{A}\) (here, \(r_B\) is the secret key of party B). In addition, it also computes the signal function
modular function
and the parameter \(\alpha _B=H_{2}(x_{B},x_{A},w_{B},\sigma _{B})\) (see Fig. 2).
Now,
where \(k \in \{0,\ldots ,q-1\}\).
As soon as the adversary will vary the value of k, likewise she will guess the value of \(k.r_{B}[i]\) correctly, because the number of the signal \(w_{B}\) changes for every coefficient of \(r_{B}[i]\). When there is a change in the signal for any \(i\textrm{th}\) coefficient of \(r_{B}[i]\), then the number of that change is exactly \(2.r_{B}[i]\). But the value of \(+\)1 and −1 only gives signal change of the same number, due to which the adversary can only guess the value up to ± sign. For the value of \(-r_{B}\), the value of k changes in the reverse direction which is a multiple of \(r_{B}\).
Therefore, to find out the exact value of the \(r_{B}\) coefficient, the adversary initiates the q number of sessions with party B with its public key (for more details, see [1]).
Improved Signal Leakage Attack:
Attack details:
In the beginning, adversary \(\mathcal {A}\) sends its \(<ID_A \ and \ request>\) to party B. Moreover, she derives her public key \(x_A=a.r_{A}+k.f_{A}\), here \(r_A\) and \(f_A\) are the adversary’s secret key and the error term, respectively (see Fig. 2). Now, two cases arise here. In the first case, the adversary takes the value of \(r_A\) as 0, and in the second case, the value of \(r_A\) is taken as very small depending on error distribution.
In the improved signal leakage attack case, the adversary chooses the value of error term \(f_{A}\) as 1 and selects the value of secret key \(r_{A}\) according to the error distribution. Therefore, the public key of the adversary is \(x_{A}=a.r_{A}+k\) so that the public key of the adversary cannot be distinguished. Here,
and signal function
As adversary \(\mathcal {A}\) iterates over k values, \(a.r_{A}.r_{B}\) remains constant.
Consequently, \(\mathcal {A}\) continues to observe the signal changes of \(r_{B}[i]\) while she varies the values of k toward the positive values and starts from \(k = 0\). After this, the adversary records the first signal change in \(w_{B}\) at \(k=k_1\).
The adversary then varies k toward the negative values and observes the first signal change in \(w_{B}\) and in this direction it records the first signal change at \(k=k_2\).
Now, the period of region T or \(T^{c}\) in multiples of \(r_{B}[i]\) is \(k_1-k_2\). The period of the signal change is \(k_1-k_2\), due to which the value of \(r_B[i]\) up to the ± sign is revealed by \(\dfrac{q}{2.(k_1-k_2)}\). The process of changing the signal continues till the signal becomes stationary after the change, and then adversary can query a small constant number here more than \(\dfrac{q}{2}\) times.
In this way, the adversary can recover \(r_B[i]\) up to the sign by doing \(\dfrac{q}{2}+c\) queries. Here c is a small value because as the value of k increases, the value stabilizes and \(k.r_B[i]\) moves away from the boundary point. Now, adversary performs \(q+c\) queries so that \(\mathcal {A}\) can recover the exact value of the secret (for more details, see [2]).
4 Conclusion
We have studied Islam and Basu’s [3] proposed protocol based on a password-based three-party authenticated key agreement protocol for mobile devices in post-quantum environment (PB-3PAKA). It has been found that their protocol is vulnerable to dishonest user’s attack. The security is compromised when keys are reused in TLS v1.3, and due to this the PB-3PAKA protocol is vulnerable to signal leakage attack. In future, we will propose an improved protocol to overcome the above-identified attacks on Islam and Basu’s proposed protocol.
References
Ding J, Alsayigh S, Saraswathy R, Fluhrer S, Lin X (2017) Leakage of signal function with reused keys in RLWE key exchange. In: 2017 IEEE international conference on communications (ICC). IEEE, pp 1–6
Ding J, Fluhrer S, Rv S (2018) Complete attack on RLWE key exchange with reused keys, without signal leakage. In: Australasian conference on information security and privacy. Springer, pp 467–486
Islam SH, Basu S (2021) PB-3PAKA: password-based three-party authenticated key agreement protocol for mobile devices in post-quantum environments. J Inf Secur Appl 63:103026
Kirkwood D, Lackey BC, McVey J, Motley M, Solinas JA, Tuller D (2015) Failure is not an option: standardization issues for post-quantum key agreement. In: Workshop on cybersecurity in a post-quantum world, p 21
Rescorla E (2018) The transport layer security (TLS) protocol version 1.3. Technical report
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Yadav, S., Dabra, V., Malik, P., Kumari, S. (2024). Flaws of a Password-Based Three-Party Authenticated Key Agreement Protocol in Post-quantum Environment. In: Roy, B.K., Chaturvedi, A., Tsaban, B., Hasan, S.U. (eds) Cryptology and Network Security with Machine Learning. ICCNSML 2022. Algorithms for Intelligent Systems. Springer, Singapore. https://doi.org/10.1007/978-981-99-2229-1_6
Download citation
DOI: https://doi.org/10.1007/978-981-99-2229-1_6
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-2228-4
Online ISBN: 978-981-99-2229-1
eBook Packages: EngineeringEngineering (R0)