Abstract
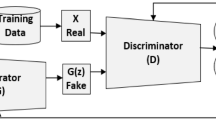
We present an architecture, an Anomaly-based Generative Adversarial Network (IGAN), that detects malicious strings with decent accuracy. The proposed IGAN is comprised of an encoder, a decoder, and a discriminator. The encoder and decoder form the generative unit, trying to reconstruct the input and map that input and output to a latent space variable. IGAN exploits this latent space together with the adversarial training with the discriminator to enhance the learning of the normal distribution. The discriminator used is as a classifier as well as a feature extractor. To identify an anomaly or a normal instance, the anomaly score is calculated after passing it to the trained model. We have performed a detailed analysis of the existing and the proposed architecture using reliable metrics such as AUC score, Precision, Recall, and F_score. The experimental results of the proposed IGAN outperform other existing models in detecting anomalies with high accuracy.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Goodfellow, I., Abadie, J.P., Mirza, M., Xu, B., Farley, D.W., Ozair, S., Courville, A., Bengi, Y.: Generative Adversarial Nets. In: Advances in Neural Information Processing Systems, pp. 2672–2680 (2014)
Schlegl, T., Seebock, P., Waldstein, S.M., Langs, G., Erfurth, U.S.: f-anogan: fast unsupervised anomaly detection with generative adversarial networks. Med. Image Anal. 54, 30–44 (2019)
Zenati, H., Romain, M., Foo, C.S., Lecouat, B., Chandrasekhar, V.R.: Adversarially learned anomaly detection. In: Proceedings of IEEE International Conference on Data Mining, pp. 727–736 (2018)
Gherbi, E., Hanczar, B., Janodet, J.C., Klaudel, W.: An encoding adversarial network for anomaly detection. In: Proceedings of Asian Conference on Machine Learning, pp. 188–203 (2019)
Akcay, S., Atapour-Abarghouei, A., Breckon, T.P.: Ganomaly: semi-supervised anomaly detection via adversarial training. In: Proceedings of Asian Conference on Computer Vision, pp. 622–637 (2018)
Makhzani, A., Shlens, J., Jaitly, N., Goodfellow, I., Frey, B.: Adversarial autoencoders (2015). arXiv: 1511.05644
Dhanabal, L., Shantharajah, S.P.: A study on NSL-KDD dataset for intrusion detection system based on classification algorithms. Int. J. Adv. Res. Comput. Commun. Eng. 4(6), 446–452 (2015)
Kingma, D.P., Adam, J.B.: A method for stochastic optimization (2014). arXiv:1412.6980
Hanley, J.A., McNeil, B.J.: The meaning and use of the area under a receiver operating characteristic curve. Radiology 143(1), 29–36 (1982)
Tavallaee, M., Bagheri, E., Lu, W., Ghorbani, A.: A Detailed Analysis of the KDD CUP 99 data set. In: Proceedings of IEEE Symposium on Computational Intelligence for Security and Defense Applications (2009)
Arjovsky, M., Chintala, S., Bottou, L.: Wasserstein GAN 1701, 07875 (2017)
Gulrajani, I., Ahmed, F., Arjovsky, M., Dumoulin, V., Courville, A.C.: Improved training of wasserstein GANs. In: Proceedings of Advances in Neural Information Processing Systems, pp. 5767–5777 (2017)
Yi, X., Walia, E., Babyn, P.: Generative adversarial network in medical imaging: a review. Med. Image Anal. 58 (2019)
Salimans, T., Goodfellow, I., Zaremba, W., Cheung, V., Radford, A., Chen, X.: Improved Techniques for Training GANs. In: Proceedings of Advances in Neural Information Processing Systems, pp. 2234–2242 (2016)
Bojanowski, P., Joulin, A., Paz, D.L., Szlam, A., Optimizing the latent space of generative networks (2017). arXiv:1707.05776
Makhzani, A., Shlens, J., Jaitly, N., Goodfellow, I., Frey, B.: Adversarial autoencoders. 1511, 05644 (2015)
Davis, J., Goadrich, M.: The Relationship between Precision-Recall and ROC curves. In: Proceedings of the international Conference on Machine learning, pp. 233–240 (2006)
Goutte, C., Gaussier, E.: A probabilistic interpretation of precision, recall and f-score, with implication for evaluation. In: Proceedings of European Conference on Information Retrieval, pp. 345–359 (2005)
Hanley, J., McNeil, B.J.: The meaning and use of the area under a receiver operating characteristic (ROC) curve. Radiology 143(1), 29–36 (1982)
Radford, A., Metz, L., Chintala, S.: Unsupervised representation learning with deep convolutional generative adversarial networks (2015). arXiv:1511.06434
LeCun, Y., Cortes, C.: MNIST handwritten digit database. http://yann.lecun.com/exdb/mnist/
Krizhevsky, A., Hinton, G.: Learning multiple layers of features from tiny images. https://www.cs.toronto.edu/~kriz/learning-features-2009-TR.pdf
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Shah, J., Das, M. (2022). IGAN: Intrusion Detection Using Anomaly-Based Generative Adversarial Network. In: Iyer, B., Ghosh, D., Balas, V.E. (eds) Applied Information Processing Systems . Advances in Intelligent Systems and Computing, vol 1354. Springer, Singapore. https://doi.org/10.1007/978-981-16-2008-9_36
Download citation
DOI: https://doi.org/10.1007/978-981-16-2008-9_36
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-2007-2
Online ISBN: 978-981-16-2008-9
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)