Abstract
Security aspects must be considered in the next generation of IoT and 5G networks. From the different aspects that can be considered that belong to the area of security, we focus in this work as core aspects, the processes of authentication and key management operations that are essential to establish security associations between end-devices and data services. However, little effort has been put so far into providing a network-independent solution for service access authentication in the field of constrained devices based on IoT such as LoRaWAN, NarrowBand IoT (NB-IoT) and LTE-M in 5G networks. Therefore, this paper proposes a novel architecture based on EAP bootstrapping and AAA infrastructure for IoT and 5G networks to manage service authentication and security association in order to enable secure end-to-end communication. In this work, we propose the use of an improved bootstrapping mechanism for secondary authentication adapted to be compliant with the 3GPP specifications for integrating IoT technologies in 5G networks. We propose the adaptation of LO-COAP-EAP (Low-Overhead CoAP-EAP) as an EAP lower layer for enabling the secondary service authentication with high flexibility, scalability and networks independence.
This work has been partially funded by the H2020 EU IoTrust project under Grant Agreement 825618, the H2020 PHOENIX project under Grant Agreement 893079, the H2020 Fed4IoT project under Grant Agreement 814918, the H2020 PRECEPT project under Grant Agreement 958284, the National GUARDIAN project under Grant Agreement TSI-100110-2019-20, the H2020 Plug-n-Harvest project under Grant Agreement 768735, and also Fundación Séneca de la Región de Murcia FPI Grant 20751/FPI/18.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
5G is the next generation of cellular communications, specified by the 3rd Generation Partnership Project (3GPP) [2, 3]. The 3GPP identifies three major use cases in 5G, namely massive Machine Type Communications (mMTC), enhanced Mobile Broadband (eMBB), and Ultra Reliable Low Latency Communications (URLLC). We pay attention to the mMTC, since 5G plays an important role in the integration of heterogeneous access technologies, acting as a unifying framework to interconnect “things” to the Internet in order to foster Internet of Things (IoT) deployments. Our interest in this paper, gravitates around the concept of integrating IoT into 5G, having into account that this is something that is being remarked in the literature and it is of interest to academia and industry. 5G is brought in some literature as key to create a global IoT [14] or Internet of Everything [11].
To integrate IoT technologies into 5G networks, one of the most important aspects is to provide security to the communications. Concretely, we pay attention to the homogenization of security in the convergence of 5G and IoT technologies such as Low-Power Wide Area Networks (LPWAN) with limitations in terms of power and bandwidth. On the one hand, there are research works to advance in the IoT integration into 5G as we will see in Sect. 2. On the other hand, 3GPP has created elements in its 5G architecture to support non-native (non-3GPP) technologies [1].
For security, 5G brings several improvements over the previous generation such as providing a flexible framework for authentication at network and service layers. In particular, the 3GPP specifies a primary authentication for network access and a secondary authentication for service and application access [1]. To provide the aforementioned authentications, 5G specifies the use of protocols such as Authentication Authorization and Accounting (AAA) infrastructures and the Extensible Authentication Protocol (EAP). Since EAP can be transported over several EAP lower-layer protocols, it is desirable to employ a feasible EAP lower-layer for the constrained device requirements.
In this paper, we propose the adaptation of a lightweight LO-COAP-EAP protocol, a novel and lightweight EAP lower layer, specially designed for IoT and very constrained networks, for transporting EAP to authenticate wireless IoT devices and bootstrap key material through the 5G core in order to enable services access. LO-CoAP-EAP has been evaluated in LoRa showing a valuable reduction in the number of bytes as well as number of messages sent over the network to complete the bootstrapping process, to gain network access.
We assume that the IoT devices have already access to the 5G network, having already established the network access by primary authentication. Our proposal is based on the secondary EAP authentication concept that 3GPP defines in 5G specifications. It defines the messages to be exchanged between the a IoT device and the 5G core, which can rely EAP messages to the AAA infrastructure in an external data network. Our approach provides a common lightweight procedure to enable the bootstrapping process in constrained IoT networks through 5G core.
The remainder of the paper is organized as follows. Section 2 summarizes the related work about the integration of IoT technologies in 5G networks and bootstrapping mechanisms. Section 3 describes the proposed architecture as well as the involved entities, and Sect. 4 explains the interactions among the entities of the architecture. Section 5 shows the use cases of the proposed architecture. Finally, Sect. 6 concludes the paper with an outlook of our future work in this area and presents the acknowledgements.
2 Related Work
The literature is rather positive about the integration of IoT technologies in 5G networks. In [6], the authors discuss the work of the 3GPP towards integrating non-3GPP technologies into 5G. Additionally, there are recent efforts to facilitate the integration of IoT in 5G. The work in [12] proposed an orchestrated IoT architecture over 5G to achieve a better QoS performance. Authors in [16] motivated a new paradigm to converge IoT and 5G for intelligent data acquisition and analysis, employing 5G communication protocols and architecture as a fundamental building block in their design. In [8], the authors reviewed the convergence of 5G with IoT while discussing the proliferation of multi-radio IoT devices. Finally, the work in [15] analyzed the viability of 5G for supporting Internet of Vehicles (IoV) scenarios in Vehicle-to-Everything (V2X) applications. The mentioned works showcase an interest to integrate IoT and 5G technologies within research community and industry.
Moreover, recent research works have explored the possibility of integrating constrained IoT devices based on wireless LPWAN networks (Low-Power Wide Are Networks) into 5G. Concretely, in the work of Yasmin et al. [17] they proposed four different ways in which the LoRaWAN network can be integrated with their 5G test network (5GTN) and demonstrate the feasibility of the integration. They placed an EPC (Envolved Packet Core) of 5G core network between the LoRaWAN Gateway and the centralized LoRaWAN Application Server. Similarly, the research of Navarro et al. in [13] went one step further and fused two different elements of the architecture. In order to do this, the LoRaWAN Gateway implemented both the LoRaWAN PHY layer and the 3GPP stack needed to communicate with the EPC. The LoRaWAN packets received through the constrained radio link, were encapsulated and transmitted through the EPC to a LoRaWAN Server. Nevertheless, these works employ the 5G core network as a mere backhaul network in order to access the LoRaWAN Application Server. Thus, the end-devices simply address the LoRaWAN Application Server as regular, limiting the aforementioned integration with 5G.
We argue that even in this 5G enabled architecture, some of the wireless IoT technologies can be quite constrained in the link and need considered optimization to reduce the number of bytes sent over the link. This, coupled with the fact that 5G integrates natively the use of Extensible Authentication Protocol (EAP) and Authentication, Authorization and Accountability (AAA) as part of the security framework. In non-constrained networks, the AAA framework is typically implemented with protocols like RADIUS or Diameter. This is because they are very extended protocols that give support to a large number of device types, typically used by TELCOs deployments. The use of AAA conveys: (i) authenticate a device, (ii) authorize the device to access a service or resource, e.g., access to a different domain network, and (iii) accountability of the usage of said service. Also, identity federation is possible thanks to AAA. The advantages of identity federation include a better scalability when deploying a large amount of devices that belong to different organizations. Coupled with AAA, there is the Extensible Authentication Protocol (EAP), which allows the use of different methods of authentication. Additionally, it enables the use of a Key Management Framework (KMF). EAP itself permits the bootstrapping Security Association Protocols (e.g. Datagram Transport Layer Security (DTLS)). EAP also requires an EAP lower-layer, a protocol (or protocols) that transport EAP packets from devices to a domain controller. Finally, the domain controller is the element that gives access to the solicited service. Following that, in this paper we propose adding EAP support to wireless constrained IoT technologies integrated in 5G networks.
For wireless constrained IoT technologies, there are standardization organizations (i.e IETF) that are working on the homogenization of the native IoT protocols stack for the application use, which typically consists of Internet Protocol (IPv6), User Datagram Protocol (UDP), and Constrained Application Protocol (CoAP). On the other hand, there is no such effort towards the standardization of the bootstrapping procedure in wireless IoT technologies such as Low-Power Wide Area Networks (LPWAN). Therefore we see an opportunity to research in the bootstrapping process of IoT networks integrated into 5G core. To do that, we consider the 5G specifications that are already being developed by 3GPP in that context.
Our approach is to adapt an EAP lower layer that is independent of the underlying technology such as our previous work LO-CoAP-EAP [9]. LO-COAP-EAP is an EAP lower layer that was designed for constrained IoT networks in mind and a reduced footprint of the EAP transport, using a standardized protocol in IoT as is CoAP. LO-CoAP-EAP is an enabler of the interoperability and integration of LPWAN technologies, that could be generalized to any IoT technology reliant of CoAP and with basic computational capabilities i.e., Class 1+ as defined in RFC7228 [4], to connect to the Internet on their own, as well as performing symmetric cryptography. Due to its characteristics, LO-CoAP-EAP can be adapted as an enabler to integrate different LPWAN technologies into 5G. To the best of the authors’ knowledge, there are no previous proposals of homogeneous standardized bootstrapping protocol stacks to integrate constrained IoT technologies into 5G mobile networks.
3 Proposed Architecture
In this section we describe the proposed architecture mapping the entities in the current 5G specifications of the 3GPP documentation [3] for the use case of the secondary authentication. Below, we define the main entities of the architecture:
-
Smart Object: The IoT device intends to communicate with the AAA infrastructure located in External Data Network through the 5G core network. It is the entity called User Equipment (EU) in 3GPP terminology.
-
gNodeB: This is the base station, which is based on the design of Navarro et al. [13] to support a IoT technology to communicate with Smart Object and the integration with 5G networks.
-
5G Core Network: This is the 5G core network that allows the connectivity between the Smart Object and the External Data Network.
-
External Data Network: This network could be public Internet or a private network. The AAA infrastructure is located in the external network. The Smart Object must authenticate and bootstrap key material with AAA Server to enable secure network access and further end-to-end communication.
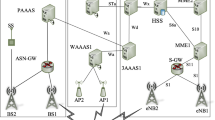
As shown in Fig. 1, we can see that the Smart Object, which can be a non-3GPP technology, is communicating with the 5G base station —gNodeB (gNB) in 5G terminology. This communication is done using an IoT technology, for instance LoRaWAN, and is performed through the constrained link in terms of bandwidth and low power. After this, the communication is done through the non-constrained 5G network. At this point, in case of non-3GPP technologies, the communications go through the Non-3GPP Inter-Working Function (N3IWF) that implements the functionality of bridging non-3GPP technologies with the 5G core. Then, the Access Management Function (AMF) receives all connection and session related information from the User Equipment (EU) —Smart Object in our instance —such as verifying the UE’s subscription. All related traffic is then forwarded to the Session management Function (SMF) which implements the EAP authenticator for the specific case of the secondary authentication, steering the authentication process with the DN-AAA. Finally, the EAP traffic is forwarded to the Data Network AAA (DN-AAA), the entity that authenticates the Smart Object.
Next, we elaborate the process mapping the aforementioned entities to the LO-CoAP-EAP architecture as explained in [9]. The User Equipment (UE), that we refer to here as Smart Object, implements the LO-CoAP-EAP Smart Object. This entity is also the EAP peer and implements the role of a CoAP Server, altering a bit the original design of [9] as we will explain in more detail in Sect. 3. The Session Management Function (SMF) will implement the LO-CoAP-EAP Controller. This entity is the EAP authenticator, which implements the AAA client that communicates the DN-AAA. The LO-CoAP-EAP Controller, implements a CoAP client that queries the LO-CoAP-EAP service implemented in the LO-CoAP-EAP Smart Object.
4 Interactions Description
Before explaining the interaction between the different entities here (Fig. 3), we have to state some assumptions regarding the scenario. First, the Smart Object is assumed to have already performed the primary authentication which gives it access to the 5G core services and to protect the communications between the 5G core entities and the Smart Object. Since the focus of this article is to provide access through the secondary authentication mechanism of 5G to access external data network services or applications, we work on that context to provide services access.
In this sense, being the SMF the EAP authenticator, and having already established a trust (even if its transitive) with that entity, there is no inherent need to perform a handshake to assure that the is going to be message sent blindly to perform some kind of attack. These assumptions are not valid when there is no previous trust relation, hence falling back on the specific flow of the original work. Figure 2 shows a detail protocol exchange of the proposal. For the sake of simplicity we omit the AMF entity in this flow. For the proposal we have to make some modifications to LO-CoAP-EAP in order to comply with the process of the secondary authentication in 5G networks specified by 3GPP.
The trigger message sent originally from the Smart Object is omitted, and is left to the SMF to start the secondary authentication. Furthermore, along with this initial change, it comes the addition of the EAP Request Identity and Response Identity. Our proposal would be to omit these messages in the particular case of very constrained technologies, following our previous approach in Garcia-Carrillo et al. [9], but we maintain this design to comply with the secondary authentication flow showed in the 3GPP document called TS 33.501 [3]. Once the SMF (EAP Authenticator) receives the EAP Response Identity, SMF sends the first AAA message (we use a generic term as we do not want to associate a specific AAA technology), which starts the EAP authentication.
The first message (1) is sent from the SMF to the Smart Object containing the EAP request identity message. This message clearly states that the SMF is accessing the bootstrapping service of the Smart Object that is represented by the URI /b. Since the EAP protocol is lock-step, and by design the responses and sent piggybacked, there is no need to correlate CoAP Requests and responses, beyond the use of a simple identifier that is represented by a single CoAP Token value —EMPTY in this case. After this, the Smart Object responds (2) with the EAP Response Identity and the CoAP resource created that is associated with this bootstrapping procedure. Then, the SMF forwards the EAP Response in a AAA message —we leave to the specific implementation to decide which AAA protocol to use. At this point the AAA decides which EAP method to use to authenticate the Smart Object and the EAP exchange begins between the AAA Server and the Smart Object, while the SMF is acting as a mere forwarder. Following the LO-CoAP-EAP proposal, the next messages (5–11) belonging to the EAP method will refer to the bootstrapping service URI with the resource ID returned by the Smart Object in message (2). When the EAP method is finished and the device is authenticated successfully, the SMF receives (12) the EAP Success message along with the Master Session Key (MSK) and some authorization information. Then, the last exchange between the SMF and the Smart Object is used to confirm the MSK by establishing an AUTH Security Association, by using a key derived from the MSK, following the schema explained in [9]. At this point the Smart Object is authenticated and can access the services from the external data network that it is authorized to use.
5 Use Cases in IoT and 5G Networks
IoT and 5G refers to a massive number of low-cost, low-complexity devices deployed for advanced solutions of smart cities, precise agriculture and industry 4.0. LPWAN The main use cases include those that benefit from massive sensors and actuators deployment for structure and environmental monitoring, asset tracking, process monitoring, autonomous and driverless vehicles [7] among others. However, these use cases are affected for the vendor-specific and non-standardized of wireless technologies that are creating isolated islands of connectivity [4]. For example, some IoT technologies (i.e. Sigfox and LoRaWAN) do not allow the connection of end-devices to the Internet and requiring some ad-hoc middleware adaptation layer. Moreover in 5G, the current specification of massive machines-type communications (mMTC) is very heterogeneous and vendor-specific. Thus, devices from different vendors may have different reliability, latency, and throughput requirements, even within the same use case and vertical application. Hence, this heterogeneity also affects how security is implemented and what are the minimum requirements. Currently, there are many running deployments that employ vendor-specific or private security protocols.
Therefore, security is one of the main elements in the vision of 5G use cases [5, 10]. For 5G, the 3GPP defined security aspects, architecture and procedures with the aim of integrating untrusted and non-3GPP technologies. The 3GPP is working on the secure integration of heterogeneous deployments into a common secure ecosystem. To do that, the 3GPP defines a secondary authentication for data service access, for instance a cloud monitoring platform. Nevertheless, the description of how untrusted end-devices must achieve secondary authentication against an external data network is limited.
Because of this, the use cases and wireless deployments, that require secondary authentication, can benefit from our LO-COAP-EAP proposal. In particular, our proposal is focused on use cases where LPWAN devices are integrated in a 5G network to communicate with data service network. The LPWAN device requires a second authentication to establish a secure end-to-end communication with the data service network. Thus, the LPWAN integration into 5G through Lo-CoAP-EAP serves as a consolidating adaptation to be compliant with the 5G security specifications.
6 Conclusion
Bootstrapping and key establishment are crucial aspects to build more secure IoT and 5G scenarios. This paper has presented novel EAP-based bootstrapping architecture to enable secondary authentication and key establishment specially designed to work on constrained devices in 5G. In particular, we proposed the use of the bootstrapping protocol LO-COAP-EAP and AAA infrastructure for the integration of Low-Power Wide Area Networks (LPWAN) into a 5G Core Network to enable the secondary authentication feature of 5G for constrained devices. Besides, the paper has described how the constrained devices based on LPWAN technologies can bootstrap and establish the key material with AAA server through the 5G core network. The proposal is adapted to be compliant with 3GPP specifications in order to perform secondary service authentication and derive cryptography material that can be employed to enable security associations to secure end-to-end communications (e.g. DTLS) between constrained devices and external data network. Moreover, the proposal extends a standardization effort of IETF called COAP-EAP in order to provide high flexibility, scalability and networks independence. As future work, the development of the proposed approach is being carried out in a pilot testbed with real constrained devices, a 5G core network and AAA infrastructure in order to evaluate the solution as a whole.
References
3GPP: Security architecture and procedures for 5G System. Technical Specification (TS) 33.501, 3rd Generation Partnership Project (3GPP) (2018). http://www.3gpp.org/DynaReport/33501.htm. version 15.5.0
3GPP: Procedures for the 5G System (5GS). Technical Specification (TS) 23.502, 3rd Generation Partnership Project (3GPP) (2019). http://www.3gpp.org/DynaReport/23502.htm. version 16.1.1
3GPP: System architecture for the 5G System (5GS). Technical Specification (TS) 23.501, 3rd Generation Partnership Project (3GPP) (2019). http://www.3gpp.org/DynaReport/23501.htm. version 16.1.0
Bormann, C., Ersue, M., Keränen, A.: Terminology for Constrained-Node Networks. RFC 7228, May 2014. https://doi.org/10.17487/RFC7228, https://rfc-editor.org/rfc/rfc7228.txt
Chandramouli, D., Liebhart, R., Pirskanen, J.: 5G for the Connected World. Wiley, Hoboken (2019)
Condoluci, M., Dohler, M., Araniti, G., Molinaro, A., Sachs, J.: Enhanced radio access and data transmission procedures facilitating industry-compliant machine-type communications over LTE-based 5G networks. IEEE Wirel. Commun. 23(1), 56–63 (2016). https://doi.org/10.1109/MWC.2016.7422406
Fabio Arena, G.P., Collotta, M.: A survey on driverless vehicles: from their diffusion to security features. J. Internet Serv. Inf. Secur. (JISIS) 8(3), 1–19 (2018). https://doi.org/10.22667/JISIS.2018.08.31.001
Galinina, O., Andreev, S., Komarov, M., Maltseva, S.: Leveraging heterogeneous device connectivity in a converged 5G-IoT ecosystem. Comput. Netw. 128, 123–132 (2017). https://doi.org/10.1016/j.comnet.2017.04.051, http://www.sciencedirect.com/science/article/pii/S1389128617301822. survivability Strategies for Emerging Wireless Networks
Garcia-Carrillo, D., Marin-Lopez, R., Kandasamy, A., Pelov, A.: A CoAP-based network access authentication service for low-power wide area networks: LO-CoAP-EAP. Sensors 17(11), 2646 (2017). https://doi.org/10.3390/s17112646, https://www.mdpi.com/1424-8220/17/11/2646
Gaurav Choudhary, J.K., Sharma, V.: Security of 5G-mobile backhaul networks: a survey. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. (JoWUA) 9(4), 41–70 (2018)
Hošek, J.: Enabling Technologies and User Perception Within Integrated 5G-IoT Ecosystem. Vysoké učení technické v Brně, nakladatelství VUTIUM (2016)
Kapassa, E., Touloupou, M., Stavrianos, P., Kyriazis, D.: Dynamic 5G slices for IoT applications with diverse requirements. In: 2018 Fifth International Conference on Internet of Things: Systems, Management and Security, pp. 195–199, October 2018. https://doi.org/10.1109/IoTSMS.2018.8554386
Navarro-Ortiz, J., Sendra, S., Ameigeiras, P., Lopez-Soler, J.M.: Integration of LoRaWAN and 4G/5G for the industrial internet of things. IEEE Commun. Mag. 56(2), 60–67 (2018). https://doi.org/10.1109/MCOM.2018.1700625
Palattella, M.R., et al.: Internet of things in the 5G era: enablers, architecture, and business models. IEEE J. Sel. Areas Commun. 34(3), 510–527 (2016)
Storck, C.R., Duarte-Figueiredo, F.: A 5G V2X ecosystem providing internet of vehicles. Sensors 19(3), 550 (2019). https://doi.org/10.3390/s19030550, https://www.mdpi.com/1424-8220/19/3/550
Wang, D., Chen, D., Song, B., Guizani, N., Yu, X., Du, X.: From IoT to 5G I-IoT: the next generation IoT-based intelligent algorithms and 5G technologies. IEEE Commun. Mag. 56(10), 114–120 (2018). https://doi.org/10.1109/MCOM.2018.1701310
Yasmin, R., Petäjäjärvi, J., Mikhaylov, K., Pouttu, A.: On the integration of LoRaWAN with the 5G test network. In: 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), pp. 1–6, October 2017. https://doi.org/10.1109/PIMRC.2017.8292557
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Garcia-Carrillo, D., Sanchez-Gomez, J., Marin-Perez, R., Skarmeta, A. (2020). EAP-Based Bootstrapping for Secondary Service Authentication to Integrate IoT into 5G Networks. In: You, I., Chen, HC., Leu, FY., Kotenko, I. (eds) Mobile Internet Security. MobiSec 2019. Communications in Computer and Information Science, vol 1121. Springer, Singapore. https://doi.org/10.1007/978-981-15-9609-4_2
Download citation
DOI: https://doi.org/10.1007/978-981-15-9609-4_2
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-9608-7
Online ISBN: 978-981-15-9609-4
eBook Packages: Computer ScienceComputer Science (R0)