Abstract
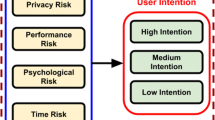
This paper focuses on the brand of mobile devices having the better quality transmission security policy available in the market as per the need of the customers. However, the criteria for each brand of the mobile device have its own functions. So, to choose the reasonable one among accessible options is a challenge and leads to decision-making issues. These issues might be tended to by multiple-criteria decision-making (MCDM) approach. PROMETHEE is one of the decision-making processes that encourage clients to choose the appropriate option depending on their own observation and the criteria they take into consideration. The experiment has been performed based on the feedback provided and the outcome is recorded.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Smartphone Security Threats and Trends. http://www.fishnetsecurity.com/News-Release/Smartphone-Attacks-and-Hacking-Security-Threats-and-Trends-2011, Description: a webpage to introduce recent security threats trends in 2011.
Hajebrahimi, Mehdi. 2014. Evaluation of financial efficiencies of cement companies accepted In Tehran Stock Exchange by multi–criterion decision methods.
Hwang, Junseok, and Irfan Syamsuddin. 2009. Information security policy decision making. Republic of Korea, B. C.: Seoul National University.
Saaty, Thomas L. 1996. Decision making with dependence and feedback: The analytic network process. Pittsburgh, PA: RWS Publications.
İnce, M., T. Yiğit, and A.H Işık. Multi criteria decision making system for learning object repository
https://en.wikipedia.org/wiki/Service-oriented_architecture.
Roy, S., and P.K. Pattnaik. 2013. Some popular usability evaluation techniques for websites. Advances in Intelligent Systems and Computing.
Al-Azab, F.G.M., and M.A. Ayu. 2010. Web based multi-criteria decision making using AHP method. In International Conference on Information and Communication Technology for the Muslim World.
Brans, J.P. 1982. L’ingénierie de la décision; Elaboration d’instruments d’aide à la décision. La méthode PROMETHEE. In L’aide à la décision: Nature, Instruments et Perspectives d’Avenir, ed. R. Nadeau and M. Landry, 183–213. Québec, Canada: Presses de l’Université Laval.
Davignon, G., and B. Mareschal. 1989. Specialization of hospital services in Quebec—An application of the PROMETHEE and GAIA methods. Mathematical and Computer Modelling 12 (10–11): 1393–1400.
Anderson, R. 2001. Why information security is hard: An economic perspective. In Proceedings of 17th Annual Computer Security Applications Conference, 10–14.
Kolli, S., and H.R. Parsaei. 1992. Multicriteria analysis in the evaluation of advanced manufacturing technology using PROMETHEE. Computers & Industrial Engineering 23 (1–4): 455–458.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Samantraj, S., Dash, S., Patnaik, P.K. (2020). Mobile Device Transmission Security Policy Decision Making Using PROMETHEE. In: Swain, D., Pattnaik, P., Gupta, P. (eds) Machine Learning and Information Processing. Advances in Intelligent Systems and Computing, vol 1101. Springer, Singapore. https://doi.org/10.1007/978-981-15-1884-3_1
Download citation
DOI: https://doi.org/10.1007/978-981-15-1884-3_1
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-1883-6
Online ISBN: 978-981-15-1884-3
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)