Abstract
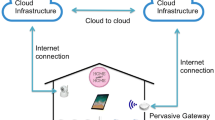
This paper proposes that the healthcare domain can serve as an archetypical field of research in pervasive computing. We present this area from a technological perspective, arguing that it provides a wide range of possible applications of pervasive computing technology. We further recognize that pervasive computing technology is likely to create concerns about the security of healthcare systems, due to increased data aggregation, ubiquitous access, and increasing dependency on technical solutions. But we also justify why the same technology can help building more robust, more dependable systems that increase the quality of healthcare. We identify building blocks that are necessary to achieve this goal: a pervasive middleware, appropriate handling of exceptional situations, and dependability assertions for small devices.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Preview
Unable to display preview. Download preview PDF.
Similar content being viewed by others
References
Agency for Healthcare Research and Quality (February 2003), http://www.ahcpr.gov/qual/errorsix.htm
Allen, J., Christie, A., Fithen, W., McHugh, J., Pickel, J., Stoner, E.: State of the Practice of Intrusion Detection Technologies. Technical Report CMU/SEI-99TR-028, Software Engineering Institute, Carnegie Mellon University, Pittsburgh, PA 15213-3890, USA (2000)
American Accounting Association (AAA), Home page http://accounting.rutgers.edu/raw/aaa/
Anderson, R.J.: A Security Policy Model for Clinical Information Systems. In: IEEE Symposium on Security and Privacy (1996)
Arens, A.A., Loebbecke, J.K.: Auditing: An Integrated Approach, 8th edn. Prentice-Hall, Englewood Cliffs (1999)
Bacon, J., Moody, K., Yao, W.: Access Control and Trust in the Use of Widely Distributed Services. In: Guerraoui, R. (ed.) Middleware 2001. LNCS, vol. 2218, p. 295. Springer, Heidelberg (2001)
Baldwin, F.D.: Putting your assets to work. Healthcare Informatics (April 2001)
Bardram, J.E., Christensen, H.B.: Middleware for Pervasive Healthcare. In: Advanced TopicWorkshop: Middleware for Mobile Computing. IFIP/ACMMiddleware 2001 Conference (2001), http://www.cs.arizona.edu/mmc/ , http://www.pervasivehealthcare.dk/
Barrett, M.J.: The evolving computerized medical record. Healthcare Informatics (May 2000)
Bass, T.: Intrusion Detection Systems and Multisensor Data Fusion. Communications of the ACM 43(4), 99–105 (2000)
Bernstein, P., Hadzilacos, V., Goodman, N.: Concurrency Control and Recovery in Database Systems. Addison-Wesley, Reading (1987)
Bohn, J., Coroama, V., Langheinrich, M., Mattern, F., Rohs, M.: Allgegenwart und Verschwinden des Computers – Leben in einerWelt smarter Alltagsdinge. In: Grötker, R. (ed.) Privat! Kontrollierte Freiheit in einer vernetzten Welt, Heise-Verlag, Hannover (2003)
Brown, D.J., Suckow, B., Wang, T.: A Survey of Intrusion Detection Systems (2001)
Kunze, C., Grossmann, U., Storkand, W., Müller-Glaser, K.D.: Application of Ubiquitous Computing in Personal Health Monitoring Systems. In Biomedizinische Technik. Beiträge zur 36. Jahrestagung der Deutschen Gesellschaft für Biomedizinische Technik 47, 360–362 (2002), http://www.vde.com/de/fg/dgbmt/
Cachin, C., Kursawe, K., Shoup, V.: Random Oracles in Constantinople: Practical Asynchronous Byzantine Agreement Using Cryptography. In: Proceedings of the Symposium on Principles of Distributed Computing, Portland, Oregon, pp. 123–132 (2000)
cnn.com. Medical errors kill tens of thousands annually, panel says (November 1999), http://www.cnn.com/HEALTH/9911/29/medical.errors/
DeJesus, E.: Disease management in a warehouse. Healthcare Informatics (September 1999)
Denley, I., Smith, S.W.: Privacy in Clinical Information Systems in Secondary Care. British Medical Journal 318, 1328–1330 (1999)
Flörkemeier, C., Lampe, M., Schoch, T.: The Smart Box Concept for Ubiquitous Computing Environments. In: Proc. of Smart Objects Conference SOC (2003)
Hightower, J., Borriello, G.: Location Systems for Ubiquitous Computing. Computer 34(8), 57–66 (2001)
The Health Insurance Portability and Accountability Act (HIPAA), http://www.hipaa.org/
Healthcare Informatics. On record: New contracts and installations. Healthcare Informatics (1997) (today)
Joch, A.: Right place, right time. Healthcare Informatics (May 2000)
Kistler, J.J., Satyanarayanan, M.: Disconnected Operation in the Coda File System. ACM Transactions on Computer Systems 10(1), 3–25 (1992)
Kohn, L.T., Corrigan, J. (eds.): To Err Is Human: Building a Safer Health System. National Academy Press (2000), http://books.nap.edu/books/0309068371/html/index.html
Lamport, L., Shostak, R., Pease, M.: The Byzantine Generals Problem. ACM Transactions on Programming Languages and Systems 4(3), 382–401 (1982)
Lunt, T.F.: Automated Audit Trail Analysis and Intrusion Detection: A Survey. In: Proceedings of the 11th National Computer Security Conference, Baltimore, MD (1988)
Marietti, C.: Delivering the goods: How healthcare can plug the leak of billions of supply-chain dollars. Healthcare Informatics (August 1999)
Menezes, A.J., Van Oorschot, P.C., Vanstone, S.A.: Handbook of Applied Cryptography. CRC Press, Boca Raton (1997)
Napoli, M.: Preventing medical errors: A call to action. Health Facts (January 2000)
Clifford Neumann, B., Ts’o, T.: An authentication service for computer networks. IEEE Communications 32(9), 33–38 (1994)
Várady, P., Benyó, Z., Benyó, B.: An Open Architecture Patient Monitoring System Using Standard Technologies. IEEE Transactions on Information Technology in Biomedicine 6(1), 95–98 (2002)
McGraw-Hill Healthcare Information Programs. Industry Report: Health Insurance Portability and Accountability Act. Healthcare Informatics (2000)
Rabin, M.O.: Efficient Dispersal of Information for Security, Load Balancing, and Fault Tolerance. Journal of the ACM 36(2), 335–348 (1989)
Ranum, M.J.: Thinking About Firewalls. Technical report, Trusted Information Systems, Inc. Glenwood, Maryland (1993)
(February 2003), http://www.robocup.org/
Stammer, L.: Seeking SAFETY. Healthcare Informatics (October 2000)
Tsudik, G., Summers, R.: AudES: An Expert System for Security Auditing. In: Proceedings of the AAAI Conference on Innovative Application in Artificial Intelligence (1990)
Weiser, M.: The Computer for the 21st Century. Scientific American, 94–104 (September 1991)
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2004 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Bohn, J., Gärtner, F., Vogt, H. (2004). Dependability Issues of Pervasive Computing in a Healthcare Environment. In: Hutter, D., Müller, G., Stephan, W., Ullmann, M. (eds) Security in Pervasive Computing. Lecture Notes in Computer Science, vol 2802. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-39881-3_8
Download citation
DOI: https://doi.org/10.1007/978-3-540-39881-3_8
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-540-20887-7
Online ISBN: 978-3-540-39881-3
eBook Packages: Springer Book Archive