Abstract
Unified Theory of Acceptance and Use of Technology (UTAUT) is considered as the most comprehensive theory in Information Systems (IS) research to understand technology acceptance across various use contexts. The theory was extended to consumer context by incorporating three external constructs. This extended version is referred as UTAUT2. Although UTAUT2 is relatively new, the increasing number of citations is a testimony to the fact that it’s popular amongst IS researchers especially for examining consumer- focused issues. However, none of the existing studies attempted to analyze the pattern of UTAUT2 citations. This study is aimed to undertake a systematic review of 650 citations with a motivation to fulfill this research gap. The study revealed that majority of the studies i.e. 77% cited UTAUT2 for general citation purpose. However, the remaining 23%, even if they utilized UTATU2, did so in combination with external theories where the moderators of UTAUT2 were rarely considered.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
- Adoption
- Acceptance
- Citation analysis
- Diffusion
- Information systems
- Information technology
- Systematic review
- UTAUT2
1 Introduction
Understanding individual acceptance and use of information technology (IT) is considered as one of the most mature streams of research in the field of information systems (IS) [1]. The adoption and use related issues have been constantly examined due to two reasons: new technologies are constantly evolving and finding their place both in organizations and society, and the IS failure rate continued to be high [2]. Due to constant effort to understand adoption and diffusion related issues, many theories have been developed, adopted or adapted in IS literature to explain technology acceptance and use in various contexts [3,4,5]. This plurality often poses a challenge to IS researchers when selecting an appropriate theory for undertaking a new study. Venkatesh et al. [6] noted that many of these existing theories used similar constructs with different names. Considering that Venkatesh et al. [6] developed the unified theory of acceptance and use of technology (UTAUT) by reviewing, mapping and integrating constructs from eight dominant theories/models (generally utilized in organizational context) of technology adoption emphasizing on the utilitarian value of technology users [4, 5, 7]. The UTAUT theory postulates performance expectancy, effort expectancy and social influence as indirect determinants of use behavior through behavioral intention, whereas behavioral intention and facilitating conditions influence use behavior directly. The theory also hypothesized the relationship amongst the constructs are influenced through various combinations of its moderators namely: gender, age, experience and voluntariness of use [6, 8]. UTAUT explained about 70% of the variance in behavioral intention and about 50% of the variance in technology use [6, 9]. However, the review of 1,267 UTAUT cited papers since its publication revealed just 62 studies (approximately 5%) utilized UTAUT whereas remaining 1,205 studies (comprising 95%) just cited the article for general purposes without using UTAUT or its constructs [8]. This result was consistent with a similar earlier study by [7] on 450 UTAUT cited articles, which revealed only 43 articles (around 10%) utilized UTAUT and the remaining 407 articles (90%) employed it for general citation purpose.
Venkatesh et al. [9] extended their UTAUT for the consumer context emphasizing on hedonic value (intrinsic motivation) of technology users. The extended version of UTAUT is known as UTAUT2, which incorporated three new constructs such as hedonic motivation, price value and habit into original UATUT. However, in UTAUT2 voluntariness of use was dropped as moderator since consumers have no organizational mandate and in many situations, consumer behavior is voluntary [9]. UTAUT2 is gaining momentum in terms of its use to examine IS/IT adoption and diffusion related issues leading to a fast increase in its citations.
Besides UTAUT based theories, the most extensive theory used to study IS/IT adoption within the IS discipline was TAM [4, 6, 10]. Cross-disciplinary and extensive application of TAM since its existence attracted numerous researchers to analyze its actual performance through systemic literature review and meta-analysis approach. Instances of such efforts include Lee et al. [11], King and He [12] and Williams et al. [5, 7]. Similarly, the systematic review of UTAUT with more than 10 years of its existence revealed that UTAUT has been utilized as is or used in combination with other theories or was extended with additional constructs to evaluate a range of technologies in a variety of settings including both organizational and non-organizational [8]. The number of studies using UTAUT2 in various context of technology adoption has increased substantially in the last few years. However, none of the existing studies have conducted a systematic review of UTAUT2 citations for understanding the trend emerging from its use including its purpose of citation, its application and adaptation in various contexts. This study intends to fulfill that purpose.
Given the preceding discussion, the paper is structured as follows. Section 2 will describe the research method employed in this study; Sect. 3 will present the trend emerging from the systematic review of UTAUT2 cited articles into various categories. This will be followed by discussion in Sect. 4 and conclusion in final Sect. 5.
2 Research Method
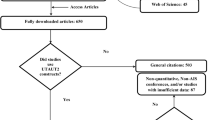
In order to achieve objectives of this research, it was deemed appropriate to conduct a combined analysis of “cited reference search” and systematic review [4, 5, 7, 11, 13]. This study utilized “cited reference search” method in Scopus and Web of Science databases for identifying papers that cited the originating article (i.e. Venkatesh et al. [9]) of UTAUT2 theory from March 2012 to March 2017. The initial search resulted in 1320 total citations (497 from web of science and 823 citations from Scopus). Later it was found that 452 out of 1,320 total citations were overlapping amongst the two databases resulting in a total of 868 unique citations (see Fig. 1). After this step, these 868 citations were screened for the availability of full articles resulting in 650 fully downloaded articles. These articles were then systematically reviewed to reveal various patterns, application and types of UTAUT2 usage.
Total unique citations (C = 868) for Venkatesh et al. [9] article
3 Systematic Review Findings of UTAUT2 Citations
This section presents and explains results from the systematic review based on their purpose of UTAUT2 utilization. Following the approach of Williams et al. [7] the 650 downloaded articles were broadly classified into two categories: (1) General Citation – 503 studies; and (2) UTAUT2 Utilization – 147 studies.
3.1 General Citation
This category refers to studies which just cited Venkatesh et al.’s [9] article for general purposes but did not utilize the theory in any substantial manner. This category of citations included 503 studies. We adapted Williams et al.’s [7] classification to further categories studies with no actual use of UTAUT2. In the process, some of the existing categories were removed, modified and few new categories were introduced resulting in final eight general citation categories of UTAUT2 as summarized in Table 1 and briefly discussed hereafter.
3.1.1 Reference to the Evolution of Technology Adoption Theories in IS Research
The majority of the studies under general citation fell under this category 1. There were 214 studies in total which cited UTAUT2 article either in the introduction section on the discussion about the evolution of individual technology adoption or during the review of existing technology adoption theories in the theory development section. Gu et al. [15] is an example where Venkatesh et al. [9] is cited in the introduction section to support statement on the evolution of individual acceptance and use of IT. On the other hand, Chuah et al. [14] cited UTAUT2 alongside with various other technology acceptance models in the theory development section.
3.1.2 Development of Constructs
Category 2 titled development of constructs consists of 118 studies which cited UTAUT2 to define, compare and support the role of utilizing a particular construct or moderators or control variables during hypothesis development although they didn’t employ the same construct as used in UTAUT2. For instance, Gao and Bai [16] cited UTAUT2 to define “perceived usefulness” construct which is similar to “Performance expectancy” construct of UTAUT2. However, in some cases even if the studies employ few same constructs as in UTAUT2 they adapted measurement items fully or partially from other studies. This phenomenon is observed in Matt et al. [17] study which utilized habit from the UTAUT2 construct. However, the study cited UTUAT2 to compare the construct alongside with other studies and adapted the measurement items for Habit from Limayem et al. [30].
3.1.3 Supporting Findings with UTAUT2
51 studies in this category cited UTAUT2 to support their findings. UTAUT2 is cited to support outcomes evolving from relationship amongst various constructs or moderators used in these studies. For instance, the positive significant effect of the habit construct on users IS continuing intention in Wang et al. [19] was consistent with the UTAUT2 study. On the other hand, the study of Shaikh and Karjaluoto [18] cited UTAUT2 to support the negative effect of experience as a moderating variable.
3.1.4 Research Methodology Design
39 studies fell under this category which cited UTAUT2 in research methodology section. These studies either adopted similar data collection methods or adopted measurement scales from UTAUT2. However, these studies did not utilize any measurement items from UTAUT2 constructs. The study of Stock and Schulz [21] cited UTAUT2 as they employed similar data collection methods by personally contacting consumers in large public places like malls and asked them whether they have used high-tech products. In the case of Alalwan et al. [20] the study adopted the seven-point measurement scale usage pattern from UATUT2 and cited it.
3.1.5 Justification for Application of UTAUT2 in Various Contexts
Category 5 contains 24 studies which justified the application of UTAUT2 in various contexts. Samples include Hess et al. [23], which criticized the extensive application of UTAUT in an institutional context and justified the need for adoption theories such as UTAUT2 in the consumer context. Similarly, Cimperman et al. [22] cited UTAUT2 and demanded the introduction of contextual predictors which could enable more accurate understanding of users of technology in specific domains.
3.1.6 Criticism of TAM or UTAUT2
Category 6 consists of 17 studies which cited UTAUT2 while criticizing TAM or UTAUT2 theory on their various shortcomings. Chandrasekhar and Nandagopal [24] criticized TAM related theories which do not account for many new technology adoption enablers and disablers. The study cited UTAUT2 by stating that in order to make TAM relevant to current day requirements it has to be revised with additional elements. Also, UTAUT2 is not without its criticism. Choi [25] found although hedonic motivation was included as the predictor of behavioral intention and use behaviour in UTAUT2, it failed to discuss factors that lead to enjoyment.
3.1.7 Future Research Suggestion
15 studies under category 7 cited UTAUT2 by referring that it should be used in future. The majority of them are UTAUT based studies insisting to include additional UTAUT2 constructs to their model and test them in consumer context as mentioned in Chang et al. [26]. There were also instances where studies (for example, Hoehle et al. [27]) attempted to integrate their model with existing IS theories like UTAUT2 in future.
3.1.8 Others
This category contains studies which could not be readily classified into any of the other 7 categories and provides brief references to Venkatesh et al. [9] under wider technology adoption research contexts. There were 25 such studies, instances range from McLean et al. [29] study citing UTAUT2 to refer mobile interface research to Brenner et al. [28] study citing UTAUT2 to refer ‘human center design’.
3.2 UTAUT2 Utilization
This category refers to studies which utilized UTAUT2 in some form either standalone or in combination with external theories. There were 147 such studies.
3.2.1 UTAUT2 as Basis for Conceptual Model Development
15 among 147 UTAUT2 based studies were classified under this category. The studies under this category used UTAUT2 as base line model in combination with external theories and proposed a conceptual model to be empirically tested in future along various technology use contexts. The analysis of studies in Table 2 reveals ECT model and trust as most frequently used external theories alongside with UTAUT2- both of them were utilized on three occasions each. This is followed by TOE, TAM, TTF, MMT and SQM each of them being utilized twice with UTAUT2; the remaining theories were used on one instance in combination with UTAUT2. The exploration of remaining 134 UTAUT2 based studies is underway.
Venkatesh et al. [8] provided generic baseline model for individual technology use at feature level for various cross–context research. The remaining studies proposed conceptual model to understand individual users of technology along three major contexts such as employees in organizations, consumers of various technologies and societal context - citizens using E-government services. Research on organizational technology users comprises of three studies: Alazzam et al. [34] study on Medical staffs Intention to use Electronic Health Records, Balaid et al. [35] conceptual model for examining knowledge maps adoption in software development organizations and Rosli et al. [36] study on factors influencing computer-assisted auditing tools (CAATs) acceptance in public audit firms. Two of these three studies employed TOE as an external theory alongside UTAUT2 in understanding organizational technology users signifying popularity of TOE theory in organizational context. Eight studies developed conceptual framework by utilizing UTAUT2 alongside external theories to understand consumers use intention of various technologies. These studies include consumer acceptance of smart mobile devices [37], customer repurchase behaviour in mobile service business [38], customer retention framework in mobile telecommunication services [39], consumers behavioural intention of using autonomous vehicle (AV) [44], individual use of social network sites [46], consumer acceptance behavior of mobile shopping [41] and mobile technology acceptance for library information services [40, 45]. Whereas, Nwanekezie et al. [53] study on public sector online communication channel adoption, Hassan et al. [48] study on citizens’ acceptance and use of health information application embedded in Smart National Identity Card (SNIC) and Kasaj [50] study on user’s adoption of mandatory E-government explored individual use of technology from citizen’s perspective.
4 Discussion
From the results section, it’s observed out of 650 studies only 147 studies (23%) employed UTAUT2 theory in some form. The remaining 503 studies (77%) cited it for general purpose without employing the theory in any substantial manner. Although 23% UTAUT2 utilization is way higher than the application of UTAUT where it was employed by 5% of studies (see Venkatesh et al. [8]) and 10% of studies as reported by Williams et al. [7]. The marked increase in UTAUT2 utilization can be attributed to penetration of IT exploding across the globe touching every aspect of society giving rise to various individuals in the different context to use IT and UTAUT2 is focused on consumer context [8]. We assume given its focus on consumer context, UTAUT2 has not just been utilized by IS/IT researchers but in also other related academic disciplines such as marketing.
The general citation still comprises of 77% studies with majority of them citing UTAUT2 article in introduction section referring to the evolution of technology adoption theories in IS research or during the development of conceptual model as UTAUT and UTAUT2 theories are dominant theory in the field of IS research with similar constructs from major technology adoption theories. However, the higher citation doesn’t correlate to actual usage of theory, which should serve as the caution for future researchers in IS [7].
One of the major limitations of UTAUT based theories is its complex interactions among the various attributes and moderators resulting in relatively less parsimony hindering its usage as such [8]. This shortcoming is still unaddressed in UTAUT2 as the majority of the 15 studies which utilized UTAUT2 didn’t include moderating variables during conceptual model development. The irony of UTAUT/UTATUT2 theories is that since it is comprehensive in nature, it not only hinders efforts in extending the existing theory but also hampers the further theoretical advancement [8].
In terms of methodology this study employed combination of “cited reference search” and systematic review. The results of which partly revealed although UTAUT2 is comprehensive theory many studies utilized external theories alongside UTAUT2 in their research model. This pattern is similar to results shown by Lee et al. [11] in relation to TAM and Williams et al. [7] with respect to UTAUT. This reaffirms careful consideration is required in terms of selecting constructs while developing unified models such as UTAUT in order for them to be deployed as such across various technology use contexts.
5 Conclusion
The noteworthy outcomes of this study through systematic review and findings are listed as follows: (1) there has been a proportionate increase in UTAUT2 theory utilization amongst articles which cited it in comparison to UTAUT. However, most of the studies cited it for general purposes like supporting an argument, following research methodology design rather using the actual theory in substantial manner; (2) Majority of the 15 studies which utilized UTAUT2 omitted the moderating variables due to the complexity of their relationship amongst various constructs; (3) Although UTAUT2 is considered as the most comprehensive model in the field IS/IT adoption research with addition of three new constructs to UTAUT, still most of the studies which utilized UTAUT2, did so in combination with external theories signifying UTAUT2 cannot be used standalone across all technology use context and (4) the analysis of remaining 134 studies that utilized UTAUT2 is underway which could reveal more insightful results. This systematic review of UTAUT2 citations revealed various general citation categories; most frequently used external theories alongside UTAUT2 while developing conceptual model and individual users of technology along three major contexts such as employees in organizations, consumers of various technologies and citizens using e-government services. Although, this study didn’t provide information on UTAUT2 model performance, it did provide understanding about various purposes of UTAUT2 citations which are of scholarly importance to future researchers.
References
Venkatesh, V., Davis, F.D., Morris, M.G.: Dead or alive? The development, trajectory and future of technology adoption research. J. Assoc. Inf. Syst. 8(4), 268–286 (2007)
Dwivedi, Y.K., Wastell, D., Laumer, S., Henriksen, H.Z., Myers, M.D., Bunker, D., Elbanna, A., Ravishankar, M.N., Srivastava, S.C.: Research on information systems failures and successes: status update and future directions. Inf. Syst. Front. 17(1), 143–157 (2015)
Morosan, C.: Toward an integrated model of adoption of mobile phones for purchasing ancillary services in air travel. Int. J. Contemp. Hosp. Manag. 26(2), 246–271 (2014)
Williams, M.D., Dwivedi, Y.K., Lal, B., Schwarz, A.: Contemporary trends and issues in IT adoption and diffusion research. J. Inf. Technol. 24(1), 1–10 (2009)
Williams, M.D., Rana, N.P., Dwivedi, Y.K.: The unified theory of acceptance and use of technology (UTAUT): a literature review. J. Enterp. Inf. Manag. 28(3), 443–488 (2015)
Venkatesh, V., Morris, M.G., Davis, G.B., Davis, F.D.: User acceptance of information technology: toward a unified view. MIS Q. 27(3), 425–478 (2015)
Williams, M.D., Rana, N.P., Dwivedi, Y.K., Lal, B.: Is UTAUT really used or just cited for the sake of it? A systematic review of citations of UTAUT’s originating article. In: ECIS (2011)
Venkatesh, V., Thong, J.Y.L., Xu, X.: Unified theory of acceptance and use of technology: a synthesis and the road ahead. J. Assoc. Inf. Syst. 17(5), 328–376 (2016)
Venkatesh, V., Thong, J.Y., Xu, X.: Consumer acceptance and use of information technology: extending the unified theory of acceptance and use of technology. MIS Q. 36(1), 157–178 (2012)
Dwivedi, Y.K., Williams, M.D., Lal, B.: The diffusion of research on the adoption and diffusion of information technology. In: León, G., Bernardos, A.M., Casar, J.R., Kautz, K., De Gross, J.I. (eds.) TDIT 2008. ITIFIP, vol. 287, pp. 3–22. Springer, Boston, MA (2008). doi:10.1007/978-0-387-87503-3_1
Lee, Y., Kozar, K.A., Larsen, K.R.: The technology acceptance model: past, present, and future. Commun. Assoc. Inf. Syst. 12(50), 752–780 (2003)
King, W.R., He, J.: A meta-analysis of the technology acceptance model. Inf. Manag. 43(6), 740–755 (2006)
Legris, P., Ingham, J., Collerette, P.: Why do people use information technology? A critical review of the technology acceptance model. Inf. Manag. 40(3), 191–204 (2003)
Chuah, S.H.W., Rauschnabel, P.A., Krey, N., Nguyen, B., Ramayah, T., Lade, S.: Wearable technologies: the role of usefulness and visibility in smartwatch adoption. Comput. Hum. Behav. 65, 276–284 (2016)
Gu, R., Jiang, Z., Oh, L.B., Wang, K.: Exploring the influence of optimum stimulation level on individual perceptions of IT innovations. In: PACIS (2014)
Gao, L., Bai, X.: A unified perspective on the factors influencing consumer acceptance of internet of things technology. Asia Pac. J. Mark. Logist. 26(2), 211–231 (2014)
Matt, C., Hess, T., Heinz, S.: Should we take a closer look? Extending switching theories from singular products to complex ecosystem structures. Paper presented at the 2015 International Conference on Information Systems: Exploring the Information Frontier, ICIS (2015)
Shaikh, A.A., Karjaluoto, H.: Mobile banking services continuous usage–case study of Finland. In: 49th Hawaii International Conference on System Sciences (HICSS), 2016, pp. 1497–1506. IEEE (2016)
Wang, Y.S., Li, H.T., Li, C.R., Zhang, D.Z.: Factors affecting hotels’ adoption of mobile reservation systems: a technology-organization-environment framework. Tour. Manag. 53, 163–172 (2016)
Alalwan, A.A., Dwivedi, Y.K., Rana, N.P., Williams, M.D.: Consumer adoption of mobile banking in Jordan: examining the role of usefulness, ease of use, perceived risk and self-efficacy. J. Enterp. Inf. Manag. 29(1), 118–139 (2016)
Stock, R.M., Schulz, C.: Understanding consumers’ predispositions toward new technological products: taxonomy and implications for adoption behaviour. Int. J. Innov. Manag. 19(5), 1550056 (2015)
Cimperman, M., Brenčič, M.M., Trkman, P.: Analyzing older users’ home telehealth services acceptance behavior—applying an Extended UTAUT model. Int. J. Med. Inform. 90, 22–31 (2016)
Hess, T., Legner, C., Esswein, W., Maaß, W., Matt, C., Österle, H., Zarnekow, R.: Digital life as a topic of business and information systems engineering? Bus. Inf. Syst. Eng. 6(4), 247–253 (2014)
Chandrasekhar, U., Nandagopal, R.: Mobile payments at retail point of sale-an Indian perspective. Life Sci. J. 10(2), 2684–2688 (2013)
Choi, S.: The flipside of ubiquitous connectivity enabled by smartphone-based social networking service: social presence and privacy concern. Comput. Hum. Behav. 65, 325–333 (2016)
Chang, H.H., Fu, C.S., Jain, H.T.: Modifying UTAUT and innovation diffusion theory to reveal online shopping behavior: familiarity and perceived risk as mediators. Inf. Dev. 32(5), 1757–1773 (2016)
Hoehle, H., Zhang, X., Venkatesh, V.: An espoused cultural perspective to understand continued intention to use mobile applications: a four-country study of mobile social media application usability. Eur. J. Inf. Syst. 24(3), 337–359 (2015)
Brenner, W., Karagiannis, D., Kolbe, L., Krüger, D.K.J., Leifer, L., Lamberti, H.J., Schwabe, G.: User, use & utility research. Bus. Inf. Syst. Eng. 6(1), 55–61 (2014)
McLean, G., Al-Nabhani, K., Wilson, A.: The Customer Experience… Is there an App for that? A conceptual understanding of the customer experience with m-commerce mobile applications. In: Tiziana Russo-Spenaand Cristina Mele, 1088 (2016)
Limayem, M., Hirt, S.G., Cheung, C.M.: How habit limits the predictive power of intention: the case of information systems continuance. MIS Q. 31(4), 705–737 (2007)
Dwivedi, Y.K., Rana, N.P., Chen, H., Williams, M.D.: A meta-analysis of the Unified Theory of Acceptance and Use of Technology (UTAUT). In: Nüttgens, M., Gadatsch, A., Kautz, K., Schirmer, I., Blinn, N. (eds.) TDIT 2011. IAICT, vol. 366, pp. 155–170. Springer, Heidelberg (2011). doi:10.1007/978-3-642-24148-2_10
Weber, R.: Evaluating and developing theories in the information systems discipline. J. Assoc. Inf. Syst. 13(1), 1–30 (2012)
Johns, G.: The essential impact of context on organizational behavior. Acad. Manag. Rev. 31(2), 386–408 (2006)
Alazzam, M.B., Basari, A.S.H., Sibghatullah, A.S., Ramli, M.R., Jaber, M.M., Naim, M.H.: Pilot study of EHRs acceptance in Jordan hospitals by UTAUT2. J. Theor. Appl. Inf. Technol. 85(3), 378–393 (2016)
Balaid, A., Rozan, M.Z.A., Abdullah, S.N.: Conceptual model for examining knowledge maps adoption in software development organizations. Asian Soc. Sci. 10(15), 118–132 (2014)
Rosli, K., Yeow, P.H., Siew, E.G.: Computer-assisted auditing tools acceptance using I-Toe: a new paradigm. Computer 7, 15 (2012)
Ally, M., Gardiner, M.: The moderating influence of device characteristics and usage on user acceptance of Smart Mobile Devices. In: Proceedings of the 23rd Australasian Conference on Information Systems 2012, pp. 1–10 (2012)
Bhatti, H., Abareshi, A., Pittayachawan, S.: An evaluation of customer repurchase behaviour in mobile telecommunication services in Australia. In: IEEE International Conference on Industrial Engineering and Engineering Management, pp. 602–606 (2016a)
Bhatti, H., Abareshi, A., Pittayachawan, S.: An empirical examination of customer retention in mobile telecommunication services in Australia. In: Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (ICETE 2016), vol. 2 (2016b)
Chaveesuk, S., Vongjaturapat, S., Chotikakamthorn, N.: Analysis of factors influencing the mobile technology acceptance for library information services: conceptual model. In: International Conference on Information Technology and Electrical Engineering (ICITEE), pp. 18–24 (2013)
Marriott, H.R., Williams, M.D.: Developing a theoretical model to examine consumer acceptance behavior of mobile shopping. In: Dwivedi, Y.K. (ed.) I3E 2016. LNCS, vol. 9844, pp. 261–266. Springer, Cham (2016). doi:10.1007/978-3-319-45234-0_24
Matthews, T., Pierce, J., Tang, J.: No smart phone is an island: the impact of places, situations, and other devices on smart phone use. IBM Research Report, pp. 1–10 (2009)
Jacoby, J., Kaplan, L.B.: The components of perceived risk. Adv. Consumer Res. 3(3), 382–383 (1972)
Seuwou, P., Banissi, E., Ubakanma, G., Sharif, M.S., Healey, A.: Actor-network theory as a framework to analyse technology acceptance model’s external variables: the case of autonomous vehicles. In: Jahankhani, H., Carlile, A., Emm, D., Hosseinian-Far, A., Brown, G., Sexton, G., Jamal, A. (eds.) ICGS3 2017. CCIS, vol. 630, pp. 305–320. Springer, Cham (2016). doi:10.1007/978-3-319-51064-4_24
Vonjaturapat, S., Chaveesuk, S.: Proposed mobile technology acceptance model of the information services in a library context. In: Proceedings of the 4th International Conference on Information Systems Management and Evaluation (Icime2013), Acad Conferences Ltd., England, pp. 385–388 (2013)
Zhao, Y., Srite, M.: Modeling online social network use: incorporating espoused national cultural values into an extended unified theory of acceptance and use of technology. In: Proceedings of International Conference on Information Systems, Milan, Italy (2013)
Hofstede, G.: Cultures and Organizations: Software of the Mind. McGraw-Hill, London (1991)
Hassan, I.B., Murad, M.A.A., Nor, R.N.H.B., Abdullah, S.B.: Towards developing a new IP technology adoption framework: a research road map. In: International Conference in Computer Assisted System in Health, pp. 77–83 (2014)
Dinev, T., Bellotto, M., Hart, P., Russo, V., Serra, I., Colautti, C.: Privacy calculus model in e-commerce–a study of Italy and the United States. Eur. J. Inf. Syst. 15(4), 389–402 (2006)
Kasaj, A.: User adoption of mandatory e-government systems: notarial system in Albania, an empirical analyse. In: CBU International Conference Proceedings, vol. 4, pp. 531–543 (2016)
Susanto, T.D., Goodwin, R.: User acceptance of SMS-based e-government services: Differences between adopters and non-adopters. Govern. Inf. Q. 30(4), 486–497 (2013)
Delone, W.H., McLean, E.R.: The DeLone and McLean model of information systems success: a ten-year update. J. Manag. Inf. Syst. 19(4), 9–30 (2003)
Nwanekezie, U., Choudrie, J., Spencer, N.: Public Sector Online Communication Channel Adoption and Usage amongst older adults: a UK local government perspective. In: Proceedings of Twenty-Fourth European Conference on Information Systems, İstanbul, Turkey (2016)
Jøsang, A., Keser, C., Dimitrakos, T.: Can we manage trust? In: Herrmann, P., Issarny, V., Shiu, S. (eds.) iTrust 2005. LNCS, vol. 3477, pp. 93–107. Springer, Heidelberg (2005). doi:10.1007/11429760_7
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 IFIP International Federation for Information Processing
About this paper
Cite this paper
Tamilmani, K., Rana, N.P., Dwivedi, Y.K. (2017). A Systematic Review of Citations of UTAUT2 Article and Its Usage Trends. In: Kar, A., et al. Digital Nations – Smart Cities, Innovation, and Sustainability. I3E 2017. Lecture Notes in Computer Science(), vol 10595. Springer, Cham. https://doi.org/10.1007/978-3-319-68557-1_5
Download citation
DOI: https://doi.org/10.1007/978-3-319-68557-1_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-68556-4
Online ISBN: 978-3-319-68557-1
eBook Packages: Computer ScienceComputer Science (R0)