Abstract
In this paper, we study the problem of minimizing the network coverage breach in a rechargeable wireless sensor network (RWSN). Due to the node density and charging capability constraint, it may happen that a RWSN cannot provide required area coverage some time, yet it may recover later on after obtaining enough recharged energy. To minimize the coverage breach, we propose a family of sensor scheduling algorithms, each of which uses an utility function to greedily choose an active node in each step. Furthermore, we consider a new confident information coverage model that is more efficient for environment monitoring applications. Since this new coverage model takes into consideration of the collaborations in between sensors, it may still exist coverage-redundant active sensors after the scheduling. We then propose another redundancy removal algorithm to further optimize the selected active nodes. Simulation results show that our algorithm with both coverage and energy capability considerations can outperform the traditional coverage-based scheduling algorithm in terms of much smaller breach rate.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
1 Introduction
Wireless Sensor Networks (WSN) have many applications in precision agriculture [1], where sensors are deployed to monitor the soil temperature, humidity and salinity. Network coverage which can reflect the monitoring performance has been widely used to evaluate the quality of service of a WSN [15]. The sensors’ sensing capability and quality can be abstracted by the coverage model, which, however, can be defined in different ways due to the wide range of sensor types and functionalities [15]. Although the simplistic disk coverage has been widely used, it may not be the most appropriate one for such monitoring applications. In this paper, we consider a novel confident information coverage (CIC) model [16], which is based on the theory of field reconstruction and can be used for many physical phenomenon monitoring applications. In Sect. 2, we will briefly introduce the CIC model.
Network lifetime is another important performance metric. In traditional non-rechargeable WSNs, network lifetime is often defined as the maximum time duration till the required network coverage cannot be assured by all available sensor nodes. As such non-rechargeable battery-powered have only limited operation time, therefore the whole network lifetime is not infinite. In order to extend network lifetime, sensor activity scheduling can be used to organize sensors into a series of set covers and then work alternatively, each satisfying the network coverage requirement.
Recently, rechargeable sensor nodes that can harvest energy from environment have been proposed to be used in WSNs to improve network lifetime [3–5, 10, 11, 13, 14, 18–21]. A good survey on how energy harvesting sensor nodes can be used to improve WSN performance can be found in [14]. Most existing works have studied the problem of scheduling rechargeable sensor nodes for target coverage based on the simplistic disk model [4, 5, 11–13, 18–20]. They assume an energy harvesting sensor network is with limited lifetime and they consider the continuous coverage similar as in the non-rechargeable WSNs. Their common objective is to schedule sensor activity efficiently to prolong the lifetime while ensuring the coverage requirement continuously. Furthermore, in most of these studies [3, 4, 11, 12, 17, 20], a centralized controller is assumed to know the exact battery level information and locations of all nodes. However, most of these studies have not considered the different charging capabilities for sensors located at different geographic locations.
A WSN consisting of all rechargeable nodes can achieve infinite lifetime in theory. However, due to the node density and charging capability constraint, it may happen that a RWSN cannot provide required area coverage some time, yet it may recover later on after obtaining enough recharged energy. We call this temporarily loss of coverage requirement as coverage breach, which was previously termed for traditional non-chargeable WSNs for target coverage yet with feedback bandwidth constraint [2, 17]. In [2], sensor activity scheduling based on coverage contribution has been proposed to minimize coverage breach; While in [17], both coverage contribution and residual energy have been considered. But both of them have not considered the charging capability in rechargeable WSNs, yet applying the simplistic disk model for target coverage.
In this paper, we study the minimum coverage breach problem in a rechargeable WSN based on the CIC model. To solve this problem, we propose a family of greedy heuristic active sensor selection algorithms for constructing set covers each satisfying the application coverage requirement. In the set coverage construction, the algorithms greedily select one active sensor node with the maximum utility at each step. We design several utility functions, which take into consideration of the coverage contribution, remaining energy and predicted charging energy. Since this new CIC model considers the collaborations in between sensors, it may still exist coverage-redundant active sensors after the scheduling. We then propose another redundancy removal algorithm to further optimize the selected active nodes. Simulation results show that our algorithm with both coverage and energy capability considerations can outperform the traditional coverage-based scheduling algorithm in terms of much smaller breach rate.
The rest of the paper is structured as follows. The system model is introduced in Sect. 2 and we precisely define our problem in Sect. 3, Sect. 4 presents a family of greedy heuristic solutions. Simulation results are provided in Sect. 5, and Sect. 6 concludes the paper.
2 Preliminaries
2.1 Confident Information Coverage
The CIC model [16] is based on the theory of field reconstruction. We assume that a specific physical phenomenon within the sensing field needs to be monitored. Let \(z^t(x)\) denote the true value of the physical attribute at a reconstruction point x, and \(\hat{z}^{t}(x)\) denote its estimated value. We use the time-average root mean square error (RMSE) to evaluate the reconstruction quality for each reconstruction location, that is,
Given a reconstruction function and reconstruction requirement \(\varepsilon \), a space point x is called being \(\varPhi \)-covered, if \(\varPhi (x) \le \varepsilon \). A sensor field is said being completely \(\varPhi \)-covered, if all the space points within the field are \(\varPhi \)-covered.
In many applications, the physical phenomenon can be modeled as a second-order stationary stochastic process. We can adopt the widely used ordinary Kriging [6, 7] as a reconstruction function. Furthermore, we use only those sensor nodes located within the correlation range of a space point for its attribute reconstruction. This is due to that the spatial correlation of a physical phenomenon is often within a limited range. We note that after some further mathematical transformations, whether a point is \(\varPhi \)-covered can be determined by the geometric relations among the point and the sensors within its correlation range.
2.2 Energy Charging Model
Each rechargeable sensor node can harvest energy by its solar panel, but it can only be charged in the sleep state, since in many cases each node is equipped with only one rechargeable battery with a simple switch circuitry [9, 20]. We adopt an approximate one-day energy charging model for each solar panel [8], which uses a quadratic curve to model the solar energy harvested in the daytime; While in the night, the harvested energy is zero:
where \(E^{max}\) is the maximum charging rate and \(\kappa =\mathrm {mod}(k,24)\) is to obtain the remainder after k is divided by 24 h of a day.
In practice, since the solar panel and recharge battery are not cheap, the solar panel size and battery storage capacity are generally not made very large. The charging rate is determined by the size of a solar panel. So the maximum battery capacity can be set to store the maximal chargeable energy in a whole day. On the other hand, it is possible that different nodes are equipped with different sizes of solar panel. Furthermore, solar power generation depends on the intensity of solar radiation, and obstruction of sunlight can impact on the charging rate. In a large sensor field, sensor nodes are widely distributed at different locations, and it is not uncommon that some sensor nodes may be within the shadow of foliage and crops for different times. Therefore, the charging rates are uneven across sensor nodes.
3 Problem Statement
We consider a randomly deployed WSN consisting of rechargeable sensor nodes, each equipped with a solar panel and a rechargeable battery. We assume that each sensor node can be in one of two states: active and sleep. In the active state, a sensor node samples the physical phenomenon and consumes an amount of the energy stored in its battery. Furthermore, a sensor node in the active state cannot charge its battery. In the sleep state, a sensor node consumes negligible energy, but it can charge its battery.
In traditional non-rechargeable WSNs, the battery of each sensor node is with limited capacity and is not rechargeable. Therefore, the operational time of a sensor node is not infinite, and so is a non-rechargeable WSN. Sensor activity scheduling is a common approach to extend the network operational time by alternatively activating only a subset of sensors at a time. The scheduled active sensors need to meet the network coverage requirement. The network lifetime is often defined as the maximum time duration till the network coverage cannot be guaranteed by all available sensors.
In rechargeable WSNs, a sensor node can be recharged after its battery depletion. In theory, the operational time of a rechargeable node can be infinite, and so is a rechargeable WSN. However, as a sensor node cannot charge all the time, like in the night and in the active state, the totally available sensors with enough battery energy may not be enough at sometimes, which can lead to coverage breach, i.e., the network coverage requirement cannot be achieved even with all sensors being active sometimes. In this paper, we study the coverage breach problem in such a rechargeable WSN.
Coverage breach can be avoided by deploying more nodes and/or equipping larger solar panel and rechargeable battery, but this approach is too expensive. In a rechargeable WSN, coverage breach is not permanent, but can be self-recovered after sensor nodes are recharged. We can adopt the sensor scheduling approach to alternatively activate sensors, such that the coverage requirement can be satisfied by active sensors, yet the network breach can be minimized.
In this paper, we divide the continuous time line into consecutive slots with equal length. In one slot, a sensor can be in either active or sleep state. In the beginning of each slot, a sensor node is called a candidate if its remaining energy can support the whole slot. In the beginning of each slot, we select active sensors from all candidates to form a set cover by which the network coverage requirement can be achieved. The worst case is that a coverage breach occurs, even if all the candidates are active. If this happens, we have two options: One is still to activate all candidates to only fulfill partial coverage requirement; The other is to deactivate all nodes such that they can have chances to recharge. In this paper, we choose the latter option, as our main objective is to minimize the average breach rate in a long term viewpoint, other than differentiating breaches.
Table 1 summarizes the symbols and notations. We next provide the problem formulation as follows. Consider a long term duration consisting of K slots, the breach rate is defined as
where \(\mathbb {I}(\cdot )\) is an indicator function. \(\mathbb {I}(\varPhi (C_k) < \varPhi _{th})=1\), if \(\varPhi (C_k) < \varPhi _{th}\); Otherwise, it equals to 0. Note that a set cover can be an empty set, which means no rechargeable nodes been selected to be active.
The problem of minimizing coverage breach rate can be formulated as:
Where
Remarks:
-
The first constraint guarantees that the remaining energy does not exceed the maximum storing energy of each sensor \(s_i\) across the lifetime and it is non-negative.
-
The second constraint guarantees that the remaining energy of each selected active sensor is not smaller than consumed energy in a time slot.
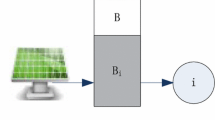
We further illustrate our problem in Fig. 1. We consider a long duration of K slots. There may exist coverage breach in some time slots. For example in Fig. 1, \(C_3\) is a breach slot. In a breach slot, all the rechargeable sensor nodes will switch to the sleep state. Note from Fig. 1, the required \(\varPhi \)-coverage can still be guaranteed in the 5th slot, if some nodes have recharged enough energy in the 4th slot. Therefore, although a RWSN can in theory work infinitely, coverage breach may happen due to the lack of sensor density and charging capability. For this new characteristic of RWSNs, few work have been done before for minimizing coverage breach. Although an optimum solution to the minimum breach rate problem may be found through exhaustive search for all possible set covers in all slots, its computation complexity is very prohibitive. In the next section, we propose a family of greedy selection algorithms to approach this problem.
4 Heuristic Solutions for Breach Minimization
In the beginning of each slot, the proposed algorithm constructs a set cover to satisfy the network coverage requirement. The set cover is initiated as an empty set. The basic idea of these algorithms is the same: A set cover is constructed by greedily selecting the sensor with the largest utility to be included into the set cover in each step, until the coverage requirement is satisfied or all the candidates are included into the set cover.
Table 2 provides the core pseudo-codes of the proposed algorithms. In the beginning of each iteration, we first obtain the candidate sensor sets \(\mathcal {I}\) (line 4). In each iteration of the While loop, it constructs one set cover until the required \(\varPhi \)-coverage is guaranteed or the candidate set is empty (line 6). In each iteration for sensor selection, we choose the one with the largest utility (line 7). When it cannot find a set cover to provide required \(\varPhi \)-coverage, a coverage breach happens and all selected sensor nodes switch to sleep state (line 12); Otherwise, we implement the redundancy removal algorithm to optimize the constructed set cover (line 14). We next present our proposed utility functions and redundancy removal algorithms.
4.1 Utility Function
Coverage Contribution: The first utility function is purely based on the \(\varPhi \)-coverage contribution. For a sensor \(s_i\), its \(\varPhi \)-coverage contribution is defined as the newly increased \(\varPhi \)-coverage ratio, if it is included into the set cover \(C_k\):
According to the CIC property, if a single sensor is used for \(\varPhi \)-coverage, its covered area is actually the disk coverage model, i.e., a disk centered at itself with a radius r. However, when two sensors within the correlation range are used for \(\varPhi \)-coverage, their covered area is in general more than the union of their respective coverage disks. For example, in Fig. 2, we use a disk to illustrate the coverage of a single sensor; yet the yellow region surrounding the sensors \(s_1\) and \(s_2\) is the \(\varPhi \)-covered area by the two sensors. Clearly, the concept of \(\varPhi \)-coverage expands the disk coverage, yet it can still maintain the same coverage quality in terms of the RMSE of \(\varPhi \)-covered area being larger than the same threshold.
Therefore, when computing the \(\varPhi \)-coverage of \(\varPhi (C_k \cup \{s_i\})\), not only the area within the sensing radius \(s_i\) should be considered, but also the area that could be covered by the collaboration of \(s_i\) and some sensors in \(C_k\) within the correlation range of \(s_i\). For example, in Fig. 2(a)–(d), the blue, green, magenta and cyan area represents the coverage contribution \(\varDelta \varPhi (s_3)\), \(\varDelta \varPhi (s_4)\), \(\varDelta \varPhi (s_5)\), and \(\varDelta \varPhi (s_6)\), respectively. Among them, the sensor \(s_3\) has the largest coverage contribution.
The first utility function is hence defined as:
The above utility function is efficient in selecting the least number of sensors. However, it may happen that a sensor could be selected into multiple consecutive set covers, which leads to its loss of recharging opportunities and even renders its temporarily shutdown. Coverage breach may happen due to such temporary death of some sensor nodes, which might become even more prominent in a rechargeable WSN with uneven charging rate. Therefore, a utility function should also take energy into consideration.
Coverage Contribution and Remaining Energy: The storage capacity of the rechargeable battery is limited due to its high cost. Therefore, for a fully charged sensor node, if the scheduling algorithm puts it into the sleep sate, it is a waist of its recharging opportunity; Whereas other sensor nodes in the active state with less residual energy could miss the opportunity for harvesting energy. Therefore, we include the remaining energy into the utility function as follows:
Here we compute the battery level of sensor i by its remaining energy divided by its maximum battery storage. Compared with Eq. (5), the above utility function takes the remaining energy into consideration, which may help to improve the energy balance across all sensors. For example in Fig. 2, among \(s_3, ..., s_6\), the sensor \(s_6\) has the largest utility. Its selection may help to reduce the risk that some other sensor losses of charging opportunity.
Coverage Contribution and Predicted Energy: Considering the fact of uneven charging rates, the prospective energy level may be different in the spatial domain, which is another critical factor we should consider. We assume that the amount of energy harvested by the sensor in a certain future time period is estimable [8]. Here we denote the prospective energy level as the predicted energy divided by the maximum battery storage. We thus consider to increase the likelihood for a sensor with high prospective energy level to charge its energy such that from the whole network perspective, more environment energy can be exploited. Hence we define the next utility function:
With the above utility the sensor nodes which cannot harvest plenty of energy, for example \(s_4\), should give the charging opportunity to those sensors with high perspective energy level, such \(s_3\), \(s_5\) or \(s_6\), in order to increase the energy inflow to the whole network.
Coverage Contribution, Remaining Energy and Predicted Energy: Based on the above discussions, we know that there are three main factors impacting on the selection of a sensor node, namely, coverage contribution, remaining energy and predicted energy. Therefore, we propose another utility function to combine all the three factors as follows:
Compared with Eqs. (6) and (7), the above utility function assigns a higher priority to a sensor node with higher remaining energy as well as lower recharging potential. As it makes some balance in between of using abundant remaining energy and charging more environment energy, it can increase the likelihood of more charging energy for the whole network for future usage while without dramatically depleting a single sensor. For example from Fig. 2, we should compare the battery level, perspective energy level and coverage contribution to compute the utility of candidate sensors \(s_3,...,s_6\), and then select \(s_5\) for its highest utility.
4.2 Redundancy Removal
The greedy nature of the proposed algorithms implicitly imposes a constraint of nonreversible selection. That is, once a sensor node is selected, it will not be removed from the set cover. The only exception is that the set cover cannot fulfill the network \(\varPhi \)-coverage requirement, and all the sensor nodes in the set cover are dismissed and converted back into the sleep state.
This irreversibility of the greedy algorithms needs to be considered in our \(\varPhi \)-coverage model. Note that in the \(\varPhi \)-coverage model, the area covered by a set of sensors is also dependant on the geometric relations in between these sensors. Therefore, after a sensor has been newly included, it not only covers some previously uncovered area, but also changes the geometric relations among the sensors being selected. Therefore, this inclusion of a new sensor may change the \(\varPhi \)-coverage structure of the whole field. So we need to recheck the coverage redundancy after the set cover construction.
We next propose a redundancy removal (RR) algorithm. A redundant node is defined as such a node that its deletion from the set cover does not compromise the network coverage requirement. The basic idea of the proposed RR algorithm is to iteratively remove one redundant node with the smallest utility at a step, until the network coverage cannot be satisfied if further deletion is performed.
Table 3 presents the pseudo-codes of the proposed RR algorithm. In each iteration of the For loop, the algorithm checks the coverage redundancy of constructed set cover. If redundancy does not exist, return the set cover (line 13). Otherwise, we will remove the redundant sensor in terms of its utility step by step (line 15–17). Note that a redundant sensor has its coverage contribution equal to zero. Therefore, we redefine the utility for redundant sensor node as \(\frac{{U({s_i})}}{{\varDelta \varPhi ({s_i})}}\) (line 15). Ties are broken randomly. After deleting one redundant sensor nodes, we should recheck the redundancy (line 17).
5 Simulation Results
Our simulations are written in MATLAB 7.10.0 (2012a). We simulate a rechargeable WSN randomly deployed in a 1 km \(\times \) 1 km sensor field. For the CIC model, the correlation range is set to 0.4 km, and the reconstruction RMSE requirement \(\varepsilon \) is set to 0.2. For each rechargeable node, we use Eq. (2) as its charging model and set one hour as a slot. We also normalize the energy charging and consumption with respect to a slot. The initial energy or the maximum energy storage of all sensor nodes is set to 1 slot and the energy consumed in each slot is set to 0.2 slot.
We call the algorithms using different utility functions as CC using Eq. (5), CC-RE using Eq. (6), CC-PE using Eq. (7), and CC-REPE using Eq. (8). We use a uniform distribution to model the uneven charging rates across sensors. The maximum charging rate \(E^{max}\) of each node is set to be uniformly distributed within \([0.1,\mathcal {K}]\). Therefore, we change the value of \(\mathcal {K}\) to change the uneven charging degree. We simulate a long period of 500 slots and all results are average over 20 different network deployments.
Figures 3 and 4 compare the breach rate for the four algorithms against the number of deployed nodes and the uneven charging degree, respectively. It is not unexpected that the breach rate decreases with the increase of number of sensors, and with the increase of uneven charging degree on the whole. It can also be observed that the proposed algorithms with energy consideration outperform the CC algorithm without energy consideration. Furthermore, the CC-REPE algorithm achieves the smallest breach rate. This indicates that our greedy selection algorithms can maximally reduce the coverage breach when the utility function takes both the remaining energy and predicted energy charging into the scheduling consideration.
Figure 5 plots the breach rate against different network RMSE thresholds. It is observed that the breach rate decreases with the increase of the RMSE threshold. Again the CC-REPE algorithm achieves the smallest breach rate among the algorithms. In the CIC model, the network RMSE determines the reconstruction quality requirement. When the RMSE requirement is relaxed, the number of sensors which can collaborate to provide CIC coverage for a same field can be generally reduced. Hence more sensor nodes could have more time to harvest energy and the breach rate can be reduced.
We further use the Fig. 6 to illustrate the breach distribution of four proposed utility functions among the simulation of the 500 time slots. A burst breach is defined as a coverage breach spanning two or more consecutive breach slots. Here we define the number of breach slots in each burst breach as burst value, namely, the degree of burst breach. In the Fig. 6, the burst value can be reflected by the thickness and the shade of bar. Figure 7 compares the number of total breached slots and the number of different predefined burst breach for the four utility functions. It is clearly seen that the utility functions taking energy into account can improve the performance of network compared with the purely coverage-based CC algorithm. Moreover, CC-REPE outperforms the other two in terms of both of the number of breach slot and burst breach. This is because that the CC-REPE considers both of remaining energy and charging potential, which might help to balance the energy distribution not only in the temporal domain for individual sensors, but also in the spatial domain for the whole network.
6 Conclusion
In this study, we have studied the problem of minimizing breach rate in rechargeable sensor networks and proposed a family of greedy selection algorithms to organize sensor nodes into a series of set covers which work alternatively based on the novel CIC model, each satisfying applications coverage requirement. Moreover we implement the redundancy removal algorithms (RR) to optimize the constructed set cover. Simulation results demonstrate that the utility function CC-REPE which consider the coverage benefit, remaining energy and predicted energy outperforms the others in terms of the smallest breach rate. Our future work will further consider the connectivity and design efficient distributed scheduling algorithms.
References
Camilli, A., Cugnasca, C.E., Saraiva, A.M., Hirakawa, A.R., Corrêa, P.L.P.: From wireless sensors to field mapping: anatomy of an application for precision agriculture. Comput. Electron. Agric. 58(1), 25–36 (2007). (Elsevier)
Cheng, M.X., Ruan, L., Weili, W.: Coverage breach problems in bandwidth-constrained sensor networks. ACM Trans. Sens. Netw. 3(2), 2198–2216 (2007)
Dewitt, J., Patt, S., Hongchi Shi: Maximizing continuous barrier coverage in energy harvesting sensor networks. In: IEEE International Conference on Communications (ICC), pp. 172–177 (2014)
Eto, M., Katsuma, R., Tamai, M., Yasumoto, K.: Efficient coverage of agricultural field with mobile sensors by predicting solar power generation. In: IEEE International Conference on Advanced Information Networking and Applications (AINA), pp. 62–69 (2015)
Fu, N., Suppakitpaisarn, V., Kimura, K., Kakimura, N.: Maximum lifetime coverage problems with battery recovery effects. In: IEEE Global Communications Conference (GLOBECOM), pp. 118–124 (2014)
Harrington, B., Huang, Y., Yang, J., Li, X.: Energy-efficient map interpolation for sensor fields using kriging. IEEE Trans. Mob. Comput. 8(5), 622–635 (2008)
Hernandez-Penaloza, G., Beferull-Lozano, B.: Field estimation in wireless sensor networks using distributed kriging. In: IEEE International Conference on Communications (ICC), pp. 724–729 (2012)
Huan, X., Wang, B., Mo, Y., Yang, L.T.: Rechargeable router placement based on efficiency and fairness in green wireless mesh networks. Comput. Netw. 78(4), 83–94 (2015). (Elsevier)
Kar, K., Krishnamurthy, A., Jaggi, N.: Dynamic node activation in networks of rechargeable sensors. In: INFOCOM 2005, Proceedings IEEE of the 24th Annual Joint Conference of the IEEE Computer and Communications Societies, vol. 3, pp. 1997–2007 (2005)
Lexie, D., Lin, S., Wu, J.: Adaptive battery charge scheduling with bursty workloads. In: IEEE Global Communications Conference (GlOBECOM), pp. 708–713 (2012)
Pryyma, V., Turgut, D., Bölöni, L.: Active time scheduling for rechargeable sensor networks. Comput. Netw. 54(4), 631–640 (2010). (Elsevier)
Ren, X., Liang, W., Wenzheng, X.: Quality-aware target coverage in energy harvesting sensor networks. IEEE Trans. Emerg. Top. Comput. 3(1), 8–21 (2015)
Severini, M., Squartini, S., Piazza, F.: Energy-aware lazy scheduling algorithm for energy-harvesting sensor nodes. Neural Comput. Appl. 23(7–8), 1899–1908 (2013). (Springer)
Sudevalayam, S., Kulkarni, P.: Energy harvesting sensor nodes: survey and implications. IEEE Commun. Surv. Tutorial 13(3), 443–461 (2011)
Wang, B.: Coverage problems in wireless sensor networks: a survey. ACM Comput. Surv. 43(4), 1–53 (2011)
Wang, B., Deng, X., Liu, W., Yang, L.T., Chao, H.-C.: Confident information coverage in sensor networks for field reconstruction. IEEE Wireless Commun. 20(6), 74–81 (2013)
Wang, C., Thai, M.T., Li, Y., Wang, F., Wu, W.: Minimum coverage breach and maximum network lifetime in wireless sensor networks. In: IEEE Global Communications Conference (GLOBECOM), pp. 1118–1123 (2007)
Yang, C., Chin, K.-W.: Novel algorithms for complete targets coverage in energy harvesting wireless sensor networks. IEEE Commun. Lett. 18(1), 118–121 (2014)
Yang, C., Chin, K.-W.: A novel distributed algorithm for complete targets coverage in energy harvesting wireless sensor networks. In: IEEE International Conference on Communications (ICC), pp. 361–366 (2014)
Yang, C., Chin, K.-W.: On complete target coverage in wireless sensor networks with random recharging rates. IEEE Wirel. Commun. Lett. 4(1), 50–53 (2015)
Yoo, H., Shim, M., Kim, D.: Dynamic duty-cycle scheduling schemes for energy-harvesting wireless sensor networks. IEEE Commun. Lett. 16(2), 202–204 (2012)
Acknowledgement
This paper is supported in part by the National Natural Science Foundation of China (No. 61371141), and the Fundamental Research Funds for the Central Universities (No. HUST2015QN081).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing Switzerland
About this paper
Cite this paper
Xiong, Z., Wang, B. (2016). Minimizing Confident Information Coverage Breach in Rechargeable Wireless Sensor Networks with Uneven Recharging Rates. In: Huang, X., Xiang, Y., Li, KC. (eds) Green, Pervasive, and Cloud Computing. Lecture Notes in Computer Science(), vol 9663. Springer, Cham. https://doi.org/10.1007/978-3-319-39077-2_14
Download citation
DOI: https://doi.org/10.1007/978-3-319-39077-2_14
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-39076-5
Online ISBN: 978-3-319-39077-2
eBook Packages: Computer ScienceComputer Science (R0)