Abstract
The security of information is one of the most important attributes to be available when the secret information passes between two parties. Many techniques like watermarking, cryptography and steganography used for this purpose. Cryptography changes the position of original information or scramble the original information, but it reveals the existence of secret information. The hiding the data behind any other object is steganography characteristic. Information hiding characteristic make the steganography more popular as compare to cryptography process. In this paper transform domain-based steganography process are discussed. The main focus in transform domain steganography is the wavelet family; paper includes detail information about different wavelet used in steganography process. The procedure is investigated and contended in the provisions of its payload limit i.e., the capacity to conceal data, how much data can be covered up, and its robustness.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Digital data transmission over the internet is the most popular source to share secrete information now days. Advanced medium has acquired a lot of significance nowadays and is turning into the dependable mechanism for the exchange of data. With the improvement and induction of web to everybody, it has become simpler and conceivable to copy and to disseminate the computerized data misguidedly. Carefully communicated information can be unimaginative with no deficiency of information and its quality too, which is a major issue to the security, credibility and ownership to the proprietor of the information [1].
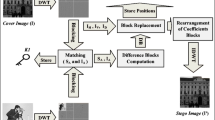
From history of numerous years, individuals have been attempting to foster best in class procedures for secret correspondence. The three strategies related to security systems are interlaced; steganography, watermarking and cryptography. Both the procedures of cryptography and steganography used for treatment of data and information to encode and cover them exclusively. Both the systems are extensively known and used. Steganography covers the presence of information however cryptography calculates a message with the objective that it can’t be seen. In explicit cases, sending the code information draws the thought, while the hidden information doesn’t. The foundation of a stenographical mixed structure can be assessed through key parts like intangibility and breaking point. Impalpability shows the difficulty to choose the mysterious message. The other measure limit shows the best proportion of secret message or data that can be concealed securely, and strength, which implies that how fine the steganography system counterattacks the extraction of introduced data. The structure of steganography is displayed in Fig. 1, according to the steganography subdivision; four main categories play important role with their special characteristics. The most common and oldest techniques come in spatial domain categories. Least significant bit replacement and matching are the most popular methods in this category. The spatial domain is easy to use but it has also had drawbacks in information security upcoming techniques like frequency domain, spread spectrum, and other feature extraction techniques strengthen the security of data in image steganography.
The paper is subdivided in sections: Sect. 2 contains the introduction about transform domain, Sect. 3 contains wavelet family introduction, and Sect. 4 include the conclusion of the transform domain techniques.
2 Literature Survey on Transform Domain Techniques
The image steganography used transform domain method very frequently; in transform domain method first step is to transform the cover image into different domain. In the second step transformed coefficients used to hide the secret information. The transform domain transformed back into spatial domain to get stego image. The main characteristic of transform domain is use of signal processing operations. There are different kind of transform domain method are available, let’s look into them one by one.
2.1 Discrete Cosine Transform
One of the main current conversations in picture improvement is the Discrete Cosine Transform (DCT) strategy. A DCT is another well-known strategy utilized in light of the fact that it is quick and powerful. The essential capacity of DCT is to change signals from the spatial portrayal into the frequency portrayal [2]. Many fields those are not related to the scientific field also use the DCT for their application development common applications are picture editing, picture formation. One of the important applications in the field of DSP is video conferencing. The DCT is used in change for data pressure. DCT is an even change, which has a fair course of action of reason work [3].
See Fig. 2, if the image contains red, green and blue components then at the time of sampling they are divided in blocks. In \(8 \times 8\) pixel array starts at the upper right at \((\mathrm{0,0})\) and finish at the lower right at \((\mathrm{7,7})\). At the point \((x, y)\) the data value is \(f (x,y).\) Here \(x\) and \(y\) represent the coordinate in image blocks.
2.2 Discrete Wavelet Transform
The digital images use DWT, there are many DWTs are available. According to the properties of wavelet application appropriate wavelet are selected from DWT family. The essential work design of DWT is deterioration picture in 4 sub-groups named as: LL, HL, LH and HH. The LL sub band contains the main components of the picture. So according to the image embedding requirement sub band are used to store the secret information. There are many types of wavelets are available let’s take a look in Sect. 3 how they are work and how they are different to each other [4].
2.3 Discrete Fourier Transform
In the field of advanced sign preparing discrete fourier transform (DFT) is very important tool. In image steganography DFT can be used in three possible ways. First, by using the DFT signal’s frequency spectrum calculation which is directly examine the encoded frequency, phase, and amplitude of the image sinusoids signal. Second, DFT able to discover a framework’s motivation reaction and framework’s recurrence reaction, as well as the other way around. Third, DFT help in more elaborate signals intermediate steps. The DFT is exceptionally helpful symmetrical changes and have been viewed as the critical advances for signal handling in symmetrical recurrence division multiplexing correspondence frameworks [5].
According to the Fig. 3, if DFT apply on N tests of time-space the outcome likewise is of length N tests, yet the data it contains is of the frequency domain representation.
3 Wavelet Family
3.1 Haar Wavelet
Haar wavelet is the oldest wavelet in wavelet family, the simplicity of the haar wavelet makes it more popular. It is also known as symmetric wavelet in mathematical operation it is known as haar transform. The haar transform give a generalized model for all other wavelet transform. In mathematics, haar create sequence of rescaled square shapes. The main advantage of using haar is simplicity, speed, memory efficiency and disadvantage is that it is in contiguous [6].
Figure 4 show the haar transform, consider transforming the single seismic trace. The trace consists two zones, a weak zone on the left side, and a strong zone on the right side.
3.2 Daubechies Wavelet
Daubechies wavelets are the most notable wavelets. They address the foundations of wavelet signal getting ready and are used in various applications. These are similarly called Maxflat wavelets as their repeat responses have most noteworthy equity at frequencies 0 and π. Daubechies and haar wavelet are almost similar the main contrast between them comprises in how these scaling signs and wavelets are characterized. The debaucheries family wavelet knows with name dbN see (Fig. 5), where db is surname and N is the order of wavelet [6].
3.3 Coiflets
Coiflets designed by Ingrid Daubechies, at the request of Ronal Coifman, to have scaling function with vanishing moments. It means the Coiflet wavelet can use the wavelet with the greater number of vanishing moments for analysis resulting in a sparse representation. The reconstruction part needs smoother wavelet support. The Coiflets family wavelet knows with name coifN see (Fig. 6), where coif is surname and N is the order of wavelet [7].
3.4 Symlet
Symlet wavelets are the changed variation of Daubechies wavelets with extended balance. They are similarly estimations and moderately maintained wavelets The scaling channels utilized are close immediate stage channels and the effect of Symlet is practically same as those of the Daubechies wavelets. The Symlet wavelet and scaling activity for demands are as show below in Fig. 7:
The Symlet wavelets are otherwise called Daubechies’ smallest disproportionate wavelets however they are more symmetric.
3.5 Biorthogonal Wavelet
In image and signal reconstruction linearity is the important aspect. The biorthogonal wavelet gives more control over image reconstruction than an orthogonal wavelet. The image is reconstructed similar with the help of filters impulse response. The reverse biorthogonal wavelet constructed with the help of pair of biorthogonal wavelets [8].
The resulting spline biorthogonal wavelets for \((p=4, \widehat{p}=4)\) is illustrated in Fig. 8.
3.6 Reverse Biorthogonal Wavelet
The reverse biorthogonal wavelet otherwise called rbio, it is a sort of wavelet which is corresponded to a wavelet change. It isn’t basically symmetrical yet using reverse biorthogonal wavelet, gives an open door in arranging in any system appear differently in relation to even wavelets, for case, the possibility in fostering the symmetric wavelet limits [9].
3.7 Meyer Wavelet
Meyer wavelet is a classic wavelet, it has many good properties. The haar and daubechies wavelet are support orthogonal wavelets but with the help of meyer wavelet they are able to reconstruct perfect image quality. This is achieved due to the properties of meyer wavelet like induction vastly, perfection, lessens quickly and its range is limited, meyer wavelet is gainful to mathematical ascertain, so it applies generally in designing majors [10].
Figure 9, shown the meyer wavelet, its smoothness, sufficient decay, vanishing mean and oscillatory behavior with diverse oscillation scan can be seen from the figure.
3.8 Curvelet Transform
The curvelet transform is analysis tool which is used in multiscale geometric objects. The objects include the curve inside of it. The curvelet development motive is to improve the traditional transformations work on curves and edges. The best result of curvelet came if the image contains the curves. The previous research on curvelet proof that the curvelet small scale coefficient better than wavelet’s high frequency coefficients. The curvelet implement in image steganography by two methods:
-
(i)
Using Wrapping Method.
-
(ii)
Using Fast Fourier Transformation algorithm (FFT).
The recommended technique for curvelet varies by the spatial lattice decision. The job of spatial network decision is too used the decipher curvelet coefficients at each scale and point. The result of both methods is in form of curvelet coefficient table. The coefficient table listed the curvelet coefficient according to the spatial location, angle and scaling factor [11]. Type of Curvelet Transform:
Continuous-Time Curvelet Transform.
The Curvelet work on two-measurement information type like picture. The hub of these two measurements addresses spatial variable and recurrence space variable x, ω separately. Recurrence space has two polar directions r and θ [12]. The curvelet change characterized in two windows these windows notice the materialness conditions. The windows know as spiral window {W(r)}, and precise window {V (t)}. The mathematical representation of this window is:
The radial window and angular window support the polar “wedge”, represented as Uj. The representation of Uj in fourier domain is:
Curvelet tiling of space and frequency [2].
Figure 10, induced tiling of the frequency plane and spatial cartesian grid associated with a given scale and orientation.
Fast Discrete Curvelet Transform via Wrapping.
The wrapping based curvelet is the new innovation in the field of curvelet change. The wrapping based curvelet change is a multiscale pyramid; the pyramid contains many sub groups. The sub groups are arranged on various sizes of various directions and positions in the recurrence space. The 2D picture is utilized in wrapping of fourier examples as information. The picture cluster is as cartesian exhibit f [m, n], where the scope of m lies between 0 to M and n lie between 0 to N. Here, the M and N are the elements of the cluster [11].
According to the Eq. (4), the output collected in to the curvelet coefficients \({c}^{D }\left(j,l,{k}_{1, }{k}_{2}\right)\) indexed by scale \(j\), an orientation \(l\) and spatial location parameters \({k}_{1}\) and \({k}_{2}\).
Figure 11, illustrates the whole image represented in spectral domain in the form of rectangular frequency tiling by combining all frequency responses of curvelets at different scales and orientation.
3.9 Tetrolet Transform
The tetrolet transform work on the basic structure of Haar filter. The Haar filter divided the 2D image in four blocks according to the low pass and high pass filter. The size of the block in Haar is 2 × 2 square, but in tetrolet the image divided in 4 × 4 blocks in horizontal and vertical direction. The block is not overlapping each other because the image is also not overlap. Each block divided fit for another block available in the subdivision [13]. Sometime the size of image not able to divide in four parts in that case tetrolet transform uses the zero-padding [14]. There are five shapes see (Fig. 12) available to represent the tetrolet transform they are named as:
-
1.
Square-O-Type
-
2.
Rectangle-I-Type
-
3.
T-Type
-
4.
S-Type
-
5.
L-type
5-shapes of the tetrominores [15].
After the locating work of tetrominores, the pixels of 4 × 4 blocks are rearranged according to TT rules see (Fig. 13). The image is reform by the tetrominores with the help of haar wavelet transform.
A combination of tetrominores for a 4 × 4 pixel block [15].
The decomposition of the tetrolet complete in four steps, the steps are as follows [16]:
-
1.
Divide the 2D image into 4 × 4 blocks.
-
2.
For each block find the sparsest tetrolet representation.
-
3.
Low and high pass coefficients rearrange into 2 × 2 block into every subdivide block.
-
4.
The high- pass part or tetrolet coefficients store.
Repeat step 1 to 4 to the low-pass image.
4 Wavelet Selection
Selection of correct wavelet depend upon different wavelets analysis tests. Different wavelet properties also show impact on wavelet selection such as orthogonality, compact support, symmetry, and vanishing moment. The wavelet family with its properties presented in the following Table 1.
Were Nr, Nd, and N are the orders: r for reconstruction and d for decomposition [17].
5 Comparative Study Between DCT, DWT, and DFT
The 32 × 32 binary image resolutions used as an secret. This image will embed on image with 65536 total pixel amount, since 1 pixel of binary image will embed on 8 × 8 image sub-block. Figure 14(a) is used as a secret image and Fig. 14(b) as a cover image.
(a) Secrete image, (b) Cover image [18].
Table 2 shows the results of embedding secrete image to the Low Frequency (LF), Middle Frequency MF, and Highest Frequency (HF) of cover image.
6 Comparative Study Between Daubechies and Cofilet Wavelet
The properties of different wavelet discuss in Table 1, according to the properties Daubechies and Confilet wavelet have many similarities but the vanishing point of Confilet is more than Daubechies wavelet. In this section, the results are obtained at 3rd level of decomposition [19]. The MATLAB tool is used to obtain the results. The result analyzed on Mean Square Error (MSE), Peak Signal to Noise Ratio (PSNR), and Signal to Noise Ratio (SNR) factors. Here, two images taken for result analysis as shown in Fig. 15 (a-b).
Table 3, clearly represent the Coiflet wavelet give better result for both images. The selection of correct wavelet gives better result on different comparison factors. The graphical representation of result show in Fig. 16, and Fig. 17.
7 Conclusion
In this paper, we have surveyed a transform domain image steganography technique, which is used for texture retrieval of image. This work is based on the adaptability of transform domain according to image geometry in frequency domain. The main focus of this paper is on wavelet method for image steganography, according to the study haar wavelet is the oldest one which create base for other wavelet techniques. The older wavelet is very easy to use because they break the image in four squares according to the low and high pass filters but this structure also makes them common. The curvelet and tetrolet wavelet introduce new feature in the traditional wavelet family. Curvelet give better results if your image contains the curves because the curvelet work on angular concept, at the same place on the off chance that we talk about the tetrolet, tetramines adjusts as indicated by picture math. In this way, there is no need of taking explicit bearings, rather picture calculation is thought about. We trust that this study will assist analysts with choosing the best calculation and component extraction techniques to meet their necessities.
References
Sharma, N., Batra, U.: A review on spatial domain technique based on image steganography. In: 2017 International Conference on Computing and Communication Technologies for Smart Nation (IC3TSN), Gurgaon, India, pp. 24–27. IEEE (2017)
Azani Mustafa, W., et al.: Image enhancement based on discrete cosine transforms (DCT) and discrete wavelet transform (DWT): a review. In: IOP Conference Series: Materials Science and Engineering, Bogor, Indonesia, pp. 1–10. IOP Publishing (2019)
Raid, A.M., Khedr, W.M., El-dosuky, M.A., Wesam, A.: JPEG image compression using discrete cosine transform - a survey. Int. J. Comput. Sci. Eng. Surv. 5(2), 39–47 (2014)
Hemalatha, S., Dinesh Acharay, U., Renuka, A., Priya, R.: A secure color image steganography in transform domain. Int. J. Cryptogr. Inf. Secur. 3(1), 17–24 (2013)
Zhou, J.: Realization of discrete fourier transform and inverse discrete fourier transform on one single multimode interference coupler. IEEE Photonics Technol. Lett. 23, 302–304 (2011)
Sharda, S., Budhiraja, S.: Performance analysis of image steganography based on DWT and Arnold transform. Int. J. Comput. Appl. 69, 46–50 (2013)
Kaur, S., Rani, V.: Designing an efficient image encryption-compression system using a new HAAR, SYMLET and COIFLET wavelet transform. Int. J. Comput. Appl. 129(15), 1–6 (2015)
Shaker, A.N.: Comparison between orthogonal and bi-orthogonal wavelets. J. Southwest Jiaotong Univ. 55(2), 1–10 (2020)
Abidin, Z.Z., Manaf, M., Shibhgatullah, A.S.: Experimental approach on thresholding using reverse biorthogonal wavelet decomposition for eye image. In: 2013 IEEE International Conference on Signal and Image Processing Applications, Melaka, Malaysia, pp. 349–353. IEEE (2013)
Zhang, X., Deng, C., Han, Y.: The image space of meyer wavelet transform. In: Proceedings of 2013 2nd International Conference on Measurement, Information and Control, Harbin, pp. 1136–1139. IEEE (2013)
Mostafa, H., Fouad, A., Sami, G.: A hybrid curvelet transform and genetic algorithm for image steganography. Int. J. Adv. Comput. Sci. Appl. 8(8), 328–336 (2017)
Alzubi, S., Islam, N., Abbod, M.: Multiresolution analysis using wavelet, ridgelet, and curvelet transforms for medical image segmentation. Int. J. Biomed. Imaging 2011(2011), 1–18 (2011)
Liu, S., Huang, X., Zhang, D., Yan, Q., Du, X., Fang, F.: Stationary tetrolet transform: an improved algorithm for tetrolet transform. J. Phys: Conf. Ser. 1069(1), 1–8 (2018)
Ceylan, M.: Performance comparison of tetrolet transform and wavelet-based transforms for medical image denoising. Int. J. Intell. Syst. Appl. Eng. 5(4), 222–231 (2017)
Rajeshkumar, N., Yuvaraj, D., Manikandan, G., Balakrishnan, R., Karthikeyan, B., Raajan, N.R.: Secret image communication scheme based on visual cryptography and tetrolet tiling patterns. Comput. Mater. Continua 65(2), 1283–1301 (2020)
Indra, P.: Tetrolet transform based efficient breast cancer classification system. In: Second International Conference on Current Trends in Engineering and Technology - ICCTET, Coimbatore, India, pp. 579–583. IEEE (2014)
Achmamad, A., Jbari, A.: A comparative study of wavelet families for electromyography signal classification based on discrete wavelet transform. Bull. Electr. Eng. Inform. 9(4), 1420–1429 (2020)
Asmara, R.A., Agustina, R.: Comparison of Discrete Cosine Transforms (DCT), Discrete Fourier Transforms (DFT), and Discrete Wavelet Transforms (DWT) in Digital Image Watermarking. Int. J. Adv. Comput. Sci. Appl. 8(2), 245–249 (2017). https://doi.org/10.14569/IJACSA.2017.080232
Abhinav, D., Swatilekha, M.: Comparative analysis of Coieflet and Daubechies wavelets using global threshold for image denoising. Int. J. Adv. Eng. Technol. 6(5), 2247–2252 (2013)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Khandelwal, J., Sharma, V.K., Raguru, J.K., Goyal, H. (2022). Recent Trend of Transform Domain Image Steganography Technique for Secret Sharing. In: Joshi, S., Bairwa, A.K., Nandal, A., Radenkovic, M., Avsar, C. (eds) Cyber Warfare, Security and Space Research. SpacSec 2021. Communications in Computer and Information Science, vol 1599. Springer, Cham. https://doi.org/10.1007/978-3-031-15784-4_14
Download citation
DOI: https://doi.org/10.1007/978-3-031-15784-4_14
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-15783-7
Online ISBN: 978-3-031-15784-4
eBook Packages: Computer ScienceComputer Science (R0)