Abstract
Nowadays both sciences and technology, including Intelligent Transportation Systems, are involved in improving current approaches. Overview studies give you fast, comprehensive, and easy access to all of the existing approaches in the field. With this inspiration, and the effect of traffic congestion as a challenging issue that affects the regular daily lives of millions of people around the world, in this work, we concentrate on communications paradigms which can be used to address traffic congestion problems. Vehicular Ad-hoc Networking (VANET), a modern networking technology, provides innovative techniques for vehicular traffic control and management. Virtual traffic light (VTL) methods for VANET seek to address traffic issues through using vehicular network communication models. These communication paradigms can be classified into four scenarios: Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) and Vehicle-to-Network (V2N) and Vehicle-to-Pedestrian (V2P). In general, these four scenarios are included in the category of vehicle-to-everything (V2X). Therefore, in this paper, we provide an overview of the most important scenarios of V2X communications based on their characteristics, methodologies, and assessments. We also investigate the applications and challenges of V2X.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The use of normal traffic lights to control the flow of traffic on the road and at intersections is usually a challenging issue. By leveraging new technology in the area of communication, information science, and positioning, we will lead to more efficient, secure, safer, and thus more sustainable locomotion.
The advancement of vehicular communications systems, as well as the growing number of vehicles on the road, has created a requirement for the manufacturing and academic community to address the new challenges. The traditional traffic light scheme has a number of weaknesses. Vehicles encounter delays as a result of fixed time intervals, particularly when traffic is not heavy. It is difficult to manage traffic based on vehicle priority and road capacity when there is traffic congestion. In addition to the fast advancement of communication technologies, future cars are supposed to be intelligent enough to communicate with their environment in a variety of ways. Many car companies, including BMW, Tesla, Hyundai, and Google, are designing self-driving or autonomous vehicles. Accordingly, a new networking technique known as vehicular ad-hoc networking is receiving a lot of interest in vehicular communication systems study. Vehicle Ad-hoc Networking (VANET) is a new emerging field that is currently being studied extensively [1]. The information distributed for future vehicles is taken into account by car manufactures. Therefore, VANET is anticipated to incorporate various applications. Future vehicles applications will include traffic and parking data, weather situations, bus schedules, fuel costs, and entertainment applications [2]. Moreover, vehicles are supposed to communicating practical information same as location, speed, rout direction, and goods/passengers being transported to each other [3].
For VANET, a considerable number of algorithms have been suggested. The Virtual Traffic Light system (VTL) is one of the most famous traffic optimization methods for improving the movement of vehicles on the roads and intersections. Indeed, VTL and the smart traffic light system are alternatives that have been identified for the failings of the traditional traffic light system. Despite the advantages of having a smart traffic light system, there are still some issues to be considered, such as the cost of installing traffic lights on the roads and intersections and the high expenses of service, and preservation. Hence, researchers are currently focusing their efforts on designing traffic lights using VTL in the context of smart cities, Vehicle-to-Everything communications, and IoT. Ferreira et al. in [4] introduced the first VTL method for VANET. Many researchers have investigated and applied related experiments and performance monitoring since the first studies on VTL were published. In this paper a number of the most important researches in this area are investigated. Some of the advantages of VTL are as follows:
-
Time is important in our life. VTL helps people to spend less time in traffic congestion.
-
With spending less time in traffic congestion, VTL reduces air and environmental pollution.
-
Traffic causes stress, pollution, and road rages. VTL helps us to reduce them and improve the health and life quality.
-
VTL expedites large-scale deployment of autonomous vehicles.
-
VTL increases safety at intersections, on highways, and other road segments.
As it was mentioned before, in 2010, VTL was presented for the first time. Its aim is to alleviate traffic congestion by utilizing communications paradigms known as Vehicle-to-everything technology (V2X) [5]. V2X is a new descendant of information and communication technology aimed at connecting vehicles to everything surrounding them. So many studies and researches have been conducted in this area since the first introduction.
The paper is organized as follows: Sect. 2 introduces V2X technology and describes some of its applications and challenges. Section 3 summarizes the main scenarios of V2X and gives a review of them. In Sect. 4 we discuss what we reviewed in the previous section. Finally, in Sect. 5 the conclusion is drawn.
2 V2X: Applications and Challenges
The transportation sector’s accelerated growth is beset by major challenges, obstacles, and problems: how to reduce the number of road accidents, fossil energy dependency, the greenhouse impact induced by fossil fuel pollution, fossil fuel reliance, the greenhouse impacts induced by fossil fuels, ways of optimizing and making efficient use of automobiles, as well as enhancing the drivers’ skills, and plenty of other significant and related issues.
One of the most serious challenges among those mentioned above is decreasing the number of deaths and injuries in road crashes, which is current throughout all countries around the world. Road deaths and accidents have far-reaching consequences not only for the victims but also for the whole of society and economic prosperity.
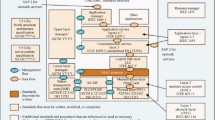
To overcome the aforementioned problems, a number of vehicle communication networks are being developed by both communications and automotive companies, and also scientific and government organizations around the world. Based on the participants that communicate information directly, various forms of vehicle communication networks exist. Vehicle-to-Vehicle (V2V) networks are made up of mobile nodes that are actually moving vehicles that directly communicate with each other. Vehicle-to-Pedestrian (V2P) or Vehicle-to-Infrastructure (V2I) networks are built when vehicles, which are moving on the roads, interact and communicate either with pedestrians or with roadside infrastructure. When the communication is between vehicle and data centers and/or IT networks, the structure of the network is vehicle-to-network (V2N). A widely known concept that incorporates all these modes of communication, that provide vehicle connections to different receivers, is called vehicle-to-everything (V2X) (Fig. 1).
V2X communications, together with the current capabilities of modern vehicles, can not only address the above-mentioned problems but will also provide better quality public transportation systems, more effective logistics strategies, better road quality, efficient utilization of transport facilities, especially accurate electronic maps and many other innovative and relevant services and solutions.
Dedicated Short Range Communication (DSRC) and Cellular Vehicle-to-Everything (C-V2X) communication systems are the two information exchange technologies generally used for V2X. The DSRC scheme consists of a number of IEEE and the Society of Automotive Engineers (SAE) standards [6]. C-V2X is a wireless networking system with a high data rate and monitored QoS [7, 8], and is based on the 3rd Generation Partnership Project’s concept of Long-Term Evolution mobile communication technology.
2.1 Applications
V2X enables the existence of different applications as a result of technological advancements in the fields of wireless sensing and networking. Some of these applications are shown in Fig. 2. In general, applications of V2X communication can be classified into three categories: Safety, efficiency, and information services applications (Table 1) [5, 9, 10]:
-
Safety applications reduce crashes and protect users from hazards by using wireless communications amongst entities in the vicinity. Every roadway entity sends a safety alert to all of its neighbors regularly to inform them of its current state. They will also be required to send out warning alerts if a local or global incident is observed. Personal safety applications, such as crashes, speeding alerts, and road hazard alerts, are included in this category.
-
Green wave speed guidance and congestion alerts are examples of efficiency applications that help drivers to drive and enhance traffic efficiencies. To effectively control traffic and ensure seamless traffic flow, traffic-related applications are implemented. Their responsibility is aggregating traffic data and wirelessly sending it to a central server for processing. The results of the analysis are then delivered to vehicles for possible future use [11].
-
Services such as eCall, traffic updates and route suggestions, automated parking, and entertainment are examples of information services applications. They provide drivers with these vehicle-related data to ameliorate the driving experience [7].
V2X will gently fulfill the criteria for autonomous automated driving and applications in intelligent traffic systems, in addition to the aforementioned applications. For these specialized strategies, the 3GPP distinguishes four categories of applications: Advanced Driving, Vehicle Platooning, Remote Driving, and Extended Sensors.
However, more conventional mobile applications, like entertainment providers, will gently join the V2X market and industry.
2.2 Challenges
Reliability and Latency Challenges: For applications involving low latency and high reliability, network performance is critical. To gain crash avoidance and multi-user accessibility, DSRC employs Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). DSRC has lower latency and better reliability when there are fewer cars, but it performs more poorly when there are more vehicles. The delay of C-V2X is fairly stable over time, and communication latency is less than 100 ms when it is based on the PC5 interface, which allows less interference and predictable and manageable delay [12]. Soon, 5G networks will be capable of supporting automatic-driving-oriented V2X systems with a transmission latency of less than 1 ms and 99.999% reliability and stability. V2X communication network encounters and is vulnerable to a variety of attacks that can cause it to perform poorly. Denial of service (DOS) and distributed DoS (DDoS) refers to intense attacks on target nodes by external or domestic attackers that cause network and service resources to be exhausted [13]. They can create negative effects, like high latency in communication, unavailability of the network, and node operation unavailability. DoS attacks include attacks like greedy behavior attacks and jamming attacks [14]. A greedy behavior attack occurs when a network node breaks channel access rules and takes up many other channel resources, which causes decreasing the efficiency of other nodes and creating network congestion problems [15]. A jamming attack is a kind of attack which is a threat to the physical layer. Via electromagnetic disturbance, the attacker blocks the wireless channel, causes reducing the reliability of the network and increasing the delay of V2X communication [5, 16].
Challenges related to Security: As it is mentioned before, in vehicular communication context, V2X is frequently used in a variety of applications. These kinds of applications contain traffic safety, infotainment, and information applications that enforce different criteria to enable V2X implementation. These diversified needs lead to research challenges being developed. The main V2X security challenges are listed below [17, 18].
-
Scalability of the network: V2X communication technology contains a huge and large-scale worldwide network of vehicles. V2X standards, such as DSRC, do not require a universal authority to regulate and govern them. Controlling large networks while also dealing with security problems such as certificate exchange is a really difficult task to tackle. For such networks, security strategies that require prior information of participating vehicles/nodes are ineffective.
-
Communication latency: Some specific issues, like which data to collect, which data to analyze, what data should be refined, and what must be transferred and received, can induce latency in V2X communication. Hence all factors relating to V2X communication latency must be investigated to manage security-critical and safety circumstances in real-time.
-
Dynamic topology of the network: The dynamic and complex nature of the topology of the network in V2X (due to mobility) is a critical concern that is hard to manage, specifically when it comes to security features and frameworks. In general, vehicles move at high speed and therefore make connections for a short time. So it will be a tough challenge to adapt the security requirements to the quality of communication, which is affected by high-speed vehicles.
-
Attack prevention: The vehicular communication network is expected to serve a wide range of applications and services. Vehicles would have to transfer important data, such as vehicle identity, to enable these operations, which demands maximum security for approval from the perspectives of the overall communication infrastructure. In V2X, attacks can be classified into two types: system-level attacks and user-level attacks. Creating a particular public key infrastructure framework for preserving the high mobility function of vehicular communication can be an effective strategy for minimizing the aforementioned threats [5].
There are some other challenges related to security same as data priority, heterogeneity, user’s privacy and trust, and acceptance of future operating systems and platforms.
3 V2X Communications Scenarios
In previous sections, we mentioned that V2X incorporates all methods of vehicle communications, including V2V, V2I, V2N, and V2P. This section focuses on reviewing these paradigms. The first subsection investigates the V2V scenario, the most significant scenario of this series, addressing the principal services, systems, and applications that better satisfy the needs to attain effective collaboration between vehicles. In other subsections, we review some studies and features of V2I, V2N, and V2P.
3.1 Vehicle-to-Vehicle (V2V)
V2V communication technology includes wireless data transmissions among motorized vehicles. The main objective of such communication is to avoid possible crashes by enabling vehicles to exchange data on their location and speed using an ad-hoc mesh network [19]. Fully connected mesh topology improves the network structure’s robustness. Whether a node fails or temporarily malfunctions, the paths are recomputed within the transmission tables in order to access all destinations.
Before, when mesh networks were still wired, fully connected topology was prohibitively costly and impossible to implement since each node needed to be physically connected to all of the others. Nowadays, with the emergence of Wireless Personal Area Networks (WPANs) and by using the benefits of wireless networking, these drawbacks have been solved. Each independent and moving node in these networks, connected to others, generates an arbitrary-sized graph (partially linked mesh network). In the network, instead of being dependent on a base station to organize the transmission of messages to each destination, Individual nodes send packets to each other independently. While wireless topology differs quickly and unpredictably, these nodes are able to move randomly and arrange themselves arbitrarily. Besides that, these networks may function independently or be in connection with the Internet to provide extra services.
Based on developments of new technologies, the vehicle driver will receive warnings when there is a crash risk, or the vehicle itself may take preventive strategies on its own, like emergency braking, if it is developed to perform safety strategies [20]. V2V communications are anticipated to be much more efficient than existing embedded systems developed by Original Equipment Manufacturers (OEMs) because vehicle safety depends on the performance of onboard radar systems, sensors, cameras, and so on [21]. Depending on the particular parameters observed by these instruments installed on the vehicle, the system responds to any potentially hazardous situations. Speed, location, traffic flow, distance from other vehicles or a hazard, and the existence of an automobile in the wrong or blind place are generally the most significant analyzed parameters Fig. 3. Nevertheless, while V2V communication technologies are becoming more accurate and reliable, calculation and measurement errors should not be overlooked. V2V communication strategies, on the other hand, can enhance safety performance by connecting all vehicles which are close together and enabling them to communicate with each other. They can help the vehicle to make appropriate decisions in dangerous situations (for example, a driver’s nap, a component breakdown, and so on) and manage the arising problem. Thus, the main goal of each node in the mesh network will be aggregating data to ensure excellent safety and security for its own and its neighbors. This strategy is known as cooperative awareness [22]. However, as proposed in [23, 24], it is highly beneficial to use appropriate coding techniques for real-time data access.
V2V communication technology, in collaboration with already developed security frameworks, will result in effective handling of possible problems on the world’s roadways. The modern Intelligent Transport Systems (ITSs) are going to utilize data provided by V2V communication to improve traffic management and enabling vehicles to have communications with roadside infrastructures like signs or traffic lights. In the future, V2V communication technologies can become compulsory by governments and leading to significant improvements in producing more reliable self-driving vehicles. However, the deployment of V2V communications and a smart transportation system faces some major challenges: the preservation of privacy and secrecy of data transmitted in broadcast and multicast, the requirement for making vehicle manufacturers accept operation and security laws, and the funding required for the production and distribution of all technologies. It is currently uncertain if public or private companies and individuals will fund and support the construction and preservation of communication infrastructure. Nonetheless, Audi, BMW, General Motors, Volvo, and Tesla are amongst the top vehicle manufacturers that focus on ITS and V2V communication networks. In the last years, the assessment of prototypes for V2V communication applications has become a type of research and advancement for several vehicles company all around the world, particularly in the United States. As a consequence of these efforts, through a series of analytical techniques, some experimental models have been performed in order to predict the possible future effects due to the large hypothetical incorporation of applications in the sector of vehicular communications, and also the potential environmental effects, which are difficult to analyze now due to the absence of a norm.
Many researchers have focused on V2V communication technologies to improve traffic flow on the roads and intersections, where the findings of the studies confirmed the effectiveness of implemented strategies. Ferreira et al. in [4] proposed switching from traditional traffic lights to virtual traffic lights inside of the vehicles since V2V communication networks support it. They presumed that each vehicle has a DSRC system. They also assumed a similar digital route map is shared by all of the vehicles, and they have a global positioning system (GPS). Eventually, it was supposed that the wireless service is reliable and secure, and its performance is acceptable for VTL’s requirements.
Every vehicle is equipped with a specialized Application Unit (AU) that stores intersections and road information in advance to specify the locations of roads and intersections where a VTL is needed. When the vehicle arrives at these crossings, the AU looks for a VTL wireless signal followed by, if none is detected, a new VTL is made. If a VTL is required, the vehicles that are close to the intersection will select a vehicle to be the leader (which is the closest vehicle to the intersection). The leader will establish and operate the VTL, and temporarily facilitates the movement of vehicles by sending the traffic directions. Then, the leader transfers the intersection control to the next vehicle to complete the task of controlling the intersection and preserving the VTL. When the last car leaves the intersection, the VTL will terminate. This model was executed using DIVERT simulation, and the results indicated more than 60 improvement in intersections traffic flow.
Azimi et al. in [25] discussed, by simulations, the utilization of V2V communication technology among autonomous vehicles to maximize throughput and reduce accident risks at roads and intersections. Their findings demonstrated significant increases in secure throughput across a variety of traffic scenarios. The Red Light and Stop Sign Violation Warning system are some other prominent safety contributions of connected vehicles (CV).
Sepulcre and Gozalvez in [26] carried out several field experiments to assess three V2V collaborative safety applications in real circumstances: overtaking assistance, lane change assistance, and forward-collision warning. The experiments demonstrated the effect of vehicular blockages and communication power rate on the reliability of applications in various propagation conditions. The research findings experimentally demonstrated the strong relationship between the requirements of application and reliability, driving circumstances, and communications efficiency. Furthermore, considering the higher criteria imposed by collaborative active safety applications, the findings revealed some limitations created at high vehicular speeds.
Boban and D\('\)Orey in [27] did several field experiments to analyze the effectiveness of V2V collaborative awareness systems in terms of delivered packet ratio, neighbor beyond range ratio, and neighborhood awareness ratio. They realized that collaborative awareness is highly dependent on connection quality and conditions of propagation. As a result, awareness ratios are lower for metropolitan scenarios, moderate for suburban scenarios, and highest for highway and freeway scenarios. In terms of connection type, the findings indicate that beneficial situations of Road Side Units (RSUs) increase awareness ratios for V2V communications.
Bazzi et al. in [28] presented a decentralized VTL method which is based on V2V communication technology, intending to identify priorities of intersections in a controlled and decentralized form in IEEE 802.11p V2V communications. The protocol operates in two phases: defining the first priority, as CVs reach a vacant intersection, defining the subsequent priorities. The next step (priorities when the first CV crosses) is dependent on a priority grant process from the CV whit priority to the next CV. Experiments implemented in both standardized laboratory settings and field trials confirmed the effectiveness of the method.
3.2 Vehicle-to-Infrastructure (V2I)
V2I communication technology is defined as the wireless exchanging of operational and safety information amongst vehicles and roadside infrastructure (through the use of roadside equipment or RSE) utilizing DSRC methods. The purpose of V2I communication is to avoid and minimize the intensity of vehicle accidents. Besides that, it can also improve mobility systems and environmental advantages by helping applications like speed standardization and traffic flow optimization. Roadside infrastructure aggregates real-time data on traffic arrangements and rules (e.g., variable speed restrictions and signal state) and dangers (e.g., crashes and violations) and transmits this data to relevant vehicles in the form of alerts or guidelines. The greatest benefit of the DSRC V2I framework is that it can customize messages to specific vehicles rather than propagating identical warning signals to all users. A wide range of communication technologies and algorithms can be used to implement V2I communication.
Sepulcre et al. in [29] proposed a heterogeneous context-aware V2I method in which vehicles choose the best radio access system with the help of roadside infrastructure to enhance both personal and system efficiency. Every vehicle makes the decision on its own, with infrastructure assistance. The obtained results indicate the advantages of the suggested approach as well as its reliability to the variability and precision of the context information.
In [30] Wuthishuwong et al. developed an autonomous system for smart transportation. The main purpose of this work is to develop a mechanism that guarantees a crash-free movement of an intersection while still reducing traffic congestion, as the second goal. Via the use of V2I communication technology, they tried to implement the technique for autonomous intersection control. The intersection challenge is modeled using discrete mathematics, and the direction of a vehicle is determined through dynamic programming. The results of the simulation indicate a crossing of the intersection without any accident. Also, vehicles move continuously.
Mohammed et al. in [31] introduced a V2I framework to increase the awareness of car drivers at signalized intersections. The primary goals are: (1) to perform a proof-of-concept field test by using the V2I communication framework at a signalized intersection and (2) to analyze the effect of the V2I communication framework on enhancing the performance of drivers when they are crossing the intersection. The application of the suggested V2I communication framework transmits an auditory advisory notification to inform the driver about traffic signal status. The driver’s behavior and attitude are expected to change due to audible communication. Their study results indicated that maximum and average speeds were decreased as a result of crossing the intersection as well as the drop in deceleration values before arriving at the intersection, especially during the red phase.
Gheorghiu et al. in [32] presented a research work and focused on the possibilities of using ZigBee communication technology for V2I communication. In comparison with other technologies, these communications consume less energy and are suggested for crowded urban environments where infrastructure instrument density exceeds higher levels and requires significant energy consumption. As a method to evaluate V2I communications in the laboratory, a prototype for vehicle recognition using the Zigbee technology is introduced.
Al-qutwani and Wang in [33] proposed that rather than using traffic lights at each intersection, we can use a Roadside Unit (RSU) to function as the intersection manager. The RSU receives the signals of vehicles that have entered or will come to the intersection. Just after analyzing the orders in accordance with the priority rules and policy, RSU sends an instant message to each vehicle to move through the intersection or stop for a while. This method is appropriate for autonomous vehicles since instead of processing a large number of images, they just receive digital signals from RSU.
3.3 Vehicle-to-Network (V2N)
V2N communication technology illustrates the communications between the vehicle and a network provider that offers access and connectivity to the vehicle, maybe on several frequencies. This communication will include non-critical yet valuable information (like road blockage and congestion) and also some services based on the cloud, which amplify the experience of the passengers, while also acting as a hotspot for internet access. Furthermore, vehicle to cloud connectivity takes advantage of V2N connections to wideband mobile networks, aiming to exchange data with the cloud. Several methods and approaches have been proposed about V2N and vehicle to cloud communications. We review some of them as follows.
He et al. in [34] proposed an innovative multi-layered vehicular data cloud framework utilizing IoT technologies and cloud computing. Two novel vehicular data cloud systems for vehicle warranty processing in the IoT environment have also been introduced: a vehicular data mining cloud system and a smart parking cloud system. Two updated data mining methods, a Nave Bayes method, and a Logistic Regression method were thoroughly investigated for the vehicular data mining cloud system.
Pillmann et al. in [35] concentrated on estimating the accessible data rate by using an analytical method based on experiential measurements. A Common Vehicle Information Model (CVIM) is amalgamated with a vehicle simulator to generate CVIM compatible data streams, as a consequence of the individual behavior of each car (speed, the activity of steering, the activity of brake, and so on). Consequently, a novel vehicle-to-cloud communication framework has been developed, which measures the data rate of collected vehicle-to-cloud data generated by vehicles based on present traffic conditions (traffic jams and the free traffic flow).
Guldenring et al. in [36] presented a novel Multi-Radio Access Technology (Multi-RAT) sharing method which helps the vehicle sensors to upload data more efficiently and faster. This method makes use of various network interfaces and integrates them into a single coherent communication link. Data uploading may be postponed to take advantage of better channel conditions and prevent uploading when the quality of the channel is low. The simulation reports and assessments showed that the presented method is appropriate and efficient for vehicular data uploading.
3.4 Vehicle-to-Pedestrian (V2P)
Vulnerable Road Users (VRUs) include pedestrians, cyclists, and drivers of motorized two-wheelers. V2P is a general term that refers to all forms of communication between VRUs and vehicles. By implementing V2P for VRUs, they will become an active member of ITS and allow a variety of safety, comfort, and functionality ITS applications. Various traffic safety systems are introduced to enhance pedestrian safety to minimize VRUs fatalities. We will discuss some of them in the following.
Wu et al. in [37] developed a V2P platform for pedestrians based on DSRC. This system employs a smartphone as a VRU device and utilizes sensors of the smartphone to maximize the delivery of safety messages. The vehicle and the VRU device both transmit safety messages containing information about their direction, location, situation, distance, and speed.
Anaya et al. in [38] introduced a system that leverages iBeacon and Bluetooth technologies to notify vehicles about the existence of cyclists. The vehicle is provided with a V2X system which is equipped with a Bluetooth interface. The iBeacon notifications sent by cyclists can be received by that Bluetooth interface.
He et al. in [39] proposed a generalized system that consists of a responsive control mechanism, a stochastic model, and generic V2P communication scenarios (that were suggested for improving pedestrian safety). The responsive control model was used to enhance the safety of pedestrians under V2P communication circumstances. The presented stochastic model formularized multiple consequences of uncertainty in a V2P communication network. The results revealed that using either wireless local area network (Wi-Fi) or Bluetooth technologies with a long installation time is insufficient for V2P communication, while DSRC satisfies the requirements and has low latencies. In conclusion, by using the presented method and the responsive control method, DSRC incorporated with Bluetooth technology will be useful for effective pedestrian safety.
Zadeh et al. in [40] suggested a new warning-based system for protecting VRUs. This new system, which can be installed on the smartphone, utilizes 4G wireless communication and GPS technology for implementation. The system includes three steps: activation, forecasting, and alert step. The zone for sending alerts is limited during the activation step. The forecasting step recognizes the danger of a crash based on effective factors such as car and pedestrian speeds, car acceleration, driver reflex time, and time of collision of the vehicle and pedestrian. A fuzzy inference algorithm is used in the alert step to categorize real situations into low, middle, and high warnings depending on the severity of threats. These alerts lead to circumstances of no danger, being cautious, and braking, respectively.
4 Discussion
According to the aforementioned methods, there are many efforts to design more efficient V2X communication approaches. In this work some of them have been discussed based on their characteristics.
V2V enables vehicles to quickly transfer and receive information and messages, resulting in a perfect “awareness” of all vehicles in the vicinity. The range of communication signals is around 300 m, and they can detect hazards that are hidden by terrain, traffic, or weather. V2I minimizes traffic congestion and maximizes the utility of established infrastructure and facilities. The data aggregated and produced by the smart infrastructure can be used to effectively predict and model the traffic flow in real-time and in the context of long-term requirements. Onboard systems can send data to a server over a cellular network by using V2N communication. Based on the obtained data, the server produces a virtual environment, processes it using some developed frameworks, and transmits it to the connected cars and vehicles. V2P includes a direct connection between VRUs and vehicles which are close together. V2P is carried out directly or through utilizing network substructure. It can make it easier to warn pedestrians about arriving vehicles and to warn vehicles about VRUs’ existence. The identified V2X scenarios and related Key Performance Indicators are summarized and shown in Table 2, which is extracted from those works that we have investigated in this paper.
5 Conclusion
VANET is an important and new research topic with innovations in the vehicle industries and wireless networks. VANET communications paradigms have a promising future in smart transportation systems. Recently, V2X paradigms have been considered by many researchers who have been trying to propose more efficient and improved algorithms for them. What V2X technology adds to the autonomous driving system is safety and efficiency, as it constructs communication between vehicles, infrastructure, etc. Some survey papers have been published in the context of V2X communication scenarios, but it is hard to find an article that covers all scenarios together. Hence with this motivation, we decided to investigate all V2X communication paradigms together in a single paper. In this work, we reviewed some of the most important algorithms about V2V, V2I, V2N, and V2P scenarios and we discussed their positive and negative points. Several applications and challenges in this area have been investigated as well. V2X technology helps us to make roads safer, increase traffic and fuel efficiency, and decrease the number of car accidents, fatalities, and injuries. Many research works have been done in these areas, particularly about V2V and V2I algorithms, but there are still a lot of things to be done.
References
Kwatirayo, S., Almhana, J., Liu, Z.: Adaptive traffic light control using VANET: a case study. In: 9th International Wireless Communications and Mobile Computing Conference (IWCMC) on Proceedings, Sardinia, Italy, pp. 752–757. IEEE (2013)
Bouk, S.H., Ahmed, S.H., Kim, D.: Vehicular content centric network (VCCN): a survey and research challenges. In: 30th Annual ACM Symposium on Applied Computing on Proceedings, Salamanca, Spain, pp. 695–700. ACM (2015)
Bouk, S.H., Ahmed, S.H., Kim, D., Song, H.: Named-data-networking-based ITS for smart cities. IEEE Commun. Mag. 55(1), 105–111 (2017)
Ferreira, M., Fernandes, R., Conceição, H., Viriyasitavat, W., Tonguz, O.K.: Self-organized traffic control. In: ACM 7th International Workshop on Vehicular Internetworking on Proceedings, pp. 85–90, Chicago, USA. ACM Digital Library (2010)
Wang, J., Shao, Y., Ge, Y., Yu, R.: A survey of vehicle to everything (v2x) testing. Sensors 19(2), 334 (2019)
Kenney, J.B.: Dedicated short-range communications (DSRC) standards in the United States. Proc. IEEE 99(7), 1162–1182 (2011)
Araniti, G., Campolo, C., Condoluci, M., Iera, A., Molinaro, A.: LTE for vehicular networking: a survey. IEEE Commun. Mag. 51(5), 148–157 (2013)
Toukabri, T., Said, A.M., Abd-Elrahman, E., Afifi, H.: Cellular Vehicular Networks (CVN): ProSe-based ITS in advanced 4G networks. In: IEEE 11th International Conference on Mobile Ad Hoc and Sensor Systems (MASS) on Proceedings, Philadelphia, USA, pp. 28–30. IEEE (2014)
Feng, Y., He, D., Niu, L., Yang, M., Guan, Y.: The overview of Chinese cooperative intelligent transportation system; vehicular communication; application layer specification and data exchange standard. In: 2nd International Conference on Information Technology and Intelligent Transportation Systems (ITITS) on Proceedings, Beijing, China, pp. 528–616. Springer (2017)
Hamida, E.B., Noura, H., Znaidi, W.: Security of cooperative intelligent transport systems: standards, threats analysis and cryptographic countermeasures. Electronics 4(3), 380–423 (2015)
Karagiannis, G., Altintas, O., Ekici, E., Heijenk, G., Jarupan, B., Lin, K., Weil, K.: Vehicular networking: a survey and tutorial on requirements, architectures, challenges, standards and solutions. IEEE Commun. Surv. Tutorials 13(4), 584–616 (2011)
Chen, S., Hu, J., Shi, Y., Zhao, L.: LTE-V: a TD-LTE-based V2X solution for future vehicular network. IEEE Internet Things J. 3(6), 997–1005 (2016)
RoselinMary, S., Maheshwari, M., Thamaraiselvan, M.: Early detection of DOS attacks in VANET using Attacked Packet Detection Algorithm (APDA). In: International Conference on Information Communication and Embedded Systems (ICICES) on Proceedings, Chennai, India, pp. 237–240. IEEE (2013)
Mejri, M.N., Ben-Othman, J., Hamdi, M.: Survey on VANET security challenges and possible cryptographic solutions. Veh. Commun. 1(2), 53–66 (2014)
Gross, J., Punyal, O., Pereira, C., Aguiar, A.: Experimental characterization and modeling of RF jamming attacks on VANETs. IEEE Trans. Veh. Technol. 64(2), 524–540 (2015)
Al-Terri, D., Otrok, H., Barada, H., Al-Qutayri, M., Al Hammadi, Y.: Cooperative based tit-for-tat strategies to retaliate against greedy behavior in VANETs. Comput. Commun. 104(15), 108–118 (2017)
Ghosal, A., Conti, M.: Security issues and challenges in V2X: A survey. Comput. Netw. 169, Article 107093 (2020)
Hasrouny, H., Samhat, A.E., Bassil, C., Laouiti, A.: VANet security challenges and solutions: a survey. Veh. Commun. 7(1), 7–20 (2017)
Anaya, J.J., Talavera, E., Jimenez, F., Zato, J.G., Gomez, N., Naranjo, J.E.: GeoNetworking based V2V mesh communications over WSN. In: 16th International IEEE Conference on Intelligent Transportation Systems (ITSC) on Proceedings, The Hague, The Netherlands, pp. 2421–2426. IEEE (2013)
Dong, E., Zhang, L.: Vehicle stability control system of emergency brake on split-mu road. In: 9th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC) on Proceedings, Hangzhou, China, pp. 252–255. IEEE (2017)
Tornell, S.M., Patra, S., Calafate, C.T., Cano, J., Manzoni, P.: A novel on-board unit to accelerate the penetration of ITS services. In: 13th IEEE Annual Consumer Communications Networking Conference (CCNC) on Proceedings, Las Vegas, USA, pp. 467–472. IEEE (2016)
Boban, M., d’Orey, P.M.: Exploring the practical limits of cooperative awareness in vehicular communications. IEEE Trans. Veh. Technol. 65(6), 3904–3916 (2016)
Ali, G.G.M.N., Noor-A-Rahim, M., Rahman, M.A., Samantha, S.K., Chong, P.H.J., Guan, Y.L.: Efficient real-time coding-assisted heterogeneous data access in vehicular networks. IEEE Internet Things J. 5(5), 3499–3512 (2018)
Ali, G.G.M.N., Noor-A-Rahim, M., Chong, P.H.J., Guan, Y.L.: Analysis and improvement of reliability through coding for safety message broadcasting in urban vehicular networks. IEEE Trans. Veh. Technol. 67(8), 6774–6787 (2018)
Azimi, S.R., Bhatia, G., Rajkumar, R., Mudalige, P.: Vehicular networks for collision avoidance at intersections. SAE Int. J. Passeng. Cars-Mech. Syst. 4(1), 406–416 (2011)
Sepulcre, M., Gozalvez, J.: Experimental evaluation of cooperative active safety applications based on V2V communications. In: 9th ACM International Workshop on Vehicular Inter-Networking. Systems, and Applications on Proceedings, Low Wood Bay Lake District, UK, pp. 13–20. ACM (2012)
Boban, M., D\(^{\prime }\)Orey P.M.: Measurement-based evaluation of cooperative awareness for V2V and V2I communication. In: IEEE Vehicular Networking Conference (VNC) on Proceedings, Paderborn, Germany pp. 1–8. IEEE (2014)
Bazzi, A., Zanella, A., Masini, B.M.: A distributed virtual traffic light algorithm exploiting short range V2V communications. Ad Hoc Netw. 49(1), 42–57 (2016)
Sepulcre, M., Gozalvez, J., Altintas, O., Kremo, H.: Context-aware heterogeneous V2I communications. In: 7th International Workshop on Reliable Networks Design and Modeling (RNDM) on Proceedings, Munich, Germany, pp. 295–300. IEEE (2015)
Wuthishuwong, C., Traechtler, A., Bruns, T.: Safe trajectory planning for autonomous intersection management by using vehicle to infrastructure communication. EURASIP J. Wirel. Commun. Netw. 2015(1), 1–12 (2015). https://doi.org/10.1186/s13638-015-0243-3
Mohammed, M., Ke, Y., Gao, J., Zhang, H., El-Basyouny, K., Qiu, T.Z: Connected vehicle V2I communication application to enhance driver awareness at signalized intersections. In: 11th International Transportation Specialty Conference (CSCE) on Proceedings, London, UK, pp. 1–12. CSCE (2016)
Gheorghiu, R.A., Minea, M.: Energy-efficient solution for vehicle prioritisation employing ZigBee V2I communications. In: International Conference on Applied and Theoretical Electricity (ICATE) on Proceedings, Craiova, Romania, pp. 1–6. IEEE (2016)
Al-qutwani, M., Wang, X.: Smart traffic lights over vehicular named data networking. Information 10(3), 83 (2019)
He, W., Yan, G., Xu, L.D.: Developing vehicular data cloud services in the IoT environment. IEEE Trans. Indus. Inform. 10(2), 1587–1595 (2014)
Pillmann, J., Sliwa, B., Schmutzler, J., Ide, C., Wietfeld, C.: Car-to-Cloud Communication Traffic Analysis Based on the Common Vehicle Information Model. In: IEEE 85th Vehicular Technology Conference (VTC) on Proceedings, Sydney, Australia, pp. 1–5. IEEE (2017)
Guldenring, J., Wietfeld, C.: Scalability analysis of context-aware multi-RAT Car-to-Cloud communication. In: IEEE 92nd Vehicular Technology Conference (VTC2) on Proceedings, Victoria, Canada, pp. 1–6. IEEE (2020)
Wu, X., et al.: Cars talk to phones: a DSRC based vehicle-pedestrian safety system. In: 80th Vehicular Technology Conference (VTC) on Proceedings, Vancouver, Canada, pp. 14–17. IEEE (2014)
Anaya, J.J., Talavera, E., Giménez, D., Gómez, N., Jiménez, F., Naranjo, J.E.: Vulnerable road users detection using V2X communications. In: 18th International Conference on Intelligent Transportation Systems on Proceedings, Las Palmas, Spain, pp. 107–112. IEEE (2015)
He, S., Li, J., Qiu, T.Z.: Vehicle-to-pedestrian communication modeling and collision avoiding method in connected vehicle environment. Transp. Res. Rec. 2621(1), 21–30 (2017)
Zadeh, R.B., Ghatee, M., Eftekhari, H.R.: Three-phases smartphone-based warning system to protect vulnerable road users under fuzzy conditions. IEEE Trans. Intell. Transp. Syst. 19(7), 2086–2098 (2018)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Farsimadan, E., Palmieri, F., Moradi, L., Conte, D., Paternoster, B. (2021). Vehicle-to-Everything (V2X) Communication Scenarios for Vehicular Ad-hoc Networking (VANET): An Overview. In: Gervasi, O., et al. Computational Science and Its Applications – ICCSA 2021. ICCSA 2021. Lecture Notes in Computer Science(), vol 12956. Springer, Cham. https://doi.org/10.1007/978-3-030-87010-2_2
Download citation
DOI: https://doi.org/10.1007/978-3-030-87010-2_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-87009-6
Online ISBN: 978-3-030-87010-2
eBook Packages: Computer ScienceComputer Science (R0)