Abstract
The Internet would be the largest one had it been a country of the world. The population and the produced and consumed data in this new country have been exponentially increasing, and the metrics with which one can measure all this growth are zettabytes, if not the yottabytes now. The issue of forgery detection on authentication and integrity and on the ownership of the data and the users grows incrementally along with this unprecedented growth of the Internet. With the advancements in hardware and software resulting in the Internet of Things (IoT), the checking against forgery will be even harder to perform since anything and everything will be interconnected as never seen before. Signing a document has always been a direct proof for belonging and authentication of the person. Thus, forgery has always been an equally likely issue to be encountered. While the journey of the signatures in the Internet era will be browsed in this chapter, the biometric signature as a complete and better-suited answer to the problem of forgery will be introduced within ironclad protection provided by a blockchain structure which is a new cybersecurity architecture in the domain of the IoT.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
11.1 The Definition and the Function of a Signature
A signature is a person’s name or a nickname handwritten by himself or by herself as a proof of intent and identity for the authorship of the contents of a document. Traditionally, the primary function of a signature has been to create a binding in between a person and a record by perpetually attaching a person’s uniquely identifiable handwritten sign as direct evidence that the document that is in part or in whole belongs to that person.
Therefore, the peculiarities of a given signature to fulfill this traditional function are that it should be authentic, unique, unforgeable, undeniable, unalterable, and not reusable and must be created in such a way that it cannot be repudiated.
The determination of the genuineness of the signature has been a problem for centuries. Even today, when a signature drawn by a person’s handwriting with the use of a pen, which in such a case is known as the wet signature, is in question in court, many measures must be taken by the forensic laboratories of law enforcement bodies to determine whether the signature is authentic or not. All the metrics and endeavors related to a wet signature are bundled together under the science of graphology.
In the history of humankind, every century has witnessed some technological advancements like that of the invention of the wheel, a clock, steam engines, electricity, and electrical motors until the twentieth century. All these technological improvements have changed societies and their lifestyles tremendously, however, without much affecting the belonging proving methodologies. The signature, produced as a handwritten wet signature for proof of belonging, has always been around for hundreds of years, that is, until the era of Information and Communication Technologies (ICTs).
The Internet, a direct result of the ICTs, has changed humankind unprecedentedly and thus very much deserved to be defined as a game-changer. Thus, the concept of a traditional handwritten wet signature has witnessed quite a few new forms that are altogether different in structure and generation than the classical one the very first time many centuries after. So, the game both for the production and forensics of signature has changed radically.
11.2 A Brief Literature Review on Digital Signatures
The digital signature is a protocol-level application of an asymmetrical cryptosystem. It is the direct result of a combination of both the hash functions and the asymmetrical encryption. In contrast to a symmetrical cryptosystem, in which there is only one key utilized for both processes of encryption and decryption, there are two separate keys involved for each operation in asymmetrical cryptosystems.
The idea belonged to Merkle [1] and Diffie and Hellman [2]. The methodology put forward by these researchers declared that the keys should be created in pairs and be utilized one by one for the processes of encryption and decryption. Moreover, in mathematical terms, it should be intractable to generate one key from the other. The encryption key which belongs to the receiver is publicly known and thus employed by anybody in the process of sending a message to that specific receiver. That way, the encryption key was renamed as the public key.
On the other hand, the legitimate receiver is the only possessor of the decryption key. Thus, as in the renaming of the encryption key, the decryption key is renamed as the secret key. Today, by this renaming convention, the cryptographic system is designated as the public key cryptography (PKC) and the related hardware and software infrastructure as the public key infrastructure (PKI).
The Institute of Electrical and Electronics Engineers (IEEE) standardized PKC as P1363-2000 [3].
While PKC is one compound of the digital signature, the hash functions are the other. A mathematical hash function of h is given as:
where h is the hash function, m is the variable length message, and H is the fixed length hash value of the message. The hash value for the message can also be termed as the message digest, as the fingerprint, or as the digital fingerprint of the message. The peculiarities of a hash function are as follows: (i) the hash value should be computed in P time for any given message of m; (ii) the hash function should be a one-way function, that is, it must be computationally intractable; and (iii) there should only be one hash value for any given message which means that the hash function should be collision-free.
Secure Hash Algorithms (SHA) have been standardized by the US National Institute for Standards and Technology (NIST), and they produce H values with 160, 256, 384, and 512 bits, respectively [4].
11.2.1 Conventional Digital Signatures
When combined with a hashing function, as mentioned above, one of the marvelous outcomes of asymmetrical cryptosystems is a digital signature. Whether one chooses either the RSA or elliptic curve or ElGamal cryptosystem as the PKC, the digital signature can be created and be added to the document after a couple of steps. The algorithm for digital signature creation is given in Table 11.1.
Currently, one can obtain a digital signature either by having the asymmetrical keys stored on a flash memory to be utilized through the USB port of a computer or having these keys on a SIM card of a mobile phone, which in that case it is called as the mobile signature. However, each of these technologies heavily underlines a hardware dependency; thus, user reluctance has always been an issue for those systems.
11.2.2 Server Signing
Nevertheless, there is one alternative way of digital signing known as the server signing, which runs with asymmetrical keys that are stored on a networked server, and the digital signature is created by that server whenever there is a demand by the signee.
Server signing is founded upon the EU regulation on “electronic identification and trust services for electronic transactions” known as eIDAS [5]. eIDAS might be considered as one of the underlying framework regulations for server signing standard CEN/TS 41924 [6]. The server signing option frees the users form hardware dependencies. However, it is not free from the complexities of the networking hardware and software.
Although a digital signature thus obtained is mathematically proven to be secure, it is nevertheless not so easy to utilize by the signees, and unfortunately, underlying computing intractabilities are susceptible to quantum computing attacks, which seems to be the new revolutionizing technological breakthrough in the days to come along with IoT.
11.3 The Biometric Signature
Biometric authentication can be done in many ways, such as retina, voice, palm, or fingerprint recognition. Along with these, behavioral biometric verification can be used very effectively. A biometric signature is a behavioral biometric recognition thatcan be done by one’s actual handwriting signature on – say – a tablet computer or on a cell phone using a digital pen (a stylus). Since a very conventional way of handwriting does it, it is of no surprise to find the fast acceptance of biometric signatures by banks, hospitals, companies, and various government departments all throughout the world, hence the ISO’s standard 19794/7, “Biometric data interchange formats-Part 7: Signature/sign time series data” on biometric signatures [7].
The popularity of biometric signatures is continuously increasing. Recently, Páez et al. proposed an architecture for a biometric electronic document identification implemented on blockchain for enhanced security measures [8]. While Delgado-Mohatar discusses blockchain technologies for storing data in biometric templates [9], Tolosana et al. discuss the biometric signature application on smartphones not with a stylus but with an actual finger touch [10]. Moreover, Bibi et al. delineate the offline and online biometric signature verification systems by taxonomical classification models [11].
The biometric signature consists of three steps that are capturing the image, extracting the signature specific features, and comparing the signature with that of the master signature recorded earlier, respectively. After capturing the handwritten signature on a tablet or a mobile phone, 20 different features on each point of the signature (usually a signature consists of 300–350 points depending on how large the signature is) are extracted for signature recognition. Here are the typical features extracted: the normalized x coordinate, the normalized y coordinate, the pressure of the pen, the altitude angle, the azimuth angle, velocity in x coordinate, velocity in y coordinate, the absolute speed, x coordinate acceleration, y coordinate acceleration, absolute acceleration, tangential acceleration, press derivation, sine of the α, cos of the α, the α-angle between the absolute α(t) velocity vector and the x axis, derivation of α angle, sine of the α′(t), cos of the α′(t), and the angle between two adjacent line segments at each coordinate [12,13,14]. Figure 11.1 depicts a captured signature image with point number 0, and Table 11.2 shows the extracted 20 features from point number 0.
Once the extraction of these 20 different features from every 300–350 points of the handwritten biometric signature is done, then this data set (20 × 350 = 7000 specific data item in total) is dynamically compared with the original master handwritten signature data of the user which was obtained earlier. The dynamic comparing process creates a threshold value. Once and if the comparison threshold value is in the acceptance interval, then the biometric signature can be accepted, hence no forgery. Figure 11.2 shows a comparison of a genuine signature against a fraud by selected features.
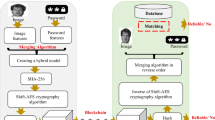
11.4 The Biometric Signature on a Blockchain
Hardware dependency has always been a significant issue for conventional digital signing. Even though server signing was kind of an answer to that unsettled question, it has not without its networking issues. On the other hand, computational intractability, which provides the security and reliability for all these asymmetrical cryptosystem protocols, is due to our current computational model.
The advancements in the science of physics and engineering make it possible that quantum computing will be in use in a decade or so. If this will be the case, the conventional asymmetrical cryptosystems will be useless. Thus, digital signing methodologies as we know them today will be pushed aside.
While handwritten signing on a touch-sensitive screen like that of a tablet and/or a mobile phone is natural, hence the frequent and rapid acceptance by the industry, the data which is composed of the signee’s signature image should still be kept under tight security. Therefore, all the information reflected as the extracted features from the points of the image must be stored along with the image of the signature itself.
The idea of utilizing the conventional cryptographic protocols to provide security for biometric data is by no means the only alternative due to the issues mentioned above.
What we propose is to have all that biometric information added to a blockchain. With a new hashing algorithm that will be developed as a quantum computing resistant, the blockchain will be one of the safest solutions to come.
As detailed in Sect. 11.3, the biometric info in the form of extracted features from all the points of the signature image provides the base for comparison. However, there must be at least five authentic signature images obtained from the signee to develop the genuine signature base with all extracted features to be kept in a blockchain. Table 11.3 shows the basic model for a blockchain.
Each block includes extracted features from all points of five genuine signatures along with client, threshold, previous hash, and timestamp info. Table 11.4 indicates the extracted features of the first point of the first signature.
All the details of a transaction must also be added to the block. Table 11.5 depicts the transaction details as kept in blockchain. Note that the latitude and longitude info along with the time info also stored in blockchain for the increased reliability of the whole transaction.
11.5 Conclusion: The Biometrix Project
The idea of storing the biometric information on blockchain was realized in a project called Biometrix. The issues in signing and the related biometric solutions along with a blockchain implementation outlined above were addressed in the Biometrix project. The detailed information concerning the application of Biometrix can be accessed in GitHub [15].
References
R.C. Merkle, Secure communications over insecure channels. Commun. ACM 21(4), 294–299 (1978)
W. Diffie, M.E. Hellman, New directions in cryptography. IEEE Trans. Inf. Theory 22(6), 644–654 (1976)
IEEE Homepage., https://standards.ieee.org/standard/1363-2000.html. last accessed 16 July 2020
Secure Hash Standard (SHA), Federal Information Processing Standards (FIPS) Publication 180–4 (2015). https://doi.org/10.6028/NIST.FIPS.180-4. August 2015
eIDAS: Regulation (EU) No 910/2014 of the European Parliament and of the Council of 23 July 2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC
EN 419241-1:2018: Trustworthy Systems Supporting Server Signing – Part 1: General System Security Requirements. 15-Jul-2018
ISO/IEC 19794/7, Biometric Data Interchange Formats-Part 7: Signature/Sign Time Series Data (2007)
R. Páez, M. Pérez, G. Ramírez, J. Montes, L. Bouvarel, An architecture for biometric electronic identification document system based on blockchain. Future Internet 12, 10 (2020)
O. Delgado-Mohatar, J. Fierrez, R. Tolosana, R. Vera-Rodriguez, Blockchain Meets Biometrics: Concepts, Application to Template Protection, and Trends (2020). https://arXiv.org/2003.09262 [cs.CV]
R. Tolosana, R. Vera-Rodriguez, R. Guest, J. Fierrez, J. Ortega-Garcia, Exploiting complexity in pen- and touch-based signature biometrics. Int. J. Doc. Anal. Recognit. (IJDAR) 23, 129–141 (2020). https://doi.org/10.1007/s10032-020-00351-3
K. Bibi, S. Naz, A. Rehman, Biometric signature authentication using machine learning techniques: Current trends, challenges, and opportunities. Multimed. Tools Appl. 79, 289–340 (2020). https://doi.org/10.1007/s11042-019-08022-0
O. Hurtada-Miguel, Online Signature Verification Algorithms and Development of Signature International Standards. Ph.D. Thesis, Universidad Carlos III de Madrid, September (2011)
T.Q. Ton, T. Pham Tung, Online signature verification using dynamic time wrapping and extended regression. Int. J. Adv. Res. Comput. Eng. Technol. (IJARCET) 4(5), 1854 (2015 May)
T. Giorgino, Computing and visualizing dynamic time warping alignments in R: The dtw package. J. Stat. Softw. 31(7), 1–24 (2009). https://doi.org/10.18637/jss.v031.i07
T. Akbaş, Biometrix- BIOMETRIX – Artificial Intelligence Assisted Biometric Signature on Block Chain (Engineering Graduation Project, Yasar University, Department of Computer Engineering, Izmir, 2020) https://github.com/taylanakbas/Biometrix
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Koltuksuz, A. (2021). The Biometric Signature as a Blockchain Application. In: Choudhury, T., Khanna, A., Toe, T.T., Khurana, M., Gia Nhu, N. (eds) Blockchain Applications in IoT Ecosystem. EAI/Springer Innovations in Communication and Computing. Springer, Cham. https://doi.org/10.1007/978-3-030-65691-1_11
Download citation
DOI: https://doi.org/10.1007/978-3-030-65691-1_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-65690-4
Online ISBN: 978-3-030-65691-1
eBook Packages: EngineeringEngineering (R0)