Abstract
Cognitive radio network concepts are used in order to solve the spectrum problem due to the fixed allocation of the channel. In this state, the secondary user (SU) is made to handoff during the arrival of primary user which offers a higher priority. The handoff scheme is processed with the help of sensing the spectrum in cognitive radio network. As a sequence, the channel which is identified through sensing is allocated for the SU. During the arrival of the primary user (PU), without interference the mobility is done by the handoff procedure. This paper suggests dynamic handoff by proposing improved PSO (iPSO) algorithm which is compared with SpecPSO algorithm for better efficiency of high throughput and data rates.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Cognitive radio networks (CRN)
- Particle swarm optimization (PSO)
- Spectrum sensing
- Spectrum handoff
- Improved PSO (iPSO)
1 Introduction
In the past, the spectrum allocation was based on the service required by the secondary user. Due to the static assignment of spectrum, there occurs a problem of inadequacy toward the spectrum allocation. So in this aspect, the cognitive radio network (CRN) has emerged a new trend in wireless communication to isolate the white spaces (spectrum hole) which are not accessible by the licensed user. The known white space is allocated for the secondary user to transmit the data smoothly without any interruption [1]. CRN works on the progress of cognitive radio cycle, namely [2, 3]:
-
Spectrum sensing: Senses the vacant space in the spectrum.
-
Spectrum sharing: The licensed channel is shared by the SU.
-
Spectrum decision: The sensed channel is selected for transmission by the SU.
-
Spectrum handoff: During the arrival of the PU, the SU has to identify the free channel and vacate.
The dynamic spectrum access (DSA) is used for reusing the spectrum in opportunistic manner by the secondary user, and its efficiency gets improved without the interference of the primary user [4]. In this aspect, to sense the channels, various methods of topologies and usage amount of spectrum utilizations by the secondary users are done effectively with the help of DSA [5]. The utilization of spectrum for the secondary user is allocated based on the concept of dynamic spectrum access using swarm-based algorithm [6].
2 Literature Review
2.1 Cognitive Radio Network
CRN is an intelligent network used to detect the channels which are currently active or inactive in the spectrum. This network is used to sense the white space available in the spectrum and allocates that identified space for the unlicensed user (i.e., secondary user) [7]. One method used to solve the problem of scarcity in cognitive radio network is spectrum handoff. It is applied during the arrival of primary user for accessing its licensed channel. When it occurs, the handoff operation is required for the secondary user to swift from corresponding channel to the next white space channel [8].
2.1.1 Components of Cognitive Radio Networks
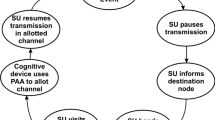
The two leading components of cognitive radio network are the authorized user and unauthorized user. The authorized user is denoted as the primary user who is fully qualified for accessing the channel, and the unauthorized user is called the secondary user or cognitive user who can access only during the absences of the primary user. The CR network is divided into three categories:
-
Interleave networks: Once the white or spectrum hole is identified, the SU will start activating its transmission till the arrival of the PU.
-
Underlay network: The PU and SU will work simultaneously in the same spectrum slot with different frequency bandwidths.
-
Overlay network: The PU and SU will work concurrently with interference. The PU will send the message before transmitting the data, and similarly the SU also performs the same before transmission.
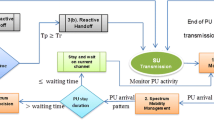
The primary user and secondary user in cognitive radio network are illustrated in Fig. 1.
2.2 Dynamic Spectrum Access
The assignment of frequency bandwidth in dynamic spectrum access is built on dynamic process instead of static. It is a main source to solve the hypothetic problem that occurs during the handoff by the secondary user. This dynamic spectrum access is used to share the channel for both the PU and SU without any interference [9]. It senses the readiness of white space in spectrum and allocates the free channel for the SU without interrupting the service during the appearance of the PU [10].
2.3 Spectrum Sensing
Sensing the white space in cognitive radio network is accomplished by spectrum sensing with the support of various techniques such as narrow band sensing and wide band sensing. The issues and challenge faced by the spectrum sensing are as follows [11]:
-
(a)
Channel uncertainty: The presence of PU is wrongly interpreted due to the delay, energy detection, and performance of the channel utilization.
-
(b)
Interference temperature measurement: The transmission data, time, and the bandwidth level is known by the SU, but the arrival of PU is not known.
-
(c)
Error prone channel: Since the SU is moving on to the accessible free channel when PU comes, there may occur erroneous channel detection.
-
(d)
Mobility: Often changing the channel by SU is a big issue.
2.4 Spectrum Handoff
The spectrum handoff is mainly used to perform the secondary user work efficiently without any interference of the primary user. In order to moderate the loss of information and throughput and to increase the signal to noise interference (SINR), the spectrum handoff is used [12].
Two types of spectrum handoff:
-
1.
Soft handoff: Interchangeability with the same frequency bandwidth
-
2.
Hard handoff: Interchangeability with different frequency bandwidths.
Techniques in spectrum handoff:
-
1.
Pure reactive handoff: Getting prior request to access the channel.
-
2.
Pure proactive handoff: The PU arrival is determined and acted upon.
-
3.
Hybrid handoff: Mixture of both pure reactive and proactive handoff.
3 Methodology
3.1 Proposed Algorithm
3.1.1 Improved PSO Algorithm
The local minima and premature convergence are the two main drawbacks that arise in spectrum particle swarm optimization (SpecPSO). To overcome the problem of SpecPSO, this proposed algorithm was suggested. The two parameters were used in order to enhance the efficiency of throughput and data transmission. One parameter is inertia weight and the other is learning factor. The chaotic optimization is used for initializing the parameter [13].
3.1.2 Chaotic Optimization
The large range of population is generated from this chaotic optimization. Using this, the global best and the local best value is identified with perfectly [14].
The following steps are architectural flow of the proposed algorithm which is shown in Fig. 2:
-
The spectrum hole is identified by spectrum sensing.
-
The primary user and the secondary user are initialized.
-
Spectrum mobility is done when the PU is in need of the channel used by the SU.
-
The channel identification takes place with the help of iPSO efficiently.
-
For smooth transmission, the next channel is traced quickly for the SU to work.
Figure 3 demonstrates the implementation of swarm-based optimization by using the parameters which is calculated as follows:
-
Step 1: Consider the number of population, particles, and parameters are to be initialized.
-
Step 2: The present iteration with the previous iteration is compared and calculated for considering the value of pbest. The objective function value which is low is treated as pbest as in Eq. (1):
$$ {\mathrm{pbest}}_{d+1}=\left\{\begin{array}{ll}{\mathrm{pbest}}_d& \mathrm{if}\kern0.5em {f}_{d+1}\ge {f}_d\\ {}{x}_{d+1}& \mathrm{if}\kern0.5em {f}_{d+1}\le {f}_d\end{array}\right. $$(1)Here k is treated for iteration value and f is function of the objective value.
-
Step 3: The gbest value is calculated by comparing with pbest value, and the minimum rate is gbest as in Eq. (4):
$$ {\mathrm{gbest}}_{d+1}=\left\{\begin{array}{ll}{\mathrm{gbest}}_d& \mathrm{if}\kern0.5em {f}_{d+1}\ge {f}_d\\ {}{\mathrm{pbest}}_{d+1}& \mathrm{if}\kern0.5em {f}_{d+1}\le {f}_d\end{array}\right. $$(2) -
Step 4: The next iteration should be modified with the velocity updation, after the calculation of the pbest and gbest by using Eqs. (3)–(5):
$$ {v}_{d+1}={v}_{d}+w\ast {v}_d+{c}_1\ast {r}_1\left(\mathrm{pbest}-{x}_d\right)+{c}_2\ast {r}_2\left(\mathrm{gbest}-{x}_d\right) $$(3)$$ {x}_{d+1}={x}_d+{v}_{d+1} \vspace*{-24pt} $$(4)$$ \omega ={\omega}_{\mathrm{maximum}}-\frac{\omega_{\mathrm{maximum}}-{\omega}_{\mathrm{minimum}}}{i_{\mathrm{maximum}}}\ast i $$(5)where i represents iteration and ω is inertia weight which is used to identify the best global best value.
-
Step 5: If i values with maximum no of iteration is performed then, move on to step 6 else step 2.
-
Step 6: Optimal solution for each and every individual population is generated to find the new global best.
4 Simulation and Result
The simulation work is done through MATLAB R2014a with the configuration of 4 GB RAM. The initial population size is 50; the assumed user is 20, and channel size considered for execution is 200. The frequency bandwidth of each and every channel is 30 kHz. The data transfer rate is 256 kbits.
The results are compared with genetic algorithm, specPSO, and iPSO. The best optimal solution is found with minimal iteration. The data transfer rate is high when compared with other evolutionary algorithms such as GA and specPSO. The total simulation time is faster in identifying the white space, in order to perform mobility during the PU’s arrival. This representation is shown in Figs. 4 and 5, respectively.
5 Conclusion
This proposed work focuses on the improvement of channel utilization for SU in order to progress its activity without any interruption. It also identifies the unused channel where the PU is not accessing it for transmission. It provides a high data transfer with limited iteration. Thus iPSO algorithm concentrates on good network communication for transmitting the data and also performs handoff during the arrival of the PU in an efficient manner. The future work focuses on handoff optimization in cognitive radio network using BPSO and iPSO techniques.
References
Ali A, Abbas L, Shafiq M, Bashir AK, Afzal MK, Liaqat HB, Siddiqi MH, Kwak KS (2018) Hybrid fuzzy logic scheme for efficient channel utilization in cognitive radio networks. IEEE Access 7:24463–24476
Koroupi F, Talebi S, Salehinejad H (2012) Cognitive radio networks spectrum allocation: an ACS perspective. Sci Iran 19:767–773
Kumar K, Prakash A, Tripathi R (2016) Spectrum handoff in cognitive radio networks: a classification and comprehensive survey. J Netw Comput Appl 61:161–188
Bhardwaj P, Panwar A, Ozdemir O, Masazade E, Kasperovich I, Drozd AL, Mohan CK, Varshney PK (2016) Enhanced dynamic spectrum access in multiband cognitive radio networks via optimized resource allocation. IEEE Trans Wirel Commun 15:8093–8106. https://doi.org/10.1109/TWC.2016.2612627
Khalid W, Yu H (2018) Sum utilization of spectrum with spectrum handoff and imperfect sensing in interweave multi-channel cognitive radio networks. Sustainability 10:1764. https://doi.org/10.3390/su10061764. www.mdpi.com/journal/sustainability
Kalpana Devi M, Umamaheswari K (2019) Intelligent process of spectrum handoff for dynamic spectrum access in cognitive radio network using swarm intelligence. Int J computers and applications, Taylor & Francis, pp. 1–9. https://doi.org/10.1080/1206212X.2019.1704483
Feng C, Wang W, Jiang X (2012) Cognitive learning-based spectrum handoff for cognitive radio network. Int J Comput Commun Eng 1:1–4
Lala NA, Balkhi AA, Mir GM (2017) Spectrum handoff in cognitive radio networks: a survey. Orient J Comput Sci Technol 10:765–772
Liu X, Zhang W (2011) A novel dynamic spectrum access strategy applied to cognitive radio network. In: 7th International conference on wireless communications networking and mobile computing (WiCOM), pp 1–5
Awoyemi BS, Maharaj BTJ, Alfa AS (2016) Solving resource allocation problems in cognitive radio networks: a survey. EURASIP J Wirel Commun Netw 2016:176–183. https://doi.org/10.1186/s13638-016-0673-6
Yucek T, Arslan H (2009) A survey of spectrum sensing algorithms for cognitive radio applications. IEEE Commun Surv Tutorials 11:116–130. https://doi.org/10.1109/SURV.2009.090109
Yawada PS, Dong MT (2019) Intelligent process of spectrum handoff/mobility in cognitive radio networks. J Electr Comput Eng 2019:1–12. https://doi.org/10.1155/2019/7692630
Jiang Y, Hu T, Huang CC, Wu X (2007) An improved particle swarm optimization algorithm. Appl Math Comput 193:231–239. https://doi.org/10.1016/j.amc.2007.03.047
Prema Kumar N, Mercy Rosalina K (2015) IPSO algorithm for maximization of system loadability, voltage stability and loss minimisation by optimal DG placement. Int J Innov Res Electr Electron Instrum Control Eng 3:73–77. https://doi.org/10.17148/IJIREEICE.2015.31115
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 The Editor(s) (if applicable) and The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Kalpana Devi, M., Umamaheswari, K. (2021). Dynamic Spectrum Access for Spectrum Handoff in Cognitive Radio Networks Using Optimization Techniques. In: Haldorai, A., Ramu, A., Mohanram, S., Chen, MY. (eds) 2nd EAI International Conference on Big Data Innovation for Sustainable Cognitive Computing. EAI/Springer Innovations in Communication and Computing. Springer, Cham. https://doi.org/10.1007/978-3-030-47560-4_25
Download citation
DOI: https://doi.org/10.1007/978-3-030-47560-4_25
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-47559-8
Online ISBN: 978-3-030-47560-4
eBook Packages: EngineeringEngineering (R0)