Abstract
Failure Mode and Effect Analysis (FMEA) is a widely used risk assessment approach for identification, quantification, and mitigation of potential failures in systems, products, processes, designs, and projects. Previous research efforts have focused on FMEA of Horizontal Axis Wind Turbines (HAWT)s, but there is a lack of application of FMEA for the failure analysis of Vertical Axis Wind Turbines (VAWT)s. This paper aims at the enhancement of reliability of VAWTs by applying system FMEA augmented with Fuzzy Logic (FL), and Dempster-Shafer (D-S) theory. A total of 12 probable failure modes have been identified, quantified and prioritized. The application of Fuzzy-FMEA and DS-FMEA approach based on three experts’ opinions accommodates the diversity of opinions and accounts for the uncertainty in decision making, due to any lack of knowledge and experience of the FMEA team.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Risk management is a mandatory requirement based on ISO 31000:2009, which provides the generic guidelines and frameworks to risk management processes. Using ISO 31000:3009 is beneficial to effectively achieve organizational objectives and utilize resources for risk treatment by identifying opportunities and threats. Failure Mode and Effect Analysis (FMEA) is an established risk management approach that prevents probable failures in the system and provides the foundation for policies and remedial measures to tackle them. FMEA was first employed in the 1960s in aerospace companies as a risk management tool during the designing phase, and afterward, this method is being used in other sectors such as automotive industry (Sharma et al. 2007). FMEA can distinguish all failure modes, while the members of the FMEA team by utilizing risk factors evaluation information, rank the risks of all distinguished failure modes in importance arrangement (Chen and Deng 2018). Previous studies on FMEA of wind turbines have focused on the components, systems, subsystems, and functional modes of Horizontal Axis Wind Turbines (HAWT)s. (Bharatbhai 2015), (Kahrobaee and Asgarpoor 2011), (Tavner et al. 2010) and (Arabian-Hoseynabadi et al. 2010) applied FMEA to investigate the failure of 5 MW, 3 MW, 2 MW and 2 MW HAWTs respectively. In this study, a risk assessment methodology based on FMEA is proposed for analyzing the reliability of VAWTs that have lesser number of system components. The probable failure modes are identified and quantified. Risk priority number (RPN) is used for prioritizing the risk of each failure mode by order.
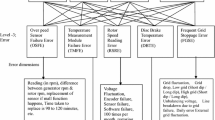
FMEA studies begin with the known, and potential failure modes at a certain level then explore its impact on the level of the sub-system. Thus this approach is bottom-up design. Moreover, a full FMEA study covers all the hierarchy levels from its bottom to the top. System Breakdown Structure of a Vertical Axis Wind Turbine is presented in Fig. 1. Ultrasonic testing, oil tracking and many other online techniques for condition monitoring as well as visual inspection are used for failure modes detection, and time-based preventive maintenance actions. Usually, a multi-disciplinary team composed of experts from different majors such as power production, operation maintenance, and design, determine the ultimate effects of each failure mode. The basic RPN is not enough when various specialists give diverse evaluations of risks to a single failure mode, which might be uncertain and imprecise. (Dinmohammadi and Shafiee 2013) applied FMEA theory on offshore WT systems using grey theory approach and fuzzy rule base. Many researchers have reported the advantages of Fuzzy based FMEA when the failure data are unreliable or unavailable and how it is a useful tool for combing the quantitative and qualitative knowledge based on field data, and experts’ opinion.
In this study, the Dempster-Shafer theory is implemented to aggregate the diversity of opinions and evaluations given by several experts, risk factors and failure modes, as the results have been compared with the results obtained by Fuzzy Logic method. The proposed FMEA process is introduced with an explanation of the DS theory and fuzzy logic. The risk prioritization by application of two FMEA approaches (DS FMEA and Fuzzy FMEA) to VAWT, is presented, followed by a comparison of both approaches.
2 Methodology
2.1 FMEA Process
In the FMEA process, the main objective is to identify the critical components of the system. In other words, the aim of FMEA is (1) to recognize the failure modes occurring during a definite period of system, (2) to determine the reasons for any failure occurrence, (3) to evaluate the effects of each failure, and (4) to prioritize the failures (Sharma et al. 2005).
The proposed Fuzzy-FMEA and DS-FMEA methodology are shown in Fig. 2.
An FMEA procedure is carried out in three fundamental steps:
-
Step 1: By dividing the system into subsystems and components, the main modules are categorized in a bottom-up diagram, and upon the occurrence of any failure in any component, the effect chain is traceable at higher levels.
-
Step 2: FMEA method is evaluable both qualitatively and quantitatively.
By considering three parameters, i.e., Severity (S), Occurrence (O), and Detection (D), and allocating a number between 1 and 10, Risk Priority Number (RPN) is calculated according to Eq. (1). (Mariajayaprakash and Senthilvelan 2013; Šolc 2012; Su et al. 2014).
The rating criteria for FMEA risk factors are listed in Table 1. RPN shows the amount of potential risk in the observed failure modes of the system. The key parameter of basic FMEA approach is allocation of a number between 1 and 10 to every risk factor of the failure mode, and categorizing them so that the more critical is the failure, the higher is the allocated number, and the more periodic inspection of the related component is required.
Allocation of numbers in RPN method is accomplished by specialists who are experts in system functions and the impact of any failure, so two factors, i.e., the experience and knowledge of specialists are effective on the final results. Therefore, an improved parameter called Weighted RPN is utilized. The weighting is based on the following coefficients given to the obtained RPN: out of the question (1), very confident (0.9), confident (0.7), less confident (0.25), and not confident (0.1). By considering experience and knowledge in the final results, the RPN value will be a qualitative evaluation, and the numbers are just comparative in rating the critical parts of the system.
Due to numerous criticisms against the RPN method, it has not been considered as an ideal approach and has been replaced by alternative methods in FMEA. (Meng Tay and Peng Lim 2006; Puente et al. 2002; Ravi Sankar and Prabhu 2001) The most serious criticism is:
-
Distinctive combinations of O, S, and D evaluations may create a similar estimation of RPN, yet their concealed risk basis might diverse completely. For instance, two distinctive failure modes with the estimations of 5, 7, 2 and 10, 1, 7 for O, S, and D, individually, will have an identical RPN estimation of 70. In any case, the concealed risk basis of the two failure modes might be completely different as a result of the diverse severities of the failure result. Therefore, this may cause the incidence of high-risk failure modes without being detected.
2.2 Dempster-Shafer Theory
Nowadays, in technical risk management and in its relative areas there are many approaches to contend with quantifying uncertainties and modelling by implementing Dempster Shafer Theory (Ji and Marefat 2003; Kukulies and Schmitt 2017; Shi et al. 2017; Zhang and Chen 2009), As the combination rule of Dempster is widely known as associative and commutative (Dempster 1967; Shafer 1976). As a result of these characteristics, evidence may be fused in any sequence, for example in the presence of different belief structures; a pair-wise combination may be executed (Certa et al. 2017). This theory is established on two models, finding a degree of beliefs for individual probability assessment and merging those above within a probabilistic framework (Chen and Deng 2018). For describing the uncertainty set in the hypothesis, the belief interval is adopted by the DS theory. Furthermore, when uncertainty, impreciseness, and incompleteness occur in the information set from several sources, this strategy is suitable to solve it.
(Yang et al. 2011) transformed the new combination rule of DS theory as
While \( \Theta _{\text{i}}^{\text{n}} \) is utilized to show the discernment frame of the nth failure mode to the ith risk factor, \( \upomega_{\text{ij}} \) is the relative weight, i represents the risk factor and j for the experts (Yang et al. 2011). By taking the weight into account, \( \overline{\text{m}}_{\text{ij}}^{\text{n}} \)(.) can represent the new Basic belief assignment, Where, i = O, S, D, j = 1, 2,…, L, L is the number of experts, n = 1, 2, …, N, N is the number of failure modes.
The combination rule can include not only two experts, as clearly revealed in Eq. (2). For all evidence sources, the synthetic effects are represented by the final result.
2.2.1 Risk Priority Number
Assume the Risk priority number has different ratings \( ({\text{RPN}}_{\text{n}}^{1} , \ldots ,{\text{RPN}}_{\text{n}}^{\text{q}} ) \) and specific probabilities \( {\text{P}}({\text{RPN}}_{\text{n}}^{1} , \ldots ,{\text{RPN}}_{\text{n}}^{\text{q}} ) \) for nth failure mode based on Eq. (2). The mean value of risk priority number is required for combining the total risk of each failure mode, as shown in Eq. (4) (Yang et al. 2011).
2.3 Fuzzy FMEA
The fuzzy approach can convert the capabilities of decision making and the fuzziness of the experts’ evaluation of mathematical terms. Hence it is convenient for failure modes ranking by utilizing fuzzy rules (Wang et al. 2018). Fuzzy approach has various advantages (Bozdag et al. 2015) such as: it can handle both precise and imprecise information in a consistent manner, it allows combination of probability of failures occurrence, severity, and detectability in a more pragmatic manner (R. K. Sharma et al. 2005) and the risk assessment function can be varied according to the specific system under consideration (Liu et al. 2013).
However, a membership function (MF) is a curve that describes how every point in the input space is associated with a membership value somewhere from 0 to 1 and often gives the designation of µ. The input space is also known as the universe of discourse (UOD). The output-axis is a number known as the membership value between 0 and 1.
A fuzzy set is an expansion of a classical set. Assume X is the universe of discourse, and its elements are represented by x. Subsequently, a fuzzy set A in X is described as a set of ordered pairs.
µA(x) is known as the membership function (or MF) of x in A. The membership function associates every element of X to a membership value from 0 to 1.
The if-then rule statements are employed for formulating the conditional statements that form fuzzy logic. A single fuzzy if-then rule typically is from the concept; if x is A then y is B; where, A and B are semantic values defined by fuzzy sets on the ranges X and Y, respectively. The if part of the rule “x is A” is known as the antecedent, whereas the then-part of the rule “y is B” is known as the consequent. The consequent is described by a number from 0 to 1, and the antecedent is an analysis that results in a number from 0 to 1 as well.
Conventionally, the input to an if-then rule is the present value for the input variable, and the output is a whole fuzzy set. Subsequently, the set is defuzzified; that is, allotting just one value to the output in the end. Interpreting an if-then rule comprises different parts. Firstly, the evaluation of the antecedent is performed (which involves input fuzzifying and employing suitable fuzzy operators). Secondly, the outcome obtained from the first part is applied to the consequent.
The Fuzzy RPN (based on 10 membership functions) is derived from the “if-then” rules, and it is determined based on the integer numbers allocated to S, O, and D (from 1 to 10) as well as on the steps of fuzzy logic control (Shaout and Trivedi 2013).
Step 1- Based on the combination of S (as input 1 in step 1) and O (as input 2 in step 1) values (each risk factor from 1 to 10), and according to the rules in Table 1 a fuzzy number is exploited (Shaout and Trivedi 2013). This step is as the first stage of multi-stage fuzzy architecture. The generated surface of the logic controller is shown in Fig. 3 (Jang 1993; Jang et al. 1997; Kaufmann and Gupta 1985; Lee 1990; Puente et al. 2002).
Step 2- The rules utilized in this step are the same as the previous step, and just input parameters will be the detection value of failure mode (as input 2 in step 2) and the output number of step 1 (as input 1 in step 2) (Mamdani 1976; Wang et al. 2009). This step is the second stage of the multi-stage structure, and as far as the rules have been kept the same as step 1, the generated surface will not display any change.
3 Results
The failure modes of VAWT are identified from (Arabian-Hoseynabadi et al. 2010), (Bharatbhai 2015), (Dinmohammadi and Shafiee 2013), (Kahrobaee and Asgarpoor 2011), (Tavner et al. 2010), and (Klein and Lalli 1989). For each failure mode, values of risk factors and the amounts of DS-RPN, and Fuzzy RPN (based on 10 membership functions) are provided. The values are obtained from survey responses from three specialists who are experts in VAWT. The proposed technique is applied to failure modes and effects analysis case of VAWTs, all three risk factors, and the failure modes were evaluated by three experts exhibiting diversity in their evaluations. In Table 2, all evaluations are listed regarding 12 components.
As shown in Table 2, the most critical failures of the system are gearbox, blades, and generator, which obtained the highest ranking numbers (between 1st to 2nd rankings at each approach). Also, the trend of scored numbers in analysis of each implemented approach is very similar, and it shows the same risk importance for the recognized failure modes of the system.
4 Discussion
By application of Dempster-Shafer theory and Fuzzy logic, the accuracy of results was increased, and aggregation of team members’ opinions had the same effect at an elevation of precision in final findings.
Concerning fuzzy logic and Dempster Shafer theory, the risk priority number rank of all 12 components is demonstrated in Figs. 4 and 5. Although both ranks showed the highest importance for the gearbox, there was a difference in the prioritization of several components, such as blades and generator, the fuzzy logic prioritized the generator over blades, but DS showed the opposite. In such uncertainty, these components should be treated similarly. The results are consistent with the practical engineering background and other similar research on failure analysis of wind turbines (Certa et al. 2017; Wang et al. 2018) thereby, demonstrating the efficiency and effectiveness of the DS-FMEA and Fuzzy-FMEA.
5 Conclusion
In this research, the System Failure Mode and Effect Analysis (FMEA) approach based on Dempster Shafer evidence theory (DS-RPN), Fuzzy RPN (based on 10 membership functions), is applied for failures prioritization of Vertical Axis Wind Turbine (VAWT). The application of Fuzzy-FMEA and DS-FMEA approach based on three experts’ opinions accommodates the diversity of opinions and accounts for the uncertainty in decision making, due to any lack of knowledge and experience of the FMEA team. D–S evidence theory is adapted to aggregate the risk evaluation information of multiple experts, which may be uncertain, imprecise, and inconsistent. Meanwhile, the uncertainty is reduced, and the accuracy is improved by increasing the number of fuzzy rules of FMEA team members’ opinions. Failure modes ranking is obtained based on Mean Value RPN. Different evaluation information given by three experts on 12 components is aggregated, and the mean value RPN is attained based on Dempster-Shafer evidence theory and fuzzy logic. The most critical system failures are gearbox, blades and generator, which obtained the highest ranking numbers. However, the DSFMEA and Fuzzy FMEA have the potential to improve the reliability of VAWT.
References
Arabian-Hoseynabadi H, Oraee H, Tavner PJ (2010) Failure modes and effects analysis (FMEA) for wind turbines. Int J Electr Power Energy Syst 32:817–824
Bharatbhai MG (2015) Failure mode and effect analysis of repower 5 M wind turbine. Int J Adv Res Eng Sci Technol 2(5):2394–2444
Bozdag E, Asan U, Soyer A, Serdarasan S (2015) Risk prioritization in Failure Mode and Effects Analysis using interval type-2 fuzzy sets. Expert Syst Appl 42(8):4000–4015
Certa A, Hopps F, Inghilleri R, La Fata CM (2017) A Dempster-Shafer Theory-based approach to the Failure Mode, Effects and Criticality Analysis (FMECA) under epistemic uncertainty: application to the propulsion system of a fishing vessel. Reliab Eng Syst Saf. 159:69–79. https://doi.org/10.1016/j.ress.2016.10.018
Chang D-S, Paul Sun K-L (2009) Applying DEA to enhance assessment capability of FMEA. Int J Qual Reliab Manag 26(6):629–643
Chen L, Deng Y (2018) A new failure mode and effects analysis model using Dempster-Shafer evidence theory and grey relational projection method. Eng Appl Artif Intell 76:13–20. https://doi.org/10.1016/j.engappai.2018.08.010
Chin K-S, Wang Y-M, Poon GKK, Yang J-B (2009) Failure mode and effects analysis using a group-based evidential reasoning approach. Comput Oper Res 36(6):1768–1779
Dempster AP (1967) Upper and lower probabilities induced by a multivalued mapping. Ann. Math. Statist. 38(2):325–339. https://doi.org/10.1214/aoms/1177698950
Dinmohammadi F, Shafiee M (2013) A fuzzy-FMEA risk assessment approach for offshore wind turbines. Int J Prognostics Health Manag
Jang J-S (1993) ANFIS: adaptive-network-based fuzzy inference system. IEEE Trans Syst Man Cybern 23(3):665–685
Jang J-SR, Sun C-T, Mizutani E (1997) Neuro-fuzzy and soft computing; a computational approach to learning and machine intelligence. IEEE Trans Autom Control 42:1482–1484
Ji Q, Marefat MM (2003) A Dempster-Shafer approach for recognizing machine features from CAD models. Pattern Recogn 36(6):1355–1368. https://doi.org/10.1016/s0031-3203(02)00260-1
Kahrobaee S, Asgarpoor S (2011). Risk-based failure mode and effect analysis for wind turbines (RB-FMEA). 1–7. https://doi.org/10.1109/naps.2011.6025116
Kaufmann A, Gupta M (1985) Introduction to fuzzy arithmetic. Van Nostrand Reinhold, New York
Klein WE, Lalli VR (1989) Model 0A wind turbine generator FMEA
Kukulies J, Schmitt R (2017) Stabilizing production ramp-up by modeling uncertainty for product design verification using Dempster-Shafer theory. CIRP J Manufact Sci Technol. https://doi.org/10.1016/j.cirpj.2017.09.008
Lee C-C (1990) Fuzzy logic in control systems: fuzzy logic controller I. IEEE Trans Syst Man Cybern 20(2):404–418
Liu H-C, Liu L, Liu N (2013) Risk evaluation approaches in failure mode and effects analysis: a literature review. Expert Syst Appl 40(2):828–838
Liu H-C, Liu L, Liu N, Mao L-X (2012) Risk evaluation in failure mode and effects analysis with extended VIKOR method under fuzzy environment. Expert Syst Appl 39(17):12926–12934
Mamdani EH (1976) Application of fuzzy logic to approximate reasoning using linguistic synthesis. Paper presented at the proceedings of the sixth international symposium on Multiple-valued logic
Mariajayaprakash A, Senthilvelan T (2013) Failure detection and optimization of sugar mill boiler using FMEA and Taguchi method. Eng Fail Anal 30:17–26
Meng Tay K, Peng Lim C (2006) Fuzzy FMEA with a guided rules reduction system for prioritization of failures. Int J Qual Reliab Manag 23(8):1047–1066
Puente J, Pino R, Priore P, de la Fuente D (2002) A decision support system for applying failure mode and effects analysis. Int J Qual Reliab Manag 19(2):137–150
Ravi Sankar N, Prabhu BS (2001) Modified approach for prioritization of failures in a system failure mode and effects analysis. Int J Qual Reliab Manag 18(3):324–336
Shafer G (1976) A mathematical theory of evidence, vol 42. Princeton University Press, Princeton
Shaout A, Trivedi J (2013) Performance appraisal system–using a multistage fuzzy architecture. Int J Comput Inf Technol 02:405–411 (ISSN: 2279–0764)
Sharma R, Kumar D, Kumar P (2007) Fuzzy decision support system (FDSS) for conducting FMEA. J-Inst Eng India Part Me Mech Eng Div 88(T):39
Sharma RK, Kumar D, Kumar P (2005) Systematic failure mode effect analysis (FMEA) using fuzzy linguistic modelling. Int J Qual Reliab Manag 22(9):986–1004
Shi Y, Zhang Z, Wang K (2017) A Dempster Shafer theory and fuzzy-based integrated framework for supply chain risk assessment 731:347–361. https://doi.org/10.1007/978-3-319-62698-7_29
Šolc M (2012) Applying of method FMEA (Failure Mode and Effects Analysis) in the logistics process. Adv Res Sci Areas 1(1):1906–1911
Su C-T, Lin H-C, Teng P-W, Yang T (2014) Improving the reliability of electronic paper display using FMEA and Taguchi methods: a case study. Microelectron Reliab 54(6–7):1369–1377
Tavner P, Higgins A, Arabian H, Long H, Feng Y (2010) Using an FMEA method to compare prospective wind turbine design reliabilities. Paper presented at the European wind energy conference and exhibition 2010, EWEC 2010
Wang Y-M, Chin K-S, Poon GKK, Yang J-B (2009) Risk evaluation in failure mode and effects analysis using fuzzy weighted geometric mean. Expert Syst Appl 36(2):1195–1207
Wang Z, Gao J-M, Wang R-X, Chen K, Gao Z-Y, Jiang Y (2018) Failure mode and effects analysis using Dempster-Shafer theory and TOPSIS method: application to the gas insulated metal enclosed transmission line (GIL). Appl Soft Comput 70:633–647. https://doi.org/10.1016/j.asoc.2018.06.015
Xu K, Tang LC, Xie M, Ho SL, Zhu M (2002) Fuzzy assessment of FMEA for engine systems. Reliab Eng Syst Saf 75(1):17–29
Yang J, Huang H-Z, He L-P, Zhu S-P, Wen D (2011) Risk evaluation in failure mode and effects analysis of aircraft turbine rotor blades using Dempster-Shafer evidence theory under uncertainty. Eng Fail Anal 18(8):2084–2092. https://doi.org/10.1016/j.engfailanal.2011.06.014
Zhang R, Chen R (2009) The Dempster-Shafer synthesis rule for service supplier selection. Paper presented at the 2009 16th international conference on industrial engineering and engineering management
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Alhijazi, M., Zeeshan, Q., Ghasemian, H. (2020). Failure Mode and Effect Analysis (FMEA) of Vertical Axis Wind Turbines. In: Calisir, F., Korhan, O. (eds) Industrial Engineering in the Digital Disruption Era. GJCIE 2019. Lecture Notes in Management and Industrial Engineering. Springer, Cham. https://doi.org/10.1007/978-3-030-42416-9_6
Download citation
DOI: https://doi.org/10.1007/978-3-030-42416-9_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-42415-2
Online ISBN: 978-3-030-42416-9
eBook Packages: EngineeringEngineering (R0)