Abstract
As the number of mobile devices increases and new networks technologies emerge, radio spectrum is becoming a rare resource. This stands as the major problem in the development of modern wireless technologies. In recent years, several methods and technologies were implemented to solve this problem, for example the licensed assisted-access (LAA) and the licensed shared access (LSA) frameworks allowing to use more efficiently the available radio resources. At the same time, radio resource management (RRM) researches showed that mechanisms (i.e. downlink power reduction, user service interruption) using efficiently the radio spectrum can also be applied. In this paper, we aim to propose different methods for the analysis of possible admission control scheme models to access the radio resources of a wireless network with the implementation of downlink power policy and user service interruption mechanisms. Such models could be described by a queuing system with unreliable servers within a random environment (RE).
The publication has been prepared with the support of the “RUDN University Program 5-100” (Gudkova I.A., mathematical model development). The reported study was funded by RFBR, project number 18-37-00231 and 18-00-01555(18-00-01685) (Markova E.V., numerical analysis). This article is based as well upon support of international mobility project MeMoV, No. CZ.02.2.69/0.0/0.0/16_027/00083710 funded by European Union, Ministry of Education, Youth and Sports, Czech Republic and Brno University of Technology.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Wireless network
- Radio resource management
- Limit power policy
- Service interruption
- Queuing system
- Random environment
- Recursive algorithm
- Approximate method
1 Introduction
The recent years have seen a rapid growth in modern cellular networks traffic, contributed by billions of mobile devices and brand new technologies [1, 2]. This growth of traffic affects the availability of radio resource necessary for serving users with the required level of quality of service (QoS) [3, 4]. The main technologies developed to solve this problem are orthogonal frequency division multiple access (OFDM) [5, 6], multiple input multiple output (MIMO) [7,8,9], multimedia broadcast multicast service (MBMS) [10], licensed assisted-access framework (LAA) [11] and licensed shared access framework (LSA) [12, 13]. Within these technologies, researchers propose different radio resource management (RRM) mechanisms, for example transmission power limitation [14, 15] and user service interruption [16], that allow using more efficiently available radio spectrum. Models implementing such mechanisms could be described by a queuing system model with unreliable servers [17]. One type of these systems are systems operating in a random environment [18, 19].
Random environment (RE) is a significant obstacle to the efficient diffusion and use of telecommunication systems. It can strongly affect the system performance measures, for example the blocking probability and the achievable bit rate.
The aim of this paper is to propose methods for analyzing performance measures of one of the possible admission control schemes models for wireless network, described by a queuing system with unreliable servers within a RE.
The rest of the paper is organized as follows. In Sect. 2, we propose a general description of the model operating in RE, state of which can vary. In Sect. 3, we propose an accurate method to calculate the stationary probability distribution of the model. In Sect. 4 is proposed an approximate method that significantly reduces the complexity of the model. Section 5 describes and analyzes the main performance measures of the model. Conclusions are drawn in Sect. 6.
2 Mathematical Model
Let us consider a single cell of a wireless mono-service network with radius R within a RE that can impact on the QoS level of users requests. We assume that user requests arrive in the system according to the Poisson law with rate \(\lambda \) and are serviced according to the exponential law with rate \(\mu \). We suppose that the distance between all the users and the Base Station (BS) is constant and equal to d. Each request processed in the system is serviced with the guaranteed bit rate (GBR) equaling \(r_0\).
We assume that the RE can change its state. Unlike [20], in this paper the RE changes state from 0 to 2. Such limitation allows to obtain an approximate solution which significantly reduces the complexity of calculations. Transition from state s to \(s-1\) is made with rate \(\alpha _s,s=1,2\) and from s to \(s+1\) with rate \(\beta _s,s=0,1\). Note that the rates \(\alpha _s\) and \(\beta _s\) are exponentially distributed.
Access to radio resource of the system is implemented in such a way that downlink power can vary under RE influence. It decreases from \(p_s\) to \(p_{s-1}, s=1,2\) with rate \(\alpha _s, s=1,2\), when transition to state \(s-1\) occurs. Recovery to \(p_s, s=1,2\) is made with rate \(\beta _s, s=0,1\). Note that the rates \(\alpha _s\) and \(\beta _s\) are exponentially distributed.
Changing downlink power affects the QoS level of users in the system, due primarily to the deterioration of such parameters as the achievable bit rate \(r_s\) and the maximum number of requests \(N_s, s=\overline{0,2}\) that can be serviced. Transition to state \(s-1, s=1,2\) leads to a decrease of that maximum number from \(N_s\) to \(N_{s-1}, s=1,2\). According to Shannon formula and system current state, the value of \(N_s, s=\overline{0,2}\) (1) can be defined as ratio of achievable bit rate \(r_s, s=\overline{0,2}\) to GBR \(r_0\).
where \(\omega \) is the bandwidth of uplink channel, G - the propagation constant, \(\kappa \) - the propagation exponent and \(N_0\) - the noise power.
We describe the behavior of the system using a two-dimensional vector (n, s) over the state space \(\mathbf X =\left\{ (n,s):0\le n\le N_s, s=\overline{0,2} \right\} \), where n represents the current number of requests in the system and s - the current state of the RE. Data transfer is performed with the minimum downlink power \(p_0\) in state \(s=0\) and with the maximum \(p_2\) in state \(s=2\). It should be noted that under RE influence, the services of \(N_s-N_{s-1},s=1,2\) requests are interrupted, when transition occurs from state s to \(s-1, s=1,2\), since \(N_2>N_1>N_0\). The corresponding state transition and central state transition diagrams are shown respectively in Figs. 1 and 2.
In accordance with the central state transition diagram shown in Fig. 2, the corresponding Markov process is described by the following system of equilibrium equations

where \(p(n,s), (n,s) \in \mathbf X \) represents the stationary probability distribution and I - the indicator function equaling 1 when the condition is met and 0 otherwise.
3 Accurate Methods for Calculating Probability Distribution
3.1 Numerical Solution
The process describing the considered system is not a reversible Markov process. Therefore, due to the implementation of the user service interruption mechanism, the system stationary probability distribution \(p(n,s)_{(n,s) \in \mathbf{X }} =\mathbf{p }\) can be computed, first of all using a numerical solution of the system of equilibrium equations \(\mathbf p \cdot \mathbf A = \mathbf 0 , \mathbf p \cdot \mathbf 1 ^T = 1\), where \(\mathbf A \) is the infinitesimal generator of Markov process, elements \(a((n,s)(n',s'))\) of which are defined as follows

where \(*=-(\alpha \cdotp I(s \ne 0)+\beta \cdotp I(s \ne S,n\le N_s)+\lambda \cdotp I(n<N_s, s=\overline{0,2})+n\mu \cdotp I(n > 0)), (n,s) \in \mathbf{X }\).
3.2 Recursive Algorithm
The system stationary probability distribution \(p(n,s), (n,s) \in \mathbf{X }\) can also be computed using a recursive algorithm that significantly reduces the complexity of the calculations.
Let us consider the unnormalized probabilities \(q(n,s), (n,s) \in \mathbf X \). To calculate these probabilities, we use the algorithm described below.
Step 1. The unnormalized probabilities q(n, s) are defined by formulas
where

Step 2. The coefficients \(\gamma _{ns}\), \(\delta _{ns}\) and \(\theta _{ns}\) are defined by recursive formulas


Finding the unnormalized probabilities \(q(n,s), (n,s) \in \mathbf X \), one can compute the stationary probability distribution of the system as follows:
4 Approximate Method
According to the model considered in the previous sections, the stationary probability distribution \(p(n,s)_{(n,s) \in \mathbf X } =\mathbf p \) is not of product form.
To determine that form we simplify the model. We suppose that under RE influence, downlink power reduction occurs only when the current number of requests n in state \(s,s=1,2\) is equal to maximum number of serviced requests in state \(s-1\), i.e. \(n=N_{s-1},s=1,2\). In other words user service is not interrupted. In Figs. 3 and 4 are shown respectively the state transition and the central state transition diagrams of the new model.
The behavior of the system is described using a two-dimensional vector (n, s) over the state space \(\mathbf X =\left\{ (n,s):0\le n\le N_s, s=0,1,2 \right\} \), where n represents the current number of requests in the system and s - the system current state.
The discussed Markov process is described by the following system of equilibrium equations:

where \(p(n,s), (n,s) \in \mathbf X \) is the stationary probability distribution.
After simplification, the process describing the behavior of the system becomes a reversible Markov process. This is verifiable using Kolmogorov criterion. Then, the stationary probability distribution \(p(n,s), (n,s) \in \mathbf X \) could be calculated using a product form (10), obtained throughout solution of system partial balance equations

where f(z) is the function equaling \(\prod _{k=1}^{z} {\beta _{k-1}/\alpha _k}\) when argument is strictly positive and 1 when null.
Note that, the stationary probability distribution \(p(n,s), (n,s) \in \mathbf X \) could also be calculated using a recursive algorithm like in Subsect. 3.2.
5 Performance Measures Analysis Using Both Methods
5.1 Performance Measures
Having found the stationary probability distribution \(p(n,s), (n,s) \in \mathbf X \), one can calculate the main performance measures of the considered model such as
-
Blocking probability B
$$\begin{aligned} B=\sum _{s=0}^{2} p(N_s,s); \end{aligned}$$(11)
-
Average number of serviced requests \(\overline{N}\)
$$\begin{aligned} \overline{N}=\sum _{s=0}^{2}\overline{N}_s=\sum _{s=0}^{2}\sum _{n=1}^{N_s} n p(n,s); \end{aligned}$$(12)
-
Mean bit rate \(\overline{r}\)
$$\begin{aligned} \overline{r}=\frac{\sum _{s=0}^{2}r_s \cdot \sum _{n=1}^{N_s}p(n,s)}{1-\sum _{s=0}^{2}p(0,s)}; \end{aligned}$$(13)
-
Interruption probability \(\varPi \)
 (14)
(14)
5.2 Comparative Analysis of Results
We evaluate how effective is the developed approximate method with a comparative analysis of results obtained after the performance measures calculation, i.e. using the recursive algorithm described in Subsect. 3.2 and formula (10).
To understand the physical interpretation of the RE, let us consider the operation of the system within the LSA framework [11]. LSA facilitates access for additional licensees in bands which are already in use by one or more incumbents allowing to dynamically share the frequency band, whenever and wherever it is unused by the incumbent users, but only on the basis of an individual authorization, i.e. licensed.
We consider one frequency band in use by one mobile operator (licensee) who rent it from another mobile operator (incumbent). Whenever needed by the incumbent, the band is returned leading to a downlink power reduction and consequently, to a QoS degradation in the licensee network. We suppose that the incumbent does not use the frequency band permanently, i.e. every 30 min (urban use of the LSA system). Downlink power reduction occurs only when the data transfer quality in the incumbent network is not satisfying. We assume that the licensee requests to use the LSA band every 30 s. When access is granted, the downlink power increases to level \(p_1\). At that level, the licensee sends a request every 60 s to reach the maximum downlink power \(p_2\). We summarize all the parameters of the comparative analysis in Tables 1 and 2 [11].
Let us consider several scenarios for the analysis of the system blocking probability.
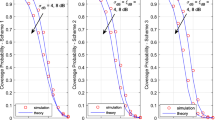
Scenario 1. We illustrate the behavior of the blocking probability B depending on the distance d between the users and the BS (Fig. 5). The results presented in the graph show that at low downlink power (i.e. 35 dBm), the approximate method is suitable only for small cells. With the increase of downlink power, approximate method becomes more accurate and can then be used for big cells.
Scenario 2. We illustrate the behavior of the blocking probability B depending on the maximum downlink power \(p_2\) (Fig. 6). The results show that the higher maximum downlink power gets, the more accurate approximate method becomes.
6 Conclusion
In this paper, a mathematical model for accessing radio resources of wireless communication networks, i.e. using downlink power reduction and user service interruption mechanisms, is constructed and investigated. The model is described as a queuing system operating in RE. An accurate method (recursive algorithm) is proposed to calculate the stationary probability distribution of the model. An approximate method based on assumption that simplifies the model is also given. Formulas are proposed to calculate the main performance measures of the model - blocking probability, average number of serviced requests, mean bit rate and interruption probability. A comparative analysis of the blocking probability calculation using both methods showed that the approximation is quite precise at high downlink power and suitable for small cells only at low downlink power.
References
Ericsson: Ericsson mobility report, November 2018
Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2017–2022, White Paper (2019)
3GPP TS 22.105: Services and service capabilities: Release 14. – 3GPP. – 2017-03
Basaure, A., Sridhar, V., Hammainen, H.: Adoption of dynamic spectrum access technologies: a system dynamics approach. Telecommun. Syst. 63(2), 169–190 (2016)
3GPP TS 36.300: Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN); Overall description; Stage 2: Release 14. – 3GPP. – 2017-07
Acar, Y., Aldirmaz, S., Basar, E.: Channel estimation for OFDM-IM systems. Turk. J. Electr. Eng. Comput. Sci. 27, 1908–1921 (2019). https://doi.org/10.3906/elk-1803-101
Ghallab, R., Shokair, M., Abouelazm, A., Sakr, A.A., Saad, W., Naguib, A.: Performance enhancement using MIMO electronic relay in massive MIMO cellular networks. IET Netw. (2019). https://doi.org/10.1049/iet-net.2018.5023
Garcia-Rodriguez, A., Geraci, G., Galati, L., Bonfante, A., Ding, M., Lopez-Perez, D.: Massive MIMO unlicensed: a new approach to dynamic spectrum access. IEEE Commun. Mag. 56, 186–192 (2017). https://doi.org/10.1109/MCOM.2017.1700533
Ouyang, F.: Massive MIMO for dynamic spectrum access, pp. 9–12 (2017). https://doi.org/10.1109/ICCE.2017.7889210
3GPP TS 23.246: Multimedia Broadcast/Multicast Service (MBMS); Architecture and functional description: Release 15. – 3GPP. – 2017-12
Markova, E., et al.: Flexible spectrum management in a smart city within licensed shared access framework. IEEE Access 5, 22252–22261 (2017)
Maule, M., Moltchanov, D., Kustarev, P., Komarov, M., Andreev, S., Koucheryavy, Y.: Delivering fairness and QoS guarantees for LTE/Wi-Fi coexistence under LAA operation. IEEE Access 6, 7359–7373 (2018)
Markova, E., Moltchanov, D., Gudkova, I., Samouylov, K., Koucharyavy, Y.: Performance assessment of QoS-aware LTE sessions offloading onto LAA/WiFi systems. IEEE Access 7, 36300–36311 (2019)
Borodakiy, V., Gudkova, I., Markova, E., Samouylov, K.: Modelling and performance analysis of pre-emption based radio admission control scheme for video conferencing over LTE. In: Proceedings of the ITU Kaleidoscope Academic Conference, pp. 53–59. ITU, Geneva (2014)
Basharin, G.P., Samouylov, K.E., Yarkina, N.V., Gudkova, I.A.: A new stage in mathematical teletraffic theory. Autom. Remote Control 70(12), 1954–1964 (2009)
Vishnevsky, V., Kozyrev, D., Rykov, V.: On the reliability of hybrid system information transmission evaluation. In: Proceedings of the Belarusian Winter Workshops in Queueing Theory BWWQT 2013, Minsk, Belarus, 28–31 January 2013, pp. 192–202 (2013)
Ali, A., Shah, G., Arshad, M.: Energy efficient resource allocation for M2M devices in 5G. Sensors 19, 1830 (2019). https://doi.org/10.3390/s19081830
Chen, S., Ma, R., Chen, H.-H., Zhang, H., Meng, W., Liu, J.: Machine-to-machine communications in ultra-dense networks - a survey. IEEE Commun. Surv. Tutor. 19, 1478–1503 (2017). https://doi.org/10.1109/COMST.2017.2678518
Su, J., Xu, H., Xin, N., Cao, G., Zhou, X.: Resource allocation in wireless powered iot system: a mean field stackelberg game-based approach. Sensors 18, 3173 (2018). https://doi.org/10.3390/s18103173
Adou, Y., Markova, E.V., Gudkova, I.: Performance measures analysis of admission control scheme model for wireless network, described by a queuing system operating in random environment. In: Proceedings of the 10th International Congress on Ultra Modern Telecommunications and Control Systems ICUMT-2018, Moscow, Russia, 5–9 November 2018, pp. 262–267. IEEE, Piscataway (2018)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Adou, Y., Markova, E., Gudkova, I. (2019). Approximate Product Form Solution for Performance Analysis of Wireless Network with Dynamic Power Control Policy. In: Vishnevskiy, V., Samouylov, K., Kozyrev, D. (eds) Distributed Computer and Communication Networks. DCCN 2019. Lecture Notes in Computer Science(), vol 11965. Springer, Cham. https://doi.org/10.1007/978-3-030-36614-8_29
Download citation
DOI: https://doi.org/10.1007/978-3-030-36614-8_29
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-36613-1
Online ISBN: 978-3-030-36614-8
eBook Packages: Computer ScienceComputer Science (R0)