Abstract
In cognitive radio mobile ad hoc networks (CR-MANETs), secondary users can cooperatively sense the spectrum to detect the presence of primary users. In this chapter, we propose a fully distributed and scalable cooperative spectrum sensing scheme based on recent advances in consensus algorithms. In the proposed scheme, the secondary users can maintain coordination based on only local information exchange without a centralized common receiver. We use the consensus of secondary users to make the final decision. The proposed scheme is essentially based on recent advances in consensus algorithms that have taken inspiration from complex natural phenomena including flocking of birds, schooling of fish, swarming of ants, and honeybees. Unlike the existing cooperative spectrum sensing schemes, there is no need for a centralized receiver in the proposed schemes, which make them suitable in distributed CR-MANETs. Simulation results show that the proposed consensus schemes can have significant lower missing detection probabilities and false alarm probabilities in CR-MANETs. It is also demonstrated that the proposed scheme not only has proven sensitivity in detecting the primary user’s presence but also has robustness in choosing a desirable decision threshold.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
1 Introduction
Recently, there has been tremendous interest in the field of cognitive radio (CR), which has been introduced in [1]. CR is an enabling technology that allows unlicensed (secondary) users to operate in the licensed spectrum bands. This can help to overcome the lack of available spectrum in wireless communications and achieve significant improvements over services offered by current wireless networks. It is designed to sense the changes in its surroundings, thus learns from its environment and performs functions that best serve its users. This is a very crucial feature of CR networks which allow users to operate in licensed bands without a license [2]. To achieve this goal, spectrum sensing is an indispensable part in cognitive radio.
There are three fundamental requirements for spectrum sensing. In the first place, the unlicensed (secondary) users can use the licensed spectrum as long as the licensed (primary) user is absent at some particular time slot and some specific geographic location. However, when the primary user comes back into operation, the secondary users should vacate the spectrum instantly to avoid interference with the primary user. Hence, a first requirement of cognitive radio is that the continuous spectrum sensing is needed to monitor the existence of the primary user. Also, since cognitive radios are considered as lower priority and they are secondary users of the spectrum allocated to a primary user, the second fundamental requirement is to avoid the interference to potential primary users in their vicinity [3]. Furthermore, primary user networks have no requirement to change their infrastructure for spectrum sharing with cognitive radios. Therefore, the third requirement is for secondary users to be able to independently detect the presence of primary users.
Taking those three requirements into consideration, such spectrum sensing can be conducted non-cooperatively (individually), in which each secondary user conducts radio detection and makes decision by itself. However, the sensing performance for one cognitive user will be degraded when the sensing channel experiences fading and shadowing [4]. In order to improve spectrum sensing, several authors have recently proposed collaboration among secondary users [5, 6, 7, 3], which means a group of secondary users perform spectrum sensing by collaboration. As a result, it shows that collaboration may enhance secondary spectrum access significantly [5].
Our research is focused on the distributed cooperative spectrum sensing (DCSS) in cognitive radio and, more precisely, the distributed cooperative schemes of spectrum sensing in a Cognitive Radio Mobile Ad-hoc NETworks (CR-MANETs).
In the first place, at present, distributed cooperative detection problems are discussed in [6, 8–10]. In a typical wireless distributed detection problem, each sensor or secondary user individually forms its own discrete messages based on its local measurement and then reports to a fusion center via wireless reporting channels. In certain models [10], however, there is, in general, no direct communication among the sensors. A sensor may indirectly obtain information about other sensors, but this is achieved by feedback from a common fusion center. Nevertheless, a centralized fusion center may not be available in some CR-MANETs. Moreover, as indicated in [11], gathering the entire received data at one place may be very difficult under practical communication constraints. In addition, authors of [4] study the reporting channels between the cognitive users and the common receiver. The results show that there are limitations for the performance of cooperation when the reporting channels to the common receiver are under deep fading.
Based on recent advances in consensus algorithms [12], we propose a new scheme in distributed cooperative spectrum sensing called distributed consensus-based cooperative spectrum sensing (DCCSS).
The main contributions of this work include as follows:
-
We propose a consensus-based spectrum sensing scheme, which is a fully distributed and scalable scheme. Unlike many existing schemes [46, 21, 22], there is no need for a common receiver to do data fusion and to reach the final decision. Since it is rare to have a centralized node in MANETs, in the proposed scheme, a secondary user needs only to setup local interactions without centralized information exchange.
-
Unlike most decision rules, such as OR-rule or n-out-of-N, adopted in existing spectrum sensing schemes, we use consensus from secondary users. The proposed scheme has self-configuration and self-maintenance capabilities.
-
Since the CR paradigm imposes human-like characteristics (e.g., learning, adaptation, and cooperation) in wireless networks, the bio-inspired consensus algorithm used in this work can provide some insight into the design of future CR-MANETs.
Extensive simulation results illustrate the effectiveness of the proposed scheme. It is shown that the proposed scheme can have both lower missing detection probability and lower false alarm probability compared to the existing schemes. In addition, it is able to make better detection when secondary users undergo worse fading (lower average SNR). Last but not the least, with the help of this scheme, a fixed threshold is feasible, which can take active effect in different fading channels.
The rest of the chapter is organized as follows. Section 1.2 describes the research background of this research, which includes spectrum sensing in cognitive radios, cooperative spectrum sensing, and centralized/distributed cooperative spectrum sensing. Section 1.3 presents system models, spectrum sensing model, fixed/random graphs theories, and consensus notions. In Section 1.4, the distributed consensus-based cooperative spectrum sensing scheme is proposed based on fixed graphs, together with the network models. Going further, the distributed consensus-based cooperative spectrum sensing scheme based on random graphs is described in Section 1.5. In Section 1.6, the simulation results and discussions are presented. Finally, we conclude this chapter in Section 1.7.
2 Background
This section is intended to cover the topics regarding the research background. They include the introduction of cognitive radio, functionalities of cognitive radio, differences of individual spectrum sensing, and cooperative spectrum sensing, followed by the introduction of centralized distributed cooperative spectrum sensing and distributed consensus-based cooperative spectrum sensing.
2.1 Introduction of Spectrum Sensing in Cognitive Radio
The idea of cognitive radio is first presented officially in an article by Joseph Mitola and Gerald Q. Maguire, Jr. [13]. It is a novel approach in wireless communications that Mitola later describe in his PhD dissertation as:
The point in which wireless Personal Digital Assistants (PDAs) and the related networks are sufficiently computationally intelligent about radio resources and related computer-to-computer communications to detect user communications needs as a function of use context, and to provide radio resources and wireless services most appropriate to those needs.
It is thought of as an ideal goal toward which a software-defined radio platform should evolve: a fully reconfigurable wireless blackbox that automatically changes its communication variables in response to network and user demands.
The above citation originates from the following fact. On one hand, the growing number of wireless standards is occupying more and more naturally limited frequency bandwidth for exclusive use as licensed bands. However, large part of licensed bands is unused for what concerns a large amount of both time and space: even if a particular range of frequencies is reserved for a standard, at a particular time and at a particular location it could be found free. The Federal Communication Commission (FCC) estimates that the variation of use of licensed spectrum ranges from 15 to 85%, whereas according to Defence Advance Research Projects Agency (DARPA) only the 2% of the spectrum is in use in United States at any given moment. It is then clear that the solution to these problems can be found dynamically looking at spectrum as a function of time and space.
With the high demand of bit transmission rate for 4G or IMT-advanced high-speed wireless applications, there are several approaches to increase the system capacity as stated in the following equation:
The first approach is using MIMO to increase n, so that capacity may have a gain proportionally. The second approach is trying to increase SNR. The third one is focusing on the bandwidth. Cognitive radio is among the third category and thrives to fully utilize the frequency.
2.1.1 Functionalities of Cognitive Radios
The main functionalities of cognitive radios are [14]
-
Spectrum Sensing (SS): Detecting the unused spectrum and sharing it without harmful interference with other users, it is an important requirement of the cognitive radio network to sense spectrum holes and detecting primary users is the most efficient way to detect spectrum holes. Spectrum sensing techniques can be classified into three categories:
-
Transmitter detection: cognitive radios must have the capability to determine if a signal from a primary transmitter is locally present in a certain spectrum, there are several approaches proposed:
-
Matched filter detection
-
Energy detection
-
Cyclostationary feature detection
-
-
Cooperative detection: refers to spectrum sensing methods where information from multiple cognitive radio users is incorporated for primary user detection.
-
Interference-based detection.
-
-
Spectrum Management (SMa): Capturing the best available spectrum to meet user communication requirements. Cognitive radios should decide on the best spectrum band to meet the quality of service requirements over all available spectrum bands, therefore spectrum management functions are required for cognitive radios, these management functions can be classified as spectrum analysis and spectrum decision.
-
Spectrum Mobility (SMo): Defined as the process when a cognitive radio user exchanges its frequency of operation. Cognitive radio networks target to use the spectrum in a dynamic manner by allowing the radio terminals to operate in the best available frequency band, maintaining seamless communication requirements during the transition to better spectrum.
-
Spectrum Sharing (SSh): Providing the fair spectrum scheduling method, which is one of the major challenges in open spectrum usage in the spectrum sharing. It can be regarded to be similar to generic media access control MAC problems in existing systems.
2.1.2 Individual and Cooperative Spectrum Sensing
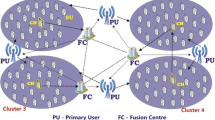
Spectrum sensing can be conducted either non-cooperatively (individually), in which each secondary user conducts radio detection and makes decision by itself, or cooperatively, in which a group of secondary users perform spectrum sensing by collaboration. No matter in which way, the common topology of such a cognitive radio network can be depicted as in Fig. 1.1. Individual spectrum sensing is conducted by secondary users on its own, and each user has a local observation and a local decision accordingly. Thus, in Fig. 1.1, each secondary user performs the spectrum sensing locally and no communication is between one another nor is the common receiver (fusion center). In such a condition, cognitive radio sensitivity can only be improved [6] by enhancing radio RF front-end sensitivity, exploiting digital signal processing gain for specific primary user signal, and network cooperation where users share their spectrum sensing measurements. However, if the sensing channels are facing deep fading or shadowing, then affected individuals will not be able to detect the presence of the primary user, which leads to missing detection failure.
In order to improve the performance of spectrum sensing, several authors have recently proposed cooperation among secondary users [2, 4, 5, , 15, ]. Cooperative spectrum sensing has been proposed to exploit multi-user diversity in sensing process. It is usually performed in three successive stages: sensing, reporting and broadcasting. In the sensing stage, every cognitive user performs spectrum sensing individually. This can be shown as in Fig. 1.1, where secondary users try to collect the signal of interest through sensing channels. In the reporting stage, all the local sensing observations are reported to a common receiver via reporting channels (see Fig. 1.1) and the latter will make a final decision on the absence or the presence of the primary user. Finally, the final decision is broadcasted via broadcast channels to all the secondary users concerned, which include not only the ones involved into the sensing stage but also those that do not have sensing capabilities but want to participate into the spectrum sharing stage.
There are several advantages offered by cooperative spectrum sensing over the non-cooperative ones [5, 11, 16–22]. If a secondary user is in the condition of deep shadowing and fading, it is very difficult for a secondary user to distinguish a white space from a deep shadowing effect. Therefore, a non-cooperative spectrum sensing algorithm may not work well in this case, and a cooperative scheme can solve the problem by sharing the spectrum sensing information among secondary users. Moreover, because of the hidden terminal problem, it is very challenging for single cognitive radio sensitivity to outperform the primary user receiver by a large margin in order to detect the presence of primary users. For this reason, if secondary users spread out in the spatial distance, and any one of them detects the presence of primary users, then the whole group can gain benefit by collaboration.
Ghasemi and Sousa [5] quantify the performance of spectrum sensing in fading environments and study the effect of cooperation. The simulation results in [5] indicate that significant performance enhancements can be achieved through cooperation. Ganesan and Li [16] study the possibility to forward the signal with higher SNR to the one on the boundary of decidability region of the primary user. The performance is evaluated under correlated shadowing and user compromise in [11]. When the exchange of observations from all secondary users to the common receiver is not applicable, Peh and Liang [17] show that it is still worth doing by cooperating a certain number of users with relatively higher SNR. Moreover, in [18], a linear-quadratic (LQ) fusion strategy is designed with the consideration of the correlation between the nodes. In order to further reduce the computational complexity, Quan et al. [19] propose a heuristic approach so as to develop an optimal linear framework during cooperation. Sensing-throughput tradeoff is analyzed in [20] for both multiple mini-slots and multiple secondary users cooperative sensing.
2.1.3 Centralized Cooperative Spectrum Sensing
Although some research activities have been conducted in cooperative spectrum sensing, most of them use a common receiver (fusion center) to do data fusion for the final decision whether or not the primary user is present. However, a common receiver may not be available in some CR-MANETs. Moreover, as indicated in [11], gathering the entire received data at one place may be very difficult under practical communication constraints. In addition, Sun et al. [4] study the reporting channels between the cognitive users and the common receiver. The results show that there are limitations for the performance of cooperation when the reporting channels to the common receiver are under deep fading. In summary, the use of a centralized fusion center in CR-MANETs may have the following problems (see Fig. 1.1):
-
Every secondary user needs to join/establish the connection with the common receiver, which requires a network protocol to implement.
-
Some secondary users need a kind of relay routes to reach the common receiver if they are far away from the latter.
-
Communication errors or packet drops can affect the performance of such a network if more users have worse reporting channels (e.g., Rayleigh Fading) to reach the common receiver.
-
There should be a reliable wireless broadcast channel for the common receiver to inform each of every user once there is a decision made.
-
The current centralized network does not fit for the average calculation of all the estimated sensing energy levels, because it requires the common receiver to correctly receive all the local estimated sensing results. Otherwise, the decision precision cannot be guaranteed.
2.2 Mobile Ad Hoc Networks
In recent years, MANETs have become a popular subject because of their self-configuration and self-organization capabilities. Each device in a MANET is free to move independently in any direction and will therefore change its links to other devices frequently. Wireless nodes can establish a dynamic network without the need of a fixed infrastructure. A node can function both as a network router for routing packets from the other nodes and as a network host for transmitting and receiving data. MANETs are particular useful when a reliable fixed or mobile infrastructure is not available. Instant conferences between notebook PC users, military applications, emergency operations, and other secure-sensitive operations are important applications of MANETs due to their quick and easy deployment.
2.2.1 Self-Organization of MANETs
Due to the lack of centralized control, MANETs nodes cooperate with each other to achieve a common goal [23]. The major activities involved in self-organization are neighbor discovery, topology organization, and topology reorganization. Through periodically transmitting beacon packets or promiscuous snooping on the channels, the activities of neighbors can be acquired. Each node in MANETs maintains the topology of the network by gathering the local or entire network information. MANETs need to update the topology information whenever the networks change such as participation of new node, failure of node, and links. Therefore, self-organization is a continuous process that has to adapt to a variety of changes or failures.
2.3 Distributed Consensus-Based Cooperative Spectrum Sensing Scheme
In this work, we will present a distributed consensus-based cooperative spectrum sensing scheme without using a common receiver. Our scheme is based on recent advances in consensus algorithms [12], or more precisely, bio-inspired mechanisms, which have become important approaches to handle complex communication networks [24–26]. An important motivational background of this area is initially related to the study of complex natural phenomena including flocking of birds, schooling of fish, and swarming of ants and honeybees (see the survey [27]). The investigation of such biological systems has generated fundamental insights into understanding the relation between group decision making at the higher level and the individual animals’ communication at the lower level [28–32], and in fact consensus seeking in animal colonies is vital for group survival [32]. Such collective animal behavior has motivated many effective yet simple control algorithms for the coordination of multi-agent systems in engineering. Recently, consensus problems have played a crucial role in spacial distributed control models [12, 33], wireless sensor networks [34], and stochastic seeking with noise measurement [35]. Since these algorithms are usually constructed based on local communication of neighboring agents, they have low implementation complexity and good robustness, and the overall system may still function when local failure occurs.
The main highlights of this scheme are as follows:
-
It is a fully distributed and scalable scheme. Unlike the existing schemes [21, 22, 46], there is no need for a common receiver to do the data fusion for the final decision. A secondary user only needs to set up neighborhood with those users having desired channel characteristics, such as Line of Sight ones, or even with probabilistic link failures.
-
Unlike most decision rules, such as OR-rule or 1-out-of-N, adopted in the existing schemes, we use the consensus of secondary users to make the final decision. Therefore, the proposed scheme can leverage the detection results among users in a severe wireless fading networks.
-
The proposed spectrum sensing scheme uses a consensus algorithm to cope with two underlying network models, one with fixed bidirectional graphs and one with random graphs.
Our consensus-based approach is different from those used in distributed/decentralized detection problems [8–10, 36]. In a typical distributed detection problem [36, 8, 9], each sensor individually forms its own discrete messages based on its local measurement and then reports to a fusion center, and there is in general no direct communication among the sensors. In certain models [10], a sensor may indirectly obtain information about other sensors, but this is achieved by feedback from a common fusion center.
3 Secondary Users Network Modeling
This section is organized in the following order. First, a network topology in distributed consensus-based cooperative spectrum sensing is presented. Then, the local spectrum sensing model is discussed in details. At last, the network model and consensus notions are presented.
3.1 Network Topology in Distributed Consensus-Based Cooperative Spectrum Sensing
As shown in Fig. 1.2, no common receiver is necessary compared with Fig. 1.1, and secondary users are communicating with each other via communication channels that are in good radio coverage of each of secondary users. Secondary users that are far away from each other do not have direct communication channels due to poor radio signal quality.
There are two stages in the proposed cognitive radio consensus schemes. In the first stage, secondary users use a spectrum sensing model to make measurements about primary users at the beginning of detection. This is done via sensing channels in Fig. 1.2. We denote the local measurement of user i as Y i . In the second stage, secondary users establish communication links with their own neighbors to locally exchange information among them, and then calculate the obtained data so as to make a local decision whether primary users are around. The above process in the second stage is done iteratively. At the initial time instant k = 0, each user i sets \(x_i(0)=Y_i\) as the initial value of the local state variable. Next, at time \(k=0,1,2,\ldots\) , according to the real-time network topology (or local wireless neighborhood), users mutually transmit and receive their states and then use local computation rules to generate updated states \(x_i(k+1)\). Those iterations are done repeatedly until all the individual states \(x_i(k)\) converge toward a common value x *.
Before we introduce the detailed algorithms used in our consensus scheme, the common spectrum sensing model used in the first stage and the network model used in the second stage are to be presented, followed by the formal definition of the spectrum sensing consensus scheme.
3.2 The Spectrum Sensing Model
In the first stage, secondary users make measurements about primary users at the beginning of each time slot. Three kinds of methods are widely used for spectrum sensing [6]: matched filter, energy detector, and cyclostationary feature detector.
-
Matched Filter
The optimal way for any signal detection is a matched filter [37], since it maximizes received signal-to-noise ratio. However, a matched filter effectively requires demodulation of a primary user signal. This means that cognitive radio has a priori knowledge of primary user signal at both PHY and MAC layers, e.g., modulation type and order, pulse shaping, and packet format. Such information might be pre-stored in CR memory, but the cumbersome part is that for demodulation it has to achieve coherency with primary user signal by performing timing and carrier synchronization, even channel equalization. This is still possible since most primary users have pilots, preambles, synchronization words, or spreading codes that can be used for coherent detection. For examples: TV signal has narrowband pilot for audio and video carriers; CDMA systems have dedicated spreading codes for pilot and synchronization channels; OFDM packets have preambles for packet acquisition. The main advantage of matched filter is that due to coherency it requires less time to achieve high processing gain [38]. However, a significant drawback of a matched filter is that a cognitive radio would need a dedicated receiver for every primary user class.
-
Energy Detector
One approach to simplify matched filtering approach is to perform non-coherent detection through energy detection. This sub-optimal technique has been extensively used in radiometry. There are several drawbacks of energy detectors that might diminish their simplicity in implementation. First, a threshold used for primary user detection is highly susceptible to unknown or changing noise levels. Even if the threshold would be set adaptively, presence of any in-band interference would confuse the energy detector. Furthermore, in frequency selective fading it is not clear how to set the threshold with respect to channel notches. Second, energy detector does not differentiate between modulated signals, noise, and interference. Since, it cannot recognize the interference, it cannot benefit from adaptive signal processing for canceling the interferer. Furthermore, spectrum policy for using the band is constrained only to primary users, so a cognitive user should treat noise and other secondary users differently. Lastly, an energy detector does not work for spread spectrum signals: direct sequence and frequency hopping signals, for which more sophisticated signal processing algorithms need to be devised. In general, we could increase detector robustness by looking into a primary signal footprint such as modulation type, data rate, or other signal feature.
-
Cyclostationary Feature Detection
Modulated signals are in general coupled with sine wave carriers, pulse trains, repeating spreading, hoping sequences, or cyclic prefixes which result in built-in periodicity. Even though the data is a stationary random process, these modulated signals are characterized as cyclostationary, since their statistics, mean and autocorrelation, exhibit periodicity. This periodicity is typically introduced intentionally in the signal format so that a receiver can exploit it for: parameter estimation such as carrier phase, pulse timing, or direction of arrival. This can then be used for detection of a random signal with a particular modulation type in a background of noise and other modulated signals.
In summary, Matched filter is optimal theoretically, but it needs the prior knowledge of the primary system, which means higher complexity and cost to develop adaptive sensing circuits for different primary wireless systems. Energy detection is suboptimal, but it is simple to implement and does not have too much requirement on the position of primary users. Cyclostationary feature detection can detect the signals with very low SNR, but it still requires some prior knowledge of the primary user [4].
In this chapter, we consider the modeling scenario where the prior knowledge of the primary user is unknown. For implementation simplicity, an energy detection spectrum sensing method [5] is used. Fig. 1.3 shows the block diagram of an energy detector. The input band pass filter (BPF) selects the center frequency f s and the bandwidth of interest W. This filter is followed by a squaring device and subsequently an integrator over a period of T. The output Y of the integrator is the received energy at the secondary user and its distribution depends on whether the primary user signal is present or not. The goal of spectrum sensing is to decide between the following two hypotheses:
where x(t) is the signal received by the secondary user, s(t) is the primary user’s transmitted signal, n(t) is the additive white Gaussian noise (AWGN), and h is the amplitude gain of the channel. We also denote by γ the signal-to-noise ratio (SNR). The output of integrator in Fig. 1.3 is Y, which serves as the decision statistic. Following the work of [39], Y has the following form:
where \(\chi^2_{2TW}\) and \(\chi^2_{2TW}(2\gamma)\) denote random quantities with central and non-central chi-square distributions, respectively, each with 2TW degrees of freedom and a non-centrality parameter of 2γ for the latter distribution. For simplicity we assume that the time-bandwidth product, TW, is an integer number, which is denoted by m.
Under Rayleigh fading, the gain h is random, and the resulting SNR γ would have an exponential distribution, so in this case the distribution of the output energy depends on the average SNR \(({\overline{\gamma}})\). When the primary user is absent, Y is still distributed according to \(\chi_{2TW}^2\). When the primary user is present, Y may be denoted as the sum of two independent random variables [40, 41]:
where the distribution of Y χ is \(\chi_{2TW-2}^2\) and Y e has an exponential distribution with parameter \(2(\overline\gamma+1)\).
As a summary, after T seconds, each secondary user i detects the energy and gets the measurement \(Y_i \in {\mathbb{R}^+ }\).
3.3 The Network Model and Consensus Notions
In the second stage, secondary users establish communication links with its neighbors to locally exchange information among them. In our scheme, the network formed by the secondary users can be described by a standard graph model. For simplicity, this can be represented by an undirected graph (to be simply called a graph) \({\boldsymbol{G}=({\cal N},{\cal E})}\) [42] consisting of a set of nodes \({{\{i=1,2,\ldots,n\}}}\) and a set of edges \(\cal E \subset N \times N\). Denote each edge as an unordered pair (i, j). Thus, if two secondary users are connected by an edge, it means they can mutually exchange information. A path in G consists of a sequence of nodes \(i_1, i_2, \ldots, i_l,\ l \geq 2\), such that \((i_m, i_{m+1})\in \cal E\) for all \(1\leq m\leq l-1\). The graph \(\boldsymbol{ G}\) is connected if any two distinct nodes in \(\boldsymbol{ G}\) are connected by a path. For convenience of exposition, we often refer node i as secondary user i. The two names, secondary user and node, will be used interchangeably. The secondary user j (resp., node j) is a neighbor of user i (resp., node i) if \((j, i)\in {\cal E}\), where \(j \neq i\). Denote the neighbors of node i by \({\cal N}_i=\{j|(j,i)\in {\cal E}\} \subset \cal N\). The number of elements in \({\cal N}_i\) is denoted by \(|{\cal N}_i|\) and called the degree of node i.
Throughout this chapter, the analysis is for undirected graphs, because we only deal with good duplex wireless links by which two adjacent nodes can establish communication (being connected) with each other. That is, the graph G is connected, and the information exchange between two neighboring nodes is bidirectional.
The Laplacian of the graph G is defined as \(\boldsymbol{ L}=(l_{ij})_{n\times n}\), where
The matrix \(\boldsymbol{ L}\) defined by (1.5) is positive semi-definite. Further, if \(\boldsymbol{ G}\) is a connected undirected graph, then \(\mbox{rank}(\boldsymbol{ G})=n-1\) (see, e.g., [27]).
Since the cooperative spectrum sensing problem is viewed as a consensus problem where the users locally exchange information regarding their individual detection outcomes before reaching an agreement, we give the formal mathematical definition of consensus as follows.
The underlying network turns out to consist of secondary users reaching a consensus via local communication with their neighbors on a graph \(\boldsymbol{ G}=(\cal N,\cal E)\).
For the n secondary users distributed according to the graph model \(\boldsymbol{ G}\), we assign them a set of state variables x i , \(i\in {\cal N}\). Each x i will be called a consensus variable, and in the cooperative spectrum sensing context, it is essentially used by node i for its estimate of the energy detection.
By reaching consensus, we mean the individual states x i asymptotically converge to a common value x *, i.e.,
for each \(i\in {\cal N}\), where k is the discrete time, \(k=0,1,2,\ldots,\) and \(x_i(k)\) is updated based on the previous states of node i and its neighbors.
The special cases with \(x^*=\mbox{Ave}(x)=({1}/{n})\sum^n_{i=1}x_i(0)\), \(x^*=\max^n_{i=1}x_i(0)\), and \(x^*=\min^n_{i=1}x_i(0)\) are called average-consensus, max-consensus, and min-consensus, respectively. It is worth mentioning that the existing spectrum sensing algorithm with the OR-rule can be viewed as a form of max-consensus. This chapter is intended to propose a cooperative spectrum sensing scheme in the framework of average consensus.
4 Distributed Consensus-Based Cooperative Spectrum Sensing in Fixed Graphs
In this chapter, let us assume the secondary users have established duplex wireless connections with their desired neighbors, and the connections remain working until the consensus is reached. This kind of topology is called as a fixed graph. Based on this assumption, we are going to propose the spectrum sensing consensus algorithm as follows.
4.1 The Consensus Algorithm
We denote for user i, its measurement Y i at time k = 0 by \(x_i(0)=Y_i \in {\mathbb{R}^+}\). The state update of the consensus variable for each secondary user occurs at discrete time \(k=0,1,2,\ldots,\) which is associated with a given sampling period. From \(k=0,1,2,\ldots\) , the iterative form of the consensus algorithm can be stated as follows [27]:
where
The number Δ is called the maximum degree of the network.
This algorithm can be written in the vector form:
where \(\boldsymbol{ P}=\boldsymbol{ I}-\varepsilon \boldsymbol{ L}\). Notice that the upper bound in (1.8) for ε ensures that \(\boldsymbol{ P}\) is a stochastic matrix, and in fact one can further show that P is ergodic when \(\boldsymbol{ G}\) is connectedFootnote 1. Since \(\boldsymbol{ G}\) is an undirected graph, all row sums and column sums of \(\boldsymbol{ L}\) are equal to zero. Hence \(\boldsymbol{ P}\) is a doubly stochastic matrix (i.e., \(\boldsymbol{ P}\) is a nonnegative matrix and all of its row sums and column sums are equal to one).
We also point out that (1.9) uses only a particular construction of the coefficient matrix for the consensus algorithm, which is based on the graph Laplacian \(\boldsymbol{ L}\). As long as each node has the prior knowledge of an upper bound of the maximum degree Δ of the network, the iteration may be implemented and there is no necessity for neighboring nodes to exchange information regarding the network structure. Also, it is possible to construct \(\boldsymbol{ P}\) in other forms.
An alternative choice of \(\boldsymbol{ P}\) may be based on the so-called Metropolis weights [34] by taking
where \(d_i=|{\cal N}_i|\) is the degree of node i. If \(\boldsymbol{ G}\) is a connected graph and we define \(\widetilde{\boldsymbol{ P}}=(\tilde p_{ij})_{n\times n}\), then \(\widetilde{\boldsymbol{ P}}\) is an ergodic doubly stochastic matrix. When \(\widetilde{\boldsymbol{ P}}\) is used in (1.9) in place of \(\boldsymbol{ P}\), the state average will still be preserved as an invariant during the iterations and our convergence analysis below is still valid. Notice that when \(\widetilde{\boldsymbol{ P}}\) is used in the consensus algorithm, it is only required that any two neighboring nodes report to each other their degrees, and the knowledge of the maximum degree of the network is no longer needed.
We cite a theorem concerning the convergence property of the consensus algorithm.
Theorem 1
(see, e.g., [27]) Consider a network of secondary users,
with topology \(\boldsymbol{ G}\) applying the distributed consensus algorithm (1.7), where \({u_i(k)}=\varepsilon\sum_{j\in {\cal N}_i}(x_j(k)-x_i(k))\), \(0\!<\!\varepsilon\!<\!{1}/{\varDelta}\), and Δ is the maximum degree of the network. Let \(\boldsymbol{ G}\) be a connected undirected graph. Then
-
1.
A consensus is asymptotically reached for all initial states;
-
2.
\(\boldsymbol{ P}\) is doubly stochastic, and an average consensus is asymptotically reached with the limit \(x^*=({1}/{n})\sum^n_{i=1}{x_i(0)}\) for the individual states.
According to Theorem 1, if we choose ε such that \(0\!<\!\varepsilon\!<\!{1}/{\varDelta}\), then an average consensus is ensured and the final common value \(x^*=({1}/{n})\sum^n_{i=1}{x_i(0)}\) will be the average of the initial vector \(\boldsymbol {x(0)}\), or equivalently, the average of \(\boldsymbol {Y^T}=\{{Y_1},{Y_2},\ldots,{Y_n}\}\), which has been obtained during the energy detection stage.
Finally, by comparing the average-consensus result x * with a pre-defined threshold λ based on Fig. 1.3, every secondary user i gets the final data fusion locally:
4.2 Performance of the Consensus Algorithm
It is quite apparent that the convergence rate is yet another interesting issue in evaluating the performance of the spectrum sensing consensus algorithm. This is due to the fact that secondary users must continuously detect the presence of primary users and back up as soon as possible on recognizing such incident. From this point of view, the speed of reaching a consensus is the key in the design of the network topology as well as the analysis of the performance of a consensus algorithm for a given spectrum sensing network. For the connected undirected graph \(\boldsymbol{ G}\), the above algorithm can ensure exponential convergence rate, where the error can be parameterized in the form \(O(e^{-\delta t})\) with the exponent \(\delta>0\). To have some bound estimate for the parameter δ, we first recall that \(\boldsymbol{ P}=\boldsymbol{ I}-\varepsilon \boldsymbol{ L}\). Since L is a positive semi-definite matrix, denote its n eigenvalues by
Here \(\lambda_2>0\) since the undirected graph G is connected which ensures that the rank of \(\boldsymbol{ L}\) is equal to \(n-1\) ([43]). The second smallest eigenvalue λ 2 of \(\boldsymbol{ L}\) is usually called the algebraic connectivity of the undirected graph \(\boldsymbol{ G}\). Then the second largest absolute value of the eigenvalues of \(\boldsymbol{ P}\) is determined as \( \alpha(\varepsilon)=\max\{|1-\varepsilon \lambda_2|, |1-\varepsilon\lambda_n|\}\), which can be verified to satisfy \(\alpha(\varepsilon) <1\). By using standard results in nonnegative matrix theory (see, e.g., [44]), we can obtain an upper bound for δ. In fact, we can take δ as any value in the interval \((0, -\ln \alpha(\varepsilon)).\) We also remark that similar convergence rate estimates can be carried out when general weight matrices in averaging are used.
Since \(\boldsymbol{ P}\) has a unit eigenvalue, we see that the difference between the first two largest absolute values of the eigenvalues of \(\boldsymbol{ P}\) is given as \(g(\varepsilon)=1-\alpha(\varepsilon)\), which is customarily called the spectral gap of \(\boldsymbol{ P}\). In general, the greater is g(ε), the greater is the upper bound \(-\ln \alpha(\varepsilon)\) for the exponent δ, and the faster is the convergence of the consensus algorithm. In practical implementations, it is desirable to choose a suitable value for ε to increase the spectral gap g(ε) while \(\boldsymbol{ P}\) is ensured to be ergodic. We will discuss the convergence rate in the simulation part of this chapter.
5 Distributed Consensus-Based Cooperative Spectrum Sensing in Random Graphs
In the previous section, it has been assumed that any two neighboring nodes can reliably exchange data at all times. Hence the network topology remains unchanged during the overall time period of interest. This kind of network modeling may not be accurate in certain situations. For example, fading of wireless signals can cause packet errors, which will result in wireless link failures for that period. Furthermore, even under LOS channels, moving objects between neighboring nodes may temporarily affect signal reception. For the above reasons, in this chapter, we consider a more realistic inter-node communication model with random link failures. Unlike the previous model, which is based on fixed bidirectional graphs, the new model is based on random graphs. Nevertheless, similar to the previous fixed topology scenario, for the random graph-based modeling below, we still consider bidirectional links when two nodes can communicate.
5.1 Random Graph Modeling of the Network Topology
Before characterizing random connectivity of the network of all secondary users, let us first introduce a fixed undirected graph \(\boldsymbol{ G} = ({\cal N} ,{\cal E} )\) which describes the maximal set of communication links when there is no link failure. Due to the random link failures, at time k the inter-user communication is described by a subgraph of \(\boldsymbol{ G}\) denoted by \(\boldsymbol{ G}(k) = ({\cal N} ,{\cal E}(k) )\) where \({\cal E}(k) \subset {\cal E}\); the edge \((j, i) \in {\cal E}(k)\) if and only if nodes j and i can communicate at time k where \((j, i) \in {\cal E}\). Thus, the (undirected) graph \(\boldsymbol{ G}(k)\) is generated as the outcome of random link failures. Note that an edge (j, i) never appears in \(\boldsymbol{ G}(k)\) if it is not an edge of \(\boldsymbol{ G}\). The neighbor set of node i is \({\cal N}_i(k) =\{j|(j, i) \in {\cal E}(k)\}\) at time k. The number of elements in \({\cal N}_i(k)\) is denoted by \(|{\cal N}_i(k)|\). At time \(k\geq 0\), the adjacency matrix of \(\boldsymbol{ G}(k)\) is defined as \(\boldsymbol{ A}(k)=(\alpha_{ji}(k))_{1\leq j,i \leq |{\cal N}|}\), where \(\alpha_{ji}(k)=1\) if \((j,i)\in {\cal E}(k)\), and \(\alpha_{ji}(k)=0\) otherwise. It is clear that the graph \(\boldsymbol{ G}(k)\) is completely characterized by the random matrix \(\boldsymbol{ A}(k)\).
Concerning the statistical properties of link failures, we assume that for all links (each associated with an edge in the graph \(\boldsymbol{ G}\)) fail independently with the same probability \(p\in (0,1)\). For notational simplicity we use the same parameter p to model the failure probability. The generalization of the modeling and analysis to link-dependent failure probabilities is straightforward.
5.2 The Algorithm with Random Graphs
For the random link failure-prone model, the two spectrum sensing stages introduced in the previous chapter are still applicable. In the first stage, each node performs the radio detection and computes the measurements according to (1.2). During the second stage, at time k each node exchanges states information with its neighbors and performs the corresponding computation to generate its state update \(x_i(k+1)\). Let Δ be the maximum degree of the graph \(\boldsymbol{ G}\) and take \(\varepsilon \in (0, 1/\varDelta)\).
The state of user \(i \in {\cal N}\) is updated by the rule
where ε is a pre-determined constant step size. If \({\cal N}_i(k)=\emptyset\) (empty set), (1.13) reduces to \(x_i(k+1)=x_i(k)\).
Theorem 2
Under the independent link failure assumption, the algorithm (1.13) ensures average-consensus, i.e., \(\lim_{k \rightarrow \infty}x_i(k)=(1/n)\sum_{j=1}^n x_j(0)\) for all \(i\in {\cal N}\), with probability 1. If, in addition, \(E|x(0)|^2<\infty\) and \(x(0)\) is independent of the sequence of adjacency matrices \(\textbf{A}(k)\), \(k=0,1,\ldots\) , then each \(x_i(k)\) converges to \((1/n)\sum_{j=1}^n x_j(0)\) in mean square with an exponential convergence rate.
Proof
We can write the algorithm (1.13) in the vector form
where \(\boldsymbol{ L}(k)\) is the Laplacian of the graph \(\boldsymbol{ G}(k)\). For a vector \(\boldsymbol{ z}=(z_1,\ldots, z_n)^T\!\), denote the Euclidean norm \(|\boldsymbol{ z}|= \left(\sum_{i=1}^n z_i^2\right)^{{1}/{2}}\). For any given sample point, we can show that \(\boldsymbol{ M}(k)= \boldsymbol{ I}-\varepsilon \boldsymbol{ L}(k)\) is a symmetric aperiodic stochastic matrix so that it has all its eigenvalues within the interval \((-1, 1] \) (see, e.g., [44]), and therefore \(\boldsymbol{ M}(k)\) determines a paracontracting map [45, 34] in the sense \(\boldsymbol{ M}(k)\boldsymbol{ z}\neq \boldsymbol{ z} \) if and only if \(|\boldsymbol{ M}(k)\boldsymbol{ z}|<|\boldsymbol{ z}|\). For \(\boldsymbol{ M}(k)\), we denote its fixed point subspace \({\cal H}(\boldsymbol{ M}(k))=\boldsymbol{z}\in \mathbb{R}^n| \boldsymbol{ M}(k)\boldsymbol{ z}=\boldsymbol{ z}\}\).
By the assumption on the independent link failures, we see that with probability 1, \(\boldsymbol{ G}(k)=\boldsymbol{ G}\) for an infinite number of times k. Let Ω denote the underlying probability sample space. Thus, after excluding a set A 0 of zero probability, for all \(\omega\in\Omega\backslash A_0\), \(\boldsymbol{ G}(k)=\boldsymbol{ G}\) infinitely often with the associated Laplacian being \(\boldsymbol{ L}(k)=\boldsymbol{ L}\). Hence, for each \(\omega\in\Omega\backslash A_0\), x(k) converges to a point in the space \({\cal H}( \boldsymbol{ I}-\varepsilon \boldsymbol{ L})=\{z\in \mathbb{R}^n|\boldsymbol{ L}z=0\} \) when \(k\rightarrow \infty\). Furthermore, \(\boldsymbol{z}\in \mathbb{R}^n|\boldsymbol{ L}\boldsymbol{z}=0\} =\mbox{span} \{1_n\}\) since \(\boldsymbol{ G}\) is a connected undirected graph.
On the other hand, it is straightforward to check that \((1/n)\sum_{j=1}^n x_j(k)\) remains as a constant since \(\boldsymbol{ M}(k)\) is a doubly stochastic matrix (i.e., nonnegative matric with all row sums and column sums equal to 1). Now it follows that each \(x_i(k)\) converges to \((1/n)\sum_{j=1}^n x_j(0)\) with probability one, as \(k\rightarrow\infty\).
We continue to analyze mean square convergence. Since \(E|\boldsymbol{ x}(0)|^2<\infty\) and \(\sup_{i\in {\cal N},k\geq 0}|x_i(k)|\leq \max_{i\in {\cal N}}|x_i(0)|\leq |\boldsymbol{ x}(0)|\), by the probability 1 convergence of \(x_i(k)\), it follows from dominated convergence results in probability theory that \(x_i(k)\) also converges to \((1/n)\sum_{j=1}^n x_j(0)\) in mean square.
Now, we proceed to give an estimation of the mean square convergence rate within the random network model. Denote \(\mbox{Ave}(\boldsymbol{ x}(0))=(1/n)\sum_{j=1}^n x_j(0)\). It is straightforward to show that
In fact, for each \(\omega\in \Omega\), by the eigenvalue distribution of the matrices \((1/n) \boldsymbol{ 1}_n \boldsymbol{ 1}_n^T\) and \(\boldsymbol{ L}(k)\), we can show that \(\boldsymbol{ B}^T\!(k) \boldsymbol{ B}(k)\), and subsequently \(E[\boldsymbol{ B}^T(k) \boldsymbol{ B}(k)]\), have n real eigenvalues on the interval \([0,1]\). We use a contradiction argument to show that the largest eigenvalue ρ of \(E[\boldsymbol{ B}^T(k) \boldsymbol{ B}(k)]\) is less than 1. Suppose \(\rho=1\) for \(E[\boldsymbol{ B}^T(k) \boldsymbol{ B}(k)]\); then there exists a real-valued vector \(\boldsymbol{ x}\neq 0\) such that
By the fact \(\boldsymbol{ x}^T[\boldsymbol{ B}^T(k) \boldsymbol{ B}(k)] \boldsymbol{ x}\leq \boldsymbol{ x}^T \boldsymbol{ x}\), the equality (1.16) leads to
with probability 1. On the other hand, by the link failure assumption, there exists a set \(A_1\subset \Omega\) such that \(P(A_1)>0\) and for each \(\omega\in A_1\), the associated matrix value \(\boldsymbol{ B}(k)= \boldsymbol{ I}-\varepsilon \boldsymbol{ L}\). Without the loss of generality, we can assume A 1 has been chosen in such a manner that for any \(\omega\in A_1\) (1.17) also holds.
By noticing the fact that for any \(\boldsymbol{ z}\in \mathbb{R}^n\),
we obtain from (1.17) that
Hence, (1.19) implies that \(\boldsymbol{ x}\) is the eigenvector of \( \boldsymbol{ I}-\varepsilon \boldsymbol{ L}\) associated with the eigenvalue 1, which further implies that \(\boldsymbol{ x}\in \mbox{span}\{\boldsymbol{1_n}\}\). Denote \(\boldsymbol{ x}=c\boldsymbol{ 1}_n\) where c is a constant. By substituting \(\boldsymbol{ x}=c\boldsymbol{ 1}_n\) into the left hand side of (1.17), we obtain \(\boldsymbol{ x}^T[\boldsymbol{ B}^T(k) \boldsymbol{ B}(k)] \boldsymbol{ x}=0\) for each \(\omega\in \Omega\), which contradicts with (1.17) and the fact \(\boldsymbol{ x}\neq 0\). Hence, we conclude that the largest eigenvalue ρ of \(E[\boldsymbol{ B}^T(k) \boldsymbol{ B}(k)]\) is in the interval \([0,1)\).
Finally, by elementary calculation we obtain the convergence rate estimate
In fact, we have the simplified expression:
and therefore, ρ is also given as the largest eigenvalue of the positive semi-definite matrix \(E[\boldsymbol{ I}-\varepsilon \boldsymbol{ L}(k)]^2 -(1/n) \boldsymbol{ 1}_n \boldsymbol{ 1}_n^T\).
6 Simulation Results and Discussions
In this section, we present and discuss the simulation results of the distributed consensus-based scheme.
6.1 Distributed Consensus-Based Cooperative Spectrum Sensing
6.1.1 Simulation Setup
In the simulations, we assume that all secondary users are experiencing i.i.d. Rayleigh fading without spatial correlation. Each secondary user uses an energy detector. We simulate the output Y of the energy detector directly in our simulations. When the primary user is absent, Y is a random quantity with chi-square distribution. When the primary user is present, Y may be denoted as the sum of two independent random variables [40, 41]. The parameters of Y depend on the average SNR in the Rayleigh fading (see (1.3) and (1.4)). The simulations are done in three test conditions. In the first condition, every user has the same average \({\textit{SNR}(\overline{\gamma})}\), which is 10 dB. In the second condition, each user has different average \({{\textit{SNR}(\overline{\gamma})}}\) varying from 5 dB to 9 dB. In the third condition, each user has different average \({{\textit{SNR}(\overline{\gamma})}}\) varying from 5 dB to 15 dB. The relevant information of primary users, such as the position, the moving direction and the moving velocity, is unknown to the secondary users.
We compare the performance of the proposed scheme with that of an existing OR-rule cooperative sensing scheme [21, 22, 45], which is better than AND-rule and MAJORITY-rule in many cases of practical interest [22, 46]. In the OR-rule cooperative sensing scheme, each secondary user makes local spectrum sensing decision, which is a binary variable – a “one” denotes the presence of a primary user, and a “zero” denotes its absence. Then, all of the local decisions are sent to a data collector to sum up all local decision values. If the sum is greater than or equal to 1, a primary user is believed to be present.
In the first stage of spectrum sensing, after time synchronization, every secondary user performs energy detection with \(T\!W=5\) individually to get local measurement \({Y_i}\) at the selected center frequency f s and the bandwidth of interest W. To set up the initial energy vector \(\boldsymbol{ X}(0)\), we set \(x_i(0)={Y_i}\).
In the second stage, the existing method and the proposed consensus algorithm (1.7) are conducted based on fixed graph models, while the proposed consensus algorithm (1.13) is run based on random graph models. For fixed graphs, the basic requirement is to set up duplex wireless channels. In the simulations, we consider a network topology with 10 secondary users that establish a graph, \(\boldsymbol{ G}=\{{\cal N},{\cal E}\}\), as shown in Fig. 1.4 a. For random graphs, we use the same set of nodes as in Fig. 1.4 b, but replace solid lines with dotted ones, which have probabilities of link failure of 40% (refer to Fig. 1.4 b). The links in those figures stand for bidirectional wireless links. With regard to link failure probabilities, they mean both directions will fail to work in case of link failure. We also consider a network topology with 50 nodes in the simulations, which is shown in Fig. 1.5. All of the 50 nodes are located randomly. The links in the 50-node network have probabilities of failure of 40%.
6.1.2 Convergence of the Consensus Algorithm
Figs. 1.6a and 1.6b show the estimated primary user energy in the network with a 10-node fixed graph. We can observe that, although the initially sensed energy varies greatly due to their different wireless channel conditions for different secondary nodes, a consensus will be reached after several iterations. The step size ε has effects on the convergence rate of the consensus algorithm. According to (1.7) and (1.13), a value should be selected for ε such that \(0 < \varepsilon < \varDelta^{-1}\). Since the maximum number of neighbors of a node in Figs. 1.4a and 1.4b is 5, \(\varDelta = 5\). Then, \(0 < \varepsilon < 0.2\).
Here we provide some discussion about the choice of the parameter ε. First, given the network topology, we may construct the associated Laplacian \(\boldsymbol{ L}\) as a \(10\times 10\) matrix. For reasons of space, \(\boldsymbol{ L}\) is not displayed. The eigenvalue of \(\boldsymbol{ L}\) are listed as follows:
On the interval \((0,\ 0.2)\), the spectral gap g(ε) may be shown to be
which monotonically decreases on (0, 0.2). We note that for this specific network topology, when \(\varepsilon=0.2\), the resulting matrix \(\boldsymbol{ P}= I-\varepsilon \boldsymbol{ L}\) is ergodic. On the interval \((0,0.2]\) the spectral gap is maximized at \(\varepsilon=0.2\).
In below we select two values for ε, 0.1 and 0.19, in Fig. 1.6 a and Fig. 1.6 b, respectively. We can see that the algorithm converges faster when \(\varepsilon = 0.19\) than that when \(\varepsilon = 0.1\), which is due to the fact that \(\varepsilon=0.19\) corresponds to a larger spectral gap g(0.19).
After about five iterations in Fig. 1.6 b, the difference between the nodes is less than 1 dB, which indicates that a consensus is achieved. Figure 1.7 shows the estimated primary user energy in the network with a random graph when \(\varepsilon = 0.19\). Comparing Fig. 1.7 with Fig. 1.6 b, we can see that the algorithm converges more slowly in the random graph case due to the random link failure in the CR network. In Fig. 1.7, after about 10 iterations, the difference between the nodes is less than 1 dB, which indicates that a consensus is achieved.
Figure 1.8 shows the convergence performance for the 50-node network. \(\varepsilon = 0.15\) is used. We can observe that the algorithm converges more slowly in the 50-node network compared to the 10-node network due to a larger number of nodes. Nevertheless, after about 30 iterations, the difference between the nodes is less than 1 dB, which indicates that a consensus is achieved.
In the rest of the simulations, we conduct the simulations in three scenarios. In scenario one, under each of the three test conditions, the simulations are conducted by using one of the existing methods and the proposed scheme, respectively. The purpose of this scenario is to evaluate the performance of the proposed scheme in terms of P m (probability of missing detection) and P f (probability of false alarm). In scenario two, we focus on test condition one, and try to find the best detection sensitivity for different algorithms. In scenario three, we also work on test condition one and set a fixed detection threshold λ as stated in (1.11) to simulate the real situation in practice.
6.1.3 Scenario One
We compare the performance of the proposed scheme with that of an existing OR-rule cooperative sensing scheme [21, 22, 46]. Before the comparison, let us discuss briefly the relationship between P m (probability of missing detection)\(= 1-{P_d}\) (probability of detection) and P f (probability of false alarm). The fundamental tradeoff between P m and P f has different implications in the context of spectrum sensing [5]. A high P m will result in the missing detection of primary users with high probability, which in turn increases the interference to primary users. On the other hand, a high P f will result in low spectrum utilization since false alarms increase the number of missed opportunities (white spaces). As expected, P f is independent of γ since under H 0 there is no primary signal.
Figures 1.9 and 1.10 show P f vs. P m . We can see that the proposed algorithm has better performance than the existing OR-rule cooperative sensing scheme. The numbers beside the curves are the corresponding thresholds λ in dB. In Fig. 1.9, where each secondary user has the same average SNR 10 dB, if the threshold λ is in the range of 11.4 to 12 dB, both P f and P m can simultaneously drop below the probability of 10−2 for the proposed consensus algorithm in both fixed and random graphs. Also, the results are the same between the fixed and random models. In comparison, to reach the same goal, the existing OR-rule method must set λ to be around 14.8 dB, which has far worse P m (10−2 vs. 10−3) with regard to the same P f level (10−2).
In condition two, secondary users undergo different average SNR varying from 5 dB to 9 dB. In condition three, secondary users undergo different average SNR varying from 5 dB to 15 dB. The similar results are demonstrated in Figs. 1.10 and 1.11 for conditions two and three, respectively.
6.2 Scenario Two
Next, we examine the performance of detection probabilities P d to find out the sensitivity in detecting the primary user’s presence. Figure 1.12 shows P d (detection probability = \(1-{P_m})\) vs. average SNR \(({\bar\gamma})\) of secondary users. Condition one is used in this scenario, and the simulation is performed when the average SNR varies from 5 to 10 dB for all the nodes. The decision threshold, λ, is chosen so as to keep \({P_{\!f}} = 10^{-1}\). Time-bandwidth product, TW, is set to be 5, which is the same as before. From Fig. 1.12, we see that the proposed scheme can have a significant improvement in terms of the required average SNR for detection. In particular, if the probability of detection is expected to be kept above 0.99 (or \({P_m} < 10^{-2})\), the existing spectrum sensing scheme requires \(\bar\gamma=7.8\) dB. This required average SNR is higher than those in the proposed consensus scheme, both of which are approximately 6.8 dB.
6.2.1 Scenario Three
In reality, it is unlikely to adjust the threshold λ on demand with regard to the different average SNR. Rather, a fixed threshold that can work in any \(\bar\gamma\) is much more desirable. We can call it as threshold robustness. Therefore, in this scenario, we use condition one and intend to set a pre-defined threshold λ by using (1.11) so as to achieve a certain goal. In fact, there are three options when we choose such a goal to keep missing detection probability (P m ) below a certain level, to keep false alarm probability P f around a certain level, or to keep both P m and P f as low as possible.
We first try to keep P m below 10−2 when all the 10 users undergo the same \(\overline{\gamma}\) varying from 5 to 10 dB. Fig. 1.13 a shows a fixed λ that lets P m below 10−2 for the average SNR ranging from 5 to 10 dB. As the result, the worst P f decreases from 0.586 by using the existing method to 0.356 in both the random graph and the fixed graph by using the proposed scheme.
Results in simulation scenario three: Part One. (a) Missing detection probability (P m ) and false alarm probability (P f ) vs. average SNR \((\overline{\gamma})\) with fixed threshold λ to keep P m below 10−2, when all the ten users undergo same \(\overline{\gamma}\) varying from 5 to 10 dB and (b) Missing detection probability (P m ) and false alarm probability (P f ) vs. average SNR \((\overline{\gamma})\) with fixed threshold λ to keep P f below 10−1, when all the ten users undergo same \(\overline{\gamma}\) varying from 5 to 10 dB
The second option is to let P f always around 10−1 when all the 10 users undergo \(\overline{\gamma}\) varying from 5 to 10 dB. The result is shown in Fig. 1.13 b, where P f keeps around 10−1. The proposed consensus algorithm has the better performance in terms of P m , down from 0.161 in the existing method to 0.0527 in the proposed method.
Results in simulation scenario three: Part Two. (a) Missing detection probability (P m ) and false alarm probability (P f ) vs. threshold λ in dB when same \(\overline{\gamma}=5\mathrm{dB}\) for all users. (b) Missing detection probability (P m ) and false alarm probability (P f ) vs. average SNR \((\overline{\gamma})\) with fixed threshold λ to keep both P m and \(P_{\!f}\) below a certain level, when all the 10 users undergo same \(\overline{\gamma}\) varying from 5 to 10 dB
In the third option, keep both P m and P f as low as possible. When determining a threshold, we refer to Fig. 1.14 a, which shows the worst case when all the 10 users suffers \(\overline\gamma=5\) dB. For the consensus scheme to have better missing detection performance, the threshold chosen in the proposed scheme should be lower than that in the OR-rule scheme. In Fig. 1.14 a, we can see that, with the same missing detection probability, the threshold is lower in the proposed scheme than that in the OR-rule scheme. On the other hand, with this lower threshold, a better false alarm probability can be achieved in the proposed scheme. The reason is that, when there is no primary user, the output of the energy detector, Y, of each secondary user is a random quantity with central chi-square distribution (see (1.2)). Since Y varies greatly, it is easy for a secondary user to have a false alarm in the OR-rule scheme. By contrast, the consensus scheme does not use the raw data Y to make decisions. Instead, it uses the consensus among the secondary users to make decisions, thus it can remove some randomness in the raw data Y. Therefore, the consensus scheme can have a better false alarm probability than the OR-rule scheme with the same threshold. This can be shown in Fig. 1.14 a. From Fig. 1.14 a, we can also observe that both missing detection and false alarm probabilities are low when the threshold is round 11 dB for the consensus scheme and when the threshold is around 13.6 dB for the OR-rule scheme. In Fig. 1.14 a, if we compare the performance of the consensus scheme with a threshold 11 dB to that of the OR-rule scheme with a threshold 13.6 dB, we can see that both missing detection and false alarm probabilities are lower in the consensus scheme than those in the OR-rule scheme. We choose \(\lambda=11\) dB for the proposed consensus algorithm and \(\lambda=13.6\) dB for the existing method to conduct our numerical studies. Fig. 1.14 b illustrates the result of such a fixed λ. It is seen that both P m and P f have better performance for the proposed algorithm than those of the existing method. P m and P f drops to a relatively low level. This highlights the overall advantage in so-called threshold robustness for the proposed consensus algorithm. That is, for a given \({\lambda}\), the proposed consensus algorithm can output less P m and P f than those of the existing method. The algorithm works well in both fixed graphs and random ones. Another observation in scenario three is, when the average SNR rises, P m drops for a given threshold λ, but P f remains more or less at the same level. This means, for a fixed λ, P m is subject to the change of the average SNR. In contrast, P f is stable, because this parameter deals with the condition of H 0, where only the collective noises exist.
7 Conclusion
In this chapter, we have presented a fully distributed and scalable scheme for spectrum sensing based on recent advances in consensus algorithms. Cooperative spectrum sensing is modeled as a multi-agent coordination problem. Secondary users can maintain coordination based on only local information exchange without a centralized receiver. Simulation results were presented to show the effectiveness of the proposed consensus-based scheme. It is shown that both missing detection probability and false alarm probability can be significantly reduced in the proposed scheme compared to those in the existing schemes.
Also, as the real network topologies undergo random changes and the primary user may randomly enter and leave the network, a protocol is necessary to quickly decide when the consensus is considered to be practical reached. If the secondary users cannot efficiently form a decision in finite steps, the energy measurements obtained at the beginning may become obsolete. To address this finite time detection issue, in implementations a certain toleration threshold may be used by the users. A secondary user may stop the iteration if it finds the difference between the states of each neighbor and itself has fallen below the threshold. The choice of threshold depends on empirical studies. Our simulation indicates that the threshold may be chosen to be around a fraction of 1 dB or close to 1 dB.
One limitation of the proposed scheme is that the choice of the step size ε depends on the maximum number of neighbors of a node in the network. In other words, each node needs to have the prior knowledge of an upper bound of the maximum degree of the network. To solve this problem, an alternative approach may be used, which is based on so-called Metropolis weights [34]. This approach does not need the knowledge of the maximum degree of the network. Future work is in progress in this direction. We also want to simplify the data format of detection statistics from each secondary user to save the wireless bandwidth. In addition, as energy detection does not work well for spread spectrum signals, other approaches will be studied to deal with such networks.
Notes
- 1.
For some network topologies, it is possible to have an ergodic matrix \(P= I-\varepsilon L\) when \(\varepsilon =1/{\varDelta}\). For instance, if ε is taken as \({1}/{\varDelta}\) and meanwhile it is ensured that P has at least one positive diagonal entry, then it can be shown that P is an ergodic stochastic matrix.
References
J. Mitola, Cognitive radio: An integrated agent architecture for software defined radio. Doctor of Technology Thesis, Royal Inst. Technol. (KTH), Stockholm, Sweden, 2000.
G. Ganesan and Y. Li, “Cooperative spectrum sensing in cognitive radio, part I: Two user networks,” IEEE Trans. Wireless Commun., vol. 6, pp. 2204–2213, 2007.
S. Haykin, “Cognitive radio: Brain-empowered wireless communications,” IEEE J. Sel. Areas Commun., vol. 23, pp. 201–220, 2005.
C. Sun, W. Zhang, and K. B. Letaief, “Cluster-based cooperative spectrum sensing in cognitive radio systems,” in Proc. IEEE ICC’07, pp. 2511–2515, 2007.
A. Ghasemi and E. Sousa, “Collaborative spectrum sensing for opportunistic access in fading environments,” in Proc. IEEE DySPAN’05, pp. 131–136, 2005.
D. Cabric, S. Mishra, and R. Brodersen, “Implementation issues in spectrum sensing for cognitive radios,” in Proc. Thirty-Eighth Asilomar Conference on Signals, Systems and Computers, vol. 1, pp. 772–776, 2004.
J. Hillenbrand, T. Weiss, and F. Jondral, “Calculation of detection and false alarm probabilities in spectrum pooling systems,” IEEE Commun. Lett., vol. 9, no. 4, pp. 349–351, 2005.
J.-F. Chamberland and V. V. Veeravalli, “Wireless sensors in distributed detection applications,” IEEE Signal Proc. Mag., vol. 24, pp. 16–25, 2007.
R. Niu and P. Varshney, “Performance analysis of distributed detection in a random sensor field,” IEEE Trans. Signal Proc., vol. 56, no. 1, pp. 339–349, 2008.
V. Veeravalli, “Decentralized quickest change detection,” IEEE Trans. Inform. Theory, vol. 47, no. 4, pp. 1657–1665, 2001.
S. Mishra, A. Sahai, and R. Brodersen, “Cooperative sensing among cognitive radios,” in Proc. IEEE ICC’06, pp. 1658–1663, 2006.
W. Ren, R. Beard, and E. Atkins, “A survey of consensus problems in multi-agent coordination,” in Proc. American Control Conference’05, pp. 1859–1864, 2005.
J. Mitola and G. Q. Maguire, “Cognitive radio: Making software radios more personal,” IEEE Pers. Commun., vol. 6, pp. 13–18, 1999.
I. Akyildiz, W. Lee, M. Vuran, and S. Mohanty, “Next generation/dynamic spectrum access/cognitive radio wireless networks: A survey,” Comput Networks, vol. 50, no. 13, pp. 2127–2159, 2006.
G. Ganesan and Y. Li, “Cooperative spectrum sensing in cognitive radio - part II: Multiuser networks,” IEEE Trans. Wireless Commun., vol. 6, pp. 2214–2222, 2007.
G. Ganesan and Y. G. Li, “Agility improvement through cooperative diversity in cognitive radio,” in Proc. IEEE GLOBECOM’05, pp. 2505–2509, 2005.
E. Peh and Y.-C. Liang, “Optimization for cooperative sensing in cognitive radio networks,” in Proc. IEEE WCNC’07, pp. 27–32, 2007.
J. Unnikrishnan and V. V. Veeravalli, “Cooperative sensing for primary detection in cognitive radio,” IEEE J. Sel. Topics Signal Proc., vol. 2, no. 1, pp. 18–27, 2008.
Z. Quan, S. Cui, and A. H. Sayed, “Optimal linear cooperation for spectrum sensing in cognitive radio networks,” IEEE J. Sel. Topics Signal Proc., vol. 2, no. 1, pp. 28–40, 2008.
Y.-C. Liang, Y. Zeng, E. Peh, and A. T. Hoang, “Sensing-throughput tradeoff for cognitive radio networks,” IEEE Trans. Wireless Commun., vol. 7, no. 4, pp. 1326–1337, 2008.
R. Chen, J.-M. Park, and K. Bian, “Robust distributed spectrum sensing in cognitive radio networks,” in Proc. INFOCOM 2008. The 27th Conference on Computer Communications. IEEE, pp. 1876–1884, 2008.
W. Zhang and K. Ben Letaief, “Cooperative communications for cognitive radio networks,” Proc. IEEE, vol. 97, no. 5, pp. 878–893, 2009.
C. S. R. Murthy and B. S. Manoj, Ad Hoc Wireless Networks: Architectures and Protocols. Upper Saddle River, NJ: Prentice Hall, 2004.
T. Nakano and T. Suda, “Applying biological principles to designs of network services,” Appl. Soft Comput., vol. 7, no. 3, pp. 870–878, 2007.
I. Carreras, I. Chlamtac, F. D. Pellegrini, and D. Miorandi, “Bionets: Bio-inspired networking for pervasive communication environments,” IEEE Trans. Veh. Technol., vol. 56, pp. 218–229, 2007.
F. Dressler, Ö. B. Akan, and A. Ngom, “Guest Editorial - Special Issue on Biological and Biologically-inspired Communication,” Springer Trans. on Computational Systems Biology (TCSB), vol. LNBI 5410, 2008.
R. Olfati-Saber, J. Fax, and R. Murray, “Consensus and cooperation in networked multi-agent systems,” Proc. IEEE, vol. 95, no. 1, pp. 215–233, 2007.
J.-M. Amé, J. Halloy, C. Rivault, C. Detrain, and J. L. Deneubourg, “Collegial decision making based on social amplification leads to optimal group formation,” Proc. Natl. Acad. Sci., vol. 103, no. 15, pp. 5835–5840, 2006.
L. Conradt and T. J. Roper, “Consensus decision making in animals,” Trends Ecol. Evol., vol. 20, pp. 449–456, 2005.
T. Vicsek, “A question of scale,” Nature, vol. 441, p. 421, 2001.
I. D. Couzin, “Collective cognition in animal groups,” Trends Cogn. Sci., vol. 13, pp. 36–43, 2008.
P. K. Visscher, “How self-organization evolves?” Nature, vol. 421, pp. 799–800, 2003.
W. Ren and R. Beard, “Consensus seeking in multiagent systems under dynamically changing interaction topologies,” IEEE Trans. Auto. Control, vol. 50, no. 5, pp. 655–661, 2005.
L. Xiao, S. Boyd, and S. Lall, “A scheme for robust distributed sensor fusion based on average consensus,” in Proc. Fourth International Symposium on Information Processing in Sensor Networks, pp. 63–70, 2005.
M. Huang and J. H. Manton, “Stochastic consensus seeking with measurement noise: Convergence and asymptotic normality,” in Proc. American Control Conference’08, pp. 1337–1342, 2008.
W. Irving and J. Tsitsiklis, “Some properties of optimal thresholds in decentralized detection,” IEEE Trans. Auto. Control, vol. 39, no. 4, pp. 835–838, 1994.
J. Proakis and M. Salehi, Digital Communications. New York, NY: McGraw-hill 1995.
A. Sahai, N. Hoven, and R. Tandra, “Some fundamental limits on cognitive radio,” in Allerton Conference on Communication, Control, and Computing, Citeseer, 2004.
H. Urkowitz, “Energy detection of unknown deterministic signals,” Proc. IEEE, vol. 55, no. 4, pp. 523–531, 1967.
F. Digham, M.-S. Alouini, and M. Simon, “On the energy detection of unknown signals over fading channels,” in Proc. IEEE ICC’03, vol. 5, pp. 3575–3579, 2003.
V. Kostylev, “Energy detection of a signal with random amplitude,” in IEEE Proc. ICC’02, vol. 3, pp. 1606–1610, 2002.
M. Huang and J. H. Manton, “Coordination and consensus of networked agents with noisy measurements: Stochastic algorithms and asymptotic behavior,” SIAM J. Control and Optimization, vol. 48, pp. 134–161, 2009.
C. Godsil and G. Royle, Algebraic Graph Theory. New York, NY: Springer, 2001.
E. Seneta, Non-negative Matrices and Markov Chains. New York, NY: Springer, 1981.
L. Elsner, I. Koltracht, and M. Neumann, “On the convergence of asynchronous paracontractions with applications to tomographic reconstruction from incomplete data,” Linear Algebra and its Applications, vol. 130, pp. 65–82, 1990.
A. Ghasemi and E. Sousa, “Opportunistic spectrum access in fading channels through collaborative sensing,” J Commun, vol. 2, no. 2, p. 71, 2007.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2011 Springer Science+Business Media, LLC
About this chapter
Cite this chapter
Yu, F.R., Tang, H., Huang, M., Mason, P., Li, Z. (2011). Distributed Consensus-Based Cooperative Spectrum Sensing in Cognitive Radio Mobile Ad Hoc Networks. In: Yu, F. (eds) Cognitive Radio Mobile Ad Hoc Networks. Springer, New York, NY. https://doi.org/10.1007/978-1-4419-6172-3_1
Download citation
DOI: https://doi.org/10.1007/978-1-4419-6172-3_1
Published:
Publisher Name: Springer, New York, NY
Print ISBN: 978-1-4419-6171-6
Online ISBN: 978-1-4419-6172-3
eBook Packages: EngineeringEngineering (R0)