Abstract
The Internet of Things (IoT) creates an environment where things are permitted to act, hear, listen, and talk. IoT items can be anything, from simple sensors to smart devices, that can exchange information with or without human intervention. Although wireless knots have positive effects, their use poses some challenges. The main concern with this technology is the limited availability of resources, including storage, processing power, and energy. Among all the challenges, energy Using up poses the most significant challenge. A common method of addressing this issue is to design optimal routing patterns using exploratory methods. This article offers an algorithm for clustering dense, randomly distributed, and heterogeneous IoT networks based on the Water-Cycle Algorithm called CC-WCA. Clustering and Software-defined networking (SDN) are combined with the WCA algorithm to achieve enhanced efficiency. Model results indicate that CC-WCA performs better than previous methods regarding energy using up, throughput, and lattice longevity.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
Introduction
In recent years, as software has matured along with 5G communication technology, mobile devices, such as smartphones, have gradually gained popularity, and Internet of Things (IoT) technology has developed in tandem (Mohseni et al. 2022). Every aspect of our lives is touched by IoT, from building automation to wearable technology (Pourghebleh et al. 2022). IoT technology provides a means to visualize and represent raw data digitally. Digital visualization facilitates access to heterogeneous devices, ranging from tiny sensors to large-scale cloud computing systems (Pourghebleh et al. 2020). IoT offers ubiquitous connectivity to devices and resources via wireless networks without external infrastructure or computation resources (Pourghebleh and Hayyolalam 2019). The connected devices and service providers utilize the common Internet platform for this purpose (Pourghebleh et al. 2019). In this respect, wireless sensor networks (WSNs) contribute to the expansion of networks by providing low-cost and easy-to-install smart devices (Reddy et al. 2022). WSNs have gained attention in recent years for use in various fields, such as military applications, disaster prediction, and environmental monitoring. In these networks, the knots’ battery capacity and processing power are limited (Zhu and Wang 2022).
Each item in IoT environments has a unique identifier that allows them to connect to the internet (Attiya et al. 2022). Among the primary objectives in this regard is to enable anyone and anything to share information services anywhere and at any time (Sellami et al. 2022). The IoT paradigm provides individuals access to anyone and everything, regardless of location (Kandan et al. 2022). Consequently, routing protocols play a crucial role in the transmission of data between heterogeneous items (Reddy et al. 2022). Data transmission in such environments is time-sensitive to ensure the message reaches the intended recipient within the specified period. Therefore, it is essential to route data packets in such a way that the shortest path to the target is taken (Praveen and Prathap 2021).
Multiple major energy concerns are associated with this type of structure since, in many applications, either the knots of the network cannot be reached or cannot be replaced (Srinadh and Rao 2022). The transmission of data in wireless communications contains a greater amount of energy than processing; hence, routing and transmission of data are extremely important in wireless networks (Cao et al. 2022). Energy can be saved through clustering. The process of clustering involves the division of knots into groups. In every cluster, there is a Cluster Head (CH) and multiple Cluster Members (CMs) (Rahmani et al. 2021). CMs sense the environmental information and transmit it to CHs. CHs are responsible for collecting and integrating data from the CMs and transmitting them to the base station. The problem of clustering in WSN-enabled IoT is NP-hard. These challenges have been addressed through the use of computational intelligence. Different computational intelligence methods have been employed in WSN routing, including evolutionary algorithms (EAs). Many optimization problems have been solved using EAs. In recent years, algorithms were suggested as optimization algorithms like PSO (particle swarm optimization), DE (differential evolution), and GA (genetic algorithm) (Jesudurai and Senthilkumar 2019).
The currently available clustering mechanisms are primarily time-driven. There are three types of mechanisms: static, dynamic, and hybrid. Static clustering involves clustering initially, followed by CH rotation. A static performance network has a low overhead and is stable for a short period. Static methods have the disadvantage of discharging energy at Multiple knots. Clustering is carried out at each round in the dynamic method. One of the most well-known dynamic approaches is the LEACH (low-energy adaptive clustering hierarchy). Dynamic performance increases the network’s longevity, but its overhead is high. The hybrid method improves stability and lifespan while simultaneously reducing operational costs.
Clustering can be accomplished using either static or dynamic approaches. Clustering is carried out in a series of rounds, followed by forming new clusters. A CH rotation is also performed after each clustering round and the formation of new clusters. These time-oriented strategies are opposed to energy-oriented ones. The suggested approach differs from time-oriented approaches such as LEACH, in which CHs are chosen in advance of each round. In this way, overhead is greatly reduced. An abstract of existing techniques is offered in Table 1.
The paper offers an algorithm for clustering dissimilar and randomly distributed IoT knots based on the Water Cycle Algorithm (WCA) called CC-WCA. Clustering and Software-Defined Networking (SDN) are combined with the WCA algorithm to achieve enhanced efficiency. CC-WCA comprises two stages, deployment, and transmission. During the deployment stage, the network area is split into virtual zones in order to distribute CHs evenly on the basis of the density of knots and the geographical magnitude of the network. To formulate a cluster, WCA chooses the optimal set of CHs. The SDN controller provides a TDMA schedule. The CMs transmit information to the CHs during the transmission stage.
The main objective of the study is to design an optimal routing pattern that addresses the issue of energy consumption in IoT networks. The novelty of the study lies in the use of a clustering algorithm based on the WCA and SDN to achieve enhanced efficiency.
The main contribution of this study is the development of a novel algorithm called CC-WCA for clustering dense, randomly distributed, and heterogeneous IoT networks. The use of clustering and SDN in combination with the WCA algorithm is a novel approach that has not been explored extensively in previous studies. The model results indicate that the CC-WCA algorithm outperforms previous methods in terms of energy consumption, throughput, and network longevity.
Related work
Based on network characteristics, Said (2017) offers a mechanism for dividing the IoT environment into various zones. Then, it applies the ACO algorithm to the areas in order to resolve the routing issue. Based on the results of NS2, it is evident that the suggested routing algorithm achieves the desired energy Using up, packet loss rate, latency, bandwidth Using up, and overhead. A clustering scheme suggested by Fouladlou and Khademzadeh (2017) utilizes the GA to cluster IoT objects in order to develop an effective routing approach and extend the longevity of a network. Experiments have demonstrated that the suggested scheme performs more efficiently than IEEE 802.15.4 protocol with respect to transmission rate, energy use up, delay, and bit error rate.
A novel routing protocol to minimize the energy using up of WSNs was presented by Fouladlou and Khademzadeh (2017). The genetic algorithm is used to organize sensor devices into clusters to facilitate effective routing and extend network lifespan. The experimental results provide evidence that the protocol outperforms the IEEE 802.15.4 protocol regarding latency, energy Using up, and data transmission rate.
Thangaramya and Kulothungan (Thangaramya et al. 2019) suggested an optimized routing strategy based on neuro-fuzzy rules for IoT-based wireless sensor networks. Experiments conducted in this study have demonstrated that the patterned routing protocol performs well regarding network lifespan, latency, delivery rate, and energy Using up.
The advanced cluster-head selection method by Yousefi and Derakhshan (Yousefi et al. 2020) has two primary steps. At the initial step, the ABC algorithm determines the nearly optimal CHs. For selecting the appropriate CH, Euclidean distance among devices, the number of neighbors of each device, and the residual energy of each device are considered. In the second step, devices are organized into clusters according to the volume of data produced by each cluster and the Euclidean space among the CH and its members. The findings of the study demonstrate that the suggested approach improves transmission delay, longevity, and energy Using up.
Yarinezhad and Sabaei (2021) propose a novel clustering approach that balances traffic loads on CHs in IoT-enabled wireless sensor lattices. The suggested clustering technique employs a 1.2 approximation technique. The authors also propose an energy-aware routing scheme to transmit packets of data from CHs to intended destinations. With an appropriate segmentation of the region, the scheme distributes the computational load more evenly among more knots located near the destination. Statistical analysis indicates that the scheme is suitable for large-scale IoT-enabled WSNs and boosts the network’s performance compared with other similar algorithms.
Gulganwa and Jain (2022) propose an energy-efficient and secure weighted clustering algorithm called EES-WCA for WSNs. The algorithm incorporates a machine learning approach to improve the clustering process and ensure the security of the network. The proposed algorithm is compared with existing clustering algorithms, and the results show that the EES-WCA algorithm outperforms these methods in terms of energy efficiency, network lifetime, and security. The study demonstrates the potential of machine learning techniques in improving the performance and security of WSNs and highlights the importance of developing energy-efficient and secure clustering algorithms for WSNs.
Yadawad and Joshi (2023) presents an energy-efficient data aggregation and cluster-based routing method for WSNs that uses the Tasmanian fully recurrent deep learning network with Pelican (TFRDL-Pelican) algorithm. The proposed method combines the advantages of data aggregation and cluster-based routing to reduce the energy consumption of WSNs while maintaining the quality of the data. The TFRDL-Pelican algorithm uses a deep learning approach to predict the data values and reduce the amount of data transmitted. The proposed method is compared with other clustering and routing algorithms, and the results show that the TFRDL-Pelican algorithm outperforms these methods in terms of energy efficiency, data accuracy, and network lifetime.
Jagdale et al. (2023) propses a data reduction technique for the IoT that uses optimal cluster-based topology and a deep Long Short-Term Memory (LSTM) prediction method. The proposed method aims to reduce the amount of data transmitted in IoT networks while maintaining the accuracy of the data. The clustering algorithm groups the IoT devices into clusters based on their spatial proximity, and the LSTM prediction model predicts the future values of the sensor data based on their past values. The experimental results show that the proposed method achieves significant data reduction while maintaining the accuracy of the data, thereby reducing the energy consumption and improving the network lifetime of IoT systems.
Water-cycle algorithm
WCA originated from natural phenomena and observations that rivers and streams are generally directed downwards toward the sea. Water forms rivers or streams whenever it moves downhill from one location to another. The vast majority of rivers originate in the mountains, where snow and ancient glaciers melt. Water is collected by rainwater and other flows as they travel downhill and eventually end up at sea (Nasir et al. 2020).
WCA begins with a population known as raindrops, as with other meta-exploratory algorithms. Initially, it is totaled that precipitation has occurred. Each particle (raindrop) is elected as a sea. Multiple high-quality raindrops are chosen as rivers, and the remaining ones are treated as streams entering rivers and oceans. Rivers absorb water from streams according to the magnitude of flow described in the following subsections. As a matter of fact, the amount of water in a stream that enters a river or sea differs from the amount of water in other streams. Additionally, rivers flow towards the sea, which illustrates the lowest point on a slope.
Problem variables must be represented as arrays in order to be solved using population-based meta-exploratory algorithms. Such an array is referred to as a ‘’Chromosome’’ in GA terminology and a ‘’Particle Position’’ in PSO. Thus, in the suggested method, raindrops are referred to as a single solution. In a Nvar dimensional optimization problem, a raindrop illustrates a set of multidimensional variables as follows:
As a first step in the optimization process, candidates corresponding to raindrops of magnitude \(N_{{pop}} \times N_{{var}}\) are produced. Therefore, matrix X is created at random, in which the rows represent some of the columns, and the population stands for several design variables.
For continuous and discrete problems, decision variables (x1, x2, …, Nvar) are typically expressed as a numeric value or a set of values. Raindrop costs are determined by evaluating the cost function (C) as follows.
where Npop illustrates some of the raindrops and Nvars represent some of the design variables. In the initial stage, Npop raindrops are generated. The best Nsrs (lowest values) constitute seas and rivers. Raindrops with the lowest value are considered seas. As indicated in Eq. 4, Nsr illustrates the total of some rivers and a single sea. The remainder of the population, i.e., raindrops that form rivers or flow straightly into the sea, is computed using Eq. 5.
Based on the flow intensity, Eq. 6 can be considered to attribute raindrops to rivers and seas.
Nsr illustrates the number of streams flowing into a specific river or sea.
Suggested routing patterns
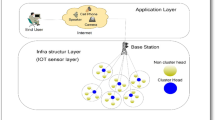
CC-WCA routing method is described in this section. During CH selection, the Graphical Position System sends the coordinates of all the knots to the cloud for use by the SDN controller. CC-WCA maintains a balanced number of CHs in accordance with the distribution of knots within an area. Figure 1 illustrates how CC-WCA separates the data and control domains by utilizing SDN technology. There are three main layers in the suggested IoT structure, namely application, control, and infrastructure. The application layer sits above the cloud and is intended for use in business-related operations. Control decisions, specifically those concerning the protocol, are handled by the SDN controller, which is located at the manage layer. A wide variety of knots are present at the infrastructure layer, which performs only packet-forwarding functions. In addition, the SDN controller takes advantage of cloud resources, including data centers and storage, to perform complex computations.
Using the SDN controller, the area of sensing is logically divided into four Virtual Zones (VZs), and the knots are grouped according to their coordinates into four subgroups (SGs). The division of CHs into geographical areas leads to an equal distribution of CHs; consequently, the zone with the more knots is allocated more CHs in comparison with other zones. Once the WCA is implemented for each SGi, the SDN controller determines the optimum group of CHs in the VZi (see Fig. 2).
Initially, WCA generates solutions randomly for each VZ; each solution illustrates a unique ID for each CH. The seek agents (solutions) then adjust their situations at each iteration or in accordance with the optimal solution acquired earlier or a randomly selected solution. The fitness of each solution is then examined using Eq. 7.
where coefficients α and β are given in Table 1, according to Table 2, K illustrates the number of CHs. A set of CHs possessing the highest level of energy is selected using Eq. 8. A communication cost between the CHs and the CMs is included in the function f2 in Eq. 9. Moreover, Eq. 10 is used to select the set of CHs that are most likely to cover a given number of knots. During the selection of CHs, the SDN controller utilizes data provided by the knots that are saved in the cloud. The SDN controller sends an optimum set of CHs and their CMs to the sink so that they can be forwarded to the knots as a set-up table. Once this has been accomplished, each CM turns on or off its radio as directed by its CH according to the TDMA schedule. In the cluster formulation procedure, the knots connect to a nearby CH, where the SDN controller selects the closest CH from the adjustment table. In the suggested manners, the energy dissipation is calculated using the first-order radio pattern suggested in (Heinzelman et al. 2002). In this pattern, the energy exhaustion of the node during transmission (ETX), reception (ERX), and data aggregation (EDA) are examined. Knots dissipate energy by transmitting or receiving bits as follows:
Experimental results
The network consists of 200 sensor knots broadcasted in an accidental way over a region of 200 m by 200 m. Each node is allocated a primary energy ranging from 0.4 to 1 J. Additionally, the network is analyzed using a single sink node with unrestricted storage, processing, and power resources. Other parameters for WCA and radio model are listed in Table 2 and 3. Models are conducted using MATLAB. CC-WCA protocol has been compared with conventional clustering approaches, including PSO-C, SEP, and LEACH, for the characteristics of throughput, energy Using up, and network longevity.
A comparison between the network longevity of the CC-WCA and those of other approaches is shown in Fig. 3. As compared to other clustering protocols, our method provides a longer lifespan for the network. Because the WCA considers the partition of the detection region by the SDN controller into VZs, the density of knots, the communication costs, and the remaining energy of knots. An illustration of the packs being sent to the go-down over model rounds can be found in Fig. 4. In comparison with traditional clustering protocols, approximately 50% more packets have been obtained by the sink during pretending time. It is because CC-WCA has improved lattice longevity in comparison with other protocols. As shown in Fig. 5, the suggested protocol demonstrates an effective way to distribute energy Using up among all knots during a given period, thereby increasing network lifespan. This optimum pattern is due to the coverage area and the sensing area’s division into four VZs.
Consequence
This article suggested a cluster-based routing protocol based on WCA. In accordance with the SDN idea, this protocol separates data forwarding and control planes. The sensing area is divided into VZs by the SDN controller. When selecting CHs, the WCA incorporates the primary energy and connection costs. The experimental outcomes indicate that our method outperforms previous methods for energy Using up, throughput, and network longevity. Since this work is primarily concerned with static networks, it is planned to incorporate the region source routing protocol into mobile networks. Furthermore, further research will examine theoretical aspects of network longevity maximization, including network overloads caused by routing protocols.
References
Attiya, I., et al.: An improved hybrid swarm intelligence for scheduling iot application tasks in the cloud. IEEE Trans. Industr. Inf. 8, 6264–6272 (2022)
Cao, K., et al.: Enhancing physical layer security for IoT with non-orthogonal multiple access assisted semi-grant-free transmission. IEEE Internet of Things J. 9, 24669–24681 (2022)
Fouladlou, M., Khademzadeh, A.: An energy efficient clustering algorithm for Wireless Sensor devices in internet of things. In: 2017 Artificial Intelligence and Robotics (IRANOPEN). IEEE (2017)
Gulganwa, P., Jain, S.: EES-WCA: energy efficient and secure weighted clustering for WSN using machine learning approach. Int. J. Inform. Technol. 14(1), 135–144 (2022)
Heinzelman, W.B., Chandrakasan, A.P., Balakrishnan, H.: An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wireless Commun. 1(4), 660–670 (2002)
Jagdale, B.N., Sugave, S.R., Kulkarni, Y.R.: Optimal cluster-based topology and deep LSTM-based prediction method for data reduction in IoT. J. Uncertain Syst. (2023). https://doi.org/10.1142/S1752890923500046
Jesudurai, S.A., Senthilkumar, A.: An improved energy efficient cluster head selection protocol using the double cluster heads and data fusion methods for IoT applications. Cogn. Syst. Res. 57, 101–106 (2019)
Kandan, M., et al.: Quasi oppositional aquila optimizer-based task scheduling approach in an IoT enabled cloud environment. J. Supercomput. (2022). https://doi.org/10.1007/s11227-022-04311-y
Mohseni, M., Amirghafouri, F., Pourghebleh, B.: CEDAR: a cluster-based energy-aware data aggregation routing protocol in the internet of things using capuchin search algorithm and fuzzy logic. Peer-Peer Netw. Appl. (2022). https://doi.org/10.1007/s12083-022-01388-3
Nasir, M., et al.: A comprehensive review on water cycle algorithm and its applications. Neural Comput. Appl. 32(23), 17433–17488 (2020)
Pourghebleh, B., Hayyolalam, V.: A comprehensive and systematic review of the load balancing mechanisms in the internet of things. Cluster Comput. (2019). https://doi.org/10.1007/s10586-019-02950-0
Pourghebleh, B., Wakil, K., Navimipour, N.J.: A comprehensive study on the trust management techniques in the internet of things. IEEE Internet Things J. 6(6), 9326–9337 (2019)
Pourghebleh, B., Hayyolalam, V., Anvigh, A.A.: Service discovery in the internet of things: review of current trends and research challenges. Wireless Netw. 26(7), 5371–5391 (2020)
Pourghebleh, B., et al.: A roadmap towards energy-efficient data fusion methods in the internet of things. Concurr Computation Pract. Exp. 34, e6959 (2022)
Praveen, K., Prathap, P.: Energy efficient congestion aware resource allocation and routing protocol for iot network using hybrid optimization techniques. Wireless Pers. Commun. 117(2), 1187–1207 (2021)
Rahmani, A.M., Babaei, Z., Souri, A.: Event-driven IoT architecture for data analysis of reliable healthcare application using complex event processing. Cluster Comput. 24(2), 1347–1360 (2021)
Reddy, C.S., et al.: Geographic routing scheme for resource and communication efficiency in the IoT ecosystem using swarm-intelligence based BFO algorithm. J. Inform. Technol. Manage. 14(1), 41–64 (2022)
Said, O.: Analysis, design and model of internet of things routing algorithm based on ant colony optimization. Int. J. Commun Syst. 30(8), e3174 (2017)
Sellami, B., et al.: Energy-aware task scheduling and offloading using deep reinforcement learning in SDN-enabled IoT network. Comput. Netw. 210, 108957 (2022)
Srinadh, V., Rao, P.N.: Implementation of dynamic resource allocation using adaptive fuzzy multi-objective genetic algorithm for IoT based cloud system. In 4th International Conference on Smart Systems and Inventive Technology (ICSSIT). 2022. IEEE. (2022)
Thangaramya, K., et al.: Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT. Comput. Netw. 151, 211–223 (2019)
Yadawad, S., Joshi, S.M.: Energy-efficient data aggregation and cluster-based routing in wireless sensor networks using tasmanian fully recurrent deep learning network with pelican variable marine predators algorithm. J. Interconnect. Netw. 23, 2350005 (2023)
Yarinezhad, R., Sabaei, M.: An optimal cluster-based routing algorithm for longevity maximization of internet of things. J. Parallel Distrib. Comput. 156, 7–24 (2021)
Yousefi, S., et al.: An energy-efficient artificial bee colony-based clustering in the internet of things. Comput. Electr. Eng. 86, 106733 (2020)
Zhu, F., Wang, W.: A distributed unequal clustering routing protocol based on the improved sine cosine algorithm for WSN. J. Sens. (2022). https://doi.org/10.1155/2022/7382098
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Xue, H., Zhang, Z. & Zhang, Y. A novel cluster-based routing protocol for WSN-enabled IoT using water-cycle algorithm. Proc.Indian Natl. Sci. Acad. 89, 724–730 (2023). https://doi.org/10.1007/s43538-023-00184-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s43538-023-00184-8