Abstract
Position and time information provided by the satellite navigation system is important in many application fields. However, the satellite navigation signal is vulnerable to interference signals due to the low navigation signal strength. This interference signal for the satellite navigation signal is being advanced to the spoofing signal, which can adjust the position and time information of the satellite navigation receiver, beyond simple jamming signal. To ensure the safe use of satellite navigation signals in the future, it is necessary to prepare for attacks by such spoofing signals. It is possible to reduce the damage to users of satellite navigation by early detection of the spoofing signals. For spoofing signals, the detection method should be applied according to the attack method, and various detection methods should be applied because the impact of the attacker on the receiver may vary depending on the attack method and attack item. In this study, we propose a method to detect the spoofing signal when the signal is induced based on the satellite navigation correction data and measurement value. The proposed detection method is advantageous in that it can be applied to a receiver directly because the spoofing signal can be detected without being equipped with additional hardware in a conventional receiver. Additionally, this method can be applied to a mobile receiver as well as a fixed receiver. It is expected that the proposed technique will increase the usefulness and reliability of the satellite navigation system.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
As the importance of position and time information grows in various fields, Global Navigation Satellite System (GNSS) is being widely used and GNSS-based applications are being gradually expanded [1]. In particular, ensuring signal stability and reliability is emerging as an important issue as satellite navigation systems are being applied to important systems in the society. GNSS receivers may exhibit errors due to failures or increasing error components, and may be subjected to intentional attacks for various purposes, including military and economic reasons [2]. Attacks on satellite navigation systems are performed in the form of signal interference and these interference signals are generally classified into jamming and spoofing signals. Jamming signals paralyze satellite navigation systems by transmitting strong interference signals to the satellite navigation signal band within a specific area. Spoofing signals cause a receiver to calculate position and time incorrectly by transmitting signals similar to those of a satellite navigation system, thereby causing the receiver to track such signals. Jamming signals are easily applicable because satellite navigation systems are neutralized using high-power signal transmission alone. When jamming signals are introduced, however, signal errors can be rapidly detected because receivers cannot calculate positions and time and thus, satellite navigation systems cannot be used. In the case of spoofing signals, it is difficult for the users of receivers to easily detect signal errors because the receivers keep producing position and time information even after spoofing signals are introduced. However, spoofing attacks are not easy for the attackers as well because similar signals must be generated in an elaborate manner to ensure receivers track the spoofing signals. As the importance of satellite navigation systems is gradually increasing in commercial and military fields, there are possibilities that attacks on such systems may be more elaborate and, thus, it is necessary to be prepared for attack by spoofing signals.
In this study, a method for the detection of spoofing signals in systems that use the GNSS augmentation system is proposed. The GNSS augmentation system improves the positioning accuracy of a satellite navigation receiver by providing correction data to the receiver. It includes the local area augmentation system (LAAS), which provides correction data for local areas, and the wide area augmentation system (WAAS), which provides receivers in wide areas with correction data using satellite broadcast messages. The augmentation system is mainly used for aircraft requiring precise position information and high stability. Additionally, the augmentation system improves the position information of aircraft in the vicinity of an airport, thereby aiding the aircraft landing process. It can also be used for shortening the landing route and improving the airport efficiency. It is expected that the augmentation system will be actively utilized for the calculation of the precise positions of unmanned aerial vehicles (UAVs), including drones. As many aircraft accidents occur due to inaccurate position information, providing accurate position information is essential for aviation safety, and with the augmentation system, the utilization of satellite navigation with many error components can be limited. Therefore, the augmentation system with an integrity function that warns the user in case of a failure or malfunctioning of the satellite navigation system is essential. Moreover, when satellite navigation receivers are exposed to spoofing attacks, system operation is severely disrupted. Therefore, it is necessary to gradually prepare for attack by spoofing signals [3]. In this study, a method for the detection of spoofing signals that are difficult to detect using the existing spoofing detection methods is proposed and its performance was verified for moving satellite navigation receivers that use the augmentation system.
The rest of this paper is structured as follows: Section 2 describes vulnerability of the existing detection methods. The proposed spoofing detection algorithm are presented in Sect. 3. Section 4 discusses simulation results, followed by the conclusion in Sect. 5.
2 Vulnerability of the Existing Detection Methods
Various spoofing detection methods have been studied. The existing detection methods can be largely classified into (i) methods that use signal-processing or antenna modules, (ii) methods that analyze the measurements from receivers, signal strength, and navigation messages, and (iii) methods that use heterogeneous sensors in addition to navigation receivers [4]. The methods of detecting spoofing signals using signal-processing or antenna modules include the spatial signal-processing method, signal arrival time monitoring, and correlation output distribution analysis. The spatial signal-processing method detects spoofing signals using multiple antennas [5] or the data from a single antenna moving along a random track [6]. The signal arrival time monitoring detects spoofing signals by examining the delay of the pseudo-random-noise (PRN) code or data bit [7,8,9] or the delay of the frequency band L1 and L2 signals [10]. The correlation output distribution analysis inspects receiver measurements and correlator outputs [11,12,13,14]. The methods that use the receiver output information include the methods of signal power monitoring, signal quality monitoring, and navigation message monitoring. The signal power monitoring detects spoofing signals by inspecting the carrier-to-noise ratio (\(C/N_{0}\)), absolute signal power value, receiver power variation for receiver movement, or difference between the L1 and L2 signal power levels [15, 16]. The signal quality monitoring inspects the code, carrier, and Doppler consistency, and the navigation message monitoring uses the received satellite position information. Satellite clock consistency monitoring detects spoofing signals when abnormal navigation data are received due to spoofing signals. Heterogeneous sensor consistency monitoring detects spoofing signals by comparing the receiver outputs with the outputs of other auxiliary devices, such as an inertia measurement device and a reference time [7, 17].
Among these spoofing detection methods, the method that uses signal-processing or antenna modules and the method that uses heterogeneous sensors have the disadvantage of requiring the addition of hardware to the existing receivers or modification of the receivers. The method of detecting spoofing signals by analyzing the output data of receivers can be used to avoid the use of additional hardware. However, the detection of spoofing signals using this method can be difficult if signal intensities or changes in measurements are small or if navigation messages are not changed. Therefore, installing a receiver at a fixed point and combining the navigation solution inspection with other inspections is effective for the existing detection methods. However, in the case of moving receivers, spoofing detection can be difficult because the accurate position of a receiver that can be treated as a reference is not known.
To overcome this limitation, the method of detecting satellite navigation spoofing signals by allowing a user receiver that utilizes the augmentation system to use correction data is proposed in this study. The proposed method calculates navigation solutions using correction data and inspects changes in measurements accordingly. It is possible to detect spoofing signals based on the measurements of a moving receiver without adding hardware to the receiver. It is also possible to detect spoofing that induces the receiver position with single channel spoofing as well as all channel spoofing because there is the effect of comprehensively judging measurements using the final navigation solution. In particular, the application of the cumulative sum (CUSUM) method enabled the detection of spoofing signals that are difficult to detect due to their similarity to normal signals. When spoofing signals are generated to induce a specific position over all channels rather than a single channel, or when normal signals are rebroadcast, it is difficult to detect signal errors because the rationality of interrelation is maintained between measurements. Detection can also be difficult when there are small differences from normal signals. The proposed method is suitable for such spoofing signal characteristics and capable of effectively detecting spoofing signals without the installation of additional hardware.
Spoofing attacks on satellite navigation systems may have various forms, such as receiver measurement spoofing, navigation message spoofing, single channel spoofing, and multi-channel spoofing, depending on the intention of the attacker. Therefore, the simultaneous application of various methods is effective for the detection of various spoofing signals. The proposed method can be utilized as a comprehensive detection factor because it has the function of inspecting the final navigation solution. It is expected that the proposed method will be highly utilized for navigation devices, such as UAVs, where installation of additional hardware is difficult.
3 Spoofing Detection Algorithm
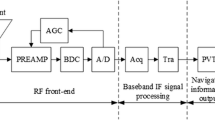
In the normal situation without spoofing attacks, a receiver that uses the GNSS augmentation system can calculate its precise position by removing the error components contained in measurements and calculating the navigation solution using the provided correction data. For UAVs, such as drones, the use of the augmentation system rather than the use of a satellite navigation system alone enables precise location estimation, thereby enabling the utilization of various services. When spoofing signals are introduced to a receiver that uses the augmentation system, the receiver produces its measurements from the spoofing signals. When the navigation solution is calculated by applying the correction data, generated based on normal signals, to the measurements of the receiver, the error of the navigation solution increases. Even at the navigation solution position targeted by the spoofing attacker, the navigation solution calculated by the receiver will have an error. Therefore, it is possible to detect spoofing signals by continuously monitoring the relationship between the navigation solutions, which are calculated using correction data by the receiver that utilizes the augmentation system, and the measurements of the receiver (Fig. 1).
A receiver that uses the augmentation system corrects measurements using the broadcast correction data and calculates the navigation solution. As the broadcast correction data almost accurately predict the error components of measurements in the current environment of the receiver, the precision of the calculated position is high compared to the actual receiver position. The corrected pseudorange also becomes similar to the distance between the actual receiver and the satellite. However, it is not easy for spoofing signals to reflect the actual error components in real time. Additionally, it is difficult to accurately synchronize time with the existing satellite navigation system. Therefore, if correction data are used when spoofing signals are introduced, the navigation solution is calculated without properly removing the error components in measurements, thereby resulting in errors. In this case, the calculated navigation solution also has a difference from the position intended by the spoofing signals.
The estimated range is defined as the distance between the receiver and the satellite computed from the calculated navigation solution and the position of the satellite. If the error terms are well corrected through the correction data of the GNSS augmentation system, most of the error terms are eliminated and the navigation solution is accurately measured. The difference of the corrected pseudorange and the estimated range reflects the receiver's time bias error and the value remains steady. If the pseudorange delay occurs due to the spoofing signal, the spoofing signal does not reflect an actual error value and the variation of the time bias occurs. This causes a change in the difference values comparing with normal situation. If the change of difference between the corrected pseudorange and the estimated range calculated using the calculated navigation solution is monitored, it is possible for the moving receiver, with its reference position unknown, to detect the introduction of spoofing signals. The proposed method is based on these characteristics for use in systems that use the data of the ground-based augmentation system (GBAS), which can be used in the vicinity of airports as well as for UAVs, such as drones, in the future. The proposed method detects spoofing signals by monitoring the change of difference between the corrected pseudorange and estimated ranges. The spoofing detection process can be summarized as follows.
- 1.
GBAS data decoding.
- 2.
Navigation message and measurement data decoding.
- 3.
Pseudorange correction using the GBAS data.
- 4.
Calculation of the navigation solution using the corrected pseudorange.
- 5.
Calculation of the estimated range using the navigation solution and satellite position.
- 6.
Calculation of test statistics (calculation of the difference between the corrected pseudoranges and estimated ranges).
- 7.
Monitoring of test statistics.
- 8.
Spoofing detection when the threshold is exceeded in the monitoring (Fig. 2).
The pseudorange correction formula of the ground-based augmentation system is defined in Eq. (1)
where, \(\rho\) is the pseudorange, PRC is the pseudorange correction data, RPRC is the pseudorange change rate correction data, t is the time, TC is the tropospheric delay correction amount, and c is the speed of light. The superscript i denotes the i-th navigation satellite, subscript C denotes the correction state using the correction data, u denotes the user receiver, z–count denotes the corrected broadcast time, and SV denotes the navigation satellite. The pseudorange p measured by the receiver can be defined by error components, such as the actual distance between the receiver and satellite, receiver time bias, and ionospheric and tropospheric delays. Equation (2) defines the pseudorange of the i-th satellite that reflects these elements
here, \(r\) is the actual distance between the receiver and satellite, \(\delta t\) is the clock error of the receiver, and \(\tilde{\varepsilon }\) is the error element included in the receiver measurement. The actual distance between the receiver and satellite can be defined using the positions of the satellite (\(X^{i} = [x^{i} ,y^{i} ,z^{i} ]\)) and receiver (\(X = [x,y,z]\))
Simply defining the time bias of the receiver as \(b = c\,\delta t_{u}\) and using Eq. (3), Eq. (2) can be redefined as follows
If the navigation solution was calculated using the corrected pseudorange, the calculated receiver position can be defined as Eq. (5) and the estimated range, using the calculated receiver position, can be defined as Eq. (6)
Therefore, the difference between the corrected pseudoranges and estimated ranges can be defined as follows
here, CR is the correction amount received from the augmentation system. As the correction amount well reflects error components in the normal state, the calculated receiver position is similar to the actual receiver position as Eq. (8). Therefore, Eq. (7) can be finally redefined as Eq. (9), which is an approximate equation. The time bias of the receiver is derived during the course of calculating the navigation solution of the receiver, and it has a relatively constant value in the normal state during the short period of detecting spoofing signals
When a spoofing signal is introduced, however, changes occur to the corrected pseudoranges and estimated ranges. The measured pseudorange and target position of the spoofing signal, when a spoofing signal is introduced, are defined in Eq. (10)
here, the subscript S denotes the spoofing signal and \(\delta \rho\) is the pseudorange change due to the spoofing signal. In this case, the difference between the corrected pseudoranges and estimated ranges changes as defined in Eq. (11) from that defined in Eq. (7)
The corrected data differ from the error components generated by the spoofing signal, and the target position of the spoofing signal also differs from the calculated receiver position
As the difference between the corrected pseudoranges and estimated ranges changes due to the introduction of the spoofing signal, the spoofing signal can be detected by monitoring the corrected pseudoranges and estimated ranges.
The receiver autonomous integrity monitoring (RAIM) method can be basically applied to the method of determining whether the measurements of a satellite navigation receiver are normal by examining if the correlations between the measurements are reasonable [18]. In the case of the existing RAIM method, however, it is not possible to detect the spoofing signal correlated to all channels because it monitors the correlations between measurements at the moment of reception. Additionally, it is not possible to detect spoofing where the correlations between measurements are maintained by simple time delays, such as meaconing [19]. When the measurements of the receiver are monitored using the proposed method, it is possible to detect the spoofing signal because the time bias change of the receiver and changes in measurements before and after spoofing can be detected. Meanwhile, the use of the corrected data has the effect of monitoring the introduction of a spoofing signal more clearly by precisely maintaining the navigation solution of the normal state and reducing error components. As can be seen from Eq. (12), monitoring becomes easier as the difference between the error generation amount of the spoofing signal and the corrected data becomes larger. The pseudorange error can be set for monitoring, as follows
Equations (7) and (8) define the characteristics of the derived test statistics before and after the spoofing signal application. When a spoofing signal is generated, the value of the pseudorange error changes according to the spoofing signal. When a spoofing signal is applied, the common error factor of each pseudorange changes. This change is reflected in the clock bias, and by detecting this change, the spoofing signal can be detected.
If the correction information reflects the error factor well under normal conditions, the difference between corrected pseudoranges and estimated ranges is dominated by the clock bias and the value remains steady, but its value changes after the application of a spoofing signal. The spoofing signal continues to influence once it is induced and has characteristics very similar to a normal signal. Considering such spoofing signal characteristics, a monitoring method capable of detecting continuous and small signal errors is needed, and it is possible to detect the spoofing signal using the CUSUM method [20]. The method of detecting spoofing signals through the CUSUM method can detect errors when a small amount of errors consistently occurs by accumulating the values. When a spoofing signal is applied and the receiver tracks the spoofing signal, the receiver loses the tracking of the normal signal and continuously tracks the spoofing signal. The CUSUM method, however, continuously accumulates errors, however small they are, and is therefore capable of detecting the generated spoofing signal [21].
As the measurements of the receiver are generated for each satellite, the application of the multivariate CUSUM is required and a method is applied to monitor changes in the average of test statistics. When multivariate CUSUM for monitoring changes in the average is applied, the equations related to the CUSUM method can be defined as follows [22]
When the test statistics of each measurement and the test statistics average of the normal state are defined as in Eq. (14), the CUSUM method can be defined as Eqs. (15) and (16). \(\mu_{G}\) is the average value in the normal state, \(G\) is the cumulative sum, \(k\) is the reference parameter, \(\Sigma\) is the covariance matrix of test statistics, and \(m\) is the number of visible satellites. In general, the reference parameter can be set as follows in the CUSUM method for monitoring changes in the average [23]
here, \({\mathbf{M}}_{B} = \left[ {\mu_{B}^{1} \,\mu_{B}^{2} \, \ldots \,\mu_{B}^{m} } \right]^{T}\) denotes the average of test statistics in the spoofing state. In the CUSUM method, the abnormal state is referred to as “out of control” and the normal state is referred to as “in control.” Finally, when \(G_{i}\) in Eq. (16) exceeds a threshold (\(h\)), the introduction of a spoofing signal can be detected
To simplify the detection equation, test statistics are normalized as follows and the measurements for each satellite in the normalized values can be defined as follows
here, \(\sigma\) is the standard deviation of test statistics. The product of the normalized measurements for each satellite and the transposed matrix can be defined as Eq. (21)
Assuming that measurements for each satellite have a normal distribution, the probability density function of the variable \(\delta\) can be defined using the chi-square distribution as follows [24]
here, \(q\) is the degree of freedom and \(\Gamma\) is the gamma function. The degree of freedom between satellite navigation measurements can be defined as \(q = m - 4\) through the number of visible satellites. Figure 3 shows the probability density distribution (PDF) of \(\delta\) according to the degree of freedom.
When measurements are changed by \(\mu\) on average due to the spoofing signal, the probability density function shows a noncentral chi-square distribution and is defined as follows [24]
here, \(\lambda\) is a noncentral parameter and \(\lambda = q\mu^{2}\) holds true. Figure 4 shows the probability density distribution according to \(\lambda\) when the degree of freedom is six (10 visible satellites).
If normalization is also introduced to the average values of the abnormal state, \({\mathbf{M}}_{B} - {\mathbf{M}}_{G}\) can be defined as Eqs. (26) and (27). When Eq. (27) is applied to Eqs. (15), (16), and (18), the CUSUM method can be simplified as defined in Eqs. (28), (29), and (30)
The performance of the CUSUM method can be expressed through the average running length (ARL). The ARL in which abnormality can be detected in the normal state (in control) is referred to as \({\text{ARL}}_{0}\), and the ARL until abnormality is detected in the abnormal state (out of control) is referred to as \({\text{ARL}}_{1}\). When the abnormal state (out of control) is defined in the discriminant equation of the CUSUM method and the value of \(k\) is set, the threshold (\(h\)) can be determined according to the required \({\text{ARL}}_{0}\). The setting of the value of \(k\) varies depending on the setting of the value of the abnormal state (out of control). The threshold and the value of \({\text{ARL}}_{1}\) change to meet the required condition \({\text{ARL}}_{0}\). When the initial value of the CUSUM method of Eq. (28) is set to a value higher than zero, the function (\(L\)) representing the ARL value can be defined as follows if the initial value is expressed as \(z\) [20]
here, \(F\) is the cumulative distribution function of \(\delta\) and \(f\) is the probability density function of \(\delta\). Equation (31) can calculate ARL according to the setting of the threshold (\(h\)) through numerical analysis, and can calculate the distributions of the threshold and \({\text{ARL}}_{1}\) according to the value of \(k\) related to the abnormal state (out of control) value. For numerical analysis, Eq. (31) can be discretized as follows [25]
Introducing a matrix as shown in Eq. (34) for the calculation of the discretized equation, Eq. (32) can be defined as Eq. (35). It can also be defined as Eq. (36) for the calculation of the ARL matrix
here, each matrix represents \({\mathbf{L}}_{m \times 1} = \left[ {\begin{array}{*{20}c} {\tilde{L}(a_{1} )} & {\tilde{L}(a_{1} )} & \cdots & {\tilde{L}(a_{1} )} \\ \end{array} } \right]^{T}\), \(1_{m \times 1} = \left[ {\begin{array}{*{20}c} 1 & 1 & \cdots & 1 \\ \end{array} } \right]^{T}\), and \({\mathbf{I}}_{m} = {\text{diag}}(1,1, \cdots x,1)\).
Figure 5 shows the threshold according to the abnormal state value. As the value of the abnormal state increased, the threshold to meet the target requirement \({\text{ARL}}_{0} = 10^{7}\) decreased (\({\text{ARL}}_{0} = 10^{7}\) corresponds to \(P_{fa} = 10^{ - 7}\) which is false alarm rate based on a sub-allocation of the specified Category I continuity risk allowed per 15 s interval in GNSS augmentation system [26]). Figure 6 shows the \({\text{ARL}}_{1}\) of the abnormal state, confirming that \({\text{ARL}}_{1}\) decreased as the value of the abnormal state increased. In general, the RAIM method is applied, and abnormal warnings can be detected when the threshold is set according to the false alarm rate and errors meeting the false alarm rate occur. When the CUSUM method is used, however, a small amount of abnormal change can be detected through accumulation. In the CUSUM method, if the threshold is set to a high value to detect a small amount of the abnormal state, detection is possible even though \({\text{ARL}}_{1}\) becomes longer. The method is suitable for the detection of a spoofing signal considering that the abnormal state by the spoofing signal continues when the tracking of the spoofing signal occurs.
4 Simulation Results
The proposed spoofing detection method performed simulation using the data of a moving receiver that utilizes GBAS. The data used for the simulation were obtained from a UAV equipped with a GPS receiver. It was assumed that a spoofing signal was applied at 20 s after the start of the simulation. The UAV start position in the simulation was 36.3914° in latitude, 127.3980° in longitude, and 112.51 m in altitude, and it corresponds to the (0, 0) position of the graph in Fig. 7a, representing the horizontal position change of the receiver. During the simulation period, there were 10 visible satellites (PRN number: 23, 3, 28, 12, 17, 6, 2, 19, 9, and 22). The simulation was performed considering the application of meaconing based on the position of the receiver. Detection of the spoofing signal is difficult because the meaconing signal is similar to the actual signal. In the simulation, the meaconing signal assumed a situation in which a pseudorange delay of 1.465 m occurred over all satellite channels. This is the situation where the pseudorange was 0.005 chip delayed compared to the reference signal, and it is difficult for the receiver to detect the spoofing signal using conventional methods.
Figure 7 illustrates changes in the horizontal and vertical positions when the spoofing signal was introduced. The position of the receiver was not significantly affected because the same delay occurred to all channels simultaneously when the spoofing signal was applied. Therefore, spoofing detection is not easy if it is to be detected based on the simple position test method. As shown in Fig. 8a, however, the receiver time bias was changed due to the introduction of the spoofing signal. The difference between the corrected pseudoranges and estimated ranges for each satellite was also changed by the error component due to the introduction of the spoofing signal, as shown in Fig. 8b. These results well represent the difference between the corrected pseudoranges and estimated ranges in the normal and spoofing states shown in Eqs. (7) and (11).
The proposed spoofing detection method detected the spoofing signal by sensing the continued change of pseudorange difference although the position error change due to the introduction of the spoofing signal was not large. Figure 9 shows the spoofing detection performance through a conventional method. Figure 9a shows the results of test statistics through the chi-square verification, and Fig. 9b shows the results of detecting spoofing using the RAIM method. In Fig. 3, \(P_{fa} = 10^{ - 7}\) holds true for the fault alarm rate of the test statistics with six degrees of freedom to have the probability corresponding to \(ARL_{0} = 10^{7}\) in the CUSUM method. In this case, the threshold corresponds to approximately 43.34, which indicates that spoofing detection is not possible when a small amount of spoofing occurs as in the simulation situation of Fig. 9a because test statistics do not exceed the threshold. Figure 9b illustrates the spoofing detection using the existing RAIM method, which detects whether the correlations between measurements are reasonable or not. Therefore, it is not easy to detect meaconing or advanced spoofing signals generated in consideration of the correlations between measurements with the target of a specific position [19]. Although a spoofing signal was applied, significant changes did not occur in the RAIM method before and after the application of the signal, which implies that it is not possible for the existing method to detect spoofing when a meaconing signal is applied based on a reference signal.
Figure 10 shows the spoofing detection results obtained using the proposed test statistics and CUSUM method. The cumulative value of the CUSUM method gradually increased from 20 s when the spoofing signal was introduced. The corresponding spoofing attack exceeded the threshold at 23.5 s and the introduction of the spoofing signal was detected, as shown in Fig. 10b. When the receiver tracked the spoofing signal, the test statistics change is very small and persistent. Hence, the CUSUM method can detect the spoofing signal using such characteristics and the spoofing detection performance can be confirmed.
5 Conclusions
To prevent the interference with satellite navigation signals and to secure their stability and reliability, it is necessary to detect attacks on satellite navigation systems in a timely manner through the continuous monitoring of the received navigation signals. In this study, a spoofing detection method for moving receivers that use satellite navigation correction data was proposed. Test statistics were derived through the corrected pseudoranges and estimated ranges using the characteristics of a receiver that uses correction data, and a spoofing detection algorithm was proposed. As spoofing signals are similar to the authorized signals, it is not easy for a receiver to detect spoofing when a spoofing signal slightly affecting the receiver is introduced. However, it was possible to detect spoofing using the CUSUM method, which uses the characteristics that a receiver is continuously affected by a spoofing signal once it tracks the spoofing signal. When changes in test statistics before and after the spoofing signal introduction are increased using correction data and the CUSUM method is applied, it is possible for a moving receiver to detect sophisticated spoofing signals without the installation of additional hardware.
Owing to the active utilization of systems, such as UAVs, the demand for high reliability of satellite navigation systems will increase and the improvement of user reliability will be more important than that of the reliability of a reference station. The proposed method can be applied as one of the spoofing detection methods and it allows the user to independently contribute to the improvement of the reliability of satellite navigation signals. The proposed method is affected by the change of visible satellite because the method is based on measurement monitoring. For practical application in the future, the study of detection technique according to change of visible satellite is needed.
References
Joo I, Sin C, Kim J, Lee S (2010) GPS L5 acquisition schemes for fast code detection and improved Doppler accuracy. ETRI J 32:142–144. https://doi.org/10.4218/etrij.10.0209.0414
Jeong S, Lee S, Lee J (2012) Algorithm analysis for GNSS spoofing detection system. In: Asia-Pacific International Symposium on Aerospace Technology
Kerns AJ, Shepard DP, Bhatti JA, Humphreys TE (2014) Unmanned aircraft capture and control via GPS spoofing. J Field Robot 31:617–633. https://doi.org/10.1002/rob.21513
Jafarnia-Jahromi A, Broumandan A, Nielsen J, Lachapelle G (2012) GPS vulnerability to spoofing threats and a review of antispoofing techniques. Int J Navig Obs. https://doi.org/10.1155/2012/127072(Article ID 127072)
Montgomery PY, Humphreys TE, Ledvina BM (2011) Receiver-autonomous spoofing detection: experimental results of a multi-antenna receiver defense against a portable civil GPS spoofer. In: Proceedings of the Institute of Navigation International Technial Meeting 124–130
Nielsen J, Broumandan A, Lachapelle G (2010) Spoofing detection and mitigation with a moving handheld receiver. GPS World 21:27–33
Humphreys TE, Ledvina BM, Psiaki ML, O'Hanlon BW, Kintner PM (2008) Assessing the spoofing threat: development of a portable GPS civilian spoofer. In: The 21st International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS ’08), 16–19
Lo S, Enge P (2010) Authenticating aviation augmentation system broadcasts. In: The IEEE/ION position, location and navigation symposium (PLANS ’10) 708–717. 10.1109/PLANS.2010.5507223
Lo S, Lorenzo DD, Enge P, Akos D, Bradley P (2009) Signal authentication, a secure civil GNSS for today. Inside GNSS 30–39
Wen H, Huang PY, Dyer J, Archinal A, Fagan J (2005) Countermeasures for GPS signal spoofing. In: The 18th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS 2005) 1285–1290
Phelts R (2001) Multicorrelator techniques for robust mitigation of threats to GPS signal quality. Ph.D. dissertation, Stanford University
Cavaleri A, Motella B, Pini M (2010) Detection of spoofed GPS signals at code and carrier tracking level. In: Fifth ESA workshop on satellite navigation technologies and European workshop on GNSS signals and signal processing (NAVITEC ’10) 1–6. 10.1109/NAVITEC.2010.5708016
Pini M, Fantino M, Cavaleri A, Ugazio S, Presti LL (2011) Signal quality monitoring applied to spoofing detection. In: 24th international technical meeting of the satellite division of the institute of navigation (ION GNSS ’11) 1888–1896
White NA, Maybeck PS, DeVilbiss SL (1998) Detection of interference/jamming and spoofing in a DCPS-aided inertial system. IEEE Trans Aerosp Electron Syst 3:1208–1217
Juang JC (2011) GNSS spoofing analysis by VIAS. Coord Mag 11–14
Jafarnia-Jahromi A, Broumandan A, Nielsen J, Lachapelle G (2012) GPS spoofer countermeasure effectiveness based on signal power, noise power and C/N0 observables. Int J Satell Commun Netw 30:181–191. https://doi.org/10.1002/sat.1012
Jafarnia-Jahromi A, Lin T, Broumandan A, Nielsen J, Lachapelle G (2012) Detection and mitigation of spoofing attack on a vector based tracking GPS receiver. In: International technical meeting of the institute of navigation, Newport Beach 790–800
Yang Y, Xu J (2016) GNSS receiver autonomous integrity monitoring(RAIM) algorithm based on robust estimation. Geodesy Geodyn 7:117–123. https://doi.org/10.1016/j.geog.2016.04.004
Psiaki ML, Humphreys TE (2016) GNSS spoofing and detection. Proc IEEE 104:1258–1270. https://doi.org/10.1109/JPROC.2016.2526658
Hawkins DM, Olwell DH (1998) Cumulative sum charts and charting for quality improvement. Springer-Verlag, New York
Lee J, Pullen S, Enge P (2006) Sigma-mean monitoring for the local area augmentation of GPS. IEEE Trans Aerosp Electron Syst 42:625–635. https://doi.org/10.1109/TAES.2006.1642577
Li, H (2007) Multivariate Extensions of CUSUM Procedure. Ph.D. dissertation, Stanford University
Joseph J, Pignatiello J, Runger GC (1990) Comparisons of multivariate CUSUM charts. J Qual Technol 22:173–186. https://doi.org/10.1080/00224065.1990.11979237
Perepetchai, V (2000) MS thesis, McGill University
Peerajit W, Areepong Y, Sukparungsee S (2018) Numerical integral equation method for ARL of CUSUM chart for long-memory process with non-seasonal and seasonal ARFIMA models. Thail Stat 16:26–37
U.S. Federal Aviation Administration (2002) Federal Aviation Administration Specification: Performance Type One Local Area Augmentation System Ground Facility, Washington, D.C., FAA-E-2937A
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jeong, S., Kim, M. & Lee, J. CUSUM-based GNSS Spoofing Detection Method for Users of GNSS Augmentation System. Int. J. Aeronaut. Space Sci. 21, 513–523 (2020). https://doi.org/10.1007/s42405-020-00272-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s42405-020-00272-9