Abstract
A Wireless Body Area Networks (WBANs) is a wireless network in which sensors are embedded inside the body of a human, to monitor the health of patient continuously without any constraint in his normal daily life activities. As the information from the embed sensor is transmitted through wireless network and device has a limited battery power, therefore, the assurance of security in such tiny devices related to medical patients is highly recommended. Thus, the shared information must be maintained in terms of integrity, confidentiality, non-repudiation, untraceable key establishment, and mutual authentication in WBAN. In this context, to achieve high security and efficiency in WBAN, an efficient mutual authentication and secret key agreement scheme have been proposed in this paper and also listed out some drawbacks of an existing mutual authentication and key agreement of Li et al.’s scheme. To confirm the efficiency and security, the proposed scheme has been verified using formal security analysis tool namely, ProVerif and BAN logic. The low communication and computation costs indicate that our scheme is more suitable for practical application in healthcare as compared to other existing schemes.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
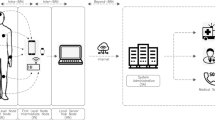
With the advancement of wireless technologies many mini nature devices are correspondingly developed, one of them is sensors or wearable sensor devices which are connected and implanted to the body to sense the physiological signals of the human body by frequently monitoring and examining. In WBAN, the sensor screens the health of humans by monitoring the parameters like body temperature, heart rate, the sugar level of blood, blood pressure level, and respiratory rate, etc. In order to prevent the old-age problem and to reduce the chronic conditions, the cost-effective healthcare infrastructure is recommended. Nowadays, medical professionals reduce stress because of advanced technologies, like implanting the sensor devices in the human body. As a result, they get high-quality medical facilities and treatments at home without any intervention of medical professionals. The application of WBAN is Emerging Medical Response System (ENRS), Ubiquitous Health Monitoring (UHM), Computer-Assisted Rehabilitation, etc. Figure 1 illustrates the communication segments of WBAN. In WBAN, personal sensitive information must be protected from unauthorized admission. Hence, maintaining security and privacy is the prime concern in healthcare.
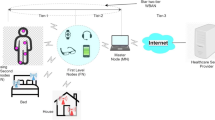
In the body area network, there are three kinds of nodes i.e., hub node, first-level node and second-level node. The wearable node which is attached to the body is called second-level nodes (\({S}_{n}\)), whereas intermediate node is a first-level node (\({I}_{n}\)) that collects the information from \({S}_{n}\) and forward to hub node (\(HNode)\) for further processing. The \({I}_{n}\) node generally has more loading capacity, high-processing speed, superior computing capabilities, and high-communication competence than \({S}_{n}\). The \(HNode\) is said to be a local server which is at the center [4] of WBAN and may assume as a trusted server [34]. The \(HNode\) collects all the complex data from sensor nodes and forwards to healthcare or diagnostic center. The Tier -1 shows the connection between \({S}_{n}\) and \({I}_{n}\) known as Intra-BAN communication. Similarly, connection between \({I}_{n}\) and \(HNode\), known as Inter-BAN communication, is Tier-2. The connections between the \(HNode\) and healthcare center are considered under Tier 3 which is outside the WBAN. Tier 3 medical center provides the services to the users or patients. The connection between the two sections comes with various difficulties and challenges. Therefore, in this paper, we have concentrated on the establishment of safe communications within these two segments.
The major contributions in this paper are mentioned bellow:
-
i.
To analyze the Li et al.’s [1] scheme and find out the possible security breaches like, linkable to the session, sensor node capture and eavesdropping; using informal security analysis.
-
ii.
To design a new efficient authentication and key agreement scheme by using only the cryptographic hash function and XOR operation to overcome the drawback of Li et al.’s scheme.
-
iii.
To verify the secrecy and authenticity between \(HNode\), and \({S}_{n}\), the proposed scheme has rigorously analyzed through informal security analysis, as well as with formal security analysis like, BAN logic to prove the correctness of our scheme and ProVerif Tools to verify secrecy of the scheme.
-
iv.
Finally, the proposed scheme has been compared with other related schemes in the context of computational cost, memory overhead, communication message exchange and security functionalities.
The remaining part of the paper is arranged as follows: Sect. 2 provides the related work. Brief review on Li et al.’s scheme [1] of WBAN has defined in Sect. 3. In Sect. 4, to defeat Li et al.’s scheme, a new efficient scheme of authentication and key agreement has been proposed. Section 5 includes the discussion of informal and formal security analysis of the proposed scheme using formal verification called BAN Logic and ProVerif simulation tool to show the credibility of the scheme. The comparison of our scheme with other existing related schemes is defined in Sect. 6 and finally, Sect. 7 defines conclusion and future scope of this research.
2 Related Work
Many researchers have developed authentication and key agreement schemes for different environments like for single sever [3,4,5], multi-server environment [6, 7], and wireless sensor network [8, 9]. In WBAN, while considering the secure transmission of medical patients’ information over wireless networks, the entity must mutually authenticate each other. The Non-cryptographic physiological signal-based [10, 11] schemes have been proposed to make secure communication in WBAN. Recently, many investigators have undertaken the further research in WBAN network to overcome the various security challenges and to increase the efficiency, overall. In 2010, Venkata Subramanian et al. [10] proposed a scheme in WBAN, where, it has been observed that the identical physiological signals are difficult to measure in the different parts of the body. Therefore, to improve the security in the WBAN, researchers integrated biometric characteristics too. Since then many of the researcher’s work on biometrics key distribution through physiological signal for WBAN [12, 13]. In 2006, Poon et al. [12] proposed an authenticated and secure communication link in WBAN system by using identifier (biometrics) physiological signal. However, the static biometrics have some restrictions, i.e., biometrics cannot be replaced in the event even if it is lost or stolen during the recording of the physiological signals. Moreover, the physiological signals change significantly and are inaccessible. Therefore, dynamic biometrics is more secure with low lastingness. In ProxiMate [14] experimental prototype build using an open-source software platform that allows wireless devices to securely pair with one another autonomously by generating a common cryptographic key directly from amplitude and phase components. On the contrary, cryptography-based schemes [15,16,17,18,19,20,21,22] have some specialized restriction depending on hardware functionality and software or programming requirement for wearable sensors in WBAN.
In 1985, Miller and Kobiltz proposed Elliptic Curve Cryptography (ECC) mechanism in public key infrastructure, which has been used further as a prevalent tool to maintain the secrecy in WBANs [12, 23,24,25,26,27,28]. In 2016, Shen et al. [20] proposed a multilayer authentication protocol based on ECC which maintains the integrity, privacy, and valid information in WBAN. Where, the authentication has been established between personal digital assistant (PDA) and sensor and also between PDA and Application provider (AP).
In 2016, Zhao et al. [29] surveyed on Physiological valued based key agreement among the biosensor nodes. In the same year, Ibrahim et al. [30] also proposed a scheme called secure mutual authentication between the sensor node and the hub node. The author claims that it satisfies all the security requirements by performing the XORed operation and cryptographic hash function, only. However, later, it has been observed that the Ibrahim et al.’s scheme may suffer from key escrow problem, impersonation on the hub, sensor and blocking or congestion attack [1, 2].
Further, to overcome the weaknesses of Ibrahim et al.’s scheme, Li et al. [1] also proposed an enhanced scheme and built up a session key in an unknown and un-linkable session with more security functions. Besides, the authors exhibited that their scheme is energy efficient and has low power computational expense than other related existing schemes. But later, in 2018, Koya et al. [2] discovered that the Li et al.’s scheme suffers from sensor node impersonation attack. To overcome the shortcoming, the Koya et al. further proposed a hybrid authentication and key agreement scheme of the original scheme of Li et al.’s where drawback has been settled by using the physiological signals.
In 2018, [31] Kompara et al. surveyed on intra-body area network communication security in which they have classified the key agreement schemes into four types: old model, physical valued, hybrid key, and secret key agreement schemes. Consecutively, in 2019, [32] Kompara et al. proposed a scheme that evacuates the drawback like linkable to session and sensor node capture attacks of Koya et al.’s scheme. However, Kompara et al.’s scheme may also suffer from time synchronization issues. In the same year 2019, Konan et al. [33] also proved that Kompara et al.’s scheme has memory storage problems. In 2019, Xu et al. [34] proposed a scheme where he made guarantee to maintain the forward secrecy without asymmetric encryption. Recently 2020, Gupta et al. [35] proposed to enhance scheme of Koya et al.’s but it has been found that Gupta et al.’s suffers from higher computation costs and communication overhead. Abdullah et al. [36] proposed a secure anonymity guarantee preserving protocol for WBAN and defined two techniques namely, P-I for authentication, and P-II for re-authentication to increase efficiency.
However, regrettably, during our research, we found that Li. et al.’s [1] scheme still exist few flaws like Hub node impersonation attack, linkable session, sensor node capture, impersonation, and eavesdropping attacks. Hence, to overcome such issues, we have designed an efficient mutual authentication and symmetric key agreement scheme and succeeded to reduce the overall complexity. The main key features of our scheme are to avoid the use of timestamp, verification of sensor node identity at the Hub node end, and resolves the security functionality of Li. et al. [1].
3 Brief Evaluation of Li et al.’s Scheme
The Li et al.’s scheme in WBAN [1] comprises of three phases: namely, the initialization phase, sensor node registration, and the authentication and key agreement phase. There are three types of nodes: first-level node (\({I}_{n}\)), second-level node (\({S}_{n}\)), and local server (\(HNode\)). The first-level node is the intermediary node (e.g., smartphone, smartwatch) which gathers the information from second-level nodes. However, they have a higher processing power, storage capacities, and higher capabilities of battery power, whereas second-level nodes are resource-constrained. The hub node or local server is a powerful node that connects to healthcare service providers. The network type is illustrated in Fig. 1. In Li et al.’s scheme, system administrator (\(SAdmin\)) performs initialization and registration phase in a protected communication network, while the authentication phase is carried out in the unprotected network. In the initialization phase, \(SAdmin\) sets up \(HNode\), register \({S}_{n}\) and \({I}_{n}\). Mutual authentication and key agreement are performed between the \({S}_{n}\) and \(HNode\), through intermediate node \({I}_{n}\). we have utilized the notations in the scheme as summarized in Table 1.
The detailed description of the Li et al.’s scheme is defined below:
3.1 Registration Phase
Initially,\(SAdmin\) creates the master key \({MK}_{hn}\) for \(HNode\) and \(SAdmin\) configures the \({S}_{n}\) by assigning identity \({Sid}_{n}\), secret key of \({S}_{n}\) as \({NK}_{n}\) for each nodes and computes \({{P}_{n}=Sid}_{n}\oplus {h(MK}_{hn}||N{K}_{n})\) and \({{Q}_{n}=MK}_{hn}\oplus {P}_{n}\oplus {NK}_{n}\). Whereas intermediate node \({I}_{n}\) chooses his single identity \({Iid}_{in}^{^{\prime}}\) by himself. The \(SAdmin\) stores the tuple \({<Sid}_{n},{P}_{n},{Q}_{n}>\) onto \({S}_{n}\) and also \(HNode\) stores all \({Iid}_{in}^{^{\prime}}\) for each of \({I}_{n}\) node. The secret key \({NK}_{n}\) of each node is not kept on any of the devices except used for computing \({P}_{n}\) and \({Q}_{n}\) parameters.
3.2 Authentication and Key Agreement
Figure 2 demonstrates the authentication and key agreement scheme of Li et al.’s. The \({S}_{n}\) anonymously authenticates \(HNode\) through the help of \({I}_{n}\) as follows:
Two-hop centralized WBAN authentication and key agreement protocol [1]
Step 1: Node \({S}_{n}\) picks \({R}_{n}\) and produces a timestamp \({t}_{n}\). After that, \({S}_{n}\) computes \({X}_{n}={P}_{n}\oplus {Sid}_{n}\), \({Y}_{n}={X}_{n}\oplus {R}_{n}\), the temporary identity \({tid}_{n}=h(S{id}_{n}\oplus {t}_{n}||{R}_{n})\) and sends the parameters \(<{tid}_{n}, {Y}_{n}, {P}_{n}, {Q}_{n}, {t}_{n}>\) to \({I}_{n}\).
Step 2: \({I}_{n}\) forward the parameters without any modification to \(HNode\) by putting \({I}_{n}\)’s identity,\({Iid}_{in}^{^{\prime}}.\)
Step 3: On the receiver side, \(HNode\) receives the parameters \({<tid}_{n}, {Y}_{n}, {P}_{n}, {Q}_{n}, {t}_{n},{Iid}_{in}^{^{\prime}}>\) and performs the operations as follows.
-
\(HNode\) verifies the \({Iid}_{in}^{^{\prime}}\) in its database to find whether it is present or not. If not, the authentication procedure stops or aborts. Apart from \({Iid}_{in}^{^{\prime}}\) verification, \(HNode\) also finds the strength of timestamp \({t}_{n}\) by checking the strength of the predicate \({(t}^{*}-{t}_{n}<\) \(\Delta t)\). Where \({t}^{*}\) is the time when the message is received and \(\Delta t\) is the maximum transmission delay. Otherwise, terminate the entire process for authentication, if time is not within the given \(\Delta t\).
-
Further \(HNode\) computes, \(N{K}_{n}^{*}={MK}_{hn}\oplus {P}_{n}\oplus {Q}_{n}\), \({X}_{n}^{*}=h({MK}_{hn}||{NK}_{n}^{*})\), \({Iid}_{n}^{*}={X}_{n}^{*}\oplus {P}_{n}\) and \({R}_{n}^{*}={X}_{n}^{*}\oplus {Y}_{n}\), \({tid}_{n}^{*}=h(I{id}_{n}^{*}\oplus {t}_{n}||{R}_{n}^{*}).\)
-
Verifies, \({tid}_{n}=?{tid}_{n}^{*}\). Terminates if the computed value is not matched or fails.
-
Picks \({F}_{n}\) and computes \(\alpha ={X}_{n}\oplus {F}_{n}\) and \(\gamma ={R}_{n}\oplus {F}_{n}\)
-
\(HNode\) picks a new secret key \({NK}_{n}^{+}\) and perform new \({P}_{n}^{+}={Sid}_{n}\oplus h\left({MK}_{hn}||{NK}_{n}^{+}\right),\) \({Q}_{n}^{+}={MK}_{hn}\oplus {P}_{n}^{+}\oplus {NK}_{n}^{+}\),\(\eta =\gamma \oplus {P}_{n}^{+},\) \(\mu ={\varvec{\gamma}}\oplus {Q}_{n}^{+}\), \(\beta =h\left({X}_{n}\left|\left|{R}_{n}\right|\right|{F}_{n}|\left|\eta \right||\mu \right)\), and computes session key \({K}_{s}=h\left({Sid}_{n} ||{R}_{n}||{F}_{n}|| {X}_{n}\right)\) and forwards \(<\alpha ,\beta ,\eta ,\mu ,{Iid}_{in}^{^{\prime}}>\) to \({I}_{n}\).
Step 4. \({I}_{n}\) drops her identity \({Iid}_{in}^{^{\prime}}\) and just forwards the rest of parameters \(<\alpha ,\beta ,\eta ,\mu >\) to \({S}_{n}\)
Step 5. \({S}_{n}\) on receiving the parameters \(<{tid}_{n},\alpha ,\beta ,\eta ,\mu >\) performs as follows.
-
Computes \({F}_{n}^{*}={X}_{n}\oplus\) α, \({\beta }^{*}=h({X}_{n}|\left|{R}_{n}\right||{F}_{n}^{*}|\left|\eta \right||\mu )\) and checks \(\beta =?{\beta }^{*}.\) Terminate if it fails.
-
Computes \(\gamma ={R}_{n}\oplus {F}_{n}\), \({P}_{n}^{+}=\gamma \oplus\) η, \({Q}_{n}^{+}= \gamma \oplus\) µ and the session key \({NK}_{n}^{*}\left(={K}_{s}\right)=h(S{id}_{n},{X}_{n},{R}_{n},{F}_{n})\) is stored for further secret communication. Change the parameters \({P}_{n}, {Q}_{n}\) with the parameters \({P}_{n}^{+}, {Q}_{n}^{+}\) in its memory.
3.3 Cryptanalysis of the Li et al.’s Scheme
Li et al. claims that their scheme achieves an anonymous mutual authentication and key agreement. In contradict, we oppose that information sent between the \({S}_{n}\) and \(HNode\) are not secured against the sensor node capture attack, \({S}_{n}\) and \(HNode\) impersonation attack, linkable to session communication between \({S}_{n}\) and \(HNode\), and eavesdropping attack.
3.3.1 Linkable to Session
The scheme sends the secret parameters (\({R}_{n}, {NK}_{n}, {F}_{n}\)) in the form of \({Y}_{n}\), \({Q}_{n}\) and \(\alpha\) respectively, over the public channel for authentication purpose by \({S}_{n}\) and \(HNode\). Therefore, the attacker may intercept the communication between \({S}_{n}\) and \(HNode\), and get messages \(<{tid}_{n}, {Y}_{n}, {P}_{n}, {Q}_{n}, {t}_{n},{Iid}_{in}^{^{\prime}}>\) and \(<\alpha ,\beta ,\eta ,\mu ,{Iid}_{in}^{^{\prime}}>\). Hence, the attacker gets access the value of γ easily just by performing \({Y}_{n}\oplus \alpha\), while underlying secret values remain unknown to him. However, it is sufficient to extract the parameters \({P}_{n}^{+}\) and \({Q}_{n}^{+}\), by computing \({P}_{n}^{+}=\eta \oplus\upgamma\) and \({Q}_{n}^{+}=\mu \oplus\upgamma\). Whereas the main purpose of these values is for using in next authentication and key agreement process. Therefore, an attacker captures successive authentication messages can consequently connect this session to a single sensor node. Hence, the attacker can effortlessly link the session between the \({S}_{n}\) and \(HNode\).
3.3.2 Sensor Node Capture Attack
In this kind of attack, the attacker may compromise any of the sensor node \({S}_{n}\) in the WBAN and after extracting the stored parameters, can perform the various operation on network and finally can compromise the entire network easily. In Li, et al.’s scheme, the main reason for not sustaining against node capture attack is because of sensor’s identity \({Sid}_{n}\) which is not stored in \(HNode\) to check the legitimacy. Once the identity of \({S}_{n}\) is impersonate, adversary removes the original \({Sid}_{n}\) by performing XORed of \({P}_{n}\) and \({Q}_{n}\) and embed a new identity \({Sid}_{n}^{new}\), \({P}_{n}^{new}\) and \({Q}_{n}^{new}\). As we know that \(HNode\) does not verify authenticity of the sensor node by the validating identities with the received identity\({Sid}_{n}\), therefore, the adversary can change the \({Sid}_{n}\) for unlimited times. Hence, the scheme does not resist against sensor node capture attack.
3.3.3 Use of Timestamps
Timestamp-based protocol experiences time synchronization issues and are expensive too [37, 38]. The estimation of these timestamps’ starting with a one-time zone then onto the next time zone, for example, \({S}_{n}\) to \(HNode\). The message arrived at the receiver side must be within valid timestamp or trusted nodes for authentication. Even if the slight change in time, the whole scheme will break down. Here, no confirmation or validation is possible when the timestamp is lost while transferring through a dubious channel. Hence, to overcome the synchronization problem, use of fresh random number is always recommended.
3.3.4 Eavesdropping Attack
The adversary can take an advantage by sniffing or eavesdropping the messages sent over the public channel like\(\eta ,\alpha , \: and\: \mu\). The attacker stores \(\eta\: and \: \mu\) values by performing XORed operation. For every new authentication, it is required to update \({P}_{n}\) and \({Q}_{n}\) with new\({R}_{n}\),\({F}_{n}\) and\({Sid}_{n}\). During the update phase, the adversary may eavesdrop to perform a reply attack. Similarly, the Koya et al. [2] suffers the similar problem\(\eta \oplus \mu ={P}_{n}\oplus {Q}_{n}\).
4 Proposed Scheme
In this section, we have proposed an enhanced authentication and key agreement scheme which removes the securities pitfalls of Li et al.’s [1] schemes. The scheme increases the efficiency of sensor nodes in terms of, communication overhead and computational complexity. In proposed scheme, we have considered that the Hub node can never be captured or negotiated by an adversary because compromising Hub node means the entire network will break down [34]. Thus, we consider that the database (DB) is protected from database security threats, and the administrator gives the privilege to legitimate sensors only to access DB because it is required to be updated periodically [46]. Hence, Hub node is trusted and it will not maltreat the encryption keys of the authorized users or the keys of sensor nodes shared among them. The proposed scheme is alike to Li et al.’s scheme; it includes \(HNode\) be trustworthy and protected. The notations used for our scheme is the same as the original scheme. The scheme consists of four phases i.e., initialization phase, registration phase, authentication and key agreement phase, and sensor node addition phase. The \(SAdmin\) performs the initialization and registration before the authentication. The phases are as follows:
4.1 Initialization Phase
In this phase, \(SAdmin\) initializes the \({S}_{n}\), \({I}_{n}\) and \(HNode\) in offline mode. The following are the steps involved:
-
Step 1: Generates a master key \({MK}_{hn}\) for the \(HNode\).
-
Step 2: Secret key of \({S}_{n}\), \(N{K}_{n}\), is stored in \(HNode\) for further authentication.
-
Step 3: Generates unique identity \({Iid}_{in}^{^{\prime}}\) of Intermediate node (\({I}_{n}\)) and stores in \({I}_{n}\) memory.
4.2 Registration Phase of \({S}_{n}\)
\(SAdmin\) performs the following tasks to register \({S}_{n}\) as follows.
-
Step 1: \(SAdmin\) chooses a secret identity \({Sid}_{n}\) for each sensor node \({S}_{n}\) and saves in \(HNode\) memory.
-
Step 2: \(SAdmin\) computes \({P}_{n}=\) \(h({MK}_{hn}||{NK}_{n})\oplus h({Sid}_{n})\) and \({Q}_{n}={MK}_{hn}\oplus {NK}_{n}\oplus {Sid}_{n}\)
-
Stores the \({<Sid}_{n},\) \({P}_{n}\), \({Q}_{n}>\) in \({S}_{n}\) memory.
4.3 Authentication and Key Agreement Phase
Figure 3 illustrates the authentication and key agreement phase of sensor node, intermediate node and hob node and detailed descriptions are given below:
Step 1: \({S}_{n}\) → \({I}_{n}\): \({S}_{n}\) computes the following values.
Picks \({R}_{n},\) Computes \({X}_{n}={P}_{n}\oplus {R}_{n}\), \({tid}_{n}=h({Sid}_{n}\oplus {R}_{n}||{X}_{n}), and \:{C}_{n}={Sid}_{n}\oplus {R}_{n}\). Later, forward the <\({tid}_{n}, {Q}_{n}, {C}_{n}>\) to \({I}_{n}\).
Step 2: \({I}_{n}\)→\({S}_{n}\): \({I}_{n}\) computes the following values.
Picks random \({IN}_{in}\), computes \({I}_{in}={IN}_{in}\oplus {Iid}_{in}^{^{\prime}}\) and forward the parameters \(<{tid}_{n}, {Q}_{n}, {C}_{n},{I}_{in}>\) to \(HNode\) without any modification in received parameters apart from appending \({I}_{in}\) which is computed by \({I}_{n}\).
Step 3: \(HNode\) computes the following parameters to validate the legitimate user and session key generation.
Computes \({IN}_{in}={I}_{in}\oplus {Iid}_{in}^{^{\prime}},\) checks the identity of intermediate node \(I{id}_{in}^{^{\prime}}\) in its DB. Similarly, the legitimate sensor identity is also checked with all the stored values of \({NK}_{n}\) and comparing \({Q}_{n}\oplus {MK}_{hn}\oplus {NK}_{n}\) with \(S{id}_{n}\) in its DB to validate the sensor (\({S}_{n}\)). If, it will be not matched in \(HNode\) DB, then the entire process will be aborted. Otherwise, it further computes\({NK}_{n}\oplus {Sid}_{n}={Q}_{n}\oplus {MK}_{hn}\),\({X}_{n}^{*}=h(M{K}_{hn}||N{K}_{n})\oplus h\left(S{id}_{n}\right)\oplus {R}_{n}\),\({R}_{n}^{*}={X}_{n}\oplus {P}_{n}\), \({tid}_{n}^{*}=h({Sid}_{n}\oplus {R}_{n}).\) Again check the\({tid}_{n}=?{tid}_{n}^{*}\), if the values are not same, it aborts the process. If it is valid then picks random nonce \({F}_{n}\) and new\({NK}_{n}^{+}\). Further, Computes \(={F}_{n}\oplus {P}_{n}\),\({P}_{n}^{+}={h(MK}_{hn}||{NK}_{n}^{+})\oplus {h(Sid}_{n}), {Q}_{n}^{+}={MK}_{hn}^{+}\oplus {NK}_{n}^{+}\oplus {Sid}_{n}\), \(\gamma =h({Sid}_{n}|\left|{R}_{n}\right||{X}_{n}|\left|\alpha \right),\)
\(\eta ={P}_{n}^{+}\oplus \gamma ,\) \(\mu ={Q}_{n}^{+}\oplus \gamma\), \(\beta =h\left({R}_{n}|\left|{X}_{n}\right||{F}_{n}\right)\). Finally, the new session key \({K}_{s}=h(\gamma \oplus h({Sid}_{n}))\) is computed. Later, \(HNode\) forward the parameters \(<\alpha , \beta ,\eta ,\mu ,{Iid}_{in}^{^{\prime}}>\) to \({I}_{n}\) for further processing and key agreement.
Step 4: Once \({I}_{n}\) receives the parameters \(<\alpha ,\beta ,\eta ,\mu ,{Iid}_{in}^{^{\prime}}>\) from \(HNode\) then it forwards \(<\alpha ,\beta ,\eta ,\mu >\) to sensor node \({S}_{n}\).
Step 5: After receiving,\(S_{n}\) performs the following:
Computes, \(F_{n}^{*} = P_{n} \oplus\) α and \(\beta^{*} = h\left( {R_{n} \left| {\left| {X_{n} } \right|} \right|F_{n} } \right)\), and verifies \(\beta^{*} ? = \beta\). If verified successfully, it computes \(P_{n}^{ + } = \eta \oplus h(Sid_{n} \left| {\left| {R_{n} } \right|} \right|X_{n} |{|}\alpha {)}\) and the session key \(K_{s} = h( h(Sid_{n} \left| {\left| {R_{n} } \right|} \right|X_{n} |{|}\alpha {)} \oplus h\left( {Sid_{n} } \right)\), otherwise, terminate session. And finally, replace \((P_{n} , Q_{n} )\).
4.4 Sensor Node Addition
In this phase, new node can be added in targeted region of WBAN when the sensor node is depleted because of intensity utilization issue or physically trapped by an adversary from the patient body or required new sensor to sense some data. Therefore, it is needed to add new sensors dynamically into WBAN. When new wearable sensor \(S_{n}^{new}\) enters to the current network, the system administrator deploys the new node by performing the system set up phases in offline mode. The steps to perform the addition of new sensor \(S_{n}^{new}\) are given below:
Step 1: \(SAdmin\) assigns a unique identity \(Sid_{n}^{new}\) and secret key \(NK_{n}^{new}\) for new sensor node and stores these in \(HNode\).
Step 2: \(SAdmin\) further computes \(P_{n}^{new} = h(MK_{hn} ||NK_{n}^{new} ) \oplus h\left( {Sid_{n}^{new} } \right)\) and \(Q_{n}^{new} = MK_{hn} \oplus NK_{n}^{new} \oplus Sid_{n}^{new}\).
Step 3: At the end, sensor node stores the, \(\left\langle {Sid_{n}^{new} , P_{n}^{new} ,Q_{n} } \right\rangle\) in \(S_{n}^{new}\)’s memory.
Hence, the addition of new \(S_{n}^{new}\) can be done as similar to initialization or setup phase of our proposed scheme in WBAN.
5 Security Study of Our Proposed Scheme
In this section, the security analysis of our proposed scheme has been evaluated. The security study brought out certain flaws in Li et al.’s scheme in which we have defeated in this proposed work. The complete analysis of our scheme is given below:
5.1 Informal Security Analysis
In this subsection, we have analyzed the scheme in an informal method to prove that the proposed scheme resists against modern attacks.
5.1.1 Resistance Against Eavesdropping Attack
According to Dolev-Yao threat model [39], an attacker can impersonate all the messages sent over an insecure channel. If the attacker collects all the parameters \(tid_{n} , Q_{n} , C_{n} , \alpha , \beta , \eta , and\: \mu\) even then it would be infeasible to construct any of the secret parameters. The secret value \(tid_{n} = h(Sid_{n} \oplus R_{n} ||X_{n} ),\) \(P_{n} =\) \(h(MK_{hn} ||NK_{n} ) \oplus h\left( {Sid_{n} } \right)\),\(and\: \beta = h\left( {R_{n} \left| {\left| {X_{n} } \right|} \right|F_{n} } \right)\) is secured by non-reversible one-way hash function \(h\left( . \right)\) and unlike Li et al.’s scheme the secret parameter \(P_{n}\) is never been shared in our proposed scheme. Moreover, for attacker, it would be difficult to know the identity of the sensor node as identity is protected with the hash function, secret value, and XORed with the random nonce. Hence, it would be difficult for an attacker to get the session secret key \(K_{s} = h\left( {\gamma \oplus h(Sid_{n} } \right)).\)
5.1.2 Resistance Against Anonymous and Unlikabilities
The main objective of the attacker is to get the services by generating fraud authentication request and/or intercepting the communication link. While communicating between \(S_{n}\) and \(HNode\), the messages \(tid_{n} , Q_{n} , C_{n} , \alpha , \beta , \eta , and\: \mu\), are shared through the public network. Where, the temporary identity of the sensor node, \(tid_{n} = h(Sid_{n} \oplus R_{n} ||X_{n} )\), contains fresh random values for each session and \(Sid_{n}\) is protected from the hash. Moreover, unlike Li et al.’s scheme, the \(Sid_{n}\) is also checked in \(HNode\) to verify legitimate sensor node or intruder node for further computation. Therefore, an attacker cannot trace the valid \(Sid_{n}\) for linking purpose. For every session, there is a different random value \(F_{n}\) and \(\alpha = F_{n} \oplus P_{n}\) are performed at \(HNode\). During the authentication and key agreement, two links cannot be together because the sent parameters contain the fresh, secret, and random values every time. As we know that randomly selected parameters cannot figure out by an attacker to accomplish a fixed parameter. Therefore, the communication parameters are fresh, secret, and random that conducted for an alternate session. So, an attacker cannot establish a two-link or more sessions to the same node \(S_{n}\).
5.1.3 Resistance Against SENSOR Node Impersonation Attack
In this attack, the attacker is able to create legitimate tuple \(< tid_{n} , P_{n} , Q_{n} >\) to prove himself as a legitimate sensor on behalf of original one. Therefore, in our proposed scheme, the attacker can listen to the message shared between two entities, but unable to create valid \(Sid_{n}\) as the temporary identity of the sensor is shielded by the one-way hash function. If the attacker compromises any sensor \(S_{n}\) parameters, still the attacker cannot disclose the master key \(MK_{hn}\) and \(NK_{n}\) as it is ensured by hash. Hence, we can conclude that the scheme is protected against \(S_{n}\) impersonation attack. Where, Koya et al.’s [2] scheme used the Bio-key to prevents sensor node impersonation attack.
5.1.4 Resistance Against Hub Node Impersonation Attack
In our scheme, we have assumed that Hub node can never be captured or negotiated by an adversary because compromising Hub node means the entire network will break down. Hence, Hub node impersonation attack is possible only if the attacker able to retrieve the valid tuples \(\left\langle {\beta ,\eta ,\mu } \right\rangle\) of \(HNode\). The \(HNode\)’s master key \(MK_{hn}\) and temporary secret key of \(S_{n}\), i.e., \(NK_{n}\) are known to only the \(SAdmin\). Even if the attacker captures the communicated parameters, still it is infeasible for an attacker to get the master key \(MK_{hn}\) and secret key \(NK_{n}\), as both the keys are secured from one-way hash.
5.1.5 Resistance Against Replay Attack
In a replay attack, the attacker tries to fool both \(S_{n}\) and \(HNode\) by using previous transmitted messages or get the valid authentication request message and resends it into the network. To avoid replay attack in proposed protocol, during authentication, \(HNode\) sends parameters < \(\alpha ,\beta ,\eta ,\mu\) > to \(S_{n}\) which shows that for each new session, protocol uses freshness and random values to create a new session \(K_{s} = h\left( {\gamma \oplus h(Sid_{n} )} \right)\) every time. Hence, we can claim that our scheme resists against a replay attack.
5.1.6 Resistance to Forward / Backward security
In this feature, by knowing the session key \(K_{s}\) of any session, the privacy of any past or future session must not to be revealed to the adversary or not influence by the adversary. In our scheme, the session is figured out using the values \(Sid_{n} ,R_{n} ,X_{n} , \alpha\),\(P_{n}\) and \(Q_{n}\). In session key \(K_{s} = h\left( {\gamma \oplus h(Sid_{n} } \right))\), all the parameters are secure by one-way hash function and also \(\gamma\) is constructed using random nonce and freshness values for each new session \((P_{n}^{ + } , Q_{n}^{ + } )\). Therefore, knowing \(K_{s}\) does not reveal any qualities or values for generating the other session keys.
5.1.7 Resistance Against Man-in-the-Middle Attack
In this attack, the attacker alters the communication between two-parties and make both the party believe that they are exchanging the message with each other without any modification, actually the attacker is in middle. In our scheme, if the attacker captures the message parameters < \(tid_{n} , Q_{n} , C_{n} >\) sent by \(S_{n}\) to \(I_{in}\) and impersonate the intermediate identity \(< Iid_{in}^{^{\prime}} >\) even then the attacker cannot perform the Man-in-the-middle attack because the \(HNode\) database stores all the registered intermediate identity. Therefore, new proposed scheme resists against man-in-the-middle attack.
5.1.8 Resistance Against Denial-of-Service Attack (DOS) or Jamming Attack
In this scheme, we do not use the timestamps instead we use the random numbers only. The XORed, concatenation, and hash function \(h\left( . \right)\) are used in every computation of parameters. The adversary has the power to capture the \(\left\langle {\alpha ,\beta ,\eta ,\mu } \right\rangle\) parameters but never be able to extract the master key \(K_{hn}\), secret key \(NK_{n}\) and identity of a legitimate user \(Sid_{n}\). Because to process further, the sensor’s \(Sid_{n}\) is checked in \(HNode\). \(HNode\) is trustworthy that any unauthorized user cannot be compromised. Hence, our scheme resists the DOS attacks and also adversary cannot perform as a legitimate sensor.
5.1.9 Resistance Against Capture Sensor Node Attack
To play the sensor node capture attack, the adversary must reveal the real user values < \(tid_{n} , P_{n} ,Q_{n}\) > . To know those values the adversary needs to find sensor personal identity \(Sid_{n}\) and \(X_{n}\) which is impossible for the adversary because the identity of the sensor node is checked in the \(HNode\) of DB. If the sensor node is captured by the adversary, even then for the attacker it is hard to compute the master key \(MK_{hn}\) because the \(MK_{hn}\) is shielded by randomness and one-way hash. Here, even if the adversary captures \(n\) th numbers of \(S_{n}\) the attacker cannot get any advantages. Therefore, our proposed scheme resists against the node capture attack.
5.1.9.1 Resistance Against Fault Node Addition or SCALABILITY
The scalability of our proposed protocol is guaranteed when the network remains non-degrade and maintains the security of the system during the joining of a new node or removing a node from the system. The proposed scheme removes the unauthorized nodes or illegitimate nodes from the system as the hub node checks the sensor identity in the hub node database whether it is registered in-network or not. If register, then only register sensors node allows for the session and discard illegitimate nodes. The proposed scheme even achieves scalability by reducing the communication cost, memory overhead, and most of the security functionalities. Hence, proposed protocol achieves the efficiency and better scalability than other related schemes [1, 2].
5.1.9.2 Resistance Against Ephemeral Secret Key Leakage
In this attack, attacker compromises the private keys of sensors and the session key from eavesdropped messages. In our proposed scheme, to achieve authentication between sensor node and hub node, The following parameters are needed to compute,\(X_{n}^{*} = h(MK_{hn} ||NK_{n} ) \oplus h\left( {Sid_{n} } \right) \oplus R_{n}\), and \(R_{n}^{*} = X_{n} \oplus P_{n}\), \(tid_{n}^{*} = h\left( {Sid_{n} \oplus R_{n} } \right).\) Again check the \(tid_{n} = ?tid_{n}^{*}\), if their value is not same it aborts the process. if it is valid, picks random nonce \(F_{n}\), and new \(NK_{n}^{ + }\). Further, α \(= F_{n} \oplus P_{n}\), \(P_{n}^{ + } = h(MK_{hn} ||NK_{n}^{ + } ) \oplus h(Sid_{n} ), Q_{n}^{ + } = MK_{hn}^{ + } \oplus NK_{n}^{ + } \oplus Sid_{n}\), \(\gamma = h(Sid_{n} \left| {\left| {R_{n} } \right|} \right|X_{n} |{|}\alpha {)},\eta = P_{n}^{ + } \oplus \gamma ,\) \(\mu = Q_{n}^{ + } \oplus \gamma\), \(\beta = h\left( {R_{n} \left| {\left| {X_{n} } \right|} \right|F_{n} } \right)\) and key \(K_{s} = h\left( {\gamma \oplus h(Sid_{n} }) \right)\) are computed. Since it would be also difficult to construct secret parameters of sensor node secret key \(NK_{n}\) and \(F_{n}\) as it is temporary which is stored in Hub node. Once the mutual authentication is done, secret key and random nonce are discarded. Therefore, attacker cannot perform Ephemeral secret key leakage even if the message is eavesdropped.
5.1.9.3 Resistance Against Hub Node Stolen Database Attack
In proposed scheme, we have considered the Hub node can never be captured or negotiated by a foe since compromising the Hub node means the whole system will pause down [34]. Even, in our scheme considered database is protected from database security threats, and only the administrator gives the privilege to genuine sensors to contact database as database is updated periodically [46]. Hence, Hub node is trusted and it will not harm the encryption keys of the authorized users or the keys of sensor nodes shared between them.
5.2 Security Analysis Using BAN-Logic
BAN logic [1, 37, 38] is used to verify the mutual authentication and key agreement between the \(S_{n}\) and \(HNode\). To prove our scheme and to demonstrate a secure mechanism, the following are the four goals we need to prove using BAN-logic.
5.2.1 Basic Notation
The basic notation used in BAN logic [1, 40, 41] is listed below.
-
\(C|\)≡\(D\): C believes if D is true.
-
\(C \triangleleft D:\) C sees D, D may be the data or messages which can be read by C and repeats D.
-
\(C|\sim D:\) C said D, C sent a data including D, in this logic C does not know the current data send or past data, the logic concludes C believes D.
-
\(C\left| = \right\rangle D:\) C control or jurisdiction over D, in this logic, C has the authority and trusted the quality of message or data.
-
\(\# \left( D \right):\) D is fresh, the logic said D is fresh, not used before for any data or authentication.
-
\(< D >_{E}\): D is combined with E
-
\(C\mathop \leftrightarrow \limits^{Key} F:\) the secret key shared between C and F which is only known to both.
5.2.2 Inference Rules
There are five rules of BAN logic [40, 41] need to prove to show the efficiency of our proposed scheme.
R_1: [Message meaning rule]: \(\frac{{{\text{C}}| \equiv {\text{C}}\begin{array}{*{20}c} E \\ \leftrightarrow \\ {} \\ \end{array} F, C \triangleleft \left\langle D \right\rangle_{E} }}{{{\text{C}}\left| { \equiv {\text{F}}} \right|\sim {\text{D}}}}\).
R_2: [Nonce-verification rule]:\({ }\frac{{{\text{C}}| \equiv \# \left( {\text{D}} \right),{\text{ C}}\left| { \equiv {\text{F}}} \right|\sim {\text{D}}}}{{{\text{C}}\left| { \equiv {\text{F}}} \right| \equiv {\text{D}}}}\).
R_3: [Jurisdiction rule]:\({ }\frac{{{\text{C}}\left| { \equiv {\text{F}}} \right| \Rightarrow {\text{D}},{\text{ C}}\left| { \equiv {\text{F}}} \right| \equiv {\text{D}}}}{{{\text{C}}| \equiv {\text{D}}}}\).
R_4: [Freshness-conjuncatenation rule]:\({ }\frac{{{\text{C}}| \equiv \# \left( {\text{D}} \right)}}{{{\text{C}}| \equiv \# \left( {{\text{D}},{\text{E}}} \right)}}\).
R_5: [Belief rule]:\({ }\frac{{{\text{C}}| \equiv \left( {{\text{C}},{\text{E}}} \right)}}{{{\text{C}}| \equiv \# \left( {\text{C}} \right)}}\).
5.2.3 Assumption
A1: \(HNode|\)≡\(\left( {S_{n} \mathop \leftrightarrow \limits^{{Sid_{n} }} HNode} \right)\).
A2: \(HNode|\)≡\(\# \left( {F_{n} } \right)\).
A3: \(HNode|\)≡\(S_{n} \left| = \right\rangle \left( {S_{n} \mathop \leftrightarrow \limits^{{X_{N} }} HNode} \right)\).
A4: \(S_{n} |\)≡\(S_{n} | \equiv \left( {S_{n} \mathop \leftrightarrow \limits^{{Sid_{n} }} HNode} \right)\).
A5: \(S_{n} |\)≡\(\# \left( {R_{n} } \right)\).
A6: \(S_{n} |\)≡\(HNode\left| = \right\rangle \left( {S_{n} \mathop \leftrightarrow \limits^{{K_{s} }} HNode} \right)\).
5.2.4 Goal
Goal_1:\(HNode|\)≡\(S_{n} | \equiv \left( {S_{n} \mathop \leftrightarrow \limits^{{X_{N} }} HNode} \right)\).
Goal_2:\(HNode|\)≡\(\left( {S_{n} \mathop \leftrightarrow \limits^{{X_{N} }} HNode} \right)\).
Goal_3:\(S_{n} |\)≡\(HNode| \equiv \left( {S_{n} \mathop \leftrightarrow \limits^{{K_{s} }} HNode} \right)\).
Goal_4: \(S_{n} |\)≡\(\left( {S_{n} \mathop \leftrightarrow \limits^{{K_{s} }} HNode} \right)\).
5.2.5 Message
Message 1: \(S_{n} \to HNode: < S_{n} \mathop \leftrightarrow \limits^{{X_{n} }} HNode,R_{n} >_{{S_{n} \mathop \leftrightarrow \limits^{{Sid_{n} }} HNode}}\).
Message 2:\(HNode \to S_{n} : < S_{n} \mathop \leftrightarrow \limits^{{X_{n} }} HNode,R_{n} , NK_{n}^{ + } ,F_{n} ,S_{n} \mathop \leftrightarrow \limits^{{K_{s} }} HNode >_{{S_{n} \mathop \leftrightarrow \limits^{{Sid_{n} }} HNode}}\).
5.2.6 Formal Verification of Proposed Scheme Using BAN Logic Rules
To achieve the Goal_1 to Goal_4, we need to prove following steps.
Step_1: Applying message meaning rule, from 5.2.4 message 1, and assumption A1, we assume
Step_2: Applying the freshness rule, and assumption A2, we assume
Step_3: Putting the Nonce-verification rule, Step_1 and Step_2, we can assume
Step_4: Applying belief rule and step_3, we can assume.
\(\frac{{HNode\left| { \equiv S_{n} } \right| \equiv \left( {S_{n} \begin{array}{*{20}c} {X_{n} } \\ \leftrightarrow \\ {} \\ \end{array} HNode,F_{n} } \right)}}{{HNode\left| { \equiv S_{n} } \right| \equiv \left( {S_{n} \begin{array}{*{20}c} {X_{n} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right)}}\) Goal_1
Step_5: Applying jurisdiction rule, A3 and Step_4, we assume.
\(\frac{{HNode\left| { \equiv S_{n} } \right| \Rightarrow \left( {S_{n} \begin{array}{*{20}c} {X_{n} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right),HNode\left| { \equiv S_{n} } \right| \equiv \left( {S_{n} \begin{array}{*{20}c} {X_{n} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right)}}{{HNode| \equiv \left( {S_{n} \begin{array}{*{20}c} {X_{n} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right)}}\) Goal_2
Step_6: Applying message meaning rule, message 2 and assumption A4, we assume
Step_7: Applying freshness rule and A5, we assume
Step_8: Applying nonce verification rule, Step_6 and Step_7, we can assume
Step_9: Applying belief rule and step_8, we can assume.
\(\frac{{S_{n} \left| { \equiv HNode} \right| \equiv \left( {S_{n} \begin{array}{*{20}c} {K_{s} } \\ \leftrightarrow \\ {} \\ \end{array} HNode,F_{n} ,R_{n} , X_{n} ,P_{n}^{ + } } \right)}}{{S_{n} \left| { \equiv HNode} \right| \equiv \left( {S_{n} \begin{array}{*{20}c} {K_{s} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right)}}\) Goal_3
Step_10: Applying jurisdiction rule, A6 and Step_9, we assume.
\(\frac{{S_{n} \left| { \equiv HNode} \right| \Rightarrow \left( {S_{n} \begin{array}{*{20}c} {K_{s} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right),S_{n} \left| { \equiv HNode} \right| \equiv \left( {S_{n} \begin{array}{*{20}c} {K_{s} } \\ \leftrightarrow \\ {} \\ \end{array} HNode,F_{n} ,R_{n} ,{ }X_{n} ,P_{n}^{ + } } \right)}}{{S_{n} | \equiv \left( {S_{n} \begin{array}{*{20}c} {K_{s} } \\ \leftrightarrow \\ {} \\ \end{array} HNode} \right)}}{ }\) Goal_4.
The above steps prove that our scheme reach all the goal. Hence, the mutual authentication and key agreement between the \(HNode\) and \(S_{n}\) is proved.
5.3 Security Analysis Using ProVerif Simulation Tool
In this subsection, we have proved the authentication and session secrecy of our proposed scheme using the simulation tool called ProVerif [42, 43]. The authenticity of all nodes \(S_{n} , HNode\) and \(I_{n}\) is verified. The detailed description of our proposed scheme is defined in Tables 2, 3, 4, 5, 6, 7, 8 . Here, we use two channels Ch1 for \(S_{n}\) and Ch2 for \(HNode\) through which communication is done.
5.3.1 Output of the Proposed Scheme
ok, secrecy assumption verified: fact unreachable attacker(Idin'[])
ok, secrecy assumption verified: fact unreachable attacker(Rn[])
ok, secrecy assumption verified: fact unreachable attacker(khn[])
ok, secrecy assumption verified: fact unreachable attacker(kn[])
ok, secrecy assumption verified: fact unreachable attacker(SIdn[])
ok, secrecy assumption verified: fact unreachable attacker(KEY[])
RESULT not attacker(khn[]) is true.
RESULT not attacker(kn[]) is true.
RESULT not attacker(SIdn[]) is true.
RESULT not attacker(KEY[]) is true.
RESULT not attacker(Idin'[]) is true.
RESULT not attacker(Rn[]) is true.
Starting query inj-event(HNAccept(IN_46,N)) = = > inj-event(INAccept(HN))
RESULT inj-event(HNAccept(IN_46,N)) = = > inj-event(INAccept(HN)) is true.
Starting query inj-event(HNAccept(IN_48,N_47)) = = > inj-event(sensorAcceptS(HN_49,IN_48))
RESULT inj-event(HNAccept(IN_48,N_47)) = = > inj-event(sensorAcceptS(HN_49,IN_48)) is true.
Output: To test identity, random, secret key, and privacy, we test the “Query not attacker” the results is true which indicates the all secret parameters not derivable by the adversary. The “Injective Correspondence” shows the one-to-one relationship of authentication. The event “event” shows that Intermediate node, Hub Node, and sensor node accept to run the protocol.
6 Performance evaluation and comparisons
In this section, we compared our scheme with other related schemes i.e., Li et al. [1], Koya et al. [2], Ibrahim et al. [30], Kompara et al. [32], Xu et al. [34], Gupta et al. [35], Almuhaideb et al. [36] and Sowjanya et al. [44]. The performance analysis is done based on security functionality, communication cost, computation cost, and memory overhead. Table 9 illustrates the types of security aspect that prevents various related schemes.
6.1 Security Functionality of Various Existing Schemes and Our Scheme
-
Table 9 shows the security comparison of various related schemes of authentication and key agreement. In Li et al. [1] scheme, the sensor node capture attack, DoS attack, eavesdropping, anonymity, unlinkable, and dynamic addition of node cannot be prevented. On other hand Koya et al. [2] scheme can prevent anonymity, unlinkable, replay attack, and addition of dynamic node. In addition, [30, 32, 34,35,36, 44] have satisfied less security functionality than the proposed scheme. Table 9 shows the attacks can be prevented in our scheme that satisfies the security functionalities.
6.2 Communication cost of message exchanges
Table 10 illustrates the communication cost of message exchange overhead among the \(S_{n}\), \(I_{n}\), and \(HNode\). Considering the other related schemes time stamp size is 32-bits, \(Iid_{in}^{^{\prime}}\) = 16 bits and other parameters as 160-bits each. While comparing to other related schemes our scheme has the less communication cost.
6.3 Computational Cost in Terms of Hash Functions and XORed Functions
While talking about the cryptography security, the cryptography function like hash function and XOR operation is considered. Here, we consider \(t_{Xor}\) for XOR operation and \(t_{H}\) for hash function. Compared to other schemes, our proposed scheme in the authentication and key agreement phase, sensor node performs the \(7t_{Xor}\) operation and \(7t_{H}\) of hash operation. On the other hand, \(HNode\) uses the total of \(14t_{Xor} + 7t_{H}\) which is at par lesser than Koya et al.’s [2] scheme. Table 11 shows the computation cost in terms of hash and XORed function.
6.4 Memory Overhead of Sensor Node and Hub Node
In our proposed scheme, sensor node stores its identity \(Sid_{n} , { }\) parameters \({ }P_{n} ,Q_{n}\) and its session key \(K_{s}\) in its memory. Let considered each parameter to be 128 bits each. So, the required memory in the sensor node is 640-bits similar to other related schemes Li et al.’s [1], Koya et al.’s [2], and Ibrahim et al.’s [30]. Similarly, hub node stores \(Iid_{in}^{^{\prime}} ,MK_{hn} ,NK_{n} ,Sid_{n}\) and its corresponding session key \(K_{s}\). The \(Iid_{in}^{^{\prime}}\) is assumed to be 16 bits and \(n\) numbers of sensor nodes in a network of \(HNode.\) Here we use SHA-1 to hash the values, and to produce of SHA-1 is 160 bits. The parameters \(MK_{hn} = NK_{n} = Sid_{n} = K_{s} = 160\) bits. Therefore, the total storage required in \(HNode\) is 160 + 16 bits. The comparison of memory overhead is illustrated in Table 12.
7 Conclusion
In this paper, we have proposed an improved secure lightweight authentication scheme for sensor node and hub node in WBAN. The scheme includes cryptographic functions like XOR operations, concatenations, nonce, and hash functions. One of the problems in Li et al.’s scheme is the session traceable for a different session. Therefore, firstly we have removed the session traceable problem. Secondly, as an adversary may create a new \(Sid_{n}\) to perform authentication and key agreement, thus, to resolve, in our proposed scheme, \(SAdmin\) stores all the legitimate \(Sid_{n}\) in \(HNode\)’s DB. As a result, an adversary cannot perform any impersonation attack. Thirdly, using the timestamp, may result of the time synchronization issue. Therefore, we have designed our proposed scheme without use of any timestamp variables. In addition, as the sensor node is resource-limited, and less battery power supply, thus, our proposed scheme has been constructed such a way which will consume less computation cost, however, memory storage is almost the equal of all previous related schemes. The BAN logic has also been used to determine the correctness of exchange information of our scheme and also helped to prove our scheme is protected from eavesdropping attacks. Lastly, the key secrecy evolution has been performed using formal verification, i.e., ProVerif simulation tool and we have proved that our proposed scheme is secure as per our claims. However, WBANs have many challenges like sensor device energy supply, mobility, health information privacy, etc.. Hence, needs to develop some more appropriate intelligence sensor devices and protocols that work under low battery, require less computation and highly secure that resolve the specific problems and helps doctors to diagnose the patients.
References
Li, X.; Ibrahim, M.H.; Kumari, S.; Sangaiah, A.K.; Gupta, V.; Choo, K.K.R.: Anonymous mutual authentication and key agreement scheme for wearable sensors in wireless body area networks. Comput. Netw. 129, 429–443 (2017)
Koya, A.M.; Deepthi, P.P.: Anonymous hybrid mutual authentication and key agreement scheme for wireless body area network. Comput. Netw. 140, 138–151 (2018)
IEEE Standards Association, 2012. IEEE standard for local and metropolitan area networks-part 15.6: wireless body area networks. IEEE std, 802(6): 2012.
Li, X.; Niu, J.; Khan, M.K.; Liao, J.: An enhanced smart card based remote user password authentication scheme. J. Netw. Comput Appl. 36(5), 1365–1371 (2013)
Jiang, Q.; Khan, M.K.; Lu, X.; Ma, J.; He, D.: A privacy preserving three-factor authentication protocol for e-Health clouds. J. Supercomput. 72(10), 3826–3849 (2016)
Li, X.; Xiong, Y.; Ma, J.; Wang, W.: An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 35(2), 763–769 (2012)
Li, X.; Ma, J.; Wang, W.; Xiong, Y.; Zhang, J.: A novel smart card and dynamic ID based remote user authentication scheme for multi-server environments. Math. Comput. Model. 58(1–2), 85–95 (2013)
Wang, D.; Wang, P.: On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 73, 41–57 (2014)
Wang, D.; Wang, P.: Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 20, 1–15 (2014)
Venkatasubramanian, K.K.; Banerjee, A.; Gupta, S.K.S.: PSKA: Usable and secure key agreement scheme for body area networks. IEEE Trans. Inf Technol. Biomed. 14(1), 60–68 (2009)
Zhang, Z.; Wang, H.; Vasilakos, A.V.; Fang, H.: ECG-cryptography and authentication in body area networks. IEEE Trans. Inf Technol. Biomed. 16(6), 1070–1078 (2012)
Poon, C.C.; Zhang, Y.T.; Bao, S.D.: A novel biometrics method to secure wireless body area sensor networks for telemedicine and m-health. IEEE Commun. Mag. 44(4), 73–81 (2006)
Miao, F.; Bao, S.D.; Li, Y.: Biometric key distribution solution with energy distribution information of physiological signals for body sensor network security. IET Inf. Secur. 7(2), 87–96 (2013)
Mathur, S.; Miller, R.; Varshavsky, A.; Trappe, W. and Mandayam, N.; 2011, June. Proximate: proximity-based secure pairing using ambient wireless signals. In Proceedings of the 9th international conference on Mobile systems, applications, and services (pp. 211–224). ACM.
Li, M.; Yu, S.; Guttman, J.D.; Lou, W.; Ren, K.: Secure ad hoc trust initialization and key management in wireless body area networks. ACM Trans. sensor Netw. (TOSN) 9(2), 18 (2013)
Liu, J.; Zhang, Z.; Chen, X.; Kwak, K.S.: Certificateless remote anonymous authentication schemes for wirelessbody area networks. IEEE Trans. Parallel Distrib. Syst. 25(2), 332–342 (2013)
Zhao, Z.: An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2), 13 (2014)
Xiong, H.: Cost-effective scalable and anonymous certificateless remote authentication protocol. IEEE Trans. Inf. Forensics Secur. 9(12), 2327–2339 (2014)
He, D.; Zeadally, S.: Authentication protocol for an ambient assisted living system. IEEE Commun. Mag. 53(1), 71–77 (2015)
Shen, J.; Tan, H.; Moh, S.; Chung, I.; Liu, Q.; Sun, X.: Enhanced secure sensor association and key management in wireless body area networks. J. Commun. Netw. 17(5), 453–462 (2016)
He, D.; Zeadally, S.; Kumar, N.; Lee, J.H.: Anonymous authentication for wireless body area networks with provable security. IEEE Syst. J. 11(4), 2590–2601 (2016)
Liu, J.; Zhang, L.; Sun, R.: 1-RAAP: An efficient 1-round anonymous authentication protocol for wireless body area networks. Sensors 16(5), 728 (2016)
Tan, C.C.; Wang, H.; Zhong, S.; Li, Q.: IBE-lite: a lightweight identity-based cryptography for body sensor networks. IEEE Trans. Inf Technol. Biomed. 13(6), 926–932 (2009)
Huang, C.; Lee, H.; Lee, D.H.: A privacy-strengthened scheme for E-healthcare monitoring system. J. Med. Syst. 36(5), 2959–2971 (2012)
Challa, S.; Das, A.K.; Odelu, V.; Kumar, N.; Kumari, S.; Khan, M.K.; Vasilakos, A.V.: An efficient ECC-based provably secure three-factor user authentication and key agreement protocol for wireless healthcare sensor networks. Comput. Electr. Eng. 69, 534–554 (2018)
Yeh, K.H.: A secure IoT-based healthcare system with body sensor networks. IEEE Access 4, 10288–10299 (2016)
Shen, J.; Chang, S.; Shen, J.; Liu, Q.; Sun, X.: A lightweight multi-layer authentication protocol for wireless body area networks. Futur. Gener. Comput. Syst. 78, 956–963 (2018)
Zebboudj, S.; Cherifi, F.; Mohammedi, M.; Omar, M.: Secure and efficient ECG-based authentication scheme for medical body area sensor networks. Smart Health 3, 75–84 (2017)
Zhao, H.; Xu, R.; Shu, M.; Hu, J.: Physiological-signal-based key negotiation protocols for body sensor networks: a survey. Simul. Model. Pract. Theory 65, 32–44 (2016)
Ibrahim, M.H.; Kumari, S.; Das, A.K.; Wazid, M.; Odelu, V.: Secure anonymous mutual authentication for star two-tier wireless body area networks. Comput. Methods Programs Biomed. 135, 37–50 (2016)
Kompara, M.; Hölbl, M.: Survey on security in intra-body area network communication. Ad Hoc Netw. 70, 23–43 (2018)
Kompara, M.; Islam, S.H.; Hölbl, M.: A robust and efficient mutual authentication and key agreement scheme with untraceability for WBANs. Comput. Netw. 148, 196–213 (2019)
Konan, M.; Wang, W.: A secure mutual batch authentication scheme for patient data privacy preserving in wban. Sensors 19(7), 1608 (2019)
Xu, Z.; Xu, C.; Liang, W.; Xu, J.; Chen, H.: A lightweight mutual authentication and key agreement scheme for medical Internet of Things. IEEE Access 7, 53922–53931 (2019)
Gupta, A.; Tripathi, M.; Sharma, A.: A provably secure and efficient anonymous mutual authentication and key agreement protocol for wearable devices in WBAN. Comput. Commun. 160, 311–325 (2020)
Almuhaideb, A.M.; Alqudaihi, K.S.: A Lightweight and Secure Anonymity Preserving Protocol for WBAN. IEEE Access. 8, 178183–178194 (2020)
Madhusudhan, R.; Shashidhara.: A secure and lightweight authentication scheme for roaming service in global mobile networks. J. Inf. Secur. Appl. 38, 96–110 (2018)
Clifford Neuman, B.; Stuart, G.S.: A Note on the Use of Timestamps as Nonces. Oper. Syst. Rev. 27(2), 10–14 (1993)
Dolev, D.; Yao, A.: On the security of public key protocols. IEEE Trans. Inf. Theory 29(2), 198–208 (1983)
Burrows, M.; Abadi, M. and Needham, R.M.: A logic of authentication. Proceedings of the Royal Society of London. A. Mathematical and Physical Sciences, 426(1871): 233–271 (1989).
Islam, S.H.; Biswas, G.P.: A pairing-free identity-based two-party authenticated key agreement protocol for secure and efficient communication. J. King Saud Univ.-Comput. Inf. Sci. 29(1), 63–73 (2017)
Blanchet, B.: Modeling and verifying security protocols with the applied pi calculus and ProVerif. Found. Trends® Priv. Secur. 1(1–2), 1–135 (2016)
Blanchet, B.: June. An efficient cryptographic protocol verifier based on prolog rules. csfw 1, 82–96 (2001)
Sowjanya, K.; Dasgupta, M.; Ray, S.: An elliptic curve cryptography based enhanced anonymous authentication protocol for wearable health monitoring systems. Int. J. Inf. Secur. 19(1), 129–146 (2020)
Kilinc, H.H.; Yanik, T.: A survey of SIP authentication and key agreement schemes. IEEE Commun. Surv. Tutor. 16(2), 1005–1023 (2013)
Yamano, K., Sharp Corp, 2006. Node structure information management method and radio network system. U.S. Patent 7,103,354.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chunka, C., Banerjee, S. An Efficient Mutual Authentication and Symmetric Key Agreement Scheme for Wireless Body Area Network. Arab J Sci Eng 46, 8457–8473 (2021). https://doi.org/10.1007/s13369-021-05532-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-021-05532-8