Abstract
User authentication is one of the most important security services required for the resource-constrained wireless sensor networks (WSNs). In user authentication, for critical applications of WSNs, a legitimate user is allowed to query and collect the real-time data at any time from a sensor node of the network as and when he/she demands for it. In order to get the real-time information from the nodes, the user needs to be first authenticated by the nodes as well as the gateway node (GWN) of WSN so that illegal access to nodes do not happen in the network. Recently, Jiang et al. proposed an efficient two-factor user authentication scheme with unlinkability property in WSNs Jiang (2014). In this paper, we analyze Jiang et al.’s scheme. Unfortunately, we point out that Jiang et al.’s scheme has still several drawbacks such as (1) it fails to protect privileged insider attack, (2) inefficient registration phase for the sensor nodes, (3) it fails to provide proper authentication in login and authentication phase, (4) it fails to update properly the new changed password of a user in the password update phase, (5) it lacks of supporting dynamic sensor node addition after initial deployment of nodes in the network, and (6) it lacks the formal security verification. In order to withstand these pitfalls found in Jiang et al.’s scheme, we aim to propose a three-factor user authentication scheme for WSNs. Our scheme preserves the original merits of Jiang et al.’s scheme. Our scheme is efficient as compared to Jiang et al.’s scheme and other schemes. Furthermore, our scheme provides better security features and higher security level than other schemes. In addition, we simulate our scheme for the formal security analysis using the widely-accepted AVISPA (Automated Validation of Internet Security Protocols and Applications) tool. The simulation results clearly demonstrate that our scheme is also secure.
Similar content being viewed by others

Avoid common mistakes on your manuscript.
1 Introduction
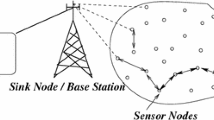
A wireless sensor network (WSN) is composed of several tiny computing nodes, called the sensor nodes or motes, which could be order of hundreds or several hundreds. Typically the sensor nodes are deployed randomly in a target field (also called the deployment area) for the purpose of sensing important information from their surrounding fields and then sending those sensing information to the nearby base station or the gateway node (GWN). Sensor nodes communicate among each other by short range radio communications. The base station is a computationally well-equipped node in the network, whereas the sensor nodes are resource-starved. Since the GWN can reach all the sensor nodes in a network, depending on the applications, the GWN can be located either in the center or at a corner of the network.
Sensor networks are widely deployed in a variety of applications ranging from military to environmental and medical research. In many applications, such as target tracking, battlefield surveillance and intruder detection, WSNs often operate in hostile and unattended environments. Therefore, there is a strong need for protecting the sensing data and sensing readings. In wireless environments, an adversary not only can eavesdrop the radio traffic, but also has the ability to intercept or interrupt the exchanged messages. Thus, many protocols and algorithms do not work in hostile environments without adequate security measures. Hence, security becomes one of the major concerns when there are potential attacks against sensor networks.
Consider the scenario of battle field surveillance which is one of the major military applications. A large number of sensor nodes are rapidly deployed in a battlefield via airplanes or trucks. Each individual sensor node monitors conditions and activities in its surroundings after deployment in the battle field and then reports these sensing observations to the GWN via wireless communications through its neighboring sensor nodes. The GWN then can conduct a more accurate detection on the activities (for example, possible attacks) of the opposing force after collecting a large number of sensing observations from the sensor nodes. Thus, the appropriate decisions as well as responses can be made quickly in the battle field.
In user authentication in WSN, a legitimate user is allowed to query and collect the real-time data at any time from a sensor node of the network as and when he/she demands for it. As most of the WSN applications are real-time based, so the users (called the external parties) are generally interested in accessing the real-time information. This could happen if we allow the users to access the real-time data directly from the nodes inside WSN. Usually, the information from nodes are gathered periodically in the GWN and hence, the gathered information may not be real-time. In order to access the real-time information from the nodes, the user needs to be first authenticated to the sensor nodes as well as the GWN so that illegal access to nodes do not happen. As a result, the user authentication problem becomes a very important topic in research of WSN security.
Several two-factor user authentication schemes have been proposed in the literature [6, 13, 17, 18, 20, 22, 28, 29, 35, 37, 40, 41], which use a user’s smart card and password. However, most of these proposals are insecure against different known attacks. Recently, Jiang et al. [21] proposed an efficient two-factor user authentication scheme for WSNs. However, in this paper, we analyze the recently proposed Jiang et al.’s scheme [21] and show that unfortunately their scheme has several drawbacks. In order to remedy these drawbacks found in Jiang et al.’s scheme, we aim to propose a secure and robust temporal credential-based user anonymity and unlinkability-preserving three factor user authentication scheme for wireless sensor networks. In our scheme, we use a user’s personal biometric as the third factor apart from that user’s smart card and password.
Tan [36] extended the security requirements of two-factor authentication schemes to three-factor authentication schemes, which are given below:
-
Mutual authentication. After run of the protocol, the server should believe that the remote user is a legitimate registered client. The user also believes that the communicating party is the server which the user intended to login to.
-
Server not knowing password and biometric. The registration center (server) should not have any information about the registered user’s password and personal biometrics. This is extremely required because several users may apply the same password to access different servers in the real applications. As a result, if a privileged insider of the registration center knows the password or biometrics of a user U i , he/she may impersonate U i for accessing the services from other servers.
-
Freedom of password and biometric update. A user should be allowed to change/update freely his/her password as well as biometric template without contacting the server. The server must be totally unaware of the change of the user’s password and biometric template.
-
Three-factor security. In the security model for three-factor authentication schemes, an adversary can have full control over the communication channel between the users and the server during the login phase and the authentication and key agreement phase. In the three-factor security adversary model, the adversary is modeled to have at most two of the following three abilities, but it is not allowed to have all the three abilities. The adversary can use the techniques in [24, 27] to extract the information from the smart card, obtain the password, or access the biometric template. This model is not applicable for a privileged insider attack, where a legal user U is himself/herself is an insider attacker, who knows all these three factors: smart card, password and personal biometrics.
1.1 Related work
Watro et al. [38] proposed a public-key cryptography based user authentication scheme in WSNs, which is known as TinyPK. Their scheme is based on RSA cryptosystem [31] and Diffie-Hellman key exchange protocol [14]. However, their protocol is insecure as pointed out in [13]. Later, Wong et al. [39] proposed a user authentication scheme, which is password-based and uses the hash function. Their scheme is vulnerable to many logged-in users with the same login id attack and also suffers from the stolen-verifier attack, because both the GWN and login-sensor node need to maintain a lookup table of the registered users’ credentials. M. L. Das [13] introduced an efficient scheme, which uses password and smart card of a user. This scheme is however vulnerable to the denial-of-service attack as well as node capture attack [12]. Many researchers then inspired from this work and proposed several improvements [6, 17, 18, 20, 22, 28, 37].
Fan et al. [17] proposed a user authentication scheme based on two-tiered WSNs. Their scheme is efficient and also resists the denial-of-service attack. Chen and Shih [6] proposed a robust mutual authentication scheme for WSNs, which withstands te security pitfalls of M. L. Das’s scheme [12]. Yuan et al. [42] proposed a biometric-based user authentication scheme, which uses the similar concept of M. L. Das’s scheme [13]. Their scheme has the same drawbacks as found in [13]. Das et al. [9, 12] proposed a two-factor dynamic password-based user authentication scheme for hierarchical wireless sensor networks, which has several attractive features such as dynamic node addition, correct password change phase and session key agreement.
Yoo et al. [41] proposed a robust two-factor user authentication scheme. But their scheme does not provide user privacy protection [21]. Sun et al. [35] proposed an improvement over Khan-Alghathar’s scheme [22] in order to withstand the GWN impersonation attack. As pointed out in [21], Sun et al.’s scheme [35] does not provide user privacy protection, mutual authentication between a user and the GWN, and also session key agreement between a user and an accessed sensor node. Xue et al. [40] further proposed a temporal credential-based mutual authentication and key agreement scheme for WSNs, which is efficient due to use of the hash function. However, Jiang et al. [21] pointed out that Xue et al.’s scheme is vulnerable to identity guessing attack, tracking attack, privileged-insider attack and stolen smart card attack. To remedy these weaknesses, Jiang et al. further proposed a two-factor user authentication scheme for WSNs. However, in this paper, we again analyze the recently proposed Jiang et al.’s scheme [21] and show that unfortunately their scheme has several drawbacks, which are discussed in detail in Section 4.
1.2 Threat model
We make use of the Dolev-Yao threat model [16] in which two communicating parties communicate over an insecure channel. Any adversary (attacker or intruder) can eavesdrop the transmitted messages over the public insecure channel and he/she has the ability to modify, delete or change the contents of the transmitted messages. Usually the smart card of a user is equipped with the tamper-resistant hardware. However, if a user’s smart card is stolen or lost, an attacker can still know all the sensitive information stored in its memory by monitoring the power consumption of the smart card [24, 27].
1.3 Notations
In this paper, we use the notations listed in Table 1 throughout the paper in order to analyze Jiang et al.’s scheme, and also describe and analyze our proposed scheme.
1.4 Our contributions
We list the following contributions made in this paper:
-
We first analyze the security of the recently proposed Jiang et al.’s scheme [21], and find that their scheme has several drawbacks.
-
In order to remedy, the drawbacks found in Jiang et al.’s scheme, we propose a secure and robust temporal credential based user anonymity and unlinkability preserving three-factor user authentication scheme in WSNs. Our scheme makes use of three factors, namely user’s identity, password and biometric.
-
Through the rigorous informal and formal security analysis, we show that our scheme can withstands several known attacks including the attacks found in Jiang et al.’s scheme.
-
We analyze the efficiency of our proposed scheme, and show that our scheme is also efficient as compared to Jiang et al.’s scheme and other related schemes in WSNs.
-
We simulate our scheme for the formal security analysis using the widely-accepted AVISPA (Automated Validation of Internet Security Protocols and Applications) tool [2] and the simulation results clearly demonstrate that our scheme is secure.
1.5 Roadmap of the paper
The remainder of this paper is organized as follows. In Section 2, we discuss some basic preliminaries such as one-way hash function and fuzzy extractor technique, which are essential for better understanding the paper. In Section 3, we review the recently proposed Jiang et al.’s scheme [21]. We then analyze the security of their scheme in Section 4. In Section 5, we propose a secure and robust three-factor user authentication scheme in WSNs. In Section 6, through the formal and informal security analysis we show that our scheme has the ability to tolerate various known attacks. In Section 7, we simulate our scheme for the formal security verification using AVISPA tool. We compare the performance of our scheme with Jiang et al.’s scheme and other schemes in Section 8. Finally, we conclude the paper in Section 9.
2 Mathematical preliminaries
In this section, we briefly describe some mathematical preliminaries, which are essential for describing and analyzing Jiang et al.’s scheme [21] as well as our proposed scheme.
2.1 Collision-resistant one-way hash function
We define the formal definition of a one-way collision-resistant hash function as follows ([10, 32, 34]).
Definition 1
A collision-resistant one-way hash function h:A → B, where A = {0, 1}∗ and B = {0, 1}n, is a deterministic algorithm that takes an input as an arbitrary length binary string x ∈ A and produces an output y ∈ B, a binary string of fixed-length, n. Let \(Adv_{\mathcal {A}}^{HASH} (t_{1})\) denote an adversary (attacker) \(\mathcal {A}\)’s advantage in finding collision. Then, we have
where P r[E] denotes the probability of a random event E, and \((x, x^{\prime }) \in _{R} \mathcal {A}\) denotes the pair (x,x ′) is selected randomly by \( \mathcal {A}\). In this case, the adversary \(\mathcal {A}\) is also allowed to be probabilistic and the probability in the advantage is computed over the random choices made by the adversary \(\mathcal {A}\) with the execution time t 1. The hash function h(⋅) is then called collision-resistant, if \(Adv_{\mathcal {A}}^{HASH} (t_{1}) \le \epsilon _{1}\), for any sufficiently small 𝜖 1 > 0.
2.2 Fuzzy extractor
We briefly describe the extraction process of key data from the given biometric of a user using a fuzzy extractor technique. The output of a conventional hash function h(⋅) is sensitive and it may also return completely different outputs even if there is a little variation in inputs. Note that the biometric information is prone to various noises during data acquisition, and the reproduction of actual biometric is hard in common practice. To avoid such problem, a fuzzy extractor method [5, 15, 19] is preferred, which can extract a uniformly random string and a public information from the biometric template with a given error tolerance t. In the reproduction process, the fuzzy extractor recovers the original biometric key data for a noisy biometric using public information and t. Let \(\mathcal {M} = \{0, 1\}^{v}\) denote a finite v-dimensional metric space of biometric data points, \(d: \mathcal {M} \times \mathcal {M} \rightarrow \mathbb {Z}^{+}\) a distance function, which can be used to calculate the distance between two points based on the metric chosen, l the number of bits of the output string, and t the error tolerance, where \(\mathbb {Z}^{+}\) represents the set of all positive integers.
Definition 2
The fuzzy extractor is a tuple \((\mathcal {M}, l, t)\), which is composed of the following two algorithms, called G e n and R e p:
-
Gen: It is a probabilistic algorithm, which takes a biometric information \(B_{i} \in \mathcal {M}\) as input, and then outputs a secret key data σ i ∈ {0, 1}l and a public reproduction parameter τ i , where G e n(B i ) = {σ i ,τ i }.
-
Rep: This is a deterministic algorithm, which takes a noisy biometric information \(B_{i}^{\prime } \in \mathcal {M}\) and a public parameter τ i and t related to B i , and then it reproduces (recovers) the biometric key data σ i . In other words, we have \(Rep(B_{i}^{\prime }, \tau _{i}) = \sigma _{i}\) provided that the condition \(d(B_{i},B_{i}^{\prime }) \le t\) is met.
One can refer to [5, 15] for more detailed description of the fuzzy extractor and the extraction procedure.
3 Review of Jiang et al.’s scheme
In this section, we review in brief the recently proposed Jiang et al.’s scheme [21]. We use the notations given in Table 1 for describing and analyzing Jiang et al.’s scheme.
3.1 Registration phase
In this phase, a legal user U i registers or re-registers with the GWN. In order to register to the GWN, the user U i need to execute the following steps:
- Step 1.:
-
U i first selects a unique identity I D i and a chosen password P W i . After that U i generates a random value r and computes R P W i = h(r||P W i ) and sends the registration request message R = 〈I D i ,R P W i 〉 to the GWN via a secure channel.
- Step 2.:
-
After receiving the registration request message R = 〈I D i ,R P W i 〉 from the user U i , the GWN verifies I D i and rejects this request if I D i is invalid. Otherwise, the GWN computes the temporal credential T C i = h (K G W N−U ||I D i ||T E i ) and P T C i = T C i ⊕R P W i for the user U i . The GWN then initializes the temporary identity T I D i of the user U i and stores the tuple (T I D i ,I D i ,T E i ) in its verification table. The GWN issues a smart card containing to the information {h(⋅), T I D i ,T E i ,P T C i } to U i and sends it via a secure channel.
- Step 3.:
-
After receiving the smart card, U i stores the random number r in the smart card.
The registration phase for all the deployed sensor nodes is as follows:
- Step 1.:
-
A sensor node S N j submits its identifier \(ID_{SN_{j}}\) to the GWN through a secure channel.
- Step 2.:
-
Upon receiving the message, the GWN computes the temporal credential for S N j as T C j = h(K G W N−S \(|| ID_{SN_{j}})\), where K G W N−S is the GWN’s private key only known to the GWN. The GWN then sends the message 〈T C j 〉 to S N j .
- Step 3.:
-
When the sensor node S N j receives the message in Step 2, S N j stores T C j as its temporal credential.
3.2 Login and authentication phase
In this phase, in order to login to the GWN and authenticate by the sensor nodes in WSN, the following steps are executed by the user U i , the GWN and the login-sensor node S N j :
- Step 1.:
-
U i first inserts his/her smart card to a terminal and then inputs his/her identity I D i and password P W i . The smart card then generates a current timestamp T S 4 and also a random key K i . After that the smart card computes T C i = P T C i ⊕h(r||P W i ), P K S i = K i ⊕h(T C i ||T S 4), C i = h(I D i ||K i ||T C i ||T S 4). U i then sends the login request message 〈T I D i , C i , P K S i , T S 4〉 to the GWN via a public channel.
- Step 2.:
-
After receiving the message in Step 1, the GWN checks the condition \(|T_{GWN}^{*} - TS_{4}| < {\Delta } T\), where \(T_{GWN}^{*}\) is the current system timestamp of the GWN and ΔT the maximum transmission delay. If this condition does not hold, the GWN immediately terminates this phase and sends the reject message REJ back to the user U i . Otherwise, the GWN fetches the identity I D i corresponding to T I D i in the verification table, and computes T C i = h(K G W N−U ||I D i ||T E i ) and \(C_{i}^{*} =\) h(I D i ||K i ||T C i ||T S 4). If \(C_{i}^{*} \neq C_{i}\), the GWN sends reject message REJ back to the user U i and terminates this phase. Otherwise, the GWN authenticates the user U i and further, computes K i = P K S i ⊕h(T C i ||T S 4). In addition, the GWN computes the accessed sensor node S N j ’s temporal credential \(TC_{j} = h(K_{GWN-S}|| ID_{SN_{j}})\), C G W N = h(T I D i ||T C j ||T S 5) and P K S G W N = K i ⊕h(T C j ||T S 5), where T S 5 is the current timestamp of the GWN. The GWN then sends the message 〈T S 5, T I D i , C G W N , P K S G W N 〉 to the sensor node S N j .
- Step 3.:
-
After receiving the message in Step 2, the sensor node S N j checks the condition \(|T_{j}^{*} - TS_{5}| < {\Delta } T\), where \(T_{j}^{*}\) is the current system timestamp of S N j . If this condition fails, S N j terminates the current session. Otherwise, S N j computes \(C_{GWN}^{*} = h(TID_{i} || TC_{j} || TS_{5})\). If \(C_{GWN}^{*} \neq C_{GWN}\), the sensor node S N j rejects this message. Otherwise, S N j confirms that the sender of the received message sent in Step 2 is an authorized GWN. After that S N j computes K i = P K S G W N ⊕h(T C j ||T S 5). S N j generates the current timestamp T S 6 and also a random key K j , and computes C j = h(K j ||\(TID_{i} || ID_{SN_{j}} || TS_{6})\), P K S j = K j ⊕h(K i ||T S 6). S N j finally sends the message \(\langle ID_{SN_{j}}, TS_{6}, C_{j}, PKS_{j} \rangle \) to the GWN.
- Step 4.:
-
If the timeliness of T S 6 in the received message \(\langle ID_{SN_{j}}, TS_{6}, C_{j}, PKS_{j} \rangle \) is verified successfully, the GWN computes \(C_{j}^{*} = h(K_{j} || ID_{i} || ID_{SN_{j}} || TS_{6})\) and checks if \(C_{j}^{*} = C_{j}\). If it is valid, S N j is considered as a legitimate sensor node. The GWN then proceeds to generate a new temporary identity \(TID_{i}^{\prime }\) and computes \(D_{GWN} = TID_{i}^{\prime } \oplus h(K_{i} || TS_{7})\), where T S 7 is the current timestamp of the GWN. The GWN replaces T I D i with \(TID_{i}^{\prime }\) in its verification table, and computes \(E_{GWN} = h(ID_{i} || ID_{SN_{j}} || TC_{i} || D_{GWN} || K_{j} || TS_{7})\). The GWN finally sends the message \(\langle ID_{SN_{j}}, TS_{7}, PKS_{j},\) D G W N , E G W N 〉 to the user U i .
- Step 5.:
-
Once the timeliness of T S 7 for the received message \(\langle ID_{SN_{j}}, TS_{7}, PKS_{j}, D_{GWN}, E_{GWN} \rangle \) is verified by the user U i , U i proceeds to compute \(TID_{i}^{\prime } = D_{GWN}\) ⊕h(K i ||T S 7), K j = P K S j ⊕h(K i ||T S 6) and \(E_{GWN}^{*} = h(ID_{i} || ID_{SN_{j}} || Tc_{i} || D_{GWN} || K_{j} || TS_{7})\). If the condition \(E_{GWN}^{*} = E_{GWN}\), the user U i confirms that both S N j and the GWN are legitimate. After that U i replaces T I D i with \(TID_{i}^{\prime }\) in the memory of the smart card, and computes the shared session key with the sensor node S N j as S K i j = h(K i ⊕K j ). The sensor node S N j also computes the same shared session key with the user U i as S K i j = h(K i ⊕K j ). Finally, both U i and S N j can use S K i j for their future secure communications.
3.3 Password update phase
In this phase, if a legal user U i wants to change his/her current password, the U i needs to insert his/her smart card to a terminal and then input his/her identity I D i , old password P W i and a new password \(PW_{i}^{\prime }\). After that the smart card computes \(PTC_{i}^{\prime } = TC_{i} \oplus RPW_{i} \oplus h(r || PW_{i}^{\prime })\) and replaces P T C i with \(PTC_{i}^{\prime }\).
4 Drawbacks of Jiang et al.’s scheme
In this section, we analyze the security of Jiang et al.’s scheme. We find that their scheme has the following drawbacks.
4.1 Privileged insider attack
During the registration phase of Jiang et al.’s scheme, a legal user U i submits the registration request message R = 〈I D i , R P W i 〉 to the GWN via a secure channel, where r is a random number generated by the user U i and R P W i = h(r||P W i ). After issuing the smart card containing the information {h(⋅), T I D i , T E i , P T C i } by the GWN, the user U i stores the secret number r in his/her smart card. In this attack, we assume that an insider of the GWN attains the lost/stolen smart card of the legal user U i . After that the insider being an attacker can mount the offline password guessing attack using dictionary attack in order to derive a low-entropy password P W i of the user U i using the following steps:
- Step 1.:
-
Extract the information stored in the lost/stolen smart card of the user U i using the power analysis attack [24, 27] (described in our threat model in Section 1.2). Thus, the insider knows r. Furthermore, note that the insider has R P W i = h(r||P W i ).
- Step 2.:
-
Pick a guessed password \(PW_{i}^{*}\) and compute \(RPW_{i}^{*} = h(r || PW_{i}^{*})\).
- Step 3.:
-
Check if \(RPW_{i}^{*} = RPW_{i}\). If there is a match, the insider is successful in finding the correct password P W i of the user U i and terminates the procedure. Otherwise, the insider discards this guessed password and guesses a new password, and goes to Step 2.
It is thus clear that an insider of the GWN is successful in deriving the correct password P W i of a legal user U i in a relatively small dictionary. Hence, Jiang et al.’s scheme fails to protect the privileged insider attack.
4.2 Inefficient registration phase
In Jiang et al.’s scheme, the registration phase for all the deployed sensor nodes is performed online after the sensor nodes are deployed in a target field. Usually, due to large number of sensor nodes deployment in WSN, it is not preferable to have a procedure where each sensor node can register online with the WSN. Rather, in most of the WSN applications, this is performed in offline by the GWN. Note that in Jiang et al.’s scheme, a deployed sensor node S N j sends its identity \(ID_{SN_{j}}\) to the GWN through a secure channel. This means that each sensor node S N j needs to establish a secret key with the GWN. After receiving the message the GWN computes the temporal credential for S N j as T C j = h(K G W N−S \(|| ID_{SN_{j}})\) and sends T C j to S N j . S N j then stores T C j for authentication purpose later. It is then clear that this procedure involves a lot of communication and computational overheads due to large number of sensor nodes involved during this process. Thus, Jiang et al.’s is inefficient for this registration phase for all sensor nodes in WSN.
4.3 Fails to provide proper authentication in login and authentication phase
This analysis is similar to that presented in [8]. In practice, a user U i is expected to keep different passwords for different applications for security reasons. In this case, we assume that U i enters his/her password P W i incorrectly by mistake during the login and authentication phase of Jiang et al.’s scheme. Let the entered wrong password be \(PW_{i}^{\prime }\), where \(PW_{i}^{\prime } \neq PW_{i}\). Then, in Step 1 of the login and authentication phase, the smart card of the user U i computes
After that the smart card of U i computes P K S i = K i ⊕h(T C i ||T S 4), C i = h(I D i ||K i ||T C i ||T S 4), and sends the login request message 〈T I D i , C i , P K S i , T S 4〉 to the GWN. After receiving this login request message, the GWN checks the timeliness of T S 4, and if it is valid, the GWN fetches I D i corresponding to T I D i in its verification table. Note that the GWN computes T C i = h(K G W N−U ||I D i ||T E i ) and \(C_{i}^{*} =\) h(I D i ||K i ||T C i ||T S 4). When the GWN verifies the condition \(C_{i}^{*} = C_{i}\), it will fail because of incorrect password \(PW_{i}^{\prime }\) (≠P W i ) entered by the user U i . However, in this case, U i is totally unaware of the fact that he/she has entered password incorrectly. On the other hand, U i may think the GWN as a cheater. Thus, Jiang et al.’s scheme fails to provide strong authentication during the login and authentication phase, because their scheme does not provide any mechanism for password verification by the smart card before the login request message is sent to the GWN.
4.4 Fails to update new password in password update phase
Similar to the analysis in Section 4.3, we also assume that a legal user U i wants to change his/her password, and enters his/her old password \(PW_{i}^{*}\) incorrectly by mistake, where \(PW_{i} \neq PW_{i}^{*}\). After that U i enters his/her new changed password \(PW_{i}^{\prime }\). Note that during the password update phase of Jiang et al.’s scheme, the smart card of U i never verifies whether the entered old password is correct. Due this problem, when the smart card computes \(PTC_{i}^{\prime } = TC_{i} \oplus RPW_{i} \oplus h(r || PW_{i}^{\prime })\), where \(RPW_{i} = h(r || PW_{i}^{*}) \neq h(r\) ||P W i ), then \(PTC_{i}^{\prime } \neq TC_{i} \oplus h(r || PW_{i}^{\prime })\). It is also noticed that there is a design flaw in computing \(PTC_{i}^{\prime }\) and it must be \(PTC_{i}^{\prime } = PTC_{i} \oplus RPW_{i} \oplus h(r || PW_{i}^{\prime })\). However, when the smart card replaces \(PTC_{i}^{\prime }\) with P T C i in its memory, this results wrong update of the new password \(PW_{i}^{\prime }\) in the smart card. As pointed out in [10], when the same user U i will login later in the system providing his/her new changed password \(PW_{i}^{*}\), we see that the login request of the same user U i will be always rejected by the GWN even if U i enters correctly \(PW_{i}^{*}\) in that time. Hence, due to such serious flaw in the design of Jiang et al.’s scheme, this effect will continue in all subsequent password change phases. As a result, this irrecoverable error enforces the user U i to issue another new smart card by the GWN and register with the GWN again.
4.5 Lack of supporting dynamic node addition
A most desirable property of user authentication schemes designed for WSNs is the dynamic node addition after initial deployment of sensor nodes in a target field [12]. Wireless sensor networks often operate in an unattended environment. An adversary may physically capture some sensors to compromise their stored sensitive secret data and codes from their memory as they are not generally equipped with tamper-resistant hardware. Moreover, some sensor nodes may expire due to energy problem, because sensors are equipped with battery. Thus, we often require to deploy some new nodes in the network. It is noted that Jiang et al.’s scheme does not support this important feature.
4.6 Lack of formal security verification
Jiang et al.’s scheme contains only informal security analysis and it lacks a rigorous formal security proof for its security. Further, it lacks the formal security verification using some widely-accepted AVISPA tool [2].
5 The proposed scheme
In this section, we describe an improvement of Jiang et al.’s scheme in order to withstand the drawbacks found in their scheme. Our proposed scheme is a three-factor authentication scheme, which uses a user’s personal biometrics as compared to Jiang et al.’s two-factor authentication scheme. The three-factor used in our scheme are (i) the smart card of a user, (ii) user’s password, and (iii) user’s personal biometrics. Traditional remote user authentication scheme based on the passwords may be vulnerable to the offline password guessing attacks, when a user picks up the chosen password from a small dictionary for the easy-to-remember purpose. In recent years, the research demonstrates that biometric-based remote user authentication schemes using passwords and smart cards are more secure and reliable, and hence this active research area has drawn a considerable research attention [8, 10, 23, 25, 26, 42]. Li and Hwang listed the following advantages of using biometric keys (e.g., fingerprints, faces, palm-prints, irises, and hand geometry) [25]:
-
Biometric keys can not be lost or forgotten.
-
Biometric keys are very difficult to copy or share.
-
Biometric keys are extremely hard to forge or distribute.
-
Biometric keys can not be guessed easily.
-
Someone’s biometrics is not easy to break than others.
In this paper, we use the user’s personal biometric in our scheme to strengthen the security and other features which are not provided by Jiang et al.’s scheme. Our scheme keeps the original merits of Jiang et al.’s scheme. The various phases of our proposed scheme are described in the following subsections.
5.1 Pre-deployment of sensor nodes phase
This phase is executed by the GWN in offline prior to deployment of the sensor nodes in the target field. It consists of the following steps:
- Step PD1.:
-
For each deployed sensor node S N j , the GWN selects a unique identifier \(ID_{SN_{j}}\).
- Step PD2.:
-
The GWN generates randomly a large 1024-bit number K G W N−S , which is considered as the GWN’s private key only known to the GWN. After that for each deployed sensor node S N j , the GWN computes T C j = h(K G W N−S \(|| ID_{SN_{j}})\), which is the temporal credential for S N j .
- Step PD3.:
-
Finally, each deployed sensor node S N j is pre-loaded with the information T C j as its temporal credential prior to its deployment in the target field.
Thus, it is clear that the pre-deployment of sensor nodes in our scheme is performed in offline. However, in Jiang et al.’s scheme this task is performed after deployment of sensor nodes. As a result, our scheme is more efficient as compared to Jiang et al.’s scheme, and our scheme thus helps to avoid a lot of communication and computational overheads by the sensor nodes after their deployment in the target field.
5.2 Registration phase
To register to the GWN in WSNs by a legal user U i , the following steps need to be executed:
- Step R1.:
-
U i first selects a unique identity I D i and chooses a password P W i .
- Step R2.:
-
U i generates randomly a large 1024-bit secret number K. U i computes the masked password R P W i = h(I D i ||K ||P W i ) and sends the registration request message 〈I D i , R P W i 〉 to the GWN via a secure channel.
- Step R3.:
-
After receiving the message in Step R2, the GWN continues to generate randomly a large 1024-bit private key K G W N−U , and computes the temporal credential for the user U i as T C i = h(K G W N−U ||I D i ||T E i ) and P T C i = T C i ⊕R P W i , where T E i is the expiration time of U i ’s temporal credential T C i . After that the GWN further randomly generates a large 1024-bit secret information X s and computes r i = h(I D i ||X s ). The GWN selects a temporary identity T I D i for the user U i and initializes it and then stores the tuple (T I D i , I D i , T E i ) in the verification table. Finally, the GWN issues a smart card S C i for the user U i , which contains the information {h(⋅),T I D i , T E i , P T C i , r i } and sends it to U i via a secure channel.
- Step R4.:
-
U i imprints the biometric information B i at the terminal of a specific device. U i applies the fuzzy extractor function G e n(⋅) to generate secret key data σ i and a public reproduction parameter τ i as G e n(B i )=(σ i , τ i ) as in [19]. U i then computes
$$\begin{array}{@{}rcl@{}} e_{i} & = & h(ID_{i} || \sigma_{i}) \oplus K, \\ f_{i} & = & h(ID_{i} || RPW_{i} || \sigma_{i}), \\ r_{i}^{*} & = & r_{i} \oplus h(ID_{i} || K) \\ & = & h(ID_{i} || X_{s}) \oplus h(ID_{i} || K). \end{array} $$U i stores e i , f i , the fuzzy extractor functions G e n(⋅) and R e p(⋅), t and τ i in the smart card. Further, U i replaces r i with \(r_{i}^{*}\) in the smart card. Finally, the smart card S C i of U i contains the information {h(⋅),T I D i , T E i , P T C i ,\(r_{i}^{*}, f_{i}, e_{i}, Gen(\cdot ), Rep(\cdot ), t, \tau _{i} \}\). Note that in our registration phase, the user U i ’s secret number K is not stored in the smart card S C i .
The registration phase of our scheme is summarized in Table 2.
5.3 Login phase
In order to login to the GWN, the user U i needs to execute the following steps:
- Step L1.:
-
U i first inserts his/her smart card S C i into a card reader and then enters his/her identity I D i , password P W i , and imprints the biometric information B i at the sensor of the card reader. As described in [36] if the user U i plans to use a mobile device to login the GWN, U i can use the scan software of the mobile device to obtain B i , and input {I D i , P W i , B i } into the login interface of the system.
- Step L2.:
-
S C i computes \(\sigma _{i}^{*} = Rep(B_{i}, \tau _{i})\) using B i , and the parameters t and τ i stored in its memory. S C i further computes \(K^{*} = e_{i} \oplus h(ID_{i} || \sigma _{i}^{*})\), \(RPW_{i}^{*} = h(ID_{i} || K^{*}\) ||P W i ) and \(f_{i}^{*} = h(ID_{i} || RPW_{i}^{*} || \sigma _{i}^{*})\), and then checks if \(f_{i}^{*} = f_{i}\) holds or not. If it does not hold, this ensures that U i enters his/her password incorrectly and does not pass both biometric and password verifications. Otherwise, S C i proceeds to the next step.
- Step L3.:
-
S C i generates a current timestamp T S 1 and randomly chooses a temporary key K i . S C i then computes \(TC_{i} = PTC_{i} \oplus RPW_{i}^{*}\), \(M_{1} = r_{i}^{*} \oplus h(ID_{i} || K^{*})\) = h(I D i ||X s ), P K S i = K i ⊕h(T C i ||M 1||T S 1) and C i = h(I D i ||K i ||T C i ||M 1||T I D i ||T S 1). Finally, S C i sends the login request message 〈T I D i , C i , P K S i , T S 1〉 to the GWN via a public channel.
The login phase of our scheme is summarized in Table 3.
5.4 Authentication and key agreement phase
After receiving the login request message 〈T I D i , C i , P K S i , T S 1〉 by the GWN from U i , the following steps are executed for mutual authentication and key establishment:
- Step AK1.:
-
The GWN checks the timeliness of T S 1 in the received message by the condition \(|T_{GWN}^{*} - TS_{1}| < {\Delta } T\), where \(T_{GWN}^{*}\) is the current timestamp of the GWN. If it is not valid, the GWN terminates this current session and sends the reject message REJ back to U i . Otherwise, the GWN obtains the real identity I D i of U i corresponding to T I D i in its verification table. The GWN then computes M 2 = h(I D i ||X s ) using its own secret information X s and retrieved I D i , T C i = h(K G W N−U || I D i ||T E i ), K i = P K S i ⊕h(T C i ||M 2||T S 1), \(C_{i}^{*} = h(ID_{i} || K_{i} || TC_{i} || M_{2} || TID_{i} || TS_{1})\), and then checks the condition \(C_{i}^{*} = C_{i}\). If this condition fails, the GWN terminates this session immediately and sends REJ message back to U i . Otherwise, the GWN confirms that U i is a legitimate user, and computes the accessed sensor node S N j ’s temporal credential \(TC_{j} = h(K_{GWN-S} || ID_{SN_{j}})\), C G W N = h(T I D i ||T C j ||T S 2), and P K S G W N = (K i ⊕M 2)⊕h(T C j ||T S 2), where T S 2 is the current timestamp of the GWN. Finally, the GWN sends the authentication request message 〈T S 2, T I D i , C G W N , P K S G W N 〉 to S N j via a public channel.
- Step AK2.:
-
When the sensor node S N j receives the message 〈T S 2, T I D i , C G W N , P K S G W N 〉 from the GWN, S N j first checks the validity of T S 2 by the condition \(|T_{j}^{*} - TS_{2}|\) <ΔT, where \(T_{j}^{*}\) is the current time of S N j . If it is not valid, S N j terminates this phase immediately. Otherwise, S N j continues to compute \(C_{GWN}^{*} = \) h(T I D i ||T C j ||T S 2) using its stored T C j and received T I D i and T S 2. If the validation of \(C_{GWN}^{*} = C_{GWN}\) does not hold, S N j rejects this message. On the other hand, S N j confirms that the GWN is legitimate. S N j further continues to compute M 3 = P K S G W N ⊕h(T C j ||T S 2) = K i ⊕M 2 = K i ⊕h(I D i ||X s ). After that S N j generates a random temporary key K j and computes \(C_{j} = h(K_{j} || TID_{i} || ID_{SN_{j}} || TS_{3})\) and P K S j = K j ⊕h(M 3 ||T S 3), where T S 3 is the current timestamp of S N j . S N j then sends the the authentication reply message \(\langle ID_{SN_{j}}, TS_{3}, C_{j}, PKS_{j} \rangle \) to the GWN via a public channel.
- Step AK3.:
-
After receiving the message in Step AK2, the GWN computes K j = P K S j ⊕h((K i ⊕M 2)||T S 3) using the received T S 3 and its previously computed K i and M 2 in step AK1. The GWN then computes \(C_{j}^{*} = h(K_{j} || TID_{i} || ID_{SN_{j}} || TS_{3})\) and checks if \(C_{j}^{*} = C_{j}\). If it does not hold, the GWN rejects this message. Otherwise, the GWN confirms that S N j is a legitimate sensor node in WSN. The GWN then generates a new temporary identity \(TID_{i}^{new}\) and computes \(D_{GWN} = TID_{i}^{new}\) ⊕h((K i ⊕M 2)||T S 3||T S 4), where T S 4 is the current time of the GWN. The GWN replaces T I D i with \(TID_{i}^{new}\) in its verification table. The GWN also computes E G W N \(= h(ID_{i} || ID_{SN_{j}} || TC_{i} || D_{GWN} || K_{j} || TS_{3} || TS_{4})\). The GWN then sends the acknowledgment message \(\langle ID_{SN_{j}},\) T S 3, T S 4, P K S j , D G W N , E G W N 〉 to the user U i via a public channel.
- Step AK4.:
-
After receiving the message in Step AK3, the smart card S C i of the user U i checks the timeliness of T S 4. If it is valid, S C i computes \(TID_{i}^{new} = D_{GWN} \oplus h((K_{i} \oplus M_{1}) || TS_{3} || TS_{4})\), K j = P K S j ⊕h((K i ⊕M 1)||T S 3), and \(E_{GWN}^{*} = h(ID_{i} || ID_{SN_{j}} || TC_{i} || D_{GWN}\) ||K j ||T S 3||T S 4). If the condition \(E_{GWN}^{*} = E_{GWN}\) passes, S C i (that is, the user U i ) confirms that both S N j and GWN are legitimate nodes in WSN. After mutual authentication between U i and S N j , S C i of U i computes the shared session key S K i j = h((K i ⊕M 1)⊕K j ) with the accessed sensor node S N j . Similarly, S N j computes the session key shared with U i as \(SK_{ij}^{*} =\) h(M 3⊕K j ), which is equal to h((K i ⊕K 2)⊕K j ) = h((K i ⊕M 1)⊕K j = S K i j , since M 1 = M 2. Thus, it is clear that both U i and S N j have the same session key, that is, \(SK_{ij} = SK_{ij}^{*}\). Finally, U i and S N j can use S K i j for their future secure communications. Note that as compared to Jiang et al.’s scheme, we have used the secret credential X s of the GWN in the computation of S K i j and \(SK_{ij}^{*}\), because M 1 = M 2 = h(I D i ||X s ).
The authentication and key agreement phase of our scheme is summarized in Table 4.
5.5 Password and biometric update phase
For security reasons, it is desirable that a legal user U i should be allowed to change/update his/her password as well as personal biometrics. This procedure should be done by the smart card of the user U i without involving the GWN, which needs to be performed locally so that the GWN must not be aware that the user U i has changed his/her password and biometrics.
Suppose U i wants to update his/her old password \(PW_{i}^{old}\) and old biometrics \(B_{i}^{old}\). The following steps are then executed:
- Step PBC1.:
-
U i first inserts his/her smart card S C i into the card reader of a terminal. U i then inputs I D i , \(PW_{i}^{old}\) and also imprints \(B_{i}^{old}\) at the terminal.
- Step PBC2.:
-
S C i then computes \(\sigma _{i}^{old} = Rep(B_{i}^{old}, \tau _{i})\), \(K^{*} = e_{i} \oplus h(ID_{i} || \sigma _{i}^{old})\), \(RPW_{i}^{old} = h(ID_{i} || K^{*} ||PW_{i}^{old})\), and \(f_{i}^{old} = h(ID_{i} || RPW_{i}^{old} || \sigma _{i}^{old})\). S C i then checks if \(f_{i}^{old} = f_{i}\). If it holds, it ensures that U i has entered his/her correct old password \(PW_{i}^{old}\) and old biometrics \(B_{i}^{old}\). Otherwise, this phase is terminated immediately.
- Step PBC3.:
-
S C i then asks U i to enter his/her new password \(PW_{i}^{new}\) and imprint new biometrics \(B_{i}^{new}\) at the terminal. S C i computes \(x = PTC_{i} \oplus RPW_{i}^{old}= TC_{i} \oplus RPW_{i} \oplus RPW_{i}^{old}\) = T C i , \(RPW_{i}^{new} = h(ID_{i} || K^{*}|| PW_{i}^{new})\), \(PTC_{i}^{new} = x \oplus RPW_{i}^{new}\), which is equal to \(TC_{i} \oplus RPW_{i}^{new}\). S C i further computes \(Gen(B_{i}^{new})= (\sigma _{i}^{new}, \tau _{i}^{new})\), \(e_{i}^{new} = h(ID_{i} || \sigma _{i}^{new}) \oplus K^{*}\), \(f_{i}^{new} = h(ID_{i} || RPW_{i}^{new} || \sigma _{i}^{new})\).
- Step PBC4.:
-
Finally, S C i replaces P T C i , f i , e i , and τ i with \(PTC_{i}^{new}, f_{i}^{new}, e_{i}^{new},\) and \(\tau _{i}^{new}\), respectively.
Thus, it is clear from our password and biometric update phase that the smart card S C i updates the new password and biometrics only when the user passes both old password and biometric verifications. Further, this phase is also executed locally without the knowledge of the GWN.
5.6 Dynamic node addition phase
Suppose a new sensor node \(SN_{j}^{new}\) is to be deployed in the existing sensor network. For this purpose, the following steps are executed by the GWN in offline prior to its deployment in the target field:
- Step DA1.:
-
The GWN first assigns a unique random identity \(ID_{SN_{j}}^{new}\) for \(SN_{j}^{new}\).
- Step DA2.:
-
The GWN then computes the temporal credential for \(SN_{j}^{new}\) as \(TC_{i}^{new} = h(K_{GWN-S} || ID_{SN_{j}}^{new})\).
- Step DA3.:
-
Finally, the GWN loads \(TC_{i}^{new}\) in the memory of \(SN_{j}^{new}\) prior to its deployment.
After deployment of the new sensor node \(SN_{j}^{new}\) in the target field, the GWN needs to inform the user U i so that he/she can access the real-time data from it later.
6 Security analysis of the proposed scheme
In this section, we analyze the security of our proposed scheme. Through both the rigorous informal and formal security analysis, we show that our scheme has the ability to tolerate various known attacks, which are outlined in the following subsections.
6.1 Informal security analysis
We show that our scheme resists the following attacks.
6.1.1 Privileged insider attack
In our proposed scheme, during the registration phase the user U i sends his/her identity I D i and pseudo-password R P W i = h(I D i ||K||P W i ) to the GWN via a secure channel. As in Section 4.1, we assume that the insider of the GWN has the lost/stolen smart card S C i of U i . Then, using the power analysis attack [24, 27], the insider can extract the information \(TID_{i}, TE_{i}, PTC_{i}, r_{i}^{*}, f_{i}, e_{i}, t, \tau _{i}\) from S C i , where P T C i = T C i ⊕R P W i , e i = h(I D i ||σ i )⊕K, \(r_{i}^{*} = h(ID_{i} || X_{s}) \oplus h(ID_{i} || K)\), and f i = h(I D i ||R P W i ||σ i ). The insider of the GWN can compute u= P T C i ⊕T C i and \(v = r_{i}^{*} \oplus h(ID_{i} || X_{s})\) = h(I D i || K). Since K is an 1024-bit large secret number only known to U i , due to collision-resistant property of a one-way hash function h(⋅) it is a computationally infeasible task for the insider attacker to derive K from v, and as a result, to correctly guess P W i without knowing K though the attacker knows I D i and R P W i . Hence, the attacker has no way to derive P W i . Thus, our scheme protects the privileged-insider attack.
6.1.2 Online password and biometric key guessing attack
Suppose an adversary intercepts all the messages 〈T I D i , C i , P K S i , T S 1〉, 〈T S 2, T I D i , C G W N , P K S G W N 〉, \(\langle ID_{SN_{j}},\) T S 3, C j , P K S j 〉, and \(\langle ID_{SN_{j}},\) T S 3, T S 4, P K S j , D G W N , E G W N 〉 during the login phase and the authentication and key agreement phase of our scheme. It is clear that none of the messages involves the password and biometric key data of the user U i . The adversary then can not derive P W i and σ i from these messages. Hence, our scheme protects online password and biometric key guessing attack.
6.1.3 Offline password and biometric key guessing attack
Assume that an adversary has the stolen smart card S C i of a legal user U i . According to our threat model in Section 1.2, the adversary can extract the sensitive information \(TID_{i}, TE_{i}, PTC_{i}, r_{i}^{*}, f_{i}, e_{i}, t, \tau _{i}\) from S C i . Without knowing the biometric B i of the user U i , the adversary cannot derive σ i using τ i . Furthermore, the adversary cannot derive K from e i without knowing both σ i and I D i . Hence, it is a computationally infeasible task for the adversary to guess correctly P W i from f i without knowing K, I D i and σ i due to the collision-resistant property of the one-way hash function h(⋅). In this way, our scheme is resilient against deriving the password and biometric key data σ i of U i . Thus, the offline password and biometric key guessing attack is eliminated from our scheme.
6.1.4 Replay attack
Suppose an adversary intercepts the login request message 〈T I D i , C i , P K S i , T S 1〉 during the login phase, and replies the same message to the GWN after some time. When the GWN receives this message, it checks the timeliness of T S 1 in the received message by the condition \(|T_{GWN}^{*} - TS_{1}| < {\Delta } T\), where \(T_{GWN}^{*}\) is the current timestamp of the GWN. If it is not valid, the GWN ensures that the received message is not a fresh message and it will immediately discards this message. Due to the timestamps used in the other messages between U i , GWN and S N j , those will be also detected as duplicate messages, if the adversary sends those same messages later. The replay attack is then prevented in our design.
6.1.5 Man-in-the-middle attack
Suppose an adversary intercepts the login request message 〈T I D i , C i , P K S i , T S 1〉 during the login phase, and tries to modify this message in order to convince the GWN that the modified message is a valid login request message. Note that the adversary has T I D i and T S 1 from the login request message. However, the adversary does not know I D i , K G W N−U , T E i and X s . In order to compute M 1 = h(I D i ||X s ) and T C i = h(K G W N−U ||I D i ||T E i ), the adversary needs to know I D i , X s , K G W N−U and T E i . Though the adversary can generates a random temporary key \(K_{i}^{\prime }\) and use a different timestamp \(TS_{1}^{\prime }\), he/she is still unable to compute \(PKS_{i}^{\prime } = K_{i}^{\prime } \oplus h(TC_{i} || M_{1} || TS_{1}^{\prime })\) and \(C_{i}^{\prime } = h(ID_{i} || K_{i}^{\prime }|| TC_{i} || M_{1} || TID_{i} || TS_{1}^{\prime })\) because these computations involve M 1 and T C i , the temporal credential of the user U i . As a result, the adversary does not have any ability to change the login request message 〈T I D i , C i , P K S i , T S 1〉 to another modified message \(\langle TID_{i}, C_{i}^{\prime },PKS_{i}^{\prime }, TS_{1}^{\prime } \rangle \). Similarly, the adversary cannot be also successful to modify other messages during the authentication and key agreement phase. Hence, our scheme tolerates the man-in-the-middle attack against the adversary.
6.1.6 Stolen-verifier attack
In this attack, an attacker tries to steal or modify the verifiers (e.g., plaintext passwords, hashed passwords, biometric key data, hashed biometric key data) stored in the GWN. Since our scheme does not maintain any authentication information derived from U i ’s password P W i , the attacker has no way to steal or modify any authentication information from the GWN. Thus, our scheme is resilient against stolen-verifier attack.
6.1.7 Forgery attacks
We consider the following three cases:
U i forgery attack: Suppose an adversary eavesdrop or intercept the login request message of the previous sessions. Then the adversary can forge a forged message and send it to the GWN. After receiving the forged message, the GWN can extract K i with the secret T C i = h(K G W N−U ||I D i ||T E i ), and then compute M 2 = h(I D i ||X s ) and \(C_{i}^{*} = h(ID_{i} || K_{i}\) ||T C i ||M 1||T I D i ||T S 1). The GWN can verify the legitimacy of the user U i by verifying the condition \(C_{i}^{*} = C_{i}\). However, as stated in Section 6.1.5, the adversary will have any ability to forge the login request message without knowing I D i , X s , K G W N−U and T E i . For this purpose, the adversary needs to compute a valid C i . Thus, the adversary cannot be passed by the GWN and hence, our scheme is secure against this attack.
GWN forgery attack: It is clear from our authentication and key agreement phase that the authentication request message 〈T S 2, T I D i , C G W N , P K S G W N 〉 is protected by the collision-resistant one-way hash function h(⋅). Without knowing \(TC_{j} = h(K_{GWN-S} || ID_{SN_{j}})\) the adversary cannot compute C G W N and P K S G W N . Furthermore, without knowing T C i = h(K G W N−U ||I D i ||T E i ) the adversary cannot compute E G W N . The adversary does not have any ability forge the messages 〈T S 2, T I D i , C G W N , P K S G W N 〉 and \(\langle ID_{SN_{j}},\) T S 3, T S 4, P K S j , D G W N , E G W N 〉. Our scheme is then secure against GWN forgery attack.
S N j forgery attack: To forge the message \(\langle ID_{SN_{j}}, TS_{3},\) C j , P K S j 〉 in Step AK2, the adversary needs to know T C j \(= h(K_{GWN-S} || ID_{SN_{j}})\) in order to compute P K S j . Thus, the adversary does not have any ability forge this message and our scheme is thus secure against S N j forgery attack.
6.1.8 Many logged-in users with the same login-id attack
Assume that two users U i and U j pick up the same password PW. Then the hash values f i = h(I D i ||R P W i ||σ i ) and f j = h(I D j ||R P W j ||σ j ) are distinct due to the properties of personal biometrics, random numbers selected by the users U i and U j , respectively, and I D i and I D j . To login to the GWN, a user U i must have a valid 〈I D i , P W i , B i 〉 and a smart card corresponding to these information. Since our scheme requires on-card computation to login to the GWN, once the smart card is removed from the system, the login session immediately terminates. As a result, our scheme prevents the many logged-in users with the same login-id attack.
6.1.9 Identity guessing attack
From our scheme, it is noted that the real identity I D i of a legal user U i is only known to that user U i and the GWN, which stores I D i in its verification table. However, I D i is never transmitted over the public channel for authentication purpose. Instead of that, the random temporary identity T I D i is used in the public communications. Thus, the adversary does not have any ability to derive I D i for verifying his/her guessing identity. As a result, our scheme is resilient against the identity guessing attack.
6.1.10 Tracing attack
In our design, as in Jiang et al.’s scheme, the temporary identity T I D i is purely generated randomly and it is also updated after each successful authentication session. Since each temporary identity for each session is distinct and random, the adversary has no way to trace a specific user during the communications. Our scheme is then resilient against the tracing attack.
6.1.11 Password and biometric change attack
In order to change the password and biometric of a legal user U i , an adversary needs to pass both biometric and password verifications. Without those, the attacker does not have any ability to update the new password and biometric in the smart card. Our scheme is thus secure against the password and biometric change attack.
6.1.12 User anonymity and unlinkability
As in Jiang et al.’s scheme, in our scheme a legal user U i ’s real identity I D i is never transmitted over an insecure channel. It is difficult task for an adversary to know the real identity of U i from the protocol messages during the login phase and the authentication and key agreement phase. Further, a different temporary identity T I D i is used for each session in order to keep the privacy of U i . Since T I D i is different and random in each session, it is then unlinkable. Thus, any adversary and sensor nodes do not have any idea that who is communicating with the GWN. As a result, it is difficult for the adversary to detect whether two protocols runs involve the same user U i . Hence, our scheme prevents the leakage of user identity and protects user’s privacy.
6.1.13 Three-factor security
In the three-factor security model, the main goals of an attacker are to mount an impersonation attack where the attacker has learned at most two elements of the triple {P W i , S C i , B i }, in order to obtain the last element or to compromise the user anonymity. As in the analysis of Tan’s scheme, it is also clear that our scheme provides the three-factor security.
6.1.14 Resilience against node capture attack
As described in [12], we measure the resilience against node capture attack of a user authentication scheme in WSN by estimating the fraction of total secure communications that are compromised by a capture of c sensor nodes not including the communication in which the compromised nodes are directly involved. In other words, we want to find out the effect of c sensor nodes being compromised on the rest of the network. For example, for any non-compromised sensor nodes S N j , we need to find out the probability that the adversary can decrypt the secure communication between S N j and a legal user U i when c sensor nodes are already compromised. Let P e (c) denote the probability that the adversary compromises a fraction of total secure communications using c compromised nodes. If P e (c)=0, our scheme is called unconditionally secure against node capture attack. Assume that the adversary captures a sensor node S N j . Then the attacker will know the secret temporal credential T C j stored in its memory because the sensor nodes or cluster heads are not equipped with tamper-resistant hardware, and the session key S K i j shared between that sensor node S N j and the user U i is also revealed to that adversary. Note that each sensor node is pre-loaded with a unique key T C j prior to its deployment, because \(TC_{j} = h(K_{GWN-S} || ID_{SN_{j}})\) and each \(ID_{SN_{j}}\) is distinct. Moreover, it is computationally infeasible to derive the 1024-bit private key K G W N−S due to the collision-resistant property of the one-way hash function h(⋅). Further, each sensor node establishes a distinct secret session key with a user, which is different from all other session keys in the network. As a result, the adversary has only the ability to respond with false data to a legitimate user by capturing a sensor node from which the user wants to access data. However, other non-captured sensor nodes have the ability to communicate with 100 % secrecy with the actual real-time data to the legitimate users. The compromise of a sensor node does not lead to compromise of any other secure communication between the user and the non-compromised sensor nodes in the network. Thus, our scheme is unconditionally security against node capture attack.
6.2 Formal security analysis
In this section, we show through the formal security analysis that our scheme is secure against an adversary. We follow the formal security analysis of our scheme similar to that in [10, 11, 29]. We have used the method of contradiction proof [7] for our formal security analysis. Note that one can also prove the formal security in the standard model.
For this purpose, we assume that there exists the following oracle for the attacker (adversary), say \(\mathcal {A}\):
-
Reveal: This is an oracle, which unconditionally outputs the input string x from the corresponding hash value y= h(x).
Theorem 1
Under the assumption that a one-way hash function h(⋅) closely behaves like an oracle, our scheme is secure against an adversary for deriving the identity ID i , the password PW i , the biometric key data σ i of a legal user U i , and the secret information X s of the GWN, even if the user U i ’s smart card SC i is lost/stolen.
Proof
In this proof, we need to construct an adversary, say \(\mathcal {A}\), who will have the ability to derive the identity I D i , the password P W i , the biometric key data σ i of a legal user U i , and the secret information X s of the GWN. We assume that the adversary \(\mathcal {A}\) has the lost/stolen smart card S C i and can extract all the sensitive information from its memory using the power analysis attack [24, 27]. For this purpose, we assume that \(\mathcal {A}\) has access to the oracle R e v e a l, which gives the input string x from the corresponding hash value y= h(x). \(\mathcal {A}\) then uses the R e v e a l oracle for running an experimental algorithm, say \(EXP1_{UAS,\mathcal {A}}^{HASH}\) for our proposed user authentication scheme, say UAS, which is provided in Algorithm 1. The success probability for \(EXP1_{UAS,\mathcal {A}}^{HASH}\) can be defined as \(Succ1_{UAS,\mathcal {A}}^{HASH} = |Pr[EXP1_{UAS,\mathcal {A}}^{HASH} = 1] -1|\), where P r[E] is the probability of an event E. The advantage function for this experiment then becomes A d v1(e t 1, q R )\(= \max _{\mathcal {A}}\{Succ1_{UAS,\mathcal {A}}^{HASH}\}\), where the maximum is taken over all \(\mathcal {A}\) with execution time e t 1, and the number of queries q R made to the R e v e a l oracle. We call our scheme is secure against an adversary \(\mathcal {A}\) for deriving I D i , P W i , σ i and X s , if A d v1 (e t 1, q R )≤𝜖, for any sufficiently small 𝜖 > 0. According to this experiment given in Algorithm 1, it is clear that if \(\mathcal {A}\) has the ability to invert the one-way hash function h(⋅), then only he/she can easily derive I D i , P W i , σ i and X s , and win the game. However, it is a computationally infeasible problem to invert h(⋅), that is, \(Adv_{\mathcal {A}}^{HASH} (t_{1})\) ≤𝜖 1, for any sufficiently small 𝜖 1 > 0 (provided in Definition 1). Hence, we have A d v1 (e t 1, q R )≤𝜖, since A d v1 (e t 1, q R ) depends on the advantage \(Adv_{\mathcal {A}}^{HASH} (t_{1})\). Thus, our scheme is secure against an adversary for deriving I D i , P W i , σ i and X s , even if the user U i ’s smart card S C i is lost/stolen.

□
Theorem 2
Under the assumption that a one-way hash function h(⋅) closely behaves like an oracle, our scheme is secure against an adversary for deriving the session key SK ij shared between a legal user U i and an accessed sensor node SN j in WSN.
Proof
The proof of this theorem is similar to that in Theorem 1. We need to construct an adversary, \(\mathcal {A}\), who will have the ability to derive the session key S K i j shared between a legal user U i and an accessed sensor node S N j in WSN. We also assume that there exits an oracle R e v e a l and \(\mathcal {A}\) has access to that oracle R e v e a l, which gives the input string x from the corresponding hash value y= h(x). \(\mathcal {A}\) then uses the R e v e a l oracle for running the experimental algorithm, say \(EXP2_{UAS,\mathcal {A}}^{HASH}\) for our proposed user authentication scheme, UAS, which is provided in Algorithm 2. We define the success probability for \(EXP2_{UAS,\mathcal {A}}^{HASH}\) as \(Succ2_{UAS,\mathcal {A}}^{HASH} = |Pr[EXP2_{UAS,\mathcal {A}}^{HASH} = 1] -1|\). The advantage function for this experiment is then defined by A d v2(e t 2, q R )\(= \max _{\mathcal {A}}\{Succ2_{UAS,\mathcal {A}}^{HASH}\}\), where the maximum is taken over all \(\mathcal {A}\) with execution time e t 2, and the number of queries q R made to the R e v e a l oracle. Our scheme is said to be secure against an adversary \(\mathcal {A}\) for deriving S K i j , if A d v2 (e t 2, q R )≤𝜖, for any sufficiently small 𝜖 > 0. Consider the experiment given in Algorithm 2. It is clear that if \(\mathcal {A}\) has the ability to invert the one-way hash function h(⋅), then only he/she can easily derive S K i j , and win the game. However, it is a computationally infeasible problem to invert h(⋅), because \(Adv_{\mathcal {A}}^{HASH} (t_{1})\) ≤𝜖 1, for any sufficiently small 𝜖 1 > 0 (provided in Definition 1). Hence, we have A d v2 (e t 2, q R )≤𝜖, since A d v2 (e t 2, q R ) is also dependent on the advantage \(Adv_{\mathcal {A}}^{HASH} (t_{1})\). As a result, our scheme is secure against an adversary for deriving S K i j .

□
7 Simulation results for formal security verification using AVISPA tool
In this section, we simulate our scheme for the formal security verification using the widely-accepted AVISPA (Automated Validation of Internet Security Protocols and Applications) tool and show that our scheme is secure against the replay and man-in-the-middle attacks against an adversary.
AVISPA is considered as a push-button tool for the automated validation of Internet security-sensitive protocols and applications. It provides a modular and expressive formal language for specifying protocols and their security properties, and integrates different back-ends that implement a variety of state-of-the-art automatic analysis techniques [1], [2]. AVISPA consists of the four backends, which are the OFMC (On-the-fly Model-Checker), CL-AtSe (Constraint-Logic based Attack Searcher), SATMC (SAT-based Model-Checker), and TA4SP (Tree Automata based on Automatic Approximations for the Analysis of Security Protocols). Protocols to be implemented by the AVISPA tool have to be specified in HLPSL (High Level Protocols Specification Language) [30], and written in a file with extension hlpsl. This language is based on roles: basic roles for representing each participant role, and composition roles for representing scenarios of basic roles. Each role is then independent from the other roles, which gets some initial information by parameters, and then communicate with the other roles by channels. The intruder is modeled using the Dolev-Yao model [16] (as described in our threat model in Section 1.2) with the possibility for the intruder can have a legitimate role in a protocol run. The role system also defines the number of sessions and the number of principals and the roles.
The output format (OF) is generated by using one of the four back-ends explained above. When the analysis of a protocol has been successful (by finding an attack or not), the output describes precisely what is the result, and under what conditions it has been obtained. In OF, we have the following sections:
-
The first printed section, called the SUMMARY, indicates that whether the tested protocol is safe, unsafe, or whether the analysis is inconclusive.
-
The second section, called DETAILS, either explains under what condition the tested protocol is declared safe, or what conditions have been used for finding an attack, or finally why the analysis was inconclusive.
-
Other remaining sections PROTOCOL, GOAL and BACKEND are the name of the protocol, the goal of the analysis and the name of the back-end used, respectively.
-
Finally, after some comments and statistics, the trace of an attack (if any) is also printed in the standard Alice-Bob format.
Protocols need to be implemented in HLPSL. HLPSL supports various basic types, and some of them are given below for better understanding for the specifications of different roles provided in the next subsection:
-
agent: It represents a principal name. The intruder is always assumed to have the special identifier i.
-
public_key: Variables of this type represent agents’ public keys in a public-key cryptosystem. For example, given a public (respectively, private) key pu, its inverse private (respectively, public) key is obtained by i n v_p u.
-
symmetric_key: This type represents a key for a symmetric-key cryptosystem.
-
text: text values are often used as nonces. These values can be used for messages. If R N a is of type text (fresh), then R N a ′ will be a fresh value, which the intruder cannot guess.
-
nat: nat type represents the natural numbers in non message contexts.
-
const: This type represents constants.
-
hash_func: It represents a cryptographic hash function. The base type function also represents functions on the space of messages. It is assumed that the intruder cannot invert hash functions (in essence, that they are one-way collision-resistant functions).
The space of legal messages are defined as the closure of the basic types. For a given message M and encryption key k, {M}_k refers to as the symmetric/public-key encryption. The associative “ ⋅” operator is always used for concatenations.
The “played_by X” declaration indicates that the agent named in variable X will play in a specific role. A knowledge declaration (generally in the top-level Environment role) is used to specify the intruder’s initial knowledge. Immediate reaction transitions have the form A=|>B, which relate an event A and an action B, and it indicates that whenever we take a transition that is labeled in such a way as to make the event predicate A true, we must immediately (that is, simultaneously) execute action B. If a variable X needs to be permanently kept secret, the goal secrecy_of X is to be used in HLPSL. As a result, if X is ever obtained or derived by the intruder, a security violation will result. A detailed description of AVISPA and HLPSL can be found in [1, 2].
7.1 Specifying our scheme
In this section, we discuss in brief the specification of our scheme for the roles of the user U i , the GWN and the sensor node S N j , the session, and also the goal and environment.
We have implemented the registration phase, the login phase and the authentication and key agreement phase of our scheme using the HLPSL language. In our implementation, we have three basic roles, namely alice, server and bob, which represent the participants as the user U i , the GWN and the sensor node S N j , respectively. The specification in HLPSL language for the role of the initiator, the user U i is shown in Fig. 1. The user U i first receives the start signal and changes its state from 0 to 1, and sends the registration request message 〈I D i , R P W i 〉 securely to the GWN using the S n d() operation. The GWN then securely sends the smart card to the user U i . During the login phase, U i sends the message 〈T I D i , C i , P K S i , T S 1〉 to the GWN via a public channel and then waits to receive the acknowledgment \(\langle ID_{SN_{j}},\) T S 3, T S 4, P K S j , D G W N , E G W N 〉 from the GWN using the R c v() operation.
In Fig. 2, we have shown the specification for the role of the GWN in HLPSL. After receiving the registration request message 〈I D i , R P W i 〉 securely from the user U i , it issues back a smart card to the GWN securely. When the GWN receives the message 〈T I D i , C i , P K S i , T S 1〉 from the user U i during the login phase, the GWN sends the message 〈T S 2, T I D i , C G W N , P K S G W N 〉 to the accessed sensor node S N j . After that the GWN receives the message \(\langle ID_{SN_{j}}, TS_{3}, C_{j}, PKS_{j} \rangle \) from S N j . Finally, GWN replies to U i with the message \(\langle ID_{SN_{j}},\) T S 3, T S 4, P K S j , D G W N , E G W N 〉. Similarly, the role specification for the sensor node S N j is provided in Fig. 3. In these specifications, secret (PWi, Bi, K), subs1, Ui) declaration tells that P W i,B i,K are kept to the user U i only, which is characterized by the protocol id subs1. Similarly, we have also specified the secrecy goals for subs2, subs3, subs4 and subs5 protocol ids. In HLPSL, witness (SNj, GWN, bob_server_ts3, TS3’) tells that S N j has freshly generated the value T S 3 for the GWN. The declaration: request(GWN, SNj, server_bob_ts2, TS2’) is meant for S N j ’s acceptance of the value T S 2, which was generated for S N j by the GWN.
In Fig. 4, we have given the specification in HLPSL for the role of session. Figure 5 shows the role specification for the goal and environment. In the session segment, all the basic roles including the roles for U i , GWN and S N j are instanced with concrete arguments. The top-level role, which is called the environment, defines in the specification of HLPSL. It contains the global constants and a composition of one or more sessions, where the intruder may play some roles as legitimate users. In HLPSL, the intruder also participates in the execution of protocol as a concrete session. The current version of HLPSL supports the standard authentication and secrecy goals. In our implementation, we have verified five secrecy goals and six authentications, which are given in Fig. 5.
7.2 Analysis of results
We have first simulated our scheme using the widely-accepted OFMC backend [4] for the execution tests and a bounded number of sessions model checking. For the replay attack checking, this back-end checks whether the legitimate agents can execute the specified protocol by performing a search of a passive intruder. The back-end then provides the intruder about the knowledge of some normal sessions between the legitimate agents. For the Dolev-Yao model check, OFMC checks if there is any man-in-the-middle attack possible by the intruder. We have simulated our scheme under the OFMC backend using the AVISPA web tool [3]. The simulation results for the formal security verification shown in Fig. 6 clearly demonstrates that our scheme is secure against active attacks such as replay and man-in-the-middle attacks.
We have then simulated our scheme using CL-AtSe backend for the formal security verification under the AVISPA web tool [3]. The simulation results for the formal security verification shown in Fig. 7 clearly demonstrates that our scheme is also secure against active attacks such as replay and man-in-the-middle attacks.
8 Performance comparison with related schemes
In this section, we compare the features, computational overhead and communication overhead of our proposed scheme with those for other schemes such as M. L. Das’s scheme [13], Yoo et al.’s scheme [41], Sun et al.’s scheme [35], Xue et al.’s scheme [40], Jiang et al.’s scheme [21].
8.1 Features comparison
In Table 5, we have summarized the comparison of security features provided by our scheme and other schemes. From this table, it is clear that our scheme provides better security features and higher security level. Our scheme has the ability to supports other good features such as correct password change by a legal user without contacting the GWN, biometric update by a legal user without contacting the GWN, non-repudiation because of applying biometric in our scheme, dynamic sensor node addition after initial deployment and formal security analysis and verification. Thus, our scheme is superior in terms of features as compared to those for other schemes.
8.2 Computational overhead comparison
In Table 6, we have compared our scheme for the computational cost with other schemes for the login phase and the authentication and key agreement phase. We denote t h and t f e for the time taken to perform one hashing operation and fuzzy extractor operation (G e n(⋅) or R e p(⋅)), respectively. Note that the fuzzy extractor function is efficient. Due to efficiency of one-way hash function h(⋅), the computational cost of our scheme is comparable with other schemes. The rough estimation of computation cost required for the user registration, login and authentication phases of our scheme and other scheme, we use the simulated values of the execution time of one-way hash function h(⋅) and an elliptic curve point multiplication. As pointed out in [19], the computational time of a one-way hashing operation h(⋅) and an elliptic curve point multiplication are 0.00032 seconds and 0.0171 seconds, respectively. Also, as in [19], we assume that the time for executing a fuzzy extractor is same as that for an elliptic curve point multiplication at the most. Thus, we have, t h ≈0.00032 s and t f e ≈0.0171 s. From Table 6, we see that M. L. Das’s scheme, Yoo et al.’s scheme, Sun et al.’s scheme, Xue et al.’s scheme, Jiang et al.’s scheme and our scheme require 0.00384 s, 0.00608 s, 0.00352 s, 0.01120 s, 0.00768 s and 0.04412 s, respectively, for all the user registration, login and authentication phases. However, for M. L. Das’s scheme, Yoo et al.’s scheme, Sun et al.’s scheme, Xue et al.’s scheme, Jiang et al.’s scheme and our scheme, a sensor node S N j requires the computation cost during the login and authentication phases as t h (0.00032 s), 2t h (0.00064 s), 2t h (0.00064 s), 6t h (0.00192 s), 5t h (0.00160 s) and 5t h (0.00160 s), respectively. Our scheme is also much suited for the resource-constrained sensor nodes due to computational efficiency of h(⋅). Again, the user registration process is a one-time procedure. Though our scheme requires little more computational cost due to fuzzy extractor operations than other schemes during the login and authentication phases, our scheme provides better security features and higher security level than other schemes.
8.3 Communication overhead comparison
Finally, in Table 7, we have compared the communication cost of our scheme with other schemes for the login phase and the authentication and key agreement phase. We assume that the hash digest (output) is 160 bits, if we use SHA-1 hash function [33], timestamp TS is 32 bits, expiration time T E i for a temporal credential is 32 bits, user identity I D i is 160 bits, user temporary identity T I D i is 160 bits, random nonce is 160 bits and sensor node identity \(ID_{SN_{j}}\) is 16 bits. It is clear that Xue et al.’s scheme [40] needs more communication cost compared to all schemes. Though M. L. Das’s scheme [13] requires minimum communication cost among all the schemes, it fails to provide several desired security features, such as mutual authentication, session key agreement, password and biometric update, non-repudiation, and formal security verification. Further, our scheme requires little more communication cost as compared to Jiang et al.’s scheme [21]. This is justified because our scheme provides better security features and higher security level than other schemes.
9 Conclusion
In this paper, we have first reviewed the recently proposed Jiang et al.’s password-based user authentication scheme for WSNs using smart card. We have then pointed out that their scheme has several drawbacks. In order to withstand these drawbacks found in Jiang et al.’s scheme, we have proposed an improved scheme using biometric, password and smart card of a legal user, while retaining the original merits of Jiang et al.’s scheme. We have shown that our scheme provides better security features and higher security level than other schemes, which are demonstrated through the formal and informal security analysis. In addition, we have performed the simulation for the formal security verification of our scheme using the widely-accepted AVISPA tool and the simulation results confirm that our scheme is also secure against replay and man-in-the-middle attacks. Our scheme is also efficient in terms of communication and computational overheads as compared to other schemes. Overall, considering better security features and higher security level, and efficiency that our scheme provides, we conclude that our scheme is more appropriate for practical applications such as healthcare and battlefield applications of WSNs as compared to other existing approaches.
References
Armando A (2005) The AVISPA tool for the automated validation of internet security protocols and applications. In: 17th International conference on computer aided verification (CAV’05). (Lecture Notes in Computer Science), vol 3576. Springer, Berlin, pp 281–285
AVISPA Automated Validation of Internet Security Protocols and Applications. http://www.avispa-project.org/. Accessed on January 2013.
AVISPA AVISPA web tool. http://www.avispa-project.org/web-interface/expert.php/. Accessed on July 2014
Basin D, Modersheim S, Vigano L (2005) OFMC: A symbolic model checker for security protocols. Int J Inf Secur 4(3):181–208
Burnett A, Byrne F, Dowling T, Duffy A (2007) A Biometric Identity Based Signature Scheme. Int J Inf Secur 5(3):317–326
Chen TH, Shih WK (2010) A robust mutual authentication protocol for wireless sensor networks. ETRI J 32(5):704–712
Chuang YH, Tseng YM (2010) An efficient dynamic group key agreement protocol for imbalanced wireless networks. Int J Netw Manag 20(4):167–180
Das AK (2011) Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. IET Inf Secur 5(3):145–151
Das AK, Chatterjee S, Sing JK (2014) Formal security analysis and verification of a password-based user authentication scheme for hierarchical wireless sensor networks. Int J Trust Manag Comput Commun (Inderscience) 2(1):78–102
Das AK, Goswami A (2013) A secure and efficient uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J Med Syst 37(3):1–16
Das AK, Paul NR, Tripathy L (2012) Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Inf Sci 209(C):80–92
Das AK, Sharma P, Chatterjee S, Sing JK (2012) A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J Netw Comput Appl 35(5):1646–1656
Das ML (2009) Two-factor user authentication in wireless sensor networks. IEEE Trans Wirel Commun 8(3):1086–1090
Diffie W, Hellman M (1976) New directions in cryptography. IEEE Trans Inf Theory 22(6):644–654
Dodis Y, Reyzin L, Smith A (2004) Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. In: Proceedings of the advances in cryptology (Eurocrypt’04), LNCS vol 3027. pp 523–540
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
Fan R, Ping LD, Fu JQ, Pan XZ (2010) A secure and efficient user authentication protocol for two-tieres wireless sensor networks. In: 2nd pacific-asia conference on circuits, communications and system (PACCS 2010). pp 425–428
He D, Gao Y, Chan S, Chen C, Bu J (2010) An enhanced two-factor user authentication scheme in wireless sensor networks. Ad hoc & sensor wireless networks 10(4)
He D, Kumar N, Lee JH, Sherratt RS (2014) Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans Consum Electron 60(1):30–37
Huang HF, Chang YF, Liu CH (2010) Enhancement of two-factor user authentication in wireless sensor networks. In: 6th international conference on intelligent information hiding and multimedia signal processing. pp 27–30
Jiang Q, Ma J, Lu X, Tian Y (2014) An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks
Khan MK, Alghathbar K (2010) Cryptanalysis and security improvements of two-factor user authentication in wireless sensor networks. Sensors 10(3):2450–2459
Khan MK, Zhang J, Wang X (2008) Chaotic hash-based fingerprint biometric remote user authentication scheme on mobile devices. Chaos, Solitons Fractals 35(3):519–524
Kocher P, Jaffe J, Jun B (1999) Differential power analysis. In: Proceedings of advances in cryptology - CRYPTO’99, LNCS, vol. 1666. pp 388–397
Li CT, Hwang MS (2010) An efficient biometric-based remote authentication scheme using smart cards. J Netw Comput Appl 33(1):1–5
Li X, Niu JW, Ma J, Wang WD, Liu CL (2011) Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl 34(1):73–79
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51(5):541–552
Nyang D, Lee MK (2009) Improvement of Das’s two-factor authentication. protocol in wireless sensor networks. http://eprint.iacr.org/2009. Report 2009/631
Odelu V, Das AK, Goswami A (2014) A secure effective key management scheme for dynamic access control in a large leaf class hierarchy. Inf Sci 269(C):270–285
von Oheimb D (2005) The high-level protocol specification language hlpsl developed in the eu project avispa. In: Proceedings of APPSEM 2005 workshop
Rivest R, Shamir A, Adleman L (1978) A method for obtaining digital signatures and public-key cryptosystems. Commun ACM 21(2):120–126
Sarkar P (2010) A simple and generic construction of authenticated encryption with associated data. ACM Trans Inf Syst Secur 13(4):33
Secure Hash Standard FIPS PUB 180-1, National institute of standards and technology (nist), u.s. department of commerce, April 1995
Stinson DR (2006) Some observations on the theory of cryptographic hash functions. Des Codes Crypt 38(2):259–277
Sun DZ, Li JX, Feng ZY, Cao ZF, Xu GQ (2013) On the security and improvement of a two-factor user authentication scheme in wireless sensor networks. Pers Ubiquit Comput 17(5):895–905
Tan Z (2014) A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J Med Syst 38(3):1–9
Vaidya B, Makrakis D, Mouftah HT (2010) Improved two-factor user authentication in wireless sensor networks. In: 2nd international workshop on network assurance and security services in ubiquitous environments. pp 600–606
Watro R, Kong D, Cuti S, Gardiner C, Lynn C, Kruus P (2004) TinyPK: Securing sensor networks with public key technology. In: Proceedings of the 2nd ACM workshop on security of ad hoc and sensor networks, SASN 2004. USA, Washington, DC, pp 59–64
Wong K, Zheng Y, Cao J, Wang S (2006) A dynamic user authentication scheme for wireless sensor networks. In: Proceedings of IEEE international conference sensor networks, ubiquitous, trustworthy computing, IEEE Computer Society, pp 244–251
Xue K, Ma C, Hong P, Ding R (2013) A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J Netw Comput Appl 36(1):316–323
Yoo SG, Park KY, Kim J (2012) A security-performance-balanced user authentication scheme for wireless sensor networks. In: International journal of distributed sensor networks 2012 (2012). Article ID 382810, 11 pages. doi:10.1155/2012/382810
Yuan J, Jiang C, Jiang Z (2010) A biometric-based user authentication for wireless sensor networks. Wuhan Univ J Nat Sci 15(3):272–276
Acknowledgments
The authors would like to acknowledge the many helpful suggestions of the anonymous reviewers and the Editor, which have improved the content and the presentation of this paper.
Conflict of interest
The author declares that there is no conflict of interest.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Netw. Appl. 9, 223–244 (2016). https://doi.org/10.1007/s12083-014-0324-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-014-0324-9