Abstract
Barrier Coverage is an important sensor deployment issue in many industrial, consumer and military applications.The barrier coverage in bistatic radar sensor networks has attracted many researchers recently. The Bistatic Radars (BR) consist of radar signal transmitters and radar signal receivers. The effective detection area of bistatic radar is a Cassini oval area that determined by the distance between transmitter and receiver and the predefined detecting SNR threshold. Many existing works on bistatic radar barrier coverage mainly focus on homogeneous radar sensor networks. However, cooperation among different types or different physical parameters of sensors is necessary in many practical application scenarios. In this paper, we study the optimal deployment problem in heterogeneous bistatic radar networks.The object is how to maximize the detection ability of bistatic radar barrier with given numbers of radar sensors and barrier’s length. Firstly, we investigate the optimal placement strategy of single transmitter and multiple receivers, and propose the patterns of aggregate deployment. Then we study the optimal deployment of heterogeneous transmitters and receivers and introduce the optimal placement sequences of heterogeneous transmitters and receivers. Finally, we design an efficient greedy algorithm, which realize optimal barrier deployment of M heterogeneous transmitters and N receivers on a L length boundary, and maximizing the detection ability of the barrier. We theoretically proved that the placement sequence of the algorithm construction is optimal deployment solution in heterogeneous bistatic radar sensors barrier. And we validate the algorithm effectiveness through comprehensive simulation experiments.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Barrier Coverage is an important sensor deployment issue in many industrial, consumer and military applications, such as machine management, health care monitoring, battlefield surveillance [19], etc. Recent years have witnessed a trend that radar sensors have been increasingly deployed in guarding militarized zones, and monitoring hazards warehouse and frontier [2, 25, 28, 31]. Traditional passive sensors typically leverage on a disk sensing model. In contrast, BR sensors use a Cassini oval sensing model [5]. The sensing region of a BR sensor depends on the locations of both the BR transmitter and receiver, and is characterized by a Cassini oval. Moreover, since a BR transmitter (or receiver) can potentially form multiple BRs with different BR transmitters (or receivers, respectively), the sensing regions of different BRs are coupled, making the coverage of a BR sensor network highly non-trivial.
The barrier coverage problem of bistatic radar sensor network has been studied by many researchers recently. Gong et al. [9] studied the barrier coverage problem of bistatic radar sensor network. In [30], a minimum cost placement algorithm was developed for line barrier coverage. To improve quality, a belt with a predefined breadth is considered and covered by several same lines. In [3], the authors studied both fault tolerance and energy-saving issues combining the minimum cost placement of BR sensors for belt barrier coverage. In the above researches,they all assumed that radar sensors have the same physical parameters, and all BRs are homogeneous in their barrier coverage model.
However, heterogeneous deployment of sensors with different physical parameters is necessary in many practical application scenarios. In [12], the authors introduce a heterogeneous barrier-coverage in which guarantees that any penetration variation of intruder is detected by at least one sensor with different sensing capabilities. In [16], the author investigates the impact of heterogeneity on lifetime sensing coverage in heterogeneous sensor network. They use an optimal mixture of inexpensive low-capability sensors and expensive high-capability sensor to significantly extend the lifetime of network. In [11], the authors consider a hybrid barrier coverage application for heterogeneous sensor network to protecting critical facilities located inside the barrier region, and preventing illegal border crossings.The existing work on bistatic radar barrier coverage mainly focus on homogeneous radar sensor networks, while little effort has been made on barrier coverage formation in heterogeneous radar sensor networks.
In this paper, we study the optimal barrier coverage problem in heterogeneous bistatic radar sensor networks. Heterogeneous bistatic radar sensor network is composed of bistatic radar sensors with different physical parameters. We consider using bistatic heterogeneous radar sensors to optimal deploy a straight barrier with predefined length, and maximize the detection probability of the barrier. Firstly, we explore the optimal placement strategy of single transmitter and multiple receiver, and propose the pattern of aggregate deployment. Then we further study the optimal deployment sequences of multiple heterogeneous transmitters and receivers. Finally, we introduce an efficient greedy algorithm, which realize optimal barrier deployment of M heterogeneous transmitters and N receivers on a L length boundary, and achieving the maximizing of the detection probability of the barrier. We theoretically prove that the deployment of heterogeneous bistatic radar barrier is optimal. And we validate the algorithm effectiveness through comprehensive simulation experiments. To the best of our knowledge, this appears the first work to investigate the barrier coverage problem in heterogeneous bistatic radar sensor networks.The main contributions of this paper are summarized as follows.
We investigate the Cassini oval sensing models and propose the optimal placement pattern of single transmitter and multiple receivers.
We introduce the convergent deployment of heterogeneous transmitters and receivers. It can achieve the maximum coverage length under the condition to satisfy the predefined detecting SNR threshold.
We propose the Greedy Selection Algorithm to realize the optimal deployment of coverage barrier with M heterogeneous transmitters and N receivers on a specific length barrier, and maximize the detection probability of an intruder crossing any part of the barrier.
We theoretically prove that the convergent deployment sequence of heterogeneous bistatic radar achieves optimal coverage, and validate the effectiveness of the optimal deployment algorithm through comprehensive simulation experiments.
The rest of paper is organized as follows: Section 2 reviews the related work. Section 3 introduces the system model and problem description. Section 4 describes the optimal deployment method of heterogeneous straight barrier coverage. Simulation results are presented in Sections 5 and 6 concludes the paper.
2 Related work
Many barrier coverage problems have been widely studied in the last decade, and most of these studies are based on the passive disk coverage model [1, 4, 13, 14, 21, 23], or passive sector coverage model [6, 20, 26, 32]. The sensors sense and receive surrounding information passively, such as seismic sensor [24], acoustic sensor [22] and so on. Many scholars studied the optimal barrier coverage problem based on the passive sensing model, examples are the weak barrier coverage [17], strong barrier coverage [19] and K-barrier coverage [29].
In recent years,some researchers studied the radar sensor coverage problem [7, 8]. Being different from passive disk sensing, the radar sensor detects the target by the active transmitting radar signal, such as Doppler radar [8], bistatic radar [30]. These sensors have important application in security and target tracking [15, 18], and have become a important research problem in wireless sensor network recently. In [10], the authors consider the problem of deploying a network of homogeneous BRs in a region to maximize the worst-case intrusion detectability, which amounts to minimizing the vulnerability of a barrier. In [30], a minimum cost bistatic radar placement algorithm was developed for line radar barrier coverage to monitor intruders. To improve quality, a belt radar sensor barrier with a predefined breadth is considered and covered by several same lines. In [5], the authors discussed how to construct a static radar barrier on the smallest circumcircle of the area which is protected to minimize the cost. In [3], the authors study belt barrier coverage in bistatic radar sensor model. They propose a new deployment method that further reduces the total placement cost and then study the fault-tolerance issue and the energy-saving issue.
Aforementioned studies of sensor coverage are mainly focused on homogeneous sensor networks. However, cooperation among different types or different physical parameters of sensors is necessary in many practical application scenarios. In [16], the author investigate the impact of heterogeneity on lifetime sensing coverage in a single-hop direct communication model and a multi-hop communication model. In [27], the authors discuss the intrusion detection in the homogeneous and heterogeneous WSN.In [12], the authors introduce a heterogeneous barrier-coverage in which guarantees that any penetration variation of intruder is detected by at least one sensor with different sensing capabilities. They use disk sensing model. In [11], the authors consider a hybrid barrier coverage application for heterogeneous sensor network to protecting critical facilities located inside the barrier region, and preventing illegal border crossings.In the existing works on heterogeneous sensors coverage issues, they mainly use disk sensing model with different sensing capabilities, or different sensor types, such as electronic, optic and acoustic sensors.
However, the existing studies of bistatic radar sensor coverage are mainly focused on homogeneous radar sensor networks. They all assumed that bistatic radar have the same physical parameters in their radar barrier coverage model.While little effort has been made on barrier coverage formation in heterogeneous radar sensor networks. Hence, in this paper, we investigate the barrier coverage in heterogeneous bistatic radar sensor networks.In order to improve the detection probability of heterogeneous bistatic radar barrier, we study how to construct barrier coverage with predefined length using given number of transmitter and receivers to achieve maximized sensing capability.
3 Sensor model and problem definition
3.1 Bistatic radar sensor model
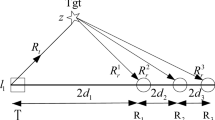
Different from traditional sensors, a bistatic radar sensor has both transmitters and receivers. A transmitter can be pair with one receiver to form a radar pair, and the transmitter and receiver are placed in different locations. The transmitter sends signals, and the receiver receives the signals when the signals are reflected by a target. Whether a target can be detected by a transmitter and receiver pair depends on SNR that the target reflects. It is shown in Figure 1.
We use ∥AB∥ to denote the (Euclidean) distance between two points A and B, Ti and Rj to denote the locations of a transmitter node and of a receiver node, respectively. X denotes the location of the target. SNR obtained by the target X is
where K denotes a bistatic radar physical parameter that reflects sensing characteristics of the TiRj pair and is determined by the transmitter. SNR obtained by a target is inversely proportional to the product of the square of the distance between the transmitter and receiver.
Definition 1 (Detection Threshold)
When SNR threshold of a BR pair is determined, its detection threshold is defined as
The detection threshold is the maximum of the product of the distance between the transmitter and the receiver when SNR threshold is determined. If the distance is exceeded, the target cannot be detected by the BR pair.
Definition 2 (Detection Value)
For a target x, the product of the distance between the transmitter Ti and x, and the distance between the receiver Rj and x is defined as the detection value of x obtained by TiRj bistatic radar pair.
For a target x, if D(x) < C (C is the detection threshold when SNR is determined), x can be detected by this TiRj pair. Therefore, the sensing region of a BR pair can be characterized by a Cassini oval, as shown in Figure 2.
A Cassini oval is a locus of points. The product of the distances to two fixed points (coci) is constant for any point on Cassini oval. If the detection value of the point on the Cassini oval locus is equal to C, the detection value of the points within the area of the Cassini oval locus is less than C, the area outside the locus is greater than C. That is, the area within the Cassini oval locus can be detected and the area outside the Cassini oval locus cannot be detected by this BR pair.
In a bistatic radar network, one transmitter paired with one receiver forms a BR pair. Theoretically, every transmitter (or receiver) can potentially pair with different receivers (or transmitters) to form multiple BR pairs.
3.2 Problem definition
In this paper, we mainly study the barrier coverage problem in heterogeneous bistatic radar sensor networks. The heterogeneous bistatic radar network is composed of M transmitters with different physical parameters and N receivers. We consider using bistatic heterogeneous radar sensors to deploy a straight barrier with length L,to achieve the optimal detection performance on the straight boundary. Every transmitter has different signal transmission frequency. All receivers are capable of receiving any frequency of radar transmitters’ signals. We assume that each receiver can only receive the specific frequency signal from a transmitter at final deployment, and each transmitter can send signal to multiple receivers.
As shown in Figure 3, the star represents the transmitter and the circle represents the receiver. We use different colors to represent transmitters with different parameters. Every receiver can select to receiving only one transmitter’s signal in heterogeneous single-receive bistatic radar barrier. We construct a heterogeneous bistatic radar barrier in which a number of transmitters with different sensing signal frequencies and a number of receivers form a fixed length bistatic radar barrier to detect cross-barrier intruder. We provide some definitions as follows.
Definition 3 (Placement sequence)
A placement sequence is an sequence of all the radar nodes on the line from left to right.
The radar transmitters in the Figure 4 have different phisical parameters , but the receivers are of the same type. The placement sequence contains two aspects: 1) the permutation of the sensor nodes (transmitters and receivers) ; 2) the space between every two adjacent radar nodes.
Definition 4 (SNR of A Point)
For any point x on the barrier Ii, it may attained multi-SNRs by multiple BR pairs. We use the maximum SNR as this point’s SNR.
Where T is the transmitter set and R is the receiver set.
Definition 5 (Vulnerability)
The vulnerability V (Ii) of a barrier Ii is the minimum SNR of all points in Ii.
Where the X is the set of all points in Ii.
As to the optimal barrier deployment model on heterogeneous bistatic radar, we give a formal description of the problem as follows.
Problem 1
The length of barrier I in Figure 3 is L, there are M transmitters that have different physical parameters and N receivers. Our goal is to find the optimal placement sequence. The optimal placement sequence has the maximum vulnerability of barrier I, namely, the barrier has the best performance of intrusion detection.
The Problem-1 is defined as follows.
Where Hl and Hr denote the left endpoint and right endpoint of barrier I, respectively.
We can formulate a related Problem-2 of Formula (7) from Formula (6).
Problem 2
As it is described by Formula (7) , it is about how to find the optimal placement sequence for maximum the barrier’s length when of SNR of I’s vulnerability is not less than r. If we can solve Formula (7), we can also solve Formula (6) by the bisection search in Algorithm 1.

The function optimal − algorithm(r) in the code of Algorithm 1 is the algorithm to solve Formula (7).
In order to solve the Formula (7) , we need to determine.
- 1.
The permutation of the transmitters and the receivers in the optimal placement sequence.
- 2.
The corresponding transmitter of every receiver is determined.
- 3.
The distance between every pair of adjacent radar nodes.
4 Model construction and Algorithm analysis
4.1 Basic coverage pattern
Every receiver can be paired only with one transmitter. Every transmitter has only one receiver set that only receive the signals from this transmitter no matter what final optimal placement sequence is. Therefore, the area covered by a transmitter and its corresponding receiver set is called basic coverage pattern, as shown in Figure 5.
4.2 Optimal placement of single transmitter and multiple receivers
We study the following problem before solving Problem-2.
Problem 3
For any one transmitter Ti, given n{n = 1,2,3,..., N} receivers, we will find the optimal placement sequence to get the maximum cover length when SNR threshold is not less than r.
Where \(S_{{T_{i}}}^{n}\) denotes the placement sequence and it consists of transmitter Ti and n receivers. \({\text {cover}}(S_{{T_{i}}}^{n})\) denotes the length covered by placement sequence \(S_{{T_{i}}}^{n}\).
For transmitter Ti, we get its detection range by Formula (2), denoted by Ci when SNR threshold is r. That is, the target x cannot be detected by the TiRj pair when the product of the distance between the target and the transmitter Ti and the distance between the target and the receiver Rj exceeds.
For Formula (8) , we consider this situation first: the receivers are only deployed at one side of the transmitter.
When n = 1, there is only one receiver, as shown in Figure 6.
Let d1 = ∥TiR1∥, the minimum SNR point between \(\overline {{T_{i}}{R_{1}}} \) is the midpoint of the \(\overline {{T_{i}}{R_{1}}} \), the detection value of this point is \(D(O) = \frac {{{d_{1}}}}{2} \times \frac {{{d_{1}}}}{2}\). We assume D(O) = Ci, and obtained \({d_{1}} = 2\sqrt {{C_{i}}} \), the coverage range is the longest (Appendix, Proof 1).
When n = 2, there are two receivers, as shown in Figure 7.
Where ∥TiR1∥ = d1, let d2 = ∥R1R2∥. The vulnerability in \(\overline {{R_{1}}{R_{2}}} \) is the midpoint of \(\overline {{R_{1}}{R_{2}}} \), and its detection value is \(D(O) = \frac {{{d_{2}}}}{2} \times \left ({\frac {{{d_{2}}}}{2} + {d_{1}}} \right )\), let \(\frac {{{d_{2}}}}{2} \times \left ({\frac {{{d_{2}}}}{2} + {d_{1}}} \right ) = {C_{i}}\), and d2 is solved. namely, when ∥TiR1∥ = d1, ∥R1R2∥ = d2, the coverage range is the longest (Appendix, Proof 2).
We obtain a formula to calculate the distance between Rk− 1 and Rk when n = k, k = 3,4,5....
According to formula (9), we obtain every value of di{i = 1,2,3...}. If we deploy receivers at one side of a transmitter according to the value di{i = 1,2,3...}, the range covered by the placement sequence is the longest. Therefore we obtained the optimal placement interval array d[] = {d1, d2, d3,...dn} of transmitter Ti. It is a decline array. di continues to decrease, the coverage range after every receiver deployed decreases when i increases, as shown in Figure 8.
We study the problem that deploys the receivers at one side of the transmitter for maximizing the coverage range in the previous studies. After that, we consider the case of deploying receivers on both sides of the transmitter. We deploy receivers on both sides of the transmitter symmetrically so that the of numbers of receivers on both sides are the same, or there is one more receiver in one side than that in the other side. And the receiver deployment interval in each side belongs to the optimal interval array (Appendix, Proof 3) . We find the deployment method to solve Formula (8), as shown in Figure 9.
4.3 Optimal placement for multiple heterogeneous transmitters and multiple receivers
In the previous sections, we have solved the problem-3: there are one transmitter and n receivers, the placement sequence for maximizing the coverage range is obtained when SNR threshold is determined. But if there are more than one transmitter, and every transmitter has several receivers. It is a problem to obtain the placement sequence for maximizing the coverage range. Details are as follows.
Problem 4
There are m transmitters {T1, T2,...Tm}, and the number of receivers that every transmitter owns is {K1, K2,...Km}. It is a problem to find the optimal placement sequence for maximizing the cover length on the line when SNR threshold is r.
Definition 6 (Converge deployment)
For a placement sequence, if every transmitter and its receiver set (its receiver set only receives its signals) are deployed together, it means there is no other transmitter(s) or receiver(s) among them, and the deployment of every transmitter and its receivers satisfies the maximum interval deployment. We call it a converge structure. In a converge structure, two adjacent basic coverage patterns clung to each other. We call this deployment strategy the converge deployment.
As shown in Figure 10, in the converge deployment, the black solid ellipse and the red dotted ellipse are arranged tightly on the left and right sides of the line barrier respectively. In Non-converge deployment, as shown in Figure 11, the black solid ellipse and the red dotted ellipse in the fence are arranged separately from each other.
Theorem 1
The optimal placement sequence of Problem-4 satisfies the converge deployment.
Proof
The Proof of Theorem 1 is in Appendix. □
If a placement sequence satisfies the converge deployment, every basic coverage pattern has the longest coverage length. Because there is no overlap among basic coverage patterns, the entire placement sequence gained is the longest coverage length.
Theorem 2
The length of range covered by a placement sequence that satisfies the converge deployment strategy are all equal.
Proof
The Proof of Theorem 2 is in Appendix. □
According to Theorem 2, when a placement sequence satisfies the converge deployment strategy, the order of basic coverage pattern does not matter, so the coverage length that the placement sequence covers is not influenced. Therefore, if we find the placement sequence that satisfied the converge deployment strategy, Problem-4 is solved.
From the definition of converge structure, there is no gap in the converge structure. If an intruder crosses the barrier which is formed by a placement sequence that satisfies the converge deployment strategy, the intruder is detected.
4.4 Optimal placement sequence algorithm in heterogeneous bistatic radar sensor
We denote the optimal placement sequence to solve Problem-2 by Sop. It contains M transmitters {T1, T2...TM}, and the numbers of receivers that every transmitter owns are {K1, K2,...KM}, and \(\sum \nolimits _{i = 1}^{M} {{K_{i}} = N} \). From Problem-4, Sop satisfies the converge deployment strategy. In order to solve Problem-2, we need to determine the value of Ki.
- 1.
every Ti’s optimal interval array di[] in Sop is computed according to the maximum placement interval deployment.
- 2.
the greedy − searchalgorithm is proposed to determine the number of receivers that every transmitter matched.
The greedy − searchalgorithm is described as follows: before a receiver is assigned, an iteration is run. In the iteration, every transmitter gets the maximal interval in all optimal interval array. Then the receiver is assigned to this transmitter. This interval is deleted in its optimal interval array. This process is repeated until every receiver is assigned.

In the above codes, the array p[] records the number of receivers that every transmitter has already owned. Line 3 ∼ 5 computes every transmitter’s optimal interval array di[]{i = 1,2...M}. Line 8 ∼ 12 selects the transmitter that has the maximal interval. The number of receivers of every transmitter is determined. These radars are deployed according to converge deployment strategy. The optimal placement sequence is obtained.
5 Simulation results
The simulation experiments are performed on Windows 10 system; Programming language is C++ and Python. The algorithms are realized in C++ language. And the visualization of deployment results is realized in Python language. We study the deployment of M transmitters that have different physical parameters and N receivers to form a barrier in a straight line with a length of L, and maximize the vulnerability in the barrier. We propose the optimal deployment strategy, OPT. In order to validate the performance of OPT, we compared with two deployment methods in simulation experiments.
Method1: As shown in Figure 12, we compute the square root of every transmitter’s physical parameters: \({q_{i}} = \sqrt {{K_{i}}} \{ i = 1,2...M\} \). Then we determine every transmitter’s coverage length and the number of receivers according to the value of qi in proportion. We combine every 2 receivers into a group when assigning the number of receivers. Every transmitter has the same or nearly the same number of receivers. For every Ti, we assume that it has Ni receivers and the length of coverage range is Li, and we determine the location of every node in the following way: Ti is deployed in the midpoint of Li, and Ni/2 receivers are deployed in both sides of Ti. The interval of deployment is half of the former one.
As shown in Figure 13, we obtain x by computation, and the location of every receiver can be determined. Therefore, we finally obtain the locations of every transmitter and every receiver.
Method2: As shown in Figure 14, the receivers are deployed in the straight line uniformly. Every transmitter’s coverage length is determined in proportion with the value of qi. These coverage ranges are placed in Line L. Every transmitter in the coverage range is deployed.
In the experiment, we investigate the influence of the number of transmitters, receivers, barrier length on the detecting performance. The detecting capability of bistatic radar barrier is determined by the minimum detecting SNRs of all point on the barrier’s boundary, called as the barrier’s vulnerability.
We assume the length of barrier L = 1000m. When the number of transmitters is fixed (M = 20), SNR of the barrier’s vulnerability is increase when the number of receivers is increased. As shown in Figure 15, our OPT deployment method has higher detecting performance compared with method 1 and method 2.
When the number of receivers is fixed (N = 100), SNR of the barrier’s vulnerability is increased when the number of transmitters is increased. As shown in Figure 16, our OPT deployment method also has higher detecting performance compared with method 1 and method 2.
In Figure 17, we use the same set of sensors, and we find that the effect of OPT is always better than the other two methods. When the barrier’s length increases,the interval spaces between transmitters and receivers increase, the detectiong vulnerability will become very small, and the performance of our method will become closer to method 1 and method 2. As shown Figure 18, when we zoom in on local charts in the case of L ≥ 1600m, the performance of OPT was still better than the other two methods.
6 Conclusions
Barrier Coverage is an important sensor deployment issue in many industrial, consumer and military applications. In this paper, we studied optimal barrier coverage in the heterogeneous bistatic radar barrier sensor networks. The object is how to maximize the detection ability of bistatic radar barrier with given numbers of radar sensors and barrier’s length. We proposed the optimal placement strategy of single transmitter and multiple receiver, and proved the optimal pattern of aggregate placement. Then we proposed the optimal deployment strategy of multiple heterogeneous transmitters and receivers and proved the optimal placement sequences of radar sensors. Finally, we design an efficient greedy algorithm, which realize optimal barrier deployment of M heterogeneous transmitters and N receivers on a L length boundary, and maximizing the detection ability of the barrier. We validated the algorithms’ effectiveness through theoretical analysis and comprehensive simulation experiments.
References
Ammari, H.M.: A Unified Framework for k -coverage and Data Collection in Heterogeneous Wireless Sensor Networks. Academic Press Inc., Cambridge (2016)
Ammari, H.M., Das, S.K.: Centralized and clustered k-coverage protocols for wireless sensor networks. IEEE Trans. Comput. 61(1), 118–133 (2011)
Chang, H.Y., Kao, L., Chang, K.P., Chen, C.: Fault-tolerance and minimum cost placement of bistatic radar sensors for belt barrier coverage. In: International Conference on Network and Information Systems for Computers, pp. 1–7 (2017)
Chen, A., Kumar, S., Lai, T.H.: Local barrier coverage in wireless sensor networks. IEEE Trans. Mob. Comput. 9(4), 491–504 (2010)
Chen, J., Wang, B., Liu, W.: Constructing Perimeter Barrier Coverage with Bistatic Radar Sensors. Academic Press Ltd., Cambridge (2015)
Cheng, C.F., Tsai, K.T.: Distributed barrier coverage in wireless visual sensor networks with β-qom. IEEE Sensors J. 12(6), 1726–1735 (2012)
Dutta, P.K., Arora, A.K., Bibyk, S.B.: Towards radar-enabled sensor networks. In: International Conference on Information Processing in Sensor Networks, pp. 467–474 (2006)
Gong, X., Zhang, J., Cochran, D.: When target motion matters:, Doppler coverage in radar sensor networks. In: IEEE INFOCOM, pp. 1169–1177 (2013)
Gong, X., Zhang, J., Cochran, D., Xing, K.: Barrier coverage in bistatic radar sensor networks:cassini oval sensing and optimal placement. In: Fourteenth ACM International Symposium on Mobile Ad Hoc NETWORKING and Computing, pp. 49–58 (2013)
Gong, X., Zhang, J., Cochran, D., Xing, K.: Optimal placement for barrier coverage in bistatic radar sensor networks. IEEE/ACM Trans. Networking 24 (1), 259–271 (2016)
Karatas, M.: Optimal deployment of heterogeneous sensor networks for a hybrid point and barrier coverage application. Computer Networks 132, 129–144 (2018)
Kim, H., Ben-Othman, J.: Heterbar: Construction of heterogeneous reinforced barrier in wireless sensor networks. IEEE Commun. Lett. PP(99), 1–1 (2017)
Kim, H., Kim, D., Li, D., Kwon, S.S., Tokuta, A.O., Cobb, J.A.: Maximum lifetime dependable barrier-coverage in wireless sensor networks. Ad Hoc Netw. 36(P1), 296–307 (2016)
Kumar, S., Lai, T.H., Arora, A.: Barrier Coverage with Wireless Sensors. Springer, New York (2007)
Kusy, B., Ledeczi, A., Koutsoukos, X.: Tracking mobile nodes using rf doppler shifts. In: International Conference on Embedded Networked Sensor Systems, SENSYS 2007, pp. 29–42. Sydney, Nsw, Australia (2007)
Lee, J.J., Krishnamachari, B., Kuo, C.C.J.: Impact of heterogeneous deployment on lifetime sensing coverage in sensor networks. In: 2004 First IEEE Communications Society Conference on Sensor and Ad Hoc Communications and Networks, 2004 IEEE SECON 2004, pp. 367–376 (2004)
Li, L., Zhang, B., Shen, X., Zheng, J., Yao, Z.: A study on the weak barrier coverage problem in wireless sensor networks. Computer Networks the International Journal of Computer & Telecommunications Networking 55(3), 711–721 (2011)
Lim, J.H.L., Terzis, A.T., Wang, I.J.W.: Tracking a non-cooperative mobile target using low-power pulsed doppler radars. In: Local Computer Networks, pp. 913–920 (2010)
Liu, B., Dousse, O., Wang, J., Saipulla, A.: Strong barrier coverage of wireless sensor networks. In: ACM Interational Symposium on Mobile Ad Hoc NETWORKING and Computing, MOBIHOC 2008, pp. 411–420. Hong Kong, China (2008)
Liu, L., Zhang, X., Ma, H.: Exposure-path prevention in directional sensor networks using sector model based percolation. In: IEEE International Conference on Communications, pp. 1–5 (2009)
Lu, Z., Li, W.W., Pan, M.: Maximum lifetime scheduling for target coverage and data collection in wireless sensor networks. IEEE Trans. Veh. Technol. 64(2), 714–727 (2015)
Nguyen, H.T.: State-of-the-art in mac protocols for underwater acoustics sensor networks. In: Emerging Directions in Embedded and Ubiquitous Computing, EUC 2007 Workshops: TRUST, WSOC, NCUS, UUWSN, USN, ESO, and SECUBIQ, Taipei, Taiwan, December 17-20, 2007, Proceedings, pp. 482–493 (2007)
Rahman, M.O., Razzaque, M.A., Hong, C.S.: Probabilistic sensor deployment in wireless sensor network: A new approach. In: The International Conference on Advanced Communication Technology, pp. 1419–1422 (2007)
Reekie, L., Chow, Y.T., Dakin, J.P.: Optical in-fibre grating high pressure sensor. Electron. Lett. 29(4), 398–399 (1993)
Saipulla, A., Westphal, C., Liu, B., Wang, J.: Barrier coverage with line-based deployed mobile sensors. Ad Hoc Netw. 11(4), 1381–1391 (2013)
Tao, D., Tang, S., Zhang, H., Mao, X., Ma, H.: Strong barrier coverage in directional sensor networks. Comput. Commun. 35(8), 895–905 (2012)
Wang, Y., Wang, X., Xie, B., Wang, D., Agrawal, D.P.: Intrusion detection in homogeneous and heterogeneous wireless sensor networks. IEEE Trans. Mob. Comput. 7(6), 698–711 (2008)
Wang, B., Xu, H., Liu, W., Liang, H.: A novel node placement for long belt coverage in wireless networks. IEEE Trans. Comput. 62(12), 2341–2353 (2013)
Wang, Z., Liao, J., Cao, Q., Qi, H., Wang, Z.: Achieving k-barrier coverage in hybrid directional sensor networks. IEEE Trans. Mob. Comput. 13(7), 1443–1455 (2014)
Wang, B., Chen, J., Liu, W., Yang, L.T.: Minimum cost placement of bistatic radar sensors for belt barrier coverage. IEEE Trans. Comput. 65(2), 577–588 (2016)
Yildiz, E., Akkaya, K., Sisikoglu, E., Sir, M.Y.: Optimal camera placement for providing angular coverage in wireless video sensor networks. IEEE Trans. Comput. 63(7), 1812–1825 (2014)
Zorbas, D., Razafindralambo, T.: Prolonging network lifetime under probabilistic target coverage in wireless mobile sensor networks. Comput. Commun. 36(9), 1039–1053 (2013)
Acknowledgements
This work is supported by the Key Science-Technology Program of Zhejiang Province, China (2017C01065) and the National Natural Science Foundation of China (61370087).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article belongs to the Topical Collection: Special Issue on Smart Computing and Cyber Technology for Cyberization
Guest Editors: Xiaokang Zhou, Flavia C. Delicato, Kevin Wang, and Runhe Huang
Appendix
Appendix
Proof
(Proof 1) When a placement sequence consist of one transmitter and one receiver, the coverage length reaches the maximum when the distance between them is \(2\sqrt {{c_{i}}} \).
Let d1 = ∥TiRj∥, we consider three possible cases as follows.
-
Case 1: when \({d_{1}} < 2\sqrt {{c_{i}}} \), the coverage range is presented in Figure 19.
We can divide the range into 3 parts: part \(\overline {A{T_{i}}} \), part \(\overline {{T_{i}}{R_{j}}} \), part \(\overline {{R_{j}}B} \). Let ∥ATi∥ = ∥RjB∥ = x, because of ∥ATi∥ ×∥ARj∥ = ci, then x (x + d1) = ci, so the length of coverage range is \({L_{1}} = \sqrt {{d_{1}^{2}} + 4{c_{i}}} \).
-
Case 2: when \({d_{1}} = 2\sqrt {{c_{i}}} \), the coverage range is presented in Figure 20.
Similar to Case 1, the length of coverage range is \({L_{2}} = \sqrt {{d_{1}^{2}} + 4{c_{i}}} \), then L2 > L1, because of \(d_{1}^{(2)} > d_{1}^{(1)}\).
-
Case 3: when \({d_{1}} > 2\sqrt {{c_{i}}} \), the coverage range is presented in Figure 21.
Because \(d_{1}^{(3)} > d_{1}^{(2)}\), then ∥ATi∥(3) = ∥RjD∥(3) < ∥ATi∥(2) = ∥RjB∥(2), and ∥TiB∥(3) = ∥RjC∥(3) < ∥TiO∥(2) = ∥RjO∥(2), so we get that L3 = 2 (∥ATi∥(3) + ∥TiB∥(3)) < L2 = 2 (∥ATi∥(2) + ∥TiO∥(2)). □
Proof
(Proof 2) Optimal deployment interval when the number of deployed receivers is n = 2, as shown in Figure 22.
As shown in Figure 21, let d1 = ∥T1R1∥, d2 = ∥R1R2∥. When \({d_{1}} = 2\sqrt {{c_{i}}} \) and d2 is the solution of \(\frac {1}{2}{d_{2}} \times \left ({\frac {1}{2}{d_{2}} + {d_{1}}} \right ) = {c_{i}}\), the coverage length of the placement sequence is the longest. It is because the following discussion.
When ∥R1R2∥ < d2, it is shown in Figure 23.
Here, compared with Figure 23, ∥T1D∗∥ < ∥T1D∥1 (the superscript 1 denotes Figure 23), and ∥AT1∥ remains unchanged, therefore the coverage length of the placement sequence becomes shorter.
When ∥R1R2∥ > d2, it is shown in Figure 24.
∥DE∥ < ∥CD∥1 (the superscript 1 denote the Figure 22), so the coverage length turns shorter compared with Figure 22. Therefore, if we deploy two receivers on one side of a transmitter, the coverage length is longest when ∥T1R1∥ = d1 and ∥R1R2∥ = d2. □
Proof
(Proof 3) When a placement sequence consists of one transmitter and n receivers, the coverage length is longest when we deploy the n receivers on both sides of the transmitter equally and the deploy intervals satisfied the optimal deployment intervals.
As shown in Figure 25, we assume that we have two deployment strategies: strategy1 and strategy2.
strategy1: |left1 − right1| ≤ 1, left1 + right1 = n
strategy2: |left2 − right2| > 1, left2 + right2 = n
left denotes the number of receivers that are deployed on the left of the transmitter, and the right denotes the number of receivers that are deployed on the right of the transmitter.
In Proof 2, if we deploy receivers on one side of the transmitter, the coverage length is the longest if the deployment intervals are the optimal deployment intervals. Therefore, we assume that the deployment intervals in strategy1 or strategy2 all satisfy the requirement of the optimal deployment intervals.
For convenience, we assume left1 ≤ right1, left2 ≤ right2, we get left1 > left2, right1 < right2 and left1 − left2 = right2 − right1. The optimal interval array d[] is a decreasing array, we assume.
sum1 = d[left2] + d[left2 + 1] + ... + d[left1]
sum2 = d[right1] + d[right1 + 1] + ... + d[right2]
Therefore, sum1 > sum2, and the range from left2 to right1 is a shared part of both strategy1 and strategy2. So the coverage length obtained from strategy1 is longer than that from strategy2. □
Proof
(Theorem 1) There are two placement sequences, S1 and S2. S1 satisfies the converge deployment and S2 don’t satisfies the converge deployment.
Our proof is reduction ad absurdum. We assume S2 is the optimal placement sequence. Its coverage range covered is the longest. Because S2 doesn’t satisfy the converge deployment, there is at least one transmitter Ti, the deployment sequence with this transmitter (and its receivers set) doesn’t satisfy the optimal interval deployment. However, S1 satisfies the converge deployment, the deployment sequence with this transmitter (and its receivers set) satisfies the optimal interval deployment. We obtain the following expression from section 4. 2, \({\text {cov}} er({~}^{1}S_{{T_{i}}}^{{K_{i}}}) > {\text {cov}} er({~}^{2}S_{{T_{i}}}^{{K_{i}}})\) and \({\text {cov}} er({~}^{1}S_{{T_{j}}}^{{K_{j}}}) > {\text {cov}} er({~}^{2}S_{{T_{j}}}^{{K_{j}}}),j = 1,2,...M{\mathrm { and j}} \ne {\mathrm {i}}\). Ki denotes the number of receivers in Ti’s receivers set. \({~}^{1}S_{i}^{{K_{i}}}\) denotes the placement sequence with Ti and its Ki receivers. Therefore, \({\text {cov}} er({S_{1}}) > {\text {cov}} er({S_{2}})\). S2 is not set up for the optimal placement sequence. □
Proof
(Theorem 2) If there are two placement sequences with the same transmitter parameters of the, and the number of receivers owned by each transmitter is the same. If both placement sequences satisfy the converge deployment, that is to say they have the same basic coverage patterns, therefore their coverage ranges are equal. We give an example to illustrate this conclusion, It is shown in Figure 26.
Both placement sequences are composed of the same three basic coverage patterns. But the arrangement sequences of these three basic coverage patterns are different, Therefore they are two different placement sequences. But the coverage range covered by each basic coverage patterns of the two placement sequences correspond are equal. The coverage range covered by these two placement sequences are equal. □
Rights and permissions
About this article
Cite this article
Xu, X., Zhao, C., Jiang, Z. et al. Optimal placement of barrier coverage in heterogeneous bistatic radar sensor networks. World Wide Web 23, 1361–1380 (2020). https://doi.org/10.1007/s11280-019-00699-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-019-00699-5