Abstract
In wireless sensor networks (WSN), for reliability, load balancing and security reason, various sinks, for the most part, sent for gathering different copies of checking data, which causes high vitality use and network lifetime diminishment. Sensors are in charge of detecting and transferring information, and gateways are furnished with 3G/4G radios and can store the gathered information from sensors incidentally and transmit the information to the remote server farm through a third party correspondence benefit. In this paper, consider remote monitoring center through a third party telecommunication service. For this situation service cost assessment in WSN, the cluster the networks used by possibilistic fuzzy C means clustering strategy and minimize the service cost of network with the help of enhanced krill swarm optimization, create an issue of amplifying network throughput with negligible service cost with a target to expand the measure of information gathered by all passages while limiting the service cost. From that re-imagined network, throughput is ensured with the greatest lifetime and information design in the Airtel network with the least cost. From the simulation analysis, outcome exhibit the proposed algorithm outperforms different algorithm in terms of service cost and performance measures.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The current advancement of limited cost sensors and microcontrollers supporting network is advancing the usage of conveyed observing and control algorithms in many industrial and civilian applications through designs made out of Wireless Sensor nodes [1]. Nowadays WSNs have concerned in a lot of concentrates because of the minimal effort of sensors and their wide-range applications. WSNs give another class of PC frameworks and grow human capacity to remotely associate with the physical world [2]. In terms of regular range observing device, site supervisors are doing their remote checking through a surveillance camera altogether stay away from exposures [3]. One more encouraging access innovation is a remote access system, for example, Wi-Fi and Wi-Max, which gives services at low cost and serves better adaptability to the client [4]. If the identities or the areas of the source node or destination nodes are uncovered, at that point it could be exceptionally harming to the sent sensor network [5]. Free space optics (FSO)-based networking is an alluring option for the next to next-generation cellular networks [6]. An FSO connect utilizes the free space between a couple of laser-photograph indicator handsets to transport information [7]. Research on sensor networks was essentially started for strategic observation in military applications, by tossing sensors in a cold landscape with the guide of an unmanned vehicle or a low flying airship; consequently empowering warriors to have upgraded attention to conceivable nearness of synthetic and natural operators [8].
The server energy constraints imposed on WSNs lead designers to endeavor for energy efficient process strategies and algorithms. Therefore, maximizing network lifetime by optimizing the energy dispersal of sensor nodes is thought to be the most significant plan objective for WSNs [9]. Sensor network has turned out to be one of the hot issues in another round advancement of financial, sciences and innovation in the present world. The utilization and advancement of it are extremely significant to advance financial improvement and social advance [10]. To limit the operational cost, there are two key issues to be tended to. One is that diverse client demands have distinctive service level agreements (SLAs), how to perform a distribution that meets different SLA necessities is testing. An answer is to assign the solicitations with a similar level SLA to one server farm [11,12,−13]. Thus, every data focus can ensure its support of the conceded demands with a given level SLA. This arrangement, however, may not be relevant to vast scale server farms with different SLA prerequisites [14].
Right now, an intriguing way to deal with expand the lifetime of sensor nodes is to outfit them with rechargeable innovations, which change over sources, for example, body warm, foot strike, finger strokes and sun oriented into power [15]. Some irregular or dishonorable back off procedures are used, which cause the impedances among two bounces transmissions and chop down the reliability increase; Most of the existing technologies [16] are intended for one source-goal combine correspondence, which can’t meet the necessity of many-to-one interchanges in WSNs [17].
2 Literature Review
In 2015 Bade et al. [18] to satisfy the bandwidth demands from end clients, dynamic engineering was proposed with co-existence of LTE, WiMax and UWB advance. Mixture wavelength division multiplexing (WDM) and a time division multiplexing (TDM) based optical access network offer reconfigurable arrangement. Upgrade the capacity to assign diverse wavelengths to various optical networking units (ONUs) on request. Furthermore, two distinctive channel routing modules (CRMs) are acquainted all together with address the cost adequacy and vitality productivity issues of the proposed network. Take-up rate versatile mode operation and activity versatile power administration is used to improve the advantages of low speculation cost with vitality effectiveness. Up to 26% power utilization lessening is accomplished at the time of minimum traffic conditions while 10% utilization is accomplished at the time of maximum traffic conditions. Besides 23% energy saving can be accomplished contrasted with ordinary frameworks in completely worked organize.
Utilizing VNS for the Optimal Synthesis of the Communication Tree in Wireless Sensor Networks by Erzin et al. [19]. NP-difficult issue finding an optimal spanning tree in a given undirected weighted chart which happens while limiting the power utilization of information transmission in radio systems. Proposed new heuristics and directed an a posteriori investigation. All the proposed techniques indicated high adequacy, however, it was signed a hybrid genetic algorithm (GA) utilizing variable neighborhood search (VNS) as mutations. From the outcomes, hole happens because, for the appraisal of the proportion for a huge measurement, the lower bound was utilized rather than the optimal value for the objective function. In fact, we accept that the 1.0009-surmised arrangement was worked for each measurement of the issue.
In 2015 Kliks et al. [20] the pattern in wireless communications systems is the upgrade of the system foundation with the presentation of little cells, where a particular topographical territory is served by low-run, low-control get to focuses. The outcome was the creation of a heterogeneous topology where macrocells coincide with an assortment of small cell sorts. In the publication article, we quickly condense the current specialized advances in the plan and deployment of future heterogeneous networks addressed in the papers that make the exceptional issue. Specifically, the accompanying perspectives were viewed as: the plan of obstruction and radio asset administration algorithms, the examination of the energy efficiency and power control issues in heterogeneous networks, the idea of coordination in small cell networks, key backhaul parts of HetNets, organization issues and general administration methodologies.
In 2015 Lin et al. [21] Analysis network process (ANP) approach fulfills these necessities by considering inward and external conditions among different criteria. In this investigation, the objective is to utilize ANP to assess the relative weights and needs of the elements deciding passenger decision of LCCs. Firstly, writing a survey and expert opinion was led to create 16 sub-criteria alongside four criteria (e.g., perceived advantages, perceived external influence, perceived service quality, and perceived corporate value) that influence passenger decision of low-cost carriers (LCC). Also, ANP was connected to build up an assessment shows that organized the relative weights connecting the over four criteria with 16 assessed sub-criteria. The outcomes not just give an assessment model to decide the relative significance of the impacts of LCCs on passenger decision, yet can likewise enable supervisors to concentrate on the principle factors and distinguish the best approach for promoting passenger acknowledgment toward LCCs.
In 2015 Viswanath et al. [22] have proposed the Monitoring Systems are important to comprehend the progressions that happen in environments. Remote monitoring and information accumulation system are helpful and successful instruments to gather data from mass stockpiling tanks and to monitor the same. The estimation of fluid inside the tank was most imperative and such frameworks are helpful in industries which are ordered as security basic frameworks. The engineering and beginning testing consequences of a low power remote framework for tank level observing utilizing ultrasonic sensors.
In 2014 Xu et al. [23] have proposed the cost related with the service will be brought about, which will be dictated by the number of gateways employed and the total volume of information effectively received within a predetermined monitoring period. For the situation, the first figure a novel compelled optimization problem with a goal to limit the service cost while a pre-characterized organize throughput was ensured. Allude to the issue as the throughput ensured benefit–cost–minimization issue and demonstrate that it was NP-finished. The key elements of the heuristic incorporate distinguishing entryways and finding a system effective backwoods of directing trees established at the portals. We additionally perform a hypothetical examination of the arrangement acquired. At long last, we direct tests by reenactments to assess the execution of the proposed calculation. Experimental comes about exhibit the proposed algorithm outperforms different algorithms as far as both the service cost and the network lifetime.
3 Methodology
The service overheads caused for the communication of the assembled through the third party network comprises of a settled cost for particular information. This exploration work builds up the model for service-cost minimization of WSN with ensured throughput in remote monitoring with inspired optimization model. The virtual topology network is industrialized that incorporates an arrangement of different sensor nodes, one base station, and server considered, these nodes are gathered based on a various mobile network utilizing possibilistic fuzzy C means (PFCM) clustering method. Besides all clusters group are pick one cluster with help of trust measure and foreseen conspire marks a sensor as a cluster head, in the event that it has minimum energy utilization and shelters the best arrangement of attracted nodes which were arranged accessible in that connection arrangement and it offer ascent to additional phases on the premise of the association of the system. The mobile communication system ad hoc on-demand distance vector (AODV) protocol utilized to generate the path of various networks.
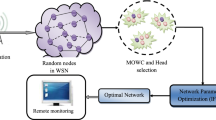
For limiting the service cost, the network throughput is optimized with the threshold (α) value and assorted optimization techniques are considered to optimize the threshold parameter α. For optimizing the threshold value, the combination of two inspired optimization techniques which are krill herd optimization (KHO) and particle swarm optimization (PSO) considered; so the proposed model is termed as enhanced krill swarm optimization (EKSO) compared for service cost and a most extreme lifetime of the various mobile network. The execution of the solutions based on the fitness value is rehashed for finding the optimal threshold of the network. The general outline of the proposed system appears in Fig. 1.
3.1 Designing of Network Topology
In the proposed routing algorithm, the source node situating in the physical framework chooses a course for information transmission based on the considered control framework states; transient and consistent states. Our proposed routing algorithm takes after an indistinguishable approach from AODV protocol. This protocol works responsively to diminish overhead discovering courses just on request. At the point when a route does not exist to a given destination, a route request (RREQ) message is overwhelmed by the source and by the intermediate node event that they have no past routes in their node. Subsequent to designing system topology additionally took after by clustering process.
3.2 Cluster Formation
In cluster arrangement process the cluster heads will broadcast request for a packet to the sensor nodes come in radio range to form a cluster. In a singlehop, the node transmits to the cluster head straightforwardly and in multi-hop, all sensor node will send their information through the neighbor node. Cluster arrangement helps to advance information transmission purpose PFCM clustering system utilized and its model appears in Fig. 2.
Possibilistic Fuzzy C-means clustering
The imperative motive of the probabilistic fuzzy C-means (PFCM) cluster module is committed to the predefined set of information into clusters. By methods for the clustering module, the training set is assembled into different subsets. The PCM utilizes the goal work (1) that depends on the averageness estimations of information to the clusters. These qualities result from the relaxation of the FCM requirement where the sum of every section of U must be equivalent to one. The system of PFCM clustering model demonstrated as follows.
Beyond objective function is minimized and it will be \(\beta_{i} > 0,1 \le i \le h > 1\), the parameters a and b define the relative importance of the membership degrees and the typicality values. Here M → membership matrix, U → typicality matrix, c → resultant cluster center and P → data points.
-
1.
Evaluate Distance matrix for sensor network nodes
At the point, when the cluster is resolved, the assessment of the distance between the centroids and data point for each segment is done. For the distance calculating process consider Euclidian distance formula. Further, the separation matrix is resolved in regard to every cluster.
-
2.
Typicality matrix calculation for nodes
The commonality matrix, thusly, is gotten from PCM. The probability estimation of every datum point in connection to each centroid is completed. Consequently, the typicality network is made.
-
3.
Membership Function generation
The evaluation of the membership matrix Mik is performed by way of assessing the membership value of information point which is gathered from the FCM. As illustrated in the help of the following Eq. (4), the membership value of each data point in relation to each centroid is finished.
-
4.
Updating of centroid
After the creation of the clusters, the modernization of the centroids is performed in accordance with the equation shown below.
Ensuring to the modernization of the centroids in regard to every cluster, the assignment of assessing the separation with the lately modernized centroids is begun and proceeded until the assessment of the modernization of the centroids. If we increment the significance (weight) of membership then that essentially drives us to lessen the significance of typicality by a similar amount. Likewise, we will see later that the optimal ordinariness values rely upon the size of a and b If give more importance to membership values than PFCM work closer to FCM algorithm and if give more importance to typicality values than PFCM work closer to PCM.
3.3 Cluster Head (CH) Selection
The CH accumulates and additionally gathers and gets data from nodes having a place with a similar cluster and after those exchanges on data to achieve the goal. By pivot of the cluster-head self-assertively, energy utilization is expected to be consistently scattered. Ordinarily, CHs are assigned from the organized nodes on the premise of the criteria like remaining energy, and network. This cluster heads far from the base station without considering nodes’ lingering energy and it’s chosen by the help of trust measure.
where T1 → recommendation trust value and T2 → direct trust value
In the event that the node assigned as CH moves to rest state throughout transmission of messages then the node staying dynamic with least cost and maximum communication will be selected as CH in the clutter.
3.4 Enhanced Optimization Model for Service Cost in WSN
Minimize the service cost while keeping up the throughput prerequisite, the proposed heuristic needs to recognize a suitable number of portals, and configuration routing trees established at the entryways spanning the rest of sensors with the end goal that the service cost is limited while the normal throughput necessity is kept up. Our proposed model distinctive seven systems considered, in view of optimization technique (enhanced krill swarm optimization) to get ensured network with least cost, most extreme lifetime.
Service Cost
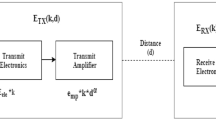
The service cost of remote observing is dictated by the number of gateways and the additional volume of information beyond the information amount at each gateway, as telecommunication organizations, for the most part, give the information transfer administration to each gateway through discretionary information designs, each of which is with a fixed cost and information design of various systems. It’s calculated by utilizing
Here
To guarantee the required information integrity and the observing quality by a particular application, we characterize the network throughput necessity. Information transmission inside the sensor network is inconsistent; this will bring about information misfortune during its transmission. Above equation, the parameters are a → a number of gateways, fc → fixed cost, \(V[D^{\tau } ]\) → Volume of data received, P → Data plan, pc → Penalty rate τ → period and kg → Data generation rate.
The penalty to a portal is either 0 if the normal volume of transmitted information by the gateway does not surpass the arrangement. Since the penalty relies upon the normal volume of information surpassing the quantity, the measure of the service cost itself is a normal value, as well. For the sake of convenience, still, refer to it as service cost.
3.4.1 Threshold Optimization: Enhanced Krill Swarm Optimization (EKSO)
Given the number of portals, need to address which sensors ought to be recognized as the portals. The decision of portals is guided by the accompanying reason. Optimize the throughput EKSO will be used to limit service cost of on WSN network. Here at first consider KHO to two rule goals, for instance, expanding krill thickness and Reaching sustenance, so the swarming behavior of extending thickness and finding food. In addition, consider PSO demonstrate speed and position to the physical diffusion of KHO process and the flowchart appears in underneath Fig. 3.
Objective function as
Fitness function of this model is a limit service cost in the mobile network model. The entire data into various clusters and objective of threshold optimization, it’s shown in the below equation.
The new threshold updating procedure
It is realized that an optimization algorithm ought to be fit for searching spaces of self-assertive dimensionality. Along these lines, the accompanying Lagrangian model is summed up to an n-dimensional choice space.
Here Mi → motion induced by other krill individuals; Ji → foraging motion, and Pi → physical diffusion of the ith krill individuals (achieved by the PSO).
Movement induced by other krill individuals
In the improvement, the course of development of a krill individual is resolved both by the neighborhood swarm thickness (local effect), an objective swarm thickness (target effect) and a ghastly swarm thickness (repulsive impact). The krill advancement can be described as
In the aboveconditions, the documentationare clarified just like Mmax the greatest incited rate, ωn is the idleness weight of the movement instigated to the extent [0, 1],
Foraging motion
The scavenging movement is thought as far as two primary successful parameters. The first is the sustenance area and the second one is the past experience about the nourishment area. This movement can be communicated to the ith krill individual as takes after:
Here Sv is the scavenging velocity, ωm is the dormancy weight of the searching movement in the reach [0, 1], is the last scrounging movement, \(\delta_{i}^{food}\) is the nourishment appealing and \(\delta_{i}^{best}\) is the impact of the best wellness of the krill as such. As indicated by the deliberate estimations of the searching rate it is taken 0.02 ms−1.
Physical Diffusion
The physical diffusion of krill individuals is believed to be an unpredictable method. This development can be express the extent that a most extraordinary dispersion speeds and an irregular directional vector.
Enhanced process or steps in EKSO
The physical diffusion of krill swarm algorithm is enhanced by the updation of speed and position of the PSO. The particles will move in every cycle to an alternate position until the point that they achieve an optimum position. At each time, the particle velocity is updated by Eq. (13),
Here Pt → particle velocity, Ct → current particle, h1 and h2 → learning factor, r1 and r2 → a random value within the [0, 1]. In the event of discriminating the velocity and location assessment of the particles, the fitness value is once more established for the freshly evaluated velocity of the particles.
3.5 Optimal Network with Communication in WSN
Remote observing scenario where a homogeneous sensor network with unreliable wireless communications is deployed in a locale that is topographically different from the one of the monitoring focus. From the proposed model chose optimal WSN mobile network with information exchange by employing administration from third-party telecommunication organization brings about least service cost and most extreme lifetime with optimal data design are recognized. From that model sensors are to be distributed to portals and an arrangement of steering trees established at the doors are to be worked to traverse all sensors with the end goal that the aggregate of the service cost of all passages is limited, while the normal volume of information relayed by the gateways meets the system throughput necessity.
4 Simulation Result analysis
In this segment, we assess the execution of the proposed algorithm and examine the service cost investigation in WSN mobile network actualized in network simulation Version 2 (NS2) with simulation parameters and IEEE 802.11b is connected as the MAC layer protocol and user datagram protocol (UDP) is connected as the transmission port operator. Mobile network and execution measurements depict in beneath and it’s contrasted with the existing optimization model.
Mobile Networks
Airtel
BhartiAirtel is an Indian multinational telecommunication service, headquartered in New Delhi. It works in 20 nations across over South Asia, Africa, and the Channel Islands. It gives GSM, 3G and 4G LTE mobile service. Additionally, it offers broadband and telephone utilities in 94 urban communities. Airtel is the biggest mobile operator in South Asia and the third biggest in the world with a 303 million endorser base.
MTS
MTS India is the Telecommunication Company of Russian Mobile Tele frameworks headquartered in New Delhi. It gives innovation of CDMA, EVDO to principle conditions of India. In Tamil Nadu, totally 30 Lakhs subscriber base are utilized for MTS mobile network.
Idea
Idea cellular normally alludes as Idea. It is an Indian mobile network administrator situated in Mumbai, India. The idea is incorporated with GSM administrator, which gives 2G and 3G mobile services. By supporter base, it is the third most operators in India. In Tamil Nadu, Idea provides the 2G pack with Unlimited (1.5 GB FUP) information, with the cost of Rs. 199 and for 3G, the cost is Rs. 374 for 1.64 GB with 28 days of legitimacy. In Tamil Nadu, Idea was utilized by 54 Lakh subscriber base.
Reliance
Reliance is an Indian web access and broadcast communications organization headquartered in Navi Mumbai, India. It gives CDMA, GSM and settled line broadband. Reliance Network coverage in Tamil Nadu is just 2G and CDMA yet no 3G. Reliance offers 2G pack, it gives an amazingoffer to their client with the least expensive cost, 1 GB 2G Data + Rs 100 Core Talk time at Rs. 189 with 28 days legitimacy. It likewise offers 3G pack, 1 GB 3G Data with the cost of Rs. 199 for 30 days. A number of Subscriber base in Telangana is 70 lakhs for CDMA.
Aircel
Aircel is an Indian mobile network administrator, headquartered in Chennai. It offers voice, 2G, 3G and 4G information benefit. In Tamil Nadu, Aircel gives both 2G and 3G benefit as postpaid and prepaid Mobile broadband Wireless Internet information designs.
BSNL
BSNL has a complete scope of telecom benefits in India including wireline, CDMA mobile, GSM mobile, web, Broadband, Carrier Service, MPLS-VPN, VSAT, VoIP administrations, IN administrations and so on. It is one of the biggest open segment organization in India. BSNL gives just 2G pack, with the cost of Rs. 198 for 1 GB information with the legitimacy of 28 days.
Vodafone
Vodafone is a British multinational telecommunications organization, headquartered in London. It is the second biggest telecommunication organization. It has 184 million clients as of April 2015. Vodafone gives both 2G and 3G mobile services. In Tamil Nadu, Idea was utilized by 10 Lakhs subscriber base.
Simulation Model
For the development of the nodes, the aggregate number of nodes is set to 250 nodes in the 1000 M × 1000 m network region. The random way point (RWP) demonstrates is utilized. In our simulation, the minimum speed is 5 m/s, the node generation appeared in Fig. 4. The source–destination pairs are spread arbitrarily finished the network. The ns-2 Constant Bit-Rate (CBR) traffic generator is connected to set up the connection patterns with various irregular seeds. Every node has one CBR movement associated with a single unique destination. The parameters appeared in Table 1.
Table 1 shows the simulation parameters for different nodes and their relating values for different networks. The movement for a total number of nodes in the network is set to 250 nodes. The ns-2 constant bit-rate (CBR) traffic generator is connected to set up the link designs with various irregular random seeds for different network examinations. The total number of nodes in the network is thought to be 500 for the network zone 1000 m × 1000 m. The reception apparatus sort is taken as Omni antenna and the transmission go for the network is 250 m and packet size is 512.
Figure 4 the above chart demonstrates the node creation show for the diverse networks Airtel, MTS, Idea, Reliance, Aircel, BSNL, and Vodafone. In this model the service cost is limited by the proposed WSN mobile network form is actualized. The nodes are connected and we have computed the separation of the connected nodes.
Performance Parameters
A number of data Transmitted: It is the quantity of information that the sensor node transmits in a time period which is typically 1 s.
Energy Consumption
Energy utilization is very much characterized as the communication overhead of the nodes where a firm number of false information are infused into a network.
Packet to Delivery Ration (PDR)
The amount of information which was viably transferred to the end node related to the measure of information which was transferred by the transmitter.
Network Life Time (NLT)
The amount of information which was viably transferred to the end node related to the measure of information which was transferred by the transmitter.
Service Cost (SC)
Service cost incurred about by transferring sensing information to the remote information monitoring focus utilizing third-party telecommunication. The decision form of the expanding network throughput with limited service cost issue in an inconsistent sensor network.
Table 2 demonstrates the node based result for various networks. For every single node compute the data transmitted (MB), energy consumption (J), the packet to delivery ratio, network lifetime (h), and service cost ($). Here, the parameters are analyzed for five types of nodes i.e. 100–500. Propositions parameters are analyzed with the proposed technique ad hoc on-demand distance vector (AODV) with EKSO. It is clarified in the underneath diagram.
Nodes Based Results
Figure 5a demonstrates the data transmitted (MB) for various nodes. For PSO algorithm the data transmitted from 0.9 to 2.2 MB. For constrained optimization, the data transmitted from 1 to 3 MB. But for EKSO algorithm, the data transmitted from 2 to 5 MB. Contrasted with the existing algorithm, the proposed algorithm EKSO transmitted the maximum data.
Figure 5b represents the energy utilization (J) for different nodes. In this graph, the energy consumption is calculated based on three optimization techniques i.e. EKSO, constrained and PSO. Based on this examination, the energy consumption for EKSO reaches 300–1250 J, constrained technique attained 300–1050 J, and PSO algorithm the energy consumption obtains 200–600 J. For the comparison of all the three optimization techniques, EKSO consumed minimum energy compared to other algorithms.
Figure 5c shows the packet to delivery ratio (PDR) for different nodes (i.e.), the amount of data transferred by the transmitter. In the PSO algorithm, the amount of data increases and then decreases linearly, then for the constrained algorithm the amount of data increases and then decreases. For EKSO algorithm the amount of data linearly increases and then decreases slightly. Contrasted to these algorithms, EKSO algorithm gives better performance for every node.
Figure 5d shows the network lifetime (h) for different nodes based optimization techniques. In node 100, the EKSO algorithm achieves the network lifetime as 125.63 h, constrained technique as 90.3 h; PSO reaches NLT as 36 h. For the analysis of this node, KSO has a higherlifetime than the other two techniques. Similarly, for other nodes (200–500) the data increases and then decreases in PSO then the data increases and then decreases linearly for the constrained technique. For EKSO algorithm, the data linearly increases and then slightly decreases. Compare to the other two algorithms EKSO gives the maximum NLT (h).
Figure 5e demonstrates the service cost ($) for different nodes. For PSO algorithm the cost increases linearly. Similarly, for the constrained algorithm the cost increases till it reaches the node 500. For EKSO algorithm the cost decreased for each node. Compared to the other two algorithms, EKSO gives the minimum cost and it gives the better performance.
Throughput Based Results
Figure 5a describes the throughput versus data transmitted (MB) for various nodes. In PSO algorithm the throughput value increases and the corresponding data increases. For the constrainedalgorithm, the data increases linearly. Similarly, for EKSO algorithm, the data transmitted from 3000–6000 MB. Finally, the proposed EKSO algorithm gives the maximum data transmitted compared to the other two.
Figure 6a represents the throughput versus network life time (h). In the throughput analysis, the NLT can be examined based on optimization techniques. The NLT increases and then decreases for the PSO algorithm. For the constrained technique, the NLT increases and then decreases. For EKSO algorithm, the NLT increases linearly. Compared to the other two algorithms EKSO gives the better network life time (NLT) (h).
Figure 6c demonstrates the throughput versus service cost ($). For PSO algorithm, the throughput increases and the corresponding cost increases. Similarly, for the constrained algorithm the service cost increases. For EKSO algorithm the service cost reaches the minimum value and it gives the better performance compared to the other two algorithms.
Figure 7a demonstrates the service cost for various nodes. For network size 100, AODV protocol achieves 100, LEACH protocol achieves 152, and DSDV protocol achieves 152. For the network size 200, AODV protocol achieves 190, LEACH protocol achieves 200, and DSDV protocol achieves 150. Similarly, the network size at 300, 400, and 500, AODV gives the minimum cost.
Figure 7b represents the network size versus network life time and service cost for various nodes. For the node at 100, AODV protocol achieves NLT 100, LEACH protocol achieves NLT 10, DSDV protocol achieves NLT 9. For the node at 200, AODV protocol achieves NLT 90, LEACH protocol achieves NLT 20, DSDV protocol achieves NLT 18, similarly at 300, 400 and 500, and AODV achieves the improved performance.
Table 3 shows the throughput based results for different nodes. When the threshold value is set as 0.5, the service cost is minimum (75) at node 100 and NLT at 500. If the node increases the service cost also increases. When the threshold value is set as 0.7, the service cost is minimum at 100, the NLT at 500. Similarly, the threshold value set as 8, 0.9, and 1, the corresponding service cost and NLT varied according to the threshold value.
Figure 8 represents the service cost for different networks such as Airtel, Aircel, MTS, Idea, Vodafone BSNL, and reliance. The various nodes are 100, 200, 300, 400, and 500. For the node at 100, Airtel achieves 49, Aircel achieves 52, MTS achieves 99, Idea achieves 100, Vodafone achieves 100, BSNL achieves 48, and Reliance achieves 58. For node at 200, Airtel achieves 120, Aircel achieves 100, MTS achieves 150, Idea achieves 120, Vodafone achieves 160, BSNL achieves 100, and Reliance achieves 150. Similarly at node 300 and 400, the cost is maximum, at node 500, the cost is the minimum for all the networks.
5 Conclusion
The study scrutinized Remote monitoring service for Wireless Sensor Network (WSN) with maximizing network throughput and minimal service cost. The cost associated with this service will be incurred, which will be determined by the number of gateways employed and the cumulative volume of data successfully received within a specified monitoring period. Furthermore, the main objective of this technique was to minimize the cost, depending on the number of nodes, performance parameters, clusters and confidentiality of the transmission. Additionally, various protocols such as AODV, LEACH, and DSDV were utilized for the generation of the path for different networks. From the simulation analysis, the proposed algorithm EKSO gives the minimum service cost and maximum lifetime, compared to the PSO and constrained technique.
References
Frezzetti, A., Manfredi, S., & Pagano, M. (2015). A design approach of the solar harvesting control system for wireless sensor node. Journal of Control Engineering Practice, 44, 45–54.
Chena, X., & Roweb, N. (2013). Energy-efficient communication in wireless cable sensor networks. Journal of Parallel, Emergent and Distributed Systems, 28(4), 289–307.
Shimura, M., Kitahara, H. K. H., Kobayashi, H., & Okamot, S. (2004). Radiation area monitoring by wireless-communicating area monitor with surveillance camera. Journal of Nuclear Science and Technology, 41(4), 271–274.
Bhatt, U. R., Chouhan, N., & Upadhyay, R. (2015). Hybrid algorithm: A cost efficient solution for ONU placement in fiber-wireless (FiWi) network. Journal of Optical Fiber Technology, 22, 76–83.
Gagneja, K. K. (2015). Secure communication scheme for wireless sensor networks to maintain anonymity. In Proceedings of the computing, networking and communications (ICNC), IEEE international conference (pp. 1142–1147), Garden Grove, CA.
Demers, F., Yanikomeroglu, H., & St-Hilaire, M. (2011). A survey of opportunities for free space optics in next generation cellular networks. In Ninth annual proceedings of communication networks and services research conference (CNSR) (pp. 210–216). Ottawa: IEEE.
Li, Y., Pappas, N., Angelakis, V., Píoro, M., & Yuan, D. (2014). Optimization of free space optical wireless network for cellular backhauling (pp. 1406–2480), arXiv preprint.
Jain, N., & Agrawal, D. (2005). Current trends in wireless sensor network design. Journal of Distributed Sensor Networks, 1, 101–122.
Yildiz, H. U., Bicakci, K., Tavli, B., Gultekin, H., & Incebacak, D. (2016). Maximizing wireless sensor network lifetime by communication/computation energy optimization of non-repudiation security service: Node level versus network level strategies. Ad Hoc Networks, 37, 301–323.
Ling, N., & Mei-Xia, D. (2015). Design of a remote data monitoring system based on sensor network. Journal of Smart Home, 9(5), 23–30.
Gandhi, A., Harchol-Balter, M., Das, R., & Lefurgy, C. (2009). Optimal power allocation in server farms. Journal of ACM Sigmetrics Performance Evaluation Review, 37(1), 157–168.
Gandhi, A., Gupta, V., Harchol-Balter, M., & Kozuch, M. (2011). Optimality analysis of energy-performance trade-off for server farm management. Journal of Performance Evaluation, 67, 1155–1171.
Guo, Y, Ding, Z, Fang, Y., & Wu, D. (2010). Cutting down electricity cost in internet data centers by using energy storage. In 2011 IEEE proceedings of the global telecommunications conference (GLOBECOM 2011) (pp. 1–5), Houston.
Xu, Z., & Liang, W. (2015). Operational cost minimization of distributed data centers through the provision of fair request rate allocations while meeting different user SLAs. Computer Networks, 83, 59–75.
Gao, D., Lin, H., & Liu, X. (2016). Routing protocol for k-anycast communication in rechargeable wireless sensor networks. Journal of Computer Standards & Interfaces, 43, 12–20.
Marina, M., & Das, S. (2006). Ad hoc on-demand multipath distance vector routing. Journal of Wireless Communications and Mobile Computing, 6(7), 969–988.
Sun, X., Chen, H., Wu, X., Yin, X., & Song, W. (2016). Opportunistic communications based on distributed width-controllable braided multipath routing in wireless sensor networks. Ad Hoc Networks, 36, 349–367.
Bade, M., Toycan, M., & Walker, S. (2015). Cost and energy efficient operation of converged, reconfigurable optical wireless networks. Journal of Optical Switching and Networking, 18, 71–80.
Plotnikov, E., et al. (2015). Using VNS for the optimal synthesis of the communication tree in wireless sensor networks. Journal of Electronic Notes in Discrete Mathematics, 47, 21–28.
Kliks, A., Pérez-Romero, J., Boukhatem, L., & Zalonis, A. (2015). Technical advances in the design and deployment of future heterogeneous networks. Journal on Wireless Communications and Networking, 1, 1–5.
Lin, H.-F., & Huang, Y.-W. (2015). Factors affecting passenger choice of low cost carriers: An analytic network process approach. Journal of Tourism Management Perspectives, 16, 1–10.
Viswanath, S., Belcastro, M., Barton, J., O’Flynn, B., Holmes, N., & Dixon, P. (2015). Low-power wireless liquid monitoring system using ultrasonic sensors. Journal on Smart Sensing & Intelligent Systems, 8(1), 26–44.
Xu, X., Liang, W., & Xu, Z. (2014). Remote monitoring cost minimization for an unreliable sensor network with guaranteed network throughput. Journal of Information Processing in Agriculture, 1(2), 83–94.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Thekkil, T.M., Prabakaran, N. Minimizing Remote Monitoring Service Cost of Wireless Sensor Networks Using Krill Swarm Optimization. Wireless Pers Commun 109, 1429–1448 (2019). https://doi.org/10.1007/s11277-019-06620-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-019-06620-7