Abstract
Cognitive radio was introduced to fill up the imbalance between spectrum scarcity and spectrum underutilization. So to make such an ideology work, a network which can utilize all the available channel in the best efficient manner, without causing any harmful interface to primary user (PU) and maintaining the Quality of Service (QoS) for cognitive user (CU) is required. In both Mesh as well as ad-hoc networks, effective utilization of the white-spaces by the CUs maintaining the QoS for both primary and CU is a challenging task due to the frequent and instant change in their channel status. In this paper an intelligent-MAC (i-MAC) for cognitive radio (CR) using two transceivers based on hybrid approach of combination of cooperative decision and contention-free approach is proposed. Cooperative decision, to overcome hidden node or the case when there is no common channel between the CU’s and contention-free approach, to solve the issues in contention mechanism, where same channel is selected simultaneously by multiple CU’s. Proposed CR-i-MAC permits an effective dynamic spectrum access to CUs without effecting the QoS for PU’s. The simulative performance analysis of proposed CR-i-MAC is tested in various critical cases like multi-channel single-radio and multi-channel multi-radio over different on demand routing protocols like dynamic source routing, ad-hoc on demand distance vector and weighted cumulative expected transmission time using network simulator (NS-2). The performance of the network is measured on the basis of parameters like throughput, delay and interference. The analysis of the simulation results shows that the proposed CR-i-MAC outperforms various other CR MAC’s in terms of both increased throughput and reduced delays thereby making the system stable and efficient.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
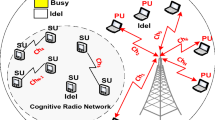
Cognitive radio (CR) is an emerging technology equipped to figure out the problem of spectrum scarcity. Opportunistically detecting the vacant portions of the spectrum and transmitting over them, while safeguarding the working of licensed or primary users (PUs) [1, 2]. Innovations in wireless technologies like software defined radios (SDRs), provide solution to limitations in legacy wireless communication systems. Inefficient utilization and management of radio frequency (RF) spectrum for both licensed and unlicensed bands is one of the basic and foremost problem of legacy wireless communication. Even now a days, Regulatory Agencies manages RF spectrum by allocating fixed portions of radio spectrum to so called PU. This ensures interference free communications between two end users and at the same time suffers from spectrum wastage during non-communicable periods. To take control over the spectrum scarcity and underutilization, several bodies headed by the Federal Communications Commission (FCC), have been taking action to make a new prototype for spectrum management. FCC in 2002, reported that more than 70 % of the allocated Radio Spectrum is idle at particular times or geographic locations [3]. To keep up pace with growing demand, more efficient dynamic spectrum access (DSA) technologies are required [4, 5] . This forces, to adapt to the dynamically changing spectrum resource, learning about the spectrum occupancy and making decisions on the quality of the available spectrum resource, which includes its expected duration of use, probability of disruption caused by the licensed users. Thus, CR Networks help to make efficient use of the available spectrum holes for CR operation [3]. In addition, frequencies reserved for public service may experience intermittent use and the frequent quiet periods may also be used for CR transmission.
In each of the above cases, an important consideration is the error-free detection of spectrum holes and utilize them in best dynamic way without causing any performance degradation to the PUs fixed to that particular band. Lot of research have already been done over the physical layer sensing. This motivates the research in cognitive radio-medium access control (CR-MAC) protocols, with an aim for providing efficient means of sensing the channel to determine its occupancy, and sharing the spectrum among the other CR. While doing so, maintain zero or bearable interference to the licensed user, as they have priority usage over the channel than cognitive users. The CR-MAC protocols differ from standard MAC, as CR-MAC schemes have close coupling of hardware support of the system with the physical layer. To illustrate this in detail, the carrier sense mechanism used by MAC layer in standard-MAC’s does not disclose complete information regarding the channel owing, as they are incapable to differentiate between the energy radiated by PUs or other secondary user in the spectrum [6]. Moreover, in case of collision, re-transmission of packets starts but in cognitive radio networks, transmission must terminate immediately due to PU activity. To differentiate this, the physical layer may support the MAC layer in the implementation of the sensing strategy and identifying the origin of the radiated power by baseband analysis of the spectrum shape. A general framework of the spectrum functions and the inter-layer coupling is shown in Fig. 1. Based on the RF stimuli from the physical layer RF environment, the sensing scheduler of CR-MAC can determine the sensing and transmission times. Spectrum Access can manage the availability of the spectrum when required. The spectrum sensing block plays critical role, both in terms of long term channel characterization and ensuring the vacant channel at time of actual data transmission [7, 8].
Cognitive radio MAC capabilities [8]
Therefore the MAC for DSA based cognitive radio networks (CRNs) needs to designed in such a way that sensing of spectrum holes and continuous monitoring of dynamic changing environment is detected instantly. This is very challenging task as interest of not only PU but also the cognitive user is required. Various MAC protocols for CRN’s have been proposed in [9–32] based on mesh as well as ad-hoc networks.
In this paper, issues in CR-MAC strategy’s in which there is collision in detection of same channel by multi cognitive users and hidden node problems. Both these issues are solved by using hybrid approach of combination of cooperative decision, to overcome hidden node or the case when there is no common channel between the CU’s and contention-free approach, to solve the issues in contention mechanism, when same channel is selected simultaneously by multiple CU’s. This permits an effective DSA to Cognitive Users as well as maintain QoS for PU’s.
The rest of the paper is organized as follows. Section 2, discusses the present state of research and the gaps in this research area. Section 3, describes the system model covering the environmental scenario in Sect. 3.1, Proposed CR-i-MAC in Sect. 3.2 and numerical analysis of the proposed approach in Sect. 3.3. Simulative performance analysis of the proposed model is done in Sect. 4, discussing the simulation environment in Sect. 4.1 and Simulation results in Sect. 4.2. In Sect. 5 conclusion is drawn.
2 Present state of research and research gaps
Countless CR-MAC protocols have been proposed so far to overcome one or the other issues but concentrating on CR-MAC’s for multiple channels featuring hidden node problem or collision mechanism [9–30] are few remarkable researches.
Zhao et al. [9] proposed decentralized CR-MAC protocol based on the concept of partially observable Markov decision processes (POMDP). This concept not only reduces the system complexity but also enhance the system performance by ensuring synchronous hopping within the spectrum bands. In [10] Hsu et al. proposed a statistical channel allocation (SCA)-MAC protocol for decentralized CRNs based on CSMA/CA protocol, which providing minimum interference to PUs, as the negotiation of transmission parameters is done over the control channel before setting up link between the sender and receiver. In an other proposal Motamedi et al. [11], proposed distributed spectrum-agile MAC protocol, based on CSMA/CA protocol for dense networks with dynamic channel selection algorithm. Felegyhazi et al. [19] also used CSMA/CA concept with game theory approach. Complexity, impractical and instability are certain issue associated with game theories. All of the above systems have decentralized control, so hidden node problem exists in them. To solve this Cordeiro et al. [12] proposed Cognitive-MAC (C-MAC) based on sharing of information during the beaconing period, to solve hidden node problem and Rendezvous channel (RC) for coordination within the nodes, but increases system complexity. Chen et al. [13] proposed a cluster-based framework for CRN which have the ability to adapt logically, to the dynamic changing environment based on sharing by local common channels, Neighbour discovery and cluster formation. In [14] Jia et al. features, hardware constrained MAC (HC-MAC) protocol for efficient spectrum sensing, sharing and access decision for ad-hoc CRNs without any synchronization within the network, but suffers from hidden node problem and deafness. Su et al. [15] propose a cross layer design of MAC protocol for multi-channel with cooperation with spectrum sensing at physical layer and packet scheduling mechanism at MAC layer, using different transceivers for control channel and data channels, while in [17], Cognitive Radio EnAbled Multichannel (CREAM-MAC) protocol is proposed, to solved the hidden node and synchronization associated in [15] but traps into issue of more communication overheads.
In [16, 20, 25, 27, 30, 33, 34] all authors worked on multi-channel networks without common control channel (CCC) and solved the issues like channel saturation, multi-channel hidden problem and Denial of Service (DoS) [16] featuring, congested CRNs [20], decentralized CRNs whereas [25], focuses on minimum interference, channel access time and packet loss [27], named it as Concurrent Access MAC (CA-MAC) and [30] as Dynamic Common Control Channel-based Medium Access Control (DCCC-MAC) protocol for centralized CRNs. All have same ultimate goal of less interference, less delays and high throughputs but differ in their implementation. In [21, 29] proposed solution to hidden node problem in multi-channel CRN environments. Ke et al. in [21] used cooperative detection based time division multiple access (TDMA) approach named Multi-channel CR MAC (MCR-MAC) while Khatiwada et al. [29] used directional antenna for the same and named it as Multi-Channel MAC protocol for Directional Antennas (MCMDA). Lau et al. [24] proposed a Bi-directional CR MAC (Bi-MAC) protocol for easy negotiation and reserve bandwidth. Hamdaoui et al. [18], proposed Opportunistic Spectrum MAC (OS-MAC) for opportunistic sensing, accessing and sharing, and compared its performance with an Ideal-MAC protocol. Kahraman et al. in [22] proposed a Protection and Fairness oriented Cognitive Radio MAC protocol (PROFCR) for ad-hoc CRNs by completely eliminating the process of spectrum sensing. CUs take decisions for channel selection by calculating state variables of channels using only local information. This process reduces hand-overs count, thereby decreases the delays due to frequent channel shifting. The new concept of active and passive primary users is proposed by Dappuri et al. [26] in which PUs transmit their intention over the channel through beacons before actual transmission starts.
Lim et al. [23] proposed a Self-scheduling Multi-channel Cognitive MAC (SMC-MAC) protocol using single transceiver, allowing multiple cognitive users to transmit data over the sensed vacant channels by combining two cooperative channel sensing algorithms, Fixed Channel Sensing (FCS) and Adaptive Channel Sensing (ACS) along with slotted contention mechanism to exchange channel request information for self-scheduling. Pandit et al. [28] extended the work of Lim and proposed a novel distributed CRN with back-off algorithm in the Self-scheduled Multichannel Cognitive radio MAC (SMC-MAC) protocol for the contention solving among the cognitive users and hence, reserve the licensed channels for data transmission. This back-off algorithm allows the cognitive users to access the idle channel within the same cycle time during collision which was not possible in [23] explained in detail in Sect. 3. However this back-off algorithm introduces more overheads and delays making the system more complex and complicated. Moreover in this technique the contention slots are made flexible i.e. increase in collisions of cognitive users the contention slot increases, thereby decreasing the data transmission time of that Cycle time. In short, performance of the network degrades as the cognitive users increases or PUs activity increases. To overcome this a novel approach of using two transceivers is proposed, in which best quality channel according to the requirement of the cognitive user is chosen and sharing of information is passed over to other cognitive users which not only avoids simultaneous accessing of one channel by different cognitive users but also solves the problem of multi-channel hidden node problem.
3 System model
In this section the detailed overview of the system is discussed, covering the environment scenario, Proposed CR-i-MAC and its numerical analysis.
3.1 Environment scenario
Simulation environment of the network is kept as simple as possible to analysis the proposed CR-i-MAC as shown in Fig. 2. We are considering two types of networks, primary user network and cognitive user network. Primary user network is presumed to be as modern cellular network with \(P_\mathrm{ch}\) orthogonal channels and traffic is based upon Poission Distribution [32]. Cognitive users senses the idle primary channels \((P_\mathrm{ch})\) and opportunistically utilize those channel until required by the PUs. We are using MAC-layer sensing mechanism and assuming the sensing to be perfect i.e no false alarm and missed detection [35–37]. Cognitive user network is composed of cognitive user having two transceiver in full-duplex mode with SDR which allow the cognitive user/node to switch to the required channel. Two transceivers allows the CU to transmit and receive signal from different channel simultaneously, thereby allowing the node to transmit over one channel and at the same time listening to the other channel within the same cycle time discussed in next subsection. Accuracy of the system increases with the increase in sensing by each terminal as continuous monitoring of the primary channels detect the presence of PU. This restricts the use of primary channel by cognitive user when required by PU and maintains the QoS for PUs. Power consumption and complexity increases as the frequent sensing by each CU increase therefore the concept of sharing the sensed results with the other CU’s is used to limit the excessive sensing of channels by each terminal, which also provide a solution to hidden node problem.
3.2 Proposed CR-i-MAC
Whole process of CR-i-MAC is divided in three interval, Sensing & Sharing interval (Tss), Contention interval (Tc) and Transmission interval (Tt). Sensing & Sharing interval is quite similar to the sensing-sharing time-frame of [14, 23, 28]. Sensing of the channel and sharing of the sensed data to other CU’s within the network is done during the Tss interval. Decision for the appropriate channel according to the demand of the CU is done during the Tc time-frame, whereas the final data transmission from the source to destination over the pre-decided channel and its successful ACK (Acknowledgement) by the destiny in response to the error free delivery of data, is done during the Tt time-frame. To improve the performance of the system, Tss and Tc should be as small as possible so that the time-frame for Tt increases significantly. So in this proposed model, techniques to reduce Tss and Tc is used, so that the overall performance of the network is enhanced in terms of increased throughput and reduced delays, also the interference level is within the tolerable range (Table 1). All these three process constitutes one Cycle time, immediately after the receiving of ACK by the corresponding CU in the Tt interval, the next cycle starts and this goes on unless or until PU appears. Detailed description of each process is as follows:
3.2.1 Sensing and sharing (Tss)
Sensing is considered as the most vital part for cognitive radio networks (CRNs). To determine the performance of the network, accurate sensing and sensing-time are the essential parameters. In this proposed model sensing-time is considered and sensing is assumed to be perfect i.e. no false alarms or missed detections. Sensing issues related to false alarms and missed detections are discussed and solved in [36, 37]. So to improve the performance of the system, CU’s should sense as many primary channel as possible. Complexity, cost, power consumption and sensing-time are the factor directly associated with sensing [38]. In short it can be said that increased sensing increases the complexity, power consumption, cost and sensing-time of the system thereby degrading the performance of the overall network. So to balance this, trade-off needs to be maintained so that all the primary channel are sensed without increasing the system complexity, cost, power and sensing-time. This is done by cooperation within CU’s i.e sharing of sensed data by CU’s with other CU’s. To make clear understanding, network scenario with five Primary channels \((P_\mathrm{ch})\) and four CU’s is considered. Each CU’s is required to sense all the five \((P_\mathrm{ch})\), but in this proposed model, motive is to sense all the primary channels not an individual sensing of all primary channels by each CU.
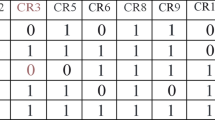
In this proposed model Sensing and Sharing Time-frame is similar to [14, 23, 28], which is divided in \((P_\mathrm{ch})\) slot which is equal to no. of Primary Channel present in the network and each slot is further divided into three sub-slots as shown in Fig. 3. CU’s randomly selects the \(`i'\) channel, \(1\le i \le P_\mathrm{ch}\) and senses during the 1st sub-slot and shares the sensed data over the control channel during the 2nd and 3rd sub-slot. The sharing of result is done using tone signal ‘0/1’. The sub-slot tones ‘0’ in 2nd and 3rd sub-slot i.e. ‘00’ for channel sensed-idle, ‘01’ for channel sensed-busy and ‘11’ for channel not-sensed as shown in Table 2. The not-sensed ‘11’ case is treated as busy channel in contention-time frame so that no errors occurs during the simulation process. Algorithm 1 in next sub-section shows the complete process of Sensing & Sharing Time-Frame.
3.2.2 Contention interval (Tc)
After the sensing and sharing of sensed data by the CU’s, the process of decision making i.e. the channel allocation by the CU’s is done, this takes place within the contention time-frame of the cycle time. This process is novel and completely different from other contention process discussed in the Sect. 2. In this process the Contention time-frame is divided into ‘M’ slots which are equal to no. of CU’s present in the network and no collision will occur while allocating the channels to the CU as shown in Fig. 4, while in [14, 23, 28] contention slots are dependent on Primary channels and is endangered to the problem of collisions of selecting same contention slot with different CUs.
To understand this a network model with four CU’s and five primary channels is considered. The sensed result by the CU’s during the Tss time interval is represented in Fig. 5. From this figure it can be seen that CU1 detects Ch1 and Ch2 as idle and all other channels as busy. Busy can be the case if the sensed result is busy or not-sensed as shown in Table 2. CU2 detects Ch2, Ch3 and Ch4 as idle, CU3 detects Ch1 and Ch3 as idle whereas CU4 detects Ch1 and Ch2 as idle. Ch5 is detected always busy, this may be the case of PU using this channel. Now firstly, the least common channel will be selected by the corresponding CU as in this case Ch4 is detected idle only by CU2, so Ch4 will be win case for CU2. Now the next least common channel i.e Ch3 will be considered. Ch3 is detected idle by CU2 and CU3, as Ch4 is already assigned to CU2 so Ch3 will be the win case for CU3. Now Ch1 and Ch2 are left with, so in this case the channel is allocated either randomly or according to the demand and requirement of the CU. Algorithm 2 in the next sub-section show the pseudo-code for Contention Time-Frame.
3.2.3 Transmission interval (Tt)
Immediately after the allocation of channels is done during the Contention Time-Frame the transmission of data packets from source to destination starts over the channel allocated during the Contention interval. After the successful delivery of data a corresponding Acknowledgement (ACK) is received by the source, confirming the end of error-free transmission as shown in Fig. 6. As described earlier the CU node is equipped with two Transceivers one for transmission and other for continuous monitoring of the PU activities. So, if during this transmission process PU emerges, CU vacant the Primary channel, the next cycle starts and resumes the transmission to the destination over the next allocated channel. Algorithm 3 in the next sub-section show the complete process of Transmission Interval.
3.3 Numerical Analysis
In this section numerical analysis of the proposed CR-i-MAC in context to the different parameters used for Cognitive Radio Network is discussed. The statistics for primary channels are based on [23, 32].
To detect the emergence of PU, continuous monitoring of PU channels need to be done, whereas continuous monitoring causes interference, so to enable continuous monitor without interfering with the PU to maintain QoS for both Primary as well as Cognitive Users, Maximum interference time needs to be analysed. Maximum interference time is the maximum time an CU is allowed to interfere with PU communication or simply we can say that time interval between the two calls as shown in the Fig. 7. \(T_i\) can also be considered as Cycle Time i.e. combined time-frame for sensing, Sharing, Contention and Transmission process.
According to Willkomm et al. [32] calculated the maximum interference time \((T_i)\) using the cumulative distribution function, if the call arrival process is exponential. Therefore the probability of interference P(i) that CU interfere with PU is expressed as follows:-
where, T is an inter-arrival time between two primary calls having exponential distribution rate of \(\lambda \). So, from Eq. 1, we can calculate \(T_i\) from as:-
This Maximum interference time \(T_i\) is considered as Cycle Time \(T_c\) hereafter. All the PU channels needs to be sensed with this Cycle Time \(T_c\). Considering, the total no. of Primary User channels are ‘\(P_\mathrm{ch}\)’ and all have same utilization \(\alpha \) and this can be considered as probability that PU channel is busy. If ‘\(N_\mathrm{Idle}\)’ be the total no. of channels to be idle, therefore the probability that channel is idle will follow binomial distribution [23] as follows:-
If ‘\(S_\mathrm{Idle}\)’ be the sensed idle channels by single CU from the total sensed channels ‘\(S_\mathrm{Max}\)’ Eq. 3 becomes:
The Average no. of sensed idle channel will be :-
Ratio of Idle channels i.e. Eq. 3 and Sensed-Idle channels i.e. Eq. 4, will drive the probability ‘\(\eta \)’ that an idle channel is sensed among the idle channels by an CU as:-
As the CUs senses the primary channels independently, the probability ‘P(j)’ that an idle channel is sensed by ‘jth’ CU among ‘\(M_\mathrm{CU}\)’ cognitive users follows the binomial distribution as:
Now from above equation Probability that an idle channel is not-sensed, ‘\(P_\mathrm{Not\hbox {-}sense}\)’ can be calculated as:
Therefore the Probability that an idle channel is sensed will be:-
Now the probability distribution of sensed idle channels, ‘\(S_\mathrm{Idle}\)’ from idle channels, ‘\(N_\mathrm{Idle}\)’ by each cognitive user can be calculated using Eqs. 4 and 9 as:
The average no. of sensed-idle channels by ‘\(M_\mathrm{CU}\)’ cognitive users will be:
After the sensing by each CU, the sensed results is further shared with the other CUs, to mitigate the problem of hidden channels or to speed up the sensing process. Algorithm 1 show complete process of sensing & Sharing Interval as discussed earlier in this section.

After sensing and sharing the sensed data within the ‘\(M_\mathrm{CU}\)’ cognitive users, the CU’s start competing to reserve the sensed-idle channels during the Contention Time-frame. In [23, 28] each CU randomly selects a contention slot from the total number of contention slots ‘M’ in the Contention intervals. Random allocation of channel to the CUs not only increase the system complexity and contention interval but also cause allocation of same contention slot to multiple CUs. The numerical analysis as shown in [23] is expressed as:
where, ‘s’ is the no. of CU that randomly selects the contention slot and ‘P(s)’ represents the probability of the same. ‘M’ are the total no. of contention slot therefore ‘1 / M’ will the probability of selecting each contention slot. If ‘\(s=1\)’ the successful allocation of contention slot is be expressed as:-
If variable, ‘t’ contains the value of successful CUs then its probability will be given as:-
The average number of successful CUs is calculated from (12) as:

Therefore the average no. of collided CUs will be:-
According to the [23, 28], the average number of successful CUs tends to increase as the number of contention slots increases as shown in Fig. 8. For successful allocation of contention slot to CU, minimum 100 to 200 contention slot are required. Increasing contention slots no doubt increases accuracy and reliability but at the same time increases complexity and delay. Moreover with the increased contention slots the Contention Interval increases which in turns reduces the transmission interval. So to overcome these problems, a completely new approach of allocating the channels to the cognitive user is applied, as discussed earlier in this Section. The pseudo-code for this contention approach is shown in Algorithm 2.
Immediately after the successful allocation of channels by the CUs, the transmission of data over the reserved primary channels during the contention interval starts. As the whole Cycle time is composed of Tss, Tc and Tt as:
Therefore ‘Tt’ can be expressed as:
To increase the Transmission ‘Tt’ Time-frame, ‘Tss’ and ‘Tc’ should be as less as possible. In this proposed CR-i-MAC, Contention free approach is used, which reduces the time-frame of both ‘Tss’ and ‘Tc’. Reducing the ‘Tc’ and ‘Tss’, an equivalent increase of ‘Tt’ time is measured, enhancing the performance of the system. Maximum achievable throughput is considered to be the throughput when all the sensed idle channels are utilized by available CUs. So, maximum achievable throughput can be computed as product of the average number of sensed idle channels ‘\(Avg[S_\mathrm{Idle}]\)’, time interval for transmission per Cycle time ‘(Tt / Tcycle)’ and data rate ‘R’. Therefore the maximum throughput is given as [23]:
In contention based approach, the throughput is calculated as [23] and [28] as:
where, ‘N’ are successful CUs and ‘\(Ch_\mathrm{Idle}\)’ are sensed-idle channels. In contention based approach, cases when channel is sensed idle even then, the channel is not allocated to the CU, due to collision during the contention interval. But in this CR-i-MAC, contention free approach is used (discussed earlier in this section) which overcomes this problem. The algorithm of the Transmission interval is shown in Algorithm 3. Therefore the throughput is only dependent on no. of sensed idle-channel as:

4 Performance evaluation
4.1 Simulation environment
To test the network, an artificial environment is created using Network Simulator (NS2). In this environmental set-up 6 nodes are used, out of which 2 are configured as PUs and four mobile Cognitive Users as shown in Fig. 9. PUs are configured to parameters similar to [39], with non-overlapping transmission range shown in Fig. 9, as Node 1 and Node 2, whereas Node 3, 4, 5 and 6 are Cognitive Users. Node 3 and 5 are in range of PU1 and Node 4 and 6 in range of PU2. System model is explain in detail in Sect. 3 and the simulation parameters used for the simulation are tabled under the Table 3.
The proposed CR-i-MAC is implemented based on IEEE 802.11 MAC [39], configured with cognitive capabilities using Cognitive Radio Cognitive Network (CRCN) patch, as build over environment based on NS2. 6 nodes are deployed over the network area of \(1000 \times 1000\) m\(^2\). Random node mobility is assigned with node speed varying from 0 to 2 m/s and random pause time 0 to 12 s. This proposed CR-i-MAC is tested over both shortest-path routing protocols like AODV/DSR and link-quality routing protocol like WCETT [40]. The performance of proposed CR-i-MAC is compared with various other existing CR-MACs. The motive is to check the performance of proposed CR-i-MAC using multiple radios and channels. Simulation is repeated by simulating the network environment with single and two interface node configuration. The network is tested and analysed with 1, 3, 5 channels per radio. The accuracy of the system is measure up-to 2 decimal values i.e. 1/100 of second. The average throughput, delay and interference with the PU is calculated as discussed earlier in previous section. The simulative results of all 100 value over a second is calculated and plotted as average throughput, delay and Interference.
4.2 Simulation results
For the fair and effective testing of the proposed CR-i-MAC, experimented simulation is done by using this proposed CR-i-MAC over both distance vector (AODV) and dynamic source routing (DSR) protocol and Link quality routing protocol (WCETT). In the simulation results, AODV/DSR protocols configured for multi channel CR is used and named as AODV and DSR respectively in the graphs.
In the first experiment the proposed CR-i-MAC is simulated with AODV, DSR and WCETT at 1 channel per PU. Fig. 10. shows the simulated average throughput in bytes per second over the period of time. As this experimental set-up is for single radio, the proposed CR-i-MAC performance equally well with all the routing protocols like AODV, DSR and WCETT. The overall average throughput is observed to be 37520 byte/s for WCETT, 38208 bytes/s for AODV and 38368 bytes/s for DSR. DSR protocol perform better for single channel low-mobile networks, therefore simulation shows marginally improved throughput. The average delay for the same first experimental set-up is plotted in Fig. 11 shown below. The overall average delay using DSR is 2.906 ms, AODV is 2.83 and 2.735 ms for WCETT. So, from the simulation result, it can be concluded that the proposed CR-i-MAC perform equally well with different types of routing protocol, making the proposed protocol universal friendly with any working environment.
Now to analyse the performance of the system over multi-channel network using single radio and two radio, the nodes of the network are configure with 1-interface and 2-interfaces per node. Total five channels per radio are made available and simulated for four different cases. Case 1 using SMC-MAC [23, 28] with back-off algorithm using 1-Radio, Case 2 using SMC-MAC with 2-Radio, Case 3 using Proposed CR-i-MAC with 1-Radio and Case 4 using proposed CR-i-MAC with 2-Radio. The average throughput is calculated from the trace file and plotted as shown in Fig. 12. The graph shows that the average throughput of the proposed CR-i-MAC doubles for two radios, this is due to the change in decision making during the contention slot ‘(Tc)’ of the Cycle-Time. As in this proposed CR-i-MAC, allocation of channel is made using the common channel available between the source and destination Cognitive User. This reduces the system complexity. The throughput of the systems depends upon the data rate and transmission time ‘Tt’ as discussed in previous section Eq. 21. Increased throughput, seen in Fig. 12 is due to reduced ‘Tc’, which significantly increases the ‘Tt’ time-frame.
This increased throughput shows the efficient utilization of all the available idle licensed channels by the cognitive users, in the absence of PUs. To maintain the QoS for PUs, Cognitive Users need to vacate the channel when required by the PU and shift to the other idle channel in the next Cycle time explained in details in Sect. 3. This process require continuous monitoring of the channels to detect the immediate emergence of PU. This continuous monitoring not only consume power but also cause interfere with the PU. So to maintain interference under the level of consideration, the monitoring of channels is done within the maximum interference time ‘\(T_i\)’. This is considered as the Cycle time, that is the time interval between two successive calls as discussed in detail in Sect. 3 Numerical Analysis computed in Eq. 2. The simulated results shows remarkable reduction in interference level in the proposed CR-i-MAC protocol. As there are two PU nodes, so interference on both the node is simulated and compared with the existing SMC-MAC [23] SMC-MAC with Back-off approach [28] as shown in Fig. 13. The average interference value observed over PU1 using proposed CR-i-MAC is 0.01 Watts, which is almost half to that of the SMC-MAC Protocol, which is 0.02 Watts. The spike show the PU activities Fig. 13a, c. While in PU2 case, marginal decrease in the interference vlaue is seen. More dense sensing interference, as marked in Fig. 13c, d is seen, as more frequent channel monitoring is done to maintain the QoS for PUs, without any increase in system complexity and delay.
To validate the performance of the proposed CR-i-MAC, comparative performance analysis with the various co-related CR MAC protocols, discussed in detail in Sect. 2. Various CR MAC’s based on multi-channel approach like C-MAC, HC-MAC, MCR-MAC, SMC-MAC and SMC-MAC with Back-off by [12, 14, 21, 23, 28] respectively, are simulated over common environment set-up having two primary nodes with five primary channels, four cognitive mobile node as described earlier in Fig. 9, and using WCETT as routing protocol. The simulation results are graphed in Fig. 14. C-MAC and SMC-MAC performs better when interference is negligible i.e. when PU activities or Cognitive Users are less, but with the increase in PU activity or dense networks the performance deteriorates extremely thereby making the system unstable for highly active or large Cognitive Radio Networks. As per Numerical Analysis in Sect. 3, with the increase in cognitive users the contention slots increases, which in turn increases Contention interval ‘Tc’ and thereby reducing the corresponding transmission interval ‘Tt’. From Eq. 20, throughput is directly proportional to ‘Tt’ time-frame, therefore, significant drop in average throughput is seen after 30 s. Whereas in the proposed CR-i-MAC contention free approach is used in which common channels between the two node is selected thereby consistent average throughput of 40 MB/s is seen throughout the simulation time as depicted in Fig. 14, thereby making the system stable and efficient for small as well as large networks.
Moreover with the increase in contention slot, the complexity of the system increases which adds additional delays. To simulate the delay, the start time \(T_\mathrm{start}\) by the source node and end time \(T_\mathrm{end}\) by the destination node is noted and difference between the \(T_\mathrm{end}\) and \(T_\mathrm{start}\) computes the delay as:
Average delay of the proposed CR-i-MAC with the same experimental set-up is plotted in Fig. 15. The delay for MCR-MAC is much high (i.e. 1.79 s) so, plotting it over the same graph is not possible therefore, its values are omitted. The overall average delay for C-MAC, HC-MAC, SMC-MAC, SMC-MAC with Back-off and proposed CR-i-MAC is 3.549, 12.697, 3.531, 2.874 and 2.596 ms respectively as shown in the Fig. 15.
5 Conclusion
In this paper Cognitive Radio Intelligent MAC (i-MAC) is proposed, which is based on hybrid approach of combination of cooperative decision (to overcome hidden node or the case when there is no common channel between the CU’s) and contention-free approach (to solve the issues in contention mechanism, when same channel is selected simultaneously by multiple CU’s). This permits an effective DSA to Cognitive Users as well as maintain QoS for PU’s. This proposed CR-i-MAC is tested in every critical case. Simulation results show that proposal works equally well in cases of single radio, but when used with two radios, multi-channel environment, throughput doubles. Under extensive simulation, comparative performance analysis of the proposed CR-i-MAC with the existing cognitive radio MAC’s is also done. C-MAC and SMC-MAC perform better for small cognitive radio networks, whereas the performance deteriorates extremely for large Cognitive Radio Networks thereby making the system unstable for dense networks. The proposed CR-i-MAC overcomes these limitations, and makes the system stable and efficient in term for both increased throughput and reduced delay. The proposed CR-i-MAC increases the network performance by 12.45 % in terms of overall throughput, whereas the delay is decreased by 26.48 %.
References
Mitola III, J. & Maguire, G. Q., Jr. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6(4), 13–18. doi:10.1109/98.788210.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220. doi:10.1109/JSAC.2004.839380.
FCC spectrum policy task force. (2008). Report of spectrum efficiency working group. Second report and order, Federal Communications Commission, ET-Docket 04-186 and 02-380, Adopted November 4, 2008. Released November 14, 2008.
Akyildiz, I. F., Lee, W. Y., Vuran, M. C., & Mohanty, S. (2006). Next generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks Elsevier, 50(13), 2127–2159. doi:10.1016/j.comnet.2006.05.001.
Singh, J. S. P., Singh, J., & Kang, A. S. (2013). Cognitive radio: State of research domain in next generation wireless networks—A critical analysis. International Journal of Computer Application, 74(10), 1–9. doi:10.5120/12918-9741.
Akyildiz, I. F., Lee, W. Y., & Chowdhury, K. R. (2009). CRAHNs: Cognitive radio ad hoc networks. Ad Hoc Networks Elsevier, 7(5), 810–836. doi:10.1016/j.adhoc.2009.01.001.
Cormio, C., & Chowdhury, K. R. (2009). A survey on MAC protocols for cognitive radio networks. Ad Hoc Networks Elsevier, 7(7), 1315–1329. doi:10.1016/j.adhoc.2009.01.002.
Akyildiz, I. F. (2005). A survey on wireless mesh networks. IEEE Communication Magazine, 43(9), S23–S30. doi:10.1109/MCOM.2005.1509968.
Zhao, Q., Tong, L., Swami, A., & Chen, Y. (2007). Decentralized cognitive MAC for opportunistic spectrum access in ad hoc networks: A POMDP framework. IEEE Journal on Selected Areas in Communications, 25(3), 589–600. doi:10.1109/JSAC.2007.070409.
Hsu, A. C. C., Wei, D. S. L., & Kuo, C. C. J. (2007). A cognitive MAC protocol using statistical channel allocation for wireless ad-hoc networks. IEEE Wireless Communications and Networking Conference (pp. 105–110). doi:10.1109/WCNC.2007.25.
Motamedi, A., & Bahai, A. (2007). MAC Protocol design for spectrum-agile wireless networks: Stochastic control approach. In 2nd IEEE International Symposium on New Frontier in Dynamic Spectrum Access Networks (pp. 448-451). doi:10.1109/DYSPAN.2007.65.
Cordeiro, C., & Challapali, K. (2007). C-MAC: A cognitive MAC protocol for multi-channel wireless networks. In 2nd IEEE International Symposium on New Frontier in Dynamic Spectrum Access Networks (pp. 147–157). doi:10.1109/DYSPAN.2007.27.
Chen, T., Zhang, H., Maggio, G. M., & Chlamtac, I. (2007). CogMesh: A cluster-based cognitive radio network. in 2nd IEEE International Symposium on New Frontier in Dynamic Spectrum Access Networks (pp. 168-178). doi:10.1109/DYSPAN.2007.29.
Jia, J., Zhang, Q., & Shen, X. (2008). HC-MAC: A hardware-constrained cognitive MAC for efficient spectrum management. IEEE Journal on Selected Areas in Communications, 26(1), 106–117. doi:10.1109/JSAC.2008.080110.
Su, H., & Zhang, X. (2008). Cross-layer based opportunistic MAC protocols for QoS provisionings over cognitive radio wireless networks. IEEE Journal on Selected Areas in Communications., 26(1), 118–129. doi:10.1109/JSAC.2008.080111.
Kondareddy, Y. R., & Agrawal, P. (2008). Synchronized MAC protocol for multi-hop cognitive radio networks. IEEE International Conference on Communications (pp. 3198–3202). doi:10.1109/ICC.2008.602.
Su, H., & Zhang, X. (2008). CREAM-MAC: An efficient cognitive radio-enabled multi-channel MAC protocol for wireless networks. IEEE International Symposium on World of Wireless, Mobile and Multimedia Networks (pp. 1–8). doi:10.1109/WOWMOM.2008.4594853.
Hamdaoui, B., & Shin, K. G. (2008). OS-MAC: An efficient MAC protocol for spectrum-agile wireless networks. IEEE Transactions on Mobile Computing, 7(8), 915–930. doi:10.1109/TMC.2007.70758.
Flegyhzi, M., Cagalj, M., & Hubaux, J. P. (2009). Efficient MAC in cognitive radio systems: A game-theoretic approach. IEEE Transactions on Wireless Communications, 8(4), 1984–1995. doi:10.1109/TWC.2009.080284.
Joshi, G. P., Kim, S. W. & Kim, B. S. (2009). An efficient MAC protocol for improving the network throughput for cognitive radio networks. In 3rd International Conference on Next Generation Mobile Applications, Services and Technologies (pp. 271– 275). doi:10.1109/NGMAST.2009.38.
Ke, Y., & Yoo, SJ., (2009). MCR-MAC: Multi-channel cognitive radio MAC protocol for cooperative incumbent system protection in wireless ad-hoc network. In 1st International Conference on Ubiquitous and Future Networks (pp. 6–11). doi:10.1109/ICUFN.2009.5174275.
Kahraman, B., & Buzluca, F. (2010). Protection and fairness oriented cognitive radio MAC protocol for ad hoc networks (PROFCR). European Wireless Conference (pp. 282–287). doi:10.1109/EW.2010.5483429.
Lim, S., & Lee, T.-J. (2011). Self-scheduling multi-channel cognitive radio MAC protocol based on cooperative communication. IEICE Transaction on Communication, 94(6), 1657–1668. doi:10.1587/transcom.E94.B.1657.
Lau, L. C., Lin, C. C., & Wang, S. Y. (2011). Bi-directional cognitive radio MAC protocol for supporting TCP flows. IEEE Vehicular Technology Conference (pp. 1–5). doi:10.1109/VETECF.2011.6092891.
Hernandez-Guillen, J., Colina, E. R., Jimnez, R. M., Chalke, M. P. (2012). CRUAM-MAC: A novel cognitive radio MAC protocol for dynamic spectrum access. In IEEE Latin-America Conference on Communications (pp. 1–6). doi:10.1109/LATINCOM.2012.6505997.
Dappuri, B., Venkatesh, T. G., & Thomas, V., (2013). MAC protocols for cognitive radio networks with passive and active primary users. In International Conference on Wireless Communications & Signal Processing (WCSP) (pp. 1–7). doi:10.1109/WCSP.2013.6677245.
Timalsina, S. K., Moh, S., Chung, I., & Kang, M. (2013). A concurrent access MAC protocol for cognitive radio ad hoc networks without common control channel. EURASIP Journal on Advances in Signal Processing, 69, 1–13. doi:10.1186/1687-6180-2013-69.
Pandit, S., & Singh, G. (2015). Backoff algorithm in cognitive radio MAC protocol for throughput enhancement. IEEE Transactions on Vehicular Technology, 64(5), 1991–2000. doi:10.1109/TVT.2014.2334605.
Khatiwada, B., & Moh, S. (2015). A novel multi-channel MAC protocol for directional antennas in ad hoc networks. Wireless Personal Communications, 80(3), 1095–1112. doi:10.1007/s11277-014-2074-7.
Thilina, K. M., Hossain, E., & Kim D. I. (2015). DCCC-MAC: A dynamic common control channel-based MAC protocol for cellular cognitive radio networks. IEEE Transactions on Vehicular Technology (in press). doi:10.1109/TVT.2015.2438058.
Wang, J., & Huang, Y. (2010). A cross-layer design of channel assignment and routing in cognitive radio networks. In 3rd IEEE International Conference on Computer Science and Information Technology 7 (pp. 542–547). doi:10.1109/ICCSIT.2010.5564800.
Willkomm, D., Machiraju, S., Bolot, J., & Wolisz, A. (2009). Primary user behavior in cellular networks and implications for dynamic spectrum access. IEEE Communications Magazine, 47(3), 88–95. doi:10.1109/MCOM.2009.4804392.
Chehata, A., Ajib, W., & Elbiaze, H. (2011). An on-demand routing protocol for multi-hop multi-radio multi-channel cognitive radio networks. Wireless Days IEEE-IFIP (pp. 1–5). doi:10.1109/WD.2011.6098215.
De Couto, D. S. J., Aguayo, D., Bicket, J., & Morris, R. (2003). A high-throughput path metric for multi-hop wireless routing. Wireless Networks Springer, 11(4), 419–434. doi:10.1007/s11276-005-1766-z.
Singh, J. S. P., Singh, J., Kang, A. S., & Rai, M. K., (2013). Cooperative fusion sensing technique for cognitive radio: An efficient detection method for shadowing environment. International Conference on Computing Sciences, WILKIES 100 Elsevier, 2 (pp. 70–79).
Singh, J. S. P., Rai, M. K., Singh, J., & Kang, A.S. (2014). Trade-off between AND and OR detection method for cooperative sensing in cognitive radio. IEEE Advance Computing Conference (IACC) (pp. 395-399). doi:10.1109/IAdCC.2014.6779356.
Singh, J. S. P., Singh, R., Rai, M. K., Singh, J., & Kang, A. S. (2015). Cooperative sensing for cognitive radio: A powerful access method for shadowing environment. Wireless Personal Communications, 80(3), 1363–1379. doi:10.1007/s11277-014-2088-1.
Salim, S., Moh, S., & Chung, I. (2013). Transmission power control aware routing in cognitive radio ad hoc networks. Wireless Personal Communications Springer, 71(4), 2713–2714. doi:10.1007/s11277-012-0966-y.
IEEE standard for Wireless Local Area Network, MAC and PHY Layer Specifications, STD 802.11-2007. www.iith.ac.in/~tbr/teaching/docs/802.11-2007.
Draves, R., Padhye, J., & Zill, B. (2004). Routing in multi-radio, multi-hop wireless mesh networks. In Proceedings of 10th International Conference on Mobile computing and networking, MobiCom’04 (pp. 114–128). doi:10.1145/1023720.1023732.
Cognitive Radio Cognitive Networks [Available Online] http://faculty.uml.edu/Tricia_Chigan/Research/helpv4.htm. Accessed On 12 February 2015.
Network Simulator-2 (ns2). http://www.isi.edu/nsnam/ns/. Accessed 12 Feb 2015.
Acknowledgments
First author is highly thankful to Dr. Davinder Pal Sharma, DSP Research Lab, University of West Indies, Dr. B.P. Patil, Prof. & Head, Army Institute of Technology, Pune and Dr. Sukhjeet Singh for providing useful information as well as critical remarks. The valuable help rendered by A.S. Kang, Assistant Professor, Department of Electronic Technology, Panjab University, Chandigarh, India and Rajwinder Singh, Assistant Professor, BCET Gurdaspur, India are also acknowledged. Gulshan Kumar, Assistant Professor and Sundas Sheikh, Research Fellow are also acknowledged for providing valuable guidance to improve the appearance and quality of the paper.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Singh, J.S.P., Rai, M.K. Cognitive radio intelligent-MAC (CR-i-MAC): channel-diverse contention free approach for spectrum management. Telecommun Syst 64, 495–508 (2017). https://doi.org/10.1007/s11235-016-0188-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-016-0188-9