Abstract
Wireless body area network (WBAN) is a wireless communication technology which facilitates the medical staff to remotely monitor and provide accurate treatment to patients. Wireless body sensors are resource constrained, and consequently, an efficient routing protocol is vital in the design of these networks. Although many protocols have been presented for the routing in WBANs, sufficient features have not been adequately addressed in these techniques. Moreover, parameters of these protocols are manually set and remain constant in all applications, i.e., no automatic tuning procedure is applied to tune the protocol based on the application requirements. To overcome these drawbacks, we introduce a swarm intelligence multi-objective fuzzy protocol (named SIMOF), as a tunable routing protocol in WBANs. The SIMOF comprises two phases, namely fuzzy inference system (FIS) and automatic rule tuning using whale optimization algorithm (WOA). The FIS utilizes a multi-objective fuzzy inference system based on residual energy, distance, reliability, bandwidth, temperature, path loss, and estimated energy consumption, to select proper relay nodes, considering IEEE 802.15.6 standard. To achieve the best performance in the SIMOF, Mamdani rules of the FIS are automatically tuned using WOA. Simulations over three WBANs demonstrate the superiority of the proposed SIMOF routing protocol against the existing techniques in terms of the stability period, path loss, reliability, and hotspot temperature.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Recent technological advancements in wireless communications have empowered the development of remote health monitoring systems such as wireless body area networks (WBANs) [1]. WBAN is an emerging wireless communication technology which facilitates medical staff to revolutionize mobile healthcare via the real-time monitoring and analysis of medical data [2]. Typically, WBANs are used to monitor abnormalities in the human body through measuring physical parameters such as electrocardiograph (ECG), electroencephalograph (EEG), and electromyograph (EMG), to measure the electrical activity of the heart, brain, and muscles [3]. These parameters are sensed and collected using a set of tiny low-power, light-weight, wearable, heterogeneous sensors implanted in or attached on the human body [4]. Each sensor node is capable of sensing the local data including physiological and non-physiological information, and then, transmitting the collected data through wireless links to a gateway or base station (sink), e.g., medical center, for further processing [5].
WBANs comprise a set of bio-sensors and a sink node on the human body. According to network architecture, WBANs can be categorized into in-body (implanted) and on-body (wearable) WBANs [6]. In in-body WBANs, the implanted sensor nodes and the sink are able to communicate with each other, while the wearable sensors sense the vital parameters and send them to the sink. Moreover, wireless sensors in WBANs can be categorized into physiological, biokinetic, and ambient nodes [7]. Physiological sensor nodes collect physical information such as ECG, EEG, EMG, blood pressure, blood oxygen, and glucose. Biokinetic sensors measure acceleration and rotation of the movements in the human body. Ambient sensor nodes gather environmental conditions such as vibration, light, and pressure [8]. Generally, WBANs cover both medical and non-medical applications [9,10,11]. Medical applications include implanted and wearable applications like sleep stage control, diabetes, asthma, and cardiovascular monitoring, while non-medical applications include entertainment, consumer electronics, lifestyle, and aerospace applications [3].
Because of the constraints of the body sensors in terms of the limited power supply, energy efficiency is a main factor which has a major impact on the stability period and network lifetime of the WBANs [12]. Among various routing protocols in WBANs, cluster-based techniques have been widely used to improve energy efficiency and load balancing [13]. In clustering protocols, different sensors are grouped into separate clusters, each of which has a cluster head (CH). These methods can be distinguished by how proper CHs (i.e., relay nodes) are selected, and proved to be more suitable than temperature-aware and cross-layer methods, due to the benefits of energy efficiency and load balancing [14]. It has proved that clustering (i.e., relay node selection) in WBANs is a NP-hard problem [4], and consequently, heuristic or metaheuristic clustering methods can be effectively applied. Generally, existing cluster-based routing protocols suffer from the following drawbacks:
-
Controllable parameters of the majority of the existing protocols are manually set and remain constant for all applications, i.e., no automatic tuning is applied based on the application specifications.
-
Real-time routing capable of responding online routing requests is of great importance in WBANs that deal with the patients' health. However, utilizing iteratively based metaheuristic algorithms doesn’t make sense, as they cause delay in the data transmission phase.
-
The heating of bio-sensors is an important issue which should be taken into account. When a node is continuously selected as a forward node, it causes overheat and will have adverse effects on the patient's body. However, most routing protocols have not addressed this issue.
To overcome the mentioned drawbacks of the existing methods, we propose a combined swarm intelligence multi-objective fuzzy system (named SIMOF). It comprises a fuzzy inference system (FIS) and a swarm intelligence algorithm based on whale optimization algorithm (WOA). There are several FIS models in literature which have been utilized to solve distinct engineering problems [15,16,17,18,19]. In this paper, we utilize a FIS based on Mamdani model. Unlike existing metaheuristics in wireless sensor networks (WSNs) and WBANs [20,21,22], in which the routes for online requests are generated by the simple heuristics and/or time-consuming metaheuristics, SIMOF utilizes a real-time FIS for the online routing, while WOA is utilized to tune the controllable parameters of the SIMOF in an offline preprocessing step. The main contributions of the paper can be listed as follows:
-
Developing a combined swarm intelligence multi-objective fuzzy model (named SIMOF) as an application-specific routing protocol for WBANs. It combines online routing based on FIS and offline tuning based on WOA, to benefit from the advantages of both techniques, i.e., fast speed of FIS in real-time routing and high precision of metaheuristics in hyper-parameter tuning [23, 24].
-
Presenting a multi-criteria FIS for the relay node selection in a real-time scheme utilizing various features of nodes and links including residual energy, distance, reliability, bandwidth, temperature, path loss, and energy consumption.
-
Utilizing WOA to obtain the optimal Mamdani fuzzy rules within FIS in an offline procedure. The fitness function of the WOA is considered according to the application requirements, e.g., network lifetime, reliability, delivery ratio, and hotspots.
-
Applying the SIMOF protocol as well as some existing heuristic and metaheuristic protocols for routing in three WBAN benchmark instances.
The rest of the paper is organized as follows: Sect. 2 reviews the existing techniques in literature. Section 3 presents the network model. Section 4 introduces the online SIMOF routing protocol. The offline tuning process using WOA is presented in Sect. 5. Simulation results are provided in Sect. 6, and finally, the paper would be concluded with some suggestions for the future works in Sect. 7.
2 Literature review
Although WBANs and WSNs share many same challenges, there are functional differences between them which should be properly addressed when designing a WBAN. Generally, routing protocols in WBANs can be classified into cross-layer, temperature-aware, cluster-based, delay-tolerant, and quality of service (QoS) techniques [4]. These approaches are discussed in the following.
2.1 Existing methods
2.1.1 Cross-layer approaches
These techniques compound different network layers rather than utilizing only one layer. Cascade information via control access with distributed assignment (CICADA) [25] and wireless autonomous span tree (WASP) [26] are two cross-layer routing protocols. These approaches provide energy efficient routing solutions with high quality in delay and throughput. However, these protocols have some drawbacks for WBANs, as the load is not properly distributed among all nodes within the network, which results more energy holes. These protocols cause extreme computational complexity and overhead for tiny resource-constrained wireless body sensors. Moreover, the performance of these protocols is not guaranteed when it faces with body movements and high path loss transmissions [27].
2.1.2 Temperature-aware approaches
Radio communications via wireless links generate electrical and magnetic fields, which increase temperature of the human body. However, it can be partially alleviated using traffic control methods, reducing the power of radio communications, and distributing the loads over different nodes/links. Thermal aware routing algorithm (TARA) [28] tries to find routing solutions to forward data packets away from hotspot zones. Adaptive least temperature routing (ALTR) [29] is an extension of TARA, in which the recently visited sensors are avoided to minimize repetitious hops. In this method, the shortest path among accessible paths is selected to reduce the total dissipated energy. Ahmed et al. [30] proposed an energy-efficient congestion mechanism based on TARA (EOCC-TARA) via spider monkey optimization algorithm in software-defined network (SDN) networks. It considers energy level, congestion, and temperature, to adaptively select proper relay nodes. However, path loss and reliability were not under consideration.
Javaid et al. [31] developed mobility-supported adaptive threshold temperature energy-efficient multi-hop routing protocol (M-ATTEMPT) to find paths to route data away from hotspot areas. For each routing request, the protocol selects the shortest path with the least hop count among all accessible paths. If there are several routes with the same number of hops, the route with the minimum energy dissipation is chosen. In the hotspot cases when the temperature of a node violates a threshold, the hotspot link is replaced with an alternative path. The main drawback of M-ATTEMPT is that it doesn’t construct any alternative path if a sensor dies. Moreover, the relay nodes are selected based on data rate, while residual energy of nodes is not under consideration. To reduce the mentioned drawbacks of M-ATTEMPT, Ahmad et al. [32] presented reliability enhanced version of M-ATTEMPT (named RE-ATTEMPT), utilizing multi-hop routing to select shortest path to the sink. If a designed routing solution is not accessible, another route is selected to ensure achieving a reliable transmission. This protocol avoids unnecessary traffics because of using the minimum number of relay nodes. Although temperature-aware protocols are effective in the case of implanted WBANs, the procedure of hotspot detection causes more computational complexity which results more energy consumption [33]. Furthermore, these protocols don’t pay attention to the lifetime and reliability [34].
2.1.3 Cluster-based approaches
These methods have proved to be more suitable than the temperature-aware and cross-layer methods due to their energy efficiency and load balancing [35]. Watteyne et al. [36] proposed a clustering technique, namely Anybody, which randomly selects relay nodes utilizing a self-election strategy. Each sensor at every round can decide about its role to be or not a relay node in a fully distributed manner. Although Anybody distributes loads among all nodes, the relative position of nodes, reliability, path loss, and energy consumption are not under consideration. Tauqir et al. [37] presented a distance aware relaying energy-efficient (DARE) method, which builds a heterogeneous WBAN comprising some relay nodes through a multi-hop routing mechanism. In this method, quality of links and path loss are not considered [38].
Nadeem et al. [39] introduced a stable increased multi-hop protocol for link efficiency (SIMPLE). At every round, the nodes with higher energy and minimum distance are selected as relay nodes. The former is considered to balance the energy consumption among all sensors, while the later ensures achieving the maximum throughput. Although SIMPLE obtains better lifetime and throughput than M-ATTEMPT, path loss, mobility, and hotspot are not under consideration, i.e., the same node may forward the gathered data of all source nodes. Javaid et al. [40] presented improved SIMPLE (IM-SIMPLE), considering mobility and throughput. In this method, the sink selects proper relay nodes, and other sensors send their data packets to the selected relay nodes according to time division multiple access (TDMA) scheduling. The main drawback of IM-SIMPLE is to select the nearest node to the sink several times, which leads to depletion of the energy of such node rapidly [41].
Ha [42] developed even energy consumption backside routing (EECBR) to extend the network lifetime and enhance the energy efficiency. In this method, different sensors are placed at backside and frontside of the body. If both transmitter and receiver are located at the same side of the human body, the communication type is line of sight (LOS); otherwise, it is considered as non-line of sight (NLOS). Evolutionary multi-hop routing protocol (EMRP) [4] is another clustering protocol, which utilizes an evolutionary algorithm to achieve an optimal routing protocol considering residual energy, distance, path loss, and dissipated energy, to select proper cluster heads. Ullah et al. [3] presented an energy reliable routing scheme (ERRS) to enhance reliability and lifetime of WBANs. It includes cluster head selection and cluster head rotation.
Shunmugapriya and Paramasivan [43] presented a fuzzy-based relay node selection (FbRNS) as a reliable energy-efficient routing protocol for WBANs. In this protocol, the routing scheme is constructed based on forwarding packets via the relay nodes, while two fuzzy variables are taken into account for the relay node selection. The first fuzzy variable is distance, which is estimated based on the received signal strength indication (RSSI). The second fuzzy variable is direction, which is estimated based on the MUSIC algorithm. These two fuzzy variables are given as the inputs of the fuzzy inference system to generate the fuzzy rules in selecting the relay nodes. However, it doesn’t take into account load balancing, path loss, and hotspot problem. Combined fuzzy firefly algorithm and random forest (FFA-RF) [44] is a hybrid metaheuristic-machine learning method for the proper cluster-based routing. In this method, a fuzzy firefly algorithm is used to collect a comprehensive dataset from various WSN applications to train the ensemble learning model based on random forest. After training of the random forest, it is used as an online routing protocol for the cluster head selection.
2.1.4 Delay-tolerant approaches
Umer et al. [45] presented hybrid rapid response routing (HRRR) protocol, in which critical data packets should be transmitted with the minimum allowable delay. It has also proved to be able of efficiently conserve the dissipated energy of nodes. However, load balancing and packet overheads have not been taken into account in this protocol. Mehmood et al. [46] utilized cooperative communication network coding (CCNC) to efficiently improve delay-tolerant, throughput, and maximize the network lifetime. However, the use of cooperative communication in the CCNC protocol has its own adverse effects of increased computational complexity and processing overhead. Dharshini and MonicaSubashini [47] presented a delay-aware routing protocol named cantor pairing lightweight key generation (CPLKG) to balance between energy efficiency and performance measures including packet delivery ratio, throughput, and end-to-end delay. Karunanithy and Velusamy [48] developed an edge device data collection protocol (named MEVPS) to alleviate the congestion problem in WBANs and minimize latency in emergency data packet delivery. They utilized an ant colony algorithm to find the minimum edge-shared vertex path between each source node to the sink.
2.1.5 QoS-based approaches
QoS techniques comprise distinguished modules to consider different QoS metrics, e.g., energy efficiency, reliability, and delay. Energy peering routing (EPR) [49] and QoS peering routing reliability-sensitive data (QPRRSD) [50] are common protocols in this category. Dhanvijay and Patil [22] presented a QoS effective protocol (QoSEP) provisioned WBANs for the effective routing of the critical packets to the destination node. To improve the quality in service offered, they applied an ant colony optimization algorithm for the routing of critical data packets, to find the shortest paths with low energy consumption, low delay, and high throughput. Cicioglu and Calhan [5] proposed energy-efficient and SDN-enabled routing (ESR-W) utilizing fuzzy-based Dijkstra algorithm, to find the proper path between WBAN users. In this method, signal per noise, energy level, and hop count are used to design the most appropriate path between users. Based on the results, ESR-W achieved acceptable results in terms of the packet delivery rate, throughput, delay, and energy efficiency. Kamruzzaman and Alruwaili [51] presented an energy-efficient sustainable WBAN using network optimization method, to prolong the network lifetime, while an adaptive scheduling protocol was integrated for the energy efficiency to enhance the network’s reliability and QoS. Although QoS-based protocols have high data delivery, high reliability, and low delay, they boost high computational complexities to manage different QoS modules. Moreover, prolonging the network lifetime is not guaranteed in these methods.
2.2 Our contributions against the existing methods
Proper design of a routing protocol is highly dependent on the type of application. Although various routing protocols have been presented for WBANs, important issues of energy-efficiency, data delivery, reliability, path loss, and temperature (hotspot problem) have not simultaneously been addressed in most of these techniques. Moreover, controllable parameters of the existing routing protocols were manually set and remain constant for all types of applications. As bio-sensor nodes in WBANs are implanted in or attached on the human body, it is of utmost importance to make the underlying tissue temperature under control. However, most studies have not addressed the hotspot problem. Generally, WBANs need agile and real-time routing solutions. Although the existing metaheuristic protocols outperform crisp and fuzzy heuristics in the aspect of solution quality, the use of metaheuristics for directly route construction doesn’t make practical sense as they are time-consuming methods which boost overhead and delay in critical data transmission. In contrast, heuristics are simple-to-use protocols with speedy running time, but they do not effectively explore the whole search space.
To simultaneously benefit from the advantages of both heuristic- and metaheuristic-based routing techniques and alleviate their drawbacks, we introduce a combined model utilizing online routing using a FIS heuristic method and offline tuning using a WOA-based metaheuristic algorithm. Our motivation is to simultaneously gain with the advantages of both methods, i.e., high speed of the fuzzy systems in real-time route construction and high quality of metaheuristics in offline hyperparameter tuning. The proposed FIS model is able to quickly select a relay node for each of normal and critical data routing requests, based on different variables including residual energy, distance, reliability, bandwidth, path loss, temperature, and energy consumption. To achieve the best performance of FIS, WOA is performed in an offline procedure only once before applying the SIMOF for each new application, to adaptively adjust it according to the application requirements.
3 System model
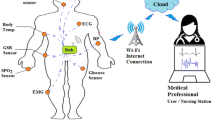
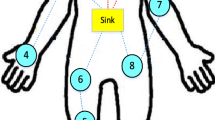
The network architecture is shown in Fig. 1. All nodes are implanted in or attached on the human body, to gather different information form the body. There is one sink placed at the waist. Each sensor is aware of its location at every time. All communications are done through wireless links. At every round, the network operates in setup and steady-state phases. In setup phase, the routes are constructed using the SIMOF protocol at sink, and then, sink informs all sensors about their routes. In steady-state phase, each sensor sends its local data to the sink through one- or two-hop communication. As seen in Fig. 1, we consider a cluster-based routing mechanism, i.e., single-hop communication for the relay (cluster head) sensors and two-hop communication for source (member) sensors; these rules may be changed from a round to another.
3.1 Energy model
Because of the limited energy resources of sensors in WBANs, efficient energy management has a major impact to maximize the network lifetime. Unlike free-space communication in classical WSNs with path loss exponent of 2 (i.e., η = 2), because of the effects of communications through the human body in WBANs, η is considered as 3–4 for LOS and 5–7 for NLOS [42]. The dissipated energy for each node n at every round due to radio reception and transmission of l-bit data packet can be formulated according to Eqs. (1) and (2), respectively.
where l is the reception/transmission data packet size (in bits), d is the Euclidean distance from the transmitter to the receiver (in meters), ETE and ERE are the dissipated energy in the electronic circuits of the receiver and transmitter, respectively (joule per bit), and Eamp is the dissipated energy of amplifier at the transmitter (joule per bit per meters powered by η).
It should be emphasized that the energy consumption for a node in each round consists of four parts including the TX state, RX state, sleep state, and the dissipated energy to complete the state transition [52]. However, in the transceiver energy consumption model in Eqs. (1) and (2), we did not consider a particular synchronization scenario where sensor nodes are active during a particular duty cycle, after which the transceiver is turned off to save energy. The model depicted above is a simple model used in [3, 4, 12, 39, 40, 53, 54], which only considers the energy consumption due to radio reception and transmission (TX and RX), as the energy consumption of the model mostly depends on the functioning time during which the model is in active model.
3.2 Path loss model
Path loss is the reduction in the power density of the electromagnetic waves. It represents the attenuation of the signal between the transmitter and receiver nodes, which is measured in decibels (dB) [39]. It can be expressed as the difference between the transmitted signal power at the transmitter node and that of received at the receiver node [55], as follows:
where d0 is the reference distance, f is frequency, and c is light speed. Moreover, PL0 is the path loss at d0 which can be calculated as follows:
Because of different postures of body due to its movements, variations in the packet forwarding may be obtained. To take this effect into account, a shadowing factor is added to model it when the path loss deviates from the mean value. To achieve this purpose, the path loss formula can be revised considering the shadowing factor according to Eq. (5):
where shadowing factor Xσ can be derived as a Gaussian-distributed random number, considering zero mean and standard deviation of σ.
3.3 Link reliability model
Appropriate link reliability increases the network reliability and avoids throughput degradation [56]. Reliability of the link between transmitter node i and receiver node j can be expressed as the ratio of the number of successfully received packets at node j to the number of transmitted data packets from node i [57]. In many applications, it is of utmost importance to reduce the packet loss probability in the connection path from the source to the destination (i.e., sink). The higher reliability of the links within a path, the less packet loss [37]. Reliability of the full path from source node n to the sink can be expressed as the multiple of the link reliabilities of all links within the full path, as follows:
where R(i,j) is the reliability of link (i,j) and Ln,sink is the set of links within the full path from node n to the sink.
3.4 Thermal model
Temperature of a sensor node implanted in or attached on the body significantly impacts the underlying tissue temperature. In WBANs, there are different reasons to increase the temperature of the tissue, which not only may result in tissue damage, but also can generate the hotspot problem which reduces the network stability and lifetime [57]. Generally, there are two main heating sources that cause the heating of the surrounding tissue of the sensor nodes: radiation from the sensor antenna and power consumption by the sensor circuitry [58]. These heating sources are described in the following.
To express the amount of the absorbed radiation by the tissue per unit of its mass, specific absorption rate (SAR) is used [59]. It is expressed according to the tissue conductivity and density and the induced electromagnetic field of radio frequency (RF) wave spectrum. Based on the distance from the antenna (near field or far field), SAR can be calculated as follows:
where dnf = λ/2π is the threshold distance for the near field radiation, λ is the wavelength of the RF, R is the distance between the antenna and the absorption point, σ is the medium conductivity, μ is the permeability, ω is the frequency of the RF power supply, ρ is the mass density, ε is the relative permeability, I is the sinusoidal drive current, and dl is the length of short conducting wire of the antenna. By assuming omnidirectional radiation pattern on the 2D tissue plane, sinθ = 1. Moreover, γ is the propagation constant which is expressed as γ = α + jβ, where α and β can be calculated according to Eqs. (8) and (9), respectively [58, 60].
The dissipated power by the sensor circuit also increases the temperature. It can be expressed as the power consumption density Pc, i.e., the ratio of the dissipated power by the sensor circuit to the sensor volume [61]. Subject to these heating sources, the underlying tissue temperature of the sensor node and its surrounding area may be raised. Utilizing finite-difference time-domain (FDTD) model [28], the body tissue is discretized into small grids. Accordingly, the temperature of a sensor at grid (i,j) at round r can be approximately estimated as a function of the temperature of grid (i,j) at the previous round r-1, radiation from the sensor antenna, fixed body temperature Tb, power consumption by the sensor circuitry, and the temperature of the neighbor grids at the previous round. It can be formulated as follows:
where K is the tissue thermal conductivity, Cp is the specific heat of the tissue, b is the blood pressure perfusion, δs is the step size of the discretized grids, and δt is the time step.
At every round, there are two steps which affect the tissue temperature changing: heating step (due to the radiation from the node antenna and power consumption by the sensor circuit) and cooling step (due to time lapses between two rounds). At the heating step, the tissue temperature rises, by taking into account the SAR and Pc, while at the cooling step, the tissue temperature drops, by ignoring the effects of SAR and Pc in Eq. (10). Considering the current temperature of the underlying tissue of different sensors, the relay (forwarder) nodes at every round should be selected to avoid hotspot points.
3.5 Medium access control (MAC)
In WBANs, a collision may occur when more than one node transmits data at the same time. In this case, the collided packets have to be retransmitted, which consumes extra energy [62]. There are two types of MAC protocols to handle such collisions including contention-based and schedule-based protocols [63]. In contention-based protocols such as Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA), a node needs to compete with other nodes during the contention access period to get the channel for data transmission. If the channel is busy, the node defers its transmission until it becomes idle. These protocols are scalable with no strict time synchronization constraint. However, they incur significant protocol overhead. In contrast, schedule-based protocols such as Time Division Multiple Access (TDMA) divide the channel into time slots of fixed or variable duration determining when each node is allowed to transmit its data packet. Since the duty cycle of radio is reduced, there are no contention, idle listening, and overhearing problems [63].
Both TDMA and CSMA/CS protocols have their advantages and disadvantages. TDMA outperforms CSMA/CA in terms of energy efficiency, bandwidth utilization, and preferred traffic level [63]. However, TDMA has some shortcomings resulting from its disability for adapting to network dynamics and its dependency on time synchronization. All the sensors (with and without data transmission) are required to receive the periodic packets to synchronize their clocks. Therefore, CSMA/CA outperforms TDMA in term of latency, which is required for emergency applications, in which the MAC protocol should allow sensor nodes to get quick access to the channel via a real-time communication [53, 54]. Researchers have come to a common view that the CSMA/CA mechanism is more suitable for networks with urgent traffic and high network dynamics, while TDMA is more suitable for networks with high, periodic traffic and low network dynamics [64]. Majority of applications in WBANs are generally not of high dynamics. TDMA is the most preferred protocol in WBANs, as it provides slot reservation to nodes providing higher energy efficiency and reliability than CSMA/CA. Due to these advantages, many studies have been conducted on WBANs using the TDMA protocols [3, 4, 12, 39, 40, 53, 54, 65].
4 Proposed SIMOF routing protocol
As mentioned above, SIMOF is a combined online routing-offline tuning model, capable of responding to online routing requests of both normal and critical data packets upon receiving the routing request. SIMOF utilizes a real-time FIS for online routing and a metaheuristic algorithm (i.e., WOA) for offline tuning. To apply SIMOF for a new application, at first, the WOA algorithm is performed in an offline preprocessing step to adjust the controllable parameters of FIS according to the application requirements, only once before applying it for the given application. Then, the tuned FIS model is programmed on the processor unit of the sink node placed at the waist of the human body. The details of online routing and offline tuning procedure in the proposed SIMOF protocol are shown in Fig. 2.
SIMOF is a centralized protocol, in which all decisions about the routes are done by the tuned FIS model in the sink node. At every round, SIMOF operates in setup phase and steady-state phase. In the setup phase, sink determines the routing paths for the data transmission of all nodes using FIS, based on different criteria including energy level, distance, path loss, reliability, bandwidth, temperature, and energy consumption. Once all routes have been designed, sink creates two TDMA schedules: TDMA-1 determines when member nodes can communicate with their corresponding relay nodes, and TDMA-2 specifies when each direct node should send its data to sink. After creating the TDMA schedules, sink broadcasts a message into the network to inform all nodes about their current role (member, direct, or relay) and the TDMAs. In the steady-state phase, member nodes transmit their data to the corresponding relay nodes according to TDMA-1, and then, direct and relay nodes send their gathered data to the sink according to TDMA-2.
In SIMOF, only one- and two-hop transmission may be determined for each node. If one-hop transmission is selected for a node, it is known as a direct node and should send its data directly to the sink; otherwise, the node is known as a member node and sends its data though a relay node. The routing process in SIMOF can be reduced into two phases. At the first phase, the SIMOF selects some candidate nodes (as existed) for each member node. Then, at the second phase, a proper relay node is chosen for each member node using the multi-objective FIS. For any member node i, if there is no any candidate node, the member node is a direct node and transmits its data to the sink directly (one-hop communication). Otherwise, if there are one or more candidate nodes, the member node sends its data to the sink by help of a relay node (two-hop communication). In this case, a relay node (i.e., node j) is selected via the tuned Mamdani FIS.
4.1 Candidate node selection
At every round, for each member node i, the possibility of other nodes is justified to be selected as the relay node. Mathematically, node j can be selected as a candidate node to forward the data packet of node i, if all conditions in Eqs. (11)–(17) are established.
where N is the number of alive nodes, E(j) is the energy level of node j, D(i,j) is the Euclidean distance of node i to node j, PL(i,j) is the path loss of data transmission from node i to node j, R(i,j) is the reliability of link (i,j), B(i,j) is the bandwidth of link (i,j), T(j) is the underlying tissue temperature of node j, and EC(i,j) is the estimated energy dissipation to transmit data from node i to node j. Moreover, TE, TD, TPL, TR, TB, TT, and TEC are threshold parameters which determine the border of the candidate node selection.
4.2 Relay node selection
For every member node i, the FIS takes seven features from each candidate node j and generates the priority of the node j to be selected as the relay of node i, i.e., P(j,i). As shown in Fig. 2, the FIS includes fuzzification, fuzzy inference system, and defuzzification [66]. In the fuzzification step, input features of the candidate node j to be selected as the relay of node i are formulated in normal form according to Eqs. (18)–(24).
We consider five membership functions to fuzzify each crisp feature into fuzzy linguistic variables. As shown in Fig. 3, the input fuzzy membership functions include very small (VS), small (S), medium (M), large (L), and very large (VL). Moreover, as shown in Fig. 4, seven fuzzy membership functions are designed for the output (priority of nodes to be selected as relay node): very low (VL), low (L), rather low (RL), medium (M), rather high (RH), high (H), and very high (VH).
After fuzzification of the input parameters using Eqs. (18)–(24), the FIS proceeds the fuzzy rules stored in the fuzzy rule base table. By running the FIS for each candidate node j, some rules are fired and contribute to calculate the crisp output using the weighted averaging method according to Eq. (25), where \({out}_{m}^{j,i}\) is max–min fuzzy value of m-th fuzzy membership for the candidate node j to be selected as the relay of node i, \({\mu }_{m}\) is the center of m-th membership, and M is the number of output memberships, i.e., M = 7.
After calculation of the priority of all candidate nodes via the FIS, the candidate node with the highest priority is chosen as the relay node of the member node i.
5 Tuning of SIMOF using WOA
The FIS utilizes AND-based Mamdani fuzzy rules, and thus, there are totally 57 = 78,125 rules. Typically, fuzzy rules are determined manually by an expert. However, we tune these rules as well as the seven threshold parameters in Eqs. (11)–(17) via the WOA in an offline process (see Sect. 4.2). To adjust the parameters of the SIMOF, we design an offline tuning procedure using WOA to automatically tune the SIMOF according to the application requirements. WOA is a nature-inspired swarm intelligence metaheuristic which was firstly proposed by Mirjalili and Lewis in 2016 [67]. The search process in WOA starts with the generation of a random initial population. At every iteration of the algorithm, the fitness value of each whale is measured using the application-specific fitness function, and eventually, the population of whales is updated via three strategies: encircling prey, search for prey, and bubble-net attacking [68]. This procedure continuous until the pre-determined number of iterations is terminated.
The SIMOF has seven threshold parameters including TE, TD, TPL, TR, TB, TT, and TEC in Eqs. (11)–(17). Moreover, there are totally 78,125 fuzzy rules that also must be tuned via the WOA. Typically, fuzzy rules of the FISs are manually determined using an expert. However, there are some techniques in literature which directly or indirectly tune these rules via metaheuristic algorithms. In the direct techniques [69], the output of all rules is optimized, while in the indirect techniques [70, 71], the impact factors (IFs) of the fuzzy inputs into the output are subjected to be optimized. To adjust the rules of the SIMOF, we perform an indirect technique to optimize the seven IFs of the seven fuzzy inputs. Considering IE, IR, and IB, to be maximized, and ID, IPL, IT, and IEC, to be minimized, the output of the fuzzy rule r (r = 1,2,…,78,125) can be expressed as follows:
where IFE, IFD, IFPL, IFR, IFB, IFT, and IFEC are the IFs of the seven fuzzy inputs normalized in [0, 1] and \(\overline{{I }_{E}^{r}}\), \(\overline{{I }_{D}^{r}}\), \(\overline{{I }_{PL}^{r}}\), \(\overline{{I }_{R}^{r}}\), \(\overline{{I }_{B}^{r}}\), \(\overline{{I }_{T}^{r}}\), and \(\overline{{I }_{EC}^{r}}\) are the corresponding membership functions of the inputs IE, ID, IPL, IR, IB, IT, and IEC for the rule r, which are considered as 1 (VS), 2 (S), 3 (M), 4 (L), and 5 (VL). To obtain the final output for each rule, the values of Eq. (26) must be discretized into {1, 2,…, M} by utilizing Eq. (27), as follows:
A feasible solution S (i.e., each whale) to optimize SIMOF can be encoded as a string of length 14, including two strings of length 7, as seen in Fig. 5. All IFs are considered to have continuous values in [0, 1], while the allowable range of the threshold parameters are set as TE ∈ [0, 1], TD ∈ [1, 2], TPL ∈ [1, 2], TR ∈ [0, 5]%, TB ∈ [0, 2]MB/s, TT ∈ [0.2, 1]°C, and TEC ∈ [1, 2]. To generate the random initial population of the WOA, each whale takes a random value for each decision variable according to the allowable range of each variable.
To evaluate the fitness value of each whale, the WBAN should be simulated by the SIMOF, considering the parameters of the whale according to Fig. 5. Then, its fitness is measured via a multi-objective application-specific function, which comprises four sub-fitness functions to maximize FND, minimize path loss, maximize reliability, and minimize hotspot temperature (maximum temperature of the sensors). All sub-fitness functions are formulated in normal values between 0 and 1 and then converted into a single-objective fitness function (FitFun) by means of a weighted average, as follows:
where Lmax is the maximum expected FND network lifetime, THotSpot is the average temperature of the hotspot node over all rounds, and w1, w2, w3 and w4, are constant weights (w1 + w2 + w3 + w4 = 1), which adjust the relative impact of the FND, path loss, reliability, and hotspot temperature, within the FitFun, respectively. These weights should be set according to the application requirements. The more value of a weight, the more impact of the corresponding sub-fitness function.
To update each whale, a random value p in [0, 1] and a random vector A are generated. If p ≥ 1, the bubble-net attacking is used to update the solution. If p < 0.5 and |A|≥ 1, the whale is updated via the search for prey, and otherwise, if |A|< 1, the encircling prey is utilized.
5.1 Encircling prey
Each whale can identify the location of prey (the best solution found so far) and encircle it. At every iteration, the best solution found so far, i.e., S*, is identified, and other whales try to encircle it using the encircling prey operator according to Eq. (29), where a is a linearly decreasing parameter from 2 to 0, r is a random vector uniformly within [0, 1], t is the number of the current iteration.
5.2 Search for prey
Whales also move toward each other, to emphasize more exploration. It can be expressed by moving the whale toward a randomly selected whale Strand, as follows:
5.3 Bubble-net attacking
Whales have a helix-shape movement (bubble-net attacking behavior), which can be modeled via a spiral equation according to Eq. (31), where l is a uniform random parameter within [− 1, 1], and b is a constant parameter, typically set as b = 1.
6 Experimental results
The SIMOF protocol has been successfully developed in a personal computer with 2.5 GHz i7 processor and 12 GB memory running on MATLAB R2020b. In the following, the proposed SIMOF protocol is applied on three WBANs and compared with four existing techniques as follows:
6.1 Simulation settings
To justify the performance of the SIMOF protocol, three WBANs with different application-specific weights were carried out, as shown in Table 1. In all WBANs, FND is the most important measure, as the WBAN is not valid after the first node dies. Therefore, in all WBANs, half (50%) of the total weights is considered for the FND, i.e., w1 = 0.5. In WBAN 1, 10 sensor nodes in the frontside of the body are considered. As all sensor nodes as well as the sink are located at the same side, path loss exponent is assumed to be LOS, i.e., η = 3. As all nodes are located at the same side of the human body, it is expected to achieve high reliability and energy efficiency. However, as intermediate nodes between the sink and nodes are successively selected as relay nodes, they suffer from the hotspot problem, and may be rapidly dead. Therefore, FND and hotspot temperature are much more important than path loss and reliability. In WBAN 2, we add 5 nodes at beside of the body, where the path loss between beside and frontside nodes is assumed to be NLOS with η = 5. In this case, more weight is considered for the path loss. In WBAN 3, we add 5 more nodes at backside of the body, considering the path loss between backside and frontside nodes to be NLOS + with η = 7. In this case, more path loss and less reliability are obtained. Moreover, due to increasing the intermediate nodes, less hotspot problem is achieved.
The network parameters including technical specifications and experimental setups used in our experiments are summarized in Table 2. In all experiments, the workspace was designed as a 3D human body with the size of 1 m \(\times\) 2 m \(\times\) 0.5 m. There is only one sink placed at the belt of the patient at (0.5 m, 1 m, 0.5 m), to obtain the maximum efficiently and the minimum body movements. Each sensor node equips with a power supply with an initial energy of 10 Joule. One of the main advantages of the WOA is that it has few parameters to be set, i.e., only population size (PS) and maximum number of iterations (MNI). Generally, the more PS and MNI, the more chance to achieve a better solution by accepting more running time. In our simulations, we have set these parameters as PS = 50 and MNI = 100.
6.2 Simulation results
To evaluate the effects of the data transmission (heating) and the rest time between consecutive rounds (cooling) in the changes in the underlying tissue temperature for each node, the temperature of a member node per round is shown in Fig. 6. It can be seen that executing the rounds leads to increase the temperature from the body temperature of 37 ̊ C, but it would be saturated to around 37.28 ̊ C at round 1000. This figure represents the underlying tissue temperature of a sample member node, which is calculated using Eq. (10) during the execution of the SIMOF protocol. The more times that a sensor node is chosen as a relay node to forward the data packets of other nodes, the more increasing in the underlying tissue temperature.
As mentioned above, the SIMOF is an application-specific routing protocol that is automatically adjusted according to the application requirements. In order to tune the SIMOF for each WBAN, the WOA was performed once to optimize the hyperparameters of the SIMOF considering the importance weights according to Table 1. By performing the WOA for each WBAN, optimized hyperparameters of the SIMOF were obtained as summarized in Table 3. Based on the obtained results in Table 3, the energy level and temperature are the most important features, on average for all simulated WBANs. Afterward, energy consumption and path loss have more priorities than the other features. Another point is that by increasing the impact of the path loss (by considering more weight in the FitFun) in WBAN 2 against WBAN 1 and also in WBAN 3 against WBAN 2, the higher value for IFPL has been obtained. The importance of the distance is rather low, mainly because its effect can be handled indirectly through the minimization of the path loss and energy consumption. The results in Table 3 clearly demonstrate the ability of application-specific design of the proposed SIMOF protocol by automatically adjusting with the application specifications.
Figures 7, 8 and 9 statistically qualify different protocols in terms of alive nodes versus rounds in WBANs 1–3, respectively. These figures show the superiority of the SIMOF protocol against the other compared protocols. According to the obtained results, SIMOF achieves more stability among all techniques, as the first node dies later and the node deaths continues linearly until all nodes die. It can be seen that FND of the SIMOF protocol occurs much later than the other protocols and thus achieves more stability in WBANs, wherein, perishing a sensor may result critical damages. To numerically evaluate the obtained results, different lifetimes (FND, HND, and LND) are summarized in Table 4. Based on the results, the gain of SIMOF in FND for WBAN 1 is 132.6%, 9.7%, 32.2%, and 20.5%, as compared with the EECBR, EMRP, ESR-W, and FbRNS methods, respectively. This gain for WBAN 2 is 133.8%, 9.4%, 31%, and 23.9%, and for WBAN 3 is 246.9%, 45.1%, 52.8%, and 33.7%, as compared with the EECBR, EMRP, ESR-W, and FbRNS protocols, respectively. Another point is that EECBR and EMPR outperform SIMOF in terms of the LND metric in Figs. 8 and 9, respectively. However, as mentioned above, the validation of WBAN is gradually diminishing after the first node dies.
Comparison of the hotspot temperature of different techniques per rounds in WBANs 1–3 is provided in Figs. 10, 11 and 12, respectively. The results show the effectiveness of the SIMOF protocol to limit the hotspot temperature through the threshold parameter TT in Eq. (16) and the impact factor IFT in Eq. (26). As seen in Figs. 10, 11 and 12, the hotspot temperature has not violated the maximum allowable temperature Tb + TT in Eq. (11) which has been optimized as 37.54, 37.46, and 37.43 for WBANs 1–3, respectively.
Finally, the round history of alive nodes and the total number of data received at the sink are provided in Tables 5 and 6, respectively. Obviously as the SIMOF protocol achieves more FND against other techniques, the total number of data received at the sink increases more linearly until the first node dies. However, as summarized in Table 6, it drops rapidly after FND reaches. By more extending FND in the SIMOF protocol, more sensors are able to send their gathered data to the sink in much more rounds than the other protocols.
6.3 Discussion
In this section, we compare the proposed SIMOF protocol against the existing techniques in terms of performance measures and CPU running time. Comparison of different protocols according to different fitness functions in Eq. (28) including FND, PL, R, THotSpot, and FitFun is summarized in Table 7. Based on the obtained results, the maximum gain of the SIMOF protocol has been achieved in FND, and then, hotspot temperature is in the second rank. However, in some cases, the SIMOF achieved less PL or R, as we have considered less importance weights for them. Comparison of the obtained FitFun by different protocols for different WBANs is shown in Fig. 13. In overall, the SIMOF outperforms other protocols in term of FitFun, which is the main performance measure, as it aggregates all performance measures via a weighted averaging formula according to Eq. (28). According to the obtained results, the gain of the SIMOF protocol in FitFun for WBAN 1 is 51%, 13%, 27.1%, and 23.7%, as compared with the EECBR, EMRP, ESR-W, and FbRNS protocols, respectively. This gain for WBAN 2 is 85.2%, 21.4%, 29.9%, and 21.2%, and for WBAN 3 is 75%, 32.5%, 27.6%, and 26.6%, as compared with the EECBR, EMRP, ESR-W, and FbRNS protocols, respectively.
To evaluate the running time of different protocols, we compare them in terms of the total time required for the offline protocol tuning and online routing (for each round) in Table 8. According to the results, although the SIMOF protocol requires a lot of execution time in the offline tuning phase using WOA, the online routing time of the SIMOF protocol is in the range of other techniques. As the offline tuning procedure via WOA is done as a pre-processing step once before applying the SIMOF for the online routing, the time-consuming procedure of the offline procedure does not boost latency in the real-time data transmission phase.
7 Conclusion
In this paper, a swarm intelligence multi-objective fuzzy model, namely SIMOF, has been proposed as a tunable routing protocol in wireless body area networks. The SIMOF utilizes a multi-objective fuzzy inference system considering energy, distance, reliability, bandwidth, temperature, path loss, and energy consumption, to select proper relay nodes under IEEE 802.15.6. To achieve the best efficiency for each application, the Mamdani fuzzy rules of the SIMOF protocol have been automatically adjusted using whale optimization algorithm in an offline procedure. To justify the proposed SIMOF protocol, it has been compared against a classical protocol, an evolutionary-based protocol, and a fuzzy-based protocol. Simulation results in MATLAB over three networks have demonstrated the superiority of the SIMOF protocol against the existing techniques, in terms of the stability period, path loss, reliability, and hotspot temperature.
The proposed SIMOF routing protocol is a combined model based on online routing using a fuzzy heuristic and offline tuning using a metaheuristic algorithm. It gains the advantages of the both techniques, i.e., fast speed of fuzzy heuristics in real-time responding to online routing requests and high quality of metaheuristics in offline hyperparameter tuning. Although the SIMOF protocol is an accurate and fast-speed routing protocol, it needs a time-consuming hyperparameter tuning, which consumes 1–2 h in different WBANs for the tuning of the SIMOF once before applying the tuned SIMOF protocol for routing in a new WBAN application. In the proposed SIMOF protocol, Mamdani fuzzy inference system has been used. As a future work, other fuzzy models, e.g., Takagi–Sugeno fuzzy system, can be utilized to select proper relay nodes. Moreover, different metaheuristic algorithms such as genetic algorithm, differential evolution, simulated annealing, or grey wolf optimizer may be utilized to optimize the fuzzy system. In this paper, we have used a simplified model for the energy consumption of sensor nodes by only taking into account the radio reception and transmission (TX and RX) states. As a future work, the proposed protocol can be customized to include extra sources of energy consumption such as the energy corresponding to low power sleep mode or idle listening for a message. The tuned fuzzy model in SIMOF is used in sink, which is capable of responding to online routing requests of both normal and critical data packets upon receiving the routing request. So, as a future research direction, the proposed routing protocol can be extended to adapt with the reactive routing approaches. Moreover, other MAC protocols such as CSMA/CA could be utilized and compared with the TDMA protocol.
Availability of data and materials
The data analyzed in this paper are available from the corresponding author on reasonable request.
References
Wan T, Wang L, Liao W, Yue S (2021) A lightweight continuous authentication scheme for medical wireless body area networks. Peer-to-Peer Network Appl 14(6):3473–3487
Cornet B, Fang H, Ngo H, Boyer EW, Wang H (2022) An overview of wireless body area networks for mobile health applications. IEEE Netw 36(1):76–82
Ullah F, Khan MZ, Faisal M, Rehman HU, Abbas S, Mubarek FS (2021) An energy efficient and reliable routing scheme to enhance the stability period in wireless body area networks. Comput Commun 165:20–32
Esmaeili H, Bidgoli BM (2018) EMRP: evolutionary-based multi-hop routing protocol for wireless body area networks. AEU-Int J Electron Commun 93:63–74
Cicioğlu M, Çalhan A (2020) Energy-efficient and SDN-enabled routing algorithm for wireless body area networks. Comput Commun 160:228–239
Deepak KS, Babu AV (2012) Packet size optimization for energy efficient cooperative wireless body area networks. In: 2012 Annual IEEE India Conference (INDICON), pp 736–741. IEEE
Kurschl W, Mitsch S, Schönböck J (2009) Modeling distributed signal processing applications. In: 2009 6th International Workshop on Wearable and Implantable Body Sensor Networks, pp 103–108. IEEE
Dharshini PMP, Tamilarasi M (2014) Adaptive reliable cooperative data transmission technique for wireless body area network. In: International Conference on Information Communication and Embedded Systems (ICICES2014), pp 1–4. IEEE
Fotouhi M, Bayat M, Das AK, Far HAN, Pournaghi SM, Doostari MA (2020) A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Comput Netw 177:107333
Mana M, Rachedi A (2021) On the issues of selective jamming in IEEE 802.15.4-based wireless body area networks. Peer-to-Peer Netw Appl 14(1):135–150
Sohrabi M, Zandieh M, Afshar-Nadjafi B (2021) A simple empirical inventory model for managing the processed corneal tissue equitably in hospitals with demand differentiation. Comput Appl Math 40(8):1–38
Sandhu MM, Javaid N, Akbar M, Najeeb F, Qasim U, Khan ZA (2014) FEEL: forwarding data energy efficiently with load balancing in wireless body area networks. In: 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, pp 783–789. IEEE
Behura A, Kabat MR (2022) Optimization-based energy-efficient routing scheme for wireless body area network. In: Cognitive Big Data Intelligence with a Metaheuristic Approach, pp 279–303. Academic Press
Priya NS, Sasikala R, Alavandar S, Bharathi L (2022) Retraction note: security aware trusted cluster based routing protocol for wireless body sensor networks. Wireless Pers Commun 128:1501
Mortazavi A (2022) Interactive fuzzy Bayesian search algorithm: a new reinforced swarm intelligence tested on engineering and mathematical optimization problems. Expert Syst Appl 187:115954
Castillo O, Melin P, Ontiveros E, Peraza C, Ochoa P, Valdez F, Soria J (2019) A high-speed interval type 2 fuzzy system approach for dynamic parameter adaptation in metaheuristics. Eng Appl Artif Intell 85:666–680
Korenevskiy N, Petrovich SS, Al-Kasasbeh RT, Alqaralleh AA, Siplivyj GV, Alshamasin MS, Rodionova SN, Kholimenko IM, Ilyash MY (2023) Managing infectious and inflammatory complications in closed kidney injuries on the basis of fuzzy models. Int J Med Eng Inf 15(1):33–44
Castillo O, Amador-Angulo L (2018) A generalized type-2 fuzzy logic approach for dynamic parameter adaptation in bee colony optimization applied to fuzzy controller design. Inf Sci 460:476–496
Mortazavi A, Moloodpoor M (2021) Differential evolution method integrated with a fuzzy decision-making mechanism and Virtual Mutant agent: Theory and application. Appl Soft Comput 112:107808
Sohrabi, M, Zandieh M, Shokouhifar M (2023) Sustainable inventory management in blood banks considering health equity using a combined metaheuristic-based robust fuzzy stochastic programming. Socio-Economic Plan Sci 101462
Shokouhifar M, Hassanzadeh A (2014) An energy efficient routing protocol in wireless sensor networks using genetic algorithm. Adv Environ Biol 8(21):86–93
Shokouhifar M, Jalali A (2015) A new evolutionary based application specific routing protocol for clustered wireless sensor networks. AEU-Int J Electron Commun 69(1):432–441
Dhanvijay MM, Patil SC (2021) Energy aware MAC protocol with mobility management in wireless body area network. Peer-to-Peer Netw Appl 15:426–443
Ghasemi Darehnaei Z, Shokouhifar M, Yazdanjouei H, Rastegar Fatemi SMJ (2022) SI-EDTL: Swarm intelligence ensemble deep transfer learning for multiple vehicle detection in UAV images. Concurr Comput Pract Exp 34(5):e6726
Braem B, Latre B, Moerman I, Blondia C, Demeester P (2006) The wireless autonomous spanning tree protocol for multihop wireless body area networks. In: 2006 3rd Annual International Conference on Mobile and Ubiquitous Systems: Networking & Services, pp 1–8. IEEE
Braem B, Latré B, Blondia C, Moerman I, Demeester P (2008) Improving reliability in multi-hop body sensor networks. In: 2008 Second International Conference on Sensor Technologies and Applications (SENSORCOMM 2008), pp 342–347). IEEE
Elhadj HB, Chaari L, Kamoun L (2012) A survey of routing protocols in wireless body area networks for healthcare applications. Int J E-Health Med Commun (IJEHMC) 3(2):1–18
Tang Q, Tummala N, Gupta SK, Schwiebert L (2005) Communication scheduling to minimize thermal effects of implanted biosensor networks in homogeneous tissue. IEEE Trans Biomed Eng 52(7):1285–1294
Bag A, Bassiouni MA (2006) Energy efficient thermal aware routing algorithms for embedded biomedical sensor networks. In: 2006 IEEE International Conference on Mobile Ad Hoc and Sensor Systems, pp 604–609. IEEE
Ahmed O, Ren F, Hawbani A, Al-Sharabi Y (2020) Energy optimized congestion control-based temperature aware routing algorithm for software defined wireless body area networks. IEEE Access 8:41085–41099
Javaid N, Abbas Z, Fareed MS, Khan ZA, Alrajeh N (2013) M-ATTEMPT: a new energy-efficient routing protocol for wireless body area sensor networks. Procedia Comput Sci 19:224–231
Ahmad A, Javaid N, Qasim U, Ishfaq M, Khan ZA, Alghamdi TA (2014) RE-ATTEMPT: a new energy-efficient routing protocol for wireless body area sensor networks. Int J Distrib Sens Netw 10(4):464010
Jiang W, Wang Z, Feng M, Miao T (2017) A survey of thermal-aware routing protocols in wireless body area networks. In: 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), vol 2, pp 17–21. IEEE
Movassaghi S, Abolhasan M, Lipman J, Smith D, Jamalipour A (2014) Wireless body area networks: a survey. IEEE Commun Surv Tutor 16(3):1658–1686
Jan B, Farman H, Javed H, Montrucchio B, Khan M, Ali S (2017) Energy efficient hierarchical clustering approaches in wireless sensor networks: a survey. Wireless Commun Mobile Comput 2017:1–14
Watteyne T, Augé-Blum I, Dohler M, Barthel D (2007). AnyBody: a self-organization protocol for body area networks. In: BODYNETS, p 6
Shokouhifar M (2021) Swarm intelligence RFID network planning using multi-antenna readers for asset tracking in hospital environments. Comput Netw 198:108427
Jafari R, Effatparvar M (2017) Cooperative routing protocols in wireless body. Int J Comput Inf Technol 5:43–51
Nadeem Q, Javaid N, Mohammad SN, Khan MY, Sarfraz S, Gull M (2013) Simple: Stable increased-throughput multi-hop protocol for link efficiency in wireless body area networks. In: 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, pp 221–226. IEEE
Javaid N, Ahmad A, Nadeem Q, Imran M, Haider N (2015) iM-SIMPLE: iMproved stable increased-throughput multi-hop link efficient routing protocol for Wireless Body Area Networks. Comput Hum Behav 51:1003–1011
Anand J, Sethi D (2017) Comparative analysis of energy efficient routing in WBAN. In: 2017 3rd International Conference on Computational Intelligence & Communication Technology (CICT), pp 1–6. IEEE
Ha I (2016) Even energy consumption and backside routing: an improved routing protocol for effective data transmission in wireless body area networks. Int J Distrib Sens Netw 12(7):1550147716657932
Shunmugapriya B, Paramasivan B (2022) Fuzzy based relay node selection for achieving efficient energy and reliability in wireless body area network. Wireless Pers Commun 122(3):2723–2743
Esmaeili H, Hakami V, Bidgoli BM, Shokouhifar M (2022) Application-specific clustering in wireless sensor networks using combined fuzzy firefly algorithm and random forest. Expert Syst Appl 210:118365
Umer T, Amjad M, Afzal MK, Aslam M (2016) Hybrid rapid response routing approach for delay-sensitive data in hospital body area sensor network. In: Proceedings of the 7th International Conference on Computing Communication and Networking Technologies, pp 1–7
Mehmood G, Khan MZ, Abbas S, Faisal M, Rahman HU (2020) An energy-efficient and cooperative fault-tolerant communication approach for wireless body area network. IEEE Access 8:69134–69147
Dharshini S, Subashini MM (2022) Cantor Pairing lightweight key generation for wireless body area networks. Smart Health 25:100298
Karunanithy K, Velusamy B (2022) Edge device based efficient data collection in smart health monitoring system using wireless body area network. Biomed Signal Process Control 72:103280
Khan Z, Aslam N, Sivakumar S, Phillips W (2012) Energy-aware peering routing protocol for indoor hospital body area network communication. Procedia Comput Sci 10:188–196
Khan Z, Sivakumar S, Phillips W, Robertson B (2012) QPRD: QoS-aware peering routing protocol for delay sensitive data in hospital body area network communication. In: 2012 7th International Conference on Broadband, Wireless Computing, Communication and Applications, pp 178–185. IEEE
Kamruzzaman MM, Alruwaili O (2022) Energy efficient sustainable Wireless Body Area Network design using network optimization with Smart Grid and Renewable Energy Systems. Energy Rep 8:3780–3788
El Azhari M, El Moussaid N, Toumanari A, Latif R (2017) Equalized energy consumption in wireless body area networks for a prolonged network lifetime. Wireless Commun Mobile Comput 2017:1–9
Ragesh GK, Baskaran K (2012) A survey on futuristic health care system: WBANs. Procedia Eng 30:889–896
Shunmugapriya B, Paramasivan B (2022) Design of three tier hybrid architecture combing TDMA-CDMA techniques to mitigate interference in WBAN. Wireless Pers Commun 125(2):1585–1614
Javaid N, Khan NA, Shakir M, Khan MA, Bouk SH, Khan ZA (2013) Ubiquitous healthcare in wireless body area networks-a survey. http://arxiv.org/abs/1303.2062
Ullah F, Khan MZ, Mehmood G, Qureshi MS, Fayaz M (2022) Energy efficiency and reliability considerations in wireless body area networks: a survey. Comput Math Methods Med 2022:1–15
Khan ZA, Sivakumar S, Phillips W, Robertson B (2014) ZEQoS: a new energy and QoS-aware routing protocol for communication of sensor devices in healthcare system. Int J Distrib Sens Netw 10(6):627689
Kim BS, Kim KI, Shah B, Ullah S (2019) A forwarder based temperature aware routing protocol in wireless body area networks. J Internet Technol 20(4):1157–1166
Hoque AKMF, Hossain MS, Mollah AS, Akramuzzaman M (2013) A study on specific absorption rate (SAR) due to nonionizing radiation from wireless/telecommunication in Bangladesh. Am J Phys Appl 1(3):104–110
Kim BS, Shah B, Al-Obediat F, Ullah S, Kim KH, Kim KI (2018) An enhanced mobility and temperature aware routing protocol through multi-criteria decision making method in wireless body area networks. Appl Sci 8(11):2245
Ahmad S, Hussain I, Fayaz M, Kim DH (2018) A distributed approach towards improved dissemination protocol for smooth handover in mediasense IoT platform. Processes 6(5):46
Ullah S, Shen B, Islam SR, Khan P, Saleem S, Kwak KS (2009) A study of MAC protocols for WBANs. Sensors 10(1):128–145
Shu M, Yuan D, Zhang C, Wang Y, Chen C (2015) A MAC protocol for medical monitoring applications of wireless body area networks. Sensors 15(6):12906–12931
Marinkovic SJ, Popovici EM, Spagnol C, Faul S, Marnane WP (2009) Energy-efficient low duty cycle MAC protocol for wireless body area networks. IEEE Trans Inf Technol Biomed 13(6):915–925
Hwang TM, Jeong SY, Kang SJ (2018) Wireless TDMA-based body area network platform gathering multibiosignals synchronized with patient’s heartbeat. Wirel Commun Mob Comput 2018:1–14
Moharamkhani E, Zadmehr B, Memarian S, Saber MJ, Shokouhifar M (2021) Multiobjective fuzzy knowledge-based bacterial foraging optimization for congestion control in clustered wireless sensor networks. Int J Commun Syst 34:e4949
Mirjalili S, Lewis A (2016) The whale optimization algorithm. Adv Eng Softw 95:51–67
Shokouhifar M, Sabbaghi MM, Pilevari N (2021) Inventory management in blood supply chain considering fuzzy supply/demand uncertainties and lateral transshipment. Trans Apher Sci 60:103103
Shokouhifar M, Jalali A (2017) Optimized sugeno fuzzy clustering algorithm for wireless sensor networks. Eng Appl Artif Intell 60:16–25
Shokouhifar M (2021) FH-ACO: fuzzy heuristic-based ant colony optimization for joint virtual network function placement and routing. Appl Soft Comput 107:107401
Fanian F, Rafsanjani MK, Saeid AB (2021) Fuzzy multi-hop clustering protocol: Selection fuzzy input parameters and rule tuning for WSNs. Appl Soft Comput 99:106923
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
PA involved in conceptualization, methodology, visualization, software, writing—original draft preparation, writing—reviewing and editing. AK took part in methodology, investigation, formal analysis, writing—reviewing and editing. SJJ took part in methodology, conceptualization, validation, writing—reviewing and editing. MH involved in formal analysis, validation, writing—reviewing and editing.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest to report regarding the present study.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Aryai, P., Khademzadeh, A., Jafarali Jassbi, S. et al. SIMOF: swarm intelligence multi-objective fuzzy thermal-aware routing protocol for WBANs. J Supercomput 79, 10941–10976 (2023). https://doi.org/10.1007/s11227-023-05102-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-023-05102-9